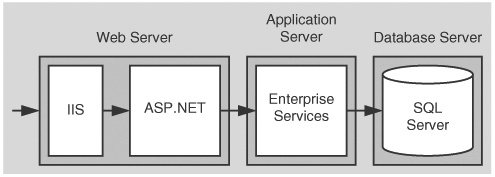
Access to intranet applications is restricted to a limited group of authorized users (such as employees that belong to a domain). While an intranet setting limits the exposure of your application, you may still face several challenges when you develop authentication, authorization, and secure communication strategies. For example, you may have non-trusting domains, which make it difficult to flow a caller’s security context and identity through to the back-end resources within your system. You may also be operating within a heterogeneous environment with mixed browser types. This makes it more difficult to use a common authentication mechanism.
If you have a homogenous intranet where all computers run the Microsoft® Windows® 2000 operating system or later and you have a domain where users are trusted for delegation, delegation of the original caller’s security context to the back end becomes an option.
You must also consider secure communication. Despite the fact that your application runs in an intranet environment, you cannot consider the data sent over the network secure. It is likely that you will need to secure the data sent between browsers and the Web server in addition to data sent between application servers and databases.
The following common intranet scenarios are used in this chapter to illustrate key authentication, authorization, and secure communication techniques:
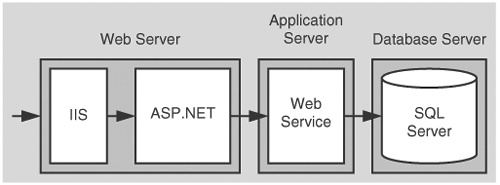
ASP.NET to SQL Server
ASP.NET to Enterprise Services to SQL Server
ASP.NET to Web Services to SQL Server
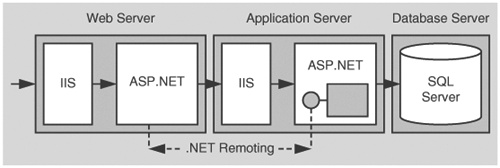
ASP.NET to Remoting to SQL Server
In addition, this chapter describes a Windows 2000 delegation scenario (Flowing the Original Caller to the Database), in which the original caller’s security context and identity flows at the operating system level from browser to database using intermediate Web and application servers.
Note
Several scenarios described in this chapter change the password of the default ASPNET account to allow duplicated accounts to be created on remote computers for network authentication purposes. This requires an update to the <processModel> element of Machine.config. <processModel> credentials should not be stored in plain text in machine.config. Instead use the aspnet_setreg.exe utility to store encrypted credentials in the registry. For more information, see Chapter 8, and article Q329290, "HOWTO: Use the ASP.NET Utility to Encrypt Credentials and Session State Connection Strings" in the Microsoft Knowledge Base.
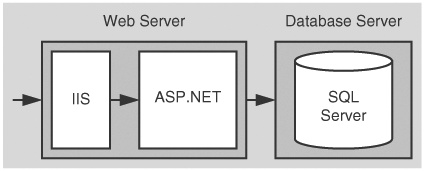
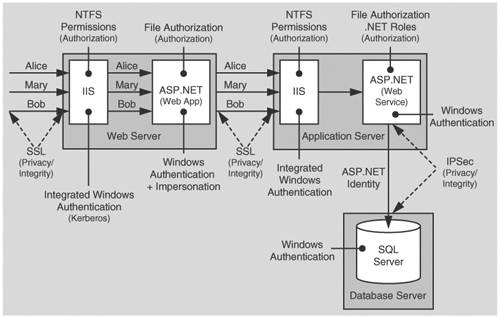
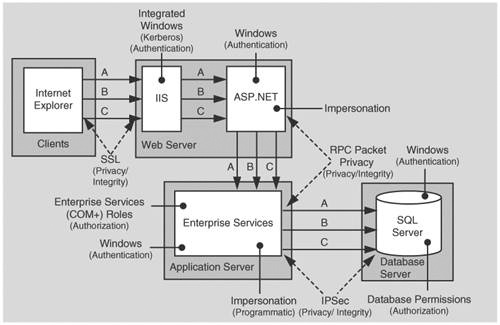
In this scenario, a HR database serves per-user data securely on a homogenous intranet. The application uses a trusted subsystem model and executes calls on behalf of the original callers. The application authenticates callers by using Integrated Windows authentication and makes calls to the database using the ASP.NET process identity. Due to the sensitive nature of the data, SSL is used between the Web server and clients.
The basic model for this application scenario is shown in Figure 5.1.
This scenario has the following characteristics:
Clients have Internet Explorer.
User accounts are in Microsoft Active Directory® directory service.
The application provides sensitive, per-user data.
Only authenticated clients should access the application.
The database trusts the application to authenticate users properly (that is, the application makes calls to the database on behalf of the users).
Microsoft SQL Server™ is using a single database user role for authorization.
