The World of the Board
A board of directors’ essential role, whether it serves a publicly listed company, a privately owned firm, or a not-for-profit organization, is to offer leadership and governance to enable an organization to fulfill its objectives and purpose. Board members function as fiduciaries or legal advisors to the organizations, instituting solid ethical and legal governance and financial management procedures. Additionally, they often are responsible for fundraising and advocacy for the organization.
Commonly, boards are made up of non-executive and executive directors, led by the board chairperson. The board is jointly accountable for the company’s performance and governance. It assigns day-to-day operating responsibilities to the CEO. They are aided in their efforts by an executive committee and other committees, including but not limited to the audit committee, risk committee, nominations committee, and remuneration committee. The board should conduct active oversight and control over the development and execution of the firm’s risk management policies and procedures.
In this chapter, we will discuss the critical requirements for a board to understand with regard to cyber risks, and how to empower it to make decisions about those risks.
It’s important for an organization to have a board of directors that will help provide stability and guidance as a company grows. But what does this group of individuals do, exactly? This chapter will explore the role of the board and identify some of the key considerations that come into play when making decisions about cybersecurity and cyber risks.
We will cover the following topics in this chapter:
- Understanding the world of the board
- The board’s structure
- The board’s interests in cybersecurity
- The CISO’s seat at the table
- Speaking the board’s language
- What not to do in the boardroom
- Reporting to the board (an add-on for CISOs and a reference for CEOs)
- Boards and mergers and acquisitions
- Asking the board the right questions and setting up your CISO for success
Understanding the world of the board
In this information age where most organizations are connected to the internet and dependent on information technology and information systems, a cyberattack could easily result in an organization suffering irreparable damage to its reputation, trust, and brand. Cyberattacks disrupt business operations and have a real financial cost. Put simply, a successful cyberattack is highly likely to cause complete disruption to the business and has the potential to put it out of business.
Nonetheless, many firms fail to prioritize cyber risks in the boardroom, resulting in concerning gaps in their cyber-risk evaluation and mitigation. As public and investor awareness of cybersecurity concerns grows, boards increasingly are compelled to commit more time and resources to manage their cyber risk. By adopting a more proactive stance at the board level, firms may embrace the opportunity to enhance their cyber-risk management, expand their access to capital, and better fulfill investor expectations.
Alternatively, businesses risk being exposed to long-term financial and reputational consequences. This applies especially when making major decisions such as mergers and acquisitions. Consideration of security early on may pave the way to better value in the form of increased revenue, increased customer happiness, and cost savings.
Forward-thinking firms are attempting to simplify the insights and knowledge gleaned from their cyber-risk analysis to the point where executives and the board can take action. They closely link risk to the organizational strategy and address it as part of their risk management decision-making process.
First, it is worth noting that the board’s main mission is to maximize the value of shareholders’ investment, although in particular cases, this could be detrimental to other stakeholders’ interests (such as employees and consumers). Hence, it is important to find a balanced outcome for both shareholders and other parties in a world marked by an increasing need to preserve a social license.
To achieve that mission, the directors of a board should have different but complementary experiences that can combine to produce a holistic view of the decision-making process, while still considering risks. In other words, the board of directors must be able to see the forest surrounding the tree, not just the tree itself. Nonetheless, both the law and daily practice continue to support the concept that the board cannot and should not be engaged in risk management on a day-to-day, hands-on basis.
Rather, directors should ensure that the risk management policies and procedures are developed and implemented by the company’s senior executives and risk managers and are aligned with the company’s strategy and risk appetite. Directors also should make sure these policies and procedures operate as intended and that the steps necessary to foster an enterprise-wide culture that promotes appropriate risk awareness, behaviors, and judgments about risk are taken.
The board should be aware of the nature and scale of the company’s primary risks and should expect full participation in risk management from the CEO and top executives. Through its oversight function, the board can communicate to management and staff that comprehensive risk management is neither a barrier to business behavior nor a mere complement to a firm’s total compliance program. Rather, it is an intrinsic part of the organization’s strategy, culture, and operations. Additionally, the roles and duties of various board committees in supervising certain risk categories should be examined to ensure the board’s oversight function is coordinated and comprehensive.
