15
NFV and NFV-based Security Services
Wenjing Chu
Futurewei Technologies, Inc.
15.1 Introduction
In this chapter, we discuss 5G and security in the context of Network Functions Virtualization (NFV), a new transformative technology that combines the technology developments in distributed systems, software virtualization, and cloud computing to modernize telecommunication infrastructure and services. We will cover the content in three parts. The first part will discuss what NFV is and how NFV relates to 5G and security. In the second part, we survey the new security challenges that NFV brings and the new opportunities to solve security problems using NFV technologies. In the third part, we look at several exciting advancements in NFV-based security solutions that can have a huge impact on the success of 5G and networking in general.
15.2 5G, NFV and Security
5G is both a quantitative and qualitative great leap forward for the wireless industry. While the standardization and planning of early commercial deployments are just getting under way at the time of writing, the goals that the industry set are very ambitious and far-reaching. For example, the NGMN Alliance white paper [1] broadly defined the characteristics of 5G in three aspects:
- Use cases, faster and more common broadband access, IoT, vehicular networks, verticals like healthcare and robotics, ultra-real-time tactile networks, AR/VR;
- Business models, XaaS, value-add services and OTT applications; and
- Value creation, encompassing diverse sets of value propositions to different customers ranging from consumers and enterprises to many vertical markets and partners.
The white paper systematically examined the requirements of 5G from user, system and business perspectives:
- User experiences: high data throughput, low latency;
- System performance: high user density, spectrum efficiency;
- Device requirements: e.g. battery life;
- Enhanced services: e.g. security, location services;
- New business models: XaaS; and
- Network deployment, operation and management: innovation agility, flexibility, operational efficiency.
By this broad definition of 5G, NFV and related technologies (e.g. SDN, telco cloud computing) are an integral part of what it means to be 5G. How we experience a 5G network as a consumer, an operator, or as a business or partner will be defined or made possible by the ideas and technologies of NFV. While some may still stick to a narrower view of defining 5G in terms of radio technology advances, it is clear to us that achieving the diverse use case goals in much broader industries outside of traditional mobile internet access and the success of 5G commercial ecosystems require NFV.
Regardless of how we prescribe the importance of NFV to 5G by definition or by necessity, we will look at the intersections of 5G and NFV in this chapter, and explore the problems and opportunities in the security domain. We will assume that readers are familiar with wireless networks and 5G. We start with a short introduction to NFV, and a section discussing the overlaps and differences of NFV, SDN and other cloud computing technologies. For the remainder of this chapter, we will use the term NFV in a broader sense to mean the wide body of technologies known collectively as “NFV and related technologies”. In other literature, people may also use terms such as Software Defined Infrastructure or Telco Cloud to mean the same concept of a cloud and software-centric infrastructure system.
15.3 A Brief Introduction to NFV
In the fall of 2012, a group of technologists from major telecom operators authored a white paper [2] that popularized the ideas around network function virtualization and served as a call to action. A few months later, in January 2013, the European Telecommunications Standards Institute (ETSI) launched the first of a series of NFV focused meetings in Sophia-Antipolis, France. This was the beginning of the NFV ISG (Industry Specification Group) [3] with a different working model that distinguishes itself from more traditional telecom industry standard bodies by refraining from heavy and rigid standard specifications and by embracing widely successful IT industry technologies and approaches such as commodity hardware, virtualization, software defined networking, cloud computing and open-source.
From the very beginning, the moniker NFV spanned a wide range of meanings. As a start, NFV means implementing network systems by using commodity servers, storage and network switches and realization of the network functions in software. However, the mandate of NFV goes far beyond this narrow scope. It encompasses the use of general-purpose operating systems, hypervisors and containers, cloud management software that enables XaaS, and the transformation of the network’s OSS (operations support systems) and BSS (business support systems).
Let us first look at the simpler, narrow case of NFV. Figure 15.1 is a graphic depiction of this transformation of moving from vertically-integrated physical appliances to virtual appliances implemented on a virtualized infrastructure, based on a pool of commodity physical resources that can be shared and reallocated on demand. We will refer to the appliances shown on the left side of Figure 15.1 as Physical Network Functions (PNF), and the equivalent software implementation as Virtual Network Functions (VNF). From a security perspective, the VNF’s role within a solution architecture stays the same as the corresponding PNF, but its implementation environment has changed. For example, the VNF’s developers can no longer use customized physical design features for security (e.g. by limiting certain device management ports), nor can they do so to the common operating system or hypervisor or container environment in the virtualization layer. These common systems represent both a potentially larger attack surface and a place where fundamentally new security solutions can be delivered. It is critical that the virtualization layer provides equivalent or stronger security features for the VNFs. The virtualization layer is an intermediary that can potentially provide more unified, uniformly enforced, and stronger security than an individual PNF developer can achieve on his/her own. In addition, virtualization means that a VNF for security (e.g. a firewall or a DPI appliance) can be deployed to anywhere in the virtual infrastructure almost instantaneously with little overhead or cost. This also opens up new opportunities for stronger security features that were not feasible before NFV.

Figure 15.1 A simple view of NFV.
Beyond virtualization of infrastructure and VNFs, NFV also integrates the management, orchestration and OSS/BSS to the architecture picture. In many aspects, the management and orchestration layer may be more fundamental than virtualization itself. The ETSI NFV ISG’s work in the NFV reference framework is the most widely known example of the current thinking in this area. In Figure 15.2, three components are introduced in the management and orchestration (MANO) area. The Virtual Infrastructure Manager (VIM) constructs an abstract consumption model for the virtualized infrastructure. The VNF Manager, whether it is a common instance for many VNFs, or a specific instance (e.g. per vendor) for a given subset of VNFs, helps to manage the lifecycle of the corresponding VNFs in a virtual infrastructure. The Orchestrator (at least in ETSI’s naming convention) looks at the service-level abstractions, such as the service catalog, and presents those abstractions to the broader users of the overall system, such as OSS and BSS. While there are clearly alternative ways of constructing such an architecture, and some aspects of ETSI’s formulation are still works in progress, let us use the ETSI framework at a high level to help us familiarize ourselves with the functional components and vocabulary and thus gain some appreciation of NFV’s security challenges and opportunities.
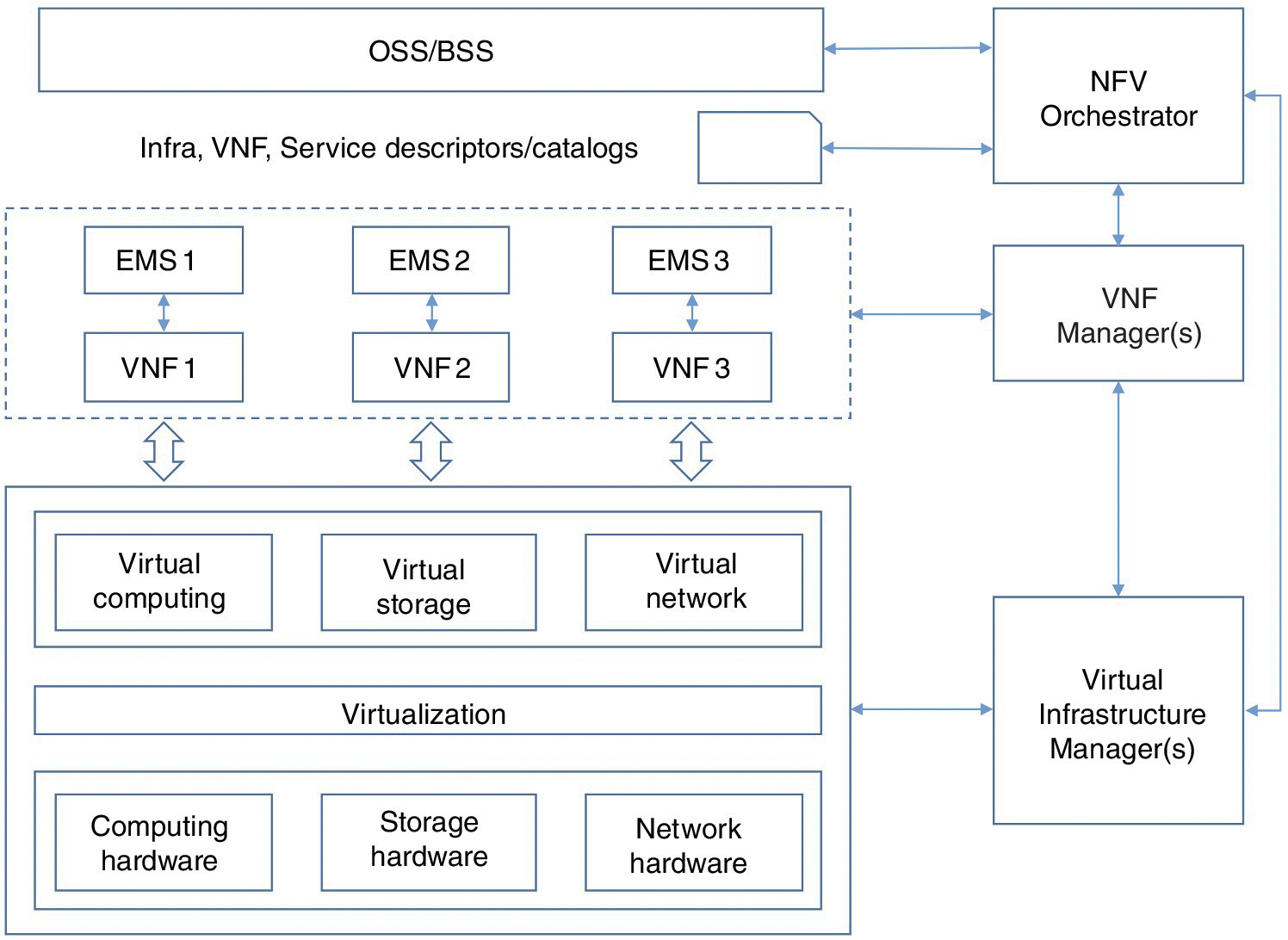
Figure 15.2 ETSI NFV reference framework.
