Ensure Burp and the OWASP BWA VM are running and that Burp is configured in the Firefox browser used to view the OWASP BWA applications.
- From the OWASP BWA Landing page, click the link to the OWASP Mutillidae II application.
- Open the Firefox browser on the login screen of OWASP Mutillidae II. From the top menu, click Login.
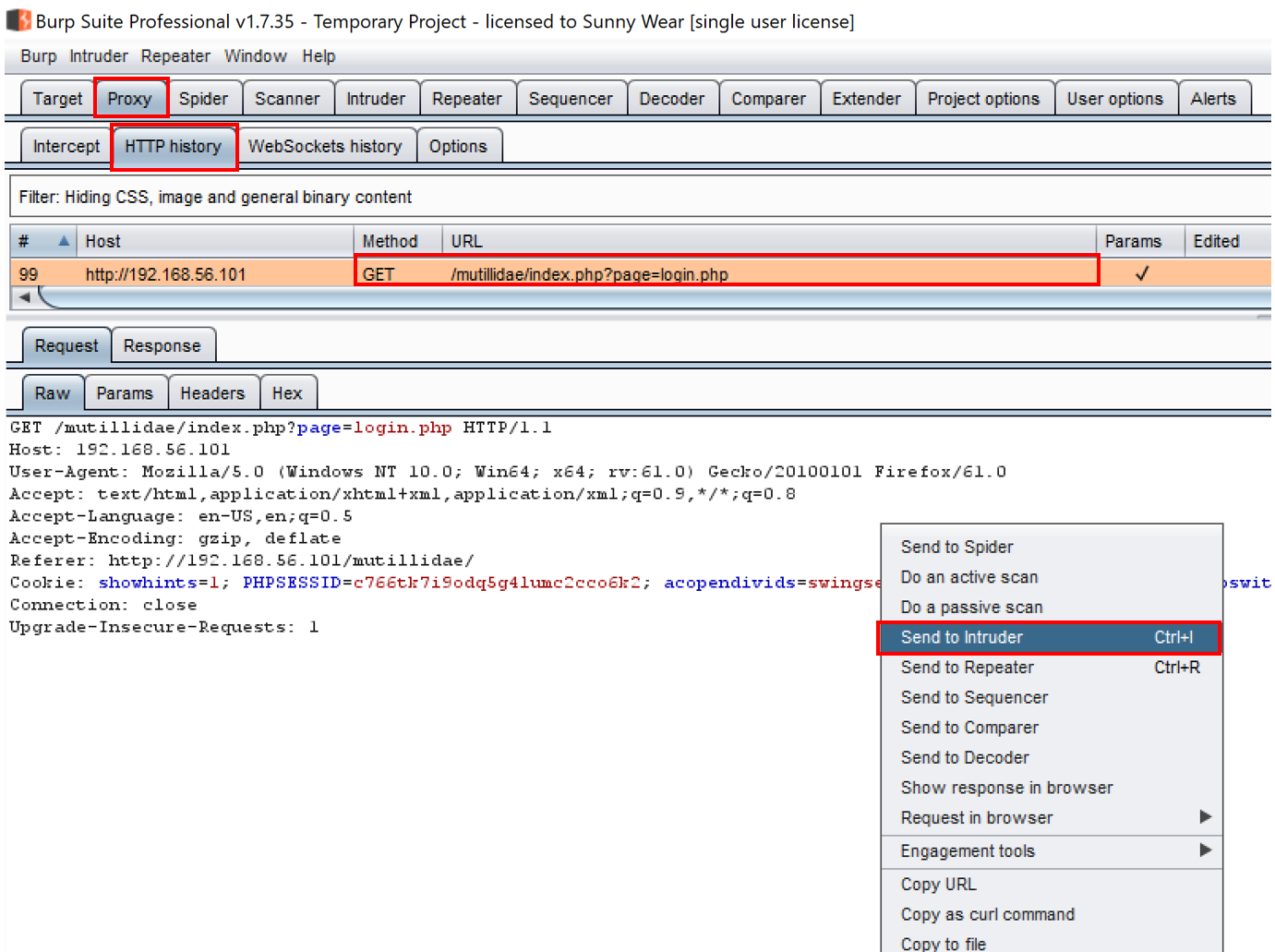
- Find the request you just performed within the Proxy | HTTP history table. Look for the call to the login.php page. Highlight the message, move your cursor into the Raw tab of the Request tab, right-click, and click on Send to Intruder:
- Switch over to the Intruder | Positions tab, and clear all Burp-defined payload markers by clicking the Clear $ button on the right-hand side.
- Highlight the value currently stored in the page parameter (login.php), and place a payload marker around it using the Add § button:

- Continue to the Intruder | Payloads tab, and select the following wordlist from the wfuzz repository: admin-panels.txt. The location of the wordlist from the GitHub repository follows this folder structure: wfuzz/wordlist/general/admin-panels.txt.
- Click the Load button within the Payload Options [Simple list] section of the Intruder | Payloads, tab and a popup will display, prompting for the location of your wordlist.
- Browse to the location where you downloaded the wfuzz repository from GitHub. Continue to search through the wfuzz folder structure (wfuzz/wordlist/general/) until you reach the admin-panels.txt file, and then select the file by clicking Open:

- Scroll to the bottom and uncheck (by default, it is checked) the option URL-encode these characters:

- You are now ready to begin the attack. Click the Start attack button at the top right-hand corner of the Intruder | Positions page:
The attack results table will appear. Allow the attacks to complete. There are 137 payloads in the admin-panels.txt wordlist. Sort on the Length column from ascending to descending order, to see which of the payloads hit a web page.
- Notice the payloads that have larger response lengths. This looks promising! Perhaps we have stumbled upon some administration pages that may contain fingerprinting information or unauthorized access:

- Select the first page in the list with the largest length, administrator.php. From the attack results table, look at the Response | Render tab, and notice the page displays the PHP version and the system information:

