RISK ASSESSMENT IS THE CRITICAL first step in designing an access control system. The risk assessment process allows you to identify potential threats and vulnerabilities within the existing system, prioritize them, and determine ways to minimize or mitigate those risks. A good risk assessment takes into account both the value of the assets to be protected as well as their impact on the overall organization.
Risk is a fact of life. There is no such thing as risk-free activity. Even the most mundane activities—like walking across your living room could be risky if, for example, you trip and fall. In IT, we attempt to minimize risk where we can and mitigate the rest.
Before continuing, let's define some of the key terms you'll see in this chapter:
Risk—The probability that a particular threat will exploit a vulnerability causing harm to an organization; risk is measured in terms of "probability" and "impact"
Asset value—Asset value is the relative value, either in monetary terms or in qualitative value, of the resource being protected by the access control system
Threat—A list or description of potential attacks on a system
Vulnerability—An unintended weakness in a system's design, vulnerability makes it possible for an attacker to take control of a system, access resources to which they are not authorized, or damage the system in some way
Probability of occurrence—The likelihood that an attack will occur
Countermeasure—An action taken to counter another action
Risk assessment is the crucial first step in designing any access control system. In a risk assessment, you determine which risks exist in your environment or may occur in the future. You can measure the level of any risk by calculating the probability of occurrence and the potential impact on your environment. The following standard equation determines the level of each risk:
Risk = Probability × Impact
Knowing the level of risk helps you take appropriate steps to prevent the risk or mitigate it. For example, in most cases it's probably not necessary to design a highly secure, three-stage access control system to protect a desktop printer. The probability that a desktop printer would be exploited is fairly low, and the overall impact of such an exploitation is similarly low. By the same logic, a simple username and password logon system would be inadequate to protect top secret military documents.
Note
You'll learn about types of risk assessments later in this chapter.
In most organizations, risk is not a single problem that can be solved once and then ignored. It is also not just an IT problem. Risk is a multifaceted issue that impacts every part of the organization. A user can create a highly secure password, but the system protected by that password is not considered secure if user passwords are not stored in a secure manner, or if numerous operating system or application-level vulnerabilities allow an attacker to go around the access control system.
Threats can take many forms, depending on the nature of the system under attack. Some systems, such as Web servers, are most vulnerable to denial of service (DoS) attacks. Servers that contain sensitive data are more susceptible to data theft and user impersonation attacks. Networks and individual workstations are most often threatened by attackers who gain access to them as a stepping stone to other, more valuable resources such as servers and databases.
Vulnerabilities are the weaknesses in a system that allow an attacker to gain access. Vulnerabilities are often obscure bugs in application or operating system code that allow attackers to gain access to low levels of the file system, but they can also take more obvious forms. Weak passwords and lax physical security measures are also vulnerabilities because they allow attackers to gain access to a system.
Tip
Case studies and background experience can help you determine threats. However, thinking like an attacker is a highly useful way to perceive potential vulnerabilities. If you can look at your infrastructure from the point of view of an attacker, you may be able to see possible weaknesses and strengthen those areas before an attacker finds them.
Probability of occurrence is a crucial aspect of risk assessments. In an ideal world, organizations would mitigate every possible vulnerability, but time and resources can be limited. It does not make sense to devote excessive resources to mitigating a vulnerability that has a very low probability of occurrence, while ignoring a vulnerability with a much higher probability. For example, if a security alert is issued concerning a certain virus that's spreading across the Internet, the probability is high that your systems may be compromised. It makes sense to devote time and resources to scanning your systems for that virus and taking appropriate measures to eliminate it.
Impact describes the potential consequences of an attack. A scenario with a high probability but low impact is a lower priority risk than one with a high probability and high impact.
For example, a virus that has already infected computers in hundreds of other organizations, costing them millions of dollars in lost productivity and lost data, has a high probability (because it is actively spreading) and a high impact (lost productivity and data). This virus would have a high-risk rating. On the other hand, a badly crafted phishing e-mail that asks the reader to click a link that downloads a 10-year-old virus has a low probability (because most people will recognize it as a fake and delete it) and a low impact (the antivirus software installed on a computer will stop a virus that old). Most risks fall somewhere in between, as shown in Figure 2-1.
Countermeasures (also known as controls) are the steps you take in IT to avoid attack, and to repair and prevent additional damage after an attack has occurred. The most useful countermeasures strike a balance between the cost of implementing the countermeasure—in terms of actual financial cost and in lost productivity—and the value of the asset being protected. A firewall, for example, adds additional maintenance and configuration costs to your organization. If the assets behind the firewall are valuable, such as a file server or database storing sensitive data, the cost is worth it.
Countermeasures do not have to be technology-based. Training employees on handling sensitive data is another valuable countermeasure because it could lessen the risk of a social engineering ploy. Although employee training is a strategic initiative that takes time and resources to execute, it is an effective method to reduce security breaches and often well worth the investment.
In this section, you'll learn about access control threats, vulnerabilities, and how to assess their impact. Access control threats are not something that can be 100 percent eliminated because new ones are constantly being devised. Instead, security professionals try to minimize their probability and impact by eliminating as much vulnerability as possible. In order to correctly prioritize efforts at mitigating threats and vulnerabilities, we perform risk assessments to accurately decide which threats represent the biggest impact to resources and data.
