Working with Your CISO
The Chief Information Security Officer (CISO) or Chief Security Officer (CSO) of an organization ensures the organization’s personnel, physical infrastructure, and digital assets are available to the business and protected from unauthorized access, loss, theft, or disruption and physical damage through appropriate cyber risk management.
Security breaches exploit people, processes, and technology. It is no longer a technical problem but a business risk and must be treated as such. Efficient recommendations need to be provided for controls across the elements of people, processes, and technology, mitigating cyber risk in alignment with the company’s risk appetite. This is the responsibility of the CISO in collaboration with their CxO peers.
The shift in focus on cybersecurity—integrating cyber risk into the overall enterprise risk management process—underpins the foundations of this chapter.
A good CISO should be a great communicator, a manager, and a thought leader with a foundational understanding of the business. They should report regularly to the executives and the board on cyber risks and clarify whether the company’s risk appetite and tolerance align with them.
In this chapter, we will cover the following topics:
- Understanding the role of the CISO
- Addressing cybersecurity challenges
- Your CISO’s understanding of your business
- Priorities for a new CISO
- Addressing cybersecurity challenges
- Questions to ask your CISO
- A bonus segment for our CISOs—decoding your CxOs’ expectations
- A bonus segment for our CISOs—purchasing cyber insurance
- A bonus segment for our CISOs—reporting to the board of directors
Understanding the role of the CISO
As CEO, your role is to challenge your CISO to think differently, to move beyond their technical knowledge and align their thinking with business priorities. It is in your interest to help the CISO succeed as a strategic partner, creating a framework that enables a business’s progress toward its goals while achieving security and privacy.
The role of a CISO is still greatly misunderstood, and while things are progressively improving, too many organizations have yet to hire a CISO. Many organizations still believe their security is a technical requirement provided by their IT department. In Asia, when Magda inquired about vendors’ cybersecurity, she was typically directed to an IT manager instead of a CISO.
Businesses that comprehend the expanding relevance and power of digitalization and digital transformation must appreciate the value of a CISO. The dependency on and increasingly faster adoption of new technologies means the consequences of a cyberattack or data breach can result in dire consequences.
The CISO’s primary responsibilities are to manage cybersecurity, mitigate cyber risks, and handle all cybersecurity incidents. These responsibilities extend to using controls and measures for people, processes, and technology to ensure the ever-expanding business landscape is duly defended from evolving cybersecurity threats. The CISO also needs to consider a complex and growing environment, with third- and fourth-party suppliers.
A CISO who takes a balanced approach between a business and its threats will ensure no significant gaps can form that might limit the effectiveness of any cybersecurity risk mitigations. In other words, the CISO’s cybersecurity strategy needs to be developed in lockstep with the organization’s business and technology strategy, which goes far beyond firewalls and antivirus solutions.
The CISO’s responsibilities include:
- Establishing a well-thought-out cybersecurity strategy that aligns with a wider business and technology strategy.
- Defining a robust cyber-risk management system and its associated processes.
- Developing a hierarchy of security governance and policy structures.
- Driving an appropriate cybersecurity awareness culture within an organization.
- Designing and developing a set of effective cybersecurity dashboards for management reporting.
- Having a broad view and understanding of the legal and regulatory obligations of the jurisdiction that a business falls within.
To perform these functions, a CISO must build their team with the skills and capabilities necessary to deliver the business strategy and key milestones.
The modern-day CISO, or the business CISO, as Shamane calls it, is great at communicating with other leaders in the organization. In addition to understanding the pros and cons of a traditional cybersecurity risk management framework, they report to the business stakeholders in a language a non-cybersecurity person can understand. The business CISO is an exceptional communicator, resourceful, and an influential manager—a great storyteller who can talk about cybersecurity and how it affects the organization.
Many CISOs first started their career in IT and have a deep technical background. This is not surprising because it takes years of study and practice before becoming qualified to lead such an important position within any organization. Nowadays, many CISOs also hold business degrees. CISOs need to have a deep understanding of both technology and business to make effective cybersecurity decisions.
Bridging the gap between technical jargon and a business is important, and while a CISO with a technical background helps, it does not preclude someone with no technology experience taking on the role of CISO.
To effectively perform the responsibilities listed earlier, it’s important for CISOs to have a strong understanding of the latest trends and developments both in emerging technologies and evolving cybercrimes to make sure their organization is prepared for whatever comes next.
Cybersecurity requires collaboration and buy-in across an organization. That must first come from the top. Under the direction of the CISOs, the leadership and board of directors must do the following:
- Understand who owns and is liable for cyber risk. Following a data breach or cyberattack, the board of directors, not the CISO, will bear most of the consequences, legal fines, and other impacts.
- Define cyber risk in the context of business risk. The majority of firms cannot appropriately define the cyber risk they face, nor the potential for substantial business disruption due to a cyberattack. Has your organization thought through the impact of a cyberattack, leading to a product recall? Probably not. It is vital to put such risks in a business context rather than considering them as technical issues.
- Quantify cyber risk through identifying, protecting, detecting, responding to, and recovering from cyberattacks.
- Consider the cybersecurity implications of third-party vendors and suppliers. They are often the weakest link, especially when cloud technologies are used and, too often, security is assumed by default. Generally, contractual provisions often do not include explicit reference to security or privacy obligations.
- Establish indicators for resilience and monitor your cyber maturity.
It is in the organization’s best interest to maximize the CISO’s value to apply a cyber risk management process and integrate it into the overarching risk management framework. In the following section, we will demystify important aspects of cybersecurity, the role of the CISO, and their understanding of the business.
