"Spoof" as a noun is defined in Microsoft Encarta 2002 as:
hoax: a good-humored hoax
amusing satire: a light amusing satire
The verb tense is defined like this:
deceive: to fool or deceive somebody
satirize: to satirize somebody or something good-naturedly
The term was originally coined by the English comedian Arthur Roberts in the late nineteenth century as the name for a game he created involving hoaxing. However, in the context of network security, spoofing does not involve good humor and good nature, and the definition that is closest to actual use in the context of network security would be to deceive. Spoofing attacks are frequently quite malevolent.
One of the earlier references to security spoofing can be found in an article in Phrack 11, "The Electronic Serial Number: a Cellular ’Sieve’? ’Spoofers’ Can Defraud Users and Carriers," which was originally published in November 1985 in Personal Communications Technology magazine. (You can find this article at http://www.phrack.org/show.php?p=11&a=9). In the article, the authors specify that spoofing is "usually with intent to defraud."
Although spoofing can refer to nearly any type of impersonation, the most common references in the network security arena are to IP spoofing, e-mail spoofing, and DNS spoofing. Let’s take a look at the various types of spoofing, how to test for the threats, and the associated countermeasures.
IP spoofing is forging the source address of an IP packet so that the packet appears to come from another source. It is also possible to forge other portions of the packet, such as the source port. You might question why an operating system would allow these packets to be created. Forged packets have legitimate uses; a number of security tools depend on them. For example, you cannot create a SYN flood tester without forging source addresses. There are many other examples of legitimate applications that depend upon creating arbitrary packets as well.
You can’t prevent a computer from emitting completely arbitrary packets on the network. First of all, the user with physical control over the computer can cause it to do nearly anything by modifying the operating system or even the hardware. To create your own tools that produce arbitrary packets, you use device drivers that allow you to emit any type of packet you like. By setting the IP_HDRINCL socket option, you can create most types of packets.
Although the IP_HDRINCL option (sometimes imprecisely cited as raw sockets) has been somewhat hysterically predicted to lead to the destruction of the Internet, anyone with a beginner’s grasp of the IP protocol can see that any system can emit packets from any source address. It’s really quite simple—a network interface can have multiple IP addresses assigned to it, and any application can bind to any interface and IP address it likes. This functionality must be supported to comply with the TCP/IP specification as well as the Winsock specification.
What can you do with spoofed packets? They are required to launch certain types of denial of service (DoS) attacks, such as SYN floods. A Smurf attack also uses spoofed ICMP echo request packets to cause large numbers of responses to be directed at the victim.
More Info
For more information about Smurf attacks, see Chapter 10, and Chapter 16.
It would be unusual to find a modern system that is both vulnerable to trivial TCP sequence number prediction and running a rsh service, though many of the older vulnerability assessment tools are capable of launching this attack. Be warned that this attack isn’t completely reliable, even under ideal circumstances. A tool that can’t compromise the remote host is little assurance that the system isn’t vulnerable. You’re better off just eliminating weak protocols like rsh from your network. If you find such a protocol running on an Internet-exposed system, disable the service and investigate whether the system was compromised. If you do require protocols with weak authentication, wrapping them in a tunneling protocol such as IPSec will mitigate the threat.
Another application-level spoofing attack involves the syslog service. Unlike TCP services, UDP services don’t have the barrier of sequence numbers to overcome. Although newer versions of syslog do allow for signed packets, older implementations just accept packets from any source. Forged packets sent to the syslog collector can cause the collector to suffer a denial of service, and if the hapless administrator configured the system to page themself when certain events occur, you could potentially take denial of service to a new level!
Because the root cause of IP spoofing is weakness in the underlying protocol, you can’t apply any patches to make the problem go away. One of your first strategies would be to reduce or eliminate services known to be vulnerable to IP spoofing, such as rsh, or unauthenticated versions of syslog.
