PHYSICAL SECURITY IS OFTEN CALLED the most overlooked branch of security. Organizations that are diligent about creating strong passwords and monitoring their firewall and intrusion detection systems aren't always as thorough with physical facility security. In this chapter, you will discover ways to secure the facilities that house sensitive resources, and how to use biometric technology to verify an individual's identity.
Physical security is humanity's oldest form of access control. Chances are good that you encounter many types of physical security every day, without really thinking about what they are and why they are there. As a security practitioner, it's important that you understand the purpose behind physical security measures and how they contribute to an overall access control strategy.
A good physical security strategy is designed in layers. This ensures that if an intruder bypasses or breaks through one layer, another layer will delay or stop him or her. In this section, you will read about the various layers that comprise a physical security strategy.
Perimeter security is any method that restricts access to a defined area, such as a military base, corporate campus, infrastructure facility, or office building. It is the first layer of defense in a physical security strategy. A backyard fence is a common example of perimeter security. It surrounds an area—a parcel of land that is designated for use by a homeowner—and restricts access to that area. Not only does it keep others out of a homeowner's yard, it also keeps the homeowner's pets inside the perimeter. In this way a fence serves two purposes. It restricts access both to the yard and to the outside world.
Landscape design is an important aspect of perimeter security. From a purely aesthetic point of view, it may seem natural to improve the look of a fence by planting trees or bushes around it. Unfortunately, these natural elements can also provide a way for an intruder to climb over the fence. They can also provide cover for an intruder. This is not to say that every fence must be surrounded by 50 feet of bare ground. Landscape elements can also double as perimeter security devices. Thorny or spiky bushes can be planted below windows and other potential vulnerable spots in the perimeter of a facility. A well-placed bush will not stop a determined intruder, but it will encourage the intruder to look for another entry point.
Lighting is another key point in both landscape design and perimeter security. You should design lighting to illuminate official entry points and those areas that an intruder may use to break in. However, landscape lighting design should also avoid creating large areas of shadow that could provide cover to an intruder.
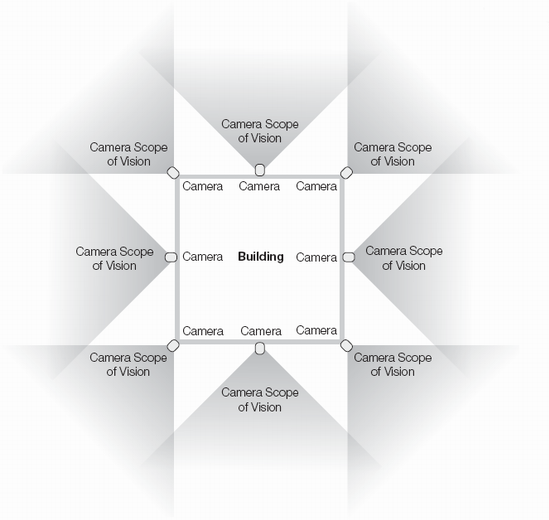
Security guards and closed-captioned video play an important role in perimeter security as well. Prior to the development of closed-captioned video systems, security guards could only patrol the area they could physically see from any given location. Therefore, to provide full perimeter coverage, a facility needed enough guards so that each of them could maintain line of sight with the guards on either side. Video cameras placed in such a way that their fields of vision overlap slightly, as shown in Figure 9-1, provide the same level of coverage with fewer guards. If they view suspicious activity on the monitors, one can investigate while the other continues to monitor the video system for additional activity in other areas of the facility.
Although fences, landscaping, and guards are all designed to keep people out of a facility, there also needs to be a way to let authorized individuals into the facility. Gates of various types allow for monitored, controlled access to a secured facility. Not only do they allow for identification and authentication of individuals wishing to gain entry, they also restrict the flow of traffic into and out of a facility.
Gates are also a weak point in the perimeter, so their security should be heightened to compensate. The mere presence of a security guard at the gate is a deterrent, because it sends the message to intruders that the area is actively monitored and their presence may be detected. The same guard can perform identification and authentication tasks by checking ID badges of those wishing to enter through the gate and cross referencing with a list of authorized individuals.
In some cases, building security and perimeter security are the same. This is most often the case with organizations located in urban office buildings. The organization's perimeter is the outer wall of the building itself. In other cases, the building will be located at the center of a large, open expanse of landscaped ground. In those circumstances, building security is a second layer of defense behind perimeter controls.
Building security involves some aspects previously discussed in perimeter security: lighting, security guards, and gates. It also includes elements such as locks.
Lighting design, both outside the building and in the entryway, is an important part of building security. Sensitive areas, including entryways, loading docks, and utility boxes, should be well-lit to deter intruders and to enable security guards to monitor those areas.
Security guards stationed at the entry points to the building provide the same benefits as those stationed at a gate. Their presence is a deterrent, and they can perform identification and authentication tasks. The next section covers securing entry points in depth.
Access controls for building security revolve around the concept of the locked door. A locking mechanism can be as simple as a deadbolt with a key held by the building owner, or it can involve a complex system of ID badges and biometrics, which you will learn about later in this chapter. It is important to remember that when designing a locking mechanism, an intruder often takes the path of least resistance. A complex and highly secure lock might not prevent an intruder from entering the building if the intruder can simply remove the hinges that attach the door to the wall or break a nearby window. The lock strength must be matched by the integrity of the door and the surrounding area.
