Chapter 9. Security Assessment and Testing
Terms you’ll need to understand:
![]() Audit
Audit
![]() Vulnerability assessment
Vulnerability assessment
![]() Penetration testing
Penetration testing
![]() Trojans
Trojans
![]() Malware
Malware
![]() Rootkits
Rootkits
![]() Logic bombs
Logic bombs
![]() Forensics
Forensics
![]() Chain of custody
Chain of custody
![]() Password cracking
Password cracking
![]() Social engineering
Social engineering
![]() Viruses
Viruses
Topics you’ll need to master:
![]() Security assessment and testing
Security assessment and testing
![]() Assessment and test strategies
Assessment and test strategies
![]() Identifying attack methodologies
Identifying attack methodologies
![]() Automated and manual testing techniques
Automated and manual testing techniques
![]() Example penetration test methodology
Example penetration test methodology
![]() Crime investigation techniques
Crime investigation techniques
![]() Understanding evidence types
Understanding evidence types
![]() Performing security assessments and penetration tests
Performing security assessments and penetration tests
![]() Honeypot use and deployment
Honeypot use and deployment
![]() Incident response techniques
Incident response techniques
Introduction
Readers preparing for the ISC2 Certified Information Systems Security Professional exam and those reviewing the security assessment and testing domain must know which resources should be protected, types of tests that can be used for security control testing, and the threats that a CISSP has to be aware of.
This chapter examines audits, vulnerability assessments, and penetration tests. Each has a role to play in securing the organization. Penetration tests are carried out by organizations to see what the criminal hacker can access, how such access can be used, and what risk or impact such access might have. Keep in mind that security violations aren’t always malicious; sometimes things break or accidents happen. Therefore, security testing must also be prepared to deal with these accidents.
This chapter also discusses how the threat landscape has changed. The risks are many; it’s not just viruses and worms anymore. Attackers have many different tools available to them to hack, target, and attack organizations. There will need to be an incident response plan in place that has been tested and approved. Potential evidence will need to be handled in a legal manner and forensics may need to be performed. These are just a few of the topics this chapter will cover, along with investigations and legal proceedings.
Security Assessments and Penetration Test Strategies
The world of information security continually evolves. There are more tools available to attackers and defenders than ever before. This makes it imperative that organizations periodically review the organization’s security. This section will review several techniques for remediation and review that can be used to meet this challenge, including policy reviews (audits), vulnerability scanning, and penetration testing. Each of these techniques is useful in identifying and resolving security architecture vulnerabilities.
Audits
Policy reviews or audits are used as a means to review the presence and strength of operation (management), technical, and physical controls, and report their capability to protect the organization. Most organizations want to do the right thing and are interested in proper controls, but might just be overwhelmed by the day-to-day demands of business. This is why it is so important for auditors to verify compliance and demonstrate due diligence.
An audit is a planned, independent, and documented assessment to determine whether agreed-upon requirements and standards of operations are being met. Basically, it is a review of the operation and activities of an organization. An auditor uses the company’s standards and procedures to guide the audit. One of the most widely used frameworks for auditing is the Control Objectives for Information and related Technology (COBIT). COBIT is a system of best practices.
Although audits can help verify that controls have been developed and are being implemented, an audit is just one piece of the puzzle in ensuring operational security. Any time problems are found, an organization needs to have procedures to perform root cause analysis to discover the cause of the problem. Root cause analysis can be described as a structured approach to identifying problems, assessing their magnitude, and determining what actions need to be taken to prevent the recurrence of similar situations.
Vulnerability Assessments
The term vulnerability assessment generally refers to a software package used to scan for known vulnerabilities. Vulnerability assessments are used to identify all potential vulnerabilities that could be exploited in an environment. Much has changed in the way the IT industry views vulnerability assessments since the first software program was created for this purpose in the early 1990s. At that time, two well-known security professionals, Dan Farmer and Wietse Venema, wrote a landmark paper titled “Improving the Security of Your Site by Breaking Into it.” They went on to develop SATAN (System Administrator Tool for Analyzing Networks), the first vulnerability assessment program used to scan for problems. Sun Microsystems actually fired Dan Farmer for releasing the program. At the time the tool was seen as something that could be dual-use—for good and bad—and some people were also uncomfortable with the name.
Today, vulnerability assessment tools are used by companies around the world to scan their networks for software problems, misconfigurations, and security vulnerabilities. A vulnerability scanner can be run against a single address or a range of addresses, and can also test the effectiveness of layered security measures.
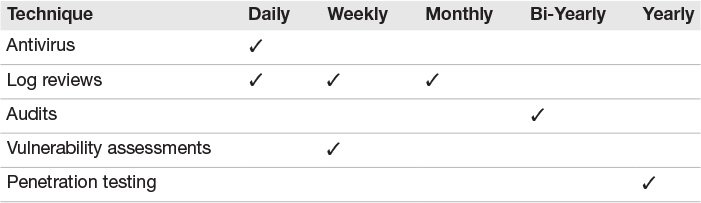
Many vulnerability assessment tools are now available. Vulnerability assessment software can be used to scan systems, compiled software, or even source code. Nessus is a good example of a system level vulnerability scanner. Even though vulnerability assessment software tools are another control that can be used to increase security, they are not a perfect solution. Vulnerability scanners cannot test for every conceivable vulnerability, and might cause a system to crash. What this really means is that vulnerability assessment tools are simply one of many items that help provide for defense in depth. As an example, you will want to layer vulnerability assessment software along with audits, penetration testing, and anti-virus to get true security. Table 9.1 provides some sample intervals for common security review functions.
Vulnerability assessment software is not a substitute for more thorough tests and examinations, a gap that penetration testing can help fill.
Penetration Testing
Penetration testing is the process of evaluating the organization’s security controls. These tests can be performed in a number of ways, including whitebox testing, blackbox testing, and graybox testing. Whitebox testing occurs when the test team knows everything about the network. The team of testers has been provided network maps, diagrams, and documents specifying all details of the organization’s network. Blackbox testing occurs when the test team has no details of the organization’s network. As an example, last year my company did a blackbox test for an organization and was provided only the IP address range. The client wanted us to ascertain all other details during the penetration test. Graybox testing is used to examine what is possible with insider access.
Although you might have seen these terms used to describe application testing, they are also used by penetration testers. Penetration testing can be performed by a manual process or via automated software packages, such as Core Impact and Metasploit. The target of the penetration test can be
![]() Outsider testing—A common type of penetration test that examines what hackers or other outsiders can access or do.
Outsider testing—A common type of penetration test that examines what hackers or other outsiders can access or do.
![]() Physical security testing—This form of penetration test refers to techniques using physical access to see what can be accomplished. Some might argue that if physical barriers can be bypassed, there is no security at all.
Physical security testing—This form of penetration test refers to techniques using physical access to see what can be accomplished. Some might argue that if physical barriers can be bypassed, there is no security at all.
![]() Wireless network testing—This form of testing is done to verify the organization’s wireless access policies and to ensure that no misconfigured devices have been introduced that may cause additional security exposures. Such tests might include Bluetooth and RFID testing of devices on premises.
Wireless network testing—This form of testing is done to verify the organization’s wireless access policies and to ensure that no misconfigured devices have been introduced that may cause additional security exposures. Such tests might include Bluetooth and RFID testing of devices on premises.
![]() Application security testing—Many organizations offer access to core business functionality through web-based applications. This can give attackers a big potential target. Application security testing verifies that the controls over the application and its process flow are adequately designed.
Application security testing—Many organizations offer access to core business functionality through web-based applications. This can give attackers a big potential target. Application security testing verifies that the controls over the application and its process flow are adequately designed.
![]() Denial-of-service (DoS) testing—The goal of DoS testing is to evaluate the network’s susceptibility to DoS attacks.
Denial-of-service (DoS) testing—The goal of DoS testing is to evaluate the network’s susceptibility to DoS attacks.
![]() War dialing—War dialing is an attempt to systematically call a range of telephone numbers and identify modems, remote access devices, and maintenance connections of computers that could exist on an organization’s network.
War dialing—War dialing is an attempt to systematically call a range of telephone numbers and identify modems, remote access devices, and maintenance connections of computers that could exist on an organization’s network.
![]() Social engineering testing—This form of penetration test refers to using social interaction techniques involving the organization’s employees, suppliers, and contractors to gather information and penetrate the organization’s systems.
Social engineering testing—This form of penetration test refers to using social interaction techniques involving the organization’s employees, suppliers, and contractors to gather information and penetrate the organization’s systems.
Caution
Penetration testing can be performed with the full knowledge of the security staff, as a blind test, or as a double-blind test. A blind test is one in which only publicly available information is used. A double-blind test is one in which only publicly available information is used and the security staff is not notified of the event. A double-blind test allows the organization to observe the reactions of the security staff.
Determining the mode of the test is just one piece of a penetration test. The network infrastructure also plays an important role. The design of the network should be such that there are layers of security. Figure 9.1 demonstrates an example of this concept.
Security tests of any type are a large undertaking. The organization will need a team to carry out these duties. This team is responsible for determining the weaknesses, technical flaws, and vulnerabilities of the organization. This team is known as a penetration test team or, informally, a red team, and the individuals on it are known as ethical hackers. Ethical hackers perform the same activities as malicious hackers, but they do so with the approval of the organization and without causing damage. The goal is to test the network in much the same fashion as a malicious hacker would. Because of the global nature of the Internet and the increased emphasis on networking, these types of activities have gained increased prominence in the last several years.
Regardless of what is known about the network, the penetration test team typically starts with basic user access. Its goal is to advance to root access or administrator access and to try to control the network. The most critical step distinguishing malicious hacking from ethical hacking is obtaining corporate approval. Without a signed consent of the company’s owner, the penetration test team could very well be breaking the law. A generic model of a penetration test is as follows:
1. Discovery or reconnaissance—Identify and document information about the targeted organization.
2. Enumeration—Use intrusive methods and techniques to gain more information about the targeted organization; for example, using software tools to scan for live machines.
3. Mapping the attack surface—Vulnerability mapping is used to discover the correlation between the findings from enumeration to known and potential vulnerabilities that could be used to gain access.
4. Exploitation—Attempt to gain user and privileged access by launching attacks against known vulnerabilities.
5. Report to management—Prepare a report of the findings of the penetration test, and detail the issues that need to be addressed, along with their priority.
Documents beyond basic penetration tests are available that offer guidance on performing tests and identifying key areas of concern. The Open Source Security Testing Methodology Manual (OSSTMM) (www.isecom.org) is a good example of a structured test guide. The Open Web Application Security Project (www.owasp.org) is another source for testing methodologies and tips. The National Institute of Standards and Technology (NIST) also has documents that are helpful for organizations planning security assessments. NIST-800-115 has areas that address:
![]() Risk analysis
Risk analysis
![]() Certification
Certification
![]() Accreditation
Accreditation
![]() Policy development
Policy development
NIST 800-115 includes recommendations for tools intended for self-evaluation. NIST divides penetration testing into four primary stages:
1. Planning—As the saying goes, success is 90% preparation and 10% perspiration. What’s the point? Good planning is the key to success. Know where you are going, what your goals are, what the time frame is, and what the limits and boundaries are.
2. Discovery—This stage consists of two distinct phases: passive and active.
![]() Passive—During this stage, information is gathered in a very covert manner. Examples of passive information gathering include surfing the organization’s website to mine valuable information and review job openings to gain a better understanding of the technologies and equipment used by the organization. This stage is deemed passive because the penetration test team is not port scanning or launching attack tools, only information gathering from available data sources.
Passive—During this stage, information is gathered in a very covert manner. Examples of passive information gathering include surfing the organization’s website to mine valuable information and review job openings to gain a better understanding of the technologies and equipment used by the organization. This stage is deemed passive because the penetration test team is not port scanning or launching attack tools, only information gathering from available data sources.
![]() Active—This phase of the test is split between network scanning and host scanning. As individual networks are enumerated, they are further probed to discover all hosts, determine their open ports, and attempt to pinpoint their OS. Nmap or Zenmap (a GUI) are popular scanning programs.
Active—This phase of the test is split between network scanning and host scanning. As individual networks are enumerated, they are further probed to discover all hosts, determine their open ports, and attempt to pinpoint their OS. Nmap or Zenmap (a GUI) are popular scanning programs.
3. Attack—At this point, the ethical hacker attempts to gain access, escalate privilege, browse the system, and finally, expand influence.
4. Reporting—This is the final step listed, but it is not the least in importance. Reporting and documentation should be conducted throughout each step of the process. This documentation should be used to compile the final report. The report should serve as the basis for corrective action. Corrective action can range from nothing more than enforcing existing policies to closing unneeded ports and adding patches and service packs.
NIST 800-115 recommends that organizations make network security a routine event and that you should always use caution when testing. Things can go wrong! It is also important that the employees be trained in security testing, so that when negative events do occur the organization has people that are already trained.
Although these are good guidelines, it’s also important to understand the limitations of security-testing activities. Penetration testing is not the cure to every conceivable problem. You still need to patch and update systems regularly, have good policies, and train employees. At the completion of the test, the results are delivered in a comprehensive report to management. Security of the report is an important issue, as is distribution and storage.
Test Techniques and Methods
There is a variety of test techniques and methods that can be used to test software, systems, and networks. The best way to start is to build security into the product. That is what the security software development lifecycle model (SSDLC) was designed for. Every step of the SSDLC model stresses the importance of incorporating security into the process. These steps are shown here:
![]() Requirements Gathering
Requirements Gathering
1. Security Requirements
2. Assessment of Risk
![]() Design
Design
1. Design requirements identification from security perspective
2. Design & architecture reviews
3. Threat modeling
![]() Coding
Coding
1. Coding best practices
2. Static analysis review
1. Vulnerability assessment
2. Fuzzing
![]() Deployment
Deployment
1. Server, network, and platform configuration review
Securing software takes a lot of time because software is very different from hardware. Most problems associated with software can be traced back to codes or errors in coding. This is the primary reason that security software development should be performed as part of system design. As an example, code review and testing might focus on which programming language was used and which functions were implemented. The C language, for instance, has some functions that can be exploited (because they do not check for proper buffer size), including strcat(), strcpy(), sprintf(), vsprintf(), bcopy(), scanf(), and gets().