A deep dive into the ETSI NFV Reference Framework is beyond the scope of this chapter; we refer interested readers to [4]. NFV is abstracting and automating many of the operational and business processes by software, and as such it requires operators to redefine trust relationships between many existing components and roles. For example, in a physical infrastructure, creating a new private network may involve a request-and-approval process – and potentially, employees with physical access permissions, and additional testing procedures to finally deliver the requested private network. NFV enables an on-demand service model where the equivalent private network can be delivered immediately without any human intervention or physical rewiring. We therefore must have an automated mechanism for approval, authentication and accounting, and for validating network topology and security policy configurations. Automation allows uniformed policy enforcement, nimbler ways of defending against attacks, and deploying enforcement points to wherever they best fit the need. Like any other digitization of a human process, it also opens up attack surfaces and methods that may not exist in the physical world. These issues are similar to what we found in the IT cloud computing world, as are the solutions. We will therefore not spend much time on these general security questions. In Section 15.6, we will discuss this topic in more detail and also look at some open-source examples of how new generations of software mechanisms found in NFV can help us minimize security threats and enhance delivered services.
As we will stress in this chapter, NFV should also be viewed as a step towards a service provider cloud, with all the benefits of cloud computing. This includes business model innovations, for example, Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS), adopted in the telecom world. These models of service deployment (collectively abbreviated as XaaS) bring up multi-tenancy-related security questions, as well as issues related to trust relationships and roles between different levels of service providers.
All of these NFV-based technology enablers promise a new generation of security products and services that will go far beyond what the industry has been accustomed to. Many researchers in academic and industry, as well as innovative entrepreneurs, have been actively working in this area and are bringing them to market in some cases. In Section 15.7, we will survey some of the work to illustrate the huge potential that NFV and the telco cloud bring to 5G and future networks.
Figure 15.3 summarizes the relationship between 5G security and NFV. The two significantly overlap; NFV brings new challenges related to security as well as new opportunities that can solve many security requirements in 5G and beyond.
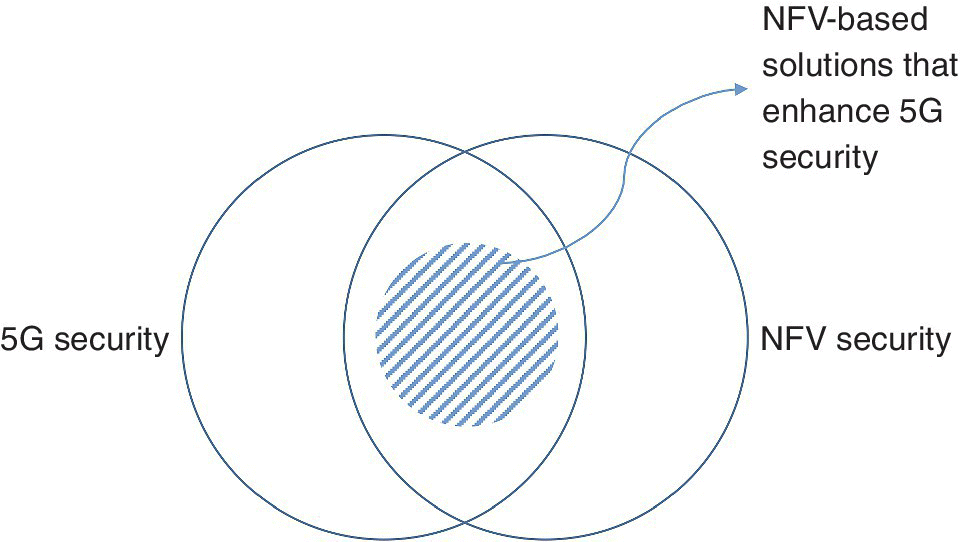
Figure 15.3 5G Security and NFV.
Next, let us devote a short section to better clarify the overlap and differences between three terms that some use interchangeably but that others separate for various (and good) reasons; while many simply use the combination “NFV/SDN” to avoid this question. Our short discussion here is not motivated to sway opinions in any direction, but rather only to clarify and to avoid any confusion for the rest of the chapter.
15.4 NFV, SDN, and a Telco Cloud
Software Defined Networking (SDN) started as a proposal to separate a network switch’s control plane from its data plane, and centralize the control plane in a software entity called a Controller, where new behaviors can be programmed in a relatively easy fashion without modifying the switch itself. It is also commonly associated with the protocol that the proponents proposed to realize such a design: OpenFlow [5]. Open Network Foundation (ONF) [6] was later formed to develop this vision further.
As with many good things in life, the basic concept of SDN has been stretched in all directions since its origin, and it can be difficult to tell when someone is referring to OpenFlow style SDN, or even ONF’s interpretation of SDN. The phrase “software defined” has also been applied to other components in the data center or other complex systems, such as “Software Defined Storage”, or “Software Defined Data Center”, or “Software Defined Infrastructure”. We will not attempt to distinguish between these.
We will use the term SDN to mean a concept different from the OpenFlow protocol, and similarly to apply it to any network device other than just an Ethernet switch. We think the essential benefits of SDN are the central control of decision-making at a high level, not centralizing the entire control plane in OpenFlow. For the purpose of this chapter, the data plane device can be any Network Function (NF) – whether it is PNF or VNF, or a software entity in NFVI virtualization layer, such as a virtual switch or a virtual router. For instance, software-defined radio is a good example of SDN. The common entity is a logically centralized controller designed with modern interfaces and distributed, loosely-coupled architecture.
Under such a definition of SDN, the role of SDN falls into two common cases. In the first case, SDN is deployed to the networking subsystem in a data center. In this case, the SDN Controller can be thought of as a part of the Virtual Infrastructure Manager (VIM) (see Figure 15.2), and the corresponding data plane can be seen as the NFVI’s hardware networking or virtual networking subsystems. In the second case, the SDN controller may reside within a data center while controlling network hardware devices outside of the data center, for instance, the aforementioned Software Defined Radio. Another example is Software Defined WAN (as in physical routers or optical switches of the wide area network). Opinions vary, but this second case is often seen as a separate domain, because the VIM usually does not provide an umbrella abstraction and common interface. This is partially because the VIM for a data center is often developed separately by the IT, not the CT industry, for enterprise uses. Service provider networks usually face fundamentally more complex requirements and constraints than the typical IT users. There is an active area of development on how to design or integrate these cases together. The following diagram in Figure 15.4 illustrates both cases in an end-to-end example of NFV and SDN, and this is the view that we will use throughout this chapter.

Figure 15.4 NFV and SDN end-to-end reference.
We believe that the efforts around SDN and NFV are part of an overall move towards a cloud model of developing, deploying, operating and monetizing operators’ infrastructure, services – and increasingly, content. It is not coincidental that 5G and NFV happen at the same time. Going back to the NGMN Alliance’s white paper on 5G goals, we can see that operators in the era of 5G do much more than provide a faster wireless pipe; 5G is much more than a speed dial-up from 4G. NFV, SDN and cloud technologies are integral to 5G. A telco cloud, in this sense, is the adoption of a cloud model in all aspects of an operator’s business, and NFV and SDN are components of the strategy to move telco infrastructure, operational processes, and business models to that vision.
To summarize, we will primarily use the simple term NFV in this chapter in a broad and forward-looking context.
15.5 Common NFV Drivers
In this section, we briefly look at some common NFV drivers and use cases and how they relate to 5G and 5G security.
15.5.1 Technology Curve
Developing custom products for the telecom industry is a costly business. This cost shows up in the extraordinary long technology cycles. It is common for this process to take a decade or more from R&D to commonly-deployed services for customers. This cost also shows up in the proprietary systems such as gateways, switches, routers, and operating systems, middle-ware, and applications. The hardware is slower to upgrade because of this cost, which deprives the industry of the full benefits of Moore Law in silicon improvements. Its customized operating systems, tool chains, and middle-layer and application software do not fully take advantage of rapid software and methodology advancements, such as distributed system algorithms, distributed or NoSQL data bases, programmable APIs, Big Data, and machine learning, just to name a few. Other segments of the IT industry have taken leaps and bounds with these software technologies, which the telecom industry cannot readily adopt because of the proprietary approach it has taken. There are, of course, unique problems in the telecom industry, such as real-time constraints and high reliability needs. But the question is, can we achieve these based on standard COTS (common off-the-shelf) hardware and modern software technologies? The answer is not only yes, but that we must. NFV can help the telecom industry not only ride the technology curve but lead it.
15.5.2 Opportunity Cost and Competitive Landscape
Proprietary systems are not only costly to develop but also slow to adapt to new customer needs and too inflexible to compete with nimble new competitors. 5G’s success depends on satisfying new customer needs that we may not fully appreciate yet, and tapping into innovative ideas of many different types of partners. IoT, connected and driverless cars, mobile healthcare – these are entirely new markets different from the traditional mobile phone services. VR/AR, immersive video, intelligent agents – these are brand-new user experience and engagement models. To fully seize these new opportunities, agility and flexibility are a competitive advantage we must attain. New competitors, often referred to as OTTs (over the top), do not have the burden of legacy systems and can often outsmart telcos. Operators cannot justify the huge investment in 5G without a strategy to capture a large share of its promised bounty. NFV is part of that strategic toolset.