Points of entry are weaknesses in any perimeter or building security plan. They must be designed to allow authorized individuals to access the building or facility, while identifying unauthorized individuals and preventing those people from entering (or exiting, in some cases).
Ensure your entry points are designed so that it is difficult or impossible to approach undetected. They should be well lit, and free from heavy landscaping that might provide cover to an intruder. Security guards posted nearby provide another layer of security at entry and exit points.
Cameras filming these areas not only allow security guards to monitor for suspicious activity, but they also provide a record of who comes and goes. Although this may not prevent an intruder from entering the facility, it will provide evidence of his or her activity later.
It is important to note that when designing a physical security system, you should not only be concerned with who enters a facility but also with who leaves. This is especially important in specialized facilities such as day care facilities, hospitals, and prisons, which are designed to keep people in as much as to keep people out. In a day care, it could be a catastrophic failure of physical security if a child were to wander away from the facility. Potential exit points must be monitored as closely as the official entry points to prevent this type of situation. Similarly, in health care facilities, especially those that serve mental health patients, exit points must be secured to prevent patients from leaving and becoming lost or harmed.
Physical barriers play an important role in perimeter and building security. Bollards are short vertical posts designed to control traffic and prevent vehicular attacks on a building. Bollards are designed to allow easy pedestrian access to an area while preventing vehicular access. They are often installed in areas where terrorist attacks are a concern.
Moveable concrete barriers are used in places where access and traffic patterns must be changed to suit differing circumstances. They are often used in large public areas during special events such as festivals and concerts, where crowd control and security are a major concern.
Once inside the building, different areas require different security measures. Generic work areas, for example, may not require any additional security systems beyond perimeter and building security. Simply monitoring those areas for suspicious behavior is usually sufficient. Sensitive areas such as data centers, however, require additional layers of security.
The primary physical security concern in generic work areas is suspicious behavior. These areas are often lightly monitored for the health and safety of employees and to ensure that employees are engaged in work activities.
These areas can also be targets for social engineers, as discussed in Chapter 8. Appropriate lighting, visible security personnel, and surveillance cameras are common ways to secure generic work areas.
Sensitive work areas are those areas where the general public is not allowed, and places the average employee may not have access to. The back office of a bank branch is a good example of a sensitive work area. The general public is restricted to the lobby area, while employees have access to the area behind the teller windows where cash is counted and stored.
In a bank branch, physical barriers are used to separate the public area—the lobby—from the sensitive work area. A reinforced counter topped with bulletproof glass generally acts as a barrier between the two areas. Security cameras, both hidden and overt, are placed to provide complete coverage of the entire area. Most bank branches have at least one uniformed security guard in attendance at all times.
Government facilities often have more stringent security requirements than private sector facilities. Federal facilities, and the security measures they require, are divided into five levels:
Level I—This facility has 10 or fewer employees, 2,500 or less square feet of office space, and little public contact.
Level II—This facility has 11 to 150 employees, 2,500 to 80,000 square feet of office space, and a moderate volume of public contact. Level II facilities are often located in shared office buildings with private sector businesses.
Level III—This facility has 151 to 450 employees, 80,000 to 150,000 square feet of office space, and a moderate to high level of public contact. These facilities are usually multi—story buildings and often contain several agencies or offices.
Level IV—This facility has more than 450 employees, 80,000 to 250,000 square feet of office space, and a high volume of public contact.
Level V—This facility is occupied by several agencies. Level V facilities require tenant agencies to secure the site according to their own needs, insofar as those needs exceed the security levels dictated by a Level IV facility.
These facilities have strict access control and physical security standards that include control of parking facilities, receiving and shipping procedures, employee and visitor identification, and training requirements.
Parking requirements at government facilities state that parking facilities should be restricted to government vehicles and personnel and that authorized parking spaces are assigned. Systems to tow unauthorized vehicles must be in place. Adequate lighting and closed-circuit television monitoring are also required to ensure the safety of employees and to deter illegal and threatening activities.
Shipping and receiving at government facilities is another area where physical security measures differ from most private sector facilities. All packages arriving at a classified government facility must be x-rayed and visually inspected to prevent attacks on government employees and facilities through the mail.
As with many secure private sector facilities, all employees at governmental facilities must display an agency-issued photo ID at all times. Visitors must wear a visitor identification badge, sign in with a receptionist or security guard, and be escorted at all times while within the facility.
Computer rooms and data centers are a specialized form of a sensitive work area. Access to these areas should be restricted to a few select individuals, and some data centers go one step further by going "dark." A dark data center is one that is monitored and managed remotely. Robotic devices in dark data centers perform tasks that normally require human intervention, such as cycling the power on a server or changing tapes in a backup system. Because human beings don't ordinarily work in a dark data center, the lights are usually off. This provides another layer of security. If the lights are on, or light from a flashlight shines through a window or across a video monitor, security personnel will most likely notice this suspicious activity.
Any data center, whether staffed or dark, should have access locks on all server racks and individual systems, as well as restrictions on electronic devices that can be brought into the data center. This prevents unauthorized data removal. Modern electronic devices, such as cell phones and universal serial bus (USB) keys, can hold a significant amount of data and are so small and ubiquitous that they often escape notice.
Port locks on servers and racks prevent intruders from downloading data to a portable device by restricting access to USB ports. Without access to these ports, it is impossible to physically connect a portable device to the server.