You might also use misuse case testing. Think of this as a negative scenario. You are testing for things that should not happen. As an example, if you enter a negative quantity in a field that requires a positive value, will the web application actually accept it? It shouldn’t! Another example is testing for an integer overflow. This occurs when a program or application attempts to store a number in a variable that is larger than that variable’s type can handle. Consider the situation where an allocated buffer can hold a value up to 65,535. If someone can exceed this value and tries to store a value in an unsigned integer type that is larger than the maximum value, only the modulus might remain—for example, 65535 + 1 might become 0. A good example of this can be seen in Figure 9.2.
Source: https://en.wikipedia.org/wiki/Integer_overflow#/media/File:Odometer_rollover.jpg
FIGURE 9.2 Integer overflow.
Yet another test technique is synthetic transactions. These are real-time transactions that are performed on monitored objects. Synthetic transactions can be used to measure the performance of a monitored object and to see how it reacts when it is stressed. As an example, you configure a synthetic transaction on a web server that simulates a user browsing website pages and perform common activities. Synthetic transactions can be used to see whether your monitoring settings, such as alerts and notifications, perform as expected.
It’s not just about input and output data. It is also about how an application passes data from system to system, subsystem to subsystem, or variable to variable. That is where interface testing is used. Its purpose is to verify whether all the interactions between various modules and components are working properly, and whether errors are handled properly.
Once the application and/or system is deployed it still must be monitored. Security professionals should periodically monitor system logs to make sure that no problems are occurring. Some of the logs that should be reviewed include the following:
![]() System logs—Should be exported to a central location and have someone assigned to periodically review. System logs should be backed up and have a hash/timestamp applied to verify that no tampering has occurred.
System logs—Should be exported to a central location and have someone assigned to periodically review. System logs should be backed up and have a hash/timestamp applied to verify that no tampering has occurred.
![]() Event logs—Designed to record system occurrences related to memory, process, system performance, uptime, or hardware issues. While the event log is not focused on security concerns, it is still something that should be reviewed.
Event logs—Designed to record system occurrences related to memory, process, system performance, uptime, or hardware issues. While the event log is not focused on security concerns, it is still something that should be reviewed.
![]() Audit logs—Monitor and record user activity. Audit logs are a concern of security professionals as they can be used to track compliance with security policy.
Audit logs—Monitor and record user activity. Audit logs are a concern of security professionals as they can be used to track compliance with security policy.
![]() Security logs—Track events that correlate directly or indirectly with security. Security logs record information, such as user access, user-privileged operations, firewall issues, IDS/IPS alerts, and so on.
Security logs—Track events that correlate directly or indirectly with security. Security logs record information, such as user access, user-privileged operations, firewall issues, IDS/IPS alerts, and so on.
![]() Access logs—Record information pertaining to access activity. Access logs should be copied to centralized servers and protected from unauthorized access and modification.
Access logs—Record information pertaining to access activity. Access logs should be copied to centralized servers and protected from unauthorized access and modification.
Why is testing so important? Attackers are always trying to tamper with data. One example is data diddling. This type of attack works by changing data as it is keyed in or processed by a computer. It can include canceling debts without proper authority or assigning a large hourly pay increase to your salary. Trying to track down the problem is difficult, and it could be months before the attack is uncovered.
Security Threats and Vulnerabilities
Now that we have examined some of the types of tests that an organization can perform, let’s turn our attention to some of the threats and vulnerabilities. By reviewing the types of threats the organization might face, we can start to build controls to address these specific issues. It is much cheaper to be proactive and build in good controls than it is to be reactive and figure out how you are going to respond after an attack has occurred.
Threat Actors
Who are the people you have to worry about? Well, generally, they can be divided into two groups:
![]() Insiders—These are individuals who either currently work for the organization, or have been fired or quit yet still have access. These insiders could be disgruntled employees or current or former contractors.
Insiders—These are individuals who either currently work for the organization, or have been fired or quit yet still have access. These insiders could be disgruntled employees or current or former contractors.
![]() Outsiders—These individuals have never worked for you and you are probably lucky they haven’t. Overall, outsiders can be segregated into several subgroups:
Outsiders—These individuals have never worked for you and you are probably lucky they haven’t. Overall, outsiders can be segregated into several subgroups:
![]() Script kiddies—These individuals cause harm with scripts, tools, and rootkits written by other, more skilled individuals. Often they don’t understand how the exploits that they are using work.
Script kiddies—These individuals cause harm with scripts, tools, and rootkits written by other, more skilled individuals. Often they don’t understand how the exploits that they are using work.
![]() Hacktivists—These hackers have an agenda in that their attacks are driven by the need to protest or make a statement. Groups like LulzSec and Anonymous can be seen as examples. They might use DDoS tools or search for and publish private or identifying information about a target; this is known as doxing.
Hacktivists—These hackers have an agenda in that their attacks are driven by the need to protest or make a statement. Groups like LulzSec and Anonymous can be seen as examples. They might use DDoS tools or search for and publish private or identifying information about a target; this is known as doxing.
![]() Corporate spies—These individuals work for rival firms. Their goal is to steal your proprietary information.
Corporate spies—These individuals work for rival firms. Their goal is to steal your proprietary information.
![]() Skilled hackers—Although they’re not driven by corporate greed or the desire to advance agendas like hacktivists, these individuals do have motives. Maybe they are looking for ways to proclaim their advanced hacking skills, or they might be at odds with a stand or position your organization has taken.
Skilled hackers—Although they’re not driven by corporate greed or the desire to advance agendas like hacktivists, these individuals do have motives. Maybe they are looking for ways to proclaim their advanced hacking skills, or they might be at odds with a stand or position your organization has taken.
![]() Hacker researchers—These individuals may accidentally (or intentionally) discover vulnerabilities in a product or infrastructure and then attempt to communicate the issue to the responsible parties.
Hacker researchers—These individuals may accidentally (or intentionally) discover vulnerabilities in a product or infrastructure and then attempt to communicate the issue to the responsible parties.
![]() Organized crime members—The primary motivation of organized crime is to make money. Their activities might include creating and renting botnets, monetizing PII, and generating revenue from crimeware kits and ransomware.
Organized crime members—The primary motivation of organized crime is to make money. Their activities might include creating and renting botnets, monetizing PII, and generating revenue from crimeware kits and ransomware.
![]() Foreign government agents—These individuals seek ways to advance the interests of their country. Your data might be the target. Their techniques include highly customized attacks and they may spend months or years to achieve their objectives.
Foreign government agents—These individuals seek ways to advance the interests of their country. Your data might be the target. Their techniques include highly customized attacks and they may spend months or years to achieve their objectives.
Note
Being a hacker researcher is not without risk. A hacker known as Weev was part of a group that exposed a flaw in AT&T security which allowed the e-mail addresses of 114,000 iPad users, including those of celebrities, to be revealed. Weev was charged and found guilty of identity fraud and conspiracy to access a computer without authorization. While the original conviction was later overturned, Weev did serve more than a year of his original sentence.
So, which group represents the biggest threat? The distinction between insiders and outsiders isn’t always useful. We should not really trust anyone. Insiders typically have the means and the opportunity to commit a crime. All they lack is a motive. Outsiders, on the other hand, are not trusted with access and being outside the organization’s structure could present them with little opportunity or means to launch an attack. Yet outsiders can be driven by motivations like money, prestige, or national interests. Figure 9.3 shows example threat actors and sample attacks.
Attack Methodologies
Attacks typically target one or more items that are tied to the security triad: confidentiality, integrity, or availability. Whereas confidentiality and integrity attacks actually give the attacker access to your data, availability attacks do not. Availability attacks usually result in denial of service (DoS).
Hackers target a variety of devices but their modus operandi remain fairly constant. Their methodology of attack generally proceeds as follows (see Figure 9.4):
1. Footprinting—The attackers identify potential targets, looking for information in such places as the organization’s website, public databases, WHOIS, NSLOOKUP, Google groups, and EDGAR financial records.
2. Scanning—This moves beyond passive information gathering. During this step of the assault, the attackers use a variety of tools to scan for open ports and processes.
3. Enumeration—Somewhat similar to scanning, this step involves obtaining more detailed information about target devices, such as OS identification. Poorly protected network shares and weak passwords are two items that are probed for at this step of the assault.
4. Penetration—What makes this step different from the previous one is that the hacker is attacking the network with the goal of gaining access. If access is not possible, the attacker might decide to launch a DoS attack.
5. Escalation—Many times the initial level of access gained by an attacker is not root or administrator. Under these circumstances, the hacker attempts to escalate privilege, pilfer data, and gain access to restricted information.
6. Covering tracks—After they’re in control of the system, most hackers seek to destroy evidence of their activities. Most likely, they will attempt to plant tools and rootkits on the compromised system to further extend their stay. Rootkits typically serve the purpose of leaving back doors so that the attackers can come and go as they please.
Note
Escalation of privilege is required because some computer operations require special privileges to complete their tasks or can only be run from root or administrative accounts. Horizontal privilege escalation is where an attacker moves from one user account to another user account that has the same level of access. Vertical privilege escalation occurs when an attacker moves from a lower privilege to higher privileged account. Many processes can only be executed as administrator, system, or root.
Network Security Threats and Attack Techniques
Many threats to network security exist. Many attackers are opportunistic and typically take the path of least resistance. This means they choose the most convenient route and exploit the most well-known flaw. Others, such as government spies and corporate hackers, might go to great lengths to gain access to the data or information they desire. In these instances the attackers or advanced persistent threats (APTs) may spend large amounts of time and money to gain access to resources they covet. Threats to network security can include denial-of-service attacks, sniffing, session hijacking, and botnets.
Session Hijacking
This attack allows an attacker to take over an existing connection between two hosts communicating. It is an effective attack because most TCP services perform authentication only at the beginning of the session. So, in this case, the attacker simply waits until authentication is complete and then jumps in and takes control of the session. Session hijacking can be performed at the host-to-host layer or the application layer. Applications like FTP and Telnet can be targeted by prediction of sequence and acknowledgement numbers, whereas others can be targeted at the application layer. Notice how some sites may log you in as HTTPS; however, the site will continue with the HTTP connection. In such situations the session ID and variable will be passed via a cleartext cookie over port 80 instead of port 433.
Preventive measures include limiting incoming connections and the use of encryption provided by tools like Kerberos or IPsec. Cleartext protocols like FTP and Telnet are very vulnerable to session hijacking because all communication is sent in cleartext. Secure Shell (SSH) is a good alternative. SSH establishes an encrypted channel between the local and remote host. Detection can be improved by using IDS or IPS systems. The use of switches, protocols like SSH, and the design of software that uses more random initial sequence numbers (ISN’s) make session hijacking more difficult.
Sniffing
A sniffer is a packet-capturing program that captures network traffic and can decode the captured frames. Sniffers work by placing the hosting system’s network card into promiscuous mode. A network card in promiscuous mode can receive all the data it can see, not just packets addressed to it.
Sniffing performed on a hub is known as passive sniffing. When sniffing is performed on a switched network, it is known as active sniffing. Switches are smarter than traditional network hubs and know which particular switch port to send all addressed network packets to, and to block all the rest. (There can be exceptions to this rule because some switches can have one port configured to receive copies of all the packets in the broadcast domain.) Attackers might not have physical access to the switch, and as a result might use techniques like Address Resolutions Protocol (ARP) poisoning and Media Access Control (MAC) address flooding to bypass the functionality of a switch.
Sniffers operate at the data link layer 2 of the OSI model. Sniffers can intercept whatever they see on the wire and record it for later review. They allow the user or attacker to see all the data contained in the packet, even information that should remain hidden. Although sniffing is a danger, it is not quite as powerful as it once was because most organizations have replaced their hubs with switches. For sniffers to be successfully used by an attacker, the attacker must be on your local network or on a prominent intermediary point, such as a border router through which traffic passes.
Cleartext protocols are particularly at risk. An example of a cleartext FTP session is shown in Figure 9.5. To further reduce the threat of sniffing, protocols like IPSec, SSL, and Secure Shell (SSHv2) should be used to pass user names, passwords, and data.
Wiretapping
Wiretapping traditionally involves connecting to telephone wires but now it could include network sniffing, VoIP sniffing, and radio frequency sniffing (for 802.11 networking, cellular traffic, Bluetooth, and so on). If an organization does not encrypt communications before transmission takes place over public networks, it can be passively or actively eavesdropped on. In the United States, Communications Assistance for Law Enforcement Act (CALEA) requires that all telecommunication providers, regardless of the technologies involved, must make it possible to eavesdrop on all forms of communications so that law enforcement can collect information when a proper search warrant is issued. Some of the techniques used to intercept traffic include intercept access points, mediation devices, and programs installed at the ISP that perform the collection function. Although you might not be too concerned about the government intercepting data, what you should be concerned about is the fact that an attacker could also attempt to use techniques like these to intercept your sensitive and private information.