There are three primary threats to any access control system:
Heightened access—The ability of an attacker to log into a system under one level of access and exploit a vulnerability to gain a higher level of access
Social engineering—The use of manipulation or trickery to convince authorized users to perform actions or divulge sensitive information to the attacker
Password cracking is a constant game of cat and mouse within IT security. Security administrators set password rules to guarantee that users create secure passwords, and attackers use a combination of brute force and sophisticated algorithms to break those passwords. Security administrators respond by modifying their password policies, and the cycle begins again. Security administrators are hampered by the users' need for convenience, while attackers are limited only by time and computing cycles.
For example, the security administrator at XYZ, Inc. implements a typical password security policy. The policy states that passwords must be a minimum of eight characters long and may contain upper-case letters, lower-case letters, and numeric characters. This policy ensures that there are at least 628 or 2.18340106 × 1014 possible combinations, as shown in Table 2-1.
Table 2-1. Possible combinations of characters.
NUMBER OF CHARACTERS IN THE PASSWORD | ALL LOWERCASE CHARACTERS | UPPERCASE AND LOWERCASE CHARACTERS | UPPERCASE, LOWERCASE, AND NUMERIC CHARACTERS |
|---|---|---|---|
1 | 26 | 52 | 62 |
2 | 262 = 676 | 522 = 2,704 | 622 = 3,844 |
3 | 263 = 17,576 | 523 = 140,608 | 623 = 238,328 |
4 | 264 = 456,976 | 524 = 7,311,616 | 624 = 14,776,336 |
5 | 265 = 11,881,376 | 525 = 380,204,032 | 625 = 916,132,832 |
6 | 266 = 308,915,776 | 526 = 19,770,609,664 | 626 = 56,800,235,584 |
7 | 267 = 8,031,810,176 | 527 = 1,028,071,702,528 | 627 = 3,521,614,606,208 |
8 | 268 = 208,827,064,576 | 528 = 5.34597285 × 1013 | 628 = 2.18340106 × 1014 |
Table 2-2. Possible combinations of characters.
NUMBER OF CHARACTERS IN THE PASSWORD | LOWERCASE CHARACTERS | UPPERCASE AND LOWERCASE CHARACTERS | UPPERCASE, LOWERCASE, AND NUMERIC CHARACTERS |
|---|---|---|---|
1 | < 1 second | < 1 second | < 1 second |
2 | < 1 second | < 1 second | < 1 second |
3 | < 1 second | 1.4 seconds | 2.4 seconds |
4 | 4.6 seconds | 1.2 minutes | 2.5 minutes |
5 | 2 minutes | 1 hour | 2.5 hours |
6 | 51 minutes | 2.2 days | 6.6 days |
7 | 22 hours | 4 months | 1.1 years |
8 | 24 days | 17 years | 69.2 years |
All these permutations are designed to increase the time it takes for an attacker to crack a password. An attacker uses an application designed to generate all possible permutations of case-sensitive alphanumeric characters and a simple script that inputs a known (or guessed) username with these generated passwords to the access control system. If an attacker's password guessing application can try 100,000 passwords per second, it will take a matter of days to break a very simple password, or thousands of years to break a complex one, as shown in Table 2-2.
Given enough time, the attacker will eventually find the right username and password combination, thus breaking into the system. The role of a security administrator is to identify this vulnerability and modify the password creation policy to require a longer minimum length and the use of at least one non-alphanumeric character. This does not necessarily make it more difficult for the attacker to break in—the attack is not really difficult to begin with because the cracking software does all the work behind the scenes. The longer, more secure password policy simply makes the process take longer. The goal is to push the time frame beyond one of two limits:
The time it takes for the security administrator to realize the attack is occurring and disable the account under attack
The expected lifespan—or at least the attention span—of the attacker
Even with the most sophisticated computing equipment available, it can take years or decades to crack a strong password. However, computer manufacturers are constantly developing more powerful systems, so a password that takes an average of 10 years to crack today may only take a few months to crack five years from now.
Continuing with the example in the last section, once the attacker cracks a user's password and can log into the system, the next step is to obtain heightened access. Chances are the really valuable assets on a system—sensitive data, for example—are protected by file and group permissions that do not allow every user on a system to read or write to them. However, attackers can exploit vulnerabilities in the operating system as well as within application code to usurp access levels normally denied to the user they are logged in as. You'll learn about these vulnerabilities in more detail in the next section.
Social engineering is the single most common strategy attackers use to compromise secure systems. Social engineering is any strategy that tricks a user into giving up their password or granting access to an attacker.
Not all social engineering tactics are technological. In fact, some of the most effective tactics are the simplest and exploit people's general sense of trust and helpfulness. How many times have you held the door open for someone following you into a building? It is simply the polite, helpful thing to do. In a public place, such as the local mall, there is no security threat from such a simple act. But in a corporate environment where access to buildings or floors is limited to authorized personnel, simply holding the door open for someone could be a serious security breach.