Computer rooms and data centers usually have strict policies against bringing in food or drink. Although these policies do prevent accidental spills that could damage sensitive equipment, they also minimize the need for custodial maintenance. If the server room rarely needs to be cleaned, custodial staff does not need regular access to that room. The fewer people who have access to a data center, the more secure it is.
Biometric access controls are those based on physical or behavioral traits. In Chapter 1, you learned that traditional access controls are based on three concepts:
What you know—A password or pass phrase
What you have—A smart card or token
What you are—Biometric traits
This section focuses on the last item, and breaks it down further into "what you are" and "what you do." The first concept deals with physical traits such as fingerprints and retinal patterns. The second covers behavioral traits such as typing speed and voice modulation.
Biometric systems are essentially sophisticated pattern recognition systems. They require a two-stage process:
Enrollment—The process of taking one or more sample readings from an individual in order to form an accurate image of that individual's traits. This data is stored in a database for later retrieval. Systems based on physical attributes may only require a single sample reading, whereas those based on behavioral traits often require a more significant enrollment period during which many readings are taken. This is done to ensure that the data stored on an individual is truly typical of that individual and not an anomaly.
Identification—The process of taking a reading on an individual and comparing it to the previously stored data on that individual.
During the identification process, an algorithm examines key match points in the live reading and compares them to the same match points on the stored sample.
There are many traits that a biometric system can analyze. They fall into two distinct categories, as mentioned above: physical characteristics and behavioral characteristics. In this section, you will learn more about the specific attributes that fall into each of these two broad categories.
Physiological biometric types are physical attributes that are unique to an individual. The accuracy of these traits can vary widely for identification and verification purposes. Some traits, such as fingerprints, are set at birth and do not change over an individual's lifetime. Others, such as facial recognition and hand geometry, can change significantly during childhood, but are relatively constant during adulthood.
Fingerprints are composed of two of characteristics:
Ridges—The raised layers of skin that form loops, whorls, and arches
Valleys—The depressed layers of skin between ridges
They are measured in two ways:
Minutiae matching—Matches specific points within the fingerprint ridge pattern. Minutiae that are considered for match points include ridge endings, spurs, and crossovers.
Pattern matching—Matches the overall characteristics of the fingerprints, rather than specific points. Pattern matching takes into account variations of characteristics such as ridge thickness, curvature, and density.
There are a variety of technologies used in fingerprint matching. The most common are optical, silicone, and ultrasound readers. They each capture data about the ridge characteristics of the fingerprint and recognize specific data points.
The retina is a membrane on the back of the eyeball that is sensitive to light. It contains a pattern of blood vessels that is unique to an individual, making it ideal for biometric identification and verification. During a retinal scan, users must remove their glasses, place their eyes close to the scanner, and stare at a specific point for 10 to 15 seconds. During this time, a low-intensity light is shone into the eye to illuminate the blood vessels on the retina. The retina is photographed and the pattern of blood vessels is compared to a known sample and analyzed.
The iris is the colored part of the eyeball. It has subtle patterns of rings, coronas, and furrows, and does not change throughout life. Iris scanning is often considered preferable to retinal scanning because glasses, contact lenses, and even eye surgery does not affect its accuracy.
Hand geometry is not as accurate as retinal or iris scanning, but many users consider it less intrusive. In this type of biometric scan, the user places his or her hand on a reader, which takes a series of measurements. It examines the length and width of the fingers, joints, and palm. It also may examine the ridge patterns on the palm.
Facial recognition involves measuring and analyzing key facial structures, including the distances between features such as the eyes, nose, cheekbones, jaw line, and mouth. A facial recognition system analyzes the size and proportion of these features and compares them with photographs taken at enrollment.
Behavioral biometrics take advantage of many characteristic behaviors that individuals exhibit consistently. Although you may not be aware of it, you follow certain rhythms when you type or write your signature. When you speak, you modulate your voice in specific ways that are unique to you. Behavioral biometrics analyze these behaviors to identify an individual.
Behavioral biometrics focus on actions that most people do automatically. You probably are not aware of your tempo when you type or the pressure you put on the pen when you write your signature. These are subconscious actions that are difficult to consciously change. Behavioral biometrics can be tricked by someone who takes the time to study a subject's behaviors and who learns to imitate them. They are best when used for lower security targets or when used in combination with another biometric or traditional access control method.
When individuals type, especially when they type words they are accustomed to typing frequently such as their username and password, they tend to develop rhythms that are idiosyncratic. Biometric software can be used to analyze the time each key is depressed, as well as the length of time between keystrokes. Although this type of biometric access control is easy to implement and most users do not consider it intrusive, it also has a high false negative rate. A false negative can be triggered if a user types standing up, for example, or has an injury that impacts his or her ability to type.
Signature analysis works in a similar way to typing tempo, by measuring the speed and pressure an individual uses to write the letters in his or her signature. It is generally well accepted by users who are already accustomed to signing their name on documents, contracts, and visitor logs.
It is difficult for an imposter to accurately mimic the way that a given individual writes. The end result—the actual written signature—can be easily faked, but the rhythms used to sign are much more difficult. This method suffers from the same issues as typing tempo: false negatives. If a user injures his dominant hand, he will not sign his name in his normal way until the injury has healed.
