ACCESS CONTROLS ARE THE METHOD by which users gain access to resources to fulfill business needs. Business drivers should always be at the heart of any access control system, because even the most secure system is useless if it does not advance or support the goals of the organization.
Part 1 of this book discusses the need for access controls. The consequences of weak or nonexistent access control range from inconvenient to downright disastrous, depending on the nature of the resources being protected. For the average user, it may be annoying and inconvenient to have someone else reading your e-mail. On the other end of the scale, without strong access controls, companies could lose billions of dollars when disgruntled employees bring down mission-critical systems. Identity theft is a major concern in modern life, because so much of our private information is stored in accessible databases. The only way that information can be both useful and safe is through strong access controls.
Part 2 covers risk mitigation. There is no such thing as a completely safe system, so you'll learn to recognize the risk factors that apply to each individual situation and mitigate those risks as best you can.
Part 3 addresses the practical matters of implementing, testing, and managing access control systems. Access control is not something you can set up and walk away from. You should continually test and adjust to meet changing business needs as well as new security threats that arise.
Chapter 1 covers a lot of ground, but do not be overwhelmed. You will see this material again in later chapters, and in more depth than what you find here. In addition, resources listed at the end of each chapter will help you learn more about the topics of greatest interest to you.
There are two fundamentally important concepts you need to know before diving into the content for this chapter:
What does "access" mean?
What is an "access control"?
In an ideal world, you wouldn't need to control access to what's important to you or of value—you wouldn't even need to lock your doors. Unfortunately that's not reality—at home or in the business world. In the real world—especially in business—there is a need to protect precious data, network bandwidth, and other assets. This chapter will help you understand how to lock your virtual doors.
Fundamentally, access refers to the ability of a subject and an object to interact. That interaction is the basis of everything we do, both in the information technology (IT) field and in life in general. Access can be defined in terms of social rules, physical barriers, or informational restrictions.
For example, consider a busy executive with an administrative assistant who serves as a gatekeeper, deciding who will be allowed to interact personally with the executive and who must leave a message with the administrative assistant. In this scenario, the visitor is the subject and the executive is the object. The administrative assistant is the access control system that decides who is authorized to access the executive.
Consider another scenario that is a bit closer to home. When you leave your house, you lock the doors. The locked door physically restricts access by anyone without a key to the assets stored inside your house—your TV, computer, and stereo system. When you come home, you unlock the door and replace the physical restriction of the locking mechanism with a human gatekeeper who decides whether or not to let someone enter the house.
What would happen if data were freely available? After all, open source software has certainly made a convincing case for open information. What if the data in question is your company's payroll file? If that file is unsecured, anyone could open the file and obtain sensitive information, including your Social Security number and annual salary. Think of the chaos that would ensue if a disgruntled employee decided you did not deserve the money you made, and reset your salary? Data is one of the most crucial assets in modern life, and it just makes sense to spend as much—if not more—time and energy securing data as you would locking your house at night.
What do executives, deadbolts, and payroll have to do with IT? They are physical counterparts to the technical access control systems that we use to protect digital and electronic resources—sensitive files, servers, and network resources. You might not have specific, documented rules for access when it comes to which visitors you allow into your home, but IT uses formalized systems to grant or restrict access to resources. Computers are not very good at making intuitive decisions, so you have to lay out specific rules for them to follow when deciding whether to grant or deny access.
Access control is the formalization of those rules for allowing or denying access. Access control defines exactly who can interact with what, and what the subject may do during that interaction. It is based on the granting of rights, or privileges, to a subject with respect to an object.
When discussing access control, a "right" is permission to perform a given action. In the preceding scenarios, the chief executive officer (CEO) of the company would have the right to interact directly with the executive, but the person who delivers the executive's mail would not. Your roommate or spouse would have the right to enter your house (as proven by ownership of a key to the door), while someone who lives down the street would not have permission to enter.
There are three principal components of any access control scenario:
Any time you have to decide whether to allow or deny access by a subject to a resource, you have entered the access control problem domain.
A well-defined access control system consists of three elements:
Organizations typically use procedures and tools together to enforce policies. For example, most companies have strict policies to determine who has access to personnel records. These records contain sensitive and confidential information that could be used to inflict serious harm on individual employees and the company as a whole if those records were compromised. The policy may state that only employees within the human resources department, with a specific need for the information contained within a given record, may have access to it.
