Section 1: Cisco Layer 2 Security
A lot of attention is paid to securing the higher layers of the OSI reference model with network-level devices such as firewalls and intrusion protection systems (IPS) and applications such as antivirus and host-based intrusion protection (HIPS).
Layer 2 attacks occur, as you would expect, at Layer 2 of the OSI model. We know that switching operates at Layer 2, and therefore most of these attacks need to be mitigated in the switches that you deploy in your network.
Types of Layer 2 Attacks
We cover several types of Layer 2 attacks in this section. This section also explains how to mitigate these attacks by implementing the correct control in Cisco IOS.
The main types of Layer 2 attacks are as follows:
• CAM overflow
• VLAN hopping
• MAC spoofing
• DHCP attacks
CAM Overflow
Switches operate by building a reference table of MAC addresses and corresponding switch ports. Based on the destination MAC address, the switch knows to which port to forward the frames. This table is called the context-addressable memory (CAM) table.
The switch can hold only a specific number of MAC addresses in this table, depending on the resources available to the switch.
A CAM overflow attack is where an attacker connects to a single or multiple switch ports and then runs a tool that s the existence of thousands of random MAC addresses on those switch ports. The switch enters these into the CAM table, and eventually the CAM table fills to capacity. When a switch is in this state, no more new MAC addresses can be learned, and therefore the switch starts to flood any traffic from new hosts out of all ports on the switch.
A CAM overflow attack turns a switch into a hub, which enables the attacker to eavesdrop on a conversation and perform man-in-the-middle attacks.
Cisco implemented a technology into IOS called Port Security that mitigates the risk of a Layer 2 CAM overflow attack.
Port Security
Port Security on a Cisco switch enables you to control how the switch port handles the learning and storing of MAC addresses on a per-interface basis. The main use of this command is to set a limit as to the maximum number of MAC addresses that can be learned and allocated to the individual switch port.
If a machine starts broadcasting multiple MAC addresses in what appears to be a CAM overflow attack, the default action of Port Security is to shut down the switch interface, although you can configure the switch just to discard any frames received from the bogus MAC addresses.
Configuring Port Security
Port Security has to be configured at the interface configuration level on a Cisco IOS switch.
It is recommended that you enable Port Security on static access ports rather than dynamic access or trunk ports.
For illustrative purposes, this section shows a common Port Security configuration. We will configure Port Security to dynamically allow three MAC addresses on the configured port. We will also make these connections sticky.
We will start by ensuring that the switch port is a static access port:
Switch(config-if)# switchport mode access
The next step is to enable Port Security on the switch interface and to configure a maximum of three MAC addresses for the interface:
Switch(config-if)# switchport port-security
Switch(config-if)# switchport port-security maximum 3
The switch will learn the MAC addresses that are connected on the switch port and allow the first three it finds. In most cases, it will just be a single end-user workstation connected to the switch, and it should see only a single MAC address. The switch has to go through this process whenever the switch is rebooted. You can enable sticky mode for Port Security so that the MAC addresses that the switch learns about are stored when the configuration is saved so that they do not have to be relearned when the switch is rebooted. To enable sticky learning, enter the following command:
Switch(config-if)# switchport port-security mac-address sticky
We have just reviewed a common configuration scenario in which the switch dynamically learns and remembers the MAC address of the devices connected to it. The other, and more secure mechanism is to configure static Port Security by manually specifying the MAC address of the host connected to it.
If we have a switch port with the host MAC address 00:16:cb:96:95:94 connected to it, we can enter the following command to ensure that only this host can be connected to the switch port:
Switch(config-if)# switchport port-security mac-address 0016.cb96.9594
VLAN Hopping
Switches implement virtual LANs (VLAN). Users are connected to access ports that are members of a VLAN as specified in the configuration. VLAN hopping is where a user is able to gain access to a VLAN that is not assigned to the switch port to which the user is connected.
A user can achieve this in two ways against the default configuration of a Cisco switch port. The first and most commonly used VLAN hopping method is where the attacker makes his workstation act as a trunk port. Most switches, in the default configuration, need only one side of a connection to announce themselves as a trunk, then the switch automatically trunks all available VLANs over the switch port. This results in the attacker being able to see all traffic across all VLANs.