You can also reduce the scope of the problem by applying ingress and egress filters at your routers that validate network traffic. Because systems vary, you need to consult your router documentation to determine the steps you need to take. In general, you need rules that drop packets originating from the outside that claim to originate from the inside. Next, you need to drop packets from the inside claiming to originate from external networks. If possible, log an alert on spoofed packets originating from your network, as shown in Figure 20-1, because the machine is either compromised or belongs to a mischievous user.
Several problems are immediately apparent with this approach. First, you need to know all your internal networks. Unless you have a really simple network, knowing all the IP ranges assigned behind your outermost routers might be difficult, and if your network is very large, the internal network ranges could change often and your router rules will have to reflect the changes. The second problem is one of performance—the more traffic you have moving through a router, the fewer rules you will want in place, or you’ll end up buying more (or larger) routers to handle the load. The best way to overcome these issues is to simplify configuration by applying your rules at as low a level as possible. Not only does ingress and egress filtering help secure your network, it also helps prevent your network from being used to attack others.
Filtering cannot help when packets do not cross routers. The only way to mitigate this problem is by implementing IPSec on your network so that all network traffic between your managed systems is authenticated. Strong authentication relies on being able to see the replies a system makes, so IPSec can nearly completely eliminate IP spoofing threats.
As mentioned earlier, the root cause of spoofing is weakly authenticated systems. One weakly authenticated system is the e-mail system. Let’s take a look at what happens when a client sends e-mail to a basic SMTP server:
220-mail.example.net ESMTP Exim 3.33 #1 Sun, 22 Feb 2004 22:01:30 -0500 220-NO UCE. Example.net does not authorize the use of its computers or network 220 equipment to deliver, accept, transmit, or distribute unsolicited e-mail. HELO mycomputer 250 mail.example.net Hello [my dial-up IP] MAIL FROM:[email protected] 250 <[email protected]> is syntactically correct RCPT TO:[email protected] 250 <[email protected]> is syntactically correct DATA 354 Enter message, ending with "." on a line by itself Wow, I can spoof mail. Isn't this easy? . 250 OK id=1Av6Mx-000584-00 QUIT 221 mail.example.net closing connection
In this transaction, the remote system first asks for a machine name. You can tell it anything you want, and it will believe you. It will then echo back your actual IP address and the DNS name that your IP address resolves to. If you’re going through a proxy server, it knows only about the IP address of your proxy. Next, the system wants to know who the e-mail is from—again, you can tell it anything you like, and it has little choice other than to believe you. You could have claimed to be someone else or even someone who doesn’t exist. Check your inbox and you will find:
Status: U Return-Path: <[email protected]> Received: from mail.example.net ([192.168.200.57]) by mail2.example.net with ESMTP id 1aV6ndyS3Nl3pK0 for <[email protected]>; Sun, 22 Feb 2004 22:03:11 -0500 (EST) Received: from [my dial-up IP] helo=mycomputer) by mail.example.net with smtp (Exim 3.33 #1) id 1Av6Mx-000584-00 for [email protected]; Sun, 22 Feb 2004 22:03:06 -0500 Message-Id: <E1Av6Mx-000584-00@ mail.example.net> From: [email protected] Date: Sun, 22 Feb 2004 22:03:06 -0500 Wow, I can spoof mail. Isn't this easy?
E-mail spoofing isn’t typically part of a penetration test (unless you incorporate it into a social engineering attack by sending mail to one administrator who claims to be another). You should, however, test for open relay systems. You can do this by sending mail to an external domain or SMTP server by connecting directly to one of your mail servers. If the mail arrives at the external system, you found an open relay. This is a better test than attempting to send the mail and looking for responses from the SMTP server, because some SMTP servers give erroneous results, sometimes in an effort to redirect spam to a black hole. The proof is whether the mail arrives.
More Info
Chapter 25, looks at how attackers leverage e-mail spoofing to conduct attacks over e-mail and send spam.