The human voice has two components: the vocal tract and the individual's accent. Accents are learned behaviors and are relatively easy to duplicate. The vocal tract is a physical attribute and is almost impossible to duplicate exactly. Even identical twins have slightly different vocal tracts. Voice recognition systems can recognize and differentiate between small variations in the spoken word by two individuals.
Typically, a voice recognition system uses an audio capture device, such as a microphone or telephone, to record an individual as she repeats random phrases. The system compares the recording to one made during the enrollment process.
Implementing a biometric access control system is more difficult than implementing a traditional access control system. User acceptance is one common barrier to biometric analysis. Many users who are unfamiliar with the technology find it intrusive or even frightening to undergo a retinal scan or face recognition. Many users have privacy concerns over the idea of their biometric data being stored.
User acceptance problems are not the only issue with implementing a biometric access control system. When choosing a biometric access control system, weigh the potential for false acceptances and rejections, crossover errors, and failures in the enrollment and capturing processes.
The false acceptance rate of any access control technology is the percentage of imposters that will be recognized as authorized users. A system with a high false acceptance rate may simply be calibrated with too low a sensitivity. In this instance, if the system has a record of a user with a blue iris, for example, any individual with blue eyes is recognized as the authorized user. In most cases, false acceptances are the result of a deliberate attempt to fool the system. False acceptances are often called Type II errors.
The false rejection rate is the percentage of attempts by legitimate users that are rejected by the system. This can happen when a user's behavior does not match the known sample. It can also happen when the sampling equipment is not calibrated properly, or if the user's physical features are obscured. For example, a fingerprint reader would produce a false rejection if the user's fingers were covered in dirt or grease, obscuring the characteristics of the fingerprint. False rejections are referred to as Type I errors.
The crossover error rate (CER) is the point at which Type I errors and Type II errors are equal, as shown in Figure 9-2. All biometric systems can be calibrated to reduce either the false acceptance or false rejection rates to near zero. Unfortunately, calibrating the system to reduce or eliminate Type I errors generally raises the rate of Type II errors. A biometric system could be calibrated such that the sensitivity is turned all the way down, so that it accepts everyone. Of course, this would produce a large number of false positives, but zero false negatives. Likewise, the sensitivity could be turned all the way up so that the system doesn't accept anyone, eliminating the false positives but producing a large number of false negatives. The CER is an accurate way to compare the real accuracy of various biometric systems. The smaller the CER, the more accurate it is. In other words, a system with a CER of 3 percent is more accurate than one with a CER of 5 percent.
All biometric systems require subjects to enroll, or present sample data, before they can use the system. As with any system, things do not always work the way they should and the sample data can be lost. The percentage of failed attempts to create a sample data set for an individual, divided by the total number of attempts to enroll users is called the failure to enroll rate.
Failure to capture, also referred to as failure to acquire, is the percentage of failed attempts to authenticate to the system. This number describes the failure of the system to acquire the necessary data from an individual to make an accept or reject decision. This is most often caused by a dirty or smudged scanning device or user error.
Biometric systems are used for two primary purposes: verification of an individual's stated identity and ascertaining the identity of an unknown user.
In verification mode, a biometric system makes a simple one-to-one comparison and returns a binary result. The individual presents a claim of identity—a token or user name, for example—and a biometric sample such as a fingerprint or retinal scan. The access control system simply retrieves the known user record for the claimed identity from a database, and then compares that to the sample data provided by the individual. If the two data sets match, the user is authenticated and the system returns a positive result. If the two data sets do not match, the system returns a negative result.
Note
Most biometric access control systems are used in verification mode.
In identification mode, the individual presents a sample data set such as a fingerprint, which the system analyzes. The system then searches the database of known users in an attempt to find a matching profile. Biometric systems are less effective in this mode because of the large number of matching user profiles that can be returned from a large database. For example, in a database of 750,000 records, a match rate of just 0.01 will return 7,500 records, which must be sorted through manually. Some systems can reduce the number of matches by cross referencing with other user data such as age, gender, and other characteristics, but it is very difficult to obtain an exact identity confirmation in this mode. Biometric systems in identification mode are most often used in law enforcement.
All biometric systems operate under some basic parameters, which you should be aware of when choosing and implementing a biometric access control system. Some types of biometric systems have advantages under one parameter but fall short under others. The right system to use depends upon the goals and users of the system. In a controlled environment where user education is possible, a system with some user acceptance issues can be considered because users can be trained and educated about the technology.
A biometric system must be based on a universal characteristic, or one that every individual will posses. A system that relies on signature analysis, for example, will not be effective in identifying very young children who cannot write.
The system must measure a characteristic that is not duplicated among users, such as a fingerprint or iris pattern. You are not likely to find a biometric access control system on the market that does not meet this requirement.
The characteristic measured by the system must be relatively permanent across the user base. Hand geometry and facial structure, for example, change significantly throughout childhood, but in adulthood is fairly permanent. Fingerprints, retinal, and iris patterns are determined before birth and do not change throughout an individual's lifetime, barring a disfiguring injury.
A biometric system must be able to collect sample data from an individual in an easy and reliable way. There are many unique, universal, and permanent characteristics that could be used for biometric access control that you will not find in use because data collection is too difficult or intrusive. DNA is a good example of this. It can be used to identify individuals very accurately, but collecting a DNA sample is impractical for the purposes of access control.
