Chapter 2. About Industrial Networks
Information in this Chapter:
• Industrial Networks and Critical Infrastructure
• Relevant Standards and Organizations
• Common Industrial Security Recommendations
• The Use of Terminology Within This Book
Before attempting to secure an industrial network, it is important to understand what an industrial network really is. Because of the diversity of both the industrial networks themselves as well as the markets that they serve, it can be confusing to discuss them in general terms. In addition, the many regulatory agencies and commissions that have been formed to help secure different industrial networks for different markets each introduce their own specific nomenclatures and terminology. Finally, the common misuse of terminology within the media further confuses the issue of what an industrial network truly is.
Industrial Networks and Critical Infrastructure
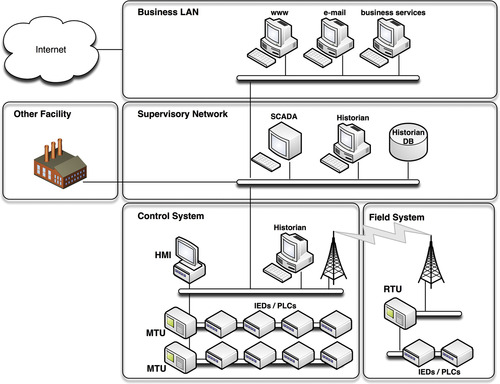
The world of industrial control systems, like many high-tech sectors, possesses its own lexicon to describe the nuances of its industry. Unfortunately, the terms used are also often interchanged and misunderstood. Industrial Control Systems are often referred to in the media as “SCADA,” for example, which is both inaccurate and misleading. An industrial network is most typically made up of several distinct areas, which are simplified here as a business network or enterprise, business operations, a supervisory network, and process and control networks (see Figure 2.1). SCADA, or Supervisory Control and Data Acquisition, is just one specific piece of an industrial network, separate from the control systems themselves, which should be referred to as Industrial Control Systems (ICS), Distributed Control Systems (DCS), or Process Control Systems (PCS). Each area has its own physical and logical security considerations, and each has its own policies and concerns.
The book title “Industrial Network Security: Securing Critical Infrastructure Networks for Smart Grid, SCADA, and Other Industrial Control Systems” was chosen because this text discusses the security concerns of all the networks that make up an industrial network, including the supervisory and distributed control systems, primarily as they apply to critical infrastructure. The business Local Area Network (LAN), the process control network, and whatever supervisory demilitarized zone (DMZ) exists between them are all equally important. To be more specific, it discusses the cyber security of these networks. For the sake of clarity, it is assumed that a strong security policy, security awareness, personnel, and physical security practices are already in place, and these topics will not be addressed except for where they might be used to strengthen specific areas of network security.
Critical Infrastructure
For the purposes of this book, the terms “Industrial Network” and “Critical Infrastructure” are used in somewhat limited contexts. “Industrial Network” is referring to any network operating some sort of automated control system that communicates digitally over a network, and “Critical Infrastructure” is referring to critical network infrastructure, including any network used in the direct operation of any system upon which one of the defined “critical infrastructures” depends. Confusing? It is, and this is perhaps one of the leading reasons that our critical infrastructures remain at risk today: many an ICS security seminar has digressed into an argument over semantics, at the sake of any real discussion on network security practices.
Luckily, the two terms are closely related in that the defined critical infrastructure, meaning those systems listed in the Homeland Security Presidential Directive Seven (HSPD-7), typically utilizes some sort of industrial control systems. In its own words, “HSPD-7 establishes a national policy for Federal departments and agencies to identify and prioritize [the] United States critical infrastructure and key resources and to protect them from terrorist attacks.” HSPD-7 includes public safety, bulk electric energy, nuclear energy, chemical manufacturing, agricultural and pharmaceutical manufacturing and distribution, and even aspects of banking and finance: basically, anything whose disruption could impact a nation. 1 However, while some, such as global banking and finance, are considered a part of our critical infrastructure, they do not typically operate industrial control networks, and so are not addressed within this book (although many of the security recommendations will still apply, at least at a high level).
1.Department of Homeland Security, Homeland security presidential directive 7: critical infrastructure identification, prioritization, and protection. < http://www.dhs.gov/xabout/laws/gc_1214597989952.shtm>, September, 2008 (cited: November 1, 2010).
Utilities
Utilities—water, gas, oil, electricity, and communications—are critical infrastructures that rely heavily on industrial networks and automated control systems. Because the disruption of any of these systems could impact our society and our safety, they are listed as critical by HSPD-7; because they use automated and distributed process control systems, they are clear examples of industrial networks. Of the common utilities, electricity is often separated as requiring more extensive security. In the United States and Canada, it is specifically regulated to standards of reliability and cyber security. Oil and gas refining and distribution are systems that should be treated as both a chemical/hazardous material and as a critical component of our infrastructures. It is often regulated as a chemical facility because of these particular qualities.
Nuclear Facilities
Nuclear facilities represent unique safety and security challenges due to their inherent danger in the fueling and operation, as well as the national security implications of the raw materials used. This makes nuclear facilities a prime target for cyber attack, and it makes the consequences of a successful attack more severe. As such, nuclear energy is heavily regulated in the United States by the Nuclear Regulatory Commission (NRC). The NRC was formed as an independent agency by Congress in 1974 in an attempt to guarantee the safe operation of nuclear facilities and to protect people and the environment. This includes regulating the use of nuclear material including by-product, source, and special nuclear materials, as well as nuclear power. 2
2.U.S. Nuclear Regulatory Commission, The NRC: who we are and what we do. < http://www.nrc.gov/about-nrc.html> (cited: November 1, 2010).