On an internal network, you can make spoofing e-mail more difficult by requiring outgoing e-mail to be authenticated. Requiring authentication for internal mail can be done fairly easily by using Microsoft Exchange Server; many other mail servers will support some form of authentication as well. Unless your internal network is fairly complicated, you can also perform ingress filtering on SMTP messages—any mail that claims to originate from your internal network but arrives at your external gateway from the outside is almost certainly spoofed.
The most certain way to mitigate the risk of e-mail spoofing is to digitally sign all your messages. However, signed e-mail can be cumbersome and increases the amount of storage you need for your users.
Various companies and organizations are coming up with a number of plans to reduce (and we hope eliminate) spam by authenticating e-mail. With any luck, this section of the book will be obsolete in the near future.
The only way to validate where an e-mail truly originates from is by looking at the SMTP headers. The problem is made worse by bugs in some SMTP servers that end up truncating the information in the "Received: from" portions of the header. Unfortunately, once you do trace the e-mail back, you’re likely to find that it actually originates from a compromised system. For additional information, CERT has a summary at http://www.cert.org/tech_tips/email_spoofing.html.
There are several ways to corrupt DNS information, and although they don’t all involve spoofing, they all result in spoofing. The basic attack involves convincing your system that the server you want to connect to is a server that is under the attacker’s control. When DNS spoofing is successful, the attacker can steal credentials, tamper with data, and engage in a number of additional attacks. DNS spoofing is a particularly effective threat because software developers all too often view man-in-the-middle (MITM) attacks as being difficult to pull off. The countermeasures that protect from MITM attacks can be difficult to implement. The combination of an attack that isn’t well understood with lots of hard work often results in applications that are vulnerable to evil server attacks. To be fair, DNS spoofing attacks are difficult to pull off in many cases. Let’s take a look at how these attacks work.
More Info
For more information about MITM attacks, see Chapter 21.
One attack target is the client. This occurs when a client resolves a DNS name to an IP address, binds to either port 53 or a random high port, and sends a packet to the DNS server. The packet has a sequence number to help ensure that different applications get the right responses. For an attacker to corrupt the result, the attacker needs to do only a few things.
First, the attacker needs to guess the source port. This isn’t as hard as it seems because it normally ranges from 1024 through 5000 (depending on the operating system). Also, ports typically start at the bottom and work up. If there is some way to provoke the client into sending you a packet, the attacker can target a small range of ports (it takes only one to match, and you have a winner). There’s no penalty for wrong guesses unless the victim is running an intrusion detection system. If the client is an older system that always sends requests from port 53, no guessing is involved.
Second, the attacker must guess the sequence number. Some older operating systems make that easy by not using a random number for the sequence number, which is only 16 bits. If the system is using a random high port, and the sequence number is random, this can be a difficult attack to pull off. The attacker also needs to provoke the client into sending a request.
A much more direct variant of this attack is launched locally, as shown in Figure 20-2. Many switches can be tricked into diverting another system’s traffic, and if the attacker can see another system’s requests, the attack becomes a race condition—one the attacker often wins because he’ll get the packets first.
In practice, you rarely need to resort to such complicated attacks. Most networks have a lot of targets. As an administrator, your major concern is updating older operating systems that make this attack easy.
Another approach is to attack the DNS server itself. A DNS server acting as a forwarder is then a client to other DNS servers, and the same attack explained earlier can be launched. An alternate way to attack the DNS server is enabled because the DNS specification allows more than one response to be placed into a reply.
First, you set up an attacking DNS server on a system you control. As you might imagine, this requires having a DNS name that can be resolved, so there’s considerable setup work before you can begin this attack. You then send to the DNS server you’re attacking a resolution request for the domain served by your evil DNS server. The corrupted DNS server replies with not only the record that was requested, but also another record for the system you want to spoof that claims to be authoritative. Unless the DNS server being attacked is configured properly, it accepts both records, and all clients being served are sent to the wrong system.