Your CISO’s understanding of your business
Depending on their career progression and experience, some CISOs may have little to no understanding of the other areas of the business or the business itself. Because cyber resilience is a business risk, an effective CISO must align all cyber frameworks with the business goals.
A common misconception many CxO teams make about the CISO is that the CISO is an enforcer of security. Instead, the CxO team needs to appreciate that the CISO brings a boardroom-level, risk-focused conversation about the impact cyber risks have in terms of business disruption, data breaches, data loss, non-compliance with regulatory requirements, and so on. More crucially and specifically, the CISO understands the financial consequences of these risks, which can in extreme conditions affect the viability of the business itself.
The CISO needs to be a part of your corporate or enterprise risk management team. They must communicate with others on the team and understand their priorities; those on the risk management team must understand the priorities of the CISO.
Although the CISO is responsible for cyber risks, in the case of a breach or a cyberattack, business owners or company directors are ultimately accountable, not the CISO. Thus, the stakeholders must clearly understand cyber risks and the CISO must clearly understand the business priorities and goals. Neither can be achieved optimally without the other.
As part of the risk management team, a CISO should communicate cyber risks regularly with the business and learn about and understand the business goals and vision. If your CISO has the support of key stakeholders, you reduce the risk of your CISO failing and working in a void.
The challenges and roadblocks CISOs face in enforcing cyber resilience are not removed with this understanding, but they are reduced when everyone has a stake in building cyber resilience. It also enables the CISO, whether new to the company or shifting to a holistic business risk approach, to prioritize specific cybersecurity elements.
Priorities for a new CISO
The first months of a new CISO in an organization are crucial and represent a critical timeframe to align the organization’s business goals and objectives with cyber risks. It is during this period that a CISO establishes their credibility throughout the organization.
It is the establishment of this core cyber foundation that allows the CISO to create a security roadmap that includes mitigation controls that aligns with the organization’s risk appetite and business goals.
But first, it is critical for the CISO to understand the existing environment and culture of the organization before designing any strategy. For the CISO, the avenue to do this is in understanding the cyber challenges the organization faces, and what approaches the business has taken (or not) to mitigate them.
Addressing cybersecurity challenges
Organizations tend to underestimate the challenges cybersecurity presents. It is not something that can be addressed as a one-time exercise. A high focus remains on addressing cybersecurity challenges with a technology-based solution. However, cybersecurity challenges require a holistic approach across people, processes, and technology, and involve a continual journey of refactoring and improvements, and communication across the organization of what each person’s responsibilities are.
This is best illustrated by how an organization handles the risk of a ransomware threat. Ransomware threats will never be zero, as the business needs an internet presence and can’t avoid using email communication. Applying technology-based controls is often the very first step an organization takes to address this risk: implementing malware protection, firewalls, and even intrusion-detection systems. But these are just the first step. These solutions are technically sound but do not address the organization’s ability to respond when faced with such threats. Instead, a complete cybersecurity response plan needs to be defined and communicated:
- Provide awareness and training to ensure employees know not to click on malicious links or, at the very least, are aware of how to report it if they do.
- Run phishing exercises on all employees as a reminder of these lessons.
- Ensure a response plan is defined to handle this threat scenario.
- Undertake periodic table-top exercises to refine and improve the response process.
- Create a predefined set of internal and external communication plans.
- Draw up a predefined financial budget to help respond to threats.
Ransomware threats require more than the latest technology safeguards. Such is the case for all cyber risks. This also demonstrates the need for an organization-wide cybersecurity culture. If everyone is aware of cyber risks, and what they can and must do to prevent attacks, or what they can do in the event of one, the organization will be better protected. It necessitates that everyone, from the board and CEO down, to recognize cyber as a business risk that needs to be addressed proactively in a continuous manner and not reactively.
To that end, it must be communicated (as appropriate), accepted, and reinforced that:
- There is no “end state” in cybersecurity. The CISO will prepare an organization for as many cybersecurity threats as possible and will prepare to respond to cyberattacks when they happen. The required controls to mitigate the cyber risks of your business will align with the risk tolerance of the organization.
- Cybersecurity controls go beyond technical solutions such as antivirus, a firewall, and other expensive tools. There should always be a balance between people (that is, roles and responsibilities), processes (that is, defined procedures), and technology solutions.
- It is not a question of if but when your organization will be a victim of cybercrime. Many malicious hackers or cybercriminals are capable of compromising your systems quietly and without attracting attention. So, if you are not looking for them, it may seem as if your data has not been compromised. Unlike physical assets, data assets can be stolen without removing the original copies. Despite the security controls the CISO defines in their roadmap, your company can still become a victim of a cyberattack.
- A CISO cannot guarantee that cyberattacks will not affect your organization. The CISO will ensure your cyber risk is mitigated and treated according to your risk tolerance. They will help minimize the likelihood and frequency of attacks with preventative and detective controls. They will also minimize the business impact and damage through corrective controls and help your organization resume normal operations faster.
- The cybersecurity strategy is effective when your organization is able to detect and respond to a cybersecurity incident quickly, continue business operations, and recover from the incident with the least amount of business impact.
- You should ensure your organization has a well-documented and well-rehearsed security incident response process and plan, a business continuity plan, and a disaster recovery plan (which will be covered further in Chapter 10, The World of the Board).
Cybersecurity must be a concern and responsibility, led by the CISO, of everyone in the organization. As CEO, it’s crucial to empower your CISO to achieve cyber resilience in your organization. Their understanding of the business is key to this.