Bulk Electric
The ability to generate and distribute electricity in bulk is highly regulated. Electrical energy generation and distribution is defined as a critical infrastructure under HSPD-7, and is heavily regulated in North America by NERC—specifically via the NERC Critical Infrastructure Protection (CIP) reliability standards—under the authority of the Department of Energy, which is ultimately responsible for the security of the production, manufacture, refining, distribution, and storage of oil, gas, and non-nuclear power. 3
3.Department of Homeland Security, Homeland security presidential directive/HSPD-7. Roles and responsibilities of sector-specific federal agencies (18)(d). < http://www.dhs.gov/xabout/laws/gc_1214597989952.shtm>, September 2008 (cited: November 1, 2010).
It’s important to note that energy generation and distribution are two distinct industrial network environments, each with its own nuances and special security requirements. Energy generation is primarily concerned with the safe manufacture of a product (electricity), while energy distribution is concerned with the safe and balanced distribution of that product. The two are also highly interconnected, obviously, as generation facilities directly feed the power grid that distributes that energy; bulk energy must be carefully measured and distributed upon production. For this same reason, the trading and transfer of power between power companies is an important facet of an electric utility’s operation.
The smart grid—an update to traditional electrical transmission and distribution systems to accommodate digital communications for metering and intelligent delivery of electricity—is a unique facet of industrial networks that is specific to the energy industry that raises many new security questions and concerns.
Although energy generation and distribution are not the only industrial systems that need to be defended, they are often used as examples within this book. This is because the North American Electric Reliability Corporation (NERC) has created a reliability standard called “Critical Infrastructure Protection” and enforces it heavily throughout the United States and Canada. Likewise, the NRC requires and enforces the cyber security of nuclear power facilities. Ultimately, all other industries rely upon energy to operate, and so the security of the energy infrastructure (and the development of the smart grid) impacts everything else, so that talking about securing industrial networks without talking about energy is practically impossible.
Is bulk power more important than other industrial systems? That is a topic of heavy debate. Within the context of this book, we assume that all control systems are important, whether or not they generate or distribute energy, or whether they are defined that way by HSPD-7 or any other directive. A speaker at the 2010 Black Hat conference suggested that ICS security is overhyped, because these systems are more likely to impact the production of cookies than they are to impact our national infrastructure. 4 However, even the production of a snack food can impact many lives: through the manipulation of its ingredients or through financial impact to the producer and its workers, for example.
4.J. Arlen, SCADA and ICS for security experts: how to avoid cyberdouchery. in: Proc. 2010 BlackHat Technical Conference, July 2010.
Chemical Facilities
Chemical manufacture and distribution represent specific challenges to securing an industrial manufacturing network. Unlike the “utility” networks (electric, nuclear, water, gas), chemical facilities need to secure their intellectual property as much as they do their control systems and manufacturing operations. This is because the product itself has a tangible value, both financially and as a weapon. For example, the formula for a new pharmaceutical could be worth a large sum of money on the black market. The disruption of the production of that pharmaceutical could be used as a social attack against a country or nation, by impacting the ability to produce a specific vaccine or antibody. Likewise, the theft of hazardous chemicals can be used directly as weapons or to fuel illegal chemical weapons research or manufacture. For this reason, chemical facilities need to also focus on securing the storage and transportation of the end product.
Critical versus Noncritical Industrial Networks
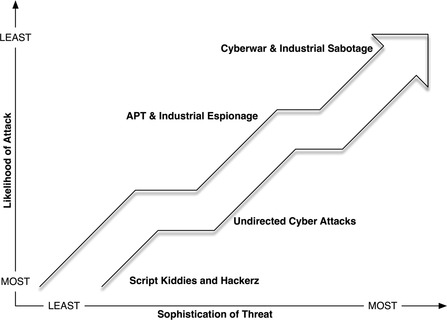
The security practices recommended within this book aim for a very high standard, and in fact go above and beyond what is recommended by many government and regulatory groups. So which practices are really necessary, and which are excessive? It depends upon the nature of the industrial system being protected. What are the consequences of a cyber attack? The production of energy is much more important in modern society than the production of a Frisbee. The proper manufacture and distribution of electricity can directly impact our safety by providing heat in winter or by powering our irrigation pumps during a drought. The proper manufacture and distribution of chemicals can mean the difference between the availability of flu vaccines and pharmaceuticals and a direct health risk to the population. Regardless of an ICS’s classification, however, most industrial control systems are by their nature important, and any risk to their reliability holds industrial-scale consequences. However, while not all manufacturing systems hold life-and-death consequences, that doesn’t mean that they aren’t potential targets for a cyber attack. What are the chances that an extremely sophisticated, targeted attack will actually occur? The likelihood of an incident diminishes as the sophistication of the attack—and its consequences—grow, as shown in Figure 2.2. By implementing security practices to address these uncommon and unlikely attacks, there is a greater possibility of avoiding the devastating consequences that correspond to them.