A biometric access control system must be able to return a positive or negative result quickly. Usually 5 to 10 seconds is the most an individual is willing to wait for access to needed resources. The system must be able to analyze the sample data and perform a database lookup extremely efficiently to avoid performance issues that will produce a bottleneck effect on an organization's operations. Think of the delays and long lines at airport security checkpoints. Most travelers accept these delays as unavoidable hassles inherent in the system, and because most do not have to deal with them every day, they do not object too strenuously. However, if those users faced a similar line just to get into work every morning, they would be less likely to accept the system.
User acceptance is a big hurdle to some biometric access control systems. This is often due to a lack of understanding of the technology by users and a concern over privacy. Users are more likely to accept a biometric system based on a technology they understand, such as fingerprinting or signature recognition, than one that is based on unfamiliar technology such as iris or retinal scanning.
Privacy concerns are usually based on worries over biometric data that is collected and stored during the enrollment process. Before implementing a biometric access control system, users must be assured that their biometric data will only be used for authentication purposes, and will be stored securely.
Most biometric systems are designed to prevent an individual from presenting a sample taken from another individual. For example, voice recognition systems will require the individual to repeat a random phrase to avoid the possibility of authenticating using a recording of another individual.
As with any access control system, there are legal and business issues to consider before implementing. Users' concerns over privacy and personal safety should be given sufficient consideration, as well as the overall cost of a biometric solution, and its efficiency and effectiveness as compared to a traditional access control system.
Privacy is a significant concern in any biometric access control solution because it involves deeply personal characteristics such as physical traits and subconscious behaviors. There are two types of biometric samples: those that are consciously given, and those that can be captured without the subject's knowledge.
Iris and retinal scans, for example, are nearly impossible to perform without the subject's knowledge and consent. Facial recognition, however, can be performed at a distance with a camera and a good telephoto lens. This presents a significant privacy concern because there is the potential for individuals to be enrolled and monitored without their knowledge or consent.
Biometric access controls tend to be significantly more expensive than traditional methods of access control such as a username and password. The technology involved is fairly new, and is more sophisticated than other methods. However, this cost is justified in some cases where accurate identity verification is crucial. Trigger locks on firearms are a good example. Biometric trigger locks that use a fingerprint scan are designed to ensure that only the owner of the gun is able to fire it. Biometric trigger locks are more expensive than typical combination style locks, but the risk that the gun will be stolen and used in a crime is significant enough to justify the additional expense.
The same argument holds up in other situations as well. Biometric access controls are frequently used in highly sensitive areas, such as classified military facilities. Adoption of biometric technology has been slower in less sensitive areas, including banking, where traditional access controls combined with emergency plans are sufficient to provide an acceptable level of access control.
For example, it makes sense to use biometrics to authorize credit card purchases. Only the owner of the credit card should be using it, and use by an unauthorized individual is a significant threat. Signature analysis would be a natural choice to implement a biometric component to existing access controls on the credit card, but that would require that every merchant who accepts credit cards purchase a special biometric signature pad, which would be costly. It would also be ineffective in preventing online credit card fraud, as no signature is required (or possible) for online purchases.
As noted in the credit card example above, cost of deployment is a significant inhibitor to widespread adoption of biometric access controls. In that example, every merchant who wanted to accept credit cards would have to obtain a signature capture device. The initial cost of the devices, as well as the cost of maintaining such a large number of devices at various locations, is significant.
Storage of biometric data is a significant part of any deployment project. The data, like any personally identifying information, must be stored as securely as possible to avoid potential identity theft or invasion of privacy. This is especially true where users have a strong concern over the privacy and safety of biometrics.
Database transmission and lookup must be optimized to avoid bottlenecks at the access control site. In most cases, the database lookup takes more time than the analysis algorithm. For very large databases, lookup of an individual record can take a significant amount of time. Given than most users are unwilling to spend more than a few seconds on any access control, the database must be optimized to minimize lookup time.
Database transmissions must be secured to avoid theft of data while in transit, and they must be optimized for speed and reliability. If the connection to the database goes down, the entire biometric system becomes inoperable. For this reason, the database server as well as the server that hosts the matching and analysis software should both be configured for high availability.
Law enforcement pioneered the use of biometrics with fingerprint identification. They maintain large databases of biometric information, including fingerprints and in some cases DNA, on individuals processed through the criminal justice system. Although most organizations use biometrics for authentication purposes, law enforcement agencies use biometric data primarily for identification. DNA matching has been used in many cases to prove conclusively that an individual was present at the crime scene. In other cases, DNA evidence has been used to prove that an individual—sometimes years after a conviction—could not have been the perpetrator of the crime.
The cost of DNA analysis has prevented it from being used as routinely as fingerprinting, but it has been proven extremely effective for identification purposes.
Users often cite theft of biometric components as a concern over the adoption of biometric access controls. In reality, most biometric systems are designed to prevent the use of stolen or faked biometric components. Hand geometry systems require the subject to move his or her fingers and test for hand temperature to avoid authenticating an artificial hand. Iris and retinal scanning devices also test for body temperature and movement. Voice recognition systems require users to repeat random phrases to prevent the use of pre-recorded voice samples.
However, the fact that biometric technologies are designed to prevent the use of stolen biometric components does not mean that this concern can be ignored. Users must be convinced that the biometric system is not dangerous before they willingly adopt it.