With a foundational understanding of the business, there then are core fundamentals the CISO has to address to establish a security framework. Cyber-risk identification and quantification management strategies, and cybersecurity metrics and indicators for dashboarding/reporting, are the starting point for building cyber resilience.
Cyber risk identification and quantification
In addressing an organization’s cyber risks, a CISO must have some visibility of the organization’s cyber exposure. Here is where the challenge starts.
The CISO might inherit an existent risk register with a list of identified cyber risks for a business. More often than not, those risks have been defined or described in multiple scenarios as IT security risks and not cyber risks. Often, security professionals associate a cyber risk with a technical IT risk—for example, describing a cyber risk as a Distributed Denial of Service (DDoS) attack, where a service or network is flooded with traffic thereby preventing legitimate users access. When attacks such as this are described solely as an IT problem, it closes the door to the business stakeholders, as it is not thought they can offer any value to the solution. In fact, such risks, when described as business disruptions, are opportunities for a business discussion.
Conversely, many of today’s cybersecurity practitioners, having spent time in a cybersecurity risk silo, are trained in traditional qualitative frameworks, the “red, yellow, green” or “high, medium, low” risk classification paradigm. The lack of clarity, precision, and expressiveness inherent in this paradigm is a significant impediment to business risk management initiatives. Instead of broadening the risk assessment and mitigation in the larger business risk context, it silos the response and any solution runs the risk of being a stop-gap effort, unique only to the specific incident. Cybersecurity risk management that is built on instinct cannot objectively measure the risk with accurate financial figures. The CISO with a holistic approach and an understanding of business goals and risks should be prepared with an appropriate remedy.
While this framework has its own benefits, it does not allow security professionals and, especially, CISOs to answer the following questions:
- What is the probability that the company will be the victim of a significant cyber incident in the next six months?
- Is the risk higher than 60 percent?
- What are the financial consequences?
- What are the potential scenarios?
These are important questions, but this framework does not support clear communication with key business stakeholders where they can understand an organization’s cyber risks. Without this understanding, it is difficult to attain the support for the necessary investments to mitigate/treat or transfer the cyberthreat in alignment with their risk tolerance. Therefore, it is crucial to put financial numbers to cyber risks, ensuring the visibility of the potential financial losses following cyberattacks and/or data breaches.
When the CISO identifies possible financial consequences, the board of directors and the C-suite can collaborate more effectively on strategic cybersecurity initiatives. A successful CISO should be capable of identifying and matching an organization’s security investment to the board’s risk tolerance, and in a diplomatic manner. This awareness, and acceptance, of cyber risk better positions the CISO to build effective mitigation measures by investing in security controls and identifying risks that may be transferred through cyber insurance.
This is the primary benefit of using a quantitative framework—adding accuracy and defensibility to cyber risk, with measurable outcomes. It is an undeniable benefit for CISOs to understand the organization’s exposures, prioritize cyber initiatives, request additional budgets, and, especially, prove the cybersecurity return on investment (ROI).
Another tool CISOs should focus on are scenario analyses: predicting the financial impact and severity of cyberattacks with reasonable accuracy. While calculating the probability of an occurrence, such as a successful phishing effort or ransomware attack, is difficult, the CISO can modify quantitative models to account for their organization’s risk profiles and relevant situations. CISOs can support the business by quantifying the impact of a cyberattack rather than focusing on the probability alone. While specialists have a variety of models at their disposal, no model is perfect. We will provide further details on this in the A Bonus Segment for Our CISOs sections in the second part of this chapter.
Once the CISO has identified and assessed the company’s cyber risk, the next step is to look at the various ways they can handle those risks.
The different approaches to handling your cyber risk
There are various approaches to addressed cyber risk. One is risk acceptance, which is when an organization recognizes that the potential loss associated with risk is insufficient to justify investing money to prevent it. This also holds true for cyber risk. If the cyber risk incurred does not exceed your risk appetite, you may accept it.
Eliminating risk is the simplest and most often overlooked strategy of risk management. This is a technique that should be used whenever feasible, since it entails simple risk removal.
Risk termination may be used, particularly in the context of merger and acquisition (M&A) due diligence, when a deal fails to close due to significant cyber risks affecting the company acquisition costs, future investments, and possible substantial residual cyber risks and expenditures.
Cyber risk transfer is a topic that increasingly interests boards because of the liquidity and cash support it brings to a business in case of financial losses following a cyberattack.
Risk transfer includes the transfer of future risks or hazards to another party. Purchasing insurance is one of the most frequent forms of risk management generally and cyber risk specifically. It transfers a business’s risk to a third party, in this case an insurance company. The transfer of residual risks ensures the recovery of any losses and maintain cash flow and business liquidity.
Cyber insurance is a catch-all word that refers to a variety of insurance policies. Defining cyber insurance is not easy, considering the evolving cyber threats and risks. A former colleague of Magda’s likened it to a growing teenager.
At its simplest, cyber insurance is a contract between an insurance carrier and a business that protects the business against financial losses caused by computer- or network-based incidents. Yet it is unrealistic to anticipate a full list of coverage, since insurers often apply policy extensions in response to the dynamic nature of cyber risk. However, the following list contains those most commonly encountered and accounted for in a cyber insurance policy:
- First-party coverage for the cost of replacing or restoring lost data
- Data privacy and network coverage for the liability claims of a third party
- Business interruption coverage for revenues lost as a result of network downtime
- Cyber-extortion coverage for investigation costs and, sometimes, the extortion demand as well
- Fees for PR firms to manage the business’s reputation in the event of a breach
- Legal costs due to litigation or lawsuits
The list is not comprehensive of all the types of potential cyberattacks. For example, it does not include financial crime or financial fraud while using a computer. This is commonly covered under commercial crime policies and is an important insurance coverage due to the increasing number of social engineering attacks, such as phishing attacks or other means of manipulating a person or people to gain access to a system or networks.