Although the goal of this book is to secure any industrial network, it focuses on Critical Infrastructure and electric energy in particular, and will reference various standards, recommendations, and directives as appropriate. Regardless of the nature of the control system that needs to be secured, it is important to understand these directives, especially NERC CIP, Chemical Facility Anti-Terrorism Standards (CFATS), Federal Information Security Management Act (FISMA), and the control system security recommendations of National Institute of Standards and Technology (NIST). Each has its own strengths and weaknesses, but all provide a good baseline of best practices for industrial network security (each is explored in more detail in Chapter 10, “Standards and Regulations”). Not surprisingly, the industrial networks that control critical infrastructures demand the strongest controls and regulations around security and reliability, and as such there are numerous organizations helping to achieve just that. The Critical Infrastructure Protection Act of 2001 and HSPD-7 define what they are, while others—such as NERC CIP, CFATS, and various publications of NIST—help explain what to do.
Relevant Standards and Organizations
Many organizations are attempting to define methods of securing our industrial systems. Some are regional, some are national, and some are global. Some are public, some are private. Some—like NERC CIP—carry heavy fines for non-compliance if one falls under their jurisdiction. Others—such as CFATS—offer recommendations for self-assessment and lack the ability to levy penalties for noncompliance.
Each standard is discussed briefly here and in more detail in Chapter 10, “Standards and Regulations.” Although this book does not attempt to provide compliance or audit guidelines, the various standards provide valuable insight into how we should and should not be securing our industrial networks. When considered as a whole, we see common requirement challenges and recommendations that can and should be considered “best practices” for industrial network security.
Homeland Security Presidential DirectiveSeven/HSPD-7
The HSPD-7 attempts to distinguish the critical versus noncritical systems. HSPD-7 does not include specific security recommendations, relying instead upon other federal security recommendations such as those by the NIST on the security of both enterprise and industrial networks, as well as the Homeland Security Risk-Based Performance Standards used in securing chemical facilities.
Which regulations apply to your specific industrial network? Possibly several, and possibly none. Although more information is provided in Chapter 10, “Standards and Regulations,” some of the more common regulations are summarized here in order to help you determine which standards you should be striving to meet.
NIST Special Publications (800 Series)
NIST’s 800 series documents provide best practices and information of general interest to information security. All 800 series documents concern information security and should be used as references where applicable. Of particular relevance to industrial network security is SP 800-53 (“Recommended Security Controls for Federal Information Systems”), which defines many aspects of information security procedures and technologies, and SP 800-82 (“Guide to Supervisory Control and Data Acquisition [SCADA] and Industrial Control Systems Security”), which discusses industrial control system security specifically. Although of the entire SP 800-53 is applicable to the protection of critical infrastructures, the technical aspects defined under SP 800-53 as Access Control, Security Assessment and Authorization, Configuration Management, Identification and Authentication, Risk Assessment, System and Communications Protection, and System and Information Integrity are directly applicable to industrial networks. 5
5.National Institute of Standards and Technology, Special Publication 800-53 Revision 3. Recommended Security Controls for Federal Information Systems and Organizations, August 2009, Computer Security Division, Information Technology Laboratory, National Institute of Standards and Technology, Gaithersburg, MD 20899-8930.
SP 800-82 (currently in draft) details control system architectures, protocols, vulnerabilities, and security controls. Specific security recommendations of SP 800-53 and SP 800-82 are addressed in more detail in Chapter 10, “Standards and Regulations.”
NERC CIP
The NERC CIP reliability standard identifies security measures for protecting critical infrastructure with the goal of ensuring the reliability of the bulk power system. Compliance is mandatory for any power generation facility, and fines for noncompliance can be steep. The CIP reliability standards consist of nine sections, each with its own requirements and measures. They are Sabotage Reporting, Critical Cyber Asset Identification, Security Management Controls, Personnel & Training, Electronic Security Perimeter(s), Physical Security of Critical Cyber Assets, Systems Security Management, Incident Reporting and Response Planning, and Recovery Plans for Critical Cyber Assets.
Nuclear Regulatory Commission
The NRC is responsible for ensuring the safe use of radioactive materials for beneficial civilian (nonmilitary) purposes by licensed nuclear facilities. Part of this responsibility is the establishment of cyber security requirements and recommendations, which are defined primarily within two documents: Title 10 Code of Federal Regulations (CFR), section 73.54 (10 CFR 73.54), and Office of Nuclear Regulatory Research’s Regulatory Guide 5.71 (RG 5.71), which explains in detail the specific cyber security requirements of 10 CFR 73.54. RG 5.71 provides recommendations to nuclear agencies or “licensees” in how to secure their facilities against cyber attack. These recommendations indicate that a licensee “shall protect digital computer and communication systems and networks associated with safety, security, emergency preparedness, and any systems that support safety, security and emergency preparedness”6 and that they shall protect the systems and networks that impact the integrity or confidentiality of data and/or software; deny access to systems, services, and/or data; and prevent any activity that might adversely impact the operation of systems, networks, and associated equipment. 7
6.U.S. Nuclear Regulatory Commission, Regulatory Guide 5.71 (New Regulatory Guide) Cyber Security Programs for Nuclear Facilities, January 2010, U.S. Nuclear Regulatory Commission, Washington, DC.