Note
Phishing is a very common social engineering tactic in which the attacker creates an authentic-looking e-mail or Web page that convinces the user to enter their confidential information or install software on their computer that secretly records information and sends it back to the attacker.
Consider the following scenario: It is 8 a.m. on a typical Tuesday morning. Hundreds of people are filtering into the office to begin their work day. To enter the building, you must swipe your smart card ID badge. The person behind you has his hands full with his briefcase, coffee cup, keys, and a box of doughnuts. He smiles and asks you to hold the door. "Sure, no problem," you answer as you hold open the door for him assuming he is a fellow employee. He nods his head, smiles again, and thanks you as he heads confidently into another area of the building.
Note
A smart card ID badge has an embedded radio frequency identification (RFID) chip that stores basic identification and authentication information.
As you turn on your computer and check your morning e-mail, the person who followed you into the building roams the hallways looking for unlocked offices and unsecured workstations. Often employees keep sensitive information on their desks, which could help an attacker obtain access to assets stored on the corporate network.
Vulnerabilities are the weaknesses in any security system that make a threat threatening. Without a vulnerability, a threat is simply a theoretical danger. For example, you live with the risk of electrocution every time you turn on the lights. The threat in this scenario is the electrical current running through the wires in your home. The vulnerability here is potentially bad wiring. If the wiring is bad, you could get a shock when you turn on the lights. However, if you were to build a home without that vulnerability—without wiring—you would face virtually no chance of electrocution. Yes, in theory you could still be electrocuted if lightning were to strike you while sitting in your electricity-free home, but the probability of that occurring is low enough to be insignificant.
The primary vulnerabilities you need to mitigate to avoid a password-cracking attack are insecure passwords and insecure storage. As we discussed in Chapter 1, users want passwords that are easy to type and easy to remember. Unfortunately, these parameters do not usually lead to passwords that are difficult to guess or crack.
Note
Microsoft Windows XP used a weak hashing algorithm to store passwords up to 15 characters in length. The algorithm converted the password to all upper case, then divided it into two fields, which were encoded separately. This allowed attackers to crack each half of the password separately using lookup tables.
Even the most secure password is worthless from a security standpoint if it is stored insecurely. Some applications store user passwords as plain text, either in a database or a flat file. This is becoming less common, but you may still run into this situation with legacy code. The more common problem is insecure password hashes. Most passwords are stored in an encrypted form. To decide whether the password entered by the user matches what the system has stored, the user-entered password is passed through a hashing algorithm. If this hashing algorithm is weak, an attacker can steal even the most secure password easily.
The most common vulnerability that allows an attacker to obtain heightened access is insecure applications that are run at too high of a privilege level. A common example of this problem is a Web server such as Apache or Microsoft Internet Information Services (IIS) that is run as the administrative or root user. Often, when installing an application, a system administrator may be tempted to run the application under a privileged user account. This prevents problems when the application tries to write to the file system or access the network, but it also makes that privileged user account vulnerable to attack.
Ultimately, the biggest vulnerability in any access control system is its users. As discussed in the previous section, people generally want to be helpful and trusting, which makes them perfect targets for social engineering. Thorough and repeated training is the best defense against social engineering.
Now that you understand what threats and vulnerabilities are, you can begin to assess their impact. There are two ways to assess risk: quantitatively and qualitatively. The following describes each type of assessment:
Quantitative risk assessment assigns a dollar value to the consequences of a threat. For example, a marketing firm's customer database stores 1,000 records. The replacement cost of each of those records is $50. This is what it would cost the firm to contact each customer to notify them of the breach, and have each record re-created and stored in a new database. The quantitative risk assessment, if this database were to be compromised, is $50,000—1,000 records times $50 per record.
Qualitative risk assessments use subjective ratings rather than dollar amounts. The result of a qualitative risk assessment is generally a subjective rating—high, medium, or low—of the impact of a security breach. Qualitative risk assessments take into account non-financial risks to an organization. For example, the customer database just analyzed above might cost $50,000 to re-create, and the potential legal ramifications combined with the firm's loss of reputation might be enough to put the company out of business. The organization might have plenty of cash on hand to cover the cost of re-creating the database but could not necessarily recover from the legal and public relations damage. Given this information, you would assign a "high" rating. However, you might also discover that the database is stored on a sequestered server that is not accessible to the public, the data stored within the database is encrypted, and it is only used by one application within the company. These factors mitigate your earlier assessment, because you now realize that the probability of a breach is fairly low.
The advantage of a quantitative approach is its simplicity. You simply "do the math" and arrive at an indisputable result. (You'll see the actual formulas later in the chapter.) This makes it easy to prioritize risk mitigation projects—you choose the one with the highest risk rating. The disadvantage to a purely quantitative approach is that it can be deceptive. It either ignores all subjective factors such as loss of reputation, or attempts to place a dollar figure on those factors, which can be exceedingly difficult.
In a qualitative approach, you try to weigh all the factors involved in a threat and come up with a subjective risk rating. The advantage to this method is that it is a more holistic approach than the quantitative method. The disadvantage is its subjectivity. One risk assessor might consider a situation high risk, while another looks at the exact same set of factors and only assigns it a medium risk level. This can make it difficult to prioritize risk mitigation projects.