Insurance providers no longer provide cyber insurance coverage without an extensive assessment of a company’s cybersecurity posture (or what is called underwriting data). Thus, it is becoming harder to get optimal coverage for all cyber risks as companies sometimes do not even have the fundamental controls in place to manage cyber risks.
Nonetheless, cyber insurance remains an important control for any cybersecurity strategy. A CISO must consider it as leverage for cash flow management and liquidity control when a cyberattack happens. A CISO new to the organization should review and update the cyber insurance the organization has, or if there is no policy, recommend insurance be purchased to protect the company.
Cyber risk management strategy
Once the CISO is aware of the cyber risk they are working with and the various ways of mitigating it, the next step is to formulate the organization’s cybersecurity vision and strategy.
The CISO’s main objective is establishing business cyber resilience and managing cyber risk, which can only be effective if security is incorporated into all planned investments and initiatives. In addition, the CISO needs to take into account the reliance of existing digital tools and services, combined with the likelihood of increased remote working and extensive dependence on third-party suppliers. This may require significant investment.
The CISO should prepare a strategy and associated roadmap, outlining the organization’s capabilities to achieve technical and strategic cyber resilience. A clear cyber strategy must align with all important business decisions, as well as a defined roadmap for cyber-risk management.
Specifically, the cyber strategy involves estimating exposures, implementing the right mix of technology solutions and processes, and developing specific recovery plans in the event of a breach. Additionally, the strategy should outline how the organization will manage its ties with partners and third-party vendors worldwide to extend your organization’s cyber capability and visibility, moving your cyber capabilities from a siloed function to a resilient and cyber-ready ecosystem.
Further, the CISO will introduce several new strategic initiatives. These include initiatives around governance, processes, culture, and new technological tools. The strategy usually includes initiatives to be implemented within the first three, or even the first five years, for detecting, preventing, and responding to cyberthreats.
One purpose of this strategy should be to establish stronger lines of communication to the C-level and board of directors about cyber risk, focusing on measures or key performance indicators (further explained in the Cybersecurity Metrics section) to evaluate the organization’s cyber maturity progression over the next few years.
Under the cybersecurity strategy, the CISO might define a budget for the initiatives they plan. For example, Magda uses the costs in her high-level draft roadmap and then updates her strategy with the budget requirements.
Once the strategy is in place, it is then supported by a roadmap with initiatives that address the following areas:
- Protect: These initiatives are intended to deploy and verify adequate cybersecurity protections in place for your organization’s systems, networks, and facilities.
Included in protection initiatives are risk identification; mitigation measures spanning people, processes, and technology; and the development of a cyber culture across the firm. Now, the strategy can include concepts such as zero-trust.
Zero trust represents a fundamental change in the way organizations think about security. It starts with the assumption that both users and devices cannot be trusted at face value regardless of their location, and all access requests must be verified before being allowed access to resources. This is a major shift from the traditional perimeter-based security model, which placed inherit trust inside the walls of the organization and blocked external access altogether. In a post-pandemic, modern technology world, our assets are no longer always within the four walls of organization, opening up major holes in our perimeter-based approach of old. Zero trust modernizes this approach—embracing the new way of working while bolstering security both inside and outside our organization’s four walls. However, it is important to mention that enabling fundamental controls is still required first before aiming to adopt newly emerging concepts and industry buzzword solutions.
- Detect: These initiatives are used to ascertain the degree to which your organization promptly uncovers cybersecurity incidents. Following protection and mitigation, a CISO provides an organization with the tools necessary to identify any suspicious behavior or incident.
- Respond: These initiatives are intended to verify the organization has policies and processes in place that outline how the company will respond to cybersecurity incidents. Your organization should have an incident response plan as part of the business continuity plan. It should be tested regularly while engaging the correct stakeholders in the response actions required to mitigate the effect of an attack. As CISO, you provide your organization with the tools necessary to react to security or data breach incidents.
- Recover: Those initiatives are to guarantee the organization plans for and executes suitable resilience operations restoring any capabilities/services that have been compromised as a result of a cyber incident. The recovery function mitigates the damage caused by a cyber incident. The CISO ensures a proper recovery following a cyber incident.
The following figure showcases the National Institute of Standards and Technology (NIST) government agency cybersecurity framework used by many CISOs as a good baseline of controls to follow while preparing their roadmaps.

Figure 5.1 – The NIST framework
CISOs use frameworks to ensure full coverage of cybersecurity controls; however, the key is to ensure relevance to an organization itself. This is done using metrics to support improvement and corrective actions.
Cybersecurity metrics
Key performance indicators (KPIs) are beneficial for the CISO to assess the performance of the cybersecurity program and assist with decision-making. One popular maturity model is ISACA’s Capability Maturity Model Integration (CMMI), a product and service development maturity model created by Carnegie Mellon University’s Software Engineering Institute.
The defined CMMI procedures chosen for integration with risk management processes include actions that lead organizations to implement highly mature development and service processes. CMMI procedures are general in nature and may be applied to a wide variety of specific business processes. CMMI has a broad scope and, hence, may be used to incorporate IT risk management into the (re-)design phase of any kind of IT process, meaning IT risk management can be integrated into the efforts to enhance IT processes or cybersecurity.
The following figure showcases examples of the maturity levels.