7.Ibid.
To accomplish this, RG 5.71 makes recommendations in how to identify critical digital assets, as well as how to implement a defense in depth strategy to mitigate the adverse effects of a cyber attack against those critical assets, all to “ultimately ensure that the functions of protected assets are not adversely impacted due to cyber attacks.”8
8.Ibid.
Important components of RG 5.71 include9
9.Ibid.
• Analyzing Digital Computer Systems and Networks (C.3.1)
• Identification of Critical Digital Assets (C.3.1.3)
• Defense-in-Depth Protective Strategies (C.3.2)
• Security Defensive Architecture (C.3.2.1)
• Establishing Security Controls (C.3.3)
• Technical Controls (C.3.3.10), including
• Access Control (C.3.3.1.1)
• Audit and Accountability (C.3.3.1.2)
• System and Communications Protection (C.3.3.1.3)
• Identification and Authentication (C.3.3.1.4)
• System Hardening (C.3.3.1.5)
• Operational Controls (C3.3.2), including
• Media Protection (C.3.3.2.1)
• System and Information Integrity (C.3.3.2.3)
• Incident Response (C.3.3.2.6)
• Continuous Monitoring and Assessment (C.4.1)
• Vulnerability Scans and Assessments (C.4.1.3)
• Change Control (C.4.2)
• Configuration Management (C.3.3.2.9 and C.4.2.1)
In addition, Appendix B of RG 5.71 is exceptionally useful, as it provides in depth detail on recommended security technical controls, of which the following apply directly to network security: 10
10.Ibid.
• Access Controls (B.1), including
• Access Control Policy and Procedures (B.1.1)
• Account Management (B.1.2)
• Access Enforcement (B.1.3)
• Information Flow Enforcement (B.1.4)
• Network Access Control (B.1.15)
• “Open/Insecure” Protocol Restrictions (B.1.16)
• Wireless Access Restrictions (B.1.17)
• Insecure and Rogue Connections (B.1.18)
• Proprietary Protocol Visibility (B.1.20)
• Audit and Accountability (B.2)
• Critical Digital Asset and Communications Protection (B.3), including
• Application Partitioning and Security Function Isolation (B.3.2)
• Transmission Integrity (B.3.6)
• Use of Cryptography (B.3.10)
• Session Authenticity (B.3.18)
• Confidentiality of Information at Rest (B.3.20)
• Identification and Authentication (B.4)
• Removal of Unnecessary Services and Programs (B.5.1)
• Host Intrusion Detection System (B.5.2)
For the most part, the NRC’s guidelines are consistent with NIST recommendations. The NRC classifies the criticality of an asset or system based on the risks to operations and safety that could result from its compromise. A severity level (SL) is assigned to a cyber asset or mechanism, and the recommendations for cyber security vary based on the assigned SL. There are five SLs, Severity Level 0 to Severity Level 4. One unique recommendation made by the NRC for the protection of nuclear facilities is the use of unidirectional access to the most critical systems, indicated by a severity level of 4—which may be accomplished using a data diode or a physical air gap—represents one of the most stringent cyber security practices recommended by any of the regulatory agencies mentioned within this book. The specific recommendation to validate sessions and monitor access to proprietary protocols is also more stringent than the requirements of other regulations—both of which are important considerations when attempting to secure industrial networks, which often use proprietary protocols and/or specialized standard protocols that may or may not include session authentication or validation. Unfortunately, RG 5.71 is purely a recommendation for complying with the broader requirements provided in 10 CFR 73.54 and is not an enforceable standard at this time.
Federal Information Security Management Act
The FISMA may or may not apply to certain critical infrastructures, depending upon their geographic location and/or their jurisdiction within the United States federal government. However, the standards include valid and useful guidelines for the security of critical environments, referring to and relying upon the NIST “800 series” Special Publication documents (especially SP 800-53 and SP 800-82). The management controls of SP 800-53 are divided into 18 security categories: 11
11.National Institute of Standards and Technology, Special Publication 800-53 Revision 3. Recommended Security Controls for Federal Information Systems and Organizations, August 2009, Computer Security Division, Information Technology Laboratory, National Institute of Standards and Technology, Gaithersburg, MD.
• Access Control (AC)
• Audit and Accountability (AU)
• Security Assessment and Authorization (CA)
• Configuration Management (CM)
• Contingency Planning (CP)
• Identification and Authentication (IA)
• Incident Response (IR)
• Maintenance (MA)
• Media Protection (MP)
• Physical and Environmental Protection (PE)
• Planning (PL)
• Personnel Security (PS)
• Risk Assessment (RA)
• System and Services Acquisition (SA)
• System and Communication Protection (SC)
• System and Information Integrity (SI)
• Program Management (PM)
While all of these controls relate to cyber security, the areas that relate most directly to network security practices are Access Control (AC), Audit and Accountability (AU), Configuration Management (CM), Identification and Authentication (IA), Media Protection (MP), Risk Assessment (RA), System and Communication Protection (SC), and System and Information Integrity (SI). 12
12.Ibid.