Quantitative risk assessment relies on several calculations:
Single loss expectancy (SLE)—The cost incurred in one loss incident, for example, a single successful attack on a database. In the example above, the Single loss expectancy (SLE) is $50,000
Annual rate of occurrence (ARO)—Annual rate of occurrence (ARO) represents the number of times per year we can expect a compromise to occur
Annualized loss expectancy (ALE)—Annualized loss expectancy (ALE) is the total cost per year of the threat under assessment
Note
You calculate ALE by multiplying the SLE by the ARO with the following formula:
ALE = SLE × ARO
Using the database with 1,000 records discussed above as an example, the SLE is $50,000. If we expect that the database will be compromised twice per year, the ARO is 2, and the ALE is $100,000:
$50,000 × 2 = $100,000
This calculation relies on two crucial data points: probability of occurrence and the value of the asset. Predicting the probability of occurrence is a tricky thing because you need to combine historical data ("over the past five years, this server has been compromised 10 times") with your expertise and experience, as well as the expertise of others in the business with knowledge of the assets in question.
The value of the assets being protected is the other crucial data point to consider. How do you value a record in a database, or a customer-facing Web site? There are several criteria you can use:
Cost of replacement—What it would cost the organization to replace the asset if it were stolen or compromised
Cost of attainment—What it cost the organization to obtain or create the asset originally
Cost of impact—What the organization would lose if the asset were unavailable; for example, a company would lose $50,000 per hour in lost productivity if the internal network went down
Which criteria you use depends upon the asset you are valuing. It makes the most sense to value a customer-facing Web site based upon its cost of impact. If the public Web site goes down, customers can not place orders and the company loses money. On the other hand, the cost of impact of a customer database record is difficult to ascertain. In that case, the cost of replacement is a more logical criteria to use. Cost of attainment is most often used when valuing legacy code.
There are many risk assessment best practices to draw from. The most effective way to perform one depends upon the scope of the IT infrastructure and assets, as well as the business needs of the organization. Below are some ideas for you to consider while designing a risk assessment approach:
Note
The four risk management strategies—avoidance, acceptance, transference, and mitigation—are discussed in detail in Chapter 6.
Create a risk assessment policy—This policy governs how risk assessments should be performed, both immediately and in the future. It also specifies how frequently to perform risk assessments, and the appropriateness of each of the four risk management strategies—avoidance, acceptance, transference, and mitigation. Many companies create this policy after their first risk assessment.
Define goals and objectives—This allows you to determine the success of the risk assessment. These will vary by organization, but might include things like "reduce the number of significant virus incidents to three per year."
Describe a consistent approach or model—Using the same approach or risk assessment model every time a risk assessment is performed is the only way to accurately define trends within the organization. For example, if the first risk assessment used a quantitative model, and the next used a qualitative model, it would be difficult to decide if the overall risk to the organization had gone up or down.
Inventory all IT infrastructure and assets—If no one remembers the router sitting behind a stack of boxes in the network closet exists, it is unlikely that the password to administer it will be changed regularly. It seems unlikely that a major component of IT infrastructure, such as a router, could be simply forgotten, but it does happen.
Determine the value (either quantitatively or qualitatively) of each asset—This value helps you prioritize risk mitigation projects.
Determine a "yardstick" or consistent measurement to determine the criticality of an asset—This yardstick can be monetary value, as described above, or it can take into consideration the importance of an asset to the organization, or even whether a particular asset is mandated through industry regulation. The key is consistency. Without a standard way of determining criticality, it is impossible to really know whether the router that one member of the risk assessment team deemed "Critical" is really more important than the server that another team member deemed "Major."
Categorize each asset's place within the infrastructure as "Critical," "Major," or "Minor"—This exercise is useful if your organization does not have the resources (either time or budget) to thoroughly secure every asset in the infrastructure. This is very common, in fact. Most organizations have budgetary or staff limitations that preclude securing every single asset. In this case, a multilayered approach on the most critical or major components offers a reasonable overall level of security. You'll learn about multilayered systems later in this chapter.
Because the risks faced by any given organization are unique to that organization, there is no one right way to conduct a risk assessment. Instead, consider the outcome of the risk assessment: what do you (or your manager) need to know? Often a risk assessment is done to justify spending on IT security infrastructure. In this case, you would need to concentrate on the quantitative aspect of risk—how much a breach could cost the organization compared to the proposed investment.
Another common driver for risk assessment is an actual security incident. In this situation, your manager wants to know how likely it is that another incident will occur, and how your proposed solution will mitigate that risk. In this situation, a qualitative approach is more appropriate (although a cost analysis would also be an important aspect of the analysis).
Next, consider the assets you are trying to protect. What are they worth, both monetarily and in terms of impact to the organization? Ideally, every asset would be protected, but you should always weigh the cost of protection against the value of the asset. Unless a desktop printer has a deeply strategic importance to the organization, it is unlikely that the asset is worth enough to justify a sophisticated access control system. Such a system is expensive to implement and costs the user time and energy that is probably not justified. A database containing sensitive information that falls under governmental regulation, on the other hand, is important enough to justify significant efforts to protect it.