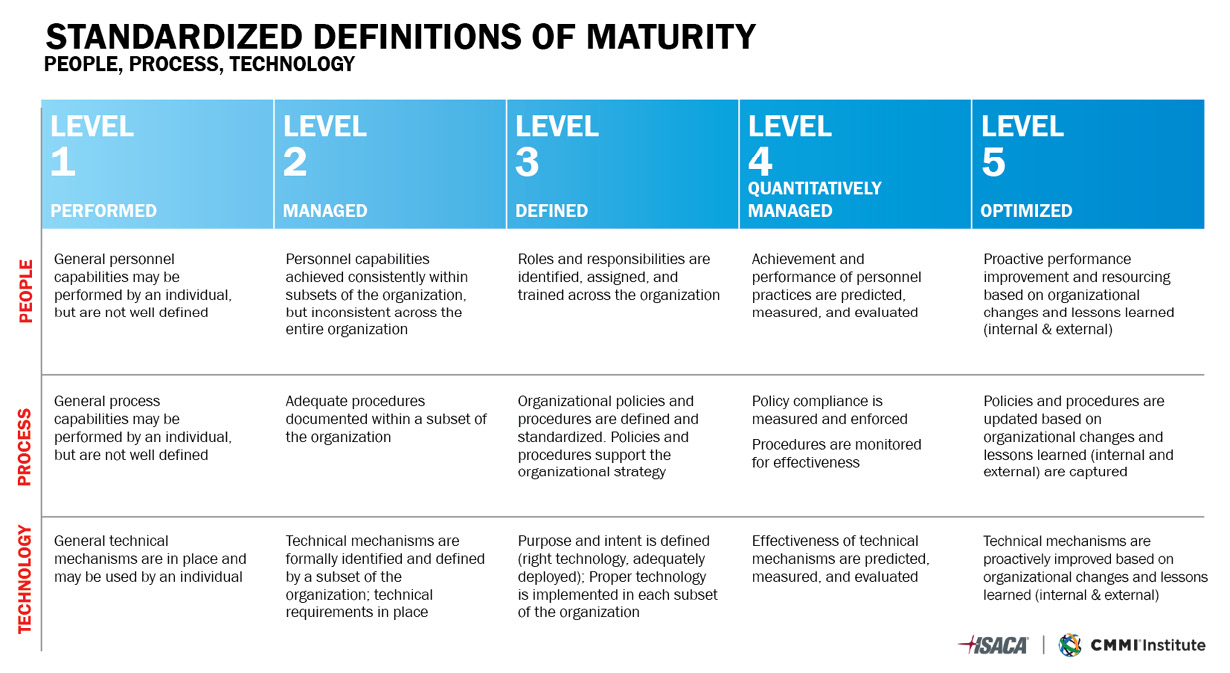
Figure 5.2 – Maturity models
Maturity is certainly a good indicator. Nonetheless, CISOs need to have a better understanding of the company’s cyber maturity and its alignment with business expectations. However, when it comes to reporting metrics to the board, it is crucial the CISO keeps it relevant and concise.
Creating dashboards to capture and report data are important to validate the cyber strategy and roadmap.
Indicators for dashboarding/reporting
The clearest way for a CISO to bring all stakeholders on board with the organization’s cyber strategy is to present the indicators relevant to them. Those likely include:
- New business initiatives and associated cyber risks.
- Unmitigated cyber risks and the cost associated versus forecasted costs.
- Transferred risks and gaps.
- Intrusion attempts.
- Rates of incidents, their severity, reaction times, and the time required for recovery.
- Response times for vulnerability patches.
Questions to ask your CISO
Because the CISO is the focal point for cybersecurity, the following questions help you determine if your CISO is leading your cyber resilience effectively. For CISOs, this is a helpful way of assessing this for yourselves.
- How do our strategy and roadmap address our business priorities?
- What is our residual risk, and how do we measure it?
- What are our major black swan events?
- What is the potential financial loss following a cyberattack?
- What is the potential loss following a data breach?
- How do we measure our ROI?
- How do we monitor improvement?
- What is our response when a cyber incident or data breach happens?
- How do we recover associated costs?
In the next part of this chapter, we include bonus segments for our CISOs. The segments include tips and advice for aspiring CISOs. They are also good recommendations for C-suite executives to read while trying to leverage further knowledge on cybersecurity and to help support their CISO. To this end, we will next take a look at decoding your CxO’s expectations.
A Bonus Segment for Our CISOs—Decoding Your CxOs’ Expectations
Boards of directors have a challenging task when it comes to cybersecurity. On one hand, they must guarantee their business remains competitive and profitable, adopting technology and executing digital transformations to stay ahead of the market. On the other hand, they must ensure their business is cyber-ready and compliant with applicable laws and regulations around privacy and cybersecurity.
Over the decades, there have been plenty of technical discussions around cybersecurity. However, the presentation ends pretty quickly when presented to the board or other CxOs if the CISO is not clear in their communication and/or uses too much technical jargon.
Every professional, including the CISO, has a domain of expertise and feels comfortable discussing that skill set. Nonetheless, a modern CISO needs to adapt further, as the expectations are higher, often putting themselves outside their comfort zone. They need to understand the other CxOs’ challenges and priorities and put themselves in their shoes to build trust and have effective communication. The expectations of your CxOs in cyber briefings differ from each other but subtly yield significantly similar outcomes—cybersecurity benefits for their initiatives and roles. Once the CISO decodes the rubrics of each executive’s expectations, aligning the responses to each of the target CxOs becomes a less onerous task.
A CISO needs to build a reputation as an enabler of the business and not an inhibitor. They need to realize and understand that the first goal of the business is business and not cybersecurity. The business objective is to generate a profitable product or service, ensuring higher gains and growth. The CISO adapts the business perspective to achieve the optimal cyber strategy.
The CISO communicates cyber risk to CxOs through routine updates or reports—for example, a company-wide quarterly executive meeting. However, communicating should occur more often than quarterly. Cyber reports sometimes have to be sent via email. Thus, it is critical that the routine updates or reports are clear and simple, and identify anticipated questions that might be on the CxOs’ minds and provide answers.
Key Communication Non-negotiables
“Simple reports often work the best,” says Dr. Siva Sivasubramanian, CISO at telecoms giant Optus. Siva provided examples of the different approaches a CISO can take for the various stakeholders:
- The CFO and CRO focus on the risks of the cyber issues that have the potential to impact an organization, particularly in specific operational domains. They need to know how initiatives that are underway, and those that are planned, will mitigate those risks. They need quantified responses with clear and defendable figures.
Often, the CISO will struggle to provide these responses, as they are more comfortable with qualitative risk assessments. The reports to the CRO and CFO must be in business-speak and risk-focused, with a clear articulation of ROI and quantified risk reduction per dollar spent. Strict avoidance of cyber buzzwords is critical. Every statement must be logically and quantitatively defensible with facts and figures. Engaging finance or risk groups when preparing the report will help.
Here are some quick tips:
- Present easily understandable relevant data to the CFO in simple tables.
- Avoid complex diagrams or graphs that are technical and unrelated to the CFO’s priorities.
- Have a cohesive storyline of the problem (for example, what is being done, what will be done, how it will eliminate or mitigate the problem, and the cost and timeline involved).
- Chief Human Resource Officers (CHROs) are often not tech-savvy but are widely read. They quickly get excited about media reports on recent cyberattacks and their impact on corporations.
The CHRO’s focus is centered entirely on the human and organizational aspect of implementing cyber protection. To them, employees mean an aggregation of direct employees, contractors, and third-party vendor resources both on- and off-premises. Their concern is on the logistics of getting staff to participate and act per directions. They also need metrics to measure what constitutes action and how inaction should be handled. In addition, the CHRO likely will seek some assurance that the proposed activity will be effective, as they are wary of employee fallout from botched activities.
CISO statements such as “security is everyone’s responsibility” and “employees must be held accountable for security,” without actionable recommendations and simple explanations, will concern the CHRO, as such statements are overly broad. Statements free of rhetoric with quantifiable measures of compliance and suggested responses to noncompliance (limit these to educating and bringing into the fold; avoid punitive recommendations) will hit the target for a CHRO.
- Ensure your presentation is simple and relevant to the CHRO.
- Integrate privacy and compliance, as they are easily understood by CHROs.
- Articulate what is expected and how that could be achieved for the CHRO.
- Suggest methods and compensating controls to bring noncompliant matters on board.
- Have a clear storyline (for example, the problem, the broader solution the company is following, the human aspect of the solution, and what is expected from the HR department).
- The CEO and board of directors are the most demanding stakeholders to deal with. Both expect all the details condensed and presented in a prescribed format that is usually very short and rigidly structured. They are masters of words and read between the lines. Every word in the report has to be well crafted, and the narrative must flow well. The report must be reviewed and ratified by their reporting lines or their team members to ensure it aligns with their expectations.
The CISO report and/or dashboards must be in business speak, provide a comprehensive picture of the problem, and call out the unknowns candidly. Any risk called out must be fully supported by the risk group. Any solution suggested must be ratified by relevant stakeholder groups. The board and CEO view solutions as team responses from the stakeholders. Therefore, the CISO’s report should be a team response from the different stakeholders, with the CISO functioning as the presenter.
Here are some quick tips:
- Align with the business priorities.
- Focus on the risk and not the technicalities.
- Talk dollars and not threats.
- Maintain a strong narrative and have proof for every point made.
- Craft every sentence well; check for potential alternative interpretations and edit or delete them.
- Do not include any unnecessary words; keep the sentences sharp and make every word count.
- Avoid complex graphs and pictures; provide simple visual aids to substantiate your message without the need for explanation.
- Have the report reviewed, ratified, and agreed to by the stakeholders.
Cyber Risk Quantification—the Holy Grail for Your Success
Cyber risk quantification has been mentioned several times throughout this book. It is increasingly considered an irreplaceable tool to address the gap between cybersecurity and business.
Enterprises long have used risk management to assess financial risks and operational risks, among others. The traditional risk management process has evolved along with a business’s scope, size, and value, and each category of risk (operational, cyber, financial, and so on) has been followed by its own risk approach and methodologies in the risk management process.
Today, business risk management techniques need to be adapted because most businesses are either technology-dependent or rely on IT to run their operations. In reality, though, we still face significant divergence in the understanding of stakeholders of risk management language, especially regarding cyber risks. This distinction is particularly pronounced between business managers and IT security, risk analysts, and CISOs. Because of this misalignment, companies continue to face challenges in implementing important controls to mitigate their risks.
Cybersecurity experts have long used qualitative frameworks for years – “green, yellow, and red” or “low, medium, and high” are on most CISO’s risk registers and, sometimes, combined with cyberthreats such as ransomware or DDoS. But this framework has little meaning to the CEO, board, or other stakeholders. Using qualitative descriptions remains subjective—especially for business stakeholders who need precise information about the potential consequences of a cyberattack. What might seem critical or high for one individual might appear green or yellow for another.