Chemical Facility Anti-Terrorism Standards
CFATS is a set of risk-based performance guidelines published by the Department of Homeland Security. CFATS also consists of 18 Risk-based Performance Standards (RBPSs), although these groups differ substantially from those defined by NIST: 13
13.Department of Homeland Security, Risk-based performance standards guidance; chemical facility anti-terrorism standards, Department of Homeland Security, Office of Infrastructure Protection, Infrastructure Security Compliance Division, Washington, DC, May 2009.
• RBPS 1—Restrict Area Perimeter
• RBPS 2—Secure Site Assets
• RBPS 3—Screen and Control Access
• RBPS 4—Deter, Detect, and Delay
• RBPS 5—Shipping, Receipt, and Storage
• RBPS 6—Theft or Diversion
• RBPS 7—Sabotage
• RBPS 8—Cyber
• RBPS 9—Response
• RBPS 10—Monitoring
• RBPS 11—Training
• RBPS 12—Personnel Surety
• RBPS 13—Elevated Threats
• RBPS 14—Specific Threats, Vulnerabilities, or Risks
• RBPS 15—Reporting of Significant Security Incidents
• RBPS 17—Officials and Organization
• RBPS 18—Records
Of these, RBPS 6 (Theft or Diversion), 7 (Sabotage), 8 (Cyber), 14 (Specific Threats, Vulnerabilities, or Risks), and 15 (Reporting of Significant Security Incidents) concern cyber security, with RBPS 8 focusing solely on cyber security. The CFATS RBPSs are not enforceable requirements at this time and are intended as guidance for chemical facilities. 14
14.Ibid.
ISA-99
ISA standard 99 (ISA-99) is an industrial control security standard created by the International Society of Automation (ISA) to protect SCADA and process control systems. ISA-99 offers varying security recommendations based on the physical and logical location of the systems being protected as well as their importance to the reliable operation of the system. In order to accomplish this, ISA-99 first attempts to classify functional areas of an industrial system into specific security levels and then provides recommendations for separating these areas into “zones.” ISA-99 also defines the interconnectedness of zones as well as how to enforce security between zones.
Using the example of an industrial network as illustrated in Figure 2.1, the most public systems such as Internet or Internet-facing systems within the business LAN would continue level 5, while the rest of the business LAN may map to level 4. Supervisory networks (i.e., the SCADA DMZ network) would represent level 3, and so on, with the actual “control system” (the SCADA networks, HMI systems, field devices, instrumentation and sensors) at level 0. This concept is very illustrative of the functional isolation of services and the establishment of security “enclaves” (see “Defense in Depth”).
ISA-99 organizes security recommendations into seven foundational requirements: 15
15.ANSI/ISA-TR99.00.01-2007, Security technologies for industrial automation and control systems, 2007, International Society of Automation (ISA), Research Triangle Park, NC.
• FR1—Access Control (AC)
• FR2—Use Control (UC)
• FR3—Data Integrity (DI)
• FR4—Data Confidentiality (DC)
• FR5—Restrict Data Flow (RDF)
• FR6—Timely Response to an Event (TRE)
• FR7—Resource Availability (RA)
Each foundational requirement consists of multiple system requirements (SRs). SRs that are especially useful to the protection of industrial networks (excluding policy and procedural recommendations) include16
16.Ibid.
• SR 1.1—IACS user identification and authentication
• SR 1.2—Account management
• SR 3.1—Communication integrity
• SR 3.3—Security functionality verification
• SR 3.4—Software and information integrity
• SR 4.3—Cryptographic key establishment and management
• SR 5.1—Information flow enforcement
• SR 5.2—Application partitioning
• SR 5.4—Boundary protection
• SR 7.1—Denial of service protection
• SR 7.2—Management of network resources
• SR 7.6—Network and security configuration settings
ISO 27002
ISO 27002 is a set of security recommendations published by the International Standards Organization (ISO) and the International Electrotechnical Commission (IEC), and may be referred to as ISO/IEC 27002 or ISO/IEC 27002:2005. ISO 27002 defines “Information technology—Security techniques—Code of practice for information security management,” and is not specific to industrial network security. ISO standards are widely used internationally and can be easily mapped to the recommendations of NIST, NRC, NERC, and others, as they consist of functional guidelines for risk assessment; security policy and management; governance; asset management; personnel security; physical and environmental security; communications and operations management; access control; asset acquisition, development, and maintenance; incident management; business continuity management; and compliance. 17
17.International Standards Organization, ISO/IEC 27002:2005. Information Technology—Security Techniques—Code of Practice for Information Security Management, ISO/IEC, Geneva, Switzerland, 2005.
Common Industrial Security Recommendations
Many of the network security practices that are either required or recommended by the aforementioned organizations are consistent between many or all of the others. Although all recommendations should be considered, these common “best practices” are extremely important and are the basis for many of the methods and techniques discussed within this book. They consist of the following steps: (1) identifying what systems need to be protected, (2) separating the systems logically into functional groups, (3) implementing a defense-in-depth strategy around each system, and (4) controlling access into and between each group.
Identification of Critical Systems
The first step in securing any system is determining what needs to be protected, and this is reflected heavily in NERC CIP, NRC 10 CFR 73.54, and ISA-99. Identifying the assets that need to be secured, as well as identifying their individual importance to the reliable operation of the overall process control system, is necessary for a few primary reasons: it tells us what should be monitored, and how closely; it tells us how to logically segment the network into high-level security enclaves; and it, therefore, indicates where our point security devices (such as firewalls and intrusion detection and prevention systems) should be placed. For North American electric companies, it also satisfies a direct requirement of NERC CIP, and therefore can help to minimize fines associated with noncompliance.