In this scenario, the Web server authenticates the caller and restricts access to local resources by using the caller’s identity. You don’t have to impersonate within the Web application in order to restrict access to resources against the original caller. The database authenticates against the ASP.NET default process identity, which is a least privileged account (that is, the database trusts the ASP.NET application).
Table 5.1. Security measures
Category | Details |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
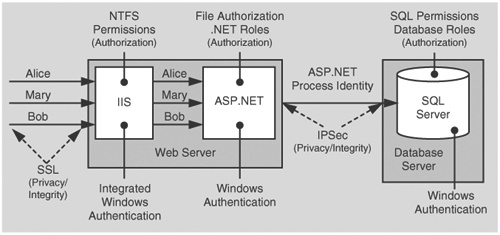
Figure 5.2 shows the recommended security configuration for this scenario.
Before you begin, you’ll want to see the following:
Creating custom ASP.NET accounts (see "Appendix " in the Reference section of this book)
Creating a least privileged database account (see Chapter 12)
Configuring SSL on a Web server (see "Appendix " in the Reference section of this book)
Configuring IPSec (see "Appendix " in the Reference section of this book)
Step | More Information |
|---|---|
Disable Anonymous access for your Web application’s virtual root directory | To work with IIS authentication settings, use the IIS MMC snap-in. Right-click your application’s virtual directory, and then click Properties. |
Enable Integrated Windows Authentication | Click the Directory Security tab, and then click Edit within the Anonymous access and authentication control group. |
Step | More Information |
|---|---|
Create a Windows account on your SQL Server computer that matches the ASP.NET process account (ASPNET) | The user name and password must match the ASPNET account. Give the account the following privileges:
|
Configure SQL Server for Windows authentication | |
Create a SQL Server Login for the local ASPNET account | This grants access to the SQL Server |
Create a new database user and map the login name to the database user | This grants access to the specified database |
Create a new user-defined database role and add the database user to the role | |
Establish database permissions for the database role | Grant minimum permissions For more information, see Chapter 12. |
Integrated Windows authentication in IIS is ideal in this scenario because all users have Windows accounts and are using Microsoft Internet Explorer. The benefit of Integrated Windows authentication is that the user’s password is never sent over the network. Additionally, the logon is transparent for the user because Windows uses the current interactive user’s logon session.
ASP.NET is running as least privileged account, so potential damage from compromise is mitigated.
You don’t need to impersonate in ASP.NET to perform .NET role checks or to secure resources within Windows ACLs against the original caller. To perform .NET role checks against the original caller, the WindowsPrincipal object that represents the original caller is retrieved from the HTTP context as follows:
WindowsPrincipal wp = (HttpContext.Current.User as WindowsPrincipal); if ( wp.IsInRole("Manager") ) { // User is authorized to perform manager-specific functionality }The ASP.NET FileAuthorizationModule provides ACL checks against the original caller for ASP.NET file types that are mapped within IIS to the aspnet_isapi.dll. For static file types such as .jpg, .gif, and .htm files, IIS acts as the gatekeeper and performs access checks using the original caller’s identity, based on the NTFS permissions associated with the file.
Using Windows authentication to SQL Server means that you avoid storing credentials in files and passing credentials over the network to the database server.
The use of a duplicated Windows account on the database server (one that matches the ASPNET local account) results in increased administration. If a password is changed on one computer, it must be synchronized and updated on the other. In some scenarios, you may be able to use a least-privileged domain account for easier administration.
The duplicated local account approach also works in the presence of a firewall where the ports required for Windows authentication may not be open. The use of Windows authentication and domain accounts may not work in this scenario.
You’ll need to ensure that your Windows groups are as granular as your security needs. Because .NET role-based security is based on Windows group membership this solution relies on Windows groups being set up at the correct level of granularity to match the categories of users (sharing the same security privileges) who access the application. The Windows groups that you use here to manage roles could be local to that computer or domain groups
SQL Server database user roles are preferred to SQL server application roles to avoid the associated password management and connection pooling issues associated with the use of SQL application roles.
Applications activate SQL application roles by calling a built-in stored procedure with a role name and a password. Therefore, the password must be stored securely. Database connection pooling must also be disabled when you use SQL application roles, which severely impacts application scalability.
For more information about SQL Server database user roles and SQL Server application roles, see Chapter 12.
The database user is added to a database user role and permissions are assigned for the role so that if the database account changes; you don’t have to change the permissions on all database objects.
Integrated Windows authentication to IIS requires Internet Explorer. In a mixed browser environment, your typical options would include:
Basic authentication and SSL. Basic authentication is supported by most browsers. Since the user’s credentials are passed over the network, you must use SSL to secure the scenario.
Client certificates. Individual client certificates can either be mapped to a unique Windows account or a single Windows account can be used to represent all clients. The use of client certificates also requires SSL.