Unlike a good penetration tester, the real attackers out there are not going to worry about operational concerns and will find a DNS server somewhere on the Internet that they can compromise and cause to deliver corrupted responses. If you want to test this attack, getting your DNS admins to assist by sending requests directly to your attack server can make the setup less complicated. Fortunately, most recent versions of BIND and Microsoft’s DNS server since at least Windows 2000 do deny piggybacked responses by default (Figure 20-3).
A third attack approach targets when a server allows updates. To work properly with DHCP, DNS servers need to know when new clients are registered. Servers can be configured to allow only secure updates, to accept secure and insecure updates, and to not allow updates at all. Updating behavior can be set at the zone level, so you need to check every zone. Unlike other attacks, you can test for this fairly easily by sending an update for a zone that the DNS server is authoritative for. For example, add an alias to your own system and then try to resolve the alias. If the resolution works, you found a vulnerable server. Insecure updates can be a serious problem because the specification also allows records to be removed.
Tip
Regarding updating name resolution services, be aware that WINS is not secure and is inherently vulnerable to this type of attack. Never use WINS exposed to the Internet. It can be challenging to reconfigure a network to use DNS exclusively, but if security is important on your internal network, work toward doing this.
A final attack on DNS is to convince your name registering company that they should accept updates from you as an attacker. One large name registry allows three methods to secure updates. In the least secure scenario, updating mail must come from a certain e-mail address. As previously discussed, this obstacle isn’t terribly difficult to overcome. The next most secure scenario is to send a clear-text password in the e-mail requesting the update. As you might well imagine, this is only a slight improvement over the least secure option. Lastly, the name registry can require a certain PGP key to sign the e-mail. Name registries have been known to enter false records based on faxes as well. Because of the potential for great disruption, it’s best to verify this attack through talking with the name registry. Hopefully, better methods will be available by the time you read this.
More Info
For more information on the name registry issue and an excellent overview of DNS attacks of all kinds, see the "DNS Spoofing (Malicious Cache Poisoning)" article by Doug Sax at http://www.giac.org/practical/gsec/Doug_Sax_GSEC.pdf.
One of the first issues to consider is whether you have anti-spoofing rules set on your routers. If you do, packet reply spoofing will be restricted to local systems. If you want to protect against purely local network attacks, take the same countermeasures you would to protect against IP spoofing, and if you have a high security environment, securing your network switches can help. Second, run newer versions of the operating systems. The problem with non-random sequence numbers has been known for some time, and Windows 2000 and later also use dynamically allocated ports to send requests.
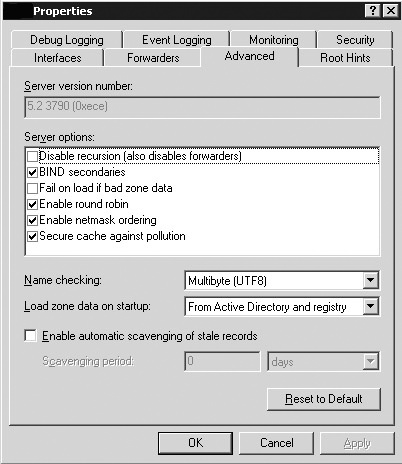
To prevent overloaded reply attacks, run a recent version of your DNS server. If you’re running Microsoft’s DNS server, verify that the Secure Cache Against Pollution setting is enabled, as shown in Figure 20-4.
To protect against update attacks, you can configure updates zone by zone on a Windows DNS server by right-clicking a zone, choosing Properties, and then choosing the General tab, as shown in Figure 20-5.
Note that you should check the update configuration for every zone, and consider that some zones should not allow any updates. For example, Internet-facing systems should probably be updated manually, and Internet-facing DNS servers should not allow updates at all.
You can help prevent name registry attacks by working with your registry company to determine the most secure methods of updating your information, and also by using the highest security possible. It is up to you to ensure that the most secure mechanism is chosen.