15.5.3 Horizontal Network Slicing
Networks are very expensive to build, maintain and operate. 5G envisions networks not only for mobile consumers on smart phones, but also for television, healthcare, automobiles, and vast swathes of other segments of the economy, as in IoT. Each of these networks has its own unique requirements. But we cannot build, maintain and operate entirely separate networks for each of them. It will be cost-prohibitive and extremely inefficient. What we need is a shared 5G mobile infrastructure that can be sliced end-to-end, or horizontally, into separate virtual networks that fit best for each market segment. This slicing applies to not only network access and topology but also to functions, such as security, provided by the slice. SDN and NFV together promise rapid provisioning and bringing up these slices on a shared and virtualized infrastructure.
15.5.4 Multi-Tenancy
Having different slices of networks is good, but we also need the virtual infrastructure to be able to support management and operations by different teams, by different functions in an organization, and by different partners and players in the industry in order to deliver sophisticated applications on shared infrastructure. NFV architecture is designed with multi-tenancy in mind as one of the major differences from traditional enterprise and telco systems.
15.5.5 Rapid Service Delivery
As we discussed earlier, the new competitive landscape demands business agility. But that is not all. Many types of requirements in 5G need the ability of rapid service delivery. For example, an “around the globe” service platform may require provisioning and tearing down of resources in a “follow the sun” pattern. Another example is the Continuous Integration/Continuous Deployment (CI/CD) model that requires applications to rapidly update live. Energy conservation is yet another example – being able to shut down part of the infrastructure when the work load is low, and then restart again when demands pick up. That also depends on the ability of rapid provisioning, and security, detecting attacks and rapidly provisioning resources to respond is a strategic arsenal in cyber defense.
15.5.6 XaaS Models
Service providers are no strangers to providing functions as a service, of course. The problem is that the legacy service definitions are rigid, hard to change (regulated by governments), and narrowly targeted. Cloud computing providers such as Amazon Web Services (AWS) pioneered much more flexible service models with a programmable API. Whether the consumable functions are at the infrastructure level, Infrastructure-as-a-Service (IaaS), platform level (PaaS) or the software level (SaaS), or anything in between or in combinations, the flexibility and on-demand nature of these services open up a vibrant ecosystem of innovative partners who come up with a vast variety of ways to consume the shared infrastructure and create value. This type of ecosystem is a must for 5G network builders to fully leverage and monetize their expensive investment. Operators can also leverage each other’s investments and provide better services to their customers. Monetizing fully the operators’ (and vendors’, and partners’) collective investment is one of the most strategically important factors in the success of 5G.
15.5.7 One Cloud
We have talked about the telco cloud as powered by NFV and related technologies so far. But is there any fundamental reason that the telco cloud needs to be distinct from any IT cloud? If we look at the long horizon (or even if one looks back in history), the answer is no. Communication, as distinctive as it is, is closely intertwined with computing; future applications, as envisioned in 5G and in IT industries, predominantly require both computing and communication. Therefore, it is a fair question to ask: Is there a One Cloud into which we will eventually converge, regardless of IT or CT? It means that we are all competing towards the same technology foundation that will one day meet many, if not all, of our IT and CT needs. That day is already here in many market segments, and we may see the contour of what it looks like and make decisions to better prepare for the future. NFV is a major pillar in the foundation that will enable the networking industry to turn its expertise into advantages in the converged one cloud.
15.6 NFV Security: Challenges and Opportunities
Because of the dynamic and loosely-coupled nature of NFV, security – from solutions to processes – must be embedded into it from day one as a basic fabric. This security infrastructure, in identity services and role-based access control (RBAC) for example, has been developed and matured in the cloud computing space and is being adopted in NFV. In this section, we will focus on new challenges and new opportunities brought forth by NFV.
15.6.1 VNF Security Lifecycle and Trust
When a physical network device is introduced into an operational network, there is established trust of this device due to the fact that this device was installed and configured by a trusted employee, delivered to a secured location by a trusted courier, and developed and manufactured by a trusted vendor with a contract or a certification, and so on. For VNFs, this chain of trust relationships needs to be created and maintained in a NFV environment throughout its lifecycle.
A VNF’s lifecycle is illustrated in Figure 15.5.
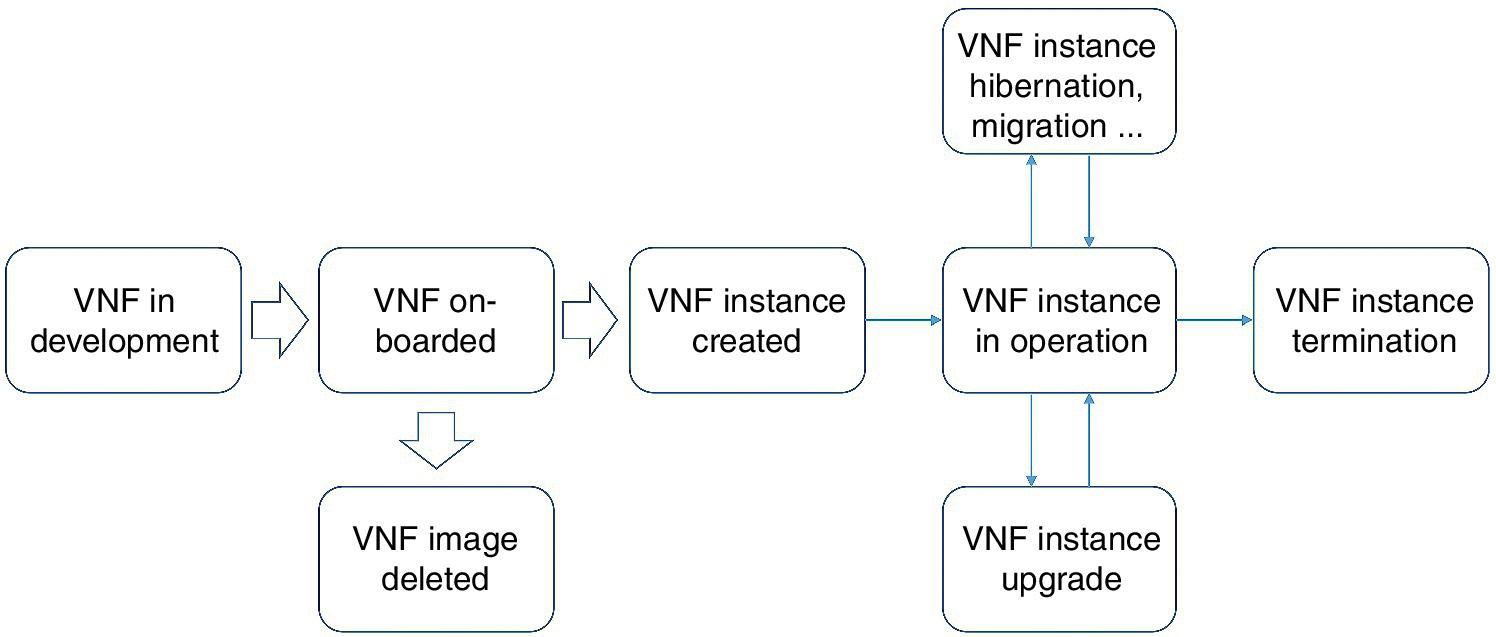
Figure 15.5 A VNFs lifecycle.
A VNF has several important trust relationships, as shown in Figure 15.6.
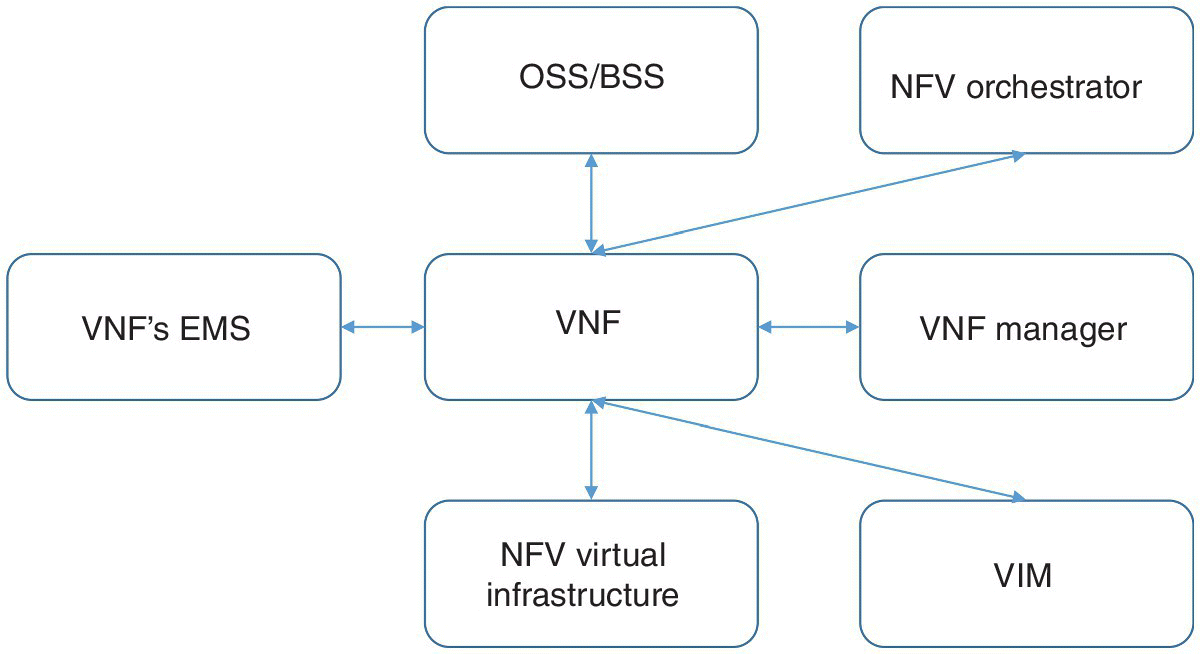
Figure 15.6 A VNF's trust relationship.
In a private NFV environment, as in a private cloud – where NFV infrastructure, MANO and OSS/BSS are in the hands of one administrator and all VNFs are managed by one operator – trust relationships can be simplified. In this section, we focus on this simpler case. We will look at multi-tenancy and XaaS in a later section.
In the development phase, a VNF vendor must design the VNF for operation in an NFV environment. For physical devices, a lot of trust is often assumed. Even when a simple password mechanism is implemented, it is common that the password has a publically-known or easy-to-guess default value. The default password, or private cryptographic key, is often stored in the image itself. All these practices must be thoroughly eliminated in order for the VNF to operate in a much more open and less-trusty environment. Comprehensive public key authentication with an identity management infrastructure must be designed into software products, and backdoors eliminated. Software integrity must be strictly maintained at every step of the lifecycle with cryptographic signing using a traceable certificate from a Certificate Authority (CA) established or recognized by the operator.
In the on-boarding phase, the operator must be able to assure the VNF’s authenticity and integrity by validating the vendor signature with an authorized CA. The operator will still need to perform the normal acceptance testing procedure. However, with VNFs, this testing procedure can be fully or largely automate. As security-related risks or bugs are identified, new releases can be quickly on-boarded and tested again through full automation in a Continuous Integration/Continuous Deployment (CI/CD) chain. Security verification is an important step in that tool chain. It also ensures that VNFs from different vendors follow the same rigorous process to achieve same level of security level and same security architecture standard. As early example of an automation security testing component in CI/CD is Amazon Web Service’s Inspector [7].
Once on-boarded, a VNF is ready for deployment. Deployment involves creation of an instance of the VNF, for example, one or more virtual machines or containers. It is given an identity and a private management IP address for communication, first with its VNF Manager (VNFM). The identity is usually provided as a service by the Virtual Infrastructure Manager (VIM). With the identity and management IP address, and the assistance of the Identity and Authentication/Authorization service, the VNF instance can now establish a trust relationship with VNFM, VIM and other MANO entities. While a VNF could be simple and contained within a single instance of VM or container, more often it is much more complex, with many VMs or containers collaborating to accomplish its functionalities. Each of these could have its own unique trusted identity, and the identity manager with the VIM facilitates trust establishment among them. It is also possible that a complex VNF or a legacy implementation may conduct the VNF internal trust management on its own. For example, a container manager or a vendor-specific PaaS layer may substitute for or complement the identity function.
The VNF Manager (VNFM) can be a common entity for many or all VNFs in a NFV environment. We can also see VNFM proprietary to a vendor and its VNFs. In either case, the VNF needs to locate the VNFM and then establish a trusted communication channel with the VNFM. Finding VNFM can be facilitated by the VIM’s or MANO’s instance creation phases via metadata to the VM (e.g. a model configuration), or by a common service discovery protocol. In a model-based approach, this VNFM identity can be one of the meta data in the descriptor that defines this VNF. There are efforts underway to standardize how a VNF should be formatted and described or modeled. Among other benefits, a model-based approach can ensure that security policies are uniformly expressed and enforced. Either way, the VNF establishes a trusted and secured management channel with the VNFM, and now it can be managed.
Let us first look at the simple case where the VNF is the only entity required for the example service. In this case, once the VNF can be securely managed and configured, it is now operational. There are a few things the VNF typically needs from the VIM to be fully operational, and they do have security implications. Common examples include publically addressable floating IP address, DNS service, and NTP time service. These services are usually provided by the VIM and NFVI, and therefore it is the responsibility of the operator to secure these services. DDoS attacks against DNS service have been widely reported in recent years, for example in [8]. The operator can also outsource some of these services, for example DNS, to professional DNS service providers. We will further discuss these XaaS scenarios in a later section.
The next step in a VNF’s lifecycle is updating its software image. Software upgrade is a major undertaking in physical network devices, including extensive testing and preparation. In the NFV methodology, the Continuous Integration and Continuous Deployment (CI/CD) [9] paradigm is a large part of changing the whole feature delivery pipeline to enable much more agile and flexible operation and business models. For the security domain, this is a great opportunity to create a threat intelligence pipeline, through which new threats are detected and analyzed, then new security patches or defenses are developed, tested and delivered through CI/CD routinely. The agility of this pipeline must beat the new threats in this game to maintain security in the future. NFV-based CI/CD is an enabler for this fundamental capability that future 5G systems must have.
The last stage of a VNF’s lifecycle is termination. Some of the tasks in a termination phase are the removal of cryptographic material from the image, orderly archival and removal of kept data records, etc.
Further discussions regarding the VNF’s lifecycle and security in each stage can be found in ETSI NFV ISG’s TST working group publications such as [10].
To summarize, in this simpler, private NFV environment, a VNF’s lifecycle is standardized by a model VNF Descriptor (VNFD) and automated through VIM, VNFM and service layer. This standardization and automation, coupled with rapid updating capability by CI/CD, will make security in NFV stronger than the manual system of today. We often hear that the most common security vulnerabilities are due to human error or human weakness exploitation. NFV-based automation will change the dynamics and allow operators to put their resources directly into defeating threats.
15.6.2 VNF Security in Operation
Managing a VNF’s lifecycle is only one aspect of VNF security. A VNF spends most of its time in the operational state. Several important factors determine a VNF’s security property.
First, let us remove one of the simplifications we made earlier: the assumption that a VNF is a single entity, for example, a virtual machine. More commonly, a VNF consists of a group of virtual machines with the same (a cluster) or different software images (VNF Components or VNFCs). In either case, each virtual machine has a unique identity and they are distributed to various computing units, not necessarily on the same physical servers.
These virtual machines will need a network over which they can: (i) coordinate their work by passing control messages among themselves, or (ii) pass around network packets (traffic) between them for distributed or pipeline processing. This is similar to a backplane in physical systems where control modules and line modules are interconnected, or there is an Ethernet-based network fabric in a data center. Inside a VNF, this interconnection is provided by a virtual network created dynamically. This virtual private network is provided on demand by virtual overlay such as VXLAN [11], a software abstraction supported by the hypervisor or by a virtual switch (vSwitch in layer 2) or a virtual router (vRouter in layer 3). Virtual networking or network slicing is a fundamental building block of the NFV infrastructure, and must support two basic requirements:
- Topology isolation; and
- Security rules.
Topology isolation means the virtual network is private, with its accessibility to the outside world fully controlled. Isolation alone is usually insufficient; security rules provide firewall-like security to the virtual machines that reside inside the virtual network. These software abstractions can be several magnitudes more scalable than physical firewalls such that security rules can be applied with very fine granularity. This is sometimes referred to as micro-segmentation [12].
Virtual networks and security rules only protect a VNF from other virtual machines that are sharing the same infrastructure. VNFs must also connect with each other to collaboratively construct a network service. This is referred to as Service Function Chaining or SFC [13]. SFC can be realized by the same mechanism using virtual networks and security rules. It is not very efficient, however, because data packets must be in and out of processors repeatedly stressing the data path bottlenecks, and the common packet parsing and classification tasks have to be repeated in each stop of the pipeline where that information of a packet is needed. An active task in IETF [13] is defining a new encapsulation scheme for SFC to address some of these issues. SFC does not provide security protection between different VNFs, however. If security is needed, a virtual firewall VNF is inserted in the chain to work the same way as a physical firewall or security gateway.
Some of the VNFs that comprise the service must eventually connect with the outside world via physical network devices to backbone networks, access networks or devices that are geographically remote. The VNFs are gateways that must contain access to physical ports directly or indirectly. These edge VNFs must be protected from threats just like any other PNF in this case. They do have one advantage compared to the physical ones: they can scale up and down on demand, and that gives them better ability to deal with DDoS attacks.
Naturally, networking is the most important aspect of security for VNFs, but not the only one. Virtualization of computing and storage also exposes new attack surfaces to VNFs and adds new protection capabilities at the same time. Because VNFs share a server’s processors, memory and disk with other virtual machines, the isolation capability provided by the hypervisor is usually not as strong as physical isolation. These types of issues have been addressed, however, and more capabilities are being added to a processor’s architecture to strengthen protections. Other issues include the noisy neighbor problem, where a less-restrained virtual machine sharing the same physical processor resources could intentionally or inadvertently abuse them and cause performance degradation, or more severe issues. To properly address these types of issues, new generations of processors will add stronger isolation mechanisms, for example, Intel Xeon’s cache reservation [14]. VIM’s resource management software will develop schemes to allocate resources and place virtual machines more intelligently.
The virtualization layer, for example the hypervisor, provides a strong level of protection for the VNFs running on the top. Modern hypervisors all have built-in security features in addition to the protection provided by the operating systems. VNFs can also migrate, scaling up and down and in and out, and new security rules or security VNFs can be added on demand. All these functions substantially enhance the overall ability of the network services to withstand threats both old and new.
