Chapter 13. Introduction to Mobile and Remote Access (MRA)
This chapter covers the following topics:
![]() Purpose of MRA: This topic will introduce the MRA solution and the purpose behind why Cisco developed this solution.
Purpose of MRA: This topic will introduce the MRA solution and the purpose behind why Cisco developed this solution.
![]() Components of MRA: This topic will identify the six main components that make up the MRA solution, and the purpose of each of these components serve.
Components of MRA: This topic will identify the six main components that make up the MRA solution, and the purpose of each of these components serve.
![]() Considerations for MRA Deployment: This topic will explain the different consideration that should be deliberated upon prior to deploying this solution.
Considerations for MRA Deployment: This topic will explain the different consideration that should be deliberated upon prior to deploying this solution.
Virtual private networks have a long-time tradition of connecting remote locations with an enterprise network. However, VPNs are very complex and require a lot of resources to operate. Additionally, the modern workplace is not always located in an office environment. Companies are now encouraging their employees to work from home, which complicates how these employees communicate with each other and the outside world. Cisco’s out-of-the-box thinking has brought about a solution to many of the problems created by the modern workplace mindset. The Mobile and Remote Access (MRA) solution is a unique deployment that incorporates many facets of the more traditional traversal solution discussed in the preceding chapter. Communication devices can operate from any network at any location without the use of VPNs. Employees can leverage these communication devices from a home office without the need to set up and store another router in their home. Additionally, all the features and capabilities that employees would have from a communications device located in an office are still at their disposal from their remote location using this MRA solution.
This chapter does not cover any of the objectives from the Implementing Cisco Collaboration Cloud and Edge Solutions (CLCEI) exam 300-820. It only serves to establish the foundation for chapters 14 and 15.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 13-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes.”
Table 13-1 ”Do I Know This Already?” Section-to-Question Mapping

Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. Which of the following statements best describe the MRA solution?
a. MRA is a call control solution designed to replace the CUCM
b. MRA is a firewall traversal solution that allows the CUCM to call outside the network
c. MRA is VPN solution that allows endpoints outside the network to register to the CUCM
d. MRA is a VPN-less solution that allows endpoints outside the network to register to the CUCM
2. Which of the following statements is true regarding MRA?
a. MRA only supports SIP
b. MRA only supports H.323
c. MRA supports either SIP or H.323
d. MRA is not based on any communications protocol
3. Which of the following Certificate requirements must be established when configuring MRA?
a. MTLS must be established between the CUCM and Expressway Core, as well as between the Expressway Core and the Expressway Edge.
b. MTLS is not required between the CUCM and Expressway Core, but it is required between the Expressway Core and the Expressway Edge.
c. MTLS must be established between the CUCM and Expressway Core, but it is not required between the Expressway Core and the Expressway Edge.
d. MTLS is recommended but not required between the CUCM and Expressway Core, nor is it required between the Expressway Core and the Expressway Edge. Standard TLS can be used instead.
4. Which outbound port must be opened on the internal firewall to allow XMPP traffic between the Expressway-C and Expressway-E?
a. TCP 7001
b. TCP 7400
c. UDP 7001
d. UDP 7400
5. Which of the following settings is required on the CUCM in every MRA deployment?
a. Cisco AXL Web Service must be running on the Publisher node
b. MRA Access Policy enabled for Jabber users
c. OAuth refresh logins
d. Denial of Service Thresholds
Foundation Topics
Purpose of MRA
No matter what line of business exists, extending to branch offices is a fundamental approach to reaching a wider market. Cisco’s next-gen routers offer incredible routing capabilities across network borders. However, these complicated network deployments can falter, leaving communication gaps at critical times. Additionally, not all companies use a modern IP solution for communication. Yet companies that have moved to an IP-based communications solution still need to be able to communicate with businesses and consumers who have not yet made this move. The Cisco Edge products allow communication to be unified and uninterrupted regardless of location or disruption.