DoS Attacks
Denial-of-service attacks seek to destroy the availability of information or information systems. Such attacks can be a last-ditch effort by malicious users to bring down a network, extort money, or hold the network hostage. The attitude could be summarized as “If I can’t get in, I’ll make sure no one else does either.” Traditionally, a DoS attack might be launched simply to get attention from peers or to see whether it will really work. Look no farther than the case of MafiaBoy. In 2000, this 16-year-old teenager launched DoS attacks against websites Amazon, Dell, eBay, and others with the goal of saying “look what I can do!” Today these attacks are usually focused on a hostage-type ransom approach and are designed to make money for the attacker. Botnets are used to facilitate DoS attacks and generate revenue for those that control the army of bots. Some common DoS attacks include the following:
![]() Ping of death—An oversize packet is illegal but possible when fragmentation is used. When the fragments are reassembled at the other end into a complete packet, it can cause a buffer overflow or fill up the data pipe on the receiving system.
Ping of death—An oversize packet is illegal but possible when fragmentation is used. When the fragments are reassembled at the other end into a complete packet, it can cause a buffer overflow or fill up the data pipe on the receiving system.
![]() Smurf—Uses a spoofed ping packet addressed to the broadcast address, with the source address listed as the victim. It floods the victim with ping responses.
Smurf—Uses a spoofed ping packet addressed to the broadcast address, with the source address listed as the victim. It floods the victim with ping responses.
![]() Teardrop—Sends packets that are malformed, with the fragmentation offset value tweaked so that the receiving packets overlap. These overlapping fragments crash or lock up the receiving system, thereby causing a denial of service.
Teardrop—Sends packets that are malformed, with the fragmentation offset value tweaked so that the receiving packets overlap. These overlapping fragments crash or lock up the receiving system, thereby causing a denial of service.
![]() Land—Sends a packet with the same source and destination port and IP address. The receiving system typically does not know how to handle these malformed packets, so the system freezes or locks up, thereby causing a denial of service.
Land—Sends a packet with the same source and destination port and IP address. The receiving system typically does not know how to handle these malformed packets, so the system freezes or locks up, thereby causing a denial of service.
![]() SYN flood—A SYN flood disrupts Transmission Control Protocol (TCP) by sending a large number of fake packets with the SYN flag set. This large number of half-open TCP connections fills the buffer on the victim’s system and prevents it from accepting legitimate connections. Systems connected to the Internet that provide services like HTTP or SMTP are particularly vulnerable. Because the source IP address is spoofed in a SYN attack, it is very hard to identify the attacker.
SYN flood—A SYN flood disrupts Transmission Control Protocol (TCP) by sending a large number of fake packets with the SYN flag set. This large number of half-open TCP connections fills the buffer on the victim’s system and prevents it from accepting legitimate connections. Systems connected to the Internet that provide services like HTTP or SMTP are particularly vulnerable. Because the source IP address is spoofed in a SYN attack, it is very hard to identify the attacker.
![]() Fraggle—Similar to a Smurf attack in that its goal is to use up bandwidth. Whereas Smurf uses ICMP for the attack, Fraggle uses UDP packets. Packets are sent to the UDP port 7. It’s a popular target because it’s the echo port and will generate additional traffic. Even if port 7 is closed, the victim will still be blasted with a large amount of ICMP unreachable messages. If enough traffic is generated, the network bandwidth will be used up and communication might come to a halt.
Fraggle—Similar to a Smurf attack in that its goal is to use up bandwidth. Whereas Smurf uses ICMP for the attack, Fraggle uses UDP packets. Packets are sent to the UDP port 7. It’s a popular target because it’s the echo port and will generate additional traffic. Even if port 7 is closed, the victim will still be blasted with a large amount of ICMP unreachable messages. If enough traffic is generated, the network bandwidth will be used up and communication might come to a halt.
Distributed Denial of Service
A DDoS attack is an amplified DoS attack. The DDoS attack started to become more popular around the year 2000, when botnets started gaining ground. A DDoS attack is similar to DoS in that the goal is a disruption of service. However, it is more powerful in that it uses a large number of previously compromised systems to direct a coordinated attack against the target. These systems, known as zombies, wait until the attacker signals the attack. A DDoS attack can be devastating because of the tremendous amount of traffic generated. Historic DDoS command and control attack tools include the following:
![]() Trinoo
Trinoo
![]() Shaft
Shaft
![]() Tribal Flood Network
Tribal Flood Network
![]() TFN 2K
TFN 2K
![]() Stacheldraht
Stacheldraht
Note
2007 was the first year that a large-scale DDoS attack was launched against a nation. This attack against Estonia caused severe outages and was blamed on Russia.
Note
Today hackers use booters for DDoS. Booters are websites that offer DDoS services. These are operated by cyber crime groups that provide paying customers with DDoS attack capabilities on demand. These services can hide behind multiple layers of IP addresses and be very difficult to take down.
Botnets
This trend of launching DoS/DDoS attacks has changed. Attackers are no longer content with just making a name for themselves. Today’s attacks are about making money. These attackers might be out-of-work Eastern European and Russian computer engineers or others working from all over the globe. Attacks might be performed for extortion or to generate revenue. Botnets fulfill this need for the attacker. Botnets, which were first seen around the year 2001, are a massive collection of computers that have been compromised or infected with dormant bots or zombies. Botnets are used to distribute spam, steal passwords used at banking and shopping websites, launch denial-of-service attacks for extortion, and spread infections to other computer systems. An example of a botnet is shown in Figure 9.6.
Note
The year 2010 is notable because it was one of the first times a large group of hacktivists was able to organize a large-scale opt-in botnet attack. The attack was organized by the group Anonymous and targeted sites like MasterCard and Visa. These attacks used Low Orbit Ion Cannon (LOIC) to flood these sites and disrupt communication. Hacktivism is a combination of the words “hack” and “activism”. Hacktivists like to refer to themselves as protesters in cyberspace.
Botnet attacks start when the controller (called a bot herder) seeks to bypass the access control of third-party computers. These computers can be broadband users, home users, or even poorly configured corporate systems. To get an idea how big the problem is, Rick Wesson, CEO of Support Intelligence, stated in USA Today (www.usatoday.com/tech/news/computersecurity/2008-03-16-computer-botnets_N.htm) that on a typical day in 2008, about 40% of the 800 million computers connected to the Internet were infected with bots.
Bot herders can use a variety of techniques to avoid detection. For example, a fast-flux botnet has numerous IP addresses mapped to one domain name. This allows the attacker to swap out IP addresses at an extremely high frequency to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts that act as proxies. Figure 9.7 shows an example.
The evolution of botnets has now progressed to the point that they are packaged into crimeware kits. These prepackaged botnets offer attackers everything they need and typically include detailed instructions.
Botnets have evolved into a multi-million-dollar industry. You can read an analysis of the Zeus crimeware kit at www.techrepublic.com/whitepapers/on-the-analysis-of-the-zeus-botnet-crimeware-toolkit/3895727.
Botnets pose a real threat to computer operations and therefore require multiple layers of defense to counter this threat. Defenses include:
![]() Patched and hardened computers
Patched and hardened computers
![]() Web security appliances
Web security appliances
![]() Updated anti-virus software to identify known threats
Updated anti-virus software to identify known threats
![]() Firewalled networks and the use of IDP to monitor traffic
Firewalled networks and the use of IDP to monitor traffic
![]() Routers configured to block spoofed traffic from within a network
Routers configured to block spoofed traffic from within a network
![]() User training to guard against advanced persistent threats and to adopt safer computing practices
User training to guard against advanced persistent threats and to adopt safer computing practices
Although these techniques might not prevent all attacks, they are a good starting point. Organizations must develop better security practices to deal with this threat.
Other Network Attack Techniques
There is no shortage of attack techniques that hackers can use to attempt to violate network security. Some basic attack techniques are listed here:
![]() ARP poisoning—This attack usually is done to redirect traffic on a switch during the address resolution from IP to MAC. Because switches do not send all traffic to all ports, as a hub does, attackers must use ARP poisoning, which places the attacker in the middle of a data exchange. When this has been achieved, the attacker can attempt a series of attacks, including sniffing, session hijacking and interception of confidential information. Many tools, such as Ettercap and Hunt, are available to help the attacker perform ARP poisoning.
ARP poisoning—This attack usually is done to redirect traffic on a switch during the address resolution from IP to MAC. Because switches do not send all traffic to all ports, as a hub does, attackers must use ARP poisoning, which places the attacker in the middle of a data exchange. When this has been achieved, the attacker can attempt a series of attacks, including sniffing, session hijacking and interception of confidential information. Many tools, such as Ettercap and Hunt, are available to help the attacker perform ARP poisoning.
![]() Database attacks—These attacks target an organization’s databases. SQL injection is one common attack vector. Although the techniques vary, the results are the same: Malicious users can run their code on the victim’s database server or steal information from the server. This can be a serious threat to the integrity or confidentiality of the organization.
Database attacks—These attacks target an organization’s databases. SQL injection is one common attack vector. Although the techniques vary, the results are the same: Malicious users can run their code on the victim’s database server or steal information from the server. This can be a serious threat to the integrity or confidentiality of the organization.
![]() DNS spoofing—Much like ARP poisoning, this attack attempts to poison the DNS process while addresses are being resolved from FQDN to IP. Individuals who succeed have their fake DNS entry placed into the victim’s DNS cache or anywhere else the address resolution is taking place, such as on a cooperating DNS server. Victims then can be redirected to the wrong Internet sites, or to a rogue server filled with malware, sitting in someone’s basement and collecting your private information.
DNS spoofing—Much like ARP poisoning, this attack attempts to poison the DNS process while addresses are being resolved from FQDN to IP. Individuals who succeed have their fake DNS entry placed into the victim’s DNS cache or anywhere else the address resolution is taking place, such as on a cooperating DNS server. Victims then can be redirected to the wrong Internet sites, or to a rogue server filled with malware, sitting in someone’s basement and collecting your private information.
![]() Mail bombing—Used to target a victim with a large amount of bogus email. Mail bombing attempts to send so much email that the user’s email account is completely full.
Mail bombing—Used to target a victim with a large amount of bogus email. Mail bombing attempts to send so much email that the user’s email account is completely full.
![]() Pharming attack—Pharming exploits are another type of attack that misuses the DNS protocol. Normally DNS is responsible for translating web addresses into IP addresses. Pharming attacks hijack the DNS and force it to redirect your browser to another site, allowing fake software updates used to install malware.
Pharming attack—Pharming exploits are another type of attack that misuses the DNS protocol. Normally DNS is responsible for translating web addresses into IP addresses. Pharming attacks hijack the DNS and force it to redirect your browser to another site, allowing fake software updates used to install malware.
![]() Traffic analysis—The sniffing of encrypted traffic to deduce information. As an example, even if the data is encrypted, frequent communications can signal planning is occurring.
Traffic analysis—The sniffing of encrypted traffic to deduce information. As an example, even if the data is encrypted, frequent communications can signal planning is occurring.
![]() War dialing—This old-school attack is based on the premise that if the attacker can successfully connect to the victim’s modem, he might be able to launch an attack. War-dialing programs work by dialing a predetermined range of phone numbers in hopes of finding one connected to an open modem. The threat of war dialing is that the compromised host acts as a gateway between the network and the Internet. War dialing is resurging because of VoIP’s low cost and ability to easily spoof the source of the attack.
War dialing—This old-school attack is based on the premise that if the attacker can successfully connect to the victim’s modem, he might be able to launch an attack. War-dialing programs work by dialing a predetermined range of phone numbers in hopes of finding one connected to an open modem. The threat of war dialing is that the compromised host acts as a gateway between the network and the Internet. War dialing is resurging because of VoIP’s low cost and ability to easily spoof the source of the attack.
![]() War driving—The practice of war driving, flying, boating, or walking around an area is to find wireless access points. Many individuals that perform this activity look specifically for unsecured wireless networks to exploit. The primary threat is that these individuals might then have a direct connection to your internal network or unrestricted Internet access. This access can then be used to conduct attacks on other Internet sites, send spam, promote pump-and-dump financial schemes, sell counterfeit goods, and so on.
War driving—The practice of war driving, flying, boating, or walking around an area is to find wireless access points. Many individuals that perform this activity look specifically for unsecured wireless networks to exploit. The primary threat is that these individuals might then have a direct connection to your internal network or unrestricted Internet access. This access can then be used to conduct attacks on other Internet sites, send spam, promote pump-and-dump financial schemes, sell counterfeit goods, and so on.
![]() Zero-day exploits—A zero-day exploit can target corruption, modification, release, or interruption of data. This attack takes advantage of an exploit that might not be known to the vendor and that has no patch available.
Zero-day exploits—A zero-day exploit can target corruption, modification, release, or interruption of data. This attack takes advantage of an exploit that might not be known to the vendor and that has no patch available.
Access Control Threats and Attack Techniques
Access control is probably one of the most targeted security mechanisms. After all, its job is to keep out unauthorized individuals. To try to bypass or subvert access control, attackers can use a variety of tools and techniques, such as unauthorized access, access aggregation, password attacks, spoofing/masquerading, sniffers, eavesdropping, shoulder surfing, and even wiretapping to capture passwords.
Unauthorized Access
Information needs to be properly protected from unauthorized access, modification, disclosure, and destruction. Part of protecting data requires the selection of the best method of authentication. One important step to help determine what authentication should be used is to perform an asset valuation. Asset valuation can be used to assign the correct dollar and non-dollar value of an asset. After the value of the asset is known, you can then start to examine the appropriate access controls to prevent unauthorized access.
Caution
You can use threat modeling to examine the security risks of an application, including the problem of unauthorized access. A threat model details potential attacks, targets, and any vulnerabilities of an application. In part, threat modeling can help determine the types of access control mechanisms that are needed to prevent an attack.
To learn more about threat modeling, review Microsoft’s Threat Modeling tool at www.microsoft.com/security/sdl/adopt/threatmodeling.aspx.
