Chapter 4. Designing a Comprehensive Network Security Solution
In this last chapter, we cover a use case and take what you’ve learned throughout this book to apply a comprehensive solution to a particular set of business requirements for a fictitious company, XYZ Corp.
XYZ Corp
XYZ Corp is a holding company that has traditionally had on-premises computing assets in the form of web servers. XYZ is a reseller of online advertising. As such, it hasn’t really traditionally stored much sensitive information directly about customers. XYZ Corp is diversifying within the marketing space and has recently purchased a direct online advertiser.
From a business standpoint this means that the type of data that will be processed by XYZ Corp will include customer information across multiple geographies. The company needs to scale its advertising campaigns quickly so that it is expanding into the cloud to take advantage of IaaS services.
XYZ Corp has asked you come up with a security architecture that addresses its existing on-premises assets as well as its new cloud footprint. The company also needs the architecture to take into account the protection of sensitive information, which it is processing as part of its direct marketing campaigns. XYZ Corp advertising campaigns require HA because they are time sensitive. It plans to run its own email infrastructure to facilitate these campaigns. The company will also be using some third-party APIs for SMS and other messaging platforms.
From an architectural perspective, let’s distill XYZ Corp’s requirements into some key considerations:
-
Data security
-
Hybrid cloud deployment
-
Heavy mail usage
-
API integration
-
Cloud/internet presence—protection against DDoS and bots
-
Global audience
-
Data is subject to regulation such as the EU’s General Data Protection Regulation (GDPR)
Let’s distill the company’s requirements into a core WAF architecture, as referenced in Figure 4-1.
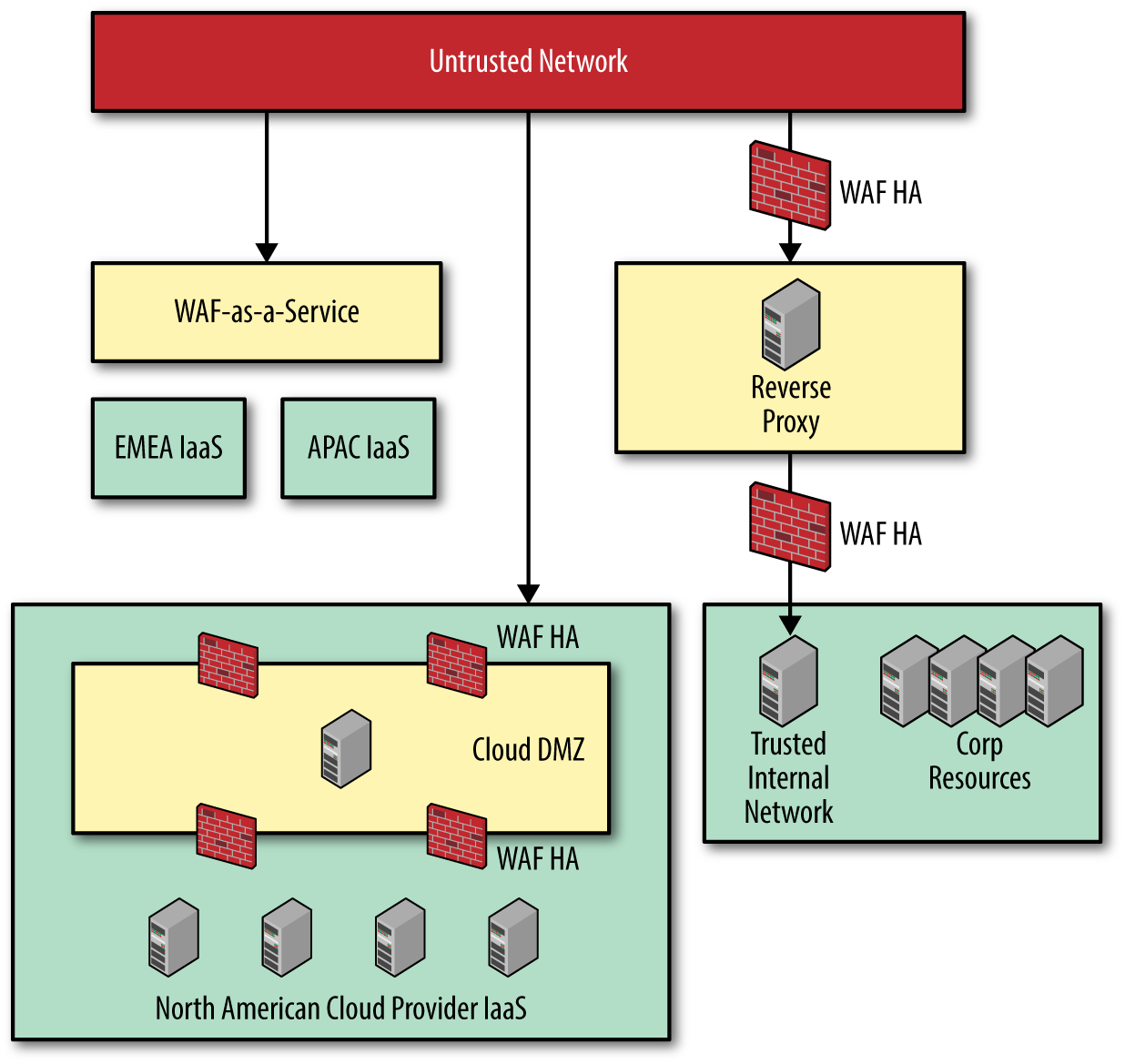
Figure 4-1. Core WAF architecture
Figure 4-1 illustrates that we have an HA WAF sandwich–style architecture for both the on-premises deployment and the cloud environment. XYZ Corp wants HA, and it needs the highest levels of security for both its cloud and on-premises infrastructure.
Although the architecture looks very similar between both the on-premises and cloud environments, there are some semantic differences. The on-premises architecture is using physical WAF appliances, whereas the cloud deployment is utilizing software-based WAF appliances. Additionally, XYZ Corp has determined that it will need smaller cloud points-of-presence in the APAC and EMEA regions. These are not large enough to necessarily justify the overhead of procuring and managing WAFs, so XYZ Corp decided to use WAF-as-a-Service for these IaaS clouds.