Hygiene is a far more realistic concern. There is the potential for spreading disease through fingerprint pads or other scanning devices that are touched by large numbers of individuals. However, this is no more risky than handling cash or touching a door handle—actions that most of us take many times a day without a second thought. Again, user training and education, coupled with the availability of hand sanitizer, will help assuage user concerns over hygiene.
There are many ways of identifying and authenticating users on a system. In this chapter, you have read about perimeter security and physical barriers to buildings and facilities. You have explored the realm of biometric access controls. In this section, you will read about other technologies that are designed to grant or prevent access to key areas or data.
The most common and widely used physical access control technology is the lock. There are a wide variety of locks, each with their own level of sophistication:
Warded locks—A typical padlock is a warded lock. It is the simplest of all mechanical locks. It consists of metal projections, or wards, in the locking chamber that match up to the grooves on the key. Once the key is inserted, it uses leverage to turn the bolt to the unlocked position. These locks are inexpensive, and are the easiest to pick. They are enough security to deter the curious, but not the determined thief.
Tumbler locks—These are more sophisticated than warded locks. They have a series of spring-loaded tumblers that are moved into alignment by the grooves on the key. Once all the tumblers are in position, the bolt can be slid into the unlocked position.
Combination locks—Combination locks, such as those used on high school lockers, provide a higher level of security than warded or tumbler locks. They work by aligning a series of wheels. When the dial is spun to the right and left in a specific sequence, the wheels are aligned and the lock will release. Electronic versions do not align a series of wheels, but rather act as a simple password system. When the user enters the combination on a keypad, it is checked against the stored password. If the two match, the lock is released.
Cipher locks—These locks are programmable and are the most sophisticated type of lock. Unlike previous styles, cipher locks can be programmed with many combinations, and can be combined with a swipe card or biometric identity verification system. This type of lock can also have added security features built in, such as a door delay alarm that triggers if the door is held open for another individual, or hostage alarms. To trigger a hostage alarm, an individual under duress would enter a panic code instead of his or her normal combination. The door will open, and the security guard or police will be notified that there is a problem at the location.
Mechanical locks are most commonly used to secure equipment such as laptops that are easy to steal. Combination and cipher locks are often used to secure sensitive areas within a facility, such as data centers.
In facilities with a large number of physical keys, keeping those keys securely can be a challenge. Electronic key management systems are locked boxes designed to control who has access to the keys, and keep a record of which keys are checked out and by whom. Typically, an EKMS has a keypad or smart card reader mounted near the lockbox. When an individual needs to check out a set of keys, he or she scans the smartcard or enters a combination on the keypad. If the credentials are acceptable, the lockbox opens and the user can remove a set of keys from a chamber. The EKMS logs the user ID, a timestamp, and which keys are removed from the lockbox. The system also logs when the keys are returned.
In situations where more sophisticated access controls are needed, challenge-response tokens on key fobs are useful. These are small devices that display a new code every minute. These codes are based on public key encryption, which you will learn about in Chapter 13. These key fob tokens are convenient for the user because of their small size. They often are designed to attach to a key ring, making them more difficult to lose than a loose device.
To access a secured facility, VPN, or other resource, the user is given a challenge. Typically, this is simply a request for a code. The user then uses the key fob device to generate a code, which they enter into the access control system. If the code is accepted, the user has the opportunity to enter a username and password, or some other authentication device. Challenge-response tokens are generally used in two-stage authentication schemes.
The Common Access Card is a smart card issued by the U.S. Department of Defense to military and civilian personnel and contractors. It is used as a single sign on for secured resources as well as an identification card for access to facilities. The CAC includes a magnetic stripe used in card readers for access to facilities, as well as a digital photograph for visual identification purposes and a microchip that stores a card holder unique identification (CHUID), personally identifying information and privilege data on the cardholder. CACs store basic identity verification data such as name and Social Security number, as well as two fingerprint biometrics.
Strong physical security requires that many disparate factors all work together—from landscape design to security guard training to programming and maintenance of biometric access controls. Rather than overseeing all these details in-house, many organizations choose to outsource. In this section, you will examine the benefits and potential risks of outsourcing physical security.
Outsourcing physical security can be beneficial, especially to small and mid-sized organizations that do not have the personnel or expertise to handle physical security in-house. A dedicated security firm will have the experience and expertise to know how to prevent many types of security breaches, and may be able to point out areas in your organization that are not as well protected as you thought.
A third-party security firm will also be able to be more impartial about security than an in-house team might. For example, security guards from a dedicated security firm are more likely to question every individual that enters a secured area, while a guard employed by the organization may be tempted to make exceptions for friends, coworkers, or upper executives. An external security auditor will also be able to see the organization's security situation with fresh eyes, while an internal security audit may overlook some areas simply because "that's the way we've always done it."
The major risk associated with outsourcing physical security is lack of control. Your organization has final responsibility for the security of facilities and resources, but the implementation details are handed off to a third party. If the outsourced security firm cuts corners or does not perform adequate background checks, your organization could be held liable for any damages caused by a security breach. To mitigate these risks, any organization considering outsourcing physical security should perform due diligence:
Conduct a thorough audit of your organization's security needs. Outsourcing vendors are likely to conduct their own audits as well, but you will be better able to choose vendors that can meet your organization's needs if you already have a good idea of what those needs are.
Conduct onsite audits of each vendor on your list of potential security partners. The best way to see how they will handle your security needs is to see how they are already securing their other clients.
Negotiate the details of staffing, background checks, equipment, and service level agreements (SLAs) to protect your organization. Be sure to include language describing the penalties for failure to prevent a security breach and procedures for handling a breach after the fact.
Remember, a third-party security firm can only implement your organization's policies. Outsourcing does not absolve your organization from its ultimate responsibility for securing facilities, resources, and data.
Outsourcing physical security can be beneficial, especially for small and mid-sized businesses, but there are risks associated with outsourcing. Conducting due diligence can mitigate many of those risks.
There are many best practices, depending on your organization's security needs. If your organization owns its own facility, landscaping and perimeter security will be a concern you will need to address. If your facility contains a data center or other highly sensitive areas, you will need to consider additional access control methods such as biometric identity verification and mechanical or programmatic locks.
The first step in ensuring physical security is to conduct a security audit. A security audit allows you to identify potential targets within your organization as well as any existing physical security risks. Some things to include in a physical security audit are:
Documentation of existing physical security measures, including perimeter security and access control systems.
Nonstandard entry points to the facility as a whole and to sensitive areas within the facility.
Standard access levels. For example, certain employees may have access to the data center, while other employees and external contractors do not.
Differences in security at various times, especially after hours.
Once existing physical security has been audited, any deficiencies or weaknesses can be dealt with. If outsourcing is an option, the organization can begin to evaluate vendors.
The best way to learn the real effects of physical security is to see them in action—both in their failures and successes. In this section, you will read about physical security measures that prevent both internal and external attacks.
Physical controls are important aspects of protecting data from both internal and external malicious users. Although attacks are a major reason that strong physical access controls are needed there are plenty of completely mundane actions that can disrupt an operation and endanger data integrity. Listed below are two incidents in the private sector where physical access controls solved major IT issues.
A new Midwestern biotech company, Acme Medical Technologies, had just expanded its offices, adding a server room to the main IT floor. This new sever room was designed to handle a high-availability Windows-based Web server that contained customer-facing Web sites. The area of the office that the server room was in had limited access. Only the networking and Web server teams in the IT department had access to the area. Because of the security in that section of the office, further physical access controls were not implemented on the server room.
An unusual issue started almost immediately. Every night around midnight, the Web servers went off line. The server configurations were verified, and when the logs where checked they showed that the servers had ungraceful shutdowns every night around the same time. To determine the root cause, the Web server administrator stayed late to see if anything physical was causing the outage.
That evening the server administrator watched as a janitor walked into the server room and proceeded to unplug the Web server from the uninterruptable power supply (UPS). He then proceeded to plug in his vacuum cleaner to vacuum the server room. The simple solution to this issue was to utilize the electronic keypad lock that had been installed on the server room, and explain to facilities management that their services were not needed in the server room.
Another example shows the need for physical security within the private sector. Agents for a major Midwestern insurance company have direct connections to the corporate mainframe systems via microcomputers at each agent's office. One office was having an intermittent connection issue. Approximately once a week, usually on Fridays, the system would crash. Due to the nature of the jobs that the system ran, it wasn't worth restarting the system until the next morning, so the agent was losing a few hours of productivity every week.
A technician was sent from IT to inspect the system. It was quickly determined that there were no hardware faults or heat issues that could be causing the problem. Oddly, the system refused to crash while the technician was onsite—the first week in months that it didn't fail at least once. After hearing this, the technician suggested installing a lock on the closet that the microcomputer was housed in. After the door was locked the server stopped crashing. It seems the staff enjoyed getting out early on the days that the server crashed and had been occasionally manually rebooting the system.
Primary schools and school districts face a number of issues when it comes to physical access control of their facilities. School districts must protect their students, staff, and school property. This must all be done while maintaining a friendly learning environment. Most districts have neither the ability nor the desire to hire full-time gate guards, but they must monitor the entry points to the schools to make sure no unauthorized adults enter, and that no unauthorized individuals leave with a child. A school must also be vigilant of student activities and be prepared to respond quickly to altercations among students. The school districts also have a secondary goal of preventing theft, vandalism, and graffiti. Let's take a look at how the Moss Point school district in Mossville, Mississippi handles these challenges.
Moss Point school district serves 3,100 students spread out between a high school, junior high, and six elementary schools. A few of the schools had VCR-based security cameras, but that solution had too many drawbacks. The images where grainy, making it hard to identify people. The systems could only be viewed onsite, and only after an incident occurred, which didn't allow the schools to identify and react to incidents as they happened.
This gave the school district two main requirements for a new system. It had to be centralized, and it must integrate with existing access controls, such as alarm systems. The solution was to implement an IP-based video surveillance network.
This network utilized over 200 digital video cameras all connected to a digital video recording (DVR) server connected to a central management system at the district office. Now, by looking at a single screen school officials can see the feed from all of their schools' cameras, and district security officials can monitor all of the schools from one location in real time. Before the fall semester of 2000, the school district installed cameras in the 10 facilities, most in hallways and on campus perimeters. Each camera is housed in a protective enclosure to prevent tampering. Eventually the school plans to have cameras in all of the classrooms as well.
The cameras allow officials to see what is happening in the schools when it is happening. This allows for a more proactive approach to safety and security. For example, the officials can detect signs that a fight may occur and defuse the situation before it starts. The cameras also act as a significant deterrent. Cases of vandalism and unsafe driving at the high school have dropped dramatically after the system was installed.
By adding digital video cameras to their physical access controls, the Moss Point schools were able to greatly enhance the safety and security of the learning environment that they provide to students.
