Authenticode is a system developed by Microsoft for digitally signing executable code. Authenticode was publicly announced in June of 1996 as part of Microsoft’s Internet Explorer 3.0 and ActiveX technologies.
ActiveX is a system for downloading programs from web pages to end user computers. There are considerable security issues associated with ActiveX. Authenticode was designed to mitigate these dangers by making software publishers accountable for programs they write. (ActiveX and the security provided by Authenticode is discussed in detail in Chapter 4.)
Authenticode describes a series of file formats for signing Microsoft 32-bit EXE, DLL, and OCX files. The signed file contains the original unsigned file, the digital signature, and an X.509 v3 digital certificate for the public key needed to verify the Authenticode signature. Authenticode cannot sign Windows COM files or 16-bit EXE files.
Microsoft and VeriSign require that all software publishers take the “Software Publisher’s Pledge.” The pledge is a binding agreement in which the software publisher promises not to sign programs that contain viruses or that will otherwise damage a person’s computer.
The Pledge is described in Section 4 of the VeriSign certification practice statement and is reprinted here:
In addition to the other representations, obligations, and warranties contained or referenced in the certificate application, the [individual] [commercial] software publisher certificate applicant represents and warrants that he, she, or it shall exercise reasonable care consistent with prevailing industry standards to exclude programs, extraneous code, viruses, or data that may be reasonably expected to damage, misappropriate, or interfere with the use of data, software, systems, or operations of the other party.
This software publisher’s pledge is made exclusively by the [individual] [commercial] software publisher certificate applicant. Issuing authorities and VeriSign shall not be held responsible for the breach of such representations and warranties by the [individual] [commercial] software publisher under any circumstance.
The Authenticode Pledge can’t make software signed by Authenticode software publisher’s keys more secure. What the Pledge actually does is give certification authorities grounds for revoking software publisher certificates that are used to sign code that does not comply with the Pledge’s terms.
To publish with Authenticode, it is necessary to have a copy of the Microsoft ActiveX Software Developer’s Kit (SDK). This kit can be freely downloaded from Microsoft’s web site at http://www.microsoft.com/activex/. It is likely that the ActiveX SDK will be included with future versions of Microsoft’s developer systems.
For developers, signing an application program represents an additional step that must be followed to publish a program. Complicating matters, signing a program must be the last thing that is done to a program before it is released, because if you make any changes to the program after it is signed, it will need to be signed again.
If you distribute your program as part of a self-extracting installer, you should sign both the program itself and the installer.
Microsoft’s
signcode
program has the following syntax:[50]
signcode -prog ProgramFile -spc credentialsFile -pvk privateKeyFile
-name opusName -info opusInfo -gui -nocerts
-provider cryptoProviderName -providerType n
{-commercial | -individual*}
{-sha | -md5*}If the program is run without any arguments, the signcode program runs the Code Signing Wizard (CSW) (see the following section).
In the following example, a program called notepad.exe is signed by a private key called classII. Signing the program increased the program’s file size by 7,064 bytes:
C:>dir notepad.exeVolume in drive C has no label Volume Serial Number is 3359-1BF8 Directory of C: NOTEPAD EXE 34,304 07-11-95 9:50a NOTEPAD.EXE 1 file(s) 34,304 bytes 0 dir(s) 29,196,288 bytes free C:>signcode -prog notepad.exe -name notepad -info http://www.microsoft.com -pvk classIIC:>dir notepad.exeVolume in drive C has no label Volume Serial Number is 3359-1BF8 Directory of C: NOTEPAD EXE 41,368 11-23-96 4:58p NOTEPAD.EXE 1 file(s) 41,368 bytes 0 dir(s) 29,196,288 bytes free C:>
Microsoft employees have said that when non-Microsoft programmers sign programs such as notepad.exe (which is distributed as part of Windows), they are violating the Software Publisher’s Pledge. Why? Because they cannot be sure that the program was created with the care consistent with prevailing industry standards to exclude programs, code, or viruses that might destroy data or damage systems.
Microsoft’s ActiveX Software Developer’s Kit includes a Code Signing Wizard that has an easy-to-use interface for signing code. The CSW’s splash screen (Figure 9.2) is displayed when the signcode program is run without sufficient arguments.
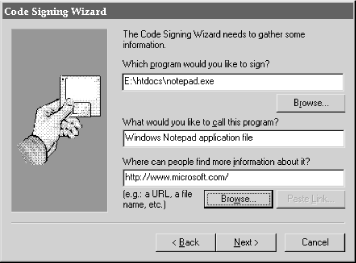
The CSW’s second screen (Figure 9.3) allows the developer to specify what program will be signed and what information will be displayed on the program’s certificate when the code is validated. It contains a URL that can be clicked on to provide more information about the program. The full name and URL are displayed on the program’s certificate when its digital signature is checked.
Next, the developer specifies which key should be used to sign the program, what credentials are used for the key, and what cryptographic digest algorithm is used for the signature (see Figure 9.4). The information is then verified (see Figure 9.5).