So, how do we begin to achieve and address the original business requirements with this core component of the security architecture?
-
Data security: SQL injection, web app protection—OWASP Top 10
-
Hybrid cloud deployment: software-based appliance for cloud, hardware-based appliance for on-premises, and WAF-as-a-Service for smaller cloud points-of-presence in EMEA and APAC
-
Heavy mail usage: TBD
-
API integration: TBD
-
Cloud/internet presence: software-based appliance for cloud and hardware-based appliance for on-premises—protection against DDoS and bot
-
Global audience: software-based appliance for cloud, hardware-based appliance for on-premises, and WAF-as-a-Service for smaller cloud points-of-presence in EMEA and APAC
-
Data subject to regulation such as the EU’s General Data Protection Regulation (GDPR): OWASP application protection
Although WAFs address many of these business security requirements, there are some that they do not address directly. This will require you to build off of your WAF core and augment with some adjacent services.
You still have some outlying requirements to address. Specifically, the API and email-specific requirements. Why don’t the WAFs address these directly? Well, as I mentioned earlier, WAFs are very HTTP specific. With email, we are talking about SMTP and a mix of other potential protocols such as IMAP and POP3. And although the APIs are largely going to be SOAP or REST oriented over HTTP, the handling of API traffic is better suited to API gateway–specific devices. API gateway devices recognize REST and SOAP formats and act as an enforcement point and abstraction layer for web-based API calls.
So, XYZ Corp could go in a few different directions to address these adjacent issues. It could use some sort of on-premises email gateway filtering solution or outsource it altogether as a service. XYZ Corp decides to outsource its email filtering and protection to a third-party provider.
For API gateway services, the company decides to deploy API gateways in an HA configuration across its various points of presence. It places these HA API gateway pairs in the DMZs of its points-of-presence, respectively.
For API gateway services, XYZ Corp decides to deploy API gateways in an HA configuration across its various points of presence. It places these HA API gateway pairs in the DMZs of their points-of-presence, respectively, as illustrated in Figure 4-2.