Identifying critical systems isn’t always easy, however. The first step is to build a complete inventory of all connected devices. Each of these devices should be evaluated independently. If it performs a critical function, it should be classified as critical. If it does not, consider whether it could impact any other critical devices or operations. Could it impact the network itself, preventing another device from interacting with a critical system and therefore causing a failure? Finally, does it protect a critical system in any way?
The NRC provides a logic map illustrating how to determine critical assets, which is adapted to more generic asset identification in Figure 2.3. This process will help to separate devices into two categories:
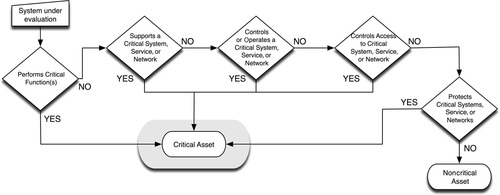 |
| Figure 2.3 NRC Process Diagram for Identifying Critical Cyber Assets. 18 18.U.S. Nuclear Regulatory Commission, Regulatory Guide 5.71 (New Regulatory Guide) Cyber Security Programs for Nuclear Facilities, U.S. Nuclear Regulatory Commission, Washington, DC, January 2010. |
• Critical Assets
• Noncritical Assets
However, in many larger operations this process may be over simplified. There may be different levels of “criticality.” A general rule to follow once the basic separation of critical versus noncritical has been completed is as follows: are there any critical assets that are not functionally related to other critical assets? If there are, next ask if one function is more or less important than the other. Finally, if there is both a functional separation and a difference in the criticality of the system, consider adding a new logical “tier” to your network. Also remember that a device could potentially be critical and also directly impact one or more other critical assets. Consider ranking the criticality of devices based on their total impact as well. Each layer of a separation can then be used as a point of demarcation, providing additional layers of defense between each group.
Network Segmentation/Isolation of Systems
The separation of assets into functional groups allows specific services to be tightly locked down and controlled, and is one of the easiest methods of reducing the attack surface that is exposed to attackers. Simply by disallowing all unnecessary ports and services, we also eliminate all of the vulnerabilities—known or unknown—that could potentially allow an attacker to exploit those services.
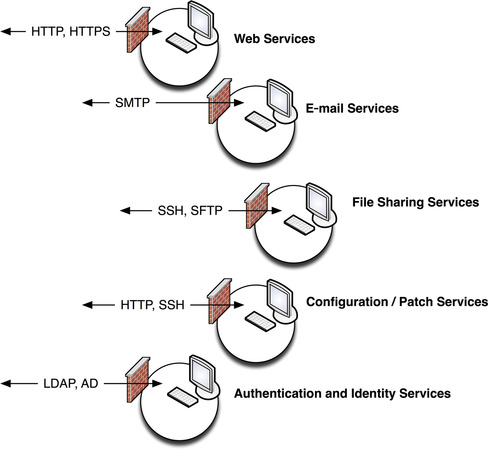
For example, if five critical services are isolated within a single functional group and separated from the rest of the network using a single firewall, it may be necessary to allow several different traffic profiles through that firewall (see Figure 2.4). If an attack is made using an exploit against web services over port 80, that attack may compromise a variety of services including e-mail services, file transfers, and patch/update services.
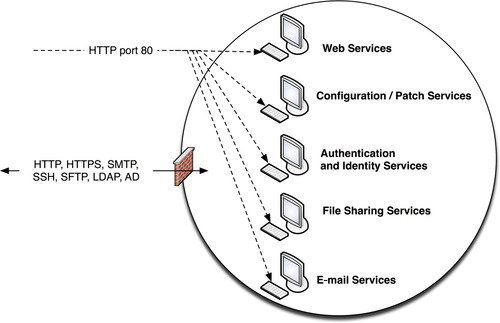 |
| Figure 2.4 |
However, if each specific service is grouped functionally and separated from all other services, as shown in Figure 2.5—that is, all web servers are grouped together in one group, all e-mail services in another group, etc.—the firewall can be configured to disallow anything other than the desired service, preventing an e-mail server from being exposed to a threat that exploits a weakness in HTTP.
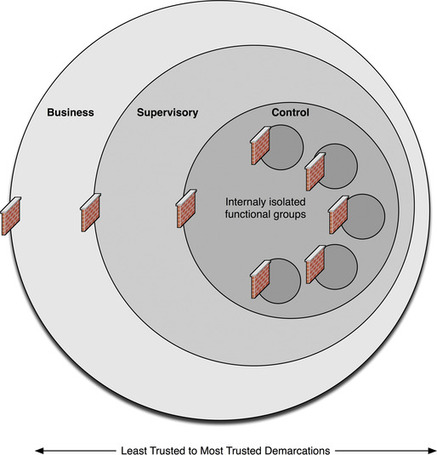
In an industrial control system environment, this method of service segmentation can be heavily utilized because there are many distinct functional groups within an industrial network that should not be communicating at all outside of established parameters. For example, protocols such as Modbus or DNP3 (discussed in depth in Chapter 4, “Industrial Network Protocols”) are specific to SCADA and ICS systems and should never be used within the business LAN and Internet services such as HTTP, SMTP, FTP, and others should never be used within supervisory or control network areas. In Figure 2.6, it can be seen how this layered approach to functional and topological isolation can greatly improve the defensive posture of the network.