Forms Authentication. Forms authentication can validate credentials against a custom data store such as a database or against Active Directory.
If you authenticate against Active Directory, make sure that you retrieve only the necessary groups that are pertinent to your application. Just like you shouldn’t issue queries against a database using SELECT * clauses, you shouldn’t blindly retrieve all groups from Active Directory.
If you authenticate against a database, you need to carefully parse the input used in SQL commands to protect against SQL injection attacks, and you should store password hashes (with salt) in the database instead of clear text or encrypted passwords.
For more information about using SQL Server as a credential store and storing passwords in the database, see Chapter 12.
Notice that in all cases, if you don’t use Integrated Windows authentication, where the platform manages credentials for you, you end up using SSL. However, this benefit pertains strictly to the authentication process. If you are passing security sensitive data over the network, you must still use IPSec or SSL.
In some scenarios you may be forced to use SQL authentication instead of the preferred Windows authentication. For example, there may be a firewall between the Web application and database, or the Web server may not be a member of your domain for security reasons. This also prevents Windows authentication. In this case, you might use SQL authentication between the database and Web server. To secure this scenario, you should:
Use the Data Protection API (DPAPI) to secure database connection strings that contain usernames and passwords. For more information, see the following resources:
"Storing Database Connection Strings Securely", in Chapter 12
"Appendix " in the Reference section of this book
"Appendix " in the Reference section of this book
"Appendix " in the Reference section of this book
Use IPSec or SSL between the Web server and database server to protect the clear text credentials passed over the network.
In this scenario, calls are made from the Web application to the database using the security context of the original caller. With this approach, it’s important to note the following:
If you choose this approach, you need to use either Kerberos authentication (with accounts configured for delegation) or Basic authentication.
A delegation scenario is discussed in the "Flowing the Original Caller to the Database" section later in this chapter.
You must also enable impersonation in ASP.NET. This means that local system resource access is performed using the original caller’s security context and as a result, ACLs on local resources such as the registry and event log require appropriate configuration.
Database connection pooling is limited because original callers won’t be able to share connections. Each connection is associated with the caller’s security context.
An alternate approach to flowing the user’s security context is to flow the original caller’s identity at the application level (for example, by using method and stored procedure parameters).
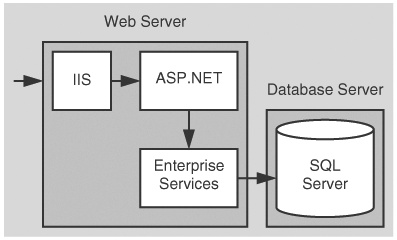
In this scenario, ASP.NET pages call business components hosted in an Enterprise Services application that in turn connects to a database. As an example, consider an internal purchase order system that uses transactions over the intranet and allows internal departments to place orders. This scenario is shown in Figure 5.3 on the next page.
This scenario has the following characteristics:
Users have Internet Explorer.
Components are deployed on the Web server.
The application handles sensitive data which must be secured while in transit.
Business components connect to SQL Server using Windows authentication.
Business functionality within these components is restricted based on the identity of the caller.
Serviced components are configured as a server application (out-of-process).
Components connect to the database using the server application’s process identity.
Impersonation is enabled within ASP.NET (to facilitate Enterprise Services role-based security).
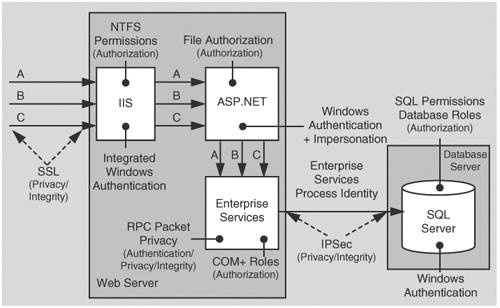
In this scenario, the Web server authenticates the original caller and flows the caller’s security context to the serviced component. The serviced component authorizes access to business functionality based on the original caller’s identity. The database authenticates against the Enterprise Service application’s process identity (that is,. the database trusts the serviced components within the Enterprise Services application). When the serviced component makes calls to the database, it passes the user’s identity at the application level (by using trusted query parameters).
Table 5.2. Security measures
Category | Detail |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
Figure 5.4 shows the recommended security configuration for this scenario.
Before you begin, you’ll want to see the following:
Creating a least privileged database account (see Chapter 12)
Configuring SSL on a Web server (see "Appendix " in the Reference section of this book)
Configuring IPSec (see "Appendix " in the Reference section of this book)
Configuring Enterprise Services security (see "Appendix " in the Reference section of this book)
Step | More Information |
|---|---|
Disable Anonymous access for your Web application’s virtual root directory | |
Enable Integrated Windows Authentication |
Step | More Information |
|---|---|
Create a Windows account on your SQL Server computer that matches the Enterprise Services process account | The user name and password must match your custom Enterprise Services account. Give the account the following privileges:
|
Configure SQL Server for Windows authentication | |
Create a SQL Server Login for your Enterprise Services account | This grants access to the SQL Server. |
Create a new database user and map the login name to the database user | This grants access to the specified database. |
Create a new database user role and add the database user to the role | |
Establish database permissions for the database user role | Grant minimum permissions For details, see Chapter 12 |
ASP.NET and Enterprise Services are running as least privileged accounts, so potential damage from compromise is mitigated. If either process identity were compromised, the account’s limited privileges reduce the scope of damage. Also, in the case of ASP.NET, if malicious script were injected, potential damage is constrained.