Figure 9-5. The fourth step is to validate all of the information that will be used to sign the binary
Finally, the developer signs the executable (see Figure 9.6).
Currently, Authenticode signatures can only be verified by programs that are developed with the Microsoft ActiveX Software Developer’s Toolkit.
The ActiveX SDK includes a program called chktrust that allows users to check the certificate on an executable. If the program being checked is signed, chktrust displays the certificate and asks the user if he wishes to trust it. If the program being checked is not signed, or if the user chooses not to trust it, the chktrust program returns an error code.
The chktrust program has these options:
C:>chktrust
Usage: CHKTRUST [-options] file-name
Options:
-I subject type is PE executable image file (default)NOTEPAD.EXE
-J subject type is Java class
-C subject type is Cabinet file
-N no UI in 'bad trust' case
C:>When chktrust is run, it displays a fancy certificate if the binary is signed showing the name of the person or organization on the certificate that signed it, and the name of the certification authority that signed the certificate (see Figure 9.7). Clicking the check-box at the bottom causes the program to stop displaying certificates and to always accept them. Clicking the “Advanced” button causes the program to display the list of approved software publishers. If the program is not signed, a warning window is displayed instead (see Figure 9.8).
Figure 9-7. The chktrust program displays a fancy certificate when it encounters a signed executable
The chktrust program returns a result of “0” if the user has decided to trust the program:
C:>chktrust signed.exe
Result: 0
C:>If the user decides against trusting the program, something else is displayed:
C:>chktrust unsigned.exe
Result: 800b0004
C:>Actual programs that wish to check signatures would simply use the APIs used by the chktrust program.
Microsoft (partially) acknowledges the potential dangers of ActiveX. However, their official position is that the solution to the security problem is not to limit what downloaded ActiveX controls can do. It can’t. Once an ActiveX control is running on your computer, there is nothing that it can’t do. It can steal your confidential documents, for example. The theory behind Authenticode is that the user will realize when a control has done damage and the user will take some form of legal action. For example, the user might contact the software publisher and seek redress. If that doesn’t work, the user might take the ActiveX publisher to court.
Microsoft’s solution is to provide traceability of the authors of ActiveX controls. This traceability is provided through the use of digital signatures and Microsoft’s Authenticode technology.
Microsoft’s Internet Explorer can be run with several different security levels. The program’s default is the highest level. When run at this level, Internet Explorer will only execute ActiveX controls that have been digitally signed by a secret key for which there exists a valid software publisher’s digital certificate. Version 3.0 of Internet Explorer recognizes two kinds of software publisher certificates: the VeriSign individual software publisher certificate and the VeriSign commercial software publisher certificate.
When Internet Explorer encounters a signed ActiveX control, it will show the user the name of the person or organization who signed it and the name of the certification authority that signed the software publisher’s digital certificate. The user is given the choice as to whether or not this particular software publisher is trusted. The user interface allows the user to say that a particular software publisher should always be trusted. The user can also choose to have all commercial software publishers unconditionally trusted.
Authenticode is controlled from the Properties window of “The Internet” icon (on the desktop) or from the Options window of Internet Explorer. (These are actually the same windows.) By selecting the “Security” tab of the window, the user can choose whether or not “Active Content” (such as ActiveX controls and Java programs) are downloaded and executed (see Figure 9.9). Pushing the button labeled “Safety Level” allows you to choose between three different settings for ActiveX:
- High
Only signed ActiveX controls will be executed.
- Medium
Users are told whether ActiveX controls are signed or not. Unsigned controls may be run at the user’s discretion.
- None
All ActiveX controls are executed, whether they are signed or not.
Figure 9-9. Microsoft Internet Explorer’s Security Preferences allow you to control whether or not ActiveX content is executed
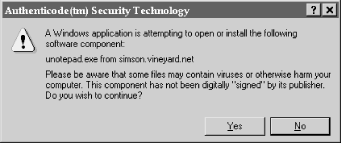
Internet Explorer will also check programs that are downloaded to see if they are or are not digitally signed. If the user attempts to download an unsigned binary with Internet Explorer, a window is displayed similar to the one in Figure 9.10.
Figure 9-10. A window displayed by Microsoft Internet Explorer when an unsigned application or component is downloaded
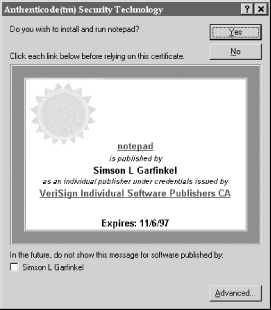
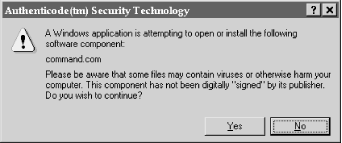
If the binary is signed, Internet Explorer will display a certificate. Binaries signed with commercial keys display a pretty certificate, such as the one shown in Figure 9.11. Internet Explorer displays binaries signed with individual keys using a plain certificate. Internet Explorer warns the user if unsigned code is being downloaded, as shown in Figure 9.12. However, the warning is misleading, because signed code can also “contain viruses or otherwise harm your computer.”