In today’s everchanging workplace, businesses are no longer tied to the four walls of the office space. Employees are now allowed and encouraged to work from home, which reduces company overhead expenses and increases employee productivity. However, with these changes to the corporate environment, there are many challenges to overcome as well. One such challenge pertains to how employees communicate with one another from many different remote locations. Cisco has designed a solution to this communication dilemma called Mobile and Remote Access (MRA). This distinctive platform allows employees to leverage the same great Cisco collaboration solution from anywhere in the world without a VPN while maintaining the same level of security that employees experience within the corporate network. MRA is a core part of the Cisco Collaboration Edge architecture. MRA allows endpoints, such as Cisco Jabber, UC phones, and CE software-based Telepresence endpoints, to securely utilize registration, call control, provisioning, messaging, and presence services that are provided by Cisco Unified Communications Manager when the endpoint is not within the enterprise network. Cisco Expressway series components are used to provide secure access and firewall traversal to the endpoints that register with the Cisco Unified Communications Manager.
The Cisco Expressway Series product portfolio is an evolved solution that originated in the Tandberg Video Communications Server (VCS) products. After Cisco acquired Tandberg, the company used these extraordinary products as the foundation of an even greater-reaching solution known as Mobile and Remote Access (MRA).
Cisco first launched the Expressway Series in version X8.1. The Cisco Expressway solution was originally designed to offer a low-cost solution for existing Cisco Unified Communications Manager customers, providing them with a traversal solution without the need to buy expensive servers and licenses. Because these servers could be virtualized, customers who were already running the Cisco Unified Communications Manager could install the Expressway Series for free, gaining the ability to do secure firewall traversal for IP communications. The Expressway Series also offered a secure VPN-less solution for unified communications, known as Mobile and Remote Access (MRA). The X8.1 version of the Expressway could not support registrations directly, but MRA allows for endpoints outside the firewall to register to an internal Cisco Unified Communications Manager from anywhere outside the corporate network through a proxied registration rather than through a VPN. This limits the need for small and medium-sized businesses to install complex VPN routers and improves the media flow of calls between internal endpoints and external endpoints. In August 2016, Cisco released version X8.9, which allows for registrations directly to the Expressway Core and Edge servers. At the writing of this book, the current version of the Expressway is 14.0.

Components of MRA
Although the MRA solution operates in a similar fashion to a standard firewall traversal solution for B2B communications, there are some significant differences between them. First, MRA is only supported for SIP; there is no H.323 support in the MRA solution. Second, certificates are required for MRA between the Expressway Core and Edge servers; there is no way to build the traversal zones with a basic TLS or TCP SIP connection. TLS Verify is required for MRA. Third, some specific settings must be configured to enable MRA on the Expressway servers. Fourth, the zones created between the Cisco Expressway Core and Cisco Expressway Edge servers are not the same traversal client zone and traversal server zone used in a standard firewall traversal solution. Finally, the DNS SRV records that need to be created are different from what is required for a traditional firewall traversal solution.
MRA consists of six main components. One of the components are DNS records. Internal and external DNS records are essential to enable endpoints to detect whether they should register directly with Cisco Unified Communications Manager or proxy registration through the MRA deployment.
Certificates are another component of MRA. This solution provides secure communication over Transport Layer Security (TLS). Mutual TLS (MTLS) Authentication, or TLS Verify, is required between the Expressway Core and Edge servers. Trust between TLS entities is established based on certificates. Implementing the necessary certificates for a public key infrastructure (PKI) is an important part of Cisco Collaboration MRA implementation.
Another component is Firewall Traversal Services. MRA supports internal firewalls between Cisco Expressway Core and Cisco Expressway Edge, and an external firewall between Cisco Expressway Edge and the Internet. The firewall traversal capabilities of MRA use the same Assent traversal protocol of standard firewall traversal, but traversal chaining is not supported with MRA. There is a specific type of Taversal Zone that must be created in association with MRA called Unified Communications Traversal.
There are other settings that must be configured to initiate MRA on the Expressways. These Unified Communications configuration settings are an essential component to MRA. Enabling these services with open additional configuration fields, such as Domain settings, they will create necessary Neighbor Zones and Search Rules to the CUCM for MRA functionality and allow communication to be established between the CUCM and the Expressway Core. If the IM and Presence server, or Unity Connection are being leveraged as well, the Expressway will use these settings to establish communication with these services as well.
