- Navigate to the homepage of OWASP Mutillidae II.
- Switch to Burp Proxy | HTTP history and look for the HTTP request you just created while browsing to the homepage of Mutillidae. Note the method used is GET. Right-click and send the request to Intruder:

-
In the Intruder | Positions tab, clear all suggested payload markers. Highlight the GET verb, and click the Add $ button to place payload markers around the verb:
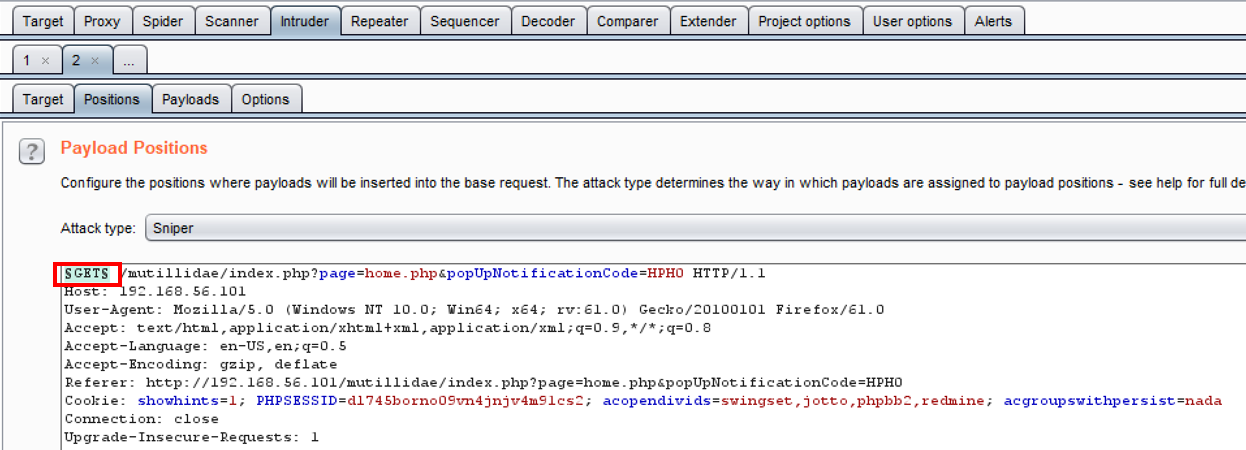
- In the Intruder | Payloads tab, add the following values to the Payload Options [Simple list] text box:
- OPTIONS
- HEAD
- POST
- PUT
- DELETE
- TRACE
- TRACK
- CONNECT
- PROPFIND
- PROPPATCH
- MKCOL
- COPY

- Uncheck the Payload Encoding box at the bottom of the Payloads page and then click the Start attack button.
- When the attack results table appears, and the attack is complete, note all of the verbs returning a status code of 200. This is worrisome as most web servers should not be supporting so many verbs. In particular, the support for TRACE and TRACK would be included in the findings and final report as vulnerabilities:

