CHAPTER 6: TECHNOLOGY CONTINUITY STANDARDS
Similar and relevant to BCM, technology continuity and readiness have gone through an interesting journey in standardization. The list of major stops within this journey continues to grow. The two most recent stops were in 2008 and 2011, when the BSI issued the first to-be-global Standard governing technology’s role in BCM and the ISO issued the first global technology continuity and readiness Standard, respectively.
ISO/IEC 27031 information technology – security techniques – guidelines for information and communication technology readiness for business continuity (IRBC)9
The ISO issued this Standard with one obvious goal in mind: integration between BCM and technology. The title gives a strong impression. Instead of ICT continuity, which implied parallelism, readiness for business continuity is used. It also shows more clarity and less ambiguity in terms of relationships between BCM and technology and setting it all right; IRBC is part of the overall BCM program, or management system.
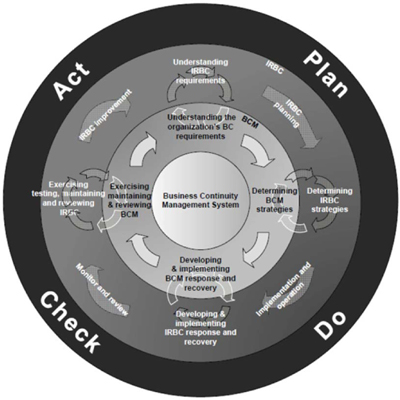
Figure 32: Integration of IRBC and BCMS
The Standard has six main sections that cover the overall IRBC activities: setting up IRBC; IRBC planning; implementation and operation; monitor and review; IRBC improvement; and the annexes that give substantial help for understanding the requirements and implementation of the IRBC.
The Standard follows the same Plan-Do-Check-Act (PDCA) Cycle as other ISO standards. This approach enables the Standard to integrate well with the ISO27001 and ISO24762 Standards.
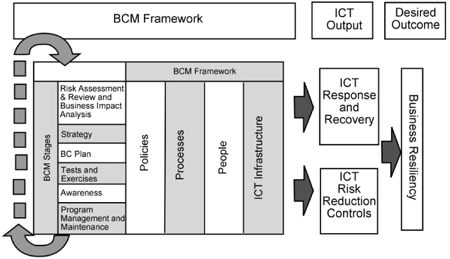
Figure 33: Business continuity framework and its related ICT output and desired outcomes
Scope
The Standard’s scope covers almost all types of organizations and incidents. It builds on the incident management processes by security to cover any type of incidents that may affect the technology infrastructure and services
Terms and definitions
The Standard’s list of terms and definitions is relatively short compared to the one in BS25777. The new development here is that MTPD, or MTPoD, is not listed. Similar to ISO22031, the concentration is on RTO and RPO as well as the minimum business continuity objective (MBCO) as the main continuity specifications.
Overview
In this section, the Standard clearly defines the relationship between BCM and IRBC as well as the setup process of IRBC, which includes the following:
- role of IRBC within BCM
- principles of IRBC
- elements of IRBC
- outcomes and benefits of IRBC
- establishing IRBC
- management responsibility and IRBC policy.
IRBC planning
Following the overview section, which describes the IRBC setup process, the IRBC planning section covers the initial stages of the IRBC process:
- IRBC staff assignment
- defining IRBC requirements
- determining the IRBC strategy options that cover the IRBC elements.
Implementation and operation
As the title suggests, in this section the Standard lists the main guidelines for implementing IRBC readiness through its elements, in normal business conditions and in disasters.
This section also includes the specifications of IRBC plans in terms of structure and documentation development and control.
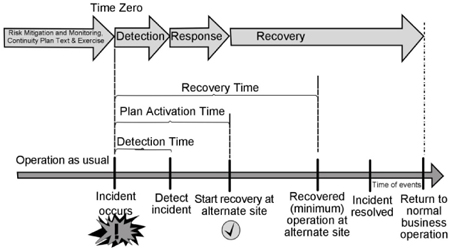
Figure 34: The principles of IRBC on a typical ICT disaster recovery timeline
Monitor and review
This section has one of the powerful features of this Standard. It has very detailed descriptions of IRBC testing and exercising tasks.
This section also specifies the requirements of audit and management review processes. The Standard also defines the key performance indicators (KPI) for IRBC readiness.
IRBC improvement
This section lists the requirements for the continuous enhancement of the IRBC process, covering corrective and preventive actions.
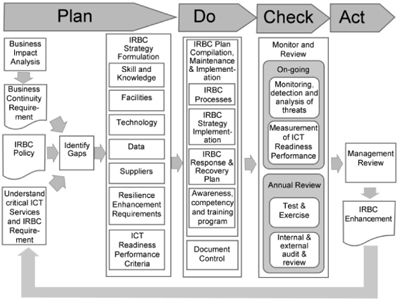
Annex A: IRBC and milestones during a disruption
This annex provides an anatomy of the typical IRBC response phases covering from before the incident and ending with preventive and improvement actions going through response, recovery, and restoration.
Annex B: high availability embedded system
This annex discusses the main considerations for designing and embedding high availability within systems and components.
Annex C: assessing failure scenarios
This annex introduces the assessment methodology and results of the failure scenarios.
Annex D: developing performance criteria
This annex details guidelines for developing the performance criteria or the key performance indicators for the IRBC process.