Access Aggregation
Access aggregation, or privilege creep, is the collection of access permissions in one or more systems. For example, Betsy starts on the help desk and in six months moves to tech support. She now gains access to the rights and permissions of a technical support representative while maintaining help desk rights and privileges. Access aggregation is a common problem and one way that allows employees to potentially end up with a greater level of access than they should have. This is a big problem for many organizations. It violates the security principle of least privileges. I have witnessed this at almost every organization I have worked at, but it can be managed with regular user audits and a good principle of least privileges policy.
Password Attacks
Do you think your passwords are secure? In 2014, a security breach at eBay required that about 145 million users change their password. Many individuals don’t practice good password security. That is a real problem because a majority of organizations and individuals still use passwords. Attackers are well aware of this and seek out passwords to attempt to gain unauthorized access. There are many ways passwords can be obtained. Listed here are some of the more common methods of attack:
![]() Password guessing—Passwords are problematic. Most of us lack the cognitive ability to create several unique, unrelated passwords. A Gartner study performed in 2000 reported that 90% of respondents reported having passwords that were dictionary words or names, whereas only 9% used cryptographically strong passwords. During penetration testing, it’s a common technique to use local sports teams’ names, landmarks, personalized license plates from a drive-by of the target parking lot, and so on.
Password guessing—Passwords are problematic. Most of us lack the cognitive ability to create several unique, unrelated passwords. A Gartner study performed in 2000 reported that 90% of respondents reported having passwords that were dictionary words or names, whereas only 9% used cryptographically strong passwords. During penetration testing, it’s a common technique to use local sports teams’ names, landmarks, personalized license plates from a drive-by of the target parking lot, and so on.
![]() Password sharing—As discussed earlier, passwords have a real problem with repudiation. Passwords can be shared both directly and indirectly. For example, maybe a co-worker mentions how she uses a pet’s name as an easy-to-remember password. In some places, sharing passwords is a common occurrence and often happens unknowingly, especially in situations where workstations are unlocked and no timeout is enforced. Other areas might have a common shared password, such as computers in hospital wards. Doctors and nurses resist having timeouts and having to log into a system while a patient requires immediate action.
Password sharing—As discussed earlier, passwords have a real problem with repudiation. Passwords can be shared both directly and indirectly. For example, maybe a co-worker mentions how she uses a pet’s name as an easy-to-remember password. In some places, sharing passwords is a common occurrence and often happens unknowingly, especially in situations where workstations are unlocked and no timeout is enforced. Other areas might have a common shared password, such as computers in hospital wards. Doctors and nurses resist having timeouts and having to log into a system while a patient requires immediate action.
![]() Physical access—If the attacker can physically access the system, there are many tools that can be used to extract passwords. Although the passwords will most likely be encrypted, password-cracking tools can be used to attempt recovery.
Physical access—If the attacker can physically access the system, there are many tools that can be used to extract passwords. Although the passwords will most likely be encrypted, password-cracking tools can be used to attempt recovery.
![]() Sniffing password hashes—Even without direct physical access, the attacker can attempt to sniff network communication. There are many tools designed specifically for this task. Although the CISSP exam will not expect you to know the names of such tools, several are listed here for the simple purpose of helping you understand the real threat. Pass the Hash from www.coresecurity.com is one such tool that can, among other actions, passively monitor the wire and capture passwords to the screen or to a file. The Dsniff suite also contains a strong SSH attack tool that is effective against SSHv1 (see www.hackinglinuxexposed.com/articles/20020430.html).
Sniffing password hashes—Even without direct physical access, the attacker can attempt to sniff network communication. There are many tools designed specifically for this task. Although the CISSP exam will not expect you to know the names of such tools, several are listed here for the simple purpose of helping you understand the real threat. Pass the Hash from www.coresecurity.com is one such tool that can, among other actions, passively monitor the wire and capture passwords to the screen or to a file. The Dsniff suite also contains a strong SSH attack tool that is effective against SSHv1 (see www.hackinglinuxexposed.com/articles/20020430.html).
![]() Cracking—Attackers typically use one of several methods to crack passwords: a dictionary crack or a brute-force crack.
Cracking—Attackers typically use one of several methods to crack passwords: a dictionary crack or a brute-force crack.
Dictionary Crack
A dictionary crack uses a predefined dictionary to look for a match between the encrypted password and the encrypted dictionary word. Many dictionary files are available, ranging from Klingon to popular movies, sports, and the NFL. Many times, these cracks can be performed in just a few minutes because individuals tend to use easily remembered passwords. If passwords are well known, dictionary-based words, dictionary tools will crack them quickly.
Just how do cracking programs recover passwords? Passwords are commonly stored in a hashed format, so most password-cracking programs use a technique called comparative analysis (see Figure 9.8):
1. The hashed password must be recovered.
2. The recovered password is loaded into the cracking program and the dictionary list is loaded.
3. Each potential password found in a dictionary list is hashed and compared to the encrypted password.
4. If a match is obtained, the password has been discovered. If not, the program continues to the next word, computes its hashed value, and compares that to the hashed password.
These programs are comparatively smart because they can manipulate a word and use its variations. For example, take the word “password”. A dictionary-cracking program would process this one word as “Password”, “password”, “PASSWORD”, “PassWord”, “PaSSword”, and so on. All common permutations of a word are attempted.
Caution
Never store passwords as cleartext. Passwords should always be created and stored by means of a one-way hashing process.
If a dictionary attack does not recover the password, the attacker can also try simple modifications of each dictionary word. Those modifications might include adding common prefixes, suffixes, and extended characters to try to crack the password. This is called a hybrid attack. Using the previous example, these attempts would look like “123password”, “abcpassword”, “drowssap”, “p@ssword”, “pa44w0rd”, and so on. These various approaches increase the odds of successfully cracking an ordinary word or any common variation of it.
Caution
Never allow passwords to be indexed or listed on the Internet in any form. The www.hackersforcharity.org/ghdb/ website has listings of this to help identify the problem. A sample search you can perform through Google is shown here for you to see how big this problem is. Just enter the following into Google: filetype:htpasswd htpasswd.
Brute-Force Crack
If attackers have not recovered a valid password, don’t expect them to give up. A brute-force crack is a type of password assault (usually associated with encryption, but it doesn’t have to be) and can take hours, days, months, or years, depending on the complexity of the password and the key combinations used. This type of password crack depends on the speed of the CPU’s power because the attacker attempts every combination of letters, numbers, and characters. With enough time, recovery is possible. As an example, password crackers have been developed to recover passwords of 14 or fewer characters in under a week for many common operating systems. There are also many online sites that can be used for cracking or to test password strengths.
Rainbow Tables
What if you do not have a week to crack passwords? An alternative to traditional brute-force password cracking is to use a rainbow table. Whereas traditional password cracking encrypts each potential password and looks for a match, the rainbow table technique precomputes all possible passwords in advance and stores them in a table. This is considered a time/space/memory trade-off technique. Precomputing the hashes requires the creation of massive databases of hashed values for every potential password, from single characters on up, using all keyboard characters. A character set that includes ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&* ()-_+=~’[]{}|:;”’<>,.?/ would require about 64GB and a considerable amount of time to create. When this process is complete, the passwords and their corresponding encrypted values are stored in a file called a rainbow table. An encrypted password can be quickly compared to the values stored in the table and cracked within a few seconds. For those that do not have the time or want to build their own, rainbow tables are available via BitTorrent, or available online with web front ends offered via free or for-pay service.
Caution
Rainbow tables currently exist for Windows LM (LAN Manager) passwords up to 14 characters in length. These precomputed hashes have been demonstrated to attack and crack passwords with a 99% success rate in less than three hours. This means that if an attacker can recover a basic LM password, the encrypted password can most likely be cracked!
To protect yourself from these password attacks, seek to implement two-factor authentication, examine lockout thresholds, monitor access to electronic password files, and enforce a strong password policy using as many different types of characters as possible, including lowercase, uppercase, numbers, and symbols. Change your password frequently, never reuse a previous password, and never use the same password for more than one account.
Caution
Some organizations and government agencies require passwords to be longer than 15 characters. Having a longer password makes cracking it via brute force more difficult, and requires the hacker to use additional time and resources to discover the password. However, hackers constantly adjust and many are now using the cloud services offered by Amazon and others to use large numbers of virtual machines to crack passwords.
Spoofing
Spoofing can best be described as the act of pretending to be something other than what you are on a network, and can take place at different layers of the OSI model by spoofing different protocols, processes, services, and humans up and down the OSI. User spoofing occurs when one user pretends to be another user. User spoofing can occur by changing user names, IP addresses, or even MAC addresses. Process spoofing occurs when a process pretends to be a valid process when in fact it is not. An example of process spoofing is a fake login screen. This could occur inside an organization or on the web. When the victim attempts to log in, the first attempt to the fake login screen might be unsuccessful and the user information is cached. At this point, the user is redirected to the real login page for a second attempt. The victim might think they simply mistyped the password the first time.
Eavesdropping and Shoulder Surfing
Securing voice communication is a critical component of good security. There are plenty of opportunities to eavesdrop on phone calls and conversations, or intercept communication. Has anyone else noticed how people typically talk louder on a cell phone? During a recent trip, I had an interesting breakfast at the hotel because the person a few tables away gave out their username and password to someone on the phone needing assistance. Eavesdropping is the act of overhearing sensitive information or data, either on purpose or by accident. This can be by telephone, network traffic, email, or instant messaging. Shoulder surfing is a related activity in which someone glances over your shoulder while you enter a password or username. Employees should be provided security training to help them be more aware of such potential problems. Some users even use monitor mirrors to see who is behind them or looking over their shoulder (see www.thinkgeek.com/computing/accessories/2940/).
Identity Theft
Identity theft has become a big problem and can be described as the process of obtaining key pieces of information about an individual. The goal of identity theft is typically monetary. Most attacks of the past were launched for notoriety and fame. Today’s attackers seek money and access to valuable resources. Identity theft can happen when attackers dig through the trash looking for information, or attempt to trick users out of the information they need.
Current and past United States military veterans came close to learning the cost of theft of personal identification when it was revealed that the personal details of as many as 26.5 million veterans had been potentially compromised because of a stolen laptop. Although the laptop and data were eventually recovered, the possibility existed that all the data on the laptop had been copied while in possession of unauthorized persons; moreover, the recovery did not negate the breach of confidentiality or the fact that stronger security controls had not been used.
Social-based Threats and Attack Techniques
Social engineering attacks use a variety of techniques and can be launched in person, remotely via phone, or via a computer. The target of the attack can be known or unknown. Think of phishing as throwing out a broad net to all users, like the email you get from a person in Nigeria offering to give you one million dollars. Some phishing scams work by sending the victim an email from what appears to be an official site, such as a bank or credit card company. The email will usually contain a link that promises to take the user to the real website to update, change, or modify that person’s account. The real purpose of the email and link is to steal the victim’s username, PIN, account number, or password. Employees should be trained to always be wary of links obtained in emails, be alert to messages that request passwords be verified or reset, be skeptical of emails requesting information, and to always verify that the correct URL is listed in the address bar. PayPal has lots of information on phishing (see tinyurl.com/3cy86a).
Spear phishing is targeted phishing. As an example, a phishing email may be sent only to people that use a particular service. Whaling is a term used to denote the attempt to capture an important user, such as an executive or even a CEO. Some social engineering attacks make use of the SMS messaging service used over mobile phone devices; that’s known as smishing.
Another social engineering attack vector is pretexting. Pretexting is the practice of obtaining personal information about an individual under false pretenses. Pretexting is usually done when an individual wants more information about a certain individual in order to investigate their activities, so as to sue them, to steal their assets, or to obtain credit in their name. Pretexters use a variety of techniques, but these are all simple variations of social engineering techniques. Pretexters might call your cell phone provider and ask for a reprint of a bill. They also might call back and say they lost their checkbook, or even contact your credit card provider. In most cases, pretexting is illegal and there are laws against pretending to be someone else to gain personal information.
Regardless of how the victim is targeted, social engineering attacks are designed to lure victims into disclosing confidential information, passwords, or other sensitive data. Social engineering is nothing new and predates the computer era. Social engineering is much like an old-fashioned con game in that the attacker uses the art of manipulation to trick a victim. What’s interesting is that many times social engineering attacks are combined with technical attacks. As an example, you find a thumb drive in the parking lot that is labeled “spring break photos”. Unknown to you is that the photos are actually wrapped remote control software, such as Trojans, designed to infect your computer. Table 9.2 lists some well-known examples of social engineering techniques.
The best defense against social engineering is to educate your users and staff never to give out passwords and user IDs over the phone, via email, or to anyone who isn’t positively identified. Users should be leery of links and login pages that don’t look right. Training can go a long way toward teaching employees how to spot social engineering.
Note
Fake login screens are a common social engineering technique that are used to trick users into attempting to login and are usually associated with phishing. The login information is then saved so the attacker can use it at a later time. Users might be given an error or be redirected to the authentic login screen for subsequent attempts.
Malicious Software Threats and Attack Techniques
During the 1970s when mainframes were prominent, the phrase computer virus did not even exist. Fred Cowen is credited with coining the term in 1983. Early computer crimes included malware, such as the Brain (1986). The Brain was written by two Pakistani brothers that said they were just out to make a name for themselves. Even the 1988 Morris Worm was said to have been an accident. Today’s malicious software is much more advanced than the simple viruses and worms from years ago. Next we will examine the evolution of this threat.
Viruses
Virus propagation requires human activity, such as booting a computer or opening an email attachment. Some basic techniques that viruses propagate throughout the computer world include:
![]() Master boot record infection—This is the original method of attack. It works by attacking the master boot record of floppy disks or the hard drive. This was effective in the days when everyone passed around floppy disks.
Master boot record infection—This is the original method of attack. It works by attacking the master boot record of floppy disks or the hard drive. This was effective in the days when everyone passed around floppy disks.