15.6.3 Multi-Tenancy and XaaS
So far we have assumed that the entire NFV system is private, that is administered by a single operator. NFV facilitates XaaS models in many different layers that can enable innovative business and operational approaches. For a given service, the provider must support multi-tenancy in the infrastructure, so that the same infrastructure can be provided to more than one consumer in a shared fashion. For the consumers, this is functionality provided to them as a service (XaaS). They can build higher-layer applications on top of the XaaS interface.
Let us take an example of IaaS (infrastructure as a service) where the provider operator offers its data center infrastructure to partners. The infrastructure is NFVI and VIM in NFV terminology and it supports multi-tenancy. The provider who may own the infrastructure and the operation of it offers the use of this infrastructure in a cloud fashion. NFVI consists of the virtualized assets being shared, and VIM provides the interface or API so that the partners can consume this service. Multi-tenancy means the provider allows the partner/consumer to slice a virtual pool of computing resources under the partner’s administrative control; the partner can virtually construct its own network services, composed of VNFs, within its slice of resources. Consumers of Amazon Web Services will be familiar with this consumption model; NFV extends this to telco services.
Multi-tenancy requires not only an efficient way of slicing the resources, but also security and privacy protections offered by the provider to its partners/consumers. Virtual private networks and their associated security rules, as described in the last section, are the basic foundation. But additional capabilities are required, including virtualization of supporting functions such as DNS, DHCP, identity, monitoring and reporting. Moreover, additional services are required for virtual gateway routing so that the virtual private network can securely connect with the Internet. We will often see that software originally developed for private use, even private cloud use, cannot adequately support these multi-tenancy requirements.
The provider may optionally support more features for its partners or consumers. These can be common tools that are needed to develop or deploy VNFs, such as performance monitoring and reporting, logging, data analytics, enhanced security services, databases, high availability, scaling and billing. These are often referred to as either Platform as a Service (PaaS) or Software as a Services (SaaS), depending on how we classify them into middle-ware or application categories. All these services will also need to support multi-tenancy.
With 5G networks and applications, this concept of resource-sharing and multi-tenancy are being pushed to new levels to include network-sharing. For instance, a new class of end-user devices (say, IoT or healthcare or automobiles) can be supported with a virtual slice of wireless access. Associated with each class is a slice of access network infrastructure (virtual networks), and a slice of virtual computing infrastructure and service applications (NFV data centers and VNFs). Each such class of services can have its own capacity, its own security policy, its own SLA, billing and support models, and so on.
15.6.4 OPNFV and Openstack: Open Source Projects for NFV
Why open source? Open source may seem like an off-topic subject for 5G, security or NFV, but it is not – for two very important reasons.
First, as we alluded to earlier, open source has been increasingly seen as an indispensable component in the development of NFV. The traditional standardization processes made tremendous accomplishments in getting mobile networks to where we are today. That being said, we see shortcomings too, such as long and slow processes from ideas to products and services, and difficulty to adopt those kinds of processes to the software domain. Open-source projects such as Linux and Openstack have emerged as de facto standards within certain domains and can be just as effective in achieving many of the goals, like interoperability and rich ecosystems, which standards try to achieve. In the security realm, the prominence of open-source components like OpenSSL is a good example. Premium standard organizations such as ETSI, 3GPP and IETF recognize this trend and see the important role open-source is likely to play for NFV, IoT, and many other areas of 5G. OPNFV (Open Platform for NFV) [15] is one such project launched in September 2014 to accelerate the adoption of NFV by integrating an open-source reference platform for NFV.
Second, as more and more people come to realize, open-source cloud computing software based on commodity off-the-shelf hardware have made incredible progress in delivering unparalleled economic computing power in the last decade. One may venture to say that this is the main reason why we started the NFV initiative in the first place. Taking advantage of the open-source technology base to accelerate NFV seems a natural and obvious thing to do. Why re-invent the wheel when we can stand on the success that open-source already created for IT, web and cloud computing industries? That is why, in about two years after ETSI’s launch of the NFV program, the Open Platform for NFV (OPNFV) project was created – with leading operators, network vendors, IT vendors, and open-source software developers joining together for the first time in industry history. It became a Linux Foundation project in September 2014 with a mission to “create a reference NFV platform to accelerate the transformation of enterprise and service provider networks”.
If we take a high-level framework like that of Figure 15.2, how do we then use open-source components to build a platform together to satisfy operators’ needs? That is essentially what OPNFV set out to do (Figure 15.7). The OPNFV reference platform is the one example of NFV design that we can closely examine – and, for those of us who are so inclined, run it in a lab to experience it. The following diagram is a rendition of the OPNFV reference platform by the author. Many will readily admit that there is not one single reference platform but several different ways we can compose the platform together. Not all technical questions have been settled yet, as is often the case in the open-source world, but we can still benefit from studying their most recent release still in development at the time of writing, code-named Danube.
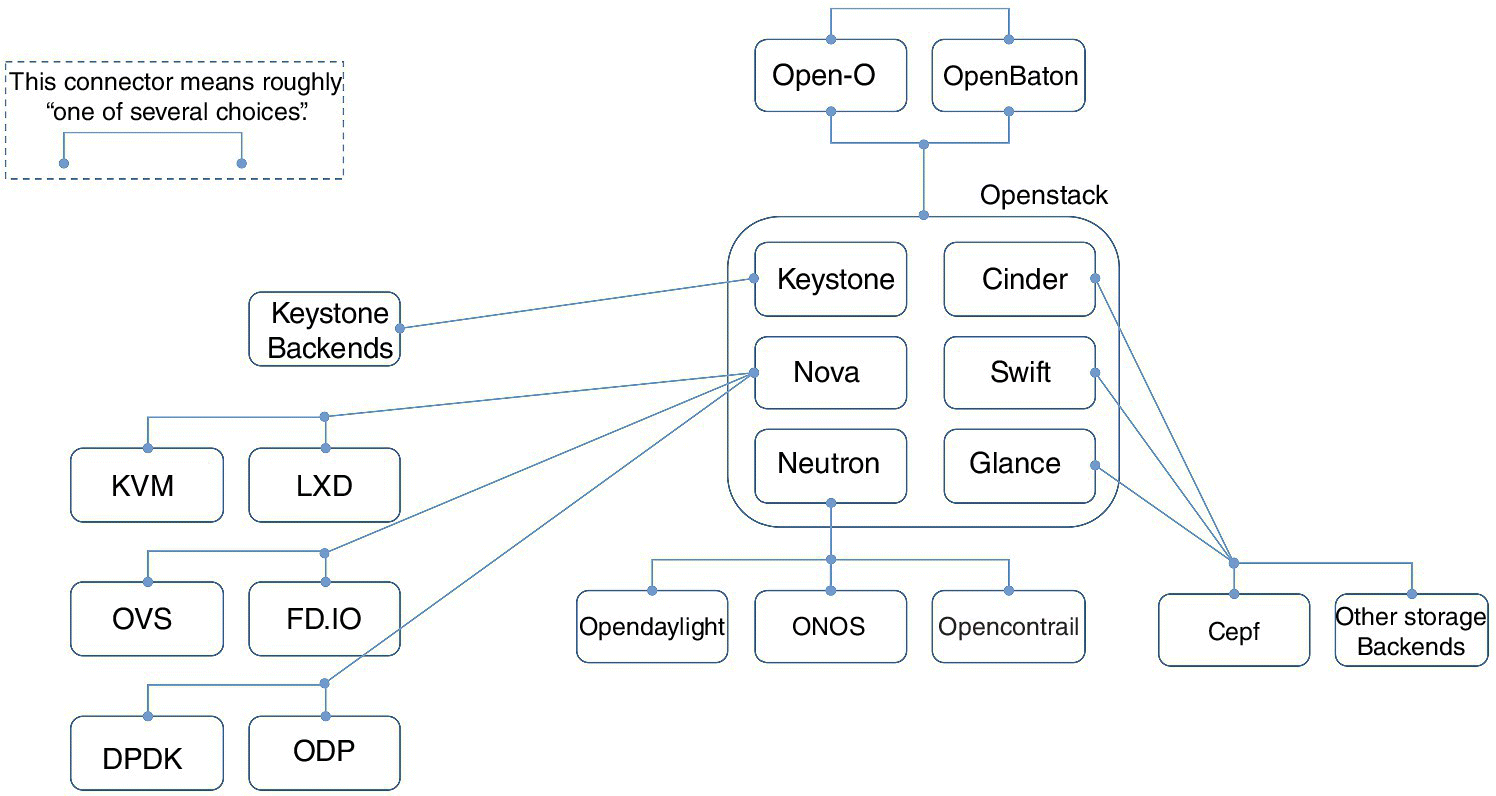
Figure 15.7 OPNFV reference platform for NFV.
As shown in Figure 15.7, the centerpiece of the OPNFV reference platform is Openstack [16] as the VIM (virtual infrastructure manager). Openstack provides abstracted services as APIs.
Nova is Openstack’s virtual computing API. For the NFV data plane, we first need a hypervisor, such as KVM [17] or LXD [18]. There are other choices for either hypervisor or container. Well-recognized examples include ESX® from VMWare and Docker®. For simplicity, we only show the components that have been actively integrated within the OPNFV at the time of writing (during the Danube release cycle). The same applies to all the discussions in this section.
The hypervisor is critical in providing security to VNFs in this environment. Hardening KVM is mandatory to prevent common vulnerabilities such as guest execution escape, guest-triggered DOS, and information leaks to guest. Modern hypervisors are safe for most common-use cases.