Once you have assessed the potential risks to a system, the next step is to design an appropriate access control system to mitigate those risks. In the following sections, you'll first consider the financial aspect of risk. This is where you get the clearest picture of the worst-case scenario, the crisis you are working to avert. You'll then evaluate where access controls are most needed, and how secure those controls must be in order to protect the assets at risk. Finally, you'll examine a multilayered approach to access control.
You read about determining the financial impact of a security breach earlier in the chapter. Security breaches are not only a financial risk, however. Depending upon the information being protected, a security breach could also result in criminal prosecution. Governmental regulations of the health care and banking industries, for example, carry heavy criminal penalties as well as fines for companies that fail to prevent a security breach. If you are responsible for securing systems in a regulated industry, the financial impact of a loss is likely less of a concern than the non-financial consequences, such as prison time.
You cannot secure everything, so you must prioritize. At the same time, many resources can be grouped to share a single access control. For example, a single point of access control at the entry point of the network may be sufficient to protect all the assets on the network. Unless there is an asset of special importance stored on the network, it is unnecessary to place separate access controls on each asset.
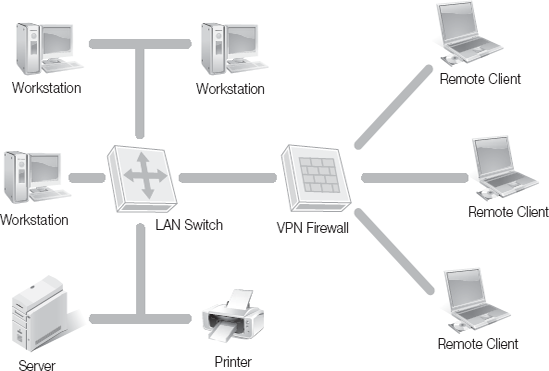
A network diagram, such as the one shown in Figure 2-2, is a helpful tool in determining where to place access controls on a network.
In Figure 2-2, each of the elements shown is an access control point. The workstations and servers all may have access controls limiting who may log on. The firewall has access controls limiting the traffic that may enter and leave the network. The switch may control which ports are able to view traffic. Finally, the printer may be restricted so that only certain users may access it.
A use case diagram, such as the one shown in Figure 2-3, is useful when determining where to place access controls in an application.
Once you know where the access controls should be placed within the system, the next step is to determine how secure they must be. Again, you should weigh the value of the assets and their relative risk level against the cost and inconvenience of the access control. A high priority asset with a risk level of "high" justifies a more sophisticated (and probably more expensive and inconvenient) level of access control than a low priority asset.
In many cases, a simple username and password system is sufficient to protect the assets in question. For more critical assets, two or more layers of access control provide additional protection. For example, the U.S. government uses a "multilayered approach" to securing classified information. Classified documents may only be opened and discussed within areas defined as "Sensitive Compartmented Information Facilities" or SCIFs. These areas have physical and informational security measures around the perimeter, including armed guards and smart card ID scanners. Once inside the SCIF, a user must provide a fingerprint or retinal scan, as well as a username and password to access the computers and files stored within the SCIF.
You may not ever deal with classified documents, but you should be able to design a multilayered access control system for sensitive information such as health records or banking information. In the private sector, the most common multilayered access control systems use a token or challenge-response device coupled with a username and password.
A multilayered approach to access control is one way to mitigate budget and staff limitations to risk mitigation. Rather than trying to secure every asset, you should layer your security efforts. By layering, you ensure that another layer covers any gaps in a given layer of defense. Ideally, these layers should cover the seven domains of a typical IT infrastructure, shown in Figure 2-4. Each domain plays a part in a multilayered access control system.
The primary layer in the User Domain is in training. Users should be trained to recognize common social engineering tactics, as discussed earlier in this chapter. They should also be trained to create strong passwords, and change them regularly.
There are three elements of security in the Workstation Domain: virus scanning, operating system patching, and application-level firewall. Workstation-level virus scanning insures that viruses coming in from e-mails, files downloaded from the World Wide Web, and other unsecure areas do not infect the host workstation. If the virus is stopped at the entry workstation, it cannot infect the rest of the workstations on the network. Regularly patching the operating system will harden against known vulnerabilities and make it harder for an attacker that gets through the outer layers of security to affect the workstation.
Note
An "application-level firewall" is a software-based firewall solution. It is designed to protect a single machine from unauthorized access.
On the local area network (LAN), security layers involve an intrusion detection/prevention system, as well as e-mail scanning and server-level virus scanning. Many organizations add a second layer of security to user training and workstation virus scanning by scanning all e-mail messages when they enter the LAN. The virus threat is not restricted to users downloading files from the Internet and receiving infected e-mails. Servers—especially Windows servers—are also vulnerable to a wide variety of viruses. It simply makes sense to have a virus scanner running on every server, as well as on every workstation.
An intrusion detection system analyzes traffic patterns and compares them to known patterns of malicious behavior. An intrusion detection system (IDS) is most useful in tracking down the mode of attack after the fact. An intrusion prevention system (IPS) is more sophisticated in that it analyzes traffic patterns and reacts to that analysis in real time, blocking suspicious traffic. You can configure an IDS or an IPS to alert systems and network administrators when suspicious activity is present. Modern systems combine IDS and IPS functionality into a single system, allowing administrators to configure flexible responses based upon the type of threat.