The fifth component in an MRA solution is reverse HTTPS proxy. To support secure data services, such as visual voicemail, contact photo retrieval, Cisco Jabber custom tabs, and so on, a reverse HTTPS proxy runs on the Cisco Expressway Edge server. If these services are not needed in an enterprise deployment of MRA, this component does not need to be set up.
The final component that needs mentioned regarding the MRA solution is the SIP Trunk Security Profile on the CUCM that will be used in connection with the Expressway Core. Mutual TLS (MTLS) is not required between these two servers. However, if MTLS is used, then a trust needs to be established between the CUCM and Expressway Core certificates, and the SANs in the Expressway Core certificate need to be included in the SIP Trunk Security Profile. Once these components are set up, the MRA deployment can support two main features:
![]() Off-Premises Access: Cisco Collaboration MRA offers a consistent experience to clients, such as Cisco Jabber; UC phones; and Cisco DX, MX, SX, and Webex series endpoints, regardless of whether they are in the internal network or on an external network.
Off-Premises Access: Cisco Collaboration MRA offers a consistent experience to clients, such as Cisco Jabber; UC phones; and Cisco DX, MX, SX, and Webex series endpoints, regardless of whether they are in the internal network or on an external network.
![]() Business-to-Business Communications: Cisco Collaboration Mobile and Remote Access offers secure communication to other businesses.
Business-to-Business Communications: Cisco Collaboration Mobile and Remote Access offers secure communication to other businesses.
Considerations for MRA Deployment
Before you begin setting up the MRA solution there are some requirements and prerequisites you will want to examine first. Refer to the Mobile Remote Access Through Cisco Expressway Deployment Guide for the version of Expressway you are running for a more accurate and detailed list of these prerequisites and requirements. For MRA port information, go to the Cisco Expressway IP Port Usage Configuration Guide at http://www.cisco.com/c/en/us/support/unified-communications/expressway-series/products-installation-and-configuration-guides-list.html. The guide describes the ports that you can use between Expressway-C in the internal network, Expressway-E in the DMZ, and the public internet. Also, assign separate IP addresses to the Expressway-C and the Expressway-E. Do not use a shared address for both elements, as the firewall cannot distinguish between them.

Ensure that the relevant ports are configured on your firewalls between your internal network where the Expressway-C is located, and the DMZ where the Expressway-E is located, and between the DMZ and the public internet. No inbound ports are required to be opened on the internal firewall. The internal firewall must allow the following outbound connections from Expressway-C to Expressway-E:
![]() SIP: TCP 7001
SIP: TCP 7001
![]() Traversal Media: UDP 2776 to 2777 (or 36000 to 36011 for large VM/appliance)
Traversal Media: UDP 2776 to 2777 (or 36000 to 36011 for large VM/appliance)
![]() XMPP: TCP 7400
XMPP: TCP 7400
![]() HTTPS (tunneled over SSH between C and E): TCP 2222.
HTTPS (tunneled over SSH between C and E): TCP 2222.
The external firewall must allow the following inbound connections to the Expressway-E:
![]() SIP: TCP 5061
SIP: TCP 5061
![]() HTTPS: TCP 8443
HTTPS: TCP 8443
![]() XMPP: TCP 5222
XMPP: TCP 5222
![]() Media: UDP 36002 to 59999.
Media: UDP 36002 to 59999.
The ideal scenario for MRA is to have a single domain with a split DNS configuration, and this is the recommended approach. This is not always possible, so there are some other approaches to deal with various alternative scenarios. The domain to which the calls are routed must match with the MRA domain to which the endpoints were registered. For example, if endpoints are registered with the domain exp.example.com, the calls must be routed to this domain, and it must not be routed to the subdomain cluster1.exp.example.com.

![]() Single Domain with Split DNS – Recommended – A single domain means that you have a common domain (example.com) with separate internal and external DNS servers. This allows DNS names to be resolved differently by clients on different networks depending on the DNS configuration, and aligns with basic Jabber service discovery requirements.
Single Domain with Split DNS – Recommended – A single domain means that you have a common domain (example.com) with separate internal and external DNS servers. This allows DNS names to be resolved differently by clients on different networks depending on the DNS configuration, and aligns with basic Jabber service discovery requirements.
