Chapter 3. Physical Asset Security
Terms you’ll need to understand:
![]() CPTED
CPTED
![]() Perimeter intrusion and detection assessment system
Perimeter intrusion and detection assessment system
![]() Bollards
Bollards
![]() CCTV
CCTV
![]() Annunciator
Annunciator
![]() Piggyback
Piggyback
![]() Intrusion detection
Intrusion detection
![]() Tamper protection
Tamper protection
![]() Halon
Halon
Topics you’ll need to master:
![]() Physical barrier design
Physical barrier design
![]() Fence height and grade specification
Fence height and grade specification
![]() Lock mechanisms and strengths identification
Lock mechanisms and strengths identification
![]() Fire safety design
Fire safety design
![]() Fire suppression methods
Fire suppression methods
![]() Fire detection systems identification
Fire detection systems identification
![]() Light placement and design
Light placement and design
![]() Specifying requirements for new facilities
Specifying requirements for new facilities
Introduction
Physical security is a key element of asset security. Many of us might underestimate the importance of physical controls. Yet these controls represent one of the three key areas (along with administrative and logical controls) into which all controls are categorized. Each control can be measured against the basic requirements of availability, confidentiality, and integrity. After all, if attackers can walk off with a portable hard drive, tablet, or smartphone, they have (at the least) denied you availability. If a co-worker throws away a DVD containing proprietary information that a criminal could recover, confidential information can be disclosed to unauthorized persons. If a disgruntled employee can physically access a server on which a key database resides as opposed to remotely accessing the database and change amounts, values, or data integrity can be compromised.
Implementations of physical security surround us. For example, you might have a sticker on your car that permits you to park in the company parking garage. Perhaps company policy requires you to get a new photo taken each year for your company ID badge. Access to the equipment room might be limited to those employees that have been assigned keys. You deal with physical security every day.
CISSP candidates must also have a good understanding of what is involved in securing a site. The goals of overall physical security are to deter, delay, detect, assess, and respond. Physical security controls are like all other controls, and must be designed in layers. Candidates must understand the benefits of layered protections, also referred to as defense in breadth, such as fences, locks, physical access control, and closed-circuit television (CCTV) to protect employees and critical infrastructures. Defense in breadth is achieved when several layers of security within one control are applied. Defense in depth, by contrast, is achieved by applying several security layers using more than one control; that is, technical, administrative, and physical.
Physical Security Risks
Threats to physical security have existed for as long as humans have inhabited Earth. Consider the Incan city, Machu Picchu, built high on a mountain more than 7,000 feet above sea level. This ancient city was surrounded by thick stone walls and many natural exterior defenses that made it difficult to attack. Careful and even ingenious planning is still evident in the design of this city’s defense.
In the modern world, our multinational organizations might not be headquartered on remote mountain peaks, but security is still evident, because a variety of threats to physical security still exist. These threats can be divided into broad categories, such as natural disasters, man-made threats, and technical problems. The sections that follow delve into these threats in greater detail.
Natural Disasters
Natural disasters come in many forms. Although natural disasters are not something that you can prevent, you can have a disaster recovery plan to mitigate the impact. A recovery and corrective plan can be implemented for facilities, information, and information systems that could be affected that will detail how you will respond when confronted with disasters. As an example, organizations planning to establish a facility in New Orleans, Louisiana, might have minimal earthquake concerns; however, hurricanes would be considered an imminent threat. Understanding a region and its associated weather-related issues are important in planning physical security. Natural disasters that organizations should consider include:
![]() Hurricanes, typhoons, and tropical cyclones—These natural products of the tropical ocean and atmosphere are powered by heat from the sea. They grow in strength and velocity as they progress across the ocean and spawn tornadoes and cause high winds and floods when they come ashore.
Hurricanes, typhoons, and tropical cyclones—These natural products of the tropical ocean and atmosphere are powered by heat from the sea. They grow in strength and velocity as they progress across the ocean and spawn tornadoes and cause high winds and floods when they come ashore.
![]() Tidal waves/tsunamis—The word tsunami is based on a Japanese word meaning “harbor wave.” This natural phenomenon consists of a series of huge and widely dispersed waves that cause massive damage when they crash on shore.
Tidal waves/tsunamis—The word tsunami is based on a Japanese word meaning “harbor wave.” This natural phenomenon consists of a series of huge and widely dispersed waves that cause massive damage when they crash on shore.
![]() Floods—Floods can result when the soil has poor retention properties or when the amount of rainfall exceeds the ground’s capability to absorb water. Floods are also caused when creeks and rivers overflow their banks.
Floods—Floods can result when the soil has poor retention properties or when the amount of rainfall exceeds the ground’s capability to absorb water. Floods are also caused when creeks and rivers overflow their banks.
![]() Earthquakes—These are caused from movement of the earth along fault lines. One example is the Nepal earthquake of 2015 that killed over 8,000 people and injured more than 21,000. Areas in the United States, such as California and Alaska, are especially vulnerable because they are on top of major active fault lines.
Earthquakes—These are caused from movement of the earth along fault lines. One example is the Nepal earthquake of 2015 that killed over 8,000 people and injured more than 21,000. Areas in the United States, such as California and Alaska, are especially vulnerable because they are on top of major active fault lines.
![]() Tornadoes—Tornadoes are violent storms that descend to the ground as violent rotating columns of air. Tornadoes leave a path of destruction that may be quite narrow or extremely broad—up to about a mile wide.
Tornadoes—Tornadoes are violent storms that descend to the ground as violent rotating columns of air. Tornadoes leave a path of destruction that may be quite narrow or extremely broad—up to about a mile wide.
![]() Fire—This disaster can be man-made (intentional or accidental) or natural, and is the most common cause of damage to property and loss of life. According to statistics at fema.gov, there were some 3,005 deaths due to fire in the United States in 2011. That’s a great loss of life. Wildfires can also cause massive damage.
Fire—This disaster can be man-made (intentional or accidental) or natural, and is the most common cause of damage to property and loss of life. According to statistics at fema.gov, there were some 3,005 deaths due to fire in the United States in 2011. That’s a great loss of life. Wildfires can also cause massive damage.
Man-Made Threats
Man-made threats are another major concern when planning your organization’s physical security. Natural threats such as floods, hurricanes, or tornadoes must be planned for, knowing that they cannot be prevented. However, man-made threats require controls that minimize (or eliminate) opportunity of occurrence, and provide for quick response in the event of any occurrence. Consider the man-made threats in the list that follows:
![]() Terrorism—As demonstrated in events such as the Paris attacks in November 2015 and the San Bernardino, California, attack in December 2015, and as painfully understood by victims worldwide, terrorists act with calculated inhumane tactics to force their goals on society. Terrorists often claim vindication in religious or political extremism. By doing a risk analysis and threat modeling, organizations can determine what aspects of their business make them a possible target for terrorism—that is, a “soft” target. This could drive the need for physical security controls. Organizations that have a higher volume of human traffic along with sensitive information to protect are increasingly becoming targets for acts of traditional terrorism and cyber-terrorism.
Terrorism—As demonstrated in events such as the Paris attacks in November 2015 and the San Bernardino, California, attack in December 2015, and as painfully understood by victims worldwide, terrorists act with calculated inhumane tactics to force their goals on society. Terrorists often claim vindication in religious or political extremism. By doing a risk analysis and threat modeling, organizations can determine what aspects of their business make them a possible target for terrorism—that is, a “soft” target. This could drive the need for physical security controls. Organizations that have a higher volume of human traffic along with sensitive information to protect are increasingly becoming targets for acts of traditional terrorism and cyber-terrorism.
![]() Vandalism—Since the Vandals sacked Rome in 455 A.D., the term vandalism has been synonymous with the willful destruction of another’s property.
Vandalism—Since the Vandals sacked Rome in 455 A.D., the term vandalism has been synonymous with the willful destruction of another’s property.
![]() Theft—Theft of company assets can range from an annoyance to legal liability. Sure, the company laptop, tablet, or smartphone can be replaced, but what about the data on the device? For example, Sophos.com reported that the average cost of a stolen laptop is upwards of $49,000. If you are curious to know how much of a problem this is, take a moment to review blogs.sophos.com/2013/09/12/how-much-does-a-lost-laptop-cost-your-business/.
Theft—Theft of company assets can range from an annoyance to legal liability. Sure, the company laptop, tablet, or smartphone can be replaced, but what about the data on the device? For example, Sophos.com reported that the average cost of a stolen laptop is upwards of $49,000. If you are curious to know how much of a problem this is, take a moment to review blogs.sophos.com/2013/09/12/how-much-does-a-lost-laptop-cost-your-business/.
![]() Destruction—Physical and logical assets are vulnerable to destruction by current employees, former employees, and/or outsiders. Consider that in 2012, the Shamoon malware is believed to have destroyed 30,000 Saudi Aramco workstations.
Destruction—Physical and logical assets are vulnerable to destruction by current employees, former employees, and/or outsiders. Consider that in 2012, the Shamoon malware is believed to have destroyed 30,000 Saudi Aramco workstations.
![]() Criminal activities—This category is a catch-all for other malicious behaviors that threaten your employees or your infrastructure. Maybe your company thought it was getting a real tax break by moving into a lower-income area. Now, employees don’t feel safe walking to their cars at night. Or, maybe the company’s web administrator is running his own music and movie download site on the company network. After all, it’s just for fun and a little added pocket money.
Criminal activities—This category is a catch-all for other malicious behaviors that threaten your employees or your infrastructure. Maybe your company thought it was getting a real tax break by moving into a lower-income area. Now, employees don’t feel safe walking to their cars at night. Or, maybe the company’s web administrator is running his own music and movie download site on the company network. After all, it’s just for fun and a little added pocket money.
Technical Problems
Unlike natural disasters or man-made threats, technical problems are the events that just seem to happen, often at highly inopportune times. These events can range from inconvenient glitches to potential large-scale disasters. Emergency situations can include the following:
![]() Communication loss—Voice and data communication systems play a critical role in today’s organizations. Communication loss can be the outage of voice communication systems or data networks. As more organizations use convergence technologies such as network-controlled door locks, Internet Protocol (IP) video cameras, and VoIP (Voice over IP), a network failure means that not only the data connection fails, but also the voice communication.
Communication loss—Voice and data communication systems play a critical role in today’s organizations. Communication loss can be the outage of voice communication systems or data networks. As more organizations use convergence technologies such as network-controlled door locks, Internet Protocol (IP) video cameras, and VoIP (Voice over IP), a network failure means that not only the data connection fails, but also the voice communication.
![]() Utility loss—Utilities include water, gas, communication systems, and electrical power. The loss of utilities can bring business to a standstill. Generators and backups can prevent these problems if they are used.
Utility loss—Utilities include water, gas, communication systems, and electrical power. The loss of utilities can bring business to a standstill. Generators and backups can prevent these problems if they are used.
![]() Equipment failure—Equipment will fail over time. This is why maintenance is so important. With insufficient planning, you might experience a business outage. A Fortune 1,000 study found that 65% of all businesses that fail to resume operations within one week never recover at all and permanently cease operation.
Equipment failure—Equipment will fail over time. This is why maintenance is so important. With insufficient planning, you might experience a business outage. A Fortune 1,000 study found that 65% of all businesses that fail to resume operations within one week never recover at all and permanently cease operation.
Caution
Service-level agreements (SLAs) are one good way to plan for equipment failure. With an SLA in place, the vendor agrees to repair or replace the covered equipment within a given time. Just keep in mind that while an SLA covers replacement of materials or repair time, it still doesn’t cover the cost incurred by the downtime or loss of credibility.
Facility Concerns and Requirements
Whether you are charged with assessing an existing facility, moving into a new facility, or planning to construct a new facility, physical security must be a high priority. It’s important to consider all the threats that have been discussed, as well as additional threats that might be unique to your operations. The last thing you want is to build a facility in an area where your employees fear for their personal safety. At the same time, you don’t want the facility to feel like a bank vault or be designed like a prison. You need a facility in which employees can be comfortable, productive, and feel safe.
CPTED
A key component of achieving this balance is Crime Prevention Through Environmental Design (CPTED). The benefits of CPTED include the following:
![]() Natural access control
Natural access control
![]() Natural surveillance
Natural surveillance
![]() Territorial reinforcement
Territorial reinforcement
CPTED is unique in that it considers the factors that facilitate crime and seeks to use the proper design of a facility to reduce the fear and incidence of crime. At the core of CPTED is the belief that physical environments can be structured to reduce crime. Let’s look at a few examples. Maybe you have noticed limited entrance and exit points into and out of mall parking lots. This is an example of natural access control. Another example is the organization that decides to place the employee parking lot in an area visible from the employee’s workspace. This enables employees to look out their windows in the office and see their parked cars. Even if this company employs a single guard, the facility’s design allows increased surveillance by all the employees.
The effect of CPTED is that it causes the criminal to feel an increase in the threat of being discovered and provides natural surveillance that can serve as a physical deterrent control. The concept of CPTED can also be applied to CCTV. CCTV should be mounted so that potential criminals can easily see the cameras and know there is a much higher risk of getting caught. A CCTV can serve as a physical deterrent control and a detective control as well. Criminals may be deterred from entering property by the presence of a warning sign that alerts intruders that the property is under surveillance. Police can refer back to video, along with log books and other technical logs, to make a human judgment of who, how, when, and where a crime was committed; therefore, a CCTV is a great physical detective control. CCTV is also a great tool for detecting and deterring the insider threat.
Every facet of facility design should be reviewed with a focus on CPTED. Even items such as hedges are important, as an aid in natural surveillance; they should not be higher than 2.5 feet. Overgrown hedges obstruct visibility.
The third benefit of CPTED is territorial reinforcement. Strategic use of walls, windows, fences, barriers, landscaping, and so on define areas and create a sense of ownership with employees. Use fences, lighting, sidewalks, and designated parking areas on the outside of the facility and move critical assets toward the center of the facility.
Area Concerns
Finding the right location is your first concern when planning a new facility. Key points to consider include:
![]() Accessibility—An organization’s facility needs to be in a location that people can access. Depending on your business and individual needs, requirements will vary, but aspects such as roads, freeways, local traffic patterns, public transportation, and convenience to regional airports need to be considered.
Accessibility—An organization’s facility needs to be in a location that people can access. Depending on your business and individual needs, requirements will vary, but aspects such as roads, freeways, local traffic patterns, public transportation, and convenience to regional airports need to be considered.
![]() Climatology and natural disasters—Mother Nature affects all of us. If you’re building in Phoenix, Arizona, you will not have the same weather concerns as someone building a facility in Anchorage, Alaska. Events such as hurricanes, earthquakes, floods, snowstorms, dust storms, and tornadoes should be discussed and planned before starting construction.
Climatology and natural disasters—Mother Nature affects all of us. If you’re building in Phoenix, Arizona, you will not have the same weather concerns as someone building a facility in Anchorage, Alaska. Events such as hurricanes, earthquakes, floods, snowstorms, dust storms, and tornadoes should be discussed and planned before starting construction.
![]() Local considerations—Issues such as freight lines, flight paths of airlines, toxic waste dumps, and insurance costs all play into the picture of where you should build a facility. Although cheap land for a new facility might seem like a bargain, the discovery that it is next to a railway used to haul toxic chemicals could change your opinion.
Local considerations—Issues such as freight lines, flight paths of airlines, toxic waste dumps, and insurance costs all play into the picture of where you should build a facility. Although cheap land for a new facility might seem like a bargain, the discovery that it is next to a railway used to haul toxic chemicals could change your opinion.
![]() Utilities—You should check that water, gas, and electric lines are adequate for the organization’s needs. This might seem like a nonissue, but California found out otherwise in the California energy crisis of 2000 and 2001, which left many without power and caused periods of rolling blackouts.
Utilities—You should check that water, gas, and electric lines are adequate for the organization’s needs. This might seem like a nonissue, but California found out otherwise in the California energy crisis of 2000 and 2001, which left many without power and caused periods of rolling blackouts.
![]() Visibility—Area population, terrain, and types of neighbors are also concerns. Depending on the type of business, you might want a facility that blends into the neighborhood. You might design individual buildings that cloak activities taking place there. Some organizations might even place an earthen dike or barrier around the facility grounds to obstruct the view of those that pass by. A good example of obscuring the location of a facility can be seen in the design of Skype’s London office (see tinyurl.com/5lzbcx).
Visibility—Area population, terrain, and types of neighbors are also concerns. Depending on the type of business, you might want a facility that blends into the neighborhood. You might design individual buildings that cloak activities taking place there. Some organizations might even place an earthen dike or barrier around the facility grounds to obstruct the view of those that pass by. A good example of obscuring the location of a facility can be seen in the design of Skype’s London office (see tinyurl.com/5lzbcx).
Location
The location of the facility is an important issue. Before construction begins, an organization should consider how the location fits with the organization’s overall tasks and goals. A good example is the NSA museum outside Baltimore. It’s the kind of place every cryptographic geek dreams of going. It’s actually behind the main NSA facility in what used to be a hotel. (Rumor has it that this was a favorite hangout of the KGB before the NSA bought the hotel.) Although having facilities nearby for visitors and guests is seen as a good idea, the placement of the hotel so close to a critical agency might be a problem as it allows for spying.
Keep in mind that the acquisition of a new corporate site involves more than just the cost of the property. Cheap property doesn’t necessarily mean a good deal. If your company manufactures rockets for satellites, you might want to be near fire stations and hospitals in case there’s an accident.
Construction
After you have chosen a location, your next big task is to determine how the facility will be constructed. In many ways, this is driven by what the facility will be used for and by federal, state, and local laws. Buildings used to store the groundskeeper’s equipment have different requirements than those used as a clean room for the manufacturer of microchips. In other words, you’ll need to know how various parts of the facility will be used. I once saw a facilities crew trying to install an electromagnetic interference (EMI) chamber on the third floor of a building. EMI chambers require the placement of many heavy tiles and copper shielding used to block radio signals. This would have placed a huge load on the floor of this building, but no one had checked to verify the load-bearing limit of the floor. Remember to make sure that the facility is built to support whatever equipment you plan to put in it.
Tip
The load is how much weight the walls, floor, and ceiling is being asked to support.
Doors, Walls, Windows, and Ceilings
Have you ever wondered why most doors on homes open inward, whereas almost all doors on businesses open outward? This design is rooted in security. The door on your home is hinged to the inside. This makes it harder for thieves to remove your door to break in, but it also gives you an easy way to remove the door to bring in that big new leather couch. Years ago, the individuals who designed business facilities had the same thought. The problem is that open-in designs don’t work well when people panic. It’s a sad fact that the United States has a long and tragic history of workplace fires. In 1911, nearly 150 women and young girls died when they couldn’t exit the Triangle Shirtwaist factory they were working in when it caught fire. The emergency exit doors were locked! Because of this and other tragic losses of life, modern businesses are required to maintain exits that are accessible, unlocked, and open out. These doors are more expensive because they are harder to install and remove. Special care must be taken to protect the hinges so that they cannot be easily removed. Many doors include a panic bar that permit quick exit: just push and you’re out. In emergencies or situations in which a crowd is exiting the building quickly, panic bars help keep people moving away from danger.
Maybe you have heard the phrase “security starts at the front door.” It is of the utmost importance to keep unauthorized individuals out of the facility or areas where they do not belong. Doors must be as secure as the surrounding walls, floor, and ceiling. If the door is protecting a critical area such as a data center or an onsite server room, the door needs to have the hinges on the inside of the door so that hinge pins cannot be removed. The structural components around the door must also be strengthened. The lock, hinges, strike plate, and the doorframe must all have enough strength to prevent someone from attempting to kick, pry, pick, or knock it down.
The construction of a door can vary. Critical infrastructure should be protected with solid core doors. The core material is the material within the door used to fill space, provide rigidity, and increase security. Hollow core doors simply have a lattice or honeycomb made of corrugated cardboard or thin wooden slats. Unlike a hollow core door, a solid core door is hard to penetrate. Solid core doors consist of low-density particle board, ridged foam, solid hardwood, or even steel that completely fills the space within the door. Solid core flush doors have much greater strength. The outer portion of the door is the skin, which can be wood, steel, or other materials such as polymers. Commercial steel doors are classified by ANSI/SDI A250.8-2014 into various categories that include standard duty, heavy duty, extra-heavy duty, and maximum duty. Selection of a steel door should be based on usage, degree of abuse, and required protection factor.
Many companies use electrically powered doors to control access. As an example, an employee might have to insert an ID card to gain access to the facility. The card reader then actuates an electric relay that allows the door to open. A CISSP should know the state of these door relays in the event of a power loss. An unlocked (or disengaged) state allows employees to ingress or egress and without being locked in. If a door lock defaults to open during a power disruption, this is referred to as fail-safe. If the lock defaults to locked during a power disruption this is referred to as fail-secure. In this situation, a panic bar or release must be provided so employees are not trapped inside the facility. For high-security doors, it is also important to consider delay alarms. A delay alarm is used to alert security that a security door has been open for a long time. A fail-safe option may be the best option and/or may be a regulatory requirement (fire code) when there are people employed within the facility verses an unmanned data warehouse.
Caution
Fail-safe locks protect employees in case of power loss because they allow employees to exit the facility.
ExamAlert
The terms fail-safe and fail-secure have very different meanings when discussed in physical security versus logical security. During the exam, read the questions carefully to determine the context in which the terms are being used.
Doors aren’t the only factor you need to consider. Data centers typically should have raised floors. These need to be constructed in such a way that they are grounded against static electricity. Cables and wiring should be in conduit, not loose nor above the raised floor such that a trip hazard exists. Walls must be designed to slow the spread of fires, and emergency lighting should be in place to light the way for anyone trying to escape in case of emergency. Other considerations include the following:
![]() Walls—These need to be floor-to-ceiling for critical areas and where they separate key departments. Walls should have an adequate fire rating, and have reinforcement to keep unauthorized personnel from accessing secure areas, such as data centers or server rooms. Anyone who works in a cubicle environment understands the deficiency of short walls. A loud noise of excitement leads other employees to “prairie dog” and look over the wall of the cube to see what is happening.
Walls—These need to be floor-to-ceiling for critical areas and where they separate key departments. Walls should have an adequate fire rating, and have reinforcement to keep unauthorized personnel from accessing secure areas, such as data centers or server rooms. Anyone who works in a cubicle environment understands the deficiency of short walls. A loud noise of excitement leads other employees to “prairie dog” and look over the wall of the cube to see what is happening.
![]() Ceilings—These need to be waterproof above the plenum space, have an adequate fire rating, and be reinforced to keep unauthorized personnel from accessing secure areas, such as server rooms.
Ceilings—These need to be waterproof above the plenum space, have an adequate fire rating, and be reinforced to keep unauthorized personnel from accessing secure areas, such as server rooms.
![]() Electrical and HVAC—Plan for adequate power. Rooms that have servers or other heat-producing equipment need additional cooling to protect contained equipment. Heating, ventilating, and air conditioning (HVAC) systems should be controllable by fire-suppression equipment; otherwise, HVAC systems can inadvertently provide oxygen and help feed a fire.
Electrical and HVAC—Plan for adequate power. Rooms that have servers or other heat-producing equipment need additional cooling to protect contained equipment. Heating, ventilating, and air conditioning (HVAC) systems should be controllable by fire-suppression equipment; otherwise, HVAC systems can inadvertently provide oxygen and help feed a fire.
Caution
Air intakes should be properly designed to protect people from breathing toxins that might be introduced into an environment. The anthrax threat of 2001 drove home this critical concern. (see www.cdc.gov/anthrax/bioterrorism/threat.html)
![]() Windows—Windows are a common point of entry for thieves, burglars, and others seeking access. Windows are usually designed with aesthetics in mind, not security. Interior or exterior windows need to be fixed in place and should at a minimum be shatterproof on the first and second floors. Depending on placement, the windows might need to be either opaque or translucent. Windows can be standard glass, tempered, laminated, acrylic, or be embedded with wire mesh that can help prevent the glass from shattering. Alarms or sensors might also be needed.
Windows—Windows are a common point of entry for thieves, burglars, and others seeking access. Windows are usually designed with aesthetics in mind, not security. Interior or exterior windows need to be fixed in place and should at a minimum be shatterproof on the first and second floors. Depending on placement, the windows might need to be either opaque or translucent. Windows can be standard glass, tempered, laminated, acrylic, or be embedded with wire mesh that can help prevent the glass from shattering. Alarms or sensors might also be needed.
![]() Fire escapes—These are critical because they provide a point of egress and allow personnel to exit in case of a fire. It is critical that fire drills be performed to practice evacuation plans and determine real exit times. After the first attack on the World Trade Center towers in 1993, it was discovered that it took people two to three times longer to exit the facility than had been planned. Increased drills would have reduced evacuation time.
Fire escapes—These are critical because they provide a point of egress and allow personnel to exit in case of a fire. It is critical that fire drills be performed to practice evacuation plans and determine real exit times. After the first attack on the World Trade Center towers in 1993, it was discovered that it took people two to three times longer to exit the facility than had been planned. Increased drills would have reduced evacuation time.
![]() Fire detectors—Smoke detectors should be installed to warn employees of danger. Sprinklers and detectors should be used to reduce the spread of fire. Placement of smoke detectors can include under raised floors, above suspended ceilings, in the plenum space, and within air ducts.
Fire detectors—Smoke detectors should be installed to warn employees of danger. Sprinklers and detectors should be used to reduce the spread of fire. Placement of smoke detectors can include under raised floors, above suspended ceilings, in the plenum space, and within air ducts.
Tip
Human safety should always be your first concern.
Asset Placement
Security management includes the appropriate placement of high-value assets, such as servers and data centers. Well-placed data centers should not be above the second floor of a facility because a fire might make them inaccessible. Likewise, you wouldn’t want the data center located in the basement because it could be subjected to flooding. I once saw a data center that was located outside the company break room. You had to literally walk through the server room to get to the break room. Another unfortunate placement I witnessed was underneath restrooms. Plumbing issues led to a flood in the server room. Although the situation was anything but humorous, I did ask the CTO if this meant the organization was “all washed up.” Unsurprisingly, she was not amused.
It’s not a good idea to have a data center with uncontrolled access or in an area where people will congregate or mill around. Even placing the data center off a main hallway is not a good idea. I often tell students that the location of the server room should be like Talkeetna, Alaska. If you are going there, you cannot be going anywhere else because that is where the road ends.
A well-placed data center should have limited accessibility and typically no more than two doors. A first-floor interior room is a good location for a data center. The ceilings should extend all the way up past the drop ceiling, access to the room should be controlled, and doors should be solid-core with hinges to the inside. The goal in your design should be to make it as hard as possible for unauthorized personnel to gain access to the data center. Server rooms should not have exterior windows or walls. Placing them inside of the facility protects against potential destruction from storms, and makes it more difficult for thieves or vandals to target them. If individuals can gain physical access to your servers, you have no security.
Physical Port Controls
After an attacker gains physical access to a system, there is no limit to the damage that can occur. One common means of accessing a system is via the ports. A computer system can have many different types of ports, such as FireWire, Thunderbolt, and USB. USB is a common form factor. USB ports can be physically blocked, unplugged or blocked via software. Microsoft Windows also allow for ports to be locked by means of an Active Directory Group Policy, which is an example of an OS being able to restrict usage of items that may not be needed.
Perimeter Controls
Many types of perimeter control mechanisms can be deployed. The overall concept is to provide defense in depth. With this approach, layers of defensive mechanisms, using different types of controls, are created. Physical security controls are your first line of defense and should be designed so that the breach of any one will not compromise the physical security of the organization. CCTV cameras, gates, lighting, guards, dogs, and locks are but a few of the layers of physical security that can be added to build a defense-in-depth strategy. Let’s work from the outside in.
Fences
Consider the Berlin Wall. This monument to the Cold War was quite effective at preventing East Germans from escaping to the West. Before its fall in 1989, most people that escaped to the west did so by hiding in trunks of cars or by bribing guards. The wall worked as both a strong physical and psychological barrier. The amount of control provided by a fence depends on the type you build. A 3-to-4-foot fence will deter only a casual trespasser, but an 8-foot fence will keep out a determined intruder. Adding three strands of razor wire topping is an additional effective security measure. If you are trying to keep individuals inside an area, you should point the razor wire in, and if you are trying to keep individuals out, you should point the razor wire out. Table 3.1 provides more details. If you are really concerned about who’s hanging around the perimeter of your facility, you might consider installing a perimeter intrusion and detection assessment system (PIDAS). This special fencing system has sensors to detect intruders. The downside is that a stray deer or other wildlife might also trigger an alarm.
Fencing can be made from a range of components, such as steel, wood, brick, or concrete. Chain link, wire, and steel mesh fences are used at many facilities and can be ranked from high- to low-security. The gauge of the wire and the size of the mesh help determine the security of these fences. The gauge is the measurement of the diameter of the wire. Keep in mind that the higher the gauge number, the smaller the wire diameter. Table 3.2 lists the common wire gauges and diameters.
The American Society for Testing and Materials (ASTM) defines fence standards and certifies vendors’ fencing. ASTM has established standards for residential, commercial, and high-security products. The distance between the two wires in the fence is the mesh size. Table 3.3 lists common fence mesh sizes and their corresponding security ratings. To visualize: a high fence with small holes is difficult for an intruder to climb, whereas a high fence with large holes can be easily climbed.
Gates
Whereas a fence acts as a barrier, a gate is a choke point and controls ingress and egress of pedestrian and vehicle traffic. A gate must be of the same level of security as the fence to act as an effective deterrent. Gates are covered by UL Standard 325 and ASTM-F2200. Gates can be designed as swing gates, rolling gates, and cantilever gates. There are four classes of gates, as shown in Table 3.4.
Other flow control mechanisms include turnstiles and mantraps. A turnstile is a form of gate that prevents more than one person at a time from gaining access to a controlled area. Turnstiles usually only rotate in one direction, restricting flow. You see turnstiles at sporting events, in the subway, and so on.
A mantrap is a set of two doors. The idea behind a mantrap is that one or more people must enter the mantrap and shut the outer door before the inner door will open. Some mantraps lock both the inner and outer door if authentication fails so that the individual cannot leave until a guard arrives to verify the person’s identity. Mantraps can be used to control the flow of individuals into and out of sensitive areas. Mantraps can help prevent piggybacking. Piggybacking is commonly attempted at controlled-entry points where authentication is required. Although some individuals use terms piggybacking and tailgating synonymously, tailgating is also associated with the practice of attempted unauthorized access at vehicle access points and gates. Some gates might open long enough that a second car can attempt to pass through.
ExamAlert
A mantrap is used to prevent piggybacking and additional layers of defense can be obtained by using guards and CCTV.
Bollards
Bollards are another means of perimeter control. Made of concrete or steel, they block vehicular traffic or protect areas where pedestrians might be entering or leaving buildings. After 9/11, these barriers have advanced far beyond the standard steel poles of the past. Companies now make bollards with electronic sensors to notify building inhabitants that someone has rammed or breached the bollards. Although fences act as a first line of defense, bollards are a close second because they can deter individuals from ramming a facility with a car or truck. Figure 3.1 shows an example of a bollard.
Perimeter controls need not look like concrete and steel. Have you ever noticed majestic ponds located next to many corporate headquarters? Don’t be lulled into believing they were placed there merely as a community beautification project. They are another form of a barricade or barrier. They are also useful in case of fire because they can serve as an additional water source. Access controls are a critical piece of premises security that can be either natural, such as a body of water, or structural, such as a fence.
What else can be done? Warning signs or notices should be posted to deter trespassing. A final review of the grounds area should be conducted to make sure that nothing has been missed. This includes any opening that is around 96 square inches or larger and 18 feet or less above the ground, such as manholes/tunnels, gates leading to the basement, elevator shafts, ventilation openings, and skylights. Even the roof, basement, and walls of a building might contain points vulnerable to entry and should be assessed.
After the premises of the facility have been secured, a CISSP should move on to an analysis of other perimeter control mechanisms (such as CCTV, card keys, radio frequency ID [RFID] tags, lighting, guards, dogs, locks, and biometric access controls). Just as networks use chokepoints and multiple layers of defenses, so should physical security controls. Each of these is explained in more depth in the sections that follow.
CCTV Cameras
CCTVs can be used as monitoring devices or as physical detective controls to assess and identify intruders. They also serve as a great deterrent. Before the first camera is installed, several important questions must be answered: Will the video feed be monitored in real-time? How long will recordings be stored? What type of area will be monitored? The CCTV by itself cannot prevent anything. If the CCTV system is to be used in a real-time, it must be used with human intervention by way of monitoring to serve as a preventative control. A guard or other individual is needed to watch as events occur. If the CCTV system is being used after the fact, it is functioning as a detection control. Different environments require different systems.
If a CCTV system is to be used outside, the amount of illumination is important. Illumination is controlled by an iris that regulates the amount of light that enters the CCTV camera. An auto iris lens is designed to be used outside where the amount of light varies between night and day; a manual iris lens is used for cameras to be used indoors. CCTV cameras can even be equipped with built-in LEDs or configured for infrared recording.
The focal length of the lens controls the camera’s depth of field, which determines how much of the visual environment is in focus on the CCTV monitor. The depth of field is critical if there is not a human being monitoring the system to make adjustments to the focus. Although some systems have fixed focal lengths, others offer the capability to pan, tilt, and zoom (PTZ), allowing the operator to zoom in or adjust the camera as needed. Older CCTV cameras are analog, whereas most modern cameras are digital, capturing enhanced detail quickly by the use of charged coupled devices (CCDs). A CCD is similar to the technology found in a fax machine or a photocopier.
A CCTV system can be wired or wireless and comprises many components including cameras, transmitters, receivers, recorders, monitors, and controllers. CCTV systems provide effective surveillance of entrances and critical access points. If employees are not available to monitor in real time, activity can be recorded and reviewed later. An annunciator can be used to reduce the burden of the individual monitoring the alarm. An annunciator can detect intrusions or other types of noise and trip an alarm so that a guard does not have to constantly watch a monitor. If you are considering CCTV systems, remember to provide for the rights of worker privacy or notification of the absence of privacy, and consider the existence of potential blind spots.
Lighting
Lighting is a common type of perimeter protection. Some studies have found that up to 80% of criminal acts at businesses and shopping centers happen at night in adjacent parking lots, so companies need to practice due care when installing exterior lights. Failure to provide adequate lighting in parking lots and other high-traffic areas could lead to lawsuits if an employee or visitor is attacked. Outside lighting discourages prowlers and thieves. Some common types of exterior lights are:
![]() Floodlights
Floodlights
![]() Streetlights
Streetlights
![]() Searchlights
Searchlights
Terms used for the measurement of light include lumen, lux, and foot-candle. One lux is one lumen per square meter and one foot-candle is one lumen per square foot. The National Institute of Standards and Technologies (NIST) states that for effective perimeter control, buildings should be illuminated with 2 foot-candles of light in a projection that is 8 feet high.
Take a moment to look at how the lights are configured the next time you visit a mall or department store. You will see rows of lights placed evenly around the facility. That is an example of continuous lighting. Areas such as exits, stairways, and building evacuation routes are equipped with standby lighting. Standby lighting activates only in the event of power outages or during emergencies; however, standby lighting is more commonly used with homes and/or businesses that are set to turn on after at a certain time after normal operating hours late at night to give the appearance that the home or business is occupied, thus deterring intruders and trespassers.
As with all security, the provision of lighting takes planning. Effective lighting requires more than the placement of a light bulb atop a pole. Security professionals need to consider what areas need to be illuminated, which direction that light should be directed, and how bright the light will be. Some lights make use of a Fresnel lens. These lenses are designed to focus light in a specific direction and were originally found in theaters and lighthouses.
Security checkpoints are another location where you will see careful design of the illumination. Here, lights are aimed away from the guard post so that anyone approaching the checkpoint can easily be seen and guards are not exposed in the light. This is an example of glare protection. If lights are used for perimeter detection, they are typically mounted above the fence. Doing so blinds intruders to the surrounding view and allows intruders to be more easily seen by the guard force.
Just as too little light can be a problem, too much light can lead to a less secure environment. Glare and over-lighting can cause problems by creating very dark areas just outside the range of the lighted area. In addition, neighboring businesses or homes might not appreciate residing in such a brightly lit area. Therefore, exterior lighting involves the balance of too little versus too much light. Exterior lights should each cover their own zone but still allow for some overlap between zones.
Guards and Dogs
Guards can offer the best and worst in the world of protection. Although our increased need for security has driven the demand for more guards, they are only human and their abilities vary. Technology has also driven our need for security guards. As we get more premises control equipment, intrusion detection systems, and computerized devices, additional guards are required to control these systems.
Unlike computerized systems, guards have the ability to make judgment calls and think through how they should handle specific situations. This is called discernment. Guards can also be used in multiple roles so that they can monitor, greet, sign in, and escort visitors. Just by having them in a facility or guarding a site, an organization has provided a visual deterrence. Before you go out and hire your own personal bodyguard, you should also be aware that guards do have some disadvantages. Guards are expensive, make mistakes, can be poorly trained, make policy exceptions for people they like or trust, can be manipulated, might sleep on the job, steal company property, or even injure someone.
Dogs, much like guards, have also been used to secure property throughout time. Breeds such as Chows, Dobermans, and German Shepherds were bred specifically for guard duty. Although dogs can be trained, loyal, obedient, and steadfast, they are sometimes unpredictable and could bite or harm the wrong person. Because of these factors, dogs are usually restricted to exterior premises control and should be used with caution.
Locks
Locks come in many types, sizes, and shapes, and are both one of the oldest forms of theft-deterrent mechanisms and the most commonly used deterrent. Locks have the highest return on investment. Locks have been around since their use in 2000 B.C. by the Egyptians.
It’s important to select the appropriate lock for your designated area. Different types of locks provide different levels of protection. Locks are designed to various strengths and levels of security. The grade of the lock specifies its level of construction. Table 3.5 lists the three basic grades of locks and their common usage.
ANSI standards define the strength and durability of locks. As an example, a grade 3 lock is designed to function for 200,000 cycles, whereas a grade 2 lock must function for 400,000 cycles, and a grade 1 lock must function for 800,000 cycles. Some common lock types include combination locks, mechanical locks, cipher locks, and device locks.
A basic combination lock requires the owner to input a correct combination of numbers to unlock it, and usually has a series of wheels inside. The longer the length of the combination, the more secure the lock is. Figure 3.2 shows an example of a three- and four-digit combination lock. Even with a four-digit lock that would only be 10,000 combinations to choose from, so basic locks are more of a deterrent than a preventive control.
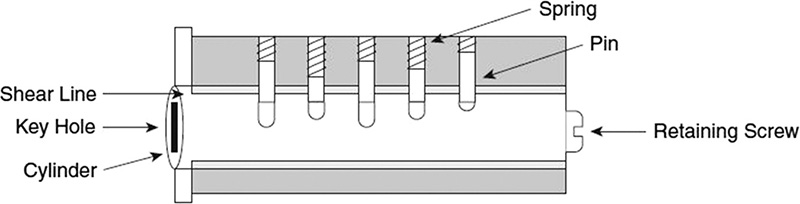
Mechanical locks have been used for hundreds of years to secure items of importance. Early locks were made of wood and attempts to improve the lock designs increased throughout the 1700s. Mechanical locks include warded locks and pin-and-tumbler locks. The modern tumbler lock was patented by Linus Yale in 1848.
A warded lock is a basic padlock that uses a key with a spring loaded bolt. Warded locks use a series of wards, or blockages, that a key must match up to. It is the cheapest type of mechanical lock and is also the easiest to pick. It can be picked by inserting a stiff piece of wire or thin strip of metal; a simple warded lock is one that can be opened with a skeleton key. Warded locks do not provide a high level of security. Tumbler locks are somewhat more complex than a warded lock. Instead of wards, they use tumblers, which increases the difficulty of using the wrong key to open a lock. When the right key is inserted into the cylinder of a tumbler lock, the pins are lifted to the right height so that the lock can open or close. Figure 3.3 illustrates a basic tumbler lock design.
In a tumbler lock, the correct key has the notches and raised areas to shift the pins into the proper position. The pins are spring-loaded so that when the key is removed, the pins return to the locked position. Tumbler locks can be designed as pin tumblers, wafer tumblers, lever tumblers, or tubular locks. Tubular locks are also known as ace locks and are considered to be of higher security. These are used for computers, vending machines, and other high-security devices.
These are not the only types of locks. There is also the category of locks known as cipher locks or programmable locks. These require the user to enter a preset or programmed sequence. Cipher locks are designed to use keypads or ciphers to control access into restricted areas. One shortcoming with a keypad device is that bystanders can “shoulder-surf” and steal passcodes. Or someone that knows the code props the door open so others can easily enter. That’s why door delay alarms should be considered. To increase security and safety, visibility shields should be used to prevent bystanders from viewing the passcodes that are entered. Door delay alarms may also be used to alert if someone props the door open. One main advantage to cipher locks is that some