In addition to the hypervisor/container, NFV requires special functions to support the network data plane. Open vSwitch (OVS) [19] is an open-source implementation of software-based switching capabilities based on SDN and is the most commonly deployed virtual switching implementation, according to Openstack user surveys. FD.io [20] is an alternative way of supporting a high-performance network data plane.
The networking data plane puts an extreme demand on packet movement (I/O) and processing to the underlying servers. The kernel TCP/IP stacks (and drivers) known to many software developers are often inadequate due to performance and other limitations. DPDK [21] is an open-source SDK that can improve, dramatically in some use cases, the data-packet movement and processing performance by taking advantage of special features in the processors. DPDK is developed by Intel® for Xeon processors. Similarly, ODP [22] (Open Data Plane) is an open-source project aiming to provide a cross-platform data plane SDK for SoCs and servers. The performance improvement levels of DPDK and ODP are particularly pronounced when we look at smaller packet sizes or packet-per-second measurements [23]. These smaller packets can be common in telecommunications networks for voice, media and others, as compared to IT and database applications in enterprises. In addition, packet-process latency or latency variation (jitter) can also be important considerations. More importantly, we also start to see that the narrow focus on SDK for performance may not be sufficient. A system’s approach, where we develop a general framework that takes into account cluster management, reliability, programmability, and other system level issues, may hold more promise [24].
The data plane is the fundamental component of the fabric, for security or any networking functionality. One prominent feature of NFV is virtual network on demand. This network level isolation, in topology by layer 2 or layer 3 means, in virtual addressing, NAT, and security rules applied to the virtual network domains lay the bedrock for NFV security.
The counterpart of network data plane is its control plane. In Openstack, Neutron is the default virtual networking API, and we use an SDN controller to achieve many challenging goals such as scaling, flexibility and reliability. OPNFV integrated several well-developed options for the SDN controller. OpenDaylight (ODL) [25] is a sister Linux Foundation project focused on developing an open-source SDN controller. ODL is backed by many networking industry major corporations. The Open Network Operating Systems (ONOS) [26] is another open-source project spearheaded by ON.lab and other members, which has also become a Linux Foundation project. ONOS closely collaborates with the AT&T CORD (Central Office Re-architected as Data center) [27] project. As we have discussed, the SDN controller is the back end to deliver a certain networking area function abstraction. In Openstack, Neutron is the abstraction that comes natively by default. Let us take Open vSwitch (OVS) as an example of the data plane, and ODL as an example of the controller. Users make a Neutron API call to create an on-demand virtual network. This request passes to and is implemented by ODL, which in turn interacts with OVS via OpenFlow. There is much more complexity in the steps taken to realize the simple virtual network abstraction, of course, but Neutron abstraction itself is quite simple.
For NFV, Neutron’s simple abstraction is often not enough, because it has to have the ability to represent many different networking technologies and use cases. For instances, virtualization of broadband access networks (vCPE: virtual Customer Premises Equipment) and VPN based on BGP/MPLS [28] for core networks will not fit into the simple Neutron model neatly. If we consider 5G use cases such as IoT, automobile, healthcare and other industries outside of traditional telco, this situation is even more complex. We have several ways to solve this problem. We could extend Neutron, but this option can make Neutron very complex and be a burden on enterprise applications that may not need or want that complexity. We could develop a separate service that specifically addresses telco networking needs (e.g. the Openstack Gluon project) [29]. Or, we could implement those networking abstractions outside of Openstack altogether by deploying SDN controller as a separate instance of VIM (Figure 15.4).
There are several abstractions in Openstack to capture different storage needs. Glance is an image service for all application software images; Swift is an API for object store; and Cinder is an API for block storage. OPNFV currently integrates a Ceph open-source project [30] to implement virtual storage from various storage hardware, for example, economical local hard drives in the servers. Other storage back ends exist and can be more common in deployments.
In Openstack, Keystone implements Openstack’s identity API, supporting API client authentication, service discovery, and distributed multi-tenant authorization services for the entire Openstack deployment. A client asks Keystone for an authentication token by providing its valid credentials. This token is then used in the REST API to access an Openstack service, such as the X-Auth-Token request header. Keystone also supports integration with existing LDAP directories for authentication and authorization.
Finally, in the Danube release cycle, OPNFV is integrating two MANO (Management and Orchestration) open-source projects. OPEN-O [31] is a Linux Foundation-backed project “that enables telecommunications and cable operators to effectively deliver end-to-end services across Network Functions Virtualization (NFV) Infrastructure.” The Open Baton project [32] is supported by TU Berlin, Fraunhofer FOKUS, and the 5G-Berlin program in Germany, and it “is a ETSI NFV compliant MANO framework. It enables virtual Network Services deployments on top of heterogeneous NFV Infrastructures.” While these MANO projects are still new at the time of writing, they complete the OPNFV stack so that an end-to-end NFV deployment reference platform is now possible in open-source through OPNFV.1
Figure 15.82 illustrates an end-to-end use case for an operator to deploy residential vCPE service with OPNFV integrated with OPEN-O VNF Manager and Orchestrator. This end-to-end network service slicing capability allows a common 5G network infrastructure to efficiently support multiple partners, multiple market segments, and use cases.
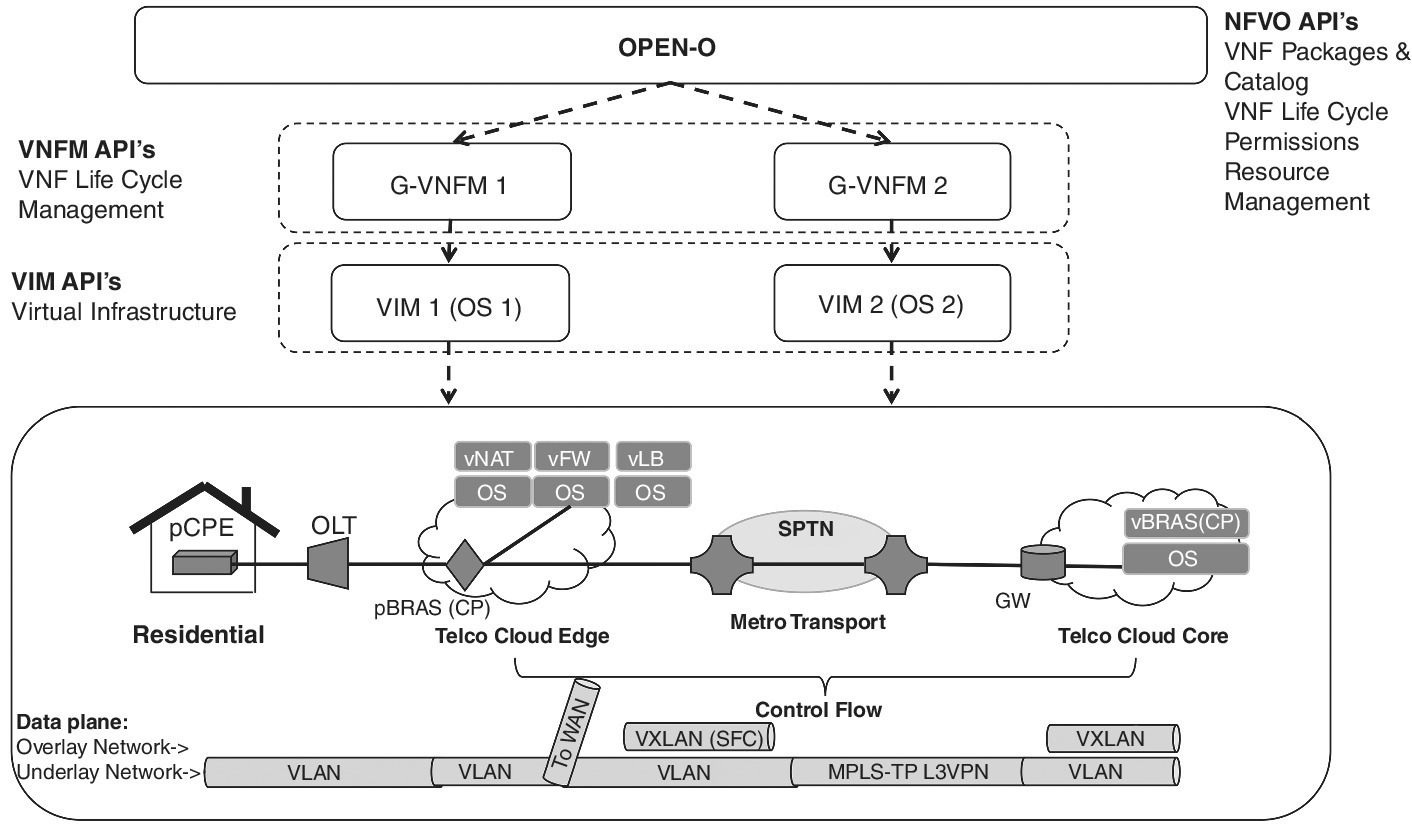
Figure 15.8 vCPE example use case by OPEN-O integrated with OPNFV.
15.7 NFV-based Security Services
In the last part of this chapter, we will highlight several exciting advances in recent years regarding NFV-based security service. We call a new security service NFV-based if the technology has been made fundamentally more potent and impactful because of the development of NFV. These technologies may not be entirely new, but their full potential was not realized until NFV started to transform telecom industry infrastructure, services, and business models.
