Chapter 6
Authentication and Authorization—AWS Identity and Access Management
THE AWS CERTIFIED SOLUTIONS ARCHITECT ASSOCIATE EXAM OBJECTIVES COVERED IN THIS CHAPTER MAY INCLUDE, BUT ARE NOT LIMITED TO, THE FOLLOWING:
- Domain 3: Design Secure Applications and Architectures
- 3.1 Design secure access to AWS resources
- 3.2 Design secure application tiers
- 3.3 Select appropriate data security options
Introduction
Your AWS resources are probably your company's crown jewels, so you definitely don't want to leave them unprotected. But you also can't lock them down so tightly that even your admins and customers can't get in.
Finding the perfect balance is possible. Getting there will have a lot to do with the way you authenticate user requests to confirm they're legitimate and then authorize no more and no less than the exact access they'll need. On AWS, authentication and authorization are primarily handled by Identity and Access Management (IAM).
In this chapter, you're going to learn about IAM identities—which are sometimes described as principals. An identity represents an AWS user or a role. Roles are identities that can be temporarily assigned to an application, service, user, or group.
Identities can also be federated—that is, users or applications without AWS accounts can be authenticated and given temporary access to AWS resources using an external service such as Kerberos, Microsoft Active Directory, or the Lightweight Directory Access Protocol (LDAP).
Identities are controlled by attaching policies that precisely define the way they'll be able to interact with all the resources in your AWS account. You can attach policies to either principals (identity‐based policies) or resources (resource‐based policies).
This chapter will describe the following:
- Creating policies to closely control what your principals can do on your account
- Managing the various kinds of keys or tokens used by principals to prove their identities
- Providing single sign‐on solutions for integrating IAM with external providers using identity federation
- Implementing best practices for configuring accounts and roles to properly secure your resources
IAM Identities
The one identity that comes with every new AWS account is the root user. By default, root has full rights over all the services and resources associated with your account. This makes sense, because otherwise there would be no way for you to get things done with the services that lie beyond root control. At the same time, having everything in the hands of this one user makes root an attractive target for hackers: they only need to get the root password or access keys to compromise the entire account.
To reduce your exposure to this vulnerability, AWS suggests that you heavily protect your root account and delegate specific powers for day‐to‐day operations to other users. Figure 6.1 shows the checklist of Amazon's recommended actions in the Security Status section of a typical account's IAM home page.
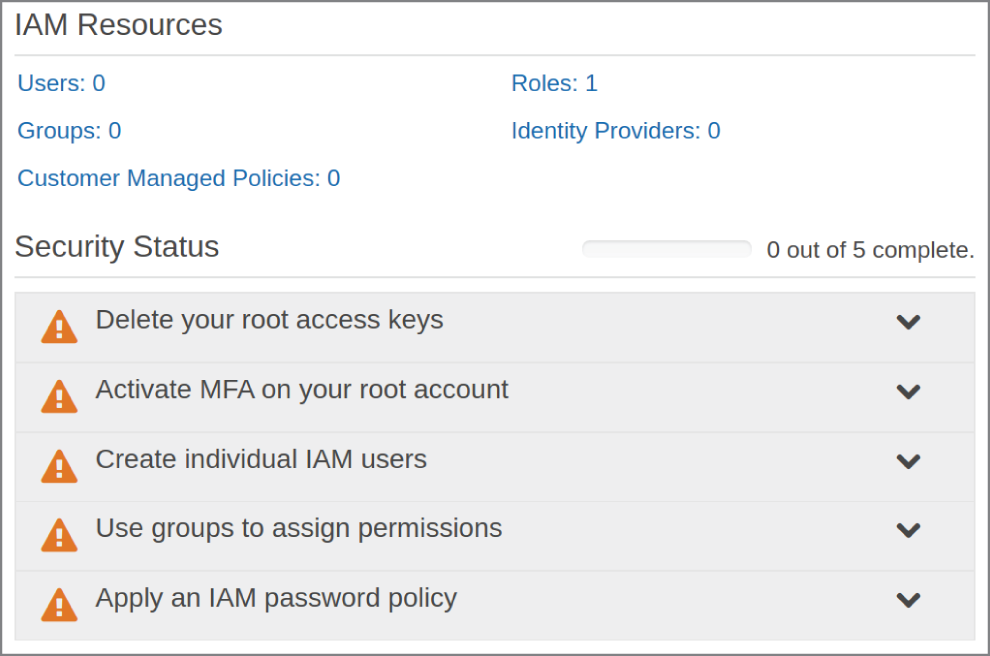
FIGURE 6.1 The Security Status checklist from the IAM page of an AWS account
Understanding how—and why—you can satisfy those recommendations is an important first step for successfully managing your AWS account.