To enforce this policy, the company has procedures that state that a record can only be given to employees with the proper credentials (the authentication process) who fill out a form stating their specific need for the information contained in the record they request. When the request is approved, the employees may be given a username and password to access the employee records intranet site (the authorization process). The intranet site, along with the username and password, are the tools required to grant access to personnel records.
The subject in an access control scenario is a person or another application requesting access to a resource such as the network, a file system, or a printer.
There are three types of subjects when it comes to access control for a specific resource:
Authorized—Those who have presented credentials and have been approved for access to the resource
Unauthorized—Those who do not possess the proper credentials or do not have the appropriate privileges to access the resource
Unknown—Those who have not presented any credentials at all; it is unknown whether they should be given access or not
The difference between an unknown person and an unauthorized one is timing. An unknown person is anonymous. They have not attempted to log in or access a restricted resource—yet. As soon as an unknown person attempts to access a restricted resource, they must fall into one of the other two categories: authorized or unauthorized.
Four broad categories of technologies can be subjects for the purposes of access control:
Networks—A network is a subject when a resource on one network requests access to a resource on another network. A firewall rule that authorizes access to the Internet might use the internal network as a subject, with the Internet as the object.
Systems—A system is a subject when one system requests access to resources on another system or on the network. This usually happens when a PC attempts to access a printer across the network.
Processes—A process is most commonly a subject when an application process requests low-level access to the file system.
Applications—An application is a subject when it needs to access external resources such as a printer or the network.
A technology subject does not have a username and password the way a human subject might, but it does have the same authorized, unauthorized, or unknown status.
There are three main categories of objects to be protected by access controls:
Information is the most common asset in terms of IT access controls. You put passwords on databases and applications to ensure that only authorized users can access them. Technology objects are just as important, because a malicious user can easily compromise the integrity of data by attacking the technology that stores and uses it. If an unauthorized user gains access to a file server, that user can easily steal, delete, or change the data stored on the file server.
Physical security is the process of ensuring that no one without the proper credentials can access physical resources, including hardware and physical locations. If all the servers require a password to log on, why bother restricting who can enter the server room? The answer is simple—if a malicious user's goal is to bring down a server, they don't need to log in. All they have to do is unplug it, steal it, or destroy it.
Note
Consider an automated teller machine (ATM) in a mall. That system deals with highly sensitive data, but in order to fulfill its purpose it must be in an open, easily accessed area. In this type of situation, information-and technology-based access controls become doubly important.
Most server and network systems have "backdoors" that are available to anyone with physical access to the machine. These backdoors allow system administrators to take control of a server that has been corrupted. A Cisco router, for example, gives anyone with the right communications device and the right codes full access to the router without the administrative password. Some locations, such as a server room, are controlled-access locations for the reasons just described. Others must have uncontrolled access in order to be useful.
There are three steps to the access control process:
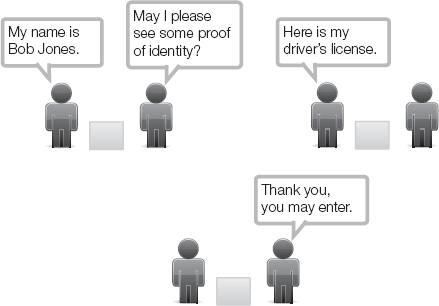
The second step usually happens behind the scenes, so the subject is really only aware of two stages: they enter their credentials and are either given or denied access to a resource. Figure 1-1 illustrates the access control process using human interaction as an example.
The first step in any access control process is identification. The system must be able to apply labels to the two parts of the access equation: the subject and the object. In this case, a label is a purely logical description that is easy for the computer to understand. A human might easily recognize that "Beth" and "Elizabeth" are the same individual, but a computer cannot necessarily make that logical connection.
To make things simpler, you can assign a universal label to each subject and object. That label remains with that individual or resource throughout the life cycle of the privileged interaction with the object. The object also has a label to distinguish it from other resources. For example, a network might have six printers available, labeled "printer1," "printer2," and so on. A person's label might be a user ID, his or her e-mail address, employee ID, or some other unique identifier.