The ASP.NET application must be configured for impersonation in order to flow the security context of the original caller to the Enterprise Services components (to support Enterprise Services (COM+) role-based authorization). If you do not impersonate, role checks are made against the process identity (that is, the ASP.NET worker process). Impersonation affects who you authorize resources against.
Without impersonation, system resource checks are against the ASP.NET process identity. With impersonation, system resource checks are made against the original caller. For more information about accessing system resources from ASP.NET, see "Accessing System Resources" in Chapter 8.
By using Enterprise Services (COM+) roles, access checks are pushed to the middle tier, where the business logic is located. In this case, callers are checked at the gate, mapped to roles, and calls to business logic are based on roles. This avoids unnecessary calls to the back end. Another advantage of Enterprise Services (COM+) roles is that you can create and administer roles at deployment rime, using the Component Services Manager.
Windows authentication to SQL means you avoid storing credentials in files and sending them across the network.
The use of a local account to run the Enterprise Services application, together with a duplicated account on the database server, also works in the presence of a firewall where the ports required for Windows authentication may not be open. The use of Windows authentication and domain accounts may not work in this scenario.
The use of a duplicated Windows account on the database server (one that matches the Enterprise Services process account) results in increased administration. Passwords should be manually updated and synchronized on a periodic basis.
Because .NET role-based security is based on Windows group membership, this solution relies on Windows groups being set up at the correct level of granularity to match the categories of users (sharing the same security privileges) who access the application.
In this scenario, a Web server that runs ASP.NET pages connects to a Web service on a remote server. This server in turn connects to a remote database server. As an example, consider a HR Web application that provides sensitive data specific to a user. The application relies on the Web service for data retrieval. The basic model for this application scenario is shown in Figure 5.5.
The Web service exposes a method that allows an individual employee to retrieve his or her own personal details. Details must be provided only to authenticated individuals using the Web application. The Web service also provides a method that supports the retrieval of any employee details. This functionality must be available only to members of the HR or payroll department. In this scenario, employees are categorized into three Windows groups:
HRDept (members of the HR department)
Members of this group can retrieve details about any employee.
PayrollDept (members of the Payroll department)
Members of this group can retrieve details about any employee.
Employees (all employees)
Members of this group can only retrieve their own details.
Due to the sensitive nature of the data, the traffic between all nodes should be secure.
Users have Internet Explorer 5.x or later.
All computers run Windows 2000 or later.
User accounts are in Active Directory within a single forest.
The application flows the original caller’s security context all the way to the database.
All tiers use Windows authentication.
Domain user accounts are configured for delegation.
The database does not support delegation.
In this scenario, the Web server that hosts the ASP.NET Web application authenticates the original caller’s identity and flows their security context to the remote server that hosts the Web service. This enables authorization checks to be applied to Web methods to either allow or deny access to the original caller. The database authenticates against the Web service process identity (the database trusts the Web service). The Web service in turn makes calls to the database and passes the user’s identity at the application level using stored procedure parameters.
Table 5.3. Security measures
Category | Detail |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
Figure 5.6 shows the recommended security configuration for this scenario.
Before you begin, you’ll want to see the following:
Step | More Information |
|---|---|
Disable Anonymous access for your Web application’s virtual root directory | |
Enable Windows Integrated Authentication for your Web application’s virtual root | |
Configure IIS | |
|---|---|
Step | More Information |
Disable Anonymous access for your Web service’s virtual root directory | |
Enable Windows Integrated Authentication for your Web service’s virtual root directory | |
Step | More Information |
|---|---|
Create a Windows account on your SQL Server computer that matches the ASP.NET process account used to run the Web service | The user name and password must match your custom ASP.NET account. Give the account the following privileges:
|
Configure SQL Server for Windows authentication | |
This grants access to the SQL Server. | |
Create a new database user and map the login name to the database user | This grants access to the specified database. |
Create a new database user role and add the database user to the role | |
Establish database permissions for the database user role | Grant minimum permissions |
Integrated Windows authentication in IIS is ideal in this scenario because all users are using Windows 2000 or later, Internet Explorer 5.x or later, and have accounts in Active Directory, which makes it possible to use the Kerberos authentication protocol (which supports delegation). This allows you to flow the security context of the user across computer boundaries.