![]() Dual Domain without Split DNS – From X12.5, the Cisco Expressway Series supports the case where MRA clients use an external domain to lookup the _collab-edge SRV record, and the _cisco-uds SRV record. That same external domain cannot be resolved by the Expressway-C. This is typically the case when split DNS is not available for the external domain. Prior to X12.5 this required a pinpoint subdomain or some other DNS workaround on the Expressway-C, to satisfy the client requirements for resolving the _cisco-uds record.
Dual Domain without Split DNS – From X12.5, the Cisco Expressway Series supports the case where MRA clients use an external domain to lookup the _collab-edge SRV record, and the _cisco-uds SRV record. That same external domain cannot be resolved by the Expressway-C. This is typically the case when split DNS is not available for the external domain. Prior to X12.5 this required a pinpoint subdomain or some other DNS workaround on the Expressway-C, to satisfy the client requirements for resolving the _cisco-uds record.
![]() Limitation: This case is not supported for Unified CM nodes identified by IP addresses, only for FQDNs.
Limitation: This case is not supported for Unified CM nodes identified by IP addresses, only for FQDNs.
This feature also supports a secondary case, for MRA deployments that only allow Jabber access over MRA even if users are working on-premises. In this case only one domain is required and typically the DNS records are publicly resolvable (although this is not required if MRA access is disallowed for users when off premises). The change in X12.5 means that there is no need to have a _cisco-uds._tcp.<external-domain> DNS SRV record available to Cisco Expressway-C or to the Jabber clients.
![]() Single Domain without Split DNS: Deployments that require Jabber clients to always connect over MRA also benefit from the X12.5 update that no longer requires the Expressway-C to resolve the _cisco-uds DNS SRV record. So, administrators only need to configure the _collab-edge DNS SRV record, and Jabber clients using service discovery will only have the option of connecting over MRA.
Single Domain without Split DNS: Deployments that require Jabber clients to always connect over MRA also benefit from the X12.5 update that no longer requires the Expressway-C to resolve the _cisco-uds DNS SRV record. So, administrators only need to configure the _collab-edge DNS SRV record, and Jabber clients using service discovery will only have the option of connecting over MRA.
![]() URL for Cisco Meeting Server Web Proxy and MRA domain cannot be the same: If you use both the CMS Web Proxy service and MRA on the same Expressway, the following configuration items must be assigned different values per service. If you try to use the same value, the service that was configured first will work, but the other one will fail:
URL for Cisco Meeting Server Web Proxy and MRA domain cannot be the same: If you use both the CMS Web Proxy service and MRA on the same Expressway, the following configuration items must be assigned different values per service. If you try to use the same value, the service that was configured first will work, but the other one will fail:
![]() MRA domain(s). The domain(s) configured on Expressway and enabled for Unified CM registration.
MRA domain(s). The domain(s) configured on Expressway and enabled for Unified CM registration.
![]() CMS Web Proxy URL link. Defined in the Expressway ”Guest account client URI” setting on the Expressway > Configuration > Unified Communications > Cisco Meeting Server page.
CMS Web Proxy URL link. Defined in the Expressway ”Guest account client URI” setting on the Expressway > Configuration > Unified Communications > Cisco Meeting Server page.
![]() Multiple External Domains for Mobile and Remote Access: Cisco Expressway supports Mobile and Remote Access with multiple external domains. With this deployment, you will have more than one external domain where your MRA clients may reside. Expressway-E must be able to connect to all of them. To configure this deployment, do the following:
Multiple External Domains for Mobile and Remote Access: Cisco Expressway supports Mobile and Remote Access with multiple external domains. With this deployment, you will have more than one external domain where your MRA clients may reside. Expressway-E must be able to connect to all of them. To configure this deployment, do the following:
![]() For Expressway-E:
For Expressway-E:
• On Expressway-E, configure _collab-edge._tls.<domain> and _sips_tcp.<domain> DNS SRV records for each Edge domain.
• Configure A records that point the Expressway-E hostname to the public IP address of Expressway-E.
![]() For Expressway-C:
For Expressway-C:
• For internal DNS, add A and PTR records that point to Expressway-E FQDN. Add these records to all Expressway-C nodes.