The second way an attacker can hop VLANs is by using what is called double tagging. With double tagging, the attacker inserts a second 802.1q tag in front of the existing 802.1q tag. This relies on the switch stripping off only the first 802.1q tag and leaving itself vulnerable to the second tag. This is not as common a method of VLAN hopping as using trunking.
To ensure you do not fall foul of a VLAN hopping attack, you have to ensure that all your user ports are assigned as access mode ports. Any unused ports should be disabled, and set as access mode ports by default.
To set a switch port to access mode, use the following configuration command from interface configuration mode:
Switch(config-if)# switchport mode access
MAC Spoofing
MAC spoofing attacks are attacks launched by clients on a Layer 2 network. Attackers spoofs their MAC address to perform what is known as a man-in-the-middle (MiTM) attack.
In one common attack, the attacker pretends to be the default gateway and sends out a gratuitous Address Resolution Protocol (ARP) to the network so that users send their traffic through the attacker rather than the default gateway. The attacker then forwards user traffic to the real default gateway. An attacker on a fast enough host can forward packets such that victims do not notice any change in their network access. Many tools available for download from the Internet can accomplish such a task, and preventing such attacks is quite problematic.
One way to mitigate this threat is to use Port Security. For this to work, however, the maximum MAC address setting must be 1, and the support headache associated with using this setting would probably be greater than the risk of this type of an attack occurring.
Private VLAN Attacks
Private VLANs (PVLAN) are special VLANs that can be used to further segment an existing Layer 2 VLAN into what are known as isolated and community ports. PVLANs are common on demilitarized zone (DMZ) segments, where the mail server does not need to communicate to the web server or similar, for example. In these instances, even though the web server and the mail server are on the same VLAN, the use of PVLANs can isolate the traffic between them so that the mail server cannot communicate with the web server unless the communication is through the default gateway.
DHCP Attacks
Dynamic Host Configuration Protocol (DHCP) is the protocol used to automatically assign a host a valid IP address out of a pre-assigned DHCP pool. DHCP has been in use for nearly as long as IP has been the main protocol used within industry.
Two types of DHCP attacks can be performed against a switched network: DHCP spoofing and DHCP starvation attacks.
In DHCP snooping attacks, an attacker configures a rogue DHCP server on the network to issue DHCP addresses to clients. The normal reason for this attack is to force the clients to use false Domain Name System (DNS) or Windows Internet Naming Service (WINS) servers and to make the clients use the attacker, or a machine under the control of the attacker, as their default gateways.
In DHCP starvation attacks, an attacker floods the DHCP server with DHCP requests to use up all the available IP addresses that the DHCP server can issue. Once these IP addresses are issued, the server cannot issue any more addresses, and this situation produces a denial-of-service (DoS) attack as new clients cannot obtain network access.
Both of these attacks can be mitigated by configuring DHCP Snooping on the switch.
DHCP Snooping
To prevent DHCP spoofing and DHCP starvation attacks, Cisco implemented DHCP Snooping as an IOS feature into their switch product line.
DHCP Snooping specifies which switch ports can respond to DHCP requests and therefore issues IP addresses using the DHCP offer and DHCP acknowledge packets. Ports on the switch are either trusted or untrusted. Trusted ports are where the DHCP servers reside, and untrusted ports are everything else.
To configure DHCP Snooping, you first have to globally enable it from global config mode and specify which VLANs it will be operating on. In this example, we enable VLAN Snooping on VLAN 10:
Switch(config)# ip dhcp snooping
Switch(config)# ip dhcp snooping vlan 10
We now have to configure the trusted interfaces where the DHCP servers reside.
From interface configuration mode, we enter the following command to make the switch port a trusted port:
Switch(config)# interface GigabitEthernet 0/1
Switch(config-if)# ip dhcp snooping trust
This port is now a trusted port, and the switch will allow a DHCP server to function as expected on this port.
Identity Based Network Services
Identity Based Network Services (IBNS) is a technology solution that expands Layer 2 security by using 802.1x technologies.