End user accounts must be NOT marked as "Sensitive and cannot be delegated" in Active Directory. The Web server computer account must be marked as "Trusted for delegation" in Active Directory. For more details, see "Appendix " in the Reference section of this book.
ASP.NET on the Web server and application server runs with a least privileged local account (the local ASPNET account), so potential damage from compromise is mitigated.
The Web service and Web application are both configured for Windows authentication. IIS on both computers is configured for Integrated Windows authentication.
When making a call to the Web service from the Web application, no credentials are passed by default. They are required in order to respond to the network authentication challenge issued by IIS on the downstream Web server. You must specify this explicitly by setting the Credentials property of the Web service proxy as shown in the following:
wsproxy.Credentials = CredentialCache.DefaultCredentials;
For more information about calling Web services with credentials, see Chapter 10.
The Web application is configured for impersonation. As a result, calls from the Web application to the Web service flow the original caller’s security context and allow the Web service to authenticate (and authorize) the original caller.
.NET roles are used within the Web service to authorize the users based on the Windows group to which they belong (HRDept, PayrollDept and Employees). Members of HRDept and PayrollDept can retrieve employee details for any employee, while members of the Employees group are authorized to retrieve only their own details.
Web methods can be annotated with the PrincipalPermissionAttribute class to demand specific role membership, as shown in the following code sample. Notice that PrincipalPermission can be used instead of PrincipalPermissionAttribute. This is a common feature of all .NET attribute types.
[WebMethod] [PrincipalPermission(SecurityAction.Demand, Role=@"DomainNameHRDept)] public DataSet RetrieveEmployeeDetails() { }The attribute shown in the preceding code means that only members of the DomainNameHRDept Windows group are allowed to call the RetrieveEmployeeDetails method. If any nonmember attempts to call the method, a security exception is thrown.
ASP.NET File Authorization (within the Web application and Web service) performs ACL checks against the caller for any file type for which a mapping exists in the IIS Metabase that maps the file type to Aspnet_isapi.dll. Static file types (such as .jpg, .gif, .htm, and so on), for which an ISAPI mapping does not exist are checked by IIS (again using the ACL attached to the file).
Because the Web application is configured for impersonation, resources accessed by the application itself must be configured with an ACL that grants at least read access to the original caller.
The Web service does not impersonate or delegate; therefore, it accesses local system resources and the database using the ASP.NET process identity. As a result, all calls are made using the single process account. This enables database connection pooling to be used. If the database doesn’t support delegations (such as SQL Server 7.0 or earlier), this scenario is a good option.
Windows authentication to SQL Server means you avoid storing credentials on the Web server and it also means that credentials are not sent across the network to the SQL Server computer.
SSL between the original caller and Web server protects the data passed to and from the Web application.
IPSec between the downstream Web server and database protects the data passed to and from the database.
The use of a duplicated Windows account on the database server (one that matches the ASP.NET process account) results in increased administration. Passwords should be manually updated and synchronized on a periodic basis.
As an alternative, consider using least-privileged domain accounts. For more information about choosing an ASP.NET process identity, see Chapter 9, "Chapter 8."
Because .NET role-based security is based on Windows group membership, this solution relies on Windows groups being set up at the correct level of granularity to match the categories of users (sharing the same security privileges) who will access the application.
Kerberos delegation is unrestricted and as a result you must carefully control which applications identities run on the Web server. To raise the bar on security, limit the scope of the domain account’s reach by removing the account from Domain Users group and provide access only from appropriate computers. For more information, see the white paper on the Microsoft Web site at http://www.microsoft.com/windows2000/techinfo/planning/security/secdefs.asp.
If you need to connect to non SQL Server databases, or you currently use SQL authentication, you must pass database account credentials explicitly using the connection string. If you do so, make sure that you securely store the connection string.
For more information, see "Storing Database Connection Strings Securely" within Chapter 10, "Chapter 12."
In this scenario, a Web server that runs ASP.NET pages makes secure connections to a remote component on a remote application server. The Web server communicates with the component by using .NET Remoting over the HTTP channel. The remote component is hosted by ASP.NET. This is shown in Figure 5.7.
Users have various types of Web browsers.
The remote component is hosted by ASP.NET.
The Web application communicates with the remote component using the HTTP channel.
The ASP.NET application calls the .NET remote component and passes the original caller’s credentials for authentication. These are available from Basic authentication.
The data is sensitive and therefore must be secured between processes and computers.