Instead, having solid quantitative estimates for both impact and probability enables CISOs and business stakeholders to be prepared in the event of a cyberattack.
Magda has addressed quantification on various levels, following extensive published research and the development of techniques and quantification models. She believes many lack industry standards or do not have potential global applications in the cyber-industry space. The most popular quantification framework is Factor Analysis of Information Risk (FAIR), which emerged as the premier Value at Risk (VaR) framework for cybersecurity.
For a CISO, a good place to start is by reading and understanding a firm’s financial statements. This first step helps identify the business’s priorities and concerns. The financial statements sometimes are published publicly and often include risk scenarios, risk appetite details, and key products and services. The financial statements also provide insights into which service or product generates the most revenue for the organization.
Using what they learn from the financial statements, a CISO needs to build out cyber-risk scenarios. What could happen that would lead to the business’s strategic initiatives, products, or services being disrupted? Scenario-building enables CISOs to see risks and opportunities more widely, envision cybersecurity challenges or roadblocks, and identify sources of risk that the business has not considered.
To succeed in this activity, a CISO needs to follow a few basic rules:
- Prioritize major risk scenarios and not minor disruptions
- Strive for realistic occurrences and not focus on the probability, as we know it is a case of when and not if
- Ensure the scenarios are business-oriented and not technical, and carry sufficient information to estimate losses appropriately
The following are some examples of high-level cyber risk scenarios:
- Interruption or disruption of core systems and business platforms for sixteen days due to a ransomware attack
- Corruption of databases and loss of data integrity, leading to major consumer complaints and cancellations
- A product recall due to a cyberattack on the production line impacting the labeling
- Physical damage and fire due to a cyberattack on a factory
- Extended third-party supplier disruption due to a cyberattack
Once good scenarios are constructed, the CISO starts the quantification process. As part of this process, the CISO needs to identify the different areas that could be affected and whether alternative work practices can be used during a period of downtime. This activity is done in collaboration with the relevant CxO in charge of the affected business activity or initiative.
The following are examples of the impacted areas:
- Business: Profit loss, market share losses, and share value fluctuation, among others
- Resources: Employees’ overtime and resources to address specific requirements, among others
- Legal: Lawsuits due to service unavailability or further damages
- Communication: Communication requirements due to a lack of service availability
- Data: Loss/theft of data or data encryption
- IT: Including the time of recovery and build
We provide additional details in the A Bonus Segment for Our CISOs—Purchasing Cyber Insurance section; however, the objective is to show clearly that with each scenario, the consequences that affect the wider business are identified, not only IT systems.
This helps the CISO forecast the potential losses and costs associated with each scenario when it happens. This certainly helps start the discussion and showcase how a cyberattack can lead to business risk, and it supports the quantitative aspect where clearly identified costs are listed, allowing business stakeholders to make informed decisions based on their risk appetite.
The following figure shows the what a forecast may look like.
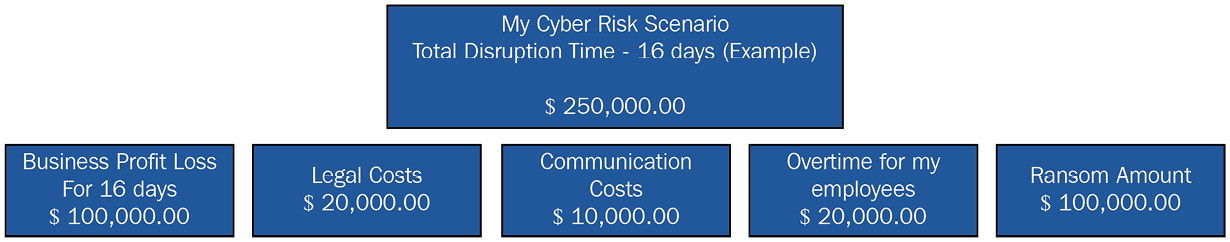
Figure 5.3 – A high-level cyber-risk quantification example
This is high-level, and a CISO should be able to identify the costs in greater detail with the support of their colleagues and peers.
Furthermore, forecasting provides visibility to the board on the ROI for cyber. The benefit (or return on investment) of an investment is calculated by dividing it by the cost of the investment. The calculated value is then given as a percentage or presented as a ratio.
The European Network and Information Security Agency (ENISA) introduced a concept called return on security investment (ROSI). To calculate cyber ROI, an investment’s net loss is divided by its potential cost. The actual cost of an incident represents a critical component of the ROSI calculation.
This quantification forecast enables an organization to raise its understanding of current cyber exposures, and its capacity to mitigate their repercussions by making deliberate and transparent judgments.
A Bonus Segment for Our CISOs—Purchasing Cyber Insurance
In some instances, cyber insurance is considered an alternative to internal cybersecurity controls by business stakeholders or IT managers. This is absolutely not the case. Cyber insurance is a fundamental cybersecurity control and is part of the cyber risk management process as a complementary treatment, providing further support when a cyberattack or data breach happens. It helps with liquidity and cash flow management and covers for losses that the firm might incur.
Foolproof security does not exist. By now, you are either convinced or at least bored from reading the same statement. However, it’s important to repeat it because it’s not if it happens, but when.
Cyber insurance is designed to protect businesses and individuals against risks associated with the internet and, more broadly, risks associated with IT infrastructure, information privacy, information governance liability, and related activities. Typically, these risks are excluded from standard business general liability policies or are not clearly stated in standard insurance packages.
Cyber insurance policies typically provide:
- First-party coverage against losses caused by data destruction, extortion, theft, hacking, and denial-of-service attacks.
