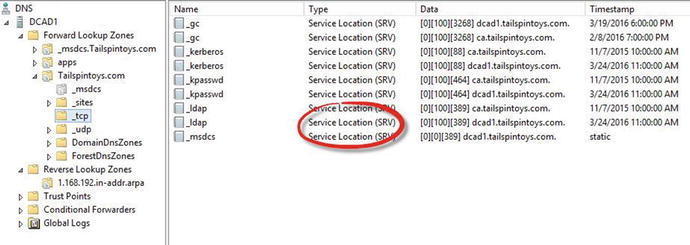
In this chapter, you’ll use the domain controller that you created in Chapter 3. You’ll create host (A) records, pointer (PTR) records, and CNAME records in preparation for your SharePoint 2016 farm. You’ll also verify that the service location (SRV) record was created; without the SRV, your other VMs could not cleanly join your farm in Chapter 6.
Before creating these resource records in the Domain Name System (DNS), let’s talk about DNS and Active Directory–integrated DNS zones.
DNS Zones
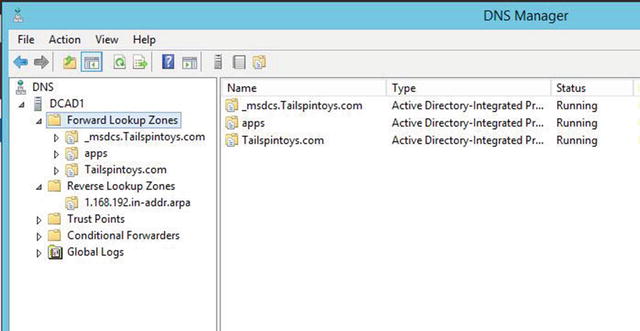
Active Directory–integrated DNS zones store their data in the Active Directory database that is replicated throughout the domain or forest, or to all domain controllers, or to a specific Active Directory partition, based on how they are established. Active Directory–integrated zones are housed at %windir% tds in a file named ntds.dit. This file is the Active Directory database.
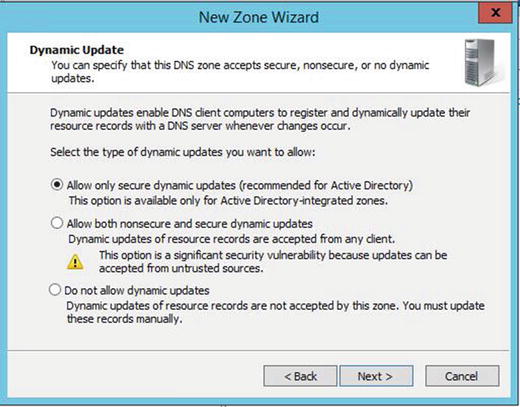
Active Directory–integrated zones are the only type of zone that allows “secure only” updates. Non-Active Directory–integrated zones, or standard primary zones, allow “secure” or “non-secure” updates, but not “secure only”. When DNS is installed on a server that is not a domain controller, the zone is usually a standard primary or a standard secondary zone, and sometimes it is a stub zone.
When you create a DNS zone, you have the option to set it to “secure only”. You can always go back and change that after experience tells you to do this.
Tip
Unfortunately, experience is usually the result of a lack of wisdom and sometimes a lack of security. That said, in a lot of cases, failure to read books and learn best practices are the mother of this experience, which is gained the hard way through trial and error and then through research; but, that’s what makes it stick.
We Are Using “Secure Only”
Non-secure updates allow non-domain members to update DNS. This means a hacker could update your DNS with bogus records that would allow her to take over your empire. That would be bad. Secure only means that a PC or server must be a domain member before ntds.dit will allow any updating to occur. And in order to be a member or a domain, the machine must be joined by someone who knows the domain admin password.
How Does the Information Replicate?
Windows Server 2008 used the File Replication Service (FRS) for zone transfers. Windows Server 2008 R2 and Server 2012 R2 use the Distributed File System (DFS) replication.
Active Directory–integrated zones win hands down on the performance meter. And they do so in more ways than one: not only can every single domain controller write to DNS, but zone transfers only need to replicate the small changes to the schema. This provides a level of fault tolerance that standard zones do not possess without administrative intervention. Remember, natively within standard DNS/file–backed DNS, only the primary DC can update records.
Resolution and Types of DNS Records
There are many types of DNS records. We are going to focus on three of them in the exercises that follow. Before we complete the exercises, we’ll talk about each type of record and give a general overview of DNS resolution, which is the way that a call is made and how DNS serves the number to the individual making the call.