• Configure the _cisco_uds SRV record for every domain to point to your CUCM clusters.
• On the Domains page of Expressway-C, add each of the internal domains that point to the CUCM cluster.
The Maximum Session Bit Rate for Video Calls on CUCM for the default region is 384 kbps by default. The Default call bandwidth on Expressway-C is also 384 kbps by default. These settings may be too low to deliver the expected video quality for MRA-connected devices.

The following Cisco Unified Communications Manager configuration requirements exist for deploying Mobile and Remote Access:
![]() IP addressing – CUCM must be using IPv4 addressing.
IP addressing – CUCM must be using IPv4 addressing.
![]() Cisco AXL Web Service – This service must be running on the publisher node.
Cisco AXL Web Service – This service must be running on the publisher node.
![]() Multiple CUCM clusters – If you have multiple UCM clusters, configure Home Cluster Discovery. End users must have the Home Cluster field assigned in End User Configuration so that the Expressway-C can direct MRA users to the correct CUCM cluster. Use either of the following configuration methods:
Multiple CUCM clusters – If you have multiple UCM clusters, configure Home Cluster Discovery. End users must have the Home Cluster field assigned in End User Configuration so that the Expressway-C can direct MRA users to the correct CUCM cluster. Use either of the following configuration methods:
![]() Option 1: ILS Network – Configure an Intercluster Lookup Service (ILS) network between your remote CUCM clusters. ILS completes cluster discovery automatically, populating the Cluster View for each cluster, connecting your clusters into an intercluster network. ILS can also replicate your enterprise dial plan across all CUCM clusters, although this functionality is not required by MRA. ILS is the recommended approach, particularly for large intercluster networks.
Option 1: ILS Network – Configure an Intercluster Lookup Service (ILS) network between your remote CUCM clusters. ILS completes cluster discovery automatically, populating the Cluster View for each cluster, connecting your clusters into an intercluster network. ILS can also replicate your enterprise dial plan across all CUCM clusters, although this functionality is not required by MRA. ILS is the recommended approach, particularly for large intercluster networks.
![]() Option 2: Manual Connections – Configure each CUCM cluster manually with connections to the other remote clusters. From Cisco Unified CM Administration, navigate to Advanced Features > Cluster View and add the remote clusters. Note that this option does not allow for dial plan replication.
Option 2: Manual Connections – Configure each CUCM cluster manually with connections to the other remote clusters. From Cisco Unified CM Administration, navigate to Advanced Features > Cluster View and add the remote clusters. Note that this option does not allow for dial plan replication.
![]() MRA Access Policy – If you have Cisco Jabber clients using OAuth authentication over MRA, make sure that your Jabber users’ User Profiles allow Mobile and Remote Access. Check that the following settings exist within the User Profile Configuration of the CUCM:
MRA Access Policy – If you have Cisco Jabber clients using OAuth authentication over MRA, make sure that your Jabber users’ User Profiles allow Mobile and Remote Access. Check that the following settings exist within the User Profile Configuration of the CUCM:
![]() The Enable Mobile and Remote Access check box must be checked (the default setting is checked).
The Enable Mobile and Remote Access check box must be checked (the default setting is checked).
![]() The Jabber Desktop Client Policy and Jabber Mobile Client Policy fields must be set to allow the appropriate Jabber services for your deployment (the default setting is IM & Presence, Voice and Video calls).
The Jabber Desktop Client Policy and Jabber Mobile Client Policy fields must be set to allow the appropriate Jabber services for your deployment (the default setting is IM & Presence, Voice and Video calls).
![]() Push Notifications – If you are deploying Cisco Jabber or Webex on iOS or Android clients over MRA, you must configure Push Notifications and Cisco Cloud Onboarding in CUCM. For configuration details, see the Push Notifications Deployment Guide.
Push Notifications – If you are deploying Cisco Jabber or Webex on iOS or Android clients over MRA, you must configure Push Notifications and Cisco Cloud Onboarding in CUCM. For configuration details, see the Push Notifications Deployment Guide.