The key is that each label must be unique, because it also provides accountability. When combined with the authentication system (which correlates the identified subject with the resources they are allowed to use) and system logging facilities, unique labels correlate subjects with their actions. This becomes especially important when trying to track down the cause of a system failure. This correlation relies on the trust between the subject and the access control system. If you do not trust that a subject is who they say they are (and this trust is predicated on proof), the use of a uniquely identifying label is pointless.
Note
Trust is a two-way street. The system must trust that a subject has not falsified his or her credentials, but at the same time the subject must be confident that the system will store those credentials securely. If a system stores usernames and passwords insecurely, they can be stolen and used to impersonate legitimate users. This destroys the integrity of the entire access control system.
Authentication takes identification one step further by requiring proof of identity. There are many ways to authenticate a subject. The most common ones are:
Password—A secret word or combination of characters that is known only to the subject. A good password is difficult to guess but easy for the subject to remember.
Token—Something the subject has that no one else does, such as a smart card or a challenge-response device.
Shared secret—Something only the subject and the authentication system know, such as the name of the subject's favorite pet or the mother's maiden name.
The key to both a password and a shared secret is secrecy. If the subject shares its password or shared secret information with someone else, the authentication system becomes less secure and the ability to correlate an action to a subject becomes less precise. Many companies regulate this problem with a policy that an employee is personally responsible for anything done under his or her credentials. If an employee shares his credentials with a friend, for example, he is personally responsible for anything the friend might do.
Most authentication systems only require a single-stage authentication, but those protecting highly sensitive assets might use multiple factors. The three most common factors are:
Something you know—Generally a password or shared secret
Something you have—A token or smart card ID badge
Something you are—Fingerprints or other biometric factors
The last two factors are often used to provide or restrict physical access to secure buildings or rooms within buildings, although they can be used in access control systems protecting data as well. You will learn more about all three authentication factors later in the chapter.
Confidence in any authentication system can be measured by two components: the type of correlation and the number of authentication factors. A "retinal scan" (which is a biometric method) is inherently more secure than a simple password because it is much more difficult to copy or steal an eyeball than it is to guess or steal a password. Using more than one authentication factor increases the security of the system, because if one stage of the authentication system is compromised, the second can still restrict access to those who do not have the proper credentials. This is referred to as "two-factor authentication" and is covered in further detail in Chapter 10.
Once a subject has identified itself and the access control system verifies the subject's identity, the access control system must determine whether the subject is authorized to access the requested resources. Authorization is a set of rights defined for a subject and an object. They are based on the subject's identity. For example, a manager in the human resources department might be authorized to view personnel records but not authorized to edit the year-end financial report.
Authorization rules can be simple—anyone with a username and password on the system can access the information stored there. Authorization rules can also be complex, depending on the value of the resources being protected and the number of people needing access.
In a small organization with a high level of trust between the users and resources that are not sensitive, a simple authentication system is reasonable. An enterprise system with a mixture of highly sensitive data and open printers on the same network needs a more complex authorization system. In this case, you might design a system with multiple levels of authorization—a low-level employee might be given rights to the printers, while a manager would have rights to the printers and some areas of the file system. High-level executives might have all the rights of a manager, as well as rights to view sensitive information. How you define your authorization rules depends upon business needs and the sensitivity of the resources.
Logical access controls are login systems, and are the ones you are most likely to find yourself creating. Physical access control is usually not the responsibility of the IT department.
Logical access controls can be based on one or more criteria, including:
Who—The identity of the subject, proven by a username and password combination
What—The presence of a specific device or access token
When—Combined with subject identity, access can be granted during one time period and denied at another time
Where—Either physical or logical location
Why—The defined purpose for which access must be granted to a subject
How—What type of access can be granted to a subject
You should take each of these criteria into account when designing an authorization system.
The "who" criterion is the most intuitive, as discussed above. One subject may be given access while another is denied.
Specific devices or tokens are generally combined with a username and password. They add a second layer of identity proof, because in theory only the authorized user will possess the token. A house or car key is a good example of a device that authorizes access to resources. The problem with an authorization system based solely on a device or token is that it can be lost or stolen. For this reason, tokens are usually combined with usernames and passwords in logical access control systems.