IAM Policies
Your first job should be to understand how policies are used to control the behavior of IAM identities. An IAM policy is a document that identifies one or more actions as they relate to one or more AWS resources. The policy document also determines the effect permitted by the action on the resource. The value of an effect will be either Allow or Deny.
A policy might, for instance, allow (the effect) the creation of buckets (the action) within S3 (the resource). Of course, the way resources and actions are defined will vary according to the particular service you're working with.
IAM provides hundreds of preset policies that you can view from the Policies page accessed from the IAM Dashboard. You can filter policies using key words to narrow down your search. You can also create your own policy using the tools available through the Create policy page in the Dashboard or by manually crafting your own using JSON‐formatted text.
The following example is a JSON AdministratorAccess policy document from the IAM Dashboard interface. Note how it allows the identity holding the policy to perform any (*) action on any (*) resource in your account.
{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": "*","Resource": "*"}]}
Any action that's not explicitly allowed by a policy will be denied. But wait, if all actions are implicitly denied, why would you ever need to explicitly invoke "Deny" within a policy? Such policies could be useful in cases where a user requires access to most—but not all—resources within a domain. "Deny" can single out exactly those resources that should remain off‐limits.
When you associate a policy document with an IAM identity, that identity will then be bound to the policy's powers and limitations. A single IAM policy can be associated with any number of identities, and a single identity can have as many as 10 managed policies (each no greater than 6,144 characters) attached to it.
This raises the potential for trouble: what happens if two policies are associated with a single identity conflict? What if, for instance, one policy permits a user to create new S3 buckets and the second forbids it? AWS always resolves such conflicts by denying the action in question.
You should also bear in mind that, in general, an explicit deny effect will always overrule an allow.
User and Root Accounts
The best way to protect your root account is to lock it down by doing the following:
- Delete any access keys associated with root.
- Assign a long and complex password and store it in a secure password vault.
- Enable multifactor authentication (MFA) for the root account.
- Wherever possible, don't use root to perform administration operations.
Before all that, however, you must create at least one new user and assign it enough authority to get the necessary work done. Typically, that means you give the main admin user the AdministratorAccess policy, and use that user to create other users, groups, and roles—each with just enough power to perform its specific task.
Once all that's done, you're ready to lock down root. You can do that right now using Exercise 6.1.
Perhaps now is also a good time to work through Exercise 6.2 to create a new user for your own account, assign it a policy, and confirm that the policy has the intended effect.
When you create a new IAM user, you'll have the option of applying a password policy. This policy can be set to enforce minimum lengths and complexity along with the maximum lapsed time between password resets. Getting your team members to use only higher‐quality passwords is an important security precaution.