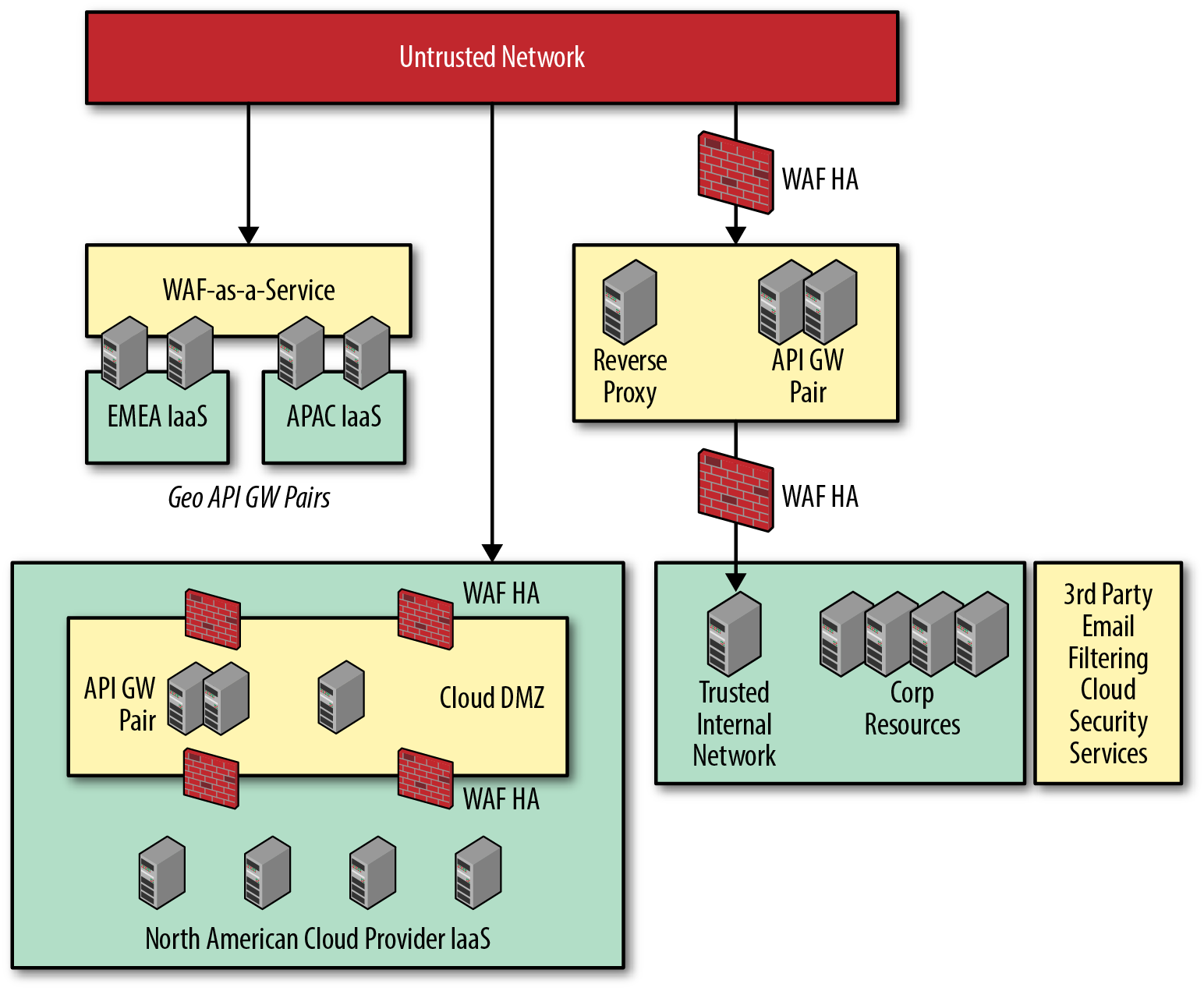
Figure 4-2. Core WAF and adjacent technologies
A Note About Native Cloud Security Services versus Specialized Services
Big cloud providers such as AWS have begun to offer additional security services as part of its traditional IaaS offerings. For instance, AWS offers an API gateway service and a WAF service.
Simply put, these are basic services. I encourage you to perform you own analysis, but generally speaking, they address some of the lowest common denominators in terms of threat protection. Sometimes, these solutions are viewed as a “good-enough” or “better-than-nothing” approach. They lack many of the advanced features such as protection against DDoS, bot, and account takeover, among others.