Think of DNS as a phonebook. You can look up people by name to get their number or you can look them up by business. The name-to-number lookup is sort of like a host (A) record and the Yellow Pages are sort of like a CNAME record. Regular phonebooks don’t have a number-to-name section. Can you imagine if there was a section that allowed you to do a reverse lookup of a person’s name based on their phone number? This would be similar to a pointer record.
Basically, when you enter www.bing.com in your computer, the computer first checks its hosts file. If it locates an entry in the hosts file, it will attempt to navigate to that addressIP. If the hosts file is empty or does not have an entry for www.bing.com , then the computer checks its local DNS cache. If the local DNS cache is empty, the computer contacts its DNS server.
The DNS server looks through its records, and if necessary, it will make calls to other DNS servers. The root servers of the Internet might even be contacted, depending on which DNS servers were authoritative for the record requested. Eventually, the DNS record will be located and sent to the computer, or a Page Not Found message could result if the record is not located.
Assuming the record is found, when it’s sent back through the domain name system, most of the DNS servers that had to call for the record will cache the record based on it’s time to live (TTL) value, which will speed up resolution the next time a computer asks for the record, provided that request occurs within the TTL period. Once a TTL period expires, so does the record. When the DNS server scavenges or cleans out stale records, the record is removed from the cache and from the zone that it was entered into. At this point, if a call is made to that same record, and if the DNS server is not authoritative for that record, then the resolution process would need to reoccur.
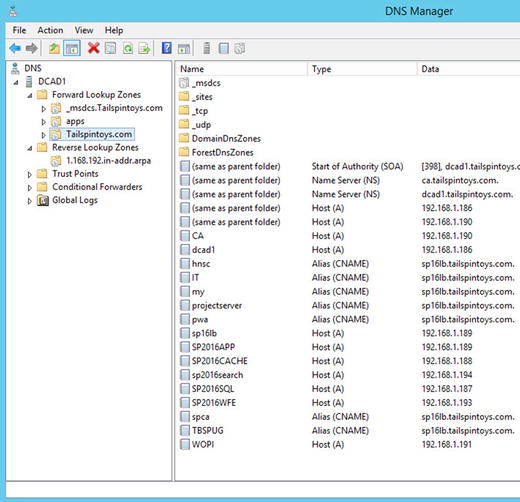
Host (A) and (AAAA)
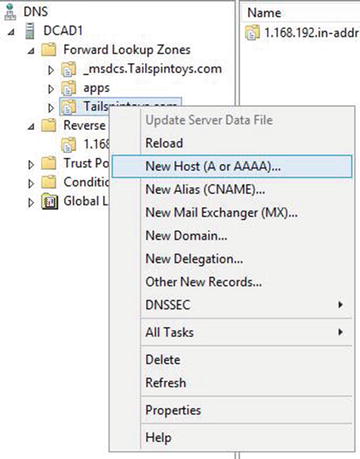
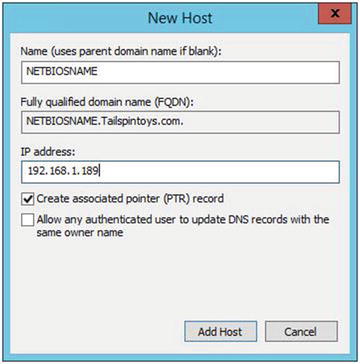
The host (A) record lists the name of the machine, printer, load balancer, server, or other device and points it to its IPv4 address. The IPv6 Host record is called an AAAA record.
So, if you know the name of a machine and enter a command such as ping and follow it with the name of the machine, what will return is the IP address that your machine thinks is correct. If you want to find out where a record points to in DNS, you need to either open DNS from the domain controller, or perform an nslookup from your computer.
To perform an nslookup, just enter nslookup and press Enter. Then enter in the name of the resource that you’re looking to locate.
If you’re looking up a publicly accessible resource, or one you think should be publicly accessible, you can use Google DNS by entering server 8.8.8.8 and then pressing Enter to start searching. After we join some servers to the domain in Chapter 6, we’ll test this theory in an exercise.
A host (A) record looks like Figure 5-1.
Figure 5-1. Host (A)
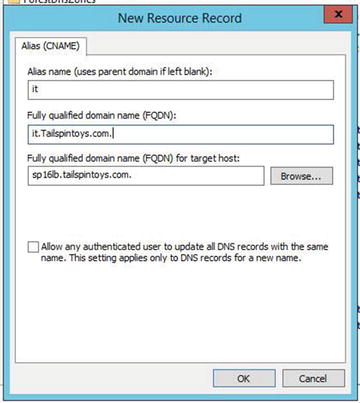
Canonical Name (CNAME) Alias Record
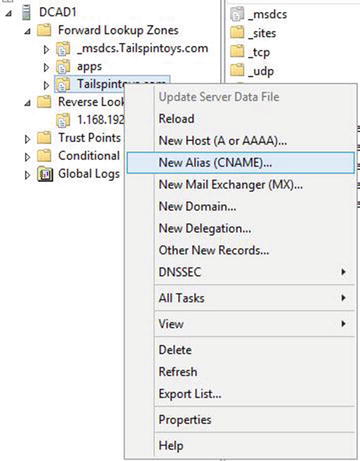
The CNAME or alias record resolves user-friendly namesaliases to host (A) records. The alias is how we “alias” hard-to-remember (let alone say) machine names into friendly Uniform Resource Locators (URLs).