15.7.1 NFV-based Network Security
Network security services are typically provided by a gateway device. They are ubiquitous today in our computing and networking infrastructures in the forms of firewalls, DPI (deep packet inspection), IDS/IPS (intrusion detection systems or intrusion prevention systems), and many more. They can be stand-alone appliances or can be embedded into other network devices. These gateways are inline devices, meaning that they must be inserted into the network data path and handle the full load of traffic in order to be most effective. They are therefore prime candidates for virtualization. We look at different ways in an NFV system in which this can be achieved, and their benefits.
15.7.1.1 Virtual Security Appliances
Virtual security appliances are easy to adopt with NFV. The virtual appliance is a VNF that has equivalent security function as its PNF counterpart. The virtual appliance also has several fundamental advantages:
- The VNF can be created on-demand within seconds, anywhere in the NFV infrastructure resource pool;
- The VNF can easily scale up or down on demand;
- The VNF can be virtually dropped in to an existing network function chain;
- If the VNF is designed in a modern way, or cloud native, then it can also easily scale out horizontally in many cases;
- The VNF can be managed remotely and automatically by applying uniform security policies.
How can these properties of the VNF improve security? We can look at one recent security incident: the DDoS attack against DNS service provider Dyn.com. By Dyn’s statement [33], the attack was the work of “tens of millions” IoT devices infected by the Mirai botnet. With the deployment of 5G and future IoT use explosion, we should expect similar incidents, with several orders of higher-scale magnitude. How can a NFV system better defend against such an attack?
First, NFV’s dynamic scaling feature will be able to absorb the first wave of attack much more effectively. In a physical appliance deployment, the system’s capability is static. Let us say the Dyn engineers foresaw an attack that may spike the load of the system by up to 10× of the normal load. That is the system capacity that they would have installed, and the malicious party only needs to generate 11× the load to cause a problem. In a NFV system, the entire data center’s resources are a shared pool among many work loads. When the DNS system is under attack, the DNS system can scale up dynamically (including by shifting resource allocation from less critical system services) and give the system much more flexibility and time to absorb the attack wave, detect DDoS activities, analyze behaviors and even figure out remedies.
Second, even if the attacker can muster a large enough load to drain the extra capacity of the entire data center, Dyn’s NAC operators would have much better MANO tools to deploy a solution quickly. The Dyn’s official statement said that it took them a heroic “two hours” to recover from the first wave of the attack. A better MANO may reduce the deployment of the remedy in minutes or even seconds, and therefore practically render the attack a non-event.
Sometimes new attacks may be deployed that no one has seen before, and existing system software may not have a ready configuration we can use to fix the problem. NFV enables developers to rapidly prototype a new network gateway using programmable SDN, and to deploy it inline in the front end, via SFC, without interrupting the existing DNS system. This third method can be an important tool to deal with ever-more sophisticated zero-day attacks that we cannot foresee.
15.7.1.2 Distributed Network Security Services
Network security can also be distributed, either implemented within the hypervisor or as a hardened distributed service of the NFVI. Since the enforcement of security rules is dispersed to all servers, their load is distributed and scaled naturally, because a percentage of each server’s computing resources are allocated to security. The network security “device” only exists virtually in a management system’s abstraction. This allows users to use security gateways pervasively, since they basically have no material cost.
This last point is very important. Once the cost of adding a network security device is eliminated, we can abstract many security solutions to general policies, and the management system can automatically provision the necessary rules without human intervention – and the associated inevitable human errors.
This fine-grained abstraction of security also allows automated gathering logs for compliance audit and monitoring. It paves the way for further uniformed policy enforcement and audit.
15.7.1.3 Network Security as a Service
Many network security functions can be abstracted and delivered as a service. One of the common network security functions is VPN access. A corporation may deploy VPN gateways in its HQ or offices around the country or the world. Its employees from home or remote locations can safely access information and computing resources located in the HQ and data centers. This pattern is very common and ubiquitous. The same pattern exists for many systems, for example healthcare, or geographically dispersed IoT sensors.
This usage pattern can be abstracted and delivered as a service by one global operator to all its customers around the world, with much lower cost and higher ease of use.
In the healthcare setting, for example, hospitals and other care providers do not wish to spend the time and money to deal with IT systems, communication systems, and security and patient privacy law compliance. An operator can supply much better solutions, including certified compliance to regulations through an API-based service. Not only security and related regulations, but mobile healthcare services can be integrated seamlessly by software on top of a shared operator infrastructure based on NFV.
This XaaS pattern can be applied to many industries and market segments that are expected to become major use cases of 5G.
15.7.2 Policy-based Security Services
The second area we will look into is that of policy-based security services. Policy refers to a higher-level notion of what we want from our systems, as compared to a lower-level procedure of how. Policy-based management shows up in all areas of IT and non-IT human endeavors, from IT security, human resources and financials, to government and law.
Policy-based systems make declarations of what our goals are, without specifying how to achieve those goals. Policy is therefore also called declarative, and it must then rely on a system that can translate the declared goals and put them into practice or enforcements. This sounds a lot like how some governments are supposed to function. We can intuitively sense that this is easier said than done.
One problem with declarations is that they are often ambiguous. We therefore must have a clear language that can express all kinds of policies we may wish to impose. Another problem is that a group of declarations often contradict each other; we will need a way to resolve internal conflicts and still maintain integrity and consistency. But even with a clear and consistent policy specification, the question remains: how do you put the policy into force? Even with a correct procedure implemented in a system that can enforce the said policy, we still do not know if it is truly being enforced. You may say this is two sides of the same coin. If you are mathematically inclined or trained in computer science theories, you know this is indeed an unsolvable problem.
Because of these difficulties, policy-based management of security, networks, and other areas have been studied but not widely implemented on a large scale. With NFV, we see a new possibility that we may come to achieve real deployment, and dramatically simplify and enhance security at the same time. This optimism comes from the properties of NFV systems that we have been discussing throughout this chapter. To illustrate, let us look at some of most recent open-source solutions in this space.
15.7.2.1 Group-based Policy
Network engineers have been configuring access control lists (ACL) or firewall rules for years. These rules may be clear but they are extremely brittle and fragile, hard to maintain because they are specific to the details of each system, and difficult to prove correct. They are also primitive and not very effective.
Group-Based Policy (GBP) is a high-level abstraction to solve some of these challenges. A group is an abstraction of a collection of network endpoints and description of their properties. In NFV, this can be a group of VNFs. A VNF can instantly inherit security and other policies by becoming a member of a group. In GBP, the actual rules are separated out of the devices with an abstract rule set describing the desired behavior. These abstract rules can therefore be “reused” by attaching to many groups. The reusable nature of the rule set allows operators to develop mature policies that comply with known regulations, such as PCI and those developed to meet IoT, healthcare or autonomous cars in the future. These rules include not only common ones that we know in firewalls or ACLs, but also NFV-powered service chaining rules and rerouting rules. For example, you can write rules to reroute “dirty” traffic through a firewall virus-scan or IDS. This redirection capability allows GBP to describe a NFV Forwarding Graph. GBP also allows rules to come from different sources, for example, VNF’s developers specifying the rules for the application, and data center operators specifying rules for operations and administration.
The example in Figure 15.93 gives a good illustration of the concept of groups and NFV service chaining to enforce dynamic security policies in an NFV system.

Figure 15.9 Example of GBP with NFV service chaining.
GBP is a policy framework specifically focused on networking and network-based security services. It is otherwise general and has been utilized in Openstack on top of Neutron [34], and in OpenDaylight [35], in addition to commercial products from several networking vendors.
Next, let us look at an example of a policy framework that is more general-purpose by design, beyond just networking.
15.7.2.2 Openstack Congress
The analogy of policy management in a data center to that of a government was not lost on the team developing a policy system for Openstack. They aptly named their system Congress.
Congress is a general-purpose policy framework that is implemented within Openstack as a service, although it could live outside of Openstack. The main components of Congress are:
- A policy language: Datalog [36];
- Data source: all main services in Openstack such as Nova, Neutron, Cinder, Glance, Swift, Keystone, other data collection services like Ceilometer/aodh, and non-Openstack systems, can all be its data sources; and
- An implementation of policy services: for monitoring, enforcement and audit of the policy.
Although the policy language, Datalog, is syntax-wise a subset of Prolog and is evaluated as first-order logic (therefore always consistent), it is closer to a query language like SQL. Congress can support many modes of policy services. For example, in reactive mode, Congress reports a policy violation after the fact, and can also trigger a corrective action. In proactive mode, Congress can check if a violation would occur if an action were taken and therefore prevent the violation from occurring in the first place. A consumer of Congress’s service could consult Congress for pre-clearance. Congress can also be used for monitoring and reporting, and provide audit trails for compliance.
Because Datalog is a general language used for deductive reasoning, Congress can be used to express any policy, for example, environmental policy, power usage – or for our purposes, security and data center operations. Here is a simple example taken from OPNFV Copper project [37] that should be self-explanatory.
- Policy
“Certain software images are not allowed to run in the DMZ.”
- Enforcement
“If such an image is found running in the DMZ, pause the VM to stop such violation.”
- Congress policy specification in Datalog
dmz_server(x) :-nova:servers(id = x,status = 'ACTIVE'),neutronv2:ports(id, device_id, status = 'ACTIVE'),neutronv2:security_group_port_bindings(id, sg),neutronv2:security_groups(sg,name = 'dmz')dmz_placement_error(id) :-nova:servers(id,name,hostId,status,tenant_id,user_id,image,flavor,az,hh),not glancev2:tags(image,'dmz'),dmz_server(id)execute[nova:servers.pause(id)] :-dmz_placement_error(id),nova:servers(id,status = 'ACTIVE')
15.7.3 Machine Learning for NFV-based Security Services
Policy-based approaches tend to favor deductive reasoning by building models of reality and analyzing the models based on logical rules. As we know, this approach has its limits and does not work well in complex, dynamic and large systems by itself. An alternative way is to find truth from observation data and inductive reasoning.