![]() File infection—This slightly newer form of virus relies on the user to execute the file. Extensions like
File infection—This slightly newer form of virus relies on the user to execute the file. Extensions like .com and .exe are typically used. Usually, some form of social engineering is used to get the user to execute the program. Techniques include renaming the program, or renaming the .exe extension to make the file appear to be a graphic or document.
![]() Macro infection—The most modern type of virus began appearing in the 1990s. Macro viruses exploit scripting services installed on your computer. Most of you probably remember the I Love You virus, a prime example of a macro infector. Macro viruses infect applications like Word or Excel by attaching themselves to the application’s initialization sequence or automated tasks within the application. These tasks run without user intervention, and when the application is started, the virus’s instructions execute before control is given to the application. Then the virus replicates itself, infecting additional parts of the computer.
Macro infection—The most modern type of virus began appearing in the 1990s. Macro viruses exploit scripting services installed on your computer. Most of you probably remember the I Love You virus, a prime example of a macro infector. Macro viruses infect applications like Word or Excel by attaching themselves to the application’s initialization sequence or automated tasks within the application. These tasks run without user intervention, and when the application is started, the virus’s instructions execute before control is given to the application. Then the virus replicates itself, infecting additional parts of the computer.
For example, some government and/or military agencies require the use of specific formats for their memorandums. Rather than recreate new documents every time and have to look up format rules, users just use templates. These templates can carry malicious code, while appearing to do nothing more than what the users expect.
As the antivirus companies have developed better ways to detect viruses, virus writers have fought back by trying to develop viruses that are harder to detect. One such technique is to make a multipartite virus. A multipartite virus can be in more than one area of the system at once. It can infect boot sectors and program files at the same time. The idea is that this would give the virus added survivability if one part is killed by antivirus software. Another technique that virus developers have attempted is to make the virus polymorphic (from Greek “poly”, meaning “many”, and Greek “morph”, meaning “shape”). Polymorphic viruses can make copies of themselves and change their signature every time they replicate and infect a new file. This technique makes it much harder for the antivirus program to detect the virus.
Worms
Worms are unlike viruses in that they can self-replicate, while viruses require user interaction. True worms require no intervention and are hard to create. Worms do not attach to a host file, but are self-contained and propagate across networks automatically. The first worm to be released on the Internet was the 1988 Morris worm. It was developed by Robert Tappan Morris and meant to be only a proof of concept. It targeted aspects of sendmail, finger, and weak passwords. The small program disabled roughly 6,000 computers connected to the Internet. Its accidental release was a rude awakening to the fact that worms can do massive damage to the Internet. The cost of the damage from the worm was estimated to be between $10 million and $100 million.
While this was the first, many other worms have been created since then. Probably the most well-known worm in the last 10 years was Stuxnet.
Worms, like viruses, are currently in a state of decline; they are becoming less commonplace as malware creators focus their time on something that will generate revenue. Keep in mind for the CISSP exam that today’s malware is much more sophisticated and can actually perform the tasks of both viruses and worms.
Note
Spam is one of the techniques used to spread viruses and worms. While much of the spam of the past was simply junk mail, more and more of it today is malicious in nature.
Logic Bombs
Logic bombs are somewhat different from viruses and worms as they are hidden in the code itself. The logic bomb gets its name as the malicious programming code is placed in the application’s code so that it will execute under given circumstances, such as the lapse of a certain amount of time or the completion of a specific event.
Note
Logic bombs and other kinds of malware can be used to launch salami attacks. This financial crime works by taking small amounts of money from accounts over an extended period. For the attackers to be successful, they must remove an amount so small that it will go unnoticed. The movie Office Space offers a good example of this type of attack.
Backdoors and Trojans
Trojans get their name from Homer’s epic tale The Iliad. To defeat their enemy, the Greeks built a giant wooden horse with a hollow belly. The Greeks tricked the Trojans into bringing a large wooden horse into the fortified city of Troy. Unbeknown to the Trojans, and under the cover of darkness, the Greeks crawled out of the wooden horse, opened the city’s gate, and allowed the waiting Greek soldiers in, which led to the complete fall and destruction of the city.
Trojans are programs that seem to do something you want but actually perform another, malicious, act. Before a Trojan program can act, it must trick the user into downloading it or performing some type of action.
Consider the home user who sees nothing wrong with downloading a movie illegally from the Internet. After it has been downloaded, however, the user realizes the movie will not play. The user receives a message about a missing driver or codec and is prompted to go to a site that has a movie player with the right codec installed. The user does as instructed and downloads the movie player and, sure enough, everything works. Seems like a movie without any cost. Well, not quite, because at the time the user installed the movie player, he also installed a remote access Trojan (RAT). The Trojan was actually part of the player.
The Trojan may be configured to do many things, such as log keystrokes, add the user’s system to a botnet, or even give the attacker full access to the victim’s computer. A user might think that a Word doc, PDF, image, or file looks harmless and is safe to run but, once executed, it delivers its malicious payload.
Even instant messaging (IM) and Internet Relay Chat (IRC) can be used to spread Trojans. These applications were not designed with security controls in mind. You never know the real contents of a file or program that someone has sent you. IM users are at great risk of becoming a target for Trojans and other types of malware. IRC is full of individuals ready to attack the newbies who are enticed into downloading a free program or application.
You might be wondering at this point how users get Trojans. Often, the infection results from a scenario similar to the one described in the preceding section: they download one from a web site. Just consider that you get an email that appears to be from HR but is actually spoofed and has an attachment named “pending fall layoffs.” Might you be tempted to open it? Social engineering plays a big part in the infection process; after all, we all want to see the attachments that are important or which we believe is sent by a friend or coworker.
The effects of Trojans can range from benign to the extreme. Some users who become infected may not know they are infected, whereas others may experience complete system failure. More often than not, the victim may just notice that something is not right. Sometimes programs will open up by themselves, or the web browser might open pages that weren’t requested. If the hacker wants, he can read your email, browse your files, capture your keystrokes, and upload/download files.
Packers, Crypters, and Wrappers
Distributing Trojans is no easy task. Users are more alert, less willing to click email attachments, and more likely to be running antivirus or other antimalware tools than in the past. Years ago, it used to be enough for the hacker to just add more space between the filename and executable extension, like important_message_text.txt.exe, or the hacker could simply choose program suffixes or names from programs that would normally be installed and running on the victim’s machine, such as notepad.exe.
Today, it is not uncommon for attackers to use multiple layers of techniques to obfuscate code—that is, make hostile code undetectable by anti-virus programs, and to employ techniques to prevent others from examining the code. These techniques improve the attacker’s chances of controlling a computer infected by a Trojan, and using it for many types of illegal purposes. Techniques to be aware of are packers, crypters, and wrappers.
Wrappers offer hackers a method to slip past a user’s normal defenses. A wrapper is a program used to combine two or more executables into a single packaged program, essentially creating a new executable file. Some wrappers only allow two programs to be joined; others allow the binding together of three, four, five, or more programs. Basically, these programs perform like installation builders and setup programs. Wrappers also add additional layers of obfuscation and encryption around the target file.
Packers work much like programs such as WinZip, Rar, and Tar, in that they compress the file. While compression programs do this to save space, packers do this to obfuscate the activity of the malware. The idea is to prevent anyone from viewing the malware’s code until it is placed in memory. Packers serve a second valuable goal to the attacker in that they work to bypass network security protection mechanisms, such as HIDS and NIDS intrusion detection systems. It is not until the malware packer decompresses the program in memory that the program’s original code is revealed.
Crypters function to encrypt or obscure the code. Some crypters obscure the contents of the Trojan by applying an encryption algorithm. Crypters can use any encryption scheme, from AES or RSA to Blowfish, or they might use more basic obfuscation techniques, such as XOR obfuscation, Base64 encoding, or ROT 13. Again, these techniques are used to conceal the contents of the executable program, making it undetectable by antivirus software and resistant to reverse-engineering efforts. A quick search on the Internet will show you how many different types of these tools are readily available. An example is shown in Figure 9.9.
Rootkits
Rootkits are a collection of tools that allow an attacker to take control of a system. Rootkits can be divided into several different types. These include application, kernel module, hardware, firmware, and bootloader. As an example, a loadable kernel module (LKM) rootkit is loaded as a driver or kernel extension. Because LKM rootkits corrupt the kernel they can do almost anything, and are by far the most dangerous. Rootkits can also avoid detection by many software methods, but there are means to detect them. Tools like MD5sum, Tripwire, and GMER can be a big help in uncovering some types of rootkits. Although the use of rootkits is very widespread, many security professionals still don’t know much about them.
Once installed, a rootkit can be used to hide evidence of an attacker’s presence and give them backdoor access to the system. Rootkits can contain log cleaners that attempt to remove all traces of the attacker’s presence from the log files. Even if you can detect and clean a system with a rootkit, the fact is that a majority of individuals who attack systems go unpunished. Even though you may find evidence of an attack, that doesn’t mean the individual will be brought to justice.
Crimeware Kits
Crimeware kits offer someone with no or little programming experience the ability to create, customize, and distribute malware. A large portion of these kits are sold by hackers from eastern Europe and Russia. In fact, roughly 70 percent of crimeware and exploit kits released in the fourth quarter of 2012 came from Russia, according to a study by Solutionary (news.softpedia.com/news/Solutionary-Q4-2012-Report-70-of-Exploit-Kits-Originated-in-Russia-323487.shtml).
A well-known example of crimeware is Citadel. It became popular around 2014 in part because of its ease of use. Citadel allows individuals to create their own tailored Trojan botnets and was a popular crimeware kit for entry-level criminals to get involved in cybercrime.
Some crimeware also offers bulletproof hosting. Bulletproof hosting refers to the practice of protecting malware-infected websites from being shut down by their service providers. In the U.S., for instance, when a website is found to contain malware, there are legal recourses to take the site offline and prevent it from being used to infect other websites. That is not always the case in Russia—these infected websites are sometimes protected from takedowns, allowing cybercriminals to thrive by having a safe platform to host their malware for infecting U.S. consumers and businesses.
Advanced Persistent Threats
Advanced persistent threats (APTs) refer to a group, government, or organization that has the capability to target an organization for an extended period of time. Such attackers might use sophisticated malware and techniques to exploit vulnerabilities in targeted systems. The Stuxnet worm is an example of an APT.
Ransomware
Imagine this: you come in-to work one day, boot up your laptop and find a warning message on your screen like the one shown in Figure 9.10. Sometimes the messages claim to be from the FBI, an international law enforcement agency, or it may accuse users of illegal activity, perhaps visiting illegal or inappropriate websites. What they all have in common is one thing: a hacker has taken over your computer and wants money before he or she will give it back. What I have just described is ransomware. Ransomware is a type of malware that hackers use to install on your computer so they can lock it from a remote location and then demand money.
Experts estimate that as many of 3% of victims actually pay the ransom, meaning that criminals are making money from the scheme. One recent ransomware scheme netted the criminals approximately $30,000 a day, according to Symantec (www.symantec.com/content/dam/symantec/docs/reports/istr-21-2016-en.pdf).
Another important item to keep in mind is that if your computer gets infected with ransomware, it may difficult or impossible to open your files. This is why it’s so important to constantly back up your data and encrypt it yourself; then, when it is stolen, you can tell the bad guys to keep your encrypted data because it is useless to them, and you can just restore your backup. There are many ways to back up either locally or to cloud-based providers. You need to be prepared for a disaster like this because you may not get a second chance to recover your data.
Caution
Closely related to ransomware is rogue security software. It is fake antivirus software that attempts to convince users their computer is infected, and manipulates them into buying and downloading the fake software. Don’t click the link and download this software—this is a link that infects your computer.
How Computer Crime Has Changed
Computer crime has changed much since the early days of computing. During these early years, computer criminals were typically seeking fame and publicity. Just consider the following:
![]() The Melissa virus—Written to impress a girl.
The Melissa virus—Written to impress a girl.
![]() I Love You virus—Written because the creator was bored with school.
I Love You virus—Written because the creator was bored with school.
Early threats were very one dimensional in that they came on strong, caused widespread damage, and hit the Internet like tsunamis. These attacks used large amounts of network traffic and required significant amounts of time to repair. Security professionals quickly turned to products like antivirus and intrusion detection to counter this threat. Somewhere around the year 2000, computer organizations and individuals began to face new threats. Traditional countermeasures started losing their effectiveness. Initially, these threats came in the form of spam and spyware.
Criminals are no longer working alone and are typically much more focused on financial gain. Today they might be financed by organized crime, businesses, or even governments. The attack vectors available to such criminals has also multiplied as rising market share of laptops, portable devices, mobile technologies, USB drives, and Wi-Fi–enabled devices offer attackers new targets. To get an idea of how big this problem is, go to your favorite web search engine and enter “stolen laptops and identity theft.”
2007 became the first year that a large-scale DDoS attack was launched against a nation state. This attack against Estonia caused severe outages and was blamed on Russia, according to www.virusbtn.com/news/2007/05_17_virus.xml. The last several years has also shown an increase in firms and countries accusing other nations of launching attacks and engaging in cybercrime. These types of crimes are difficult to prove. In 2014, the U.S. Department of Justice announced that a federal grand jury had returned an indictment of five Chinese nationals on charges of theft of confidential business information and intellectual property from U.S. commercial firms, and of planting malware on their computers. It is believed these hackers had direct ties to the Chinese government.
In 2015, www.krebsonsecurity reported that several Israeli citizens were indicted and accused of hacking into JPMorgan Chase in 2014, stealing the names, addresses, phone numbers, and email addresses of the holders of some 83 million accounts at the financial institution. The Justice Department has dubbed this breach the “largest theft of customer data from a U.S. financial institution in history.”