The risk supervision obligations of a board are generally derived from state law fiduciary duties, federal and state rules and regulations, stock exchange listing requirements, and some recognized (and changing) best practices on a national and international level.
Comprehensive risk management should not be considered a distinct corporate activity but, importantly, an essential, enterprise-wide component that influences how a business assesses and rewards performance. Risk assessment, accurate risk-reward analysis, and smart risk reduction should be included in every company’s decision-making process.
Transparency, consistency, and communication are critical in defining the proper tone at the top—the board’s vision for the business, including its commitment to risk oversight, ethics, and intolerance of compliance failures, should be successfully conveyed across the organization.
Major firms often include in their statements assurances that executive management provides regular updates to the board of directors on risk management issues. Some corporations even include such rules in their annual reports and financial filings. Although many organizations have explicit processes and predefined triggers for reporting—or “escalating”—risk concerns to the board of directors, many others do not. This includes considering the board’s supervisory function as appreciating cyber risk as an emerging risk to the firm and being informed of the criteria utilized by management in deciding which information is referred and reported to the board. In making this determination, the board of directors first has to understand the company’s cyber-risk exposure and be informed of the company’s cybersecurity program and methods for mitigating risk. The board should also encourage a crisis response strategy that requires involvement from various stakeholders in collaboration with management.
The board’s structure
The board’s structure is often determined in an organization’s constitution or a shareholders’ agreement, a legal document executed by all the parties who have a stake in the company. There are also board charters describing the firm’s governance. Good governance rules would recommend that a minimum number of independent directors also be appointed to the board to provide different perspectives, including directors who have a range of experiences in a particular subject.
Usually, the board creates different committees to evaluate specific decisions. To operate more efficiently and leverage its resources, the board could gather some of its members with particular expertise into a committee that addresses technical matters and provides points of view to the whole board to facilitate a decision. Depending on the industry, the following committees might be formed: an audit and risk committee, a regulatory committee, a remuneration committee, and a health and safety committee, among others.
A board director of a New South Wales government critical-infrastructure body shared the opinion that “whatever you do in a company, you always need to take risks to generate returns. But the risk taken must be appropriate and thoroughly monitored. At the board level, the audit and risk committee will consider whether the risk register has been properly documented (identification and qualification of the main risks concerning the internal processes, tangible and intangible assets, and employees).”
He continued: “This register rates the various risks in terms of their probability of occurrence and impact significance for the company. The audit and risk committee must ensure that the company’s management has elaborated and implemented a mitigation plan to limit the occurrence of risks as well as their significance before they materialize.”
This is done to preserve the sustainability/resilience of operations as well as financial profits.
The board must also acknowledge that risks cannot be eliminated but can be mitigated most of the time. This is incredibly important for the board, as ultimately it will be held responsible if major event damages the company’s business as a result of a lack of due diligence (risks not identified and/or adequately managed).
Shareholders might have divergent interests because of the nature of their business or certain internal constraints not necessarily related to a company. It might happen that shareholders who are represented by board members may engage with each other to learn more about their expectations in terms of the broader strategic direction for the company. The management recommendations are approved, rejected, or subject to board members’ amendments at the board meeting itself.
Ideally, the board usually wants to come to an agreement and empower top management with the agility to execute key decisions for the best interests of the company and shareholders.
A persistent disagreement on a board decision could eventually lead to a deadlock, preventing management from taking action until the matter is resolved. A party could have a minority investment position but with a “negative control” on board decisions. This governance framework is designed to provide veto rights to smaller investors to protect their interests vis-à-vis major shareholder decisions. The negative control threshold is a commercial decision decided by shareholders as part of the shareholder agreement.
The board’s interests in cybersecurity
Cyber risk should not be considered in isolation, and cyber-risk data should not be presented as random numbers or lists when discussing it with the board. Management must clearly communicate to the board how one risk impacts another risk, including cyber, so all parties can effectively formulate a solution, rather than creating confusion and disinterest.
The capacity to demonstrate how cyber risk is interconnected with other risks is just as critical as the ability to demonstrate how cyber-risk mitigation measures are succeeding. In turn, this can assist the board in prioritizing expenditures on mitigation efforts, understanding the actual return on such investments, and recognizing the value the CISO brings to the organization by developing programs and providing tangible insight into which initiatives are successful and which are not. This enables you and the board of directors to assess whether initiatives are having an effect and should be given further attention, and how your organization’s preparedness and cyber maturity compare to those of other organizations in the same industry.
This is more difficult to do when cyber-risk discussions are conducted using technical terms and numbers. To integrate cyber-risk data, it is essential to uncover vital information from internal and external data, and then standardize the data so it is comprehensible and presented in the context of business risk. When data is trended through time, this report will demonstrate what is effective, what is not, and how the CISO protects the company’s interests and aligns with its goals.
Instead of speaking at the board, the CISO should engage the board in a discussion. Conversations make for the most effective presentations. If you want the CISO to create a lasting impression in the boardroom, they must engage board members rather than just reciting information about important cyberthreats or your overall cyber-risk management strategy. And if board members have questions, your CISO should be able to provide answers … and quickly. When it comes to conveying cyber risk to board-level stakeholders, these qualities are critical.
In Shamane’s research studies with board and executives, her presentation on “Birds and Buttons” focuses on how the four bird characteristics (the dove, owl, peacock, and eagle [DOPE] personality test created by Richard M. Stevenson) play out in the boardroom and the trigger buttons that get board members to sit up and pay attention.
After countless conversations and engagements with boards and executives around the world, Shamane has narrowed it down to the following top six criteria for success:
- Business ownership
- Appropriate investment
- Rightly equipped
- Risk transfer options
- Maintaining foresight
- Industry resilience
Business ownership
First and foremost, the board needs to be aware that they own the organization’s cyber risk, and their C-suite executives are jointly responsible for cyber-risk management, not just the CISO.
Although cyber increasingly is recognized by more boards of directors as a priority issue, there is still a lack of formal governance frameworks to support board oversight. The chairperson of the board can contribute by ensuring there’s sufficient time allocated in the board agenda for cyber-risk discussions. Some questions to prompt discussion include:
- Do we know who owns cyber risk, especially since it is a strategic business enabler?
- How are we aligning cyber-risk management with business needs? Cyber risks are similar to financial, health and safety, and operational risks; there is an inherent risk, and the executive’s role is to approach them from an enterprise-wide perspective, minimizing risk and maximizing business performance.
- Do we have a formal cybersecurity framework or strategy in place? Is the board asking the right questions to ensure cyber risk is woven into business processes right from the beginning? Has it been baked into major business decision processes in a timely fashion, including mergers and acquisitions, partnerships, or new product launches?
- Does the board have oversight of our detection and response capabilities?
- Is our management team able to detect any cyberattacks or critical events requiring senior-level involvement?
- If an event does occur, do we have a plan? What is it, and how quickly can we recover?
Appropriate investment
This is an important question the board needs to ask itself: Are we investing appropriately in cybersecurity? Is our current investment (security budget) in cyber defense too much or too little?
The board needs to continuously invest appropriately in the security budget, weighing the costs and benefits of the different risk mitigation and reduction activities, while being mindful that there is no silver bullet solution.
A lot of these things can and will be resolved by more investment, controls, automation, and processes. But that still leaves us with the naïve and compassionate humans—our employees—and we need to continuously raise awareness and build a healthy security culture, highlighted in more detail in the next chapter.
Rightly equipped
Are we rightly equipped to protect our most valuable assets? This includes securing our supply chains by holding our suppliers to high standards.
How does our organizational design and structure fare in supporting our cybersecurity strategy? Residual risks that cannot be mitigated within the security budget should be accepted by the board, and if not, additional resources should be looked at to reduce those risks.
In terms of protection, do we have the right tools, processes, and people (including at the board level itself) in place to protect our boundaries? Do we have access to expert SMEs (subject matter experts) to make well-informed decisions? How are we incorporating cybersecurity expertise into board governance? Do we have appointed board directors with cyber skills? How often do our board directors receive training on cybersecurity? In the AICD survey conducted of 856 board directors in May 2022 (https://www.aisa.org.au/common/Uploaded%20files/Research/FINAL%2008299-3-5-Cyber-Security-Report-30pp-v3B.pdf), only 23 percent of them have appointed directors with cyber skills, and 43 percent of boards do not receive any training on cybersecurity.