Physical access controls in the case of critical infrastructure have a number of hurdles to cross. There are a lot of organizations that intermingle. If they do not share a common authentication method, controlling access becomes unwieldy. There is also a large volume of requestors needing access at any given time. A universal, secure, and quick method of identifying requestors and granting access is required. This is further complicated by various rules and regulations that critical facilities must adhere to. Below you will learn how U.S. port facilities handle these issues for maritime workers.
The Transportation Worker Identification Credential (TWIC) program is a joint program involving the Transportation Security Administration (TSA) and the U.S. Coast Guard (USCG) within the Department of Homeland Security (DHS). TWIC is intended to strengthen the security of U.S. maritime infrastructure through vetting of civilian maritime workers, and the issuance of tamper resistant, biometrically enabled identification credentials to workers. TWIC was developed in response to the regulations found in two legislative acts: the Maritime Transportation Security Act (MTSA) of 2002 and "the Security and Accountability for Every Port (SAFE Port) Act of 2006. TWIC is a massive program, with over 1 million workers issued a TWIC card. Possession of a TWIC card is required for unescorted access at over 3,000 land- and ocean-based facilities and over 10,000 vessels that are subject to MTSA regulations.
In the early stages of developing the TWIC card, the maritime industry expressed concerns about the proposed approach, which called for the TWIC card to be fully compliant with the Federal Information Processing Standards (FIPS) 201 standard. FIPS 201 allows access to biometric data on a smart card only through a contact interface, requiring insertion of the card into a contact interface slot on the card reader. The concern was that this standard was not appropriate for the high volume of physical access and rapid access operational requirement of the industry. There was also a concern that the extreme conditions at the port facilities would allow airborne contaminates into the readers causing delays and maintenance problems. FIPS 201 also required a pin to be entered to access the card, further slowing down the access process.
These concerns resulted in the TWIC Reader Hardware and Card Application Specification, published by the TSA. This specification implements an alternative authentication mechanism allowing for contactless reading of the biometric information stored on the card without requiring PIN entry. To protect personal privacy, the biometric data is stored on the card is encrypted. Decryption is accomplished through the use of a symmetric key called the TWIC Privacy Key (TPK), which is generated during card personalization by the TSA and is unique to each TWIC card. The TPK can only be accessed through the contact interface or through a swipe read of the magnetic stripe.
This approach to contactless biometric reading presented a unique challenge for the implementers. To decrypt the contactless biometric information the reader must first have a way to obtain the TPK. This can be achieved by having a one-time registration process that requires card contact, and then the TPK can be stored in a local server. An alternative method is to have a reader with both magnetic stripe and contactless smart card capabilities. In this scenario the cardholder would swipe the TWIC card before presenting the card to the contactless interface. It should also be noted that the TWIC card includes separate FIPS 201 compliant information, so a traditional PIN with contact biometrics reader can be utilized with the card.
Utilizing biometrics and IT to secure and simplify maritime and port access allowed TWIC to provide a more secure, reliable and quicker way to allow authorized access to our nation's critical infrastructures.
No one physical security method is the answer to an organization's access control needs. Many methods must work together to create a strong net of security. Perimeter security must be in place to deny an intruder access to the building, but if the intruder does get past the perimeter, there should be some other method of access control to protect the most sensitive areas of a facility.
The goal of any physical security plan, whether implemented in-house or outsourced, is to make access convenient for authorized users and as difficult as possible for intruders.
Bollards
Card holder unique identification (CHUID)
Crossover error rate (CER)
Failure to enroll rate
False acceptance rate
False rejection rate
Identification mode
Perimeter security
Service level agreement (SLA)
Type I error
Type II error
Uninterruptable power supply (UPS)
Verification mode
Ward
A good physical security strategy relies on a single strong point of access control.
True
False
Fencing, lighting, and security guards are all important parts of what aspect of physical security?
Outsourced security
Biometrics
Perimeter security
Access control
What is a weak point in perimeter security?
Road
Gate
Pathway
Window
Cameras trained on entry and exit points provide which security benefits? (Select two.)
Theft of resources prevention
A record of who enters and leaves the facility
Vandalism prevention
Allow guards to monitor activity in real time
What is a short vertical post designed to control traffic and prevent vehicular attacks on a building?
Balustrade
Barrier
Barm
Bollard
None of the above
Every package that arrives or leaves a classified government facility is x-rayed.
True
False
A(n)________data center has robotic devices that are controlled remotely to change backup tapes and cycle the power on servers.
What is the name of the process through which several biometric readings are taken on an individual in order to create an accurate record of the individual's characteristics?
Scanning
Identification
Verification
Enrollment
Creation
The two primary types of biometric access controls are________and________.
Anyone who can forge another person's signature can defeat a biometric access control based on signature analysis.
True
False
The crossover rate of a biometric system is________.
Most biometric access control systems are used in which mode?
Identification
Production
Elimination
Verification
Restrictive
Typical padlocks are an example of which type of locks?
Warded
Tumbler
Combination
Cipher
What is often equipped with silent alarms that notify security or police that an employee is in trouble?
Warded
Tumbler
Combination
Cipher
What is the first step in designing a physical security system?
Hire a security outsourcing firm.
Conduct a security audit.
Purchase a biometric access control system.
Install a video surveillance system.
Replace traditional locks with programmable cipher locks.