New technologies will be required for the security professional to deal effectively with these threats, such as Intrusion Detection and Prevention (IDP), Network Access Control (NAC), and other technologies to detect advanced persistent threats (APTs). These issues make it important for the security professional to understand ethics, computer crime, laws, incident response, and forensics.
Well-Known Computer Crimes and Criminals
The well-known hackers of today grew out of the phone-phreaking activities of the 1960s. In 1969, “The Midnight Skulker,” Mark Bernay, wrote a computer program that allowed him to read everyone else’s IDs and passwords at the organization where he worked. Although he was eventually fired, no charges were ever filed because computer crime was so new; there were no laws against it. Some well-known computer hackers and crackers include the following:
![]() John Draper—Dubbed “Captain Crunch” for finding that a toy whistle in a box of Cap’n Crunch® cereal had the same frequency as the trunking signal of AT&T—2600 Hz. This discovery was made with the help of Joe Engressia. Although Joe was blind, he could whistle into a phone and produce a perfect 2600 Hz frequency.
John Draper—Dubbed “Captain Crunch” for finding that a toy whistle in a box of Cap’n Crunch® cereal had the same frequency as the trunking signal of AT&T—2600 Hz. This discovery was made with the help of Joe Engressia. Although Joe was blind, he could whistle into a phone and produce a perfect 2600 Hz frequency.
![]() Robert Morris Jr.—The son of a chief scientist at the NSA, Morris accidentally released the “Morris Worm” from a Cornell lab in 1988. This is now widely seen as the first release of a worm onto the Internet.
Robert Morris Jr.—The son of a chief scientist at the NSA, Morris accidentally released the “Morris Worm” from a Cornell lab in 1988. This is now widely seen as the first release of a worm onto the Internet.
![]() Kevin Mitnick—Known as Condor, Mitnick was the first hacker to hit the FBI’s Most Wanted list. Mitnick was known for his social engineering attacks. One such attack targeted Motorola. He was arrested in 1994, but has now been released and works as a legitimate security consultant.
Kevin Mitnick—Known as Condor, Mitnick was the first hacker to hit the FBI’s Most Wanted list. Mitnick was known for his social engineering attacks. One such attack targeted Motorola. He was arrested in 1994, but has now been released and works as a legitimate security consultant.
![]() LulzSec—A Black Hat hacker group that claimed responsibility for hacking into the CIA, FBI, and Sony. Other high-profile hacks include hacking into a News Corporations account and placing a false report that Rupert Murdoch had passed away and planting another fake news story on PBS that Tupac was alive and living in New Zealand.
LulzSec—A Black Hat hacker group that claimed responsibility for hacking into the CIA, FBI, and Sony. Other high-profile hacks include hacking into a News Corporations account and placing a false report that Rupert Murdoch had passed away and planting another fake news story on PBS that Tupac was alive and living in New Zealand.
![]() Hector Monsegur—Known as Subu, this hacker served as one of the leaders of LulzSec. After being arrested by the FBI, he turned informant.
Hector Monsegur—Known as Subu, this hacker served as one of the leaders of LulzSec. After being arrested by the FBI, he turned informant.
![]() Albert Gonzalez—Known for his SQL injection attacks against sites like TJ Maxx, Gonzalez was charged with stealing and reselling more than 170 million credit card and ATM numbers. In March of 2010, he was sentenced to 20 years in federal prison.
Albert Gonzalez—Known for his SQL injection attacks against sites like TJ Maxx, Gonzalez was charged with stealing and reselling more than 170 million credit card and ATM numbers. In March of 2010, he was sentenced to 20 years in federal prison.
Tip
Can a 75-cent error lead to the discovery of foreign government hackers? It did for Clifford Stoll. He used the accounting error to track down and find KGB hackers. Being trained in astrophysics didn’t deter him, nor did initial resistance from the FBI in taking him seriously. You can read more about it in his book The Cuckoo’s Egg (Doubleday, 1989).
Investigating Computer Crime
Security incidents can come in many forms. It could be an honest mistake by an employee who thought he was helping or it could be the result of an intentional attack by an insider or outsider. One of the basic tests to help identify or eliminate the proper suspect is Means, Opportunity, and Motive (MOM), as illustrated in Figure 9.11. This is also known as the crime triangle and demonstrates why insiders pose a greater threat to security than outsiders. Insiders possess the means and opportunity to launch an attack whereas outsiders might have only a motive.
Whatever the motive or reason, the response should always be the same. Security breaches should be investigated in a structured, methodical manner. Most companies would not operate a business without training their employees how to respond to fires, but many companies do not build good incident response and investigation procedures for cybercrime.
Computer Crime Jurisdiction
The unpleasant truth is that tracking and prosecuting hackers can be a difficult job because international law is often ill-suited to deal with these problems. Unlike conventional crimes that occur in one location, hacking crimes might originate in India, use a compromised computer network located in Singapore, and target a computer network located in Canada. Each country’s conflicting views on what constitutes cybercrime, and disagreements on how, or even if, the hackers should be punished can cause a legal nightmare. It is hard to apply national borders to a medium like the Internet that is essentially borderless. The United States has proposed legislation that will claim jurisdiction over any criminal activity that travels through a U.S.-controlled portion of the Internet, regardless of the starting or destination country.
Incident Response
The Defense Advanced Research Projects Agency (DARPA) formed an early Emergency Response Team in 1988. Many people attribute the founding of the Computer Emergency Response Team (CERT) to the Morris Worm, which occurred earlier that year. The “Information Superhighway” was little more than a dirt road in 1988, so the delayed response wasn’t fatal. Few of us today have the same luxury with regard to waiting until after an attack to form an incident response plan. To reduce the amount of damage that these individuals can cause, organizations need to have incident response and handling policies in place. These policies should dictate how the organization handles various types of incidents. Most companies set up a Computer Security Incident Response Team (CSIRT) or Computer Incident Response Team (CIRT) because CERT is now a registered trademark of Carnegie Mellon University. The CIRT’s function is
![]() Analysis of an event notification
Analysis of an event notification
![]() Response to an incident if the analysis warrants it
Response to an incident if the analysis warrants it
![]() Escalation path procedures
Escalation path procedures
![]() Resolution, post-incident follow-up, and reporting to the appropriate individuals
Resolution, post-incident follow-up, and reporting to the appropriate individuals
![]() Deter future attacks
Deter future attacks
The first step is the analysis of the event. An event is a noticeable occurrence. As an example, an IDS alert was tripped. This requires an investigation because it must be determined whether the event was an incident. An incident is an adverse event or series of events that violates law, policy, or procedure. The individuals investigating the incident need a variety of skills, including
![]() Recognition skills and abilities
Recognition skills and abilities
![]() Technical skills and abilities
Technical skills and abilities
![]() Investigative and response skills
Investigative and response skills
The individuals in charge of the incident must be able to recognize that something has happened. In the example of the IDS alert, recognition is not enough because those responsible must also have the ability to look at logs, event records, and perform incident analysis. Skills are also needed to properly investigate the incident. This requires understanding concepts like chain of custody. Let’s look now at who should be involved in this process as the incident response team.
Incident Response Team
Incident response team members need to have diverse skill sets. Internal teams should include representation from various departments:
![]() Information security
Information security
![]() Legal
Legal
![]() Human resources
Human resources
![]() Public relations
Public relations
![]() Physical security
Physical security
![]() Network and system administration
Network and system administration
![]() Internal auditors
Internal auditors
![]() Information Technology Helpdesk
Information Technology Helpdesk
There will be many people involved in the incident if the attack came from the inside. Legal, HR, and others must determine what will be done. Incidents traced to the outside of organizations must also have many groups involved. Will management want to involve the police? If so, someone will need to act as a company spokesperson. Roles must be clearly defined, as must the process for escalating incidents to the proper authority. With the team in place, let’s turn our attention to the specific steps of the incident response process.
Incident Response Process
Incident response requires organizations to define the specific steps that will be carried out when an incident takes place. Good incident response procedures give the organization an effective and efficient means of dealing with the incident in a manner that reduces the potential impact. These procedures should also provide management with sufficient information to decide on an appropriate course of action. By having these procedures in place, the organization can maintain or restore business continuity, defend against future attacks, and prosecute violators to deter attacks.
The primary goal of incident response is to contain the damage, find out what happened, recover from the incident, get systems back online, and prevent it from reoccurring. This list identifies the basic steps of incident response (see Figure 9.12):
1. Planning and preparation—The organization must establish policies and procedures to address the potential of security incidents.
2. Identification and evaluation—The detection of the event. Automated systems should be used to determine whether an event occurred. There must be a means to verify that the event was real and not a false positive. The tools used for identification include IDS, IPS firewalls, audits, logging, and observation.
Caution
Is it an event or an incident? An event is a noticeable occurrence, whereas an incident is a violation of policy or law.
3. Containment and mitigation—Preplanning, training, and the use of predeveloped procedures are key to this step in the process. The incident response plan should dictate what action is required to be taken. The incident response team requires training to the desired level of proficiency to properly handle the response. This team will also need to know how to contain the damage and determine how to proceed.
Note
Management needs to make the decision as to whether law enforcement should be called in during a security breach. There are reasons both pro and con as to why they may or may not be notified.
4. Eradication and recovery—Containing the problem is not enough. It must also be removed and steps need to be taken to return to normal business processes.
5. Investigate and closure—What happened? When the investigation is complete, a report, either formal or informal, must be prepared. This will be needed to evaluate any needed changes to the incident response policies.
6. Lessons learned—At this final step, all those involved will need to review what happened and why. Most importantly, what changes must be put in place to prevent future problems? Learning from what happened is the only way to prevent it from happening again.
Incident Response and Results
Incident response procedures must be of such detail that specific types of incidents are documented and advice given as to what the proper response would be. Documentation to address each of these potential incidents is critical because investigating computer crime is complex and involved. Missteps can render evidence useless and unusable in a court of law. This means that team members must be knowledgeable of the proper procedures and have had training on how to secure and isolate the scene to prevent contamination. Table 9.3 outlines some sample response strategies.
In the end, incident response is about learning. The results of your findings should be fed back into the system to make changes or improve the environment so that the same incident isn’t repeated. Tasks you might end up doing because of an attack include the following:
![]() Figuring out how the attack occurred and looking for ways to prevent it from happening again.
Figuring out how the attack occurred and looking for ways to prevent it from happening again.
![]() Upgrading tools or software in response to finding out what the team lacked that prevented effective response to the incident.
Upgrading tools or software in response to finding out what the team lacked that prevented effective response to the incident.
![]() Finding things that went wrong and making changes to the incident response plan to improve operations during the next incident.
Finding things that went wrong and making changes to the incident response plan to improve operations during the next incident.
Although no one ever wants to end up in court or to take incident response to the next level, this is not always how it works out. All incident response must be handled meticulously to be prepared for whatever unfolds in an investigation. Sometimes, the forensic skill level required will mandate that the forensic analysis be handed off to a more skilled forensics lab. The next section discusses what happens in forensic labs.
Caution
Ultimately, incident response is about learning. What happened, how did it happen, can we prevent it from happening again, how can we better prepare and respond for the next time, and what did we learn? These are the questions that should be answered.
Forensics
Although government, military, and law enforcement have practiced forensics for many years, it’s a much younger science for private industry. Its growth can be tied to the increased role of computers in the workplace and the type of information and access these computers maintain. There are four types of digital forensics:
![]() Software forensics—Includes the analysis of malware and other types of malicious code, such as bots, viruses, worms, and Trojans. Companies like McAfee and Symantec perform such duties. Tools like decompilers and disassemblers are used.
Software forensics—Includes the analysis of malware and other types of malicious code, such as bots, viruses, worms, and Trojans. Companies like McAfee and Symantec perform such duties. Tools like decompilers and disassemblers are used.
![]() Network forensics—Includes the review of network traffic and communication. Tools used include sniffers like Wireshark and Snort.
Network forensics—Includes the review of network traffic and communication. Tools used include sniffers like Wireshark and Snort.
![]() Computer forensics—Includes the review of hard drives, solid state drives, and computer media, such as CDs, DVDs, USB thumb drives and so on. Tools used include hex editors, Encase, and FTK.
Computer forensics—Includes the review of hard drives, solid state drives, and computer media, such as CDs, DVDs, USB thumb drives and so on. Tools used include hex editors, Encase, and FTK.
![]() Hardware/embedded device forensics—Includes the review of smart phones, tablets, routers, and other hardware devices.
Hardware/embedded device forensics—Includes the review of smart phones, tablets, routers, and other hardware devices.
Tip
Hardware forensics continues to grow in importance as our reliance on electronic devices increases. One report for a former Pentagon analyst alleges that a large amount of foreign-made Telco gear has built-in back doors. See www.zdnet.com/former-pentagon-analyst-china-has-backdoors-to-80-of-telecoms-7000000908/ for more details.
As a foray into forensics, computer forensics will be examined. This branch of forensics is a complex field and includes the following:
1. Plan and prepare by means of procedures, policies, and training.
2. Secure and isolate the scene to prevent contamination.
3. Record the scene by taking photographs and recording data in an investigator’s notebook.
4. Interview suspects and witnesses.
5. Systematically search for other physical evidence.
6. Collect or seize the suspect system or media.
7. Package and transport evidence.
8. Submit evidence to the lab for analysis.
Before discussing the basic steps of computer forensics, let’s examine the overall concepts and targets of forensic activities. Computer forensics defines a precise methodology to preserve, identify, recover, and document computer or electronic data. Growth in this field is directly related to the ever-growing popularity of electronics.