This domain represents the intersection between the local area network and the wide area network (WAN). In this domain, the firewall is the primary security layer. The firewall prevents unauthorized traffic from moving from one side of the firewall (the LAN, for example) to the other side (the WAN), while allowing authorized traffic to flow freely. Figure 2-5 shows how a firewall controls network traffic.
There are several types of firewalls. Packet filter, application gateway, and proxy server are the most common. They are described as follows:
A packet filter firewall scans every packet that passes through the firewall and either rejects it or allows it to pass. It uses a custom rule set to determine which packets to allow and which to reject.
An application gateway monitors traffic going to and from a specific application, such as File Transfer Protocol (FTP) or Secure Sockets Layer (SSL). This is most commonly used for communications applications.
A proxy server intercepts all messages entering and leaving the protected network. It effectively hides the location and details of the protected network from the outside world. Proxy servers are often used to monitor and restrict Web browsing in companies. Specific Web sites and search terms can be blocked by a proxy server, or it can be set up to allow only specified uniform resource indicators (URIs).
In this domain, virtual local area networks (VLANs) are the primary point of access control. A VLAN allows network managers to segment resources into logical networks, regardless of their geographical location. A VLAN incorporates broadcast filtering and traffic flow management, as well as other security tools. Figure 2-6 shows a VLAN.
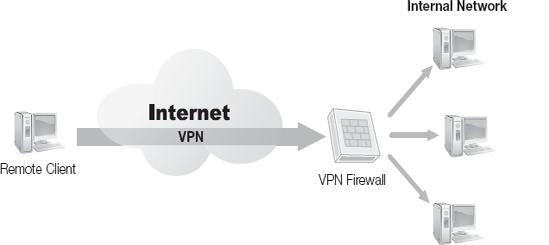
In this domain, IP tunneling and virtual private networking are the primary layers of security. An Internet Protocol (IP) tunnel is created by encapsulating packets within a new IP packet, then sending the encapsulated packets via a secured route across the Internet. A virtual private network (VPN) uses IP tunneling the same way a LAN uses Ethernet cable or wireless connections. Figure 2-7 shows how a VPN is created via IP tunneling through the public Internet. While the data passes through the public network infrastructure over a VPN connection, it is likely more secure than data passed through a private network due to the encryption technology used to protect it.
In this domain, the primary security activity is patching on a regular basis. This requires keeping up with each application vendor, checking for updates and new patches on a regular basis, and testing those patches thoroughly before implementing them. Large enterprise environments use patch management software that automatically checks for updates from multiple application vendors, taking some of the burden off the IT staff. However, you should not automatically install every patch that is released. Many patches contain new or changed functionality that can significantly change your environment. They can also update shared dynamic-link libraries (DLLs) or libraries that are used by multiple applications. If the patch does not contain a security fix or functionality that you really need, it is often a good idea not to install new patches because they introduce volatility to the environment.
Many large IT environments, especially those in heavily regulated industries, require that any change to the environment be first implemented in a test environment where it must undergo thorough regression and user acceptance testing to be sure that the patch to one application does not adversely affect other applications running in the environment by changing shared DLLs or libraries. Unless a patch contains a crucial security fix or updates critical functionality, it is often not worth putting it through such extensive testing. The benefits do not outweigh the necessary testing costs.
Within a multilayered approach, for example, you might institute a training policy for all new users that teaches them not to open suspicious e-mail attachments or download files from unknown Web sites. You would also place a virus scanner on every workstation on the network. Then you would install a firewall on the network that will protect every workstation as well as other assets on the network. In this way, most unauthorized traffic will be caught at the firewall before it ever sees the workstations, and the virus scanner on the workstations will presumably catch any viruses that get past the firewall.
Note
No access control system is 100 percent secure. A determined attacker, with plenty of resources and time, can break into just about any system. The key is to deter the casual attacker and to make your organization a hard enough target to encourage even dedicated attackers to look elsewhere. This way, only an attacker with a specific interest in your organization will continue the attack.
There is a lot of overlap between various layers of defense. This is intentional, and provides a high level of security in those areas of overlap. This type of access control system, called a defense-in-depth strategy, is designed to handle failure. Every access control system fails at some point. A multilayered approach ensures that if one element or layer fails, an attacker will only run into another line of defense. Eventually, only the most dedicated and motivated attacker will break through.
Case studies are an invaluable tool when performing a risk assessment. Rather than trying to re-invent the wheel, you can use case studies to learn how others assessed risk in similar situations to yours. In this section, you will see how risk assessments are performed in real-world situations.
In private industry, risk is understood in terms of profit and loss, and business continuity. How would a security breach impact the ability of the business to continue to run? What would it cost the company in lost revenue?
Let's look at the example of Acme Pharma, a large pharmaceutical company in the United States. Acme Pharma needed to update their network security infrastructure to bring them into compliance with new federal regulations. The first step was to identify what needed updating and the risks they were intending to mitigate. The existing system consisted of a border firewall with a demilitarized zone (DMZ) for Web servers. There were e-mail antivirus and antispam software and some access controls implemented on the internal network.