ISO/IEC 24762:2008 information technology – security techniques – guidelines for information and communications technology disaster recovery sites10
ISO/IEC 24762:2008 addresses the information and communications technology disaster recovery (ICT DR) services that are provided either internally or externally through specialized vendors. Being more specific, the Standard focuses on ICT DR sites and their specifications. Due to the specialty and complexity of ICT DR sites, specific factors should be considered when considering ICT DR programs and sites. Nevertheless, the Standard’s guidelines support and are compliant with BCM.
The Standard contains 10 main sections, or clauses, but the core guidelines are enclosed within 4 of them:
- Clause 5: ICT disaster recovery
- Clause 6: ICT disaster recovery facilities
- Clause 7: Outsourced service provider’s capability
- Clause 8: Selection of recovery sites.
Clause 5: ICT disaster recovery
Clause 5 discusses the ICT DR services provided to the organization, either internally or externally. The Standard’s guidelines discuss various aspects with some focus on ICT DR sites.
In this clause, there are requirements relating to environmental stability that are related to external surrounding events, both natural and man-made, that may endanger the ICT DR site services and operations.
The clause also discusses the various aspects of the asset management process in relation to ICT DR sites.
This clause discusses the ICT DR site’s proximity range and sets it to a distance not affected by the original risks affecting the primary site.
Clause 5 also discusses vendor management when utilizing or preparing ICT DR sites. This particular issue includes, among other factors, the procurement process, the vendor’s staff deployment, and the vendor’s equipment management.
Guidelines in this clause cover the issues of outsourcing arrangements with external vendors for staff, equipment, or services, from the pre-contracting stage, to contractual agreement, to periodic review.
In the “information security” section, the guidelines cover the aspects of physical and logical security requirements for equipment and data, including information security incident management processes.
This clause sets the guidelines for activation and deactivation of ICT DR sites.
The final major part of this clause concerns training and awareness related to ICT DR sites. Participants and types of training are covered in this regard.
Clause 6: ICT disaster recovery facilities
Guidelines in clause 6 cover the facilities aspect of ICT DR sites.
The guidelines cover the factors to consider when deciding on the location of the ICT DR site. These factors include natural hazards, weather changes, man-made hazards, primary and alternative accessibility, shared premises, and public utilities. All of these factors are discussed in further detail.
This clause discusses the physical access control process for ICT DR sites. The process covers equipment, staff, and non-staff. In addition, specific roles and responsibilities are mentioned in relation to access control.
Subsequently, the guidelines in this clause discuss physical security for the ICT DR site facilities, covering almost all aspects of this area.
Next, the clause addresses the subject of dedicated areas with specific functions as part of the ICT DR site’s facilities, for example assembly areas, holding areas, and staging areas.
The rest of the clause discusses the subjects of:
- environmental controls
- telecommunications
- power supply
- cable management
- fire protection
- emergency operations center (EOC)
- restricted areas
- non-recovery amenities (dedicated to the well-being of ICT DR site users)
- physical facilities and the support equipment life cycle
- testing.
Clause 7: outsourced service provider’s capability
In clause 7, the Standard’s guidelines discuss various aspects of the outsourced services provided to the organization. The guidelines suggest that the organization should seek external ICT DR services after producing an ICT DR plan, following a methodological approach and assigning the proper roles and responsibilities required.
The guidelines suggest the qualifications required from outsourced service providers to provide proper ICT DR services:
- Facilities: Facilities provided by the outsourced service provider should follow the same requirements and guidelines mentioned in clause 5. In other words, the service provider should satisfy the same level of requirements as internal service providers.
- Expertise: This includes the experience of the service provider as well as experience of the staff engaged in offering the services. In this regard, the guidelines discuss other relevant areas like knowledge retention and staff management.
- Logical access control: The outsourced service provider should provide appropriate levels of logical access to the organization’s equipment and applications deployed at external site.
- ICT readiness: The ICT equipment and activities should be kept in state of readiness, to be activated when necessary by the organization.
- Support capabilities: The infrastructure and the staff to support the service provided from the outsourced service provider are a requirement of the Standard and they are associated with the service levels agreed in the contract or agreement.
- Types of service: There are different types of service that are provided by an outsourced service provider, ranging from warehousing, to technical services, to complete ICT DR solutions.
- Proximity: As with the requirements in clause 6, the outsourced service provider should follow the same guidelines in offering ICT DR services to the organization.
- Managing multiple subscriptions or clients: Most outsourced service providers offer shared resources that are assigned to clients based on different schemes (first-come first-served, priority schemes, etc.). If shared resources are offered, the organization should ensure the appropriate conditions are being provided by the outsourced service providers.
- Activation: These are the invocation procedures and use policies.
- Testing: The testing process has different aspects that the organization and the outsourced service provider should agree and document.
- Changes in capability: This is the process to communicate and agree on the changes of the outsourced service provider’s ICT DR capabilities and the effects on the organization.
- Emergency response plans: The outsourced service provider should have sufficient emergency response plans to manage incidents at their premises and their environments as well as testing such plans and relevant arrangements.
- Self-assessment: This is internal certification of the outsourced service provider’s conformity with certain requirements and standards.
Clause 8: selection of recovery sites
This clause discusses the typical features of selecting the locations of recovery centers in terms of:
- infrastructure
- skilled human resources in ICT DR areas
- sufficient presence of ICT DR vendors and suppliers
- maturity of local ICT DR service providers
- proactive local support for ICT DR services.
9 International Organization for Standardization. ISO/IEC 27031 information technology – security techniques – guidelines for information and communication technology readiness for business continuity (2011).
10 ISO. ISO/IEC 24762:2008 Information technology – Security techniques – Guidelines for information and communications technology disaster recovery sites. (2008).