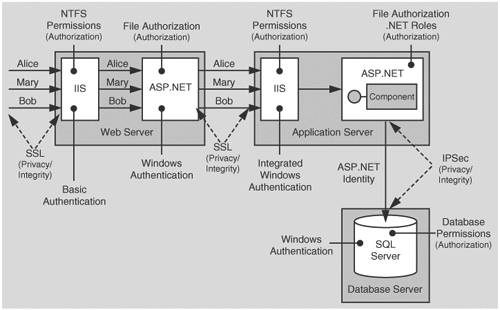
In this scenario, the Web server that hosts the ASP.NET Web application authenticates the original callers. The Web application is able to retrieve the caller’s authentication credentials (user name and password) from HTTP server variables. It can then use them to connect to the application server that hosts the remote component, by configuring the remote component proxy. The database uses Windows authentication to authenticate against the ASP.NET process identity (that is, the database trusts the remote component). The remote component in turn calls the database and passes the original caller’s identity at the application level using stored procedure parameters.
Table 5.4. Security measures
Category | Detail |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
Figure 5.8 shows the recommended security configuration for this scenario.
Before you begin, you’ll want to see the following:
Creating a least privileged database account (see Chapter 12)
Configuring SSL on a Web server (see "Appendix " in the Reference section of this book)
Configuring IPSec (see "Appendix " in the Reference section of this book)
Configure IIS | |
|---|---|
Step | More Information |
Disable Anonymous access for your Web application’s virtual root directory | |
Enable Basic authentication | Use SSL to protect the Basic authentication credentials. |
Configure IIS | |
|---|---|
Step | More Information |
Disable Anonymous access for your Web application’s virtual root directory | |
Enable Integrated Windows authentication | |
Step | More Information |
|---|---|
Create a Windows account on your SQL Server computer that matches the ASP.NET process account used to run the Web service | The user name and password must match your custom ASP.NET account. Give the account the following privileges:
|
Configure SQL Server for Windows authentication | |
This grants access to the SQL Server | |
Create a new database user and map the login name to the database user | This grants access to the specified database |
Create a new database user role and add the database user to the role | |
Establish database permissions for the database user role | Grant minimum permissions |
Step | More Information |
|---|---|
Configure the Web site on the Web server for SSL | See "Appendix " in the Reference section of this book. |
Configure the Web site on the application server for SSL | See "Appendix " in the Reference section of this book. |
Configure IPSec between application server and database server | See "Appendix in the Reference section of this book." |
ASP.NET on the Web server and application sever is running as a least privileged local account, so potential damage from compromise is mitigated. The default ASPNET account is used in both cases.
Use of the ASPNET local account (duplicated on the SQL Server computer) further reduces the potential security risk. A duplicated Windows account on the database server allows the remote component to run with a least privilege ASP.NET account on the application server.
Basic authentication at the Web server allows the user’s credentials to be used by the Web application to respond to Windows authentication challenges from the application server.
To call the remote component using the caller’s credentials, the Web application configures the remote component proxy as shown in the code fragment on the next page.
string pwd = Request.ServerVariables["AUTH_PASSWORD"]; string uid = Request.ServerVariables["AUTH_USER"]; IDictionary channelProperties = ChannelServices.GetChannelSinkProperties(proxy); NetworkCredential credentials; credentials = new NetworkCredential(uid, pwd); ObjRef objectReference = RemotingServices.Marshal(proxy); Uri objectUri = new Uri(objectReference.URI); CredentialCache credCache = new CredentialCache(); credCache.Add(objectUri, "Negotiate", credentials); channelProperties["credentials"] = credCache; channelProperties["preauthenticate"] = true;For more information about flowing security credentials to a remote component, see Chapter 11.
Impersonation is not enabled within the ASP.NET Web application, because the remoting proxy is specifically configured using the user’s credentials obtained by Basic authentication. Any other resource accessed by the Web application uses the security context provided by the ASP.NET process account.
SSL between the user and Web server protects the data passed to and from the Web server and also protects the Basic credentials passed in clear text during the authentication process.
Integrated Windows authentication at the application server provides .NET role checks against the original caller. The roles correspond to Windows groups.
Role-based checks can be performed, even without impersonation.
ASP.NET File Authorization performs ACL checks against the caller for any file type for which a mapping exists in the IIS Metabase that maps the file type to aspnet_isapi.dll. IIS performs access checks for static files (not mapped to an ISAPI extension within IIS).
Because impersonation is not enabled on the application server, any local or remote resource access performed by the remote component does so using the ASPNET security context. ACLs should be set accordingly.
Windows authentication to SQL Server means you avoid storing credentials on the application server and it also means that credentials are not sent across the network to the SQL Server computer.
The use of a duplicated Windows account on the database server (one that matches the ASP.NET process account) results in increased administration. Passwords should be manually updated and synchronized on a periodic basis.
Because .NET role-based security is based on Windows group membership, this solution relies on Windows groups being set up at the correct level of granularity to match the categories of users (sharing the same security privileges) who will access the application.
The Web server uses Kerberos to authenticate callers. Kerberos delegation is used to flow the original caller’s security context across to the remote component on the application server.