The first step in the update was assessing what the risks to the environment where, and what the highest risk systems were. Their IT department determined that some of the highest risk systems did not need to be on the corporate intranet and were segmented off into their own protected LAN. From there, extra layers of security were implemented in case of border network breaches. Network-based intrusion detection systems and intrusion prevention systems were implemented. Host-based heuristics virus scans were implemented to augment network-based virus scanning.
On Web-facing systems automated patching was implemented, as well as host-based firewalls and host- passed intrusion prevention systems. It was also determined that the servers themselves exposed too much information. Each Web site hosted on the server was given its own users, with rights limited to the directories that Web site needed to have access to.
The risk assessment showed that certain Web sites were actively targeted for attacks. These systems were segmented away from the rest of the DMZ and further protected with pass-through proxies and application-layer firewalls. It was then determined that security needed to be an ongoing priority. To achieve this goal, a new monitoring team was formed. Log shipping (automatic backup of transaction logs) was implemented, and automated monitors were created. Procedures for manual monitoring were also created, and there was active human monitoring of the network done to augment the automated monitors.
Finally they performed a full audit of user rights and file access controls. Any user with enhanced rights was closely examined to determine the need for those rights. New user groups were formed based on the different roles in the company, and document access was regulated by these groups. Users with a need for heightened rights, such as systems administrators, were not automatically granted rights to all files—they also had to be a member of the appropriate role group.
A new file team was created to handle the roles and access rights. They were tasked with reorganizing electronic document storage. To verify user rights levels and create forms to request elevated rights, they established who in each department could authorize access requests, and established a policy for adding and revoking rights.
Through honest and accurate risk assessment Acme Pharma was able to secure their infrastructure and move from a border-only security system to a defense-in-depth environment. The most valuable systems were determined to be too important and removed from the intranet, removing any possibility of outside intrusion. They also established an access control policy to handle information access inside the organization.
In the public sector, threats are often literally about life and death. Consider the U.S. Department of Defense. If an unauthorized user accesses sensitive battle plans, soldiers' lives could be at risk. Of course, the public sector encompasses far more than just the military. The U.S. Department of Energy is a very high-profile target—especially the various research labs they maintain around the country.
Consider the Pacific Northwest National Laboratory (PNNL). PNNL is a U.S. Department of Energy Office of Science National laboratory. It works on solving problems in energy, the environment, and national security. It has over 4,000 employees conducting research that translates into practical solutions to some of the most vital challenges facing the United States. This makes PNNL a very tempting target.
According to Jerry Johnson, CIO of PNNL, 10 percent of their connection requests are attacks. That translates to around 3 million attacks a day. They also receive over 1 million spam messages a day—around 97 percent of all e-mail sent to the laboratory.
These intrusion attempts come from a wide range of attackers, including organized crime and foreign governments, as well as skilled individuals. Motives for these attacks include economic, national security, and the challenge of breaking into a government facility. The targets of the attack include intellectual property, other proprietary data, and valuable employee information such as Social Security numbers.
To add further complexity to the problem, the lab needs the ability to share data and computer resources with authorized scientists around the world. Security is important, but collaboration is vital. The attackers are also evolving and becoming more sophisticated. Given time, they could defeat any one security mechanism put in place.
To handle this difficult situation PNNL has implemented a seven-layer defense-in-depth strategy. Each layer is intended to stop any attacks that defeated the layer above it:
Layer 1 is the implementation of enclaves. They have extra net enclaves to host their publicly accessible servers, as most companies do. Unlike most companies, they also utilize intranet enclaves. There are three internal security enclaves based on the sensitivity of the information and the threat to it. This allows PNNL to further secure its most sensitive information from security breaches.
Layer 2 consists of border firewalls. They use a traditional network layer firewall both between the Internet and intranet and between the intranet enclaves. Application layer firewalls scan and remove known malware before it reaches the Internet. Over 4 million attacks a day are filtered out by the firewalls.
Layer 3 is strong authentication. PNNL follows the recommendations of the National Institute of Standards and Technology. They require at least eight characters, using mixed case and a numeric or special character. Users are also required to change their password every six months. All user-generated passwords are tested to make sure they cannot be easily guessed.
Note
PNNL requires two-factor authentication for any remote access to the PNNL network. PNNL utilizes a token system that requires a user to know a PIN and have the token. This is a little inconvenient to the users, but adds very strong protection against session attacks and key loggers.
Layer 4 is configuration and patch management. It is vital to effectively manage your security devices. A border firewall does no good if it has an exploitable bug. PNNL utilizes automated patch and configuration updates to every network device, from firewall to network printer. The organization also utilizes a least-user privilege policy, which mandates that users be given the most restrictive set of privileges possible to perform necessary functions. This reduces the risk of users intentionally or accidentally introducing security flaws.
Layer 5 is host-based firewalls. Malware can enter your network through numerous channels that circumvent your border protections. Web sites, thumb drives, and installation disks are some examples. There is also the risk of insider threats. To defend against this, the PNNL utilizes host-based firewalls. These serve two purposes:
They protect workstations from attacks that have defeated the border protections.