Note that within this book, these isolated functional groups or enclaves are often depicted as being separated by a firewall. Although in many cases a separate firewall may be needed for each enclave, the actual method of securing the enclave can vary and could include dedicated firewalls, intrusion detection and prevention devices, application content filters, access control lists, and/or a variety of other controls. In some cases, multiple enclaves can be supported using a single firewall through the careful creation and management of policies that implicitly define which servers can connect over a given protocol or port. This is covered in detail in Chapter 7, “Establishing Secure Enclaves.”
Caution
Don’t forget to control communications in both directions through a firewall. Not all threats originate from outside. Open, outbound traffic policies can facilitate an insider attack, enable the internal spread of malware, enable outbound command and control capabilities, or allow for data leakage or information theft.
Defense in Depth
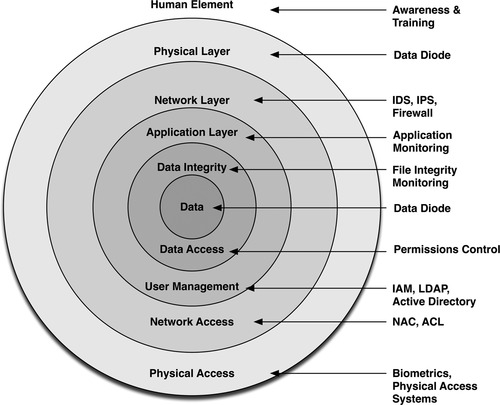
All standards organizations, regulations, and recommendations indicate that a defense-in-depth strategy should be implemented. Although the definitions of “defense in depth” vary somewhat, the philosophy of a layered or tiered defensive strategy is considered a best practice. Figure 2.7 illustrates a common defense-in-depth model, mapping logical defensive levels to common security tools and techniques.
Interestingly, because of the segregated nature of most industrial systems, the term “defense in depth” can and should be applied in more than one context, including
• The layers of the Open Systems Interconnection (OSI) model, from physical (Layer 1) to Application (Layer 7).
• Physical or Topological layers consisting of subnetworks and/or functional groups.
• Policy layers, consisting of users, roles, and privileges.
• Multiple layers of defense devices at any given demarcation point (such as implementing a firewall and an IDS or IPS).
Access Control
Access control is one of the most difficult yet important aspects of cyber security. By locking down services to specific users or groups of users, it becomes more difficult for an attacker to identify and exploit systems. The further we can lock down access, the more difficult an attack becomes. Although many proven technologies exist to enforce access control—from network access control (NAC), authentication services, and others—the successful implementation of access control is difficult because of the complexity of managing users and their roles and mapping that to the specific devices and services that relate specifically to an employee’s operational responsibilities. As shown in Table 2.1, the strength of access controls increases as a user’s identity is treated with the additional context of that user’s roles and responsibilities within a functional group.
Again, the more layers of complexity applied to the rules of user authentication and access, the more difficult it will be to gain unauthorized access. Some examples of advanced access control include the following:
• Only allow a user to log in to an HMI if the user has successfully badged into the control room (user credentials combined with physical access controls)
• Only allow a user to operate a given control from a specific controller (user credentials limited within a security enclave)
• Only allow a user to authenticate during that user’s shift (user credentials combined with personnel management)
The Use of Terminology Within This Book
Terminology specific to these various organizations and requirements will be used throughout this book. Although they may originate in a compliance mandate such as NERC CIP, they are used in the more open context of security best practices unless otherwise specified. Some terms that will be used extensively are routable and non-routable networks, assets (including cyber assets, critical assets, and critical cyber assets), enclaves, and electronic security perimeters or ESPs.
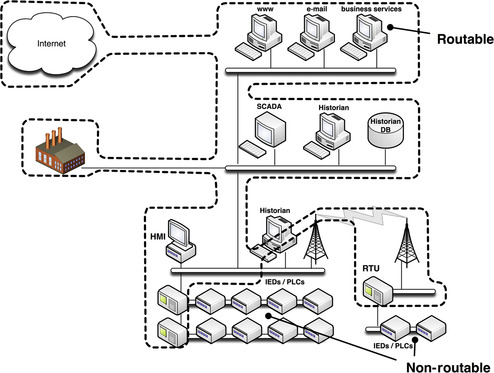
Networks, Routable and Non-routable
Although many think of a “network” as a Transmission Control Protocol/Internet Protocol (TCP/IP) network running on Ethernet, that assumption cannot be made when talking about industrial network security. Because many areas of industrial networks are connected using serial or bus networks, which operate via specific protocols, we need to expand our definition to include these areas of the industrial control systems. To make it easier to discern between the two network types, and to align with NERC CIP terminology, the terms “routable” and “non-routable” are used. A routable network typically means Ethernet and TCP/IP, although other routable protocols such as AppleTalk, DECnet, Novell IPX, and other legacy networking protocols certainly apply. “Routable” networks also include routable variants of SCADA and ICS protocols that have been modified to operate over TCP/IP, such as Modbus/TCP or ICCP over TCP/IP.