Time profiles can be a useful way to prevent an authorized user from using resources for unofficial purposes. For example, an employee may be legitimately authorized to use a network printer, but it should raise questions if that employee begins to print jobs outside of normal business hours. This could mean that the employee is working overtime, or it could be an indication that they are using company resources for personal projects. Time profiles are also used when a user has a limited amount of time to perform an action. For example, a journalist may only have until 1 p.m. to submit his or her story for the evening newscast. Restricting the journalist's access to the story submission system after 1 p.m. prevents the journalist from turning in the story on time, forcing the editing staff to scramble to fit the story in.
Tip
If you must use time profiles to meet business needs, design the system to be easy to modify for special cases such as overtime or a breaking news story.
Location can be another way to ensure that only authorized users access resources, and that those users are performing legitimate tasks. You can determine location either logically or physically.
"Logical location" refers to the Internet Protocol (IP) address or Media Access Control (MAC) address a user connects from.
"Physical location" is more obvious—within a certain building or secured facilities. If a user attempts to access resources from his or her corporate laptop on the company network, the system grants access. The same user could try to access those resources from his or her home PC and be denied. This type of restriction is often used with highly sensitive information. If an employee decided to work from the local coffee shop and accessed a confidential file, another patron at the coffee shop could "sniff" that transmission and gain access to confidential information. Restricting access by location ensures that sensitive data is only sent over trusted, secure networks.
Tip
"Why does this user need access to this resource?" This is a question you should ask every time you design a set of access controls. Every user should have a well-defined purpose related to his or her job function in order to gain access to resources.
In some cases it is not necessary to assign rights to individuals. This is especially true in large organizations. Rather than deciding and assigning rights to each individual within an enterprise, you cluster individuals into groups based on department, job title or role, or some other classification.
You can assign individuals to several groups. For example, every person within an enterprise may be a member of the Employees group, with read access to the company intranet and an account on the time card system. A manager might also be a member of the Managers group, and have write access to his or her department's page on the intranet as well as read access to each of his group's time card reports. Employees on the corporate retreat committee would have their normal levels of access as well as access to files related to the corporate retreat, regardless of their other job functions. A manager might not have access to those files, despite the fact that employees below him do.
Note
Granting access by groups rather than individuals does not reduce individual accountability for activities. An individual still needs to log in with a unique username and password, and the log files catalog actions by username, not by group.
Group access rights are a way of simplifying the management of the rules. When an employee changes roles within an organization, you merely have to change his or her group membership, rather than altering the employee's individual access rights. Similarly, when you create a new resource and want to grant access to a particular role, you can do that using the group mechanism and you don't need to list all of the individual employees.
So far you have focused primarily on subjects and access controls. Now you will examine how objects fit into access controls. Objects are defined by four factors:
Acted upon—Are the target of a subject's request
Passive—Do not act back upon the subject
Contain something of interest—Usually information
Can have a high level of granularity—Can have several layers or elements
The biggest difference between a subject and an object is passivity. A subject is active—it acts upon a passive object. An object must contain something of interest to the subject. This is usually information, but can be non-informational as well. Consider a printer. It is passive in that it is the target of a print request and does not generally initiate new contact with the subject after the print job is complete. It contains, or rather produces, something of value—a hard copy of digital information. Printers, however, do not usually have a high level of granularity. They receive a print request and process it. A server, however, can have many elements that must work together to supply the subject with the information they request.
You can define objects at many levels, depending on your business needs. Some examples of objects include:
Data element—This is the lowest level of granularity for information-based assets. For example, if a database table contains a Social Security number, you may need to place special restrictions on that data element.
Table—You may also define a database table as an object. You could grant users access to tables containing employment information, order information, or other types of information based upon their roles in the organization.
Database—You can also define an entire database as an object. For example, you might grant all employees read-only access to the entire product information database, and give product managers write access to certain tables or rows within that database.
Application—An application is also an object. You might wish to grant some users the ability to run an application, while denying it to other users. Applications may also implement their own access control systems that restrict use of individual components of the application. For example, an administrative user within the application may see a menu that allows them to add or delete other users. A basic user would see this menu and would not have access to that functionality within the application.