A more proactive approach to providing ongoing education to the board is required, given the increasing and evolving nature of cyber risk.
Risk transfer options
This is a simple question: If there is no adequate cyber insurance, do we know what the exposure to the board is? And if there is insurance, does the board know what is exactly covered? What are the benefits and does this effectively align our cyber risks with our business risk tolerance? And if not, are there risk transfer options that can be considered?
Maintaining foresight
It is important for organizations to keep up with current affairs and be prepared for regulatory changes. Has the board determined who will provide top-level sponsorship for upcoming cybersecurity-related legislation and regulation?
Have we tied in future economic drivers and digital transformation with their impacts on our cyber risk? And if so, how do we track, respond to, and budget for new threats? Do we understand the legal ramifications for the company?
We are in a constantly evolving landscape where people are now more aware than ever about securing their personal and private information. How can we champion a secure culture within the organization?
Industry resilience
Finally, we need to know that to stay resilient, we cannot do it alone. Collaboration is needed for our industry to be cyber resilient. The board should explore ways of participating with other information-sharing organizations within the wider ecosystem.
How are we doing in peer reviews? Do we know how we benchmark against other companies in the same industry and of a similar size?
As long as the board is aware of the preceding six criteria for success, they are on a strong footing and can use these criteria to guide them and their executive team accordingly.
The CISO’s seat at the table
As the CISO’s position evolves and develops, your organization must assess the success of its CISO by ensuring you hired the right candidate, asking yourself the following questions to do so:
- Is our CISO equipped with the necessary skills?
The good news is that there is no one-size-fits-all approach to success. A good CISO does not need a technical background or a degree from a well-known university. Indeed, research published by Digital Guardian found only 27 percent of CISOs have IT degrees, while those with computer science degrees accounted for 23 percent.
Modern-day CISOs need to have good management and leadership skills and recognize cybersecurity as a business risk. The CISO needs to collaborate with leadership to establish a shared understanding of security architecture, define the responsibilities of IT and security operations, and deliver outcomes via the development of the relevant team and internal connections. In summary, you need to establish the CISO’s suitability for the C-suite by making sensible judgments and engaging with other company executives as peers.
- Is our CISO capable of succinctly communicating risks—including current threats, probability, and impacts—in language that corporate leaders and the board of directors can comprehend, support, and act on?
CISOs must have an intuitive understanding of which facts and concerns should be brought to the board’s attention and the ability to communicate them effectively. When cyber risks are explained in financial terms, the board is more likely to comprehend their implications and approve investment requests, no longer seeing it as just a cost.
- Is our CISO capable of advancing the enterprise’s cybersecurity risk management to a more precise level?
The CISO is accountable for developing and executing a cyber-risk plan that safeguards critical information assets via the use of cost-effective, risk-based measures. The critical first step in managing cyber risk—or any operational risk—is to define the risk.
In understanding the key goals of your CISO, how can you provide them the much-needed support for them to succeed in their role? Simple: sit down, grab a cup of coffee, and enjoy a frank discussion. Your conversations with your CISO should focus on the burning questions about the business, security challenges, and thoughts about cybersecurity policy.
C-suite executives and board members must support and empower the CISO—this is particularly critical. CISOs have the ability to create change, which is crucial for the success and survival of businesses today. Boards of directors and C-suite executives must ensure that they pick and then support the CISO in their increasingly crucial position inside the organization. Additionally, boards and C-suite executives must reinforce the message that all leaders across the organization are responsible for cybersecurity and must collaborate with the CISO and be responsive and embrace their own specific cybersecurity responsibilities. It is the only way to ensure the business’s continued success.
Speaking the board’s language
When the board of directors fails to interact with critical risks, including cyber risk, to the same extent they engage with rewards and opportunities, this is referred to as board risk blindness. This certainly can be avoided if the CISO employs a proper communication strategy.
An aware and involved CEO and board of directors seek updates on cyber risk, do not treat it as a simple and small IT problem, and entrust their CISO with a cyber-risk management strategy and roadmap. The CEO and the board need to feel confident that, in the event of a breach, appropriate measures are part of the business continuity plan and disaster response plan to minimize the damage to consumers in particular and the firm in general.
Although cybersecurity has been increasingly declared a high-priority issue for many board directors (72 percent of the AICD survey respondents indicate it as so), it is interesting to note that most boards indicate they still have yet to receive regular reporting on key cyber issues, not to mention internal cyber training and testing. Only 36 percent of boards receive regular reports, which means that staff within an organization might not be getting the appropriate message about the importance of cyber vigilance.
Also, in the same survey (see Figure 10.1), only one in five directors receive regular updates on the cyber risk that comes from their supply chain relationships, which should be another important risk consideration for the business.
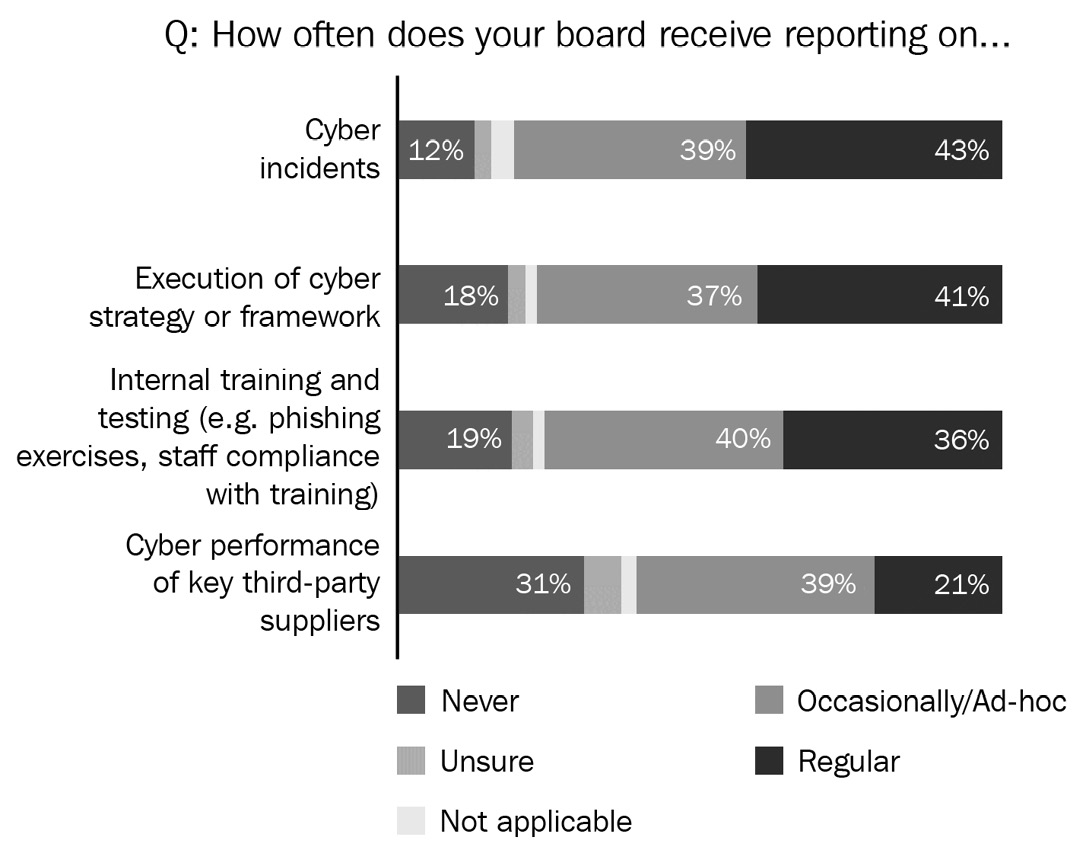
Figure 10.1 – AICD survey findings of board-reporting cyber-risk areas
In ensuring the right message is conveyed to the board, people presenting to the board need to understand how the board thinks before talking to them.
Most people are unfamiliar with the environment of the boardroom and what goes on behind the scenes. To understand how the board thinks, it is important to understand who the board members are.
Here are a few things to know when engaging with the board:
- The board is expected to have read the board pack sent to them ahead of the presentation.
- Generally, 10 to 20 minutes is taken for each presentation item, followed by a period for questions.