For example, isn’t it easier to remember marketing.contoso.com than mdcpappshr02.contoso.com? Aliases make business happen!
We’ll be creating a many-to-one relationship in DNS, where we’ll have many CNAME records that resolve to the same host (A) record, in order to show how we could resolve through or around a load balancer.
An alias record looks like Figure 5-2.
Figure 5-2. CNAME alias record
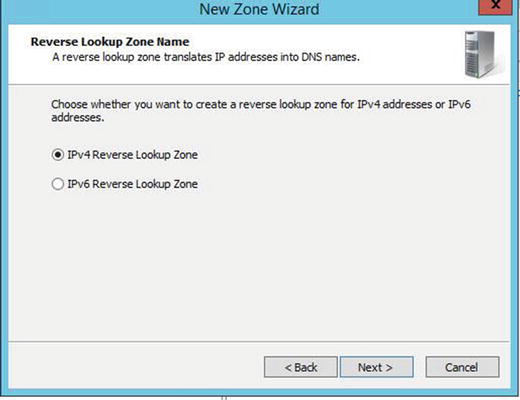
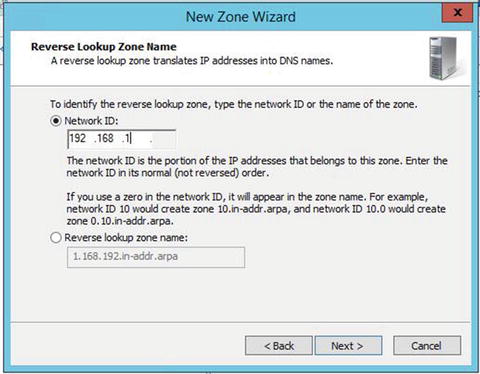
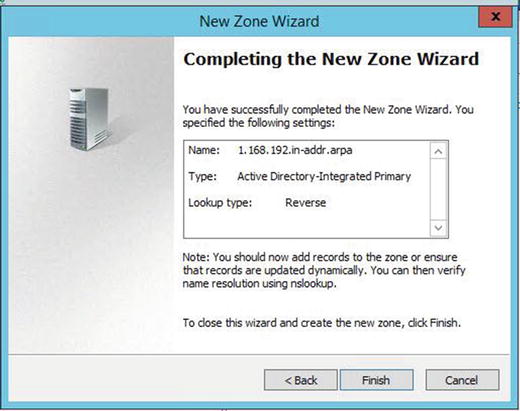
Pointer (PTR) Record
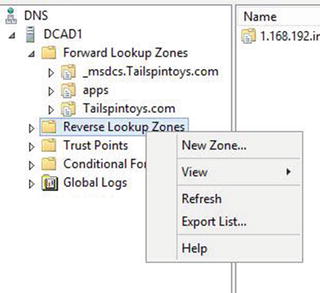
The pointer record is what makes reverse lookups in DNS possible. Pointer records are stored in DNS reverse lookup zones. You can create pointer records manually or automatically when you create your host records.
Pointer records look like what is displayed in Figure 5-3.
Figure 5-3. Pointer records and Reverse Lookup Zones
Ok, let’s get the inventory planning that we did in Chapter 1 and create the host (A) records for your machines and some additional DNS records.
Do You Want to Know More?
Table 5-2 provides additional information.
Table 5-2. Not Required Reading, but Here If You Want To Dive Deeper. These Are All Great Reads!
Topic | URL |
|---|---|
Pro DNS and BIND 10, by Ron Aitchison (Apress, 2011) | |
Practical IPv6 for Windows Administrators, by Edward Horley (Apress, 2013) | |
Cyber Operations, by Mike O’Leary (Apress, 2015) | |
The Accidental SysAdmin Handbook, by Eric A. Kralicek (Apress, 2016) |
Summary
At this point, you’ve created a domain controller and four member servers, and host (A) records, aliases, and pointer records in an Active Directory–integrated DNS. You also created a reverse lookup zone to house those PTR records.
In Chapter 6, we’ll move to joining the servers into the domain. Chapter 7 introduces group policy and creating a policy that enforces local admins on SharePoint servers. In Chapter 8, we’ll create a certificate authority and a wildcard certificate.