- Liability coverage that compensates businesses for losses caused to others by errors and omissions, data loss, or defamation.
- Other benefits such as regular security audits, post-incident public relations, and investigative expenses.
- Ransom reimbursements in some cases (at the time of writing)
In short, cyber insurance compensates for cyber-related financial losses.
There are different types of cyber coverage. Also know that coverage differs from one underwriter to another, and one company to another. The following are a sample of the kinds of cyber insurances (first-party losses) available:
- System recovery: This insurance assumes the expenditures associated with technically restoring the data and eradicating the infection—for example, when a cyberattack impacts the business operations and leads to downtime.
- Reconstruction of data: As a result of a cyberattack, not all data can be recovered using backups. Some must be manually rebuilt. This insurance bears the expense of the additional work and personnel needed to do this.
- Profit loss as a result of suspended activities: For instance, a DoS attack affects the systems of an online e-commerce website, causing major financial losses. Customers cannot access the website, and for more than 2 weeks, all operations come to a halt. This insurance compensates for lost revenue during this time.
- Forensic investigation: For instance, the Monetary Authority of Singapore (MAS) requires a detailed incident response with forensic details. This insurance covers the cost of digital forensic vendors.
- Notification costs: For instance, a cybercriminal uses a phishing email to steal sensitive patient data from a doctor’s office. This insurance bears the expense of alerting affected patients and, if required, authorities.
- Communication costs: This insurance pays for external crisis experts to protect a company’s brand and aggressively mitigate its reputation online.
- Production that is defective: For example, a competitor seeking to harm your organization employs someone to hack into the company’s IT system and make changes to the company’s product formula. The wholly automated manufacturing factory produces 50,000 bottles of erroneously labeled beverages. The beverages manufactured can no longer be sold. This insurance provides support for the expense of replacing the batch and properly disposing of the unused items.
Along with enhancing security directly, cyber insurance is advantageous in the case of a large-scale security breach. Insurance offers a streamlined financing option for large loss recovery, assisting firms in resuming regular operations and decreasing the need for government aid.
As cyber risks evolve and companies adapt their cyber strategies, insurance solutions are being tailored in conjunction with cybersecurity programs. Because of their financial benefits, they are becoming an integral part of the process.
Again, we emphasize that financial fraud and social engineering might be covered under commercial crime policies and not cyber insurance. The CISO needs to verify and acquire confirmation of coverage. Knowing that social engineering scams are growing and are one of the most popular types of cyberattacks, the CISO should also forecast its financial consequences.
Lastly, insurers’ underwriting criteria for offering cyber insurance products are still being developed, and underwriters are actively collaborating with cybersecurity businesses to improve their products. However, the trend is going toward extensive initial checks. The CISO should consider this a good added-value service, with external third-party assurances provided as free services—for example, rating reports and automated scans.
A Bonus Segment for Our CISOs—Reporting to the Board of Directors
Reporting to the CxOs or the board of directors is not easy but necessary. Several factors need to be considered when presenting to the board, including but not limited to:
- Strategy: How effectively does the CISO understand a company’s goals and strategic initiatives, and to what degree is cyber risk incorporated into wider board-level decision-making?
- Board ownership: To what degree does the board drive strategy and how effectively is it incorporated into risk management procedures at the board level?
- Financial resilience: Are cyber exposures quantified and included in a disaster recovery plan that has been stress-tested?
- Accountability of executives: How are executive duties for cyber-risk management organized, and how are executives held accountable?
- Assurance: How does the CISO ensure cyber risk has been adequately evaluated?
- Reporting: How is the board informed about a company’s cyber-risk posture and progress?
Many organizations treat cyber risk in isolation from other components of their ERM framework, failing to see the connection between cyber risk and other aspects of board-level decision-making. Reporting to the board should close this gap, and the CISO needs to focus on a few limited main points that will help achieve the end goal.
The board presentation should focus on and clearly answer the following questions:
- How well will the board of directors comprehend the company’s cyber-risk goals and strategic approach?
- What improvement initiatives are in place to reduce cyber risk to a level that is acceptable?
- How much investment is forecasted for cyber-risk management?
- How is cyber risk integrated into wider board-level decision-making?
In reporting, there should be no technical jargon nor focus on cyberthreats and scare tactics. Those serve as roadblocks and hinder the opportunity for a CISO to justify having a seat in the boardroom.
Summary
In this chapter, we managed to decode many of the expectations for a CISO, their priorities and challenges. From technical security to a seat at the table and often limited funding, CISOs do not have an easy path to building a cyber-resilient business. While a technical leader in some cases, a CISO oversees cyber-risk management. This includes first understanding the company’s exposures and then quantifying potential financial losses to understand and prioritize mitigative initiatives and risk transfer. The mitigation needs to encompass controls for people, processes, and technology and not focus solely on IT.
Nowadays, due to the extensive threats of cyberattack and massive adoption of technology solutions, companies vary in their efforts to measure their cyber-risk exposures. Some do not have any visibility into cybersecurity. Others limit it to their IT environment. This represents a major challenge for a CISO who needs to understand the broader business environment they need to protect, before analyzing and identifying the potential cyber risks.
Communication with the business side is empowered by quantifying cyber threats. While some companies are still not convinced of quantification (for example, stating that without historical data, cyber risk cannot be quantified accurately), others emphasize that quantification is necessary for effective cost evaluations. CISOs need to shift their focus to quantification rather than continuing with the usage of qualitative subjective methods. This is done in collaboration with, or with the support of, the relevant business stakeholders.
In the next chapter, we will address the role of the CHRO and its essential role in building a cyber-resilient organization.