Users can open the My Security Credentials page (accessed via the pull‐down menu beneath the user's name in the console) to manage their security settings. As you can see in Figure 6.2, that page includes sections for the following:
- Updating a password
- Activating or managing MFA
- Generating or deleting access keys for managing your AWS resources through the AWS CLI or programming SDKs
- Generating key pairs for authenticating signed URLs for your Amazon CloudFront distributions
- Generating X.509 certificates to encrypt Simple Object Access Protocol (SOAP) requests to those AWS services that allow it
- Retrieving your 12‐digit AWS Account ID and, for use with legacy S3 ACLs, your canonical user ID
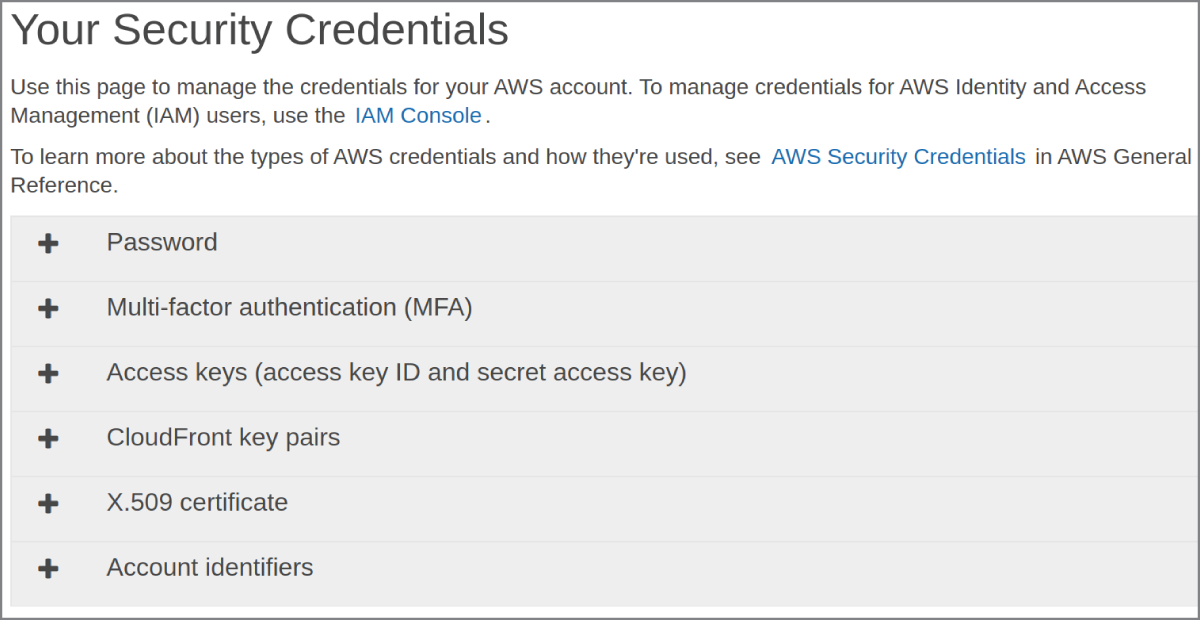
FIGURE 6.2 The six action items displayed on the Your Security Credentials page
Obviously, not all of those items will be relevant to all your users.
Access Keys
Access keys provide authentication for programmatic or CLI‐based access. Rather than having to find a way for your application to input a traditional username and password, you can make your local environment aware of the access key ID and secret access key. Using that information, your application or command can pass authentication data along with each request.
You learned about access keys in action in Chapter 2, “Amazon Elastic Compute Cloud and Amazon Elastic Block Store.” You should also become familiar with the AWS access key lifecycle and how it should be managed.
Deactivating Unused Keys
Each active access key is a potential source of account vulnerability. Audit the keys associated with each of your users from time to time, and if you can confirm that any of these keys are not currently being used, deactivate them. If you have no plans to use them in the future, delete them altogether.
Key Rotation
Best practices require that you regularly retire older access keys because the longer a key has been in use, the greater the chance that it's been compromised. Therefore, it makes good sense to set a limit—perhaps 30 days—beyond which keys must be deleted and replaced by new ones.
Key rotation is automated for IAM roles used by EC2 resources to access other AWS services. But if your keys are designated for your own applications, things can be more complicated. It's a good idea to follow this protocol:
- Generate a new access key for each of your users. Users can also be given the ability to manage their own keys.
- Update your application settings to point to the new keys.
- Deactivate (but don't delete) the old keys.
- Monitor your applications for a few days to make sure all the updates were successful. You can use the CLI command
aws iam get‐access‐key‐last‐used ‐‐access‐key‐id ABCDEFGHIJKLMNOPto determine whether any applications are still using an old key. - When you're sure you have everything, delete the old keys.
You can enforce key rotation by including rotation in the password policy associated with your IAM user accounts.