Computers are one of the most targeted items of examination, but they are not the only devices subject to forensic analysis. Smartphones, PDAs, tablets, digital cameras, iPods, USB drives, and just about any electronic device can also be analyzed. Attempted hacking attacks and allegations of employee computer misuse have added to the organization’s need to examine and analyze electronic devices. Mishandling concerns can cost companies millions. Companies must handle each event in a legal and defensible manner. Computer forensics follows a distinct and measurable process that has been standardized.
Standardization of Forensic Procedures
In March 1998, the International Organization on Computer Evidence (IOCE) was appointed to draw up international principles for the procedures relating to digital evidence. The goal was to harmonize methods and practices among nations and guarantee the capability for using digital evidence collected by one country in the courts of another country. The IOCE (www.ioec.org) has established the following six principles to govern these activities:
![]() When dealing with digital evidence, all generally accepted forensic and procedural principles must be applied.
When dealing with digital evidence, all generally accepted forensic and procedural principles must be applied.
![]() Upon seizing digital evidence, actions taken should not change that evidence.
Upon seizing digital evidence, actions taken should not change that evidence.
![]() When it is necessary for a person to access original digital evidence, that person should be trained in the techniques to be used.
When it is necessary for a person to access original digital evidence, that person should be trained in the techniques to be used.
![]() All activity relating to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review.
All activity relating to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review.
![]() An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in his or her possession.
An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in his or her possession.
![]() Any agency that is responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles.
Any agency that is responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles.
1. Acquire—This is usually performed by means of a bit-level copy. A bit-level copy is an exact duplicate of the original data using a write blocker, allowing the examiner to scrutinize the copy while leaving the original copy intact.
2. Authenticate—This process requires an investigator to show that the original data is unchanged and has not been tampered with, and that the bit-level copy is an exact copy. Authentication can be accomplished through the use of checksums and hashes, such as MD5 and SHA.
Tip
Message digests, such as MD5 and SHA, are used to ensure the integrity of files and data and to ensure that no changes have occurred.
3. Analyze—The investigator must be careful while examining the data and ensure that all actions are thoroughly documented. The investigator recovers evidence by examining files, state information, drive slack space, file slack space, free space, hidden files, swap data, Internet cache, and other locations, such as the Recycle Bin. Copies of the original disks, drives, or data are usually examined to protect the original evidence.
The methods used to handle, recover, and document evidence often determines whether the best evidence is admissible as credible and relevant. Let’s start by reviewing the acquisition process in more detail.
Acquire
To acquire is to assume possession of evidence or contracting to assume possession. In many instances, the forensic analyst is asked to acquire hard drives, computer, media, or other items on site. Just as with any investigation, the analyst should make careful notes as to what physical evidence is recovered, and include a chain of custody of all evidence acquired. Physical evidence and computer forensics can help build a relationship between the incident scene, victim, and suspect. Figure 9.13 illustrates this relationship.
Acquisition includes the following items:
![]() Documenting and collecting the evidence
Documenting and collecting the evidence
![]() Protecting chain of custody
Protecting chain of custody
![]() Identification, transportation, and storage
Identification, transportation, and storage
![]() Approved duplication and copy
Approved duplication and copy
During collection and handling of evidence, it is important to record everything. A digital camera can be used to record the layout of the scene. Document the condition of the computer systems, attachments, cables, physical layout, and all electronic media. The camera can even be used to take pictures of any screen settings visible on a running system. You will also want to document internal storage devices and hardware configuration, to include hard drive make, model, size, jumper settings, location, and drive interface as well as internal components such as sound card, video card, and network card. The goal is for the forensic analyst to keep adequate records and begin to build a proper chain of custody. Although the chain of custody is something that those in law enforcement are familiar with, it might be new to many IT professionals but will surely be called into question for all digital evidence in the court of law as well. Chain of custody is used to address the reliability and creditability of evidence. Chain of custody should be able to answer the following the questions:
![]() Who collected the evidence?
Who collected the evidence?
![]() Where was the evidence collected?
Where was the evidence collected?
![]() When was possession of the evidence taken?
When was possession of the evidence taken?
![]() How was the evidence stored and protected, meaning which software tool was used? Is this tool a best practice used by the industry? Is the professional trained on the tool? How many times has the professional used the tool?
How was the evidence stored and protected, meaning which software tool was used? Is this tool a best practice used by the industry? Is the professional trained on the tool? How many times has the professional used the tool?
![]() If the was evidence removed from storage, why, by whom, and for how long?
If the was evidence removed from storage, why, by whom, and for how long?
Chain of custody is the process of documenting the journey of any and all evidence while keeping it under control.
Caution
Computer evidence is very volatile; as such it is of utmost importance to protect the chain of custody throughout the entire evidence lifecycle.
Even though many forensic investigations might not lead to a court case or legal showdown, you must always maintain the integrity of the evidence in case it does. After collecting and recording the evidence, it is likely that you have now reached the point at which you might need hard drives or fixed disks for duplication. Any analysis will need to be performed on a copy of the original evidence so that the original can remain safely stored away. The objective of disk imaging is to preserve the original copy in a pristine state and to provide the analyst with a copy to use for investigation. This process usually consists of three steps, which are:
1. Remove the drive from the suspect’s computer.
2. Connect the suspect’s drive to a write blocker and fingerprint it using a message digest.
3. Use a clean wiped drive to make a copy of the suspect’s computer, or copy to an image file.
The copy must be an exact copy of the original. This is known as a bit-level copy, or physical copy. A bit-level copy copies everything, including all files, file slack, and drive slack or free space. A logical copy will not perform this type of copy.
Caution
Investigators must use caution when seizing computer systems because the equipment might be booby-trapped. That is, the device may be set up to act as a dead man’s switch that will activate when a network connection is broken or when a computer case is opened. In this situation, the switch can wipe all the information on a device, encrypt files, turn off a self-encrypted drive, or take other actions which will make the data inaccessible.
It’s critical that the hard drive used to receive a copy of the evidence not have any files, data, or information stored on it. Common practice is to wipe the drive before using it to receive the copy. Drive wiping is the process of overwriting all addressable locations on the disk. The Department of Defense (DoD) drive-wiping standard #5220-22M states, “All addressable locations must be overwritten with a character, its complement, then a random character and verify.” Drive wiping is useful for forensic purposes, organizations that want to dispose of hard drives, and criminals who want to dispose of evidence. By making up to seven passes over the media, an organization can further decrease the possibility of data recovery.
Authenticate
Having an exact copy is just a start. It must also be shown that the copy and the original are exactly the same. This verification can be accomplished by means of hashing or other integrity algorithms that fingerprint the original drive and the forensically produced copy. Integrity checks ensure the veracity of the information, and allow users of that information to have confidence in its correctness. There are many ways that data can become distorted, either accidentally or intentionally. A forensic analyst must protect against both.
Integrity
Integrity can apply to paper documents as well as electronic ones. Forgers can copy and create fake paper documents, but it is not a skill easily learned. Integrity in electronic documents and data is much more difficult to protect. Forensic duplication and verification requires cryptographic algorithms. These routines use one-way hashing algorithms. Rules of evidence generally require that when a duplicate of the original data is admitted as evidence, it must be an exact duplicate of the original. The hash values must match and be of sufficient strength to overcome the argument of tampering. Not every investigation you become involved in will go to court, but ethics and good practice require that evidence be authenticated as unchanged, from the moment of discovery to the point of disposal. Now let’s look at the third step, analysis.
Tip
A primary image is the original image. It should be held in storage and kept unchanged. The working image is the one used for analysis purposes. Forensics examiners should work on the copy only.
Analysis
Analysis is the process of examining the evidence. Forensic analysts typically make two copies of the original drive and work with one of the copies. Some common items of investigation include
![]() Word documents, ZIP files, images
Word documents, ZIP files, images
![]() Deleted items
Deleted items
![]() Files created/accessed/modified on suspect dates
Files created/accessed/modified on suspect dates
![]() Email files (.PST and the like)
Email files (.PST and the like)
![]() Files stored in NTFS streams
Files stored in NTFS streams
In real life, forensic investigators use many different programs to review the evidence. We have been discussing dead analysis, where a machine is turned off and the drive analyzed. Sometimes, a machine must be analyzed without turning it off, which is a live analysis. In this case, it is critical that evidence be examined from most the volatile to least volatile. Please note that no single program will do everything you need to perform during an investigation. Some software tools are available only for law enforcement, whereas others, such as hex editors, are publicly available. Hex editors can be used to examine slack space and deleted items.
Tip
The handling of evidence is of special importance to the forensic investigator. This is addressed through the chain of custody, a process that helps protect the integrity and reliability of the evidence by providing an evidence log that shows every access to evidence, from collection to appearance in court.
Investigations
Investigations are another important part of this domain. An investigation is typically a probe or inquiry into questionable activities and can occur after an incident response or in conjunction with forensic activities. Our limits as IT professionals are much different from law enforcement professionals. Some areas of concern are reviewed in the sections that follow.
Search, Seizure, and Surveillance
In the workplace, surveillance can be broken down into two categories:
![]() Physical—Closed-circuit television (CCTV) cameras, observation, and security guards
Physical—Closed-circuit television (CCTV) cameras, observation, and security guards
![]() Logical—System monitoring, keystroke logging, and network sniffers
Logical—System monitoring, keystroke logging, and network sniffers
Caution
Before you attempt any type of monitoring, be sure to check with your organization’s legal department. Most states and federal law require that each user operating the computer be notified of such activities. Otherwise, you could be breaking federal or state laws.
Interviews and Interrogations
At some time during the investigation, it might be determined that interviews and interrogations need to be conducted. If so, areas of concern include the possibility that disclosing the investigation might tip the suspect to halt his or her activities. The suspect might also flee to avoid prosecution. Some suspects might even try to deceive the investigator to prevent further action. Many individuals will lie or misrepresent the truth to avoid being fired or face legal action.
Investigators must be properly trained to carry out interviews and interrogations. As an example, investigators must understand the difference between enticement and entrapment. Enticement is legal and ethical, whereas entrapment is illegal. This is an issue with honeypots, which are discussed next.
Honeypots and Honeynets
Honeypots and honeynets are much like an IDS in that they are tools for detecting intrusion attempts. A honeypot is really a tool of deception. Its purpose is to fool an intruder into believing that the honeypot is a vulnerable computer. Honeypots contain files, services, and databases that have no real value to an organization if compromised, but are generally attractive to the hacker. Honeypots are effective because they can appear attractive without risking sensitive information. For these lures to be effective, they must adequately persuade hackers that a real system has been discovered. Some honeypot vendors sell products that can simulate an entire network, including routers and hosts, that are actually located on a single workstation—these are called honeynets. The honeynet can be deployed in such a manner that it is a separate server not being used by production.
Real servers can generate tons of traffic, which can make it hard to detect malicious activity. Because nothing is running on the honeypot or honeynet, any activity can be easily detected as potential intrusions.
Honeypots can be configured as low interaction or high interaction. Low-interaction honeypots simulate only some parts of the service. As an example, using a tool like netcat as a low-interaction honeypot, you can set a listener on a common port:
nc -v -n -l -p 80
This would show the port as open but would not return a banner; however, a high-interaction honeypot would not only show the port as open but could also return the proper banner:
HTTP/1.1 400 Bad Request
Server: Microsoft-IIS/5.0
Date: Wed, 18 Jul 2012 18:08:25 GMT
Content-Type: text/html
Content-Length: 87
Honeypots can be configured in such a way that administrators will be alerted to their use and will have time to plan a defense or guard of the real network. However, the downside of honeypots includes the fact that, just like any other security system on the network, they require time and configuration. And, in fact, they are attracting a malicious element into your domain. Administrators must spend a certain amount of time monitoring these systems. In addition, if an attacker can successfully compromise the honeypot, he now has a base of attack from which to launch further attacks.
Honeypots were originally designed to research attack styles and enable improved architectures and antimalware. More and more agencies are deploying honeypots as ways of acting as a decoy and diverting away from the real system attacks, and to act as early warning systems. It is considered legal to entice someone, but not to entrap. The fuzzy distinction can lead to interesting court cases. A good site to learn more about honeypots is www.honeynet.org.
Evidence Types
The gathering, control, storage, and preservation of evidence are extremely critical in any legal investigation. Evidence can be computer generated, oral, or written. Because computer evidence is easily altered, special care must be taken when handling it. Different types of evidence have different levels of validity in court. For evidence to be accepted in court, it must meet certain standards:
![]() Relevant
Relevant
![]() Legally obtained and legally permissible
Legally obtained and legally permissible
![]() Reliable
Reliable
![]() Identifiable
Identifiable
![]() Properly preserved and documented
Properly preserved and documented
There are also various types of evidence, different ways in which the evidence can be gathered, and legal and illegal ways in which those who break the law can be prosecuted:
![]() Best evidence—Best evidence is considered the most reliable form of evidence. Original documents are an example of best evidence.
Best evidence—Best evidence is considered the most reliable form of evidence. Original documents are an example of best evidence.
![]() Secondary evidence—Although not as reliable or as strong as best evidence, secondary evidence can still be used in court. A copy of evidence and an oral description of its contents are examples of secondary evidence.
Secondary evidence—Although not as reliable or as strong as best evidence, secondary evidence can still be used in court. A copy of evidence and an oral description of its contents are examples of secondary evidence.
![]() Hearsay evidence—Hearsay is generally not admissible in court because it is considered secondhand information. Some computer-generated records and other business records fall under this category.
Hearsay evidence—Hearsay is generally not admissible in court because it is considered secondhand information. Some computer-generated records and other business records fall under this category.
![]() Direct evidence—This form of evidence either proves or disproves a specific act through oral testimony. It is based on information gathered through the witness’s five senses.
Direct evidence—This form of evidence either proves or disproves a specific act through oral testimony. It is based on information gathered through the witness’s five senses.