System—A system is also a security object. For example, you may restrict access to the CEO's laptop so that only the CEO and his or her administrative assistant have permission to log on to it.
Operating system—This provides various user modes, such as privileged or superuser mode, user mode, and guest mode. It also governs configuration files and log files. The operating system also provides write protection on files, subdirectory permissions, and restrictions on the ability to create, delete, access, or execute new files or directories.
Network—It provides access restrictions for resources stored on the network or on a subnetwork. It provides the ability to traverse network connections and restricts external access, either inbound or outbound.
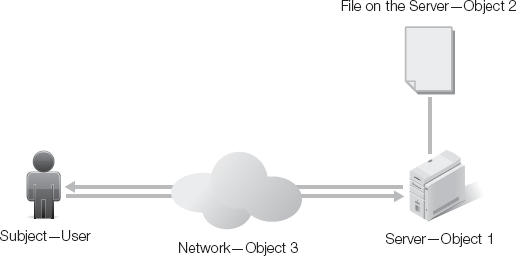
In real-world applications, these levels may work together or separately to provide access rights to resources. A simple example is an application (in this case the application is the subject) that needs to work with data stored in the database (the object). It makes a request through an application programming interface (API), which handles the communication between the application and the database.
A more complex example is that of a user who needs to modify a data file stored on a file server across the network. In this case, the user (subject) logs into the operating system (object 1) and requests access to the file server across the network (object 2). The system layer on the file server (object 3) checks the user's credentials against its rules to determine if the user has no access, read-only, read/write, or administrative access to the particular data file requested.
As described earlier in the chapter, an authentication factor is a way of confirming the identity of the subject. The three primary authentication factors are:
Something you know—Secret knowledge
Something you have—A token or device
Something you are—Unique physical characteristics
Most authentication systems rely solely on the first factor, implemented as a username and password combination. For access to highly sensitive data, you might combine the first two factors, requiring a token just to access the login screen, where the user would enter his or her username and password. The most sensitive data is protected by all three factors. For example, the United States military uses Sensitive Compartmented Information Facilities (SCIF). Just to walk through the door of a SCIF requires recognition of identifying characteristics such as a retinal or fingerprint scan (the "something you are" factor), swiping an ID badge (the "something you have" factor), and typing in a PIN (the "something you know" factor).
A password is the most common authentication tool. Many people use passwords every day to check e-mail, log into online banking, and use the ATM. The biggest password challenge you will face is convincing users to use strong passwords. Users are concerned primarily with convenience. Ideally, you would prefer to have a simple, easy-to-remember password. However, simple passwords or ones based on your name or a dictionary word are also easy for malicious users to guess. An easily guessed password is almost as unsecure as no password at all.
To address this problem, you need to set password requirements on length and composition. For example, you could require that a password have at least eight characters, and that they must contain a combination of upper and lower case characters, as well as numeric or punctuation characters. This system ensures strong passwords, but you might have difficulty remembering them. Because users are primarily concerned with convenience, not with the security of the system, they often write down difficult passwords and post them in obvious locations. A malicious user with physical access to your work space can easily find the desired password.
Tip
One solution to the password problem is the use of a passphrase, such as "IneedToRememberASecurePassword." It is longer than a typical password, but easier for a human to remember. In systems with maximum password lengths, you can use a passphrase as a mnemonic device to remember complicated passwords. For example, the passphrase "Anyone for some tennis?" could be a reminder for the highly secure password "ne14+10s."
Used alone, a physical token or device is generally used to provide physical security. Think of a smart card ID that you wave in front of a reader to gain access to specific floors of an office building. Tokens are also used in conjunction with passwords to provide logical access controls. Tokens can take a variety of forms such as the smart card or a time-variable token such as RSA's SecurID.
"Time-variable" tokens change users' passwords at regular intervals, usually every 30 to 60 seconds. Users have a physical device that tells them what their password is set to at the moment they need to log in. This two-stage authentication process ensures that passwords are not guessed or stolen—and if they are, damage is limited because the password is only valid for a brief period of time.