This approach requires that all user accounts be configured for delegation. The Web application would also be configured for impersonation and would use DefaultCredentials to configure the remote component proxy. This technique is discussed further in the "Flowing the Original Caller" section of Chapter 11.
The scenarios discussed earlier have used the trusted subsystem model and in all cases the database has trusted the application server or Web server to correctly authenticate and authorize users. While the trusted subsystem model offers many advantages, some scenarios (perhaps for auditing reasons) may require you to use the impersonation/delegation model and flow the original caller’s security context across computer boundaries all the way to the database.
Typical reasons why you may need to flow the original caller to the database include:
You need granular access in the database and permissions are restricted by object. Specific users or groups can read, while others can write to individual objects.
This is in contrast to less granular task-based authorization, where role membership determines read and write capabilities for specific objects.
You may want to use the auditing capabilities of the platform, rather than flow identity and perform auditing at the application level.
If you do choose an impersonation/delegation model (or are required to do so due to corporate security policy) and flow the original caller’s context through the tiers of your application to the back end, you must design with delegation and network access in mind (which is nontrivial when spanning multiple computers). The pooling of shared resources (such as database connections) also becomes a key issue and can significantly reduce application scalability.
This section shows you how to implement the impersonation/delegation for two of the most common application scenarios:
ASP.NET to SQL Server
ASP.NET to Enterprise Services to SQL Server
For more information about the trusted subsystem and impersonation/delegation models and their relative merits, see Chapter 3.
In this scenario, calls to the database are made using the security context of the original caller. Authentication options described in this section include Basic and Integrated Windows authentication. A Kerberos delegation scenario is described within the "ASP.NET to Enterprise Services to SQL Server" section.
The following configuration settings for Basic authentication enable you to flow the original caller all the way to the database.
Table 5.5. Security measures
Category | Detail |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
With this approach, it’s important to note the following points:
Basic authentication prompts the user with a pop-up dialog box into which they can type credentials (user name and password).
The database must recognize the original caller. If the Web server and database are in different domains, appropriate trust relationships must be enabled to allow it to authenticate the original caller.
Integrated Windows authentication results in either NTLM or Kerberos authentication and is dependent upon the client and server computer configurations.
NTLM authentication does not support delegation and as a result does not allow you to flow the original caller’s security context from the Web server to a physically remote database. The single network hop allowed for NTLM authentication is used between the browser and Web server. To use NTLM authentication, the SQL Server must be installed on the Web server, which is likely to be appropriate only for very small intranet applications.
In this scenario, ASP.NET pages call business components hosted in a remote Enterprise Services application that in turn talk to a database. The original caller’s security context flows all the way from the browser to the database. This is shown in Figure 5.9.
Users have Internet Explorer 5.x or later.
All computers are Windows 2000 or later.
User accounts are maintained in Active Directory within a single forest.
The application flows the original caller’s security context (at the operating system level) all the way to the database.
All tiers use Windows authentication.
Domain user accounts are configured for delegation and the account used to run the Enterprise Services application must be marked as "Trusted for delegation" within Active Directory.
In this scenario, the Web server authenticates the caller. You must then configure ASP.NET for impersonation in order to flow the original caller’s security context to the remote Enterprise Services application. Within the Enterprise Services application, component code must explicitly impersonate the caller (using CoImpersonateClient) in order to ensure the caller’s context flows to the database.
Table 5.6. Security measures
Category | Detail |
|---|---|
Authentication |
|
Authorization |
|
Secure Communication |
|
Figure 5.10 shows the recommended security configuration for this scenario.
Before you begin, you should be aware of the following configuration issues:
The Enterprise Services process account must be marked "Trusted for delegation" in Active Directory and end user accounts must not be marked "Sensitive and cannot be delegated." For more information, see "Appendix " in the Reference section of this book.
Windows 2000 or later is required on all computers. This includes client (browser) computers and all servers.
All computers must be in the Active Directory and must be part of a single forest.
The application server that hosts Enterprise Services must be running Windows 2000 SP3.
If you are using Internet Explorer 6.0 on Windows 2000, it defaults to NTLM authentication instead of the required Kerberos authentication. To enable Kerberos delegation, see article Q299838, "Can’t Negotiate Kerberos Authentication After Upgrading to Internet Explorer 6," in the Microsoft Knowledge Base.