A “non-routable” network refers to those serial, bus, and point-to-point communication links that utilize Modbus/RTU, point-to-point ICCP, fieldbus, and other networks. They are still networks: they interconnect devices and provide a communication path between digital devices, and in many cases are designed for remote command and control.
Routable and non-routable networks generally interconnect at the demarcation between the control systems and the SCADA or supervisory networks, although in some cases (depending upon the specific industrial network protocols used) the two networks overlap. This is illustrated in Figure 2.8 and is discussed in more depth in Chapter 4, “Industrial Network Protocols,” and Chapter 5, “How Industrial Networks Operate.”
Assets, Critical Assets, Cyber Assets, and Critical Cyber Assets
An asset is a unique device that is used within an industrial control system. Assets are often computers, but also include network switches and routers, firewalls, printers, alarm systems, Human–Machine Interfaces (HMIs), Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), and the various relays, actuators, sensors, and other devices that make up a typical control loop. As of version 3, NERC CIP defines a “cyber asset” as any device connected via a routable protocol, which limits the role of a cyber asset to those devices communicating on a routable LAN. 19 A “critical cyber asset,” again as defined by NERC, is a cyber asset whose operation can impact the bulk energy system. 20
19.North American Electric Corporation, Standard CIP–002–3, Cyber Security, Critical Cyber Asset Identification, North American Electric Corporation (NERC), Princeton, NJ, December 16, 2009.
20.Ibid.
In this book the broader definition of “asset” is used, in order to extend (as much as possible) cyber security to the non-routable devices such as PLCs and RTUs, which have been proven to be both targetable and vulnerable to cyber attack during the 2010 outbreak of Stuxnet (see “examples of Industrial Network Incidents” in Chapter 3, “Introduction to Industrial Network Security.”
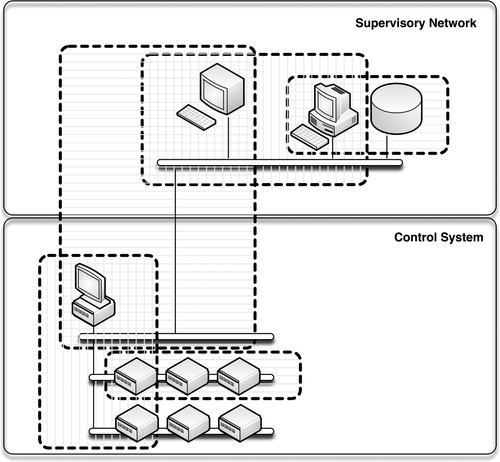
Enclaves
An “enclave” is a convenient term for defining a closed group of assets, similar to the functional “zone and conduit” model supported by ISA-99, 21 that is, the devices, applications, and users that should be interacting with each other legitimately in order to function, as illustrated in Figure 2.9. One example is a control loop: an HMI interfaces with a PLC which interacts with sensors, motors, valves, etc. to perform a specific control function. The “enclave” here includes all devices within the control loop including the PLC and HMI, and ideally the authorized users allowed to use the HMI. Nothing outside of this group should be interacting with anything inside of this group.
21.ANSI/ISA-TR99.00.01-2007, Security technologies for industrial automation and control systems, 2007, International Society of Automation (ISA), Research Triangle Park, NC.
Note
In the context of this book, an enclave is not (necessarily) a physical grouping of devices: it is a logical delineation of asset communication.
Enclaves are an important aspect of security as they define acceptable versus unacceptable behaviors. However, because a single asset can exist in multiple logical enclaves, the mapping and management of enclaves can become confusing. The concept of enclaves is expanded later in Chapter 7“Establishing Secure Enclaves”; for now it’s enough to understand the term and how it will be used.
Electronic Security Perimeters
The outermost boundary of any closed group of assets (i.e., an “enclave”) is called the perimeter. Again, this supports NERC CIP terminology, where “Electronic Security Perimeter” or “ESP” refers to the boundary between secure and nonsecure enclaves. 22 The perimeter itself is nothing more than the logical “dotted line” around an enclave that separates the closed group of assets within its boundaries from the rest of the network. “Perimeter defenses” are the security defenses established to police the entry into the enclave, and typically consist of a firewall and/or an Intrusion Prevention System (IPS).
22.North American Electric Corporation, Standard CIP–002–3, Cyber Security, Critical Cyber Asset Identification, North American Electric Corporation (NERC), Princeton, NJ, December 16, 2009.
A Note on Perimeterless Security
There is much debate about the ESP within the context of NERC and much discussion about a shift toward “perimeterless” security. In a perimeterless approach, there is no strict demarcation where all of our security products are concentrated. The goal is to move away from the “hard outer shell” with “soft gooey center” security practices that NERC’s mandate of an ESP unintentionally promotes. Although future changes to NERC CIP may alter the terminology around establishing perimeter defenses, it will remain important to establish and enforce boundaries. This will be discussed further in Chapter 7, “Establishing Secure Enclaves.”
Summary
Understanding the basic nature of industrial networks, and examining the many regulations and recommendations put forth by NERC, NIST, NRC, ISA, the ISO/IEC, and other organizations is the foundation of industrial network security. By evaluating an industrial network, identifying and isolating its systems into functional groups or enclaves, and applying a structured methodology of defense in depth and strong access control, the security of the network as a whole will be greatly improved.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.