![]() OAuth – If you are using OAuth on Expressway, you must also enable OAuth Refresh Logins on CUCM as well. This can be turned on in Cisco Unified CM Administration by setting the OAuth with Refresh Login Flow enterprise parameter to Enabled.
OAuth – If you are using OAuth on Expressway, you must also enable OAuth Refresh Logins on CUCM as well. This can be turned on in Cisco Unified CM Administration by setting the OAuth with Refresh Login Flow enterprise parameter to Enabled.
If you want to deploy SAML SSO for MRA users and clients, you must configure it on CUCM before you configure it on Expressway.
![]() For video calling over MRA, it’s recommended that you reconfigure the Maximum Session Bit Rate for Video Calls setting within the Region Configuration as the default value of 384 kbps is not enough for video.
For video calling over MRA, it’s recommended that you reconfigure the Maximum Session Bit Rate for Video Calls setting within the Region Configuration as the default value of 384 kbps is not enough for video.
If CUCM and Expressway are in different domains, you must use either IP addresses or FQDNs for the CUCM server address.
![]() Denial of Service Thresholds – High volumes of Mobile and Remote Access calls may trigger denial of service thresholds on CUCM when all calls arrive at the CUCM from the same Expressway-C (cluster). If necessary, Cisco recommends that you increase the level of the SIP Station TCP Port Throttle Threshold service parameter to 750 KB/second. You can access the parameter from System > Service Parameters menu and selecting the Cisco CallManager service.
Denial of Service Thresholds – High volumes of Mobile and Remote Access calls may trigger denial of service thresholds on CUCM when all calls arrive at the CUCM from the same Expressway-C (cluster). If necessary, Cisco recommends that you increase the level of the SIP Station TCP Port Throttle Threshold service parameter to 750 KB/second. You can access the parameter from System > Service Parameters menu and selecting the Cisco CallManager service.
In addition to everything covered in this section, you may also want to check the IM & Presence service requirements and the Cisco Unity Connection service requirements if you plan to use these services. There are also Certificate requirements specific to the MRA solution, including Certificate Signing Request (CSR) requirements for Expressway Servers. Finally, you may also want to check any endpoint requirements, including validating all compatible endpoint and soft clients that can be used with the MRA solution.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
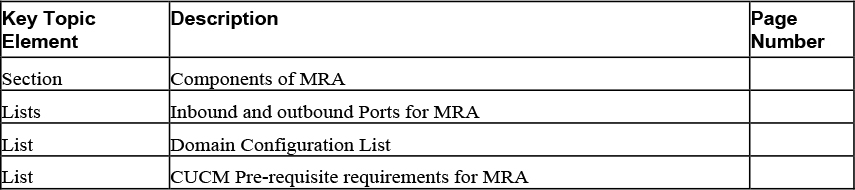
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 13-2 lists a reference of these key topics and the page numbers on which each is found.

Table 13-2 Key Topics for Chapter 13
Complete Tables and Lists from Memory
There are no Memory Tables or Lists in this chapter.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Mobile and Remote Access (MRA)
Public Key Infrastructure (PKI)
Video Communications Server (VCS)
Q&A
The answers to these questions appear in Appendix A. For more practice with exam format questions, use the Pearson Test Prep Software Online.
1. List the six main components required to deploy the MRA solution.
2. List the 5 different approaches to domain configuration with MRA.
Answers
1. Six MRA Components
![]() DNS
DNS
![]() MTLS Certificated
MTLS Certificated
![]() Firewall Traversal Services
Firewall Traversal Services
![]() Unified Communications configuration settings
Unified Communications configuration settings
![]() Reverse HTTPS Proxy
Reverse HTTPS Proxy
![]() SIP Trunk Security Profile on CUCM
SIP Trunk Security Profile on CUCM
2. 5 Domain configuration considerations:
![]() Single domain with split DNS
Single domain with split DNS
![]() Dual domain without split DNS
Dual domain without split DNS
![]() Single domain without split DNS
Single domain without split DNS
![]() URL for Cisco Meeting Server Web Proxy and MRA domain cannot be the same
URL for Cisco Meeting Server Web Proxy and MRA domain cannot be the same
![]() Multiple external domains for MRA
Multiple external domains for MRA