Exercise 6.3 guides you through a simple access key lifecycle.
Groups
Creating individual users with just the permissions they'll need to perform their duties can be a secure and efficient way to manage AWS operations. But as your account becomes busier and more complex, it can also become a nightmare to manage.
Say, for instance, you've given some level of access to a half a dozen admins and a similar number of developers. Manually assigning appropriate access policies to each user can be time‐consuming. But just imagine how much fun you'll have if you need to update permissions across the entire team—perhaps applying one set of changes for just the developers and another for the admins.
The solution for such scenarios is to create a separate IAM group for each class of user and then associate each of your users with the group that fits their job description. You could create one group for developers, another for admins, and a third for your design team.
Now whenever you need to make changes to the access profile for a particular class, rather than having to edit each user account, you just update the appropriate group. If you're adding an Elastic Beanstalk workload, you can open it up for the entire developers' group with a single action. If you're no longer running your video content through Amazon Elastic Transcoder, you can remove access from the design group.
Exercise 6.4 is a good practical introduction to working with groups.
Roles
An IAM role is a temporary identity that a user or service seeking access to your account resources can request. This kind of authorization can solve a lot of logistical problems.
You might have IAM users who will occasionally need to shut down and restart EC2 instances after an update. To prevent accidental shutdowns, however, you'd rather they didn't normally have that power. Much the way sudo works on a Linux or macOS machine—or the runas command syntax on Windows—you can allow your user to assume an authorizing role for only as long as it's needed.
Similarly, you might want to run an AWS service like Elastic Container Service (ECS) that will launch resources associated with other AWS services in your account. An ECS task, for instance, will probably require access to the Elastic Container Registry (ECR) in order to pull container images. You give ECS the authority to pull data from ECR through a role. In this case, a prebuilt managed role that'll do the job already exists: AmazonECSTaskExecutionRolePolicy.
You might also want to temporarily give IAM users from another AWS account—or users who sign in using a federated authentication service—access to resources on this account. An IAM role (which by default expires after 12 hours) is often the best mechanism for making this work.
You create a new role by defining the trusted entity you want given access. There are four categories of trusted entity: an AWS service; another AWS account (identified by its account ID); a web identity who authenticates using a login with Amazon, Amazon Cognito, Facebook, or Google; and Security Assertion Markup Language (SAML) 2.0 federation with a SAML provider you define separately.
Once your entity is defined, you give it permissions by creating and attaching your own policy document or assigning one or more preset IAM policies. When a trusted entity assumes its new role, AWS issues it a time‐limited security token using the AWS Security Token Service (STS).
Authentication Tools
AWS provides a wide range of tools to meet as many user and resource management needs as possible. The IAM functionality that you've already seen is only part of the story. The Amazon Cognito, AWS Managed Microsoft AD, and AWS Single Sign‐On services are for handling user authentication, whereas AWS Key Management Service (KMS), AWS Secrets Manager, and AWS CloudHSM simplify the administration of encryption keys and authentication secrets.
Amazon Cognito
Cognito provides mobile and web app developers with two important functions:
- Through Cognito's user pools, you can add user sign‐up and sign‐in to your applications.
- Through Cognito's identity pools, you can give your application users temporary, controlled access to other services in your AWS account.
Building a new user pool involves defining how you want your users to identify themselves when they sign up (attributes such as address or birth date) and sign in (username or email address). You can also set minimum requirements for password complexity, multifactor authentication, and email verification.
When you set up an identity pool, you define the pool from which your users can come (using Cognito, AWS, federated, or even unauthenticated identities). You then create and assign an IAM role to the pool. Once your pool is live, any user whose identity matches your definition will have access to the resources specified in the role.
AWS Managed Microsoft AD
Managed Microsoft AD is actually accessed through the AWS Directory Service, as are a number of directory management tools like Amazon Cloud Directory and Cognito. (Cloud Directory is a way to store and leverage hierarchical data like lists of an organization's users or hardware assets.) What the Directory Service tools all share in common is the ability to handle large stores of data and integrate them into AWS operations.
Technically, Managed Microsoft AD is called AWS Directory Service for Microsoft Active Directory. But whichever way you refer to it, the goal is to have Active Directory control the way Microsoft SharePoint, .NET, and SQL Server–based workloads running in your VPC connect to your AWS resources. It's also possible to connect your AWS services to an on‐premises Microsoft Active Directory using AD Connector.
Managed Microsoft AD domain controllers run in two VPC availability zones. As a managed service, AWS automatically takes care of all necessary infrastructure administration, including data replication and software updates.
AWS Single Sign‐On
AWS Single Sign‐On (SSO) allows you to provide users with streamlined authentication and authorization through an existing Microsoft Active Directory configured within AWS Directory Service. The service works across multiple AWS accounts within AWS Organizations. SSO also supports access to popular applications such as Salesforce, Box, and Office 365 in addition to custom apps that support SAML 2.0.
AWS Organizations, by the way, is a service that can manage policy‐based controls across multiple AWS accounts. Companies with more than one AWS account can use AWS Organizations to unify and integrate the way their assets are exposed and consumed no matter how distributed they might be.
AWS Key Management Service
KMS deeply integrates with AWS services to create and manage your encryption keys, which you saw regarding encryption keys for EBS volumes in Chapter 2 and regarding both server‐side and client‐side encryption for S3 buckets in Chapter 3, “AWS Storage.”
The value of KMS lies in how it provides fully managed and centralized control over your systemwide encryption. The service lets you create, track, rotate, and delete the keys that you'll use to protect your data. For regulatory compliance purposes, KMS is integrated with AWS CloudTrail, which records all key‐related events.
Key creation and administration happens through the console, AWS CLI, or SDKs. Key administration powers can be assigned to individual IAM users, groups, or roles.
AWS Secrets Manager
You already know that you can manage identity authentication to AWS services using IAM roles. However, roles won't help you securely pass credentials—referred to as secrets in this context—to third‐party services or databases.
Instead, the passwords and third‐party API keys for many of the resources your applications might need can be handled by the AWS Secrets Manager. Rather than having to hard‐code secrets into your code and then having to regularly update them when they change, with Secrets Manager you can deliver the most recent credentials to applications on request. The manager will even automatically take care of credential rotation.
AWS CloudHSM
CloudHSM (where the HSM stands for “hardware security module”) launches virtual compute device clusters to perform cryptographic operations on behalf of your web server infrastructure. One typical goal is to off‐load the burden of generating, storing, and managing cryptographic keys from your web servers so that their resources can be focused exclusively on serving your applications.
CloudHSM provides a service that's similar to AWS KMS, but according to AWS documentation (aws.amazon.com/cloudhsm/faqs), it is particularly useful for the following:
- Keys stored in dedicated, third‐party validated HSMs under your exclusive control
- Federal Information Processing Standards (FIPS) 140‐2 compliance
- Integration with applications using Public Key Cryptography Standards (PKCS)#11, Java JCE (Java Cryptography Extension), or Microsoft CNG (Cryptography API: Next Generation) interfaces
- High‐performance in‐VPC cryptographic acceleration (bulk crypto)
You activate an HSM cluster by running the CloudHSM client as a daemon on each of your application hosts. The client is configured to fully encrypt communication with the HSM.
AWS CLI Example
The following commands create a new user named steve and confirm that the user now exists:
$ aws iam create-user ––user-name steve$ aws iam get-user ––user-name steve
The list‐policies command will return a long list of the preset policies IAM provides. Among them is AmazonEC2ReadOnlyAccess, which permits its assignee only descriptions of running EC2 resources. You can attach a policy to a user by supplying the policy's Amazon Resource Name (ARN) as follows:
$ aws iam list-policies$ aws iam attach-user-policy––policy-arn arn:aws:iam::aws:policy/AmazonEC2ReadOnlyAccess––user-name steve
Here's the AmazonEC2ReadOnlyAccess policy in JSON format:
{"Version": "2012-10-17","Statement": [{"Effect": "Allow","Action": "ec2:Describe*","Resource": "*"},{"Effect": "Allow","Action": "elasticloadbalancing:Describe*","Resource": "*"},{"Effect": "Allow","Action": ["cloudwatch:ListMetrics","cloudwatch:GetMetricStatistics","cloudwatch:Describe*"],"Resource": "*"},{"Effect": "Allow","Action": "autoscaling:Describe*","Resource": "*"}]}
The list‐access‐keys command will return the names of any existing keys associated with the specified username. If you don't specify a name, keys belonging to root will be returned. The create‐access‐key command will create a new key (make sure you copy and save the key data that's returned), and delete‐access‐key will delete the specified key.
$ aws iam list-access-keys ––user-name steve$ aws iam create-access-key ––user-name steve$ aws iam delete-access-key ––user-name steve ––access-key-id AKIAJAP<. . .>
Summary
The IAM root user that's automatically enabled on a new AWS account should ideally be locked down and not used for day‐to‐day account operations. Instead, you should give individual users the precise permissions they'll need to perform their jobs.
All user accounts should be protected by strong passwords, multifactor authentication, and the use of encryption certificates and access keys for resource access.
Once authenticated, a user can be authorized to access a defined set of AWS resources using IAM policies. It's a good practice to associate users with overlapping access needs into IAM groups, where their permissions can be centrally and easily updated. Users can also be assigned temporary IAM roles to give them the access they need, when they need it.
Access keys should be regularly audited to ensure that unused keys are deleted and active keys are rotated at set intervals.
Identities (including users, groups, and roles) can be authenticated using a number of AWS services, including Cognito, Managed Microsoft AD, and Single Sign‐On. Authentication secrets are managed by services such as AWS Key Management Service (KMS), AWS Secrets Manager, and AWS CloudHSM.
Exam Essentials
- Understand how to work with IAM policies. You can build your own custom IAM policies or select preset policies and apply them to identities to control their access to AWS resources.
- Understand how to protect your AWS account's root user. You should lock down your root user and instead delegate day‐to‐day tasks to specially defined users.
- Understand how to effectively and securely manage user access. This includes the efficient use of IAM groups and roles and appropriately applying both preset and custom IAM policies.
- Understand how to optimize account access security. You can use IAM administration tools to enforce the use of strong passwords and MFA, along with properly managed (rotated) access keys and tokens.
- Be familiar with the various AWS authentication and integration tools. Cognito lets you manage your application's users, and Managed Microsoft AD applies Active Directory domains to compatible applications running in your VPC. Both permit federated identities (where users using external authentication services can be authenticated for AWS resources) through external providers.
Review Questions
- Which of the following is the greatest risk posed by using your AWS account root user for day‐to‐day operations?
- There would be no easy way to control resource usage by project or class.
- There would be no effective limits on the effect of an action, making it more likely for unintended and unwanted consequences to result.
- Since root has full permissions over your account resources, an account compromise at the hands of hackers would be catastrophic.
- It would make it difficult to track which account user is responsible for specific actions.
- You're trying to create a custom IAM policy to more closely manage access to components in your application stack. Which of the following syntax‐related statements is a correct description of IAM policies?
- The Action element refers to the way IAM will react to a request.
- The
*character applies an element globally—as broadly as possible. - The Resource element refers to the third‐party identities that will be allowed to access the account.
- The Effect element refers to the anticipated resource state after a request is granted.
- Which of the following will—when executed on its own—prevent an IAM user with no existing policies from launching an EC2 instance? (Choose three.)
- Attach no policies to the user.
- Attach two policies to the user, with one policy permitting full EC2 access and the other permitting IAM password changes but denying EC2 access.
- Attach a single policy permitting the user to create S3 buckets.
- Attach the AdministratorAccess policy.
- Associate an IAM action statement blocking all EC2 access to the user's account.
- Which of the following are important steps for securing IAM user accounts? (Choose two.)
- Never use the account to perform any administration operations.
- Enable multifactor authentication (MFA).
- Assign a long and complex password.
- Delete all access keys.
- Insist that your users access AWS resources exclusively through the AWS CLI.