Configure the Web Server (IIS) | |
|---|---|
Step | More Information |
Disable Anonymous access for your Web application’s virtual root directory | |
Enable Windows Integrated authentication | |
Configure Serviced Components (and the Application Server) | |
|---|---|
Step | More Information |
Managed class(es) must inherit from the Serviced Component class | See article Q306296, "HOW TO: Create a Serviced .NET Component in Visual C# .NET," in the Microsoft Knowledge Base. |
Add code to the serviced component to impersonate the caller by calling the CoImpersonateClient() and CoRevertToSelf() APIs from OLE32.DLL before accessing remote resources (for example, a database) in order for the caller’s context to be used. By default, the Enterprise Services process context is used for outgoing calls. | Add references to OLE32.DLL: class COMSec
{
[DllImport("OLE32.DLL", CharSet=CharSet.Auto)]
public static extern long CoImpersonateClient();
[DllImport("OLE32.DLL", CharSet=CharSet.Auto)]
public static extern long CoRevertToSelf();
}
Call these external functions before calling remote resources: COMSec.CoImpersonateClient(); COMSec.CoRevertToSelf(); |
For more information, see Chapter 9. | |
Configure Serviced Components (and the Application Server) | |
|---|---|
Step | More Information |
Configure the Enterprise Services application as a server application | This can be configured using the Component Services tool, or via the following .NET attribute placed in the service component assembly. |
[assembly: ApplicationActivation(ActivationOption.Server)] | |
Configure the Enterprise Services application to use packet privacy authentication (to provide secure communication with encryption) | Add the following .NET attribute to the serviced component assembly. [assembly: ApplicationAccessControl(
Authentication =
AuthenticationOption.Privacy)] |
Configure the Enterprise Services application for component level role-based security AccessChecksLevelOption. | To configure role checks at the process and component level (including interfaces and classes) use the following attribute. [assembly: ApplicationAccessControl(AccessChecksLevel= ApplicationComponent)] |
Decorate classes with the following attribute: | |
[ComponentAccessControl(true)] | |
For more information about configuring interface and method level role checks, see "Configuring Security" in Chapter 9. | |
Create a custom account for running Enterprise Services and mark it as Trusted for delegation in Active Directory | The Enterprise Services application needs to run as domain account marked as Trusted for Delegation in Active Directory. For more information, see "Appendix " in the Reference section of this book. |
Configure Enterprise Services to run as your custom account | This must be configured using the Component Services tool or script. You can not use .NET attributes within the serviced component assembly. |
Step | More Information |
|---|---|
Configure SQL Server for Windows authentication | |
Create SQL Server Logins for the Windows groups that the users belong to. | This grants access to the SQL Server. The access control policy treats Windows groups as roles. For example, you may have groups such as Employees, HRDept and PayrollDept. |
Create new database users for each SQL Server login | This grants access to the specified database. |
Establish database permissions for the database users | Grant minimum permissions For more information, see Chapter 12. |
The key to flowing the original caller’s security context is Kerberos authentication, which generates a delegate-level token. After the server process (IIS) receives the delegate-level token, it can pass it to any other process, running under any account on the same computer, without changing its delegation level. It does not matter whether the worker process is running as a local or domain account. It does matter what IIS is running as. If it’s running as something other than LocalSystem, the account it is running under needs to be marked as "Trusted for delegation" in Active Directory.
If IIS is running as LocalSystem, the computer account must be marked as "Trusted for delegation". For more information, see "Appendix " in the Reference section of this book.
Integrated Windows authentication (with Kerberos) in IIS is ideal in this scenario because all users have Windows accounts and they are using Internet Explorer 5.x or later. The benefit of Integrated Windows authentication is that the user’s password is never sent over the wire. Additionally, the logon will be transparent because Windows will use the current interactive user’s logon session.
ASP.NET constructs a WindowsPrincipal object and attaches it to the current Web request context (HttpContext.User). If you need to perform authorization checks within the Web application you can use the following code.
WindowsPrincipal wp = (HttpContext.Current.User as WindowsPrincipal); if ( wp.IsInRole("Manager") ) { // User is authorized to perform manager-specific functionality }The ASP.NET FileAuthorizationModule provides ACL checks against the original caller for ASP.NET file types that are mapped within IIS to the Aspnet_isapi.dll. For static file types such as .jpg, .gif and .htm files, IIS acts as the gatekeeper and performs access checks using the original caller’s identity.
By using Windows authentication to SQL, you avoid storing credentials in files on the application server and avoid passing them across the network. For example include the Trusted_Connection attribute in the connection string:
ConStr="server=YourServer; database=yourdatabase; Trusted_Connection=Yes;"
The original caller’s context flows across all tiers, which makes auditing extremely easy. You can use platform-level auditing (for example, auditing features provided by Windows and SQL Server).
If you are using Internet Explorer 6.0 on Windows 2000, the default authentication mechanism that is negotiated is NTLM (and not Kerberos). For more information, see article Q299838, "Can’t Negotiate Kerberos Authentication After Upgrading to Internet Explorer 6," in the Microsoft Knowledge Base.
Delegating users across tiers is expensive in terms of performance and application scalability compared to using the trusted subsystem model. You cannot take advantage of connection pooling to the database, because connections to the database are tied to original caller’s security context and therefore cannot be efficiently pooled.
This approach also relies on the granularity of Windows groups matching your application’s security needs. That is, Windows groups must be set up at the correct level of granularity to match the categories of users (sharing the same security privileges) who access the application.