![]() Enticement and entrapment—Enticement is the legal activity of luring an individual to perform a questionable activity. Using a honeypot to observe and monitor individuals attempting to attack your network could be seen as an act of enticement. Entrapment occurs when individuals illegally induce or trick a person into committing a crime that he had not previously considered.
Enticement and entrapment—Enticement is the legal activity of luring an individual to perform a questionable activity. Using a honeypot to observe and monitor individuals attempting to attack your network could be seen as an act of enticement. Entrapment occurs when individuals illegally induce or trick a person into committing a crime that he had not previously considered.
![]() Trace evidence—Whenever two objects come into contact, a transfer of material will occur. This is known as the Locard’s Exchange Principle and is almost universally accepted by all forensic analysts. No matter how hard someone tries, some evidence always remains. Although criminals can make recovery harder by deleting files and caches, some trace evidence always remains.
Trace evidence—Whenever two objects come into contact, a transfer of material will occur. This is known as the Locard’s Exchange Principle and is almost universally accepted by all forensic analysts. No matter how hard someone tries, some evidence always remains. Although criminals can make recovery harder by deleting files and caches, some trace evidence always remains.
Trial
Basically two types of trials occur: one heard by a judge and the other heard by a jury. Most jury panels are composed of ordinary citizens from the court’s surrounding geographical area, referred to in most jurisdiction as a jury of one’s peers. In many cases the jury might or might not be technically savvy. Computer crimes are difficult to prosecute in court because the advancement of technology is fast, whereas change in the legal system is slow. Trials also require a prosecutor with experience in computer crime. Even when cases are successful, computer criminals sometimes receive lighter sentences because this is considered a white-collar crime.
Tip
Negligence is the failure to meet the required standards in protecting information.
The Evidence Life-Cycle
Evidence follows a set life cycle-that begins when the evidence is seized and ends when it is destroyed or returned to the victim/suspect. The evidence lifecycle has the following five stages:
1. Identified and collected
2. Analyzed
3. Preserved, stored, and transported securely
4. Presented in court case or legal venue
5. Returned to suspect or victim
At the end of a trial or legal proceeding, whatever evidence the court is holding will typically be returned to the owner. Some items, such as drugs, counterfeit items, or illegal items, will not be returned. Also, some items might require that the owner to petition the court to fight for their return. As an example, if someone is arrested on drug charges and they possess a large amount of cash, it might be assumed the money is from proceeds of the drug trade and require the owner to prove otherwise to obtain the return of the funds. This may also be the case for information systems that were confiscated and child pornography was discovered on them. If a computer was used as a tool to commit a crime, there is no guarantee it will be return to the owner. Computer crime is increasing, and being seen through the same lens as traditional crimes. For example, in some states in America, if a motor vehicle is used in drug trafficking, that vehicle is often confiscated, never returned, and further used by the police departments for their patrol duties.
Exam Prep Questions
1. IP spoofing is commonly used for which of the following types of attacks?
![]() A. Salami
A. Salami
![]() B. Keystroke logging
B. Keystroke logging
![]() C. DoS
C. DoS
![]() D. Data diddling
D. Data diddling
2. Which of the following best describes session hijacking?
![]() A. Session hijacking works by first subverting the DNS process. If this is successful, an attacker can use an already established TCP connection.
A. Session hijacking works by first subverting the DNS process. If this is successful, an attacker can use an already established TCP connection.
![]() B. Session hijacking subverts the UDP protocol. It allows an attacker to use an already established connection.
B. Session hijacking subverts the UDP protocol. It allows an attacker to use an already established connection.
![]() C. Session hijacking targets the TCP connection between a client and a server. If the attacker learns the initial sequence, he might be able to hijack a connection.
C. Session hijacking targets the TCP connection between a client and a server. If the attacker learns the initial sequence, he might be able to hijack a connection.
![]() D. Session hijacking works by first subverting the DNS process. If this is successful, an attacker can use an already established UDP connection.
D. Session hijacking works by first subverting the DNS process. If this is successful, an attacker can use an already established UDP connection.
3. Several of your company’s employees have been hit with email scams over the last several weeks. One of these attacks successfully tricked an employee into revealing his username and password. Management has asked you to look for possible solutions to these attacks. Which of the following represents the best answer?
![]() A. Implement a new, more robust password policy that requires complex passwords.
A. Implement a new, more robust password policy that requires complex passwords.
![]() B. Start a training and awareness program.
B. Start a training and awareness program.
![]() C. Increase the organization’s email-filtering ability.
C. Increase the organization’s email-filtering ability.
![]() D. Develop a policy that restricts email to official use only.
D. Develop a policy that restricts email to official use only.
4. In part, the ISC2 Code of Ethics states which of the following?
![]() A. Thou shalt not use a computer to harm other people.
A. Thou shalt not use a computer to harm other people.
![]() B. Compromising the privacy of users is unethical.
B. Compromising the privacy of users is unethical.
![]() C. All information should be free.
C. All information should be free.
![]() D. Act honorably, honestly, justly, responsibly, and legally.
D. Act honorably, honestly, justly, responsibly, and legally.
5. Which of the following groups presents the largest threat to your organization?
![]() A. Insiders
A. Insiders
![]() B. Corporate spies
B. Corporate spies
![]() C. Government spies
C. Government spies
![]() D. Script kiddies
D. Script kiddies
6. Locard’s Exchange Principle states which of the following?
![]() A. The chain of custody should never be broken.
A. The chain of custody should never be broken.
![]() B. There is always some trace evidence.
B. There is always some trace evidence.
![]() C. Three things are required for a crime: means, motive, and opportunity.
C. Three things are required for a crime: means, motive, and opportunity.
![]() D. Checksums should be used to authenticate evidence.
D. Checksums should be used to authenticate evidence.
7. Which of the following international organizations was established to standardize the handling of forensic evidence?
![]() A. The International Organization on Forensic Analysis
A. The International Organization on Forensic Analysis
![]() B. The EU Policy Council of Criminal Evidence
B. The EU Policy Council of Criminal Evidence
![]() C. The United Nations Organization on Computer Evidence
C. The United Nations Organization on Computer Evidence
![]() D. The International Organization on Computer Evidence
D. The International Organization on Computer Evidence
8. For evidence to be used in court, it must not be which of the following?
![]() A. Relevant
A. Relevant
![]() B. Properly preserved
B. Properly preserved
![]() C. Identifiable
C. Identifiable
![]() D. Justifiable
D. Justifiable
9. Which of the following best defines hearsay evidence?
![]() A. Can be used in civil cases
A. Can be used in civil cases
![]() B. Is not admissible in court
B. Is not admissible in court
![]() C. Is considered third-hand information
C. Is considered third-hand information
![]() D. Can be used to verify what has been presented through best evidence
D. Can be used to verify what has been presented through best evidence
10. Ethical hackers are different from hackers in which of the following ways?
![]() A. They have permission to destroy a network.
A. They have permission to destroy a network.
![]() B. Their goal is to do no harm.
B. Their goal is to do no harm.
![]() C. They cannot be held liable for any damage.
C. They cannot be held liable for any damage.
![]() D. They cannot be prosecuted or jailed.
D. They cannot be prosecuted or jailed.
11. When dealing with computer forensics, which item should be addressed first?
![]() A. Hard drive(s)
A. Hard drive(s)
![]() B. DVDs
B. DVDs
![]() C. Contents of RAM
C. Contents of RAM
![]() D. Computer printouts
D. Computer printouts
12. Which of the following best describes SATAN?
![]() A. It is used for password cracking.
A. It is used for password cracking.
![]() B. It is used for reviewing audit logs.
B. It is used for reviewing audit logs.
![]() C. It is used to exploit systems.
C. It is used to exploit systems.
![]() D. It is used to find vulnerabilities.
D. It is used to find vulnerabilities.
13. The computer forensic investigator should do what during duplication?
![]() A. Make a direct copy
A. Make a direct copy
![]() B. Make a bit level copy
B. Make a bit level copy
![]() C. Make a logical copy
C. Make a logical copy
![]() D. Format the target drive to clear any contents before copying
D. Format the target drive to clear any contents before copying
14. What type of penetration test examines what insiders can access?
![]() A. Whitebox
A. Whitebox
![]() B. Graybox
B. Graybox
![]() C. Blackbox
C. Blackbox
![]() D. Bluebox
D. Bluebox
15. These individuals are known for their attacks on PBX and telecommunication systems.
![]() A. Script kiddies
A. Script kiddies
![]() B. Phreakers
B. Phreakers
![]() C. Crackers
C. Crackers
![]() D. Hackers
D. Hackers
Answers to Exam Prep Questions
1. C. IP spoofing is a common practice when DoS tools are used to help the attacker mask his identity. Salami attacks, data diddling, and keystroke logging do not typically spoof IP addresses, so answers A, B, and D are incorrect.
2. C. This more advanced spoof attack works by subverting the TCP connection between a client and a server. If successful, the attacker has a valid connection to the victim’s network and is authenticated with his credentials. This attack is very hard to do with modern operating systems but is trivial with older operating systems. Answer A is incorrect because session hijacking does not involve DNS; it functions by manipulating the TCP sequence number. Answer B is incorrect because session hijacking does not use the UDP protocol. UDP is used for stateless connections. Answer D is incorrect because, again, session hijacking is not based on DNS and UDP. These two technologies are unrelated to TCP sequence numbers.
3. B. The best defense against social engineering is to educate your users and staff. Training can go a long way toward teaching employees how to spot these scams. Although the other answers are not bad ideas, they will not prevent social engineering, so answers A, C, and D are incorrect.
4. D. It’s a requirement for CISSP candidates to subscribe to the ISC2 Code of Ethics, which, in part, states, “Act honorably, honestly, justly, responsibly, and legally.” All other answers are incorrect.
5. A. Insiders represent the biggest threat to the organization because they possess two of the three things needed to attempt malicious activity: means and opportunity. Answers B, C, and D are incorrect because although outsiders might have a motive, they typically lack the means or opportunity to attack your organization.
6. B. There is always some trace evidence. Locard’s Exchange Principle states that whenever two objects come into contact, a transfer of material will occur. Answers A, C, and D are incorrect because they do not describe Locard’s Exchange Principle.5
7. D. The International Organization on Computer Evidence (IOCE) was appointed to draw up international principles for the procedures relating to digital evidence. The goal was to harmonize methods and practices among nations and guarantee the capability to use digital evidence collected by one state in the courts of another state. Answer A, B, and C are incorrect because the these are not the correct name of the forensic that was established to standardize the handling of forensic evidence.
8. D. For evidence to be accepted in court, it must meet certain standards: It must be relevant (answer A), legally permissible, reliable, identifiable (answer C), and properly preserved (answer B) and documented. Because the question asked which is not applicable, the only possible answer is D, justifiable.
9. B. Hearsay is generally not admissible in court because it is considered secondhand information. Answer A is incorrect because hearsay evidence cannot be used in civil cases. Answer C is incorrect because hearsay evidence is considered secondhand information. Answer D is incorrect because hearsay evidence cannot be used to verify what has been presented through best evidence.
10. B. Ethical hackers use the same methods as crackers and black-hat hackers, but they report the problems they find instead of taking advantage of them. Ethical hacking has other names, such as penetration testing, intrusion testing, and red-teaming. Answer A is incorrect because ethical hackers do not have permission to destroy networks. Answer C is incorrect because ethical hackers can be held liable. Answer D is incorrect because ethical hackers can be jailed if they break the law or exceed the terms of their contract.
11. C. Contents of RAM should be examined first because the process should always move from most volatile to least volatile. The contents of RAM will be lost when the system is powered down. Hard drives, DVDs, printouts, and other such items can be examined later, so answers A, B, and D are incorrect.
12. D. SATAN was the first vulnerability assessment program and was designed to find vulnerabilities in a network. Programs like Retina and Nessus are also used for vulnerability assessments. SATAN is not used for password cracking (answer A), auditing logs (answer B), and is not used to exploit systems (answer C).
13. B. Make a bit-level copy. Bit-level copies are exact copies and include file slack, drive slack, and all contents of the drive being duplicated. Making a direct copy (answer A) would not be performed because the drive must be protected with a write blocker to prevent changes to the suspect’s drive. Logical copies (answer C) copy only files, not slack. Formatting the drive (answer D) would not effectively clean the disk—a drive wipe would be the approved method of preparation.
14. B. Graybox testing looks to determine what type of activities can be performed. Answer A is incorrect because whitebox testing is where everything is known about the network, answer C is incorrect because blackbox testing is where nothing is known about the network, and answer D is incorrect because blueboxing is a term used by phreakers to make free phone calls via a mechanical device.
15. B. Phreakers are individuals that are known for their attacks on PBX and telecommunications equipment. Answers C and D are incorrect because hackers and crackers both identify computer criminals. Answer A is incorrect because script kiddies are defined as junior hackers that rely on the work of others through predefined processes and programs to attack computers.
Need to Know More?
RFC 1087: www.faqs.org/rfcs/rfc1087.html
Computer Emergency Response Team: www.cert.org/
DOJ site on cybercrime: www.cybercrime.gov/
2600: The Hacker Quarterly: www.2600.com/
Underground Hacking Event: www.defcon.org/
40 years of hacking: https://trinity-hackers.wikispaces.com/CNN+40+Years+of+Hacking
ISC2 Code of Ethics: https://www.isc2.org/ethics/default.aspx
Forensic procedure information: www.forensicmag.com/articles/2007/10/documenting-computer-forensic-procedures
EU privacy laws: en.wikipedia.org/wiki/Data_Protection_Directive
Rules of evidence: www.law.cornell.edu/rules/fre/
Identity theft information: www.idtheftcenter.org/index
Honeypots and honeynet white papers: www.honeynet.org
Forensic Best practices: www.us-cert.gov/reading_room/forensics.pdf