Machine learning (ML) and Big Data have made rapid advancements and have had a huge impact on many problems that IT and CT industries face. It is not new that ML has played a large part in security – both on the positive side in protecting business systems and user privacy, and on the negative side as in hacking or unwanted surveillance. It is out of the scope of this short discussion to go into the general picture of ML applications in security and many of the envisioned 5G use cases. We will briefly touch upon several promising areas where ML can help NFV-based systems to better perform and protect [38,39].
- Autonomous Operations
Within an abstracted and service API-oriented system, ML can use collected real-time data to fine-tune optimization parameters of the overall resource management scheme. It is also promising that the ML system will be able to adapt to load spikes (e.g. during a DDoS attack) with autonomous responses by learning from long-term operational data collected from human expert operators. As we have reviewed throughout this chapter, NFV has made the system highly automatable and also made consistent real-time data readily available. In [38], we call such a highly autonomous system a Sentient Network.
- Self-Defense
There exists a large body of literature now about ML algorithm for anomaly detection and learning latent structures or patterns from network activities. Discovery of invariants in functional, operational, causal and other relationships are crucial in many complex cyber-physical systems such as a smart grid [40]. The telco physical infrastructure itself is such a system. ML can go beyond what traditional data analytics can deliver by discovering deep non-linear, distributed, and time-shifted relationships. Detection of these kinds of complex relationships, and anomalies within them, is a huge step towards creating a large self-defending NFV infrastructure and future applications that will run on it.
- Artificially-Intelligent Customer Service
Beyond the wonders of Photo Captioning, Natural Language Processing (NLP) systems and chat bots, AI and ML can also make the modeling of user needs much more intelligent. NFV allows these systems to have access to data far beyond just the Call Records and mobile device tracking, for example, into end-to-end customer services. Examples include seamless mobility between heterogeneous networks and voice or video emotion detection of quality problem detections. NFV’s flexibility allows the system to address the problem before a customer’s experience deteriorates. Security is a crucial part of this customer experience. Static systems often put security vs. privacy, or security vs. convenience into a zero-sum game. ML can help us differentiate and make choices to optimize the overall experience – without the hassle of making explicit trade-offs every time we face such a choice.
15.8 Conclusions
NFV and 5G security is a complex subject for a short chapter. We approached this topic with an introduction to the essence of what NFV is all about, and showed that an NFV-based telco cloud is fundamental to what 5G can be – much more than a faster wireless network. NFV brings to us new challenges in security, but also much more so in new opportunities – not only because of the capabilities NFV enables, but also because security is in the basic DNA of NFV from day one. These new capabilities will enable us to be ready for 5G and the envisioned 5G use cases in industries as diverse as health care, transportation, energy and media. Lastly, we introduced NFV-based security services, and looked into two areas where NFV can help transform how we meet security challenges in the future: policy-based and machine-learning-based security services. High-level abstraction and data-driven intelligent automation are absolutely essential to solve the future security problems that will be several orders of higher-scale magnitude.
References
- 1 NGMN Alliance (2015) 5G White Paper, February.
- 2 ETSI (2012) Network Functions Virtualization – An Introduction, Benefits, Enablers, Challenges and Call for Action [Online]. Available at: https://portal.etsi.org/nfv/nfv_white_paper.pdf
- 3 ETSI NFV ISG [Online]. Available at: http://www.etsi.org/technologies-clusters/technologies/nfv
- 4 ETSI GS NFV 002 (2013) NFV Architectural Framework [Online]. Available at: http://www.etsi.org/deliver/etsi_gs/nfv/001_099/002/01.01.01_60/gs_nfv002v010101p.pdf
- 5 Anderson, T., Balakrishnan, H., Parulkar, G., Peterson, Jennifer Rexford, J. et al. (2008) OpenFlow: enabling innovation in campus networks, ACM SIGCOMM Computer Communication Review, 38(2), 69–74.
- 6 Open Networking Foundation [Online]. Available at: https://www.opennetworking.org/index.php
- 7 AWS Inspector [Online]. Available at: https://aws.amazon.com/inspector/
- 8 The Guardian. DDoS attack that disrupted internet was largest of its kind in history, experts say [Online]. Available at: https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet
- 9 Wikipedia. Continuous integration [Online]. Available at: https://en.wikipedia.org/wiki/Continuous_integration
- 10 ETSI NFV ISG (2014) Security and Trust Guidance.
- 11 IETF RFC 7348 (2014) Virtual eXtensible Local Area Network (VXLAN): A Framework for Overlaying Virtualized Layer 2 Networks over Layer 3 Networks [Online]. Available at: https://tools.ietf.org/html/rfc7348
- 12 VMWare, Inc. (2014) Data Center Micro-Segmentation [Online]. Available at: https://blogs.vmware.com/networkvirtualization/files/2014/06/VMware-SDDC-Micro-Segmentation-White-Paper.pdf
- 13 IETF RFC 7665 (2015) Service Function Chaining (SFC) Architecture [Online]. Available at: https://tools.ietf.org/html/rfc7665
- 14 Intel Corp. (2015) Improving Real-Time Performance by Utilizing Cache Allocation Technology [Online]. Available at: http://www.intel.com/content/dam/www/public/us/en/documents/white-papers/cache-allocation-technology-white-paper.pdf
- 15 Open Platform for NFV (OPNFV) [Online]. Available at: https://www.opnfv.org/
- 16 The Openstack Project [Online]. Available at: https://www.openstack.org/
- 17 Kernel-based Virtual Machine (KVM) [Online]. Available at: http://www.linux-kvm.org/page/Main_Page
- 18 Linux Container (LXD) [Online]. Available at: https://www.ubuntu.com/cloud/lxd
- 19 Open vSwitch [Online]. Available at: http://openvswitch.org/
- 20 The Fast Data Project (FD.io) [Online]. Available at: https://fd.io/
- 21 Data Plane Development Kit [Online]. Available at: http://dpdk.org/
- 22 The Open Data Plane Project [Online]. Available at: http://opendataplane.org/
- 23 Dell, Inc. (2015) Telecom TV [Online]. Available at: http://static.telecomtv.com/campaigns/Dell/Dell_Custom_High_Velocity_Cloud_FINAL.pdf
- 24 Lan, C. (2016) A Framework for Network Function Virtualization. Electrical Engineering and Computer Sciences, University of California at Berkeley, Technical Report No. UCB/EECS-2016-128.
- 25 OpenDaylight: Open Source SDN Platform [Online]. Available at: https://www.opendaylight.org/
- 26 The Open Network Operating System (ONOS) [Online]. Available at: http://onosproject.org/
- 27 Central Office Re-architected as Data Center [Online]. Available at: http://opencord.org/
- 28 IETF RFC 4364. BGP/MPLS IP Virtual Private Networks (VPNs) [Online]. Available at: https://tools.ietf.org/html/rfc4364
- 29 The Openstack Gluon Project [Online]. Available at: https://wiki.openstack.org/wiki/Gluon
- 30 The Ceph Project [Online]. Available at: https://ceph.com/
- 31 The Open Orchestrator Project [Online]. Available at: https://www.open-o.org/
- 32 The Open Baton Project [Online]. Available at: https://openbaton.github.io/
- 33 Kyle York (2016) Dyn Statement on 21 October 2016 DDoS Attack [Online]. Available at: http://dyn.com/blog/dyn-statement-on-10212016-ddos-attack/
- 34 Group Based Policy [Online]. Available at: https://wiki.openstack.org/wiki/GroupBasedPolicy
- 35 Group Based Policy in OpenDaylight [Online]. Available at: https://wiki.opendaylight.org/view/Group_Based_Policy_(GBP)
- 36 McCarthy. J. (2016) Datalog: Deductive Database Programming [Online]. Available at: https://docs.racket-lang.org/datalog/
- 37 OPNFV Copper Project [Online]. Available at: https://wiki.opnfv.org/display/copper/home
- 38 Chu, W. (2016) A Sentient Network – How High-velocity Data and Machine Learning will Shape the Future of Communication Services [Online]. Available at:http://www.slideshare.net/wenjingchu/a-sentient-network-how-highvelocity-data-and-machine-learning-will-shape-the-future-of-communication-services
- 39 Nagra, J., Ahammad, P. and Jiang, H. (2016) SoK: Applying Machine Learning in Security – A Survey [Online]. Available at: https://arxiv.org/pdf/1611.03186v1.pdf
- 40 Zhang, J., Rahman, S., Sharma, R., Ramakrishnan, N. and Momtazpour, M. (2015) Analyzing Invariants in cyber-physical systems using Latent Factor Regression. in Proceedings of the 21th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining.
- 41 AT&T ECOMP [Online]. Available at: http://about.att.com/innovationblog/031716ecomp
- 42 Open Source MANO (OSM) [Online]. Available at: https://osm.etsi.org/
- 43 Openstack GroupBasedPolocy project. Group Based Policy White Paper.[Online]. Available at: https://wiki.openstack.org/w/images/a/aa/Group-BasedPolicyWhitePaper_v3.pdf
- 44 The Linux Foundation. (2017) [Online]. Available at: https://www.linuxfoundation.org/announcements/linux-foundation-announces-merger-of-open-source-ecomp-and-open-o%C2%A0to-form-new-open