IBNS provides identity-based network access control and policy enforcement at the port level. These enforcement services include the following:
• Authentication based on per user or per device
• Policies mapped to network identity
• Port-based network access control based on (authentication, authorization, and accounting (AAA) policies
• Additional policy enforcement based on access level
Cisco IBNS offers specific services that are beyond the traditional 802.1x services. Examples include the following:
• VLAN assignment
• Tied to port security
• Voice VLAN ID
• Guest VLAN
• Access control list (ACL) assignment
• High availability with redundant supervisors for high-end Catalyst switches
802.1x
802.1x is a client/server-based access control and authentication protocol that restricts unauthorized devices from connecting to a LAN through publicly accessible ports. 802.1x is a key technology in IBNS authentication and access control. It is a standard set by the IEEE 802.1 working group that defines a link-layer protocol used for transporting higher-layer authentication protocols.
There are three main components of 802.1x:
• Supplicant: The supplicant, or client, is software running on an end device that needs access to network resources. The software can be integrated into the client, such as with Microsoft Windows, or it can be included in the firmware of the device. The supplicant sends the authentication request to access the LAN via the connected authenticator (in most cases a switch) using the Extensible Authentication Protocol (EAP).
• Authenticator: The authenticator is the device that enforces access control to the network. This device is commonly a Cisco switch. The authenticator acts as a proxy to relay information between the supplicant and the authentication server. The authenticator receives the authentication information from the supplicant via EAP over LAN (EAPOL) frames that are then forwarded to the authentication server.
• Authentication server: The authentication server is a server such as the Cisco Secure Access Control Server (ACS). The authentication server validates the supplied credentials and notifies the authenticator as to whether the client is allowed or denied access to the network.
Figure 1 shows these three components of 802.1x, along with the basic message exchange.
FIGURE 1 802.1x Components
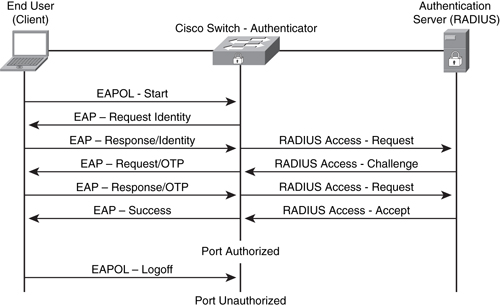
Configuring 802.1x Port-Based Authentication
Now that we have covered the basics of IBNS and 802.1x, let’s take a look at how 802.1x is implemented for port-based authentication.
We are configuring an IOS switch, which acts as the authenticator component of 802.1x. The client connecting to the switch requires supplicant software, and you have to configure the switch to communicate with the authentication server using RADIUS.
The RADIUS server has to be configured to allow 802.1x authentication and to provide information back to the authenticator, such as the correct VLAN to place the authenticated client into.
In its default state, the port on the switch will not forward traffic until it has been authenticated against with 802.1x.
In this example, we start by configuring a RADIUS server with an IP address of 10.1.1.10:
Switch(config)# aaa new-model
Switch(config)# aaa authentication dot1x default group radius
Switch(config)# aaa authorization network default group radius
Switch(config)# radius-server host 10.1.1.10 key securekey
We can now enter the 802.1x configuration. The majority of this configuration is done at the port level. When configuring multiple ports, you can save time if you use the interface range command.
In this example, we configure port-based authentication for interface fa0/1:
Switch(config)# dot1x system-auth-control
Switch(config)# interface fa0/1
Switch(config-if)# switchport mode access
Switch(config-if)# dot1x port-control auto
Switch(config-if)# dot1x guest-vlan 10
The first thing we do is to globally enable port authentication with the dot1x system-auth-control command. We then configure port authentication on interface fa0/1 with the dot1x port-control auto command. If a client fails authentication, the client is placed into the guest VLAN, which is configured as VLAN 10.
Section 1 Summary
In this section, we covered Layer 2 security. We started by looking at some common Layer 2 vulnerabilities and how you can mitigate the risk by implementing specific commands within Cisco IOS on the switch.
We finished the section by looking at IBNS. This discussion covered 802.1x and configuring port-based authentication using an IOS switch as the authenticator.
You can find more information about the Cisco IBNS on the Cisco website at http://www.cisco.com/go/ibns.