They isolate infected workstations.
If malware gets onto a workstation through an unknown attack vector, the host-based firewall keeps it from spreading to the intranet.
Layer 6 is data encryption. Any mobile device that stores data at the PNNL is required to have full disk encryption. This extends past laptops and includes smart phones, PDAs, and USB thumb drives.
Layer 7 is one of the most important and least technical: awareness and training. Users are the weakest link in any network security effort. People can make mistakes and can override controls. Effective user training is the only defense against phishing attacks, especially sophisticated spear phishing attacks tailored to attack specific users. These can get malware, especially malware that attacks unknown vulnerabilities into an intranet. Using aggressive user-awareness programs PNNL has less than a 1 percent response rate to phishing attacks compared to 15 percent typical in other organizations.
No network is 100 percent secure, but by using a defense-in-depth strategy PNNL can reliably secure their sensitive infrastructure. This strategy allows them to further secure data and facilities that are at the highest risk.
In some cases, the biggest factor in a risk assessment does not directly impact profit and loss or even injury to patrons, but damage to critical infrastructure. That infrastructure can include loss of IT resources such as a network or intranet site, or it can refer to physical infrastructure like the controllers for a hospital's emergency power generators. In these cases, risk assessment should be focused on the loss of productivity or the ability of an organization to fulfill its core mission, rather than on loss of revenue. Let's look at a case where a failure to assess the risks to the system, led to lax access controls with unfortunate consequences.
The incident happened in April 2000 at a local water treatment facility in Maroochy Shire, Queensland. A large amount of sewage was released into parks, rivers, and the grounds of a hotel by a former contractor who worked for the facility, causing major environmental and economic damage. While he was eventually caught, the damage was already done.
The attacker had several advantages, because he was familiar with the system and had a copy of the software needed to communicate with the controllers. However, several vulnerabilities contributed to the incident. The system used inadequately protected wireless communication giving the attacker an easy vector to compromise the system. The administrators at the treatment facility also failed to have a proper access control policy in place. As it turned out, the contractor still had full security rights to the system even after he was terminated. A proper access control policy would incorporate procedures for quickly removing accounts that should no longer have rights, thereby preventing or complicating an attack.
The administrators of the system also never considered the threat of an inside attack. They assumed that the proprietary nature of the controlling software and complexity of systems would keep the systems secure. An access control policy that included provisions for removing access when necessary would have greatly reduced the possibility for this attack. Had the risks to this system been accurately assessed, the access control policy would have been expanded and an effective wireless security system could have been implemented.
Risk assessments are used to identify potential threats and vulnerabilities, and prioritize steps designed to minimize or mitigate those risks. There are two basic types of risk assessment: qualitative and quantitative. Qualitative risk assessments are the more subjective of the two types. In a qualitative risk assessment, you assign a label of "high," "medium," or "low" based on a number of factors including overall impact of a perceived threat, its probability of occurrence, and the value of the assets being threatened. In a quantitative risk assessment, you would assign a dollar value to each element of risk, making it easy to prioritize mitigation projects.
Case studies are a good place to start when considering a risk assessment project. Rather than re-inventing the wheel, you can learn from what others have done and apply those lessons to your own situation. Assessment models are another useful tool. They help ensure that you analyze risks logically and do not overestimate the true risk.
Annual rate of occurrence (ARO)
Annualized loss expectancy (ALE)
Asset value
Cost of attainment
Cost of impact
Cost of replacement
Countermeasure
Defense-in-depth strategy
Heightened access
Heuristics
Intrusion detection system (IDS)
Intrusion prevention system (IPS)
IP tunneling
Local area network (LAN)
Multilayered access control
Password cracking
Password hash
Phishing
Probability of occurrence
Qualitative risk assessments
Quantitative risk assessment
Risk
Risk assessment
Single loss expectancy (SLE)
Smart card
Social engineering
Spear phishing
Threat
Virtual private network (VPN)
Virtual local area network (VLAN)
Vulnerability
Wide area network (WAN)
Risk is measured in terms of ________ and impact.
Risk assessment is the first step in designing any access control system.
True
False
The two types of risk assessments are qualitative and ________.
Vulnerabilities and threats are synonymous.
True
False
A vulnerability is a weakness purposely designed into the system.
True
False
You should consider probability of occurrence in order to prioritize limited time and resources.
True
False
What are the three primary threats to any access control system?
Password cracking
Heightened access
Social engineering
Forgotten passwords
A strong password that would take an attacker 10 years to crack in 1990 would take 10 years to crack today.
True
False
As long as users choose strong, secure passwords, how those passwords are stored is irrelevant.
True
False
Insecure applications run as the administrative user are the most common heightened access vulnerability.
True
False
You should weigh the value of the assets and their relative risk level against the cost and inconvenience of the access control.
True
False
You calculate ALE by multiplying SLE by 12.
True
False
You should install every patch that is released for the applications running in your environment.
True
False
Calculate the ALE of a threat that can be expected to occur three times per year, and will cost the organization $50,000 per incident.
Calculate the ARO of a threat with an SLE of $100,000 and an ALE of $200,000.
Calculate the SLE of a threat with an ARO of 4 and an ALE of $100,000.