B. The SSL/TLS Protocol
by Gene Spafford, Simson Garfinkel
Web Security, Privacy & Commerce, 2nd Edition
B. The SSL/TLS Protocol
by Gene Spafford, Simson Garfinkel
Web Security, Privacy & Commerce, 2nd Edition
- Web Security, Privacy & Commerce, 2nd Edition
- Message Digest Functions
- 4. Cryptography and the Web
- What Cryptography Can’t Do
- Legal Restrictions on Cryptography
- 5. Understanding SSL and TLS
- 6. Digital Identification I: Passwords, Biometrics, and Digital Signatures
- 7. Digital Identification II: Digital Certificates, CAs, and PKI
- Understanding Digital Certificates with PGP
- Certification Authorities: Third-Party Registrars
- Public Key Infrastructure
- Open Policy Issues
- Private Keys Are Not People
- Distinguished Names Are Not People
- There Are Too Many Robert Smiths
- Today’s Digital Certificates Don’t Tell Enough
- X.509 v3 Does Not Allow Selective Disclosure
- Digital Certificates Allow for Easy Data Aggregation
- How Many CAs Does Society Need?
- How Do You Loan a Key?
- Why Do These Questions Matter?
- Brad Biddle on Digital Signatures and E-SIGN
- E-SIGN and UETA
- Electronic contracting—it’s more than just “signatures”!
- “Signed writing” requirements
- Proof
- II. Privacy and Security for Users
- 8. The Web’s War on Your Privacy
- 9. Privacy-Protecting Techniques
- Choosing a Good Service Provider
- Picking a Great Password
- Cleaning Up After Yourself
- Avoiding Spam and Junk Email
- Identity Theft
- 10. Privacy-Protecting Technologies
- 11. Backups and Antitheft
- 12. Mobile Code I: Plug-Ins, ActiveX,and Visual Basic
- 13. Mobile Code II: Java, JavaScript, Flash, and Shockwave
- III. Web Server Security
- 14. Physical Security for Servers
- Planning for the Forgotten Threats
- Protecting Computer Hardware
- Protecting Your Data
- Personnel
- Story: A Failed Site Inspection
- 15. Host Security for Servers
- 16. Securing Web Applications
- 17. Deploying SSL Server Certificates
- Planning for Your SSL Server
- Creating SSL Servers with FreeBSD
- Installing an SSL Certificate on Microsoft IIS
- Obtaining a Certificate from a Commercial CA
- When Things Go Wrong
- 18. Securing Your Web Service
- 19. Computer Crime
- 14. Physical Security for Servers
- IV. Security for Content Providers
- 20. Controlling Access to Your Web Content
- Access Control Strategies
- Controlling Access with Apache
- Enforcing Access Control Restrictions with the .htaccess File
- Enforcing Access Control Restrictions with the Web Server’s Configuration File
- Commands Before the <Limit>. . . </Limit> Directive
- Commands Within the <Limit>. . . </Limit> Block
- <Limit> Examples
- Manually Setting Up Web Users and Passwords
- Advanced User Management
- Controlling Access with Microsoft IIS
- 21. Client-Side Digital Certificates
- 22. Code Signing and Microsoft’s Authenticode
- 23. Pornography, Filtering Software, and Censorship
- 24. Privacy Policies, Legislation, and P3P
- 25. Digital Payments
- 26. Intellectual Property and Actionable Content
- 20. Controlling Access to Your Web Content
- V. Appendixes
- A. Lessons from Vineyard.NET
- In the Beginning
- Planning and Preparation
- Lesson: Whenever you are pulling wires, pull more than you need.
- Lesson: Pull all your wires in a star configuration, from a central point out to each room, rather than daisy-chained from room to room. Wire both your computers and your telephone networks as stars.
- Lesson: Use centrally located punch-down blocks for computer and telephone networks.
- Lesson: Don’t go overboard.
- Lesson: Plan your computer room carefully; you will have to live with its location for a long time.
- IP Connectivity
- Commercial Start-Up
- Ongoing Operations
- Security Concerns
- Lesson: Don’t run programs with a history of security problems.
- Lesson: Make frequent backups.
- Lesson: Limit logins to your servers.
- Lesson: Beware of TCP/IP spoofing.
- Lesson: Defeat packet sniffing.
- Lesson: Restrict logins.
- Lesson: Tighten up your system beyond manufacturer recommendations.
- Lesson: Remember, the “free” in “free software” refers to “freedom.”
- Phone Configuration and Billing Problems
- Credit Cards and ACH
- Lesson: If you have the time to write it, custom software always works better than what you can get off the shelf.
- Lesson: Live credit card numbers are dangerous.
- Lesson: Encrypt sensitive information and be careful with your decryption keys.
- Lesson: Log everything, and have lots of reports.
- Lesson: Explore a variety of payment systems.
- Lesson: Make it easy for your customers to save you money.
- Lesson: Have a backup supplier.
- Monitoring Software
- Security Concerns
- Redundancy and Wireless
- The Big Cash-Out
- Conclusion
- B. The SSL/TLS Protocol
- C. P3P: The Platform for Privacy Preferences Project
- D. The PICS Specification
- E. References
- Electronic References
- Paper References
- A. Lessons from Vineyard.NET
- Index
- About the Authors
- Colophon
This appendix describes the SSL Version 3.0 protocol introduced in Chapter 5. It gives a general overview of the protocol that’s appropriate for a semi-technical audience.
The Internet Engineering Task Force (IETF) Transport Layer Security (TLS) working group was established in 1996 to create an open stream encryption standard. The group began working with SSL Version 3.0 and, in 1999, published RFC 2246. “TLS Protocol Version 1.0” RFC 2712 adds Kerberos authentication to TLS. RFC 2817 and 2818 apply to TLS using HTTP/1.1.
TLS is a general-purpose protocol for encrypting web, email, and other stream-oriented information sent over the Internet. But while TLS may eventually supersede SSL, it could be years before this happens. Even once TLS becomes widely used, people may still call it SSL by sheer force of habit.
The charter for the TLS working group can be found at http://www.ietf.org/html.charters/tls-charter.html.
The SSL protocol was designed by Netscape Communications for use with Netscape Navigator. Version 1.0 of the protocol was used inside Netscape. Version 2.0 of the protocol shipped with Netscape Navigator Versions 1 and 2. After SSL 2.0 was published, Microsoft created a similar secure link protocol called PCT (described briefly in Chapter 5) that it claimed overcame some of SSL 2.0’s shortcomings. However, PCT generally annoyed the rest of the industry, which claimed that Microsoft wasn’t interested in working with standards bodies and was more interested in doing things its own way. The advances of PCT were incorporated into SSL 3.0, which was used as the basis for the TLS protocol developed by the IETF.
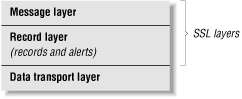
The TLS protocol is arranged in two layers:
The TLS Record Protocol, which is responsible for transmitting blocks of information called records between the two computers.
The TLS Handshake protocol, which manages key exchange, alerts, and cipher changes.
These two layers are built on top of a third layer, which is not strictly part of SSL:
The data transport layer (usually TCP/IP)
These layers are illustrated in Figure B-1.
-
No Comment