- The chair always provides adequate time for board members to ask questions. It is the responsibility of the board members to ask questions and to have done their own due diligence.
Michelle Beveridge, chair and board director of several committees across finance, education, and government, shares her preference: “Personally, I like to receive the recommendations right at the beginning of a board paper. That way I know what I am making a decision on, where to focus, and what other research I might need to do. This format makes so much of a difference!
“Most board packs are 200+ pages, and I would like to know what I should be looking out for to make a decision in the best interests of the relevant stakeholders. A good board paper will tell me this upfront.”
- The material presented to the board must be relatively easy to understand for everyone, since board members usually have different backgrounds. A total lack of questions following a presentation is often due to three reasons: low strategic materiality of the discussed item, a lack of interest, or a lack of understanding. If a board does not understand what was presented, then the presenter needs to re-evaluate their content and approach.
- Board members understand business risks, the language of revenues and margins, risk mitigation, compliance requirements, and legal ramifications. Presentations should be given in those contexts. Keep technical jargon out of it.
- Every presentation must include a recommendation to the board, from which the board members must clearly understand what they are asked to do as decision makers (be it approval or simply taking note), what you need from them in terms of resources, what the timeline is for implementation, and what risks/issues the company will face (if applicable).
Magda recalls a few positive experiences; one in particular with the board of a financial institution. The feedback was that the presentation was succinct, clear, and within the assigned time. Another experience was very different, but equally positive. Magda gave a presentation to the board of a publicly traded multinational oil and gas company. She was extremely surprised by the interest from the board members. Some mentioned exceptional insights. She had studied the business’s priorities and initiatives and showed how current and future cybersecurity initiatives work to mitigate the associated risk, and quantified the potential residual risk. She also described the gaps and the required investment. The conversation went on for an hour and a half, as a few board members canceled other meetings to ask further questions. It was a unique experience, and a very enjoyable one for all parties. The presentation turned into a discussion with the board.
What not to do in the boardroom
As a result of the increase in global rules and legislation, cyber-risk management increasingly is part of the board’s agenda.
Cybersecurity is complex. There is a plethora of expertise, guidelines, standards, requirements, and vulnerabilities, among other matters. However, there is a growing emphasis on avoiding extra complexity and ensuring that cyber-risk management contributes to the enhancement of current company structures by acting as an integrated part of established processes, rather than in opposition to them. This requires a common understanding of the impact of cyber risk on company goals and good communication between business executives, the CISO, and the board.
The CISO’s role is to make sure the board understands the threats cyber poses to the business and should have a place on almost every board agenda. A key question for CISOs to ask themselves before every board presentation is: Are we overcomplicating things?
In several of Shamane’s fireside chats with board chairpersons and directors, the highlighted their common frustration with technical experts getting too technical in their presentations: “If you present something and the board does not understand what you are saying, they leave the meeting thinking you’re too incompetent to explain things.” Keep things simple.
Magda recalls one board member saying every cybersecurity expert speaks their own language, and that they—board directors—don’t understand it.
Are we selling our message using fear?
Yes, cybersecurity is a risk. However, it is not the only risk that matters to the board. Delivering your message using fear might be useful only so often, and it can also backfire if the board becomes desensitized. Show how cyber risk affects investors and organizational risk in the bigger scheme of things.
Are we being the roadblock?
The role of cybersecurity is to solve the problem of cyberthreats and cyber risks. Decisions around risk avoidance should be made by the business owner, not the CISO. The CISO is there to help the board understand the risks and provide it with options that either mitigate, reduce, or transfer that risk.
Reporting to the board (an add-on for CISOs and a reference for CEOs)
Reporting to the board of directors about cyber risk should be done in plain English so that the board can quickly get a sense of what is happening within the organization. A cyber-reporting structure aligned with the business strategic initiatives or scorecard generated by the CISO may assist the board of directors in assessing existing cyber risks and tracking progress in cybersecurity.
A multi-year strategic plan, a current-year business strategy, resources, a cyber-training program, and other relevant information regarding the company’s cyber operations should all be made available to the board for a comprehensive picture of the company’s cyber activities, again in alignment with the strategic business initiatives.
According to a recent poll done by the Ponemon Institute, just 9 percent of security teams believe they are extremely successful in conveying security threats to the board of directors and other C-suite executives.
A CISO may feel that communicating the relevance of an organization’s cyber-risk program to an audience that sees cybersecurity as yet another tough-to-comprehend technical issue is impossible. Consequently, many security-related decisions are made by the board and the C-suite based on gut instinct and inadequate information. Or worse, decisions are not made and those organizations remains particularly vulnerable to cyber threats.
Today’s CISOs must define metrics and quantify cyber risks to make more informed decisions. These efforts assist in the prioritization of the most significant cyberthreats and the alignment of capital allocation requirements with those risks. They assist in ensuring that cyber funds are directed to the areas that will most affect the firm. It is this language that is understood by most boards and C-level executives.
At the end of the day, the amount of cyber risk must be compatible with the organization’s risk appetite. Specifically, boards of directors want to know whether management is focusing on the appropriate cyber risks, how management manages those risks, and whether the efforts are sufficient. This begins with gaining an overview of the company’s cyber-risk management program as well as its cyber-risk tolerance.
Magda uses the report template in Figure 10.2 after carefully studying the financial reports of a company.
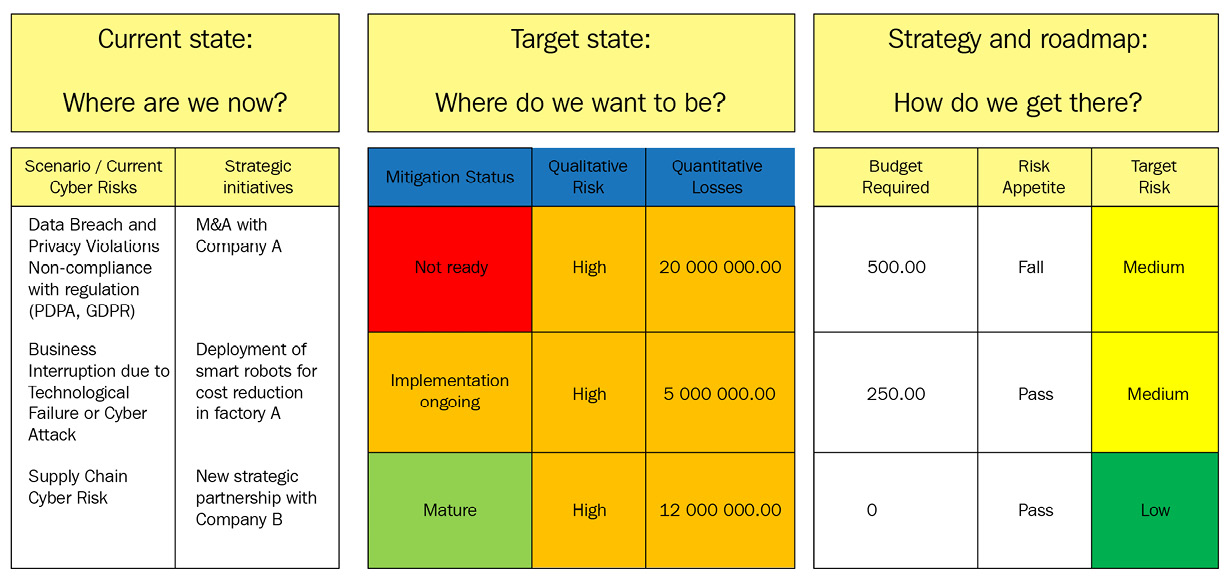
Figure 10.2 – Example of reporting
Different scenarios need to be explained and then tied back to the strategic business initiatives.
Boards and mergers and acquisitions
Cyber risk considerations for mergers and acquisitions are increasingly important. In fact, investing in a company with low cyber maturity might result in massive financial losses and incorrect valuations, and eventually lead to reputational damage in the event of a cyberattack or data breach.
At various stages of a merger and acquisition (M&A), various risks exist—from information leakage prior to public disclosure, from the risk of insider threats, from disgruntled employees stealing valuable intellectual property fearing changes and dismissal, from the unadjusted risk as two organizations merge, potentially resulting in contagion between the two entities or conflicting approaches being exploited. The timing of M&A transactions is always a delicate balance between speed and risk—the need to consummate the transaction quickly before values rise and to exploit new business opportunities (to unlock value), and the danger of not doing enough due diligence.
During the course of an M&A, cyber risk will change at different stages, each stage necessitating careful consideration. In addition, unforeseen changes in the risk profile, uneven trust levels, and contradictory approaches to policy and compliance, for example, SOX, PCI DSS, FCA DSS, ISO 27001, and the EU’s GPDR (which replaced the Data Protection Act), among other things, might all have an influence.
The board and the CEO should consider whether elements of the security program may be taken into account during the negotiation phase, and bring the CISO on board as appropriate.
The following section focuses on the questions to ask yourself—the CEO—and the board to build your organization’s cyber resilience.
Asking the board the right questions and setting up your CISO for success
It is the responsibility of the CEO and the board to discuss the following questions in to achieve cyber resilience:
- Do we have a collaborative approach to emerging cyber-risk issues? Consider whether or not the top executives in charge of developing risk management strategies and resilience are working together with the CISO toward a single objective of achieving success.
- How responsive and adaptable are we in the face of cyber threats and our management of them? Cyber risk might still be considered an IT problem, or lack integration with enterprise risk management processes, or just be seen as a compliance exercise (for example, achieving an ISO 27001:2013 certification). However, this is not enough to enable and build effective cyber resilience. Senior management should take a close look at cyber risk and collaborate to identify, quantify, treat, and transfer that cyber risk. They also should be aware of the proportion of cyber risk the organization handles as opposed to third parties, potential partners, or during an M&A.
- Are we forecasting and anticipating cyber risks as they emerge? The CEO and the CISO should support the board to look at future changes and their implications—for example, emerging technologies such as quantum computing, which has the very real potential of disrupting traditional security controls. This is very important, as it might require years of planning and significant budget resources.
- Do we have the right metrics in place? As firms confront an increasing variety of cyber risks that are complex and interlinked with other risks, many of the classic methods of presenting and measuring cyber risk may no longer be appropriate or effective. Boards of directors and C-suite executives should evaluate relevant indicators to inform and progress their business’s decision-making.
In the end, businesses that flourish in this age of growing complexity will be those that distinguish themselves in their risk management, and the way in which they employ risk capital to remove the risk from innovation and growth as much as possible.
How the board of directors and CEO address these questions will enable the CISO to develop appropriate cybersecurity strategies, build business continuity plans, and effectuate disaster recover procedures. It is all an essential part of the success of a CISO and a firm’s cyber resilience.
Summary
Managing cyber risk is difficult for almost every firm and its board of directors. Cybersecurity is a sophisticated technological field in which new threats emerge almost weekly. Despite the fact that most board members are not cyber professionals, boards of directors have a duty to recognize and monitor this risk. This requires active participation with leadership and access to experts, as well as comprehensive information and reporting from an organization’s upper management.
Specifically, boards of directors want to know whether management is focusing on the appropriate cyber risks, how management manages those risks, and whether the efforts are sufficient. This begins with gaining an overview of a company’s cyber-risk management program as well as its cyber-risk tolerance.
Furthermore, some boards have determined that cybersecurity is a risk that requires the oversight of the whole board, rather than a specific committee. Whatever the case, if supervision is delegated to a board committee, it is critical the whole board receives frequent and complete reports.
It remains beneficial to review the board’s means of oversight on a regular basis to ensure they continue to function properly. Among the factors to evaluate are whether the existing structure engages the appropriate board members and whether they have sufficient time to handle the issue in question. It’s also critical to ensure your board has access to the right subject matter experts it needs. Many boards of directors look for candidates with experience in cybersecurity. This may be beneficial but has some cons as well, particularly when the expertise is limited. The presence of a cyber specialist on the board may cause other directors to be less likely to express their thoughts on the subject.
The fact that this topic is so wide-ranging might make it difficult to devise a plan for approaching board presentations, which can be a challenge. However, it remains a critical part of building a resilient business nowadays with increasing technological dependency and complex ecosystems.
By understanding the importance of cyber resilience and implementing the necessary measures, your business can protect itself from these threats. The final chapter will discuss cyber culture and the importance of businesses bringing all the previous recommendations together to build the right business culture.