- To reduce your exposure to possible attacks, you're auditing the active access keys associated with your account. Which of the following AWS CLI commands can tell you whether a specified access key is still being used?
aws iam get‐access‐key‐used –access‐key‐id <key_ID>aws iam ‐‐get‐access‐key‐last‐used access‐key‐id <key_ID>aws iam get‐access‐key‐last‐used access‐last‐key‐id <key_ID>aws iam get‐access‐key‐last‐used ‐‐access‐key‐id <key_ID>
- You're looking to reduce the complexity and tedium of AWS account administration. Which of the following is the greatest benefit of organizing your users into groups?
- It enhances security by consolidating resources.
- It simplifies the management of user permissions.
- It allows for quicker response times to service interruptions.
- It simplifies locking down the root user.
- During an audit of your authentication processes, you enumerate a number of identity types and want to know which of them might fit the category of “trusted identity” and require deeper investigation. Which of these is not considered a trusted entity in the context of IAM roles?
- A web identity authenticating with Google
- An identity coming through a SAML‐based federated provider
- An identity using an X.509 certificate
- A web identity authenticating with Amazon Cognito
- Your company is bidding for a contract with a U.S. government agency that demands any cryptography modules used on the project be compliant with government standards. Which of the following AWS services provides virtual hardware devices for managing encryption infrastructure that's FIPS 140‐2 compliant?
- AWS CloudHSM
- AWS Key Management Service
- AWS Security Token Service
- AWS Secrets Manager
- Which of the following is the best tool for authenticating access to a VPC‐based Microsoft SharePoint farm?
- Amazon Cognito
- AWS Directory Service for Microsoft Active Directory
- AWS Secrets Manager
- AWS Key Management Service
- What is the function of Amazon Cognito identity pools?
- Gives your application users temporary, controlled access to other services in your AWS account
- Adds user sign‐up and sign‐in to your applications
- Incorporates encryption infrastructure into your application lifecycle
- Delivers up‐to‐date credentials to authenticate RDS database requests
- An employee with access to the root user on your AWS account has just left your company. Since you can't be 100 percent sure that the former employee won't try to harm your company, which of the following steps should you take? (Choose three.)
- Change the password and MFA settings for the root account.
- Delete and re‐create all existing IAM policies.
- Change the passwords for all your IAM users.
- Delete the former employee's own IAM user (within the company account).
- Immediately rotate all account access keys.
- You need to create a custom IAM policy to give one of your developers limited access to your DynamoDB resources. Which of the following elements will not play any role in crafting an IAM policy?
- Action
- Region
- Effect
- Resource
- Which of the following are necessary steps for creating an IAM role? (Choose two.)
- Define the action.
- Select at least one policy.
- Define a trusted entity.
- Define the consumer application.
- Which of the following uses authentication based on AWS Security Token Service (STS) tokens?
- Policies
- Users
- Groups
- Roles
- What format must be used to write an IAM policy?
- HTML
- Key/value pairs
- JSON
- XML
- If you need to allow a user full control over EC2 instance resources, which two of the following must be included in the policy you create?
"Target": "ec2:*""Action": "ec2:*""Resource": "ec2:*""Effect": "Allow""Effect": "Permit"
- What is the function of Amazon Cognito user pools?
- Gives your application users temporary, controlled access to other services in your AWS account
- Adds user sign‐up and sign‐in to your applications
- Incorporates encryption infrastructure into your application lifecycle
- Delivers up‐to‐date credentials to authenticate RDS database requests
- Which of the following best describe the “managed” part of AWS Managed Microsoft AD? (Choose two.)
- Integration with on‐premises AD domains is possible.
- AD domain controllers are launched in two availability zones.
- Data is automatically replicated.
- Underlying AD software is automatically updated.
- Which of the following steps are part of the access key rotation process? (Choose three.)
- Monitor the use of your new keys.
- Monitor the use of old keys.
- Deactivate the old keys.
- Delete the old keys.
- Confirm the status of your X.509 certificate.
- What tool will allow an Elastic Container Service task to access container images it might need that are being maintained in your account's Elastic Container Registry?
- An IAM role
- An IAM policy
- An IAM group
- An AIM access key