Possession of the physical device or token is the only way to retrieve the current password. Because the token could be lost or stolen, this type of authentication requires a two-stage login process. For example, a user activates the token to find her active password. She enters the password, along with her username and is granted access to a secondary login prompt. At this second prompt, she enters a conventional password that does not change. In this way, if the user's conventional password is guessed or stolen, a malicious user would not have the token and would not be able to access the secondary login prompt to enter the stolen password. If the token is lost or stolen, a malicious user is stopped at the secondary login prompt because he or she presumably does not also have the user's conventional password.
"Challenge-response tokens" are similar to time-variable tokens. An authentication system using this type of token will begin with a code (the "challenge"), which the user enters into the token device. The token provides another code (the "response"), which the user enters into the authentication system. Assuming that the response code is correct, the user will be granted access to the secondary login system where he or she enters a conventional username and password. The challenge and response codes are randomly generated to avoid the possibility of guesswork.
This is the most advanced, as well as the most time-tested of the three primary authentication factors. It relies upon either physical or behavioral characteristics. Humans have been using characteristics to authenticate each other for millennia. Consider an infant who recognizes its mother or other primary caregiver. The infant uses visual cues, scent, and the sound of the caregiver's voice to authenticate the caregiver's identity and determine whether to settle or scream.
Note
Biometrics, which includes fingerprints, retinal scans, and so on, is an important "Something you are" authentication factor. You will learn biometric essentials later in this chapter; Chapter 9 covers biometric access control systems.
Law enforcement agents also use this type of authentication when they observe an individual engaging in suspicious activity. A police officer may give only the most cursory glance to an individual walking openly down the street, but will investigate further (or call in reinforcements) if they see someone sneaking behind a building holding a gun. The police officer has used behavioral characteristics to decide whether the individual was a law-abiding citizen or a potential criminal.
Biometrics is the study of physical human characteristics. IT uses biometrics to accurately identify an individual. There are two primary types of biometric authentication systems: physical and behavioral. Physical biometrics read physical characteristics, such as fingerprints, retinal scans, hand geometry, and facial recognition. Physical biometrics are highly reliable because they measure characteristics that are unique to each individual. Even identical twins do not have the same fingerprints or retinal scans.
Note
Chapter 9 explores biometrics in detail. You'll learn more about authentication factors in Chapter 10.
Behavioral characteristics may include tempo or speed of typing (or keystroke dynamics), writing rhythms, and voice recognition. Behavioral biometrics requires a significant "training period" for the system to "learn" a legitimate user's behavior patterns. They are also much more subject to error than physical characteristics.
In this chapter, you learned the basics of access control. The purpose of access control is to regulate interactions between a subject (usually, but not always, a human user) and an object, such as data, a network, or device. The key difference between the subject and the object is passivity: the subject acts upon a passive object. There are three key components of access control: identification, authentication, and authorization. First, both the subject and object must be identified. Second, the subject's identity must be proven or authenticated. Finally, the authenticated subject is authorized to act upon the object. You can establish logical access controls for individual subjects, groups of subjects, and objects.
Authentication methodologies are based on three factors: something you know, something you have, and something you are. Once the subject is identified and authenticated using one or more of these factors, the authorization system grants access to an object based on a specified rule base.
Access
Access control
Authentication
Authentication factor
Authorization
Biometrics
Identification
Object
Passphrase
Password
Physical security
Policies
Procedures
Shared secret
Subject
Token
Tools
The three principal components of access control are ________, subjects, and objects.
The subject is always a human user.
True
False
Which of the following describes technical methods used to enforce policies?
Access control
Procedures
Tools
Physical security
Authentication
An organization typically uses procedures and tools together to enforce policies.
True
False
The three states of a subject in an access control scenario are authorized, unauthorized, and ________.
Physical security is typically the responsibility of the IT department.
True
False
What is the first step in the access control process?
Logging in
Authorization
Authentication
Identification
Access
Which of the following is an example of the "something you know" authentication factor?
Username
Token
Password
Retinal scan
Access control list
Which of the following is an example of "something you have"?
Username
Token
Password
Retinal scan
Access control list
Which of the following is an example of "something you are"?
Username
Token
Password
Retinal scan
Access control list
Authorization rules can be as simple or complex as business needs require.
True
False
The four basic access levels are ________, Author, Read only, and No access.
Assigning group access controls eliminates individual accountability.
True
False
The two types of biometric authentication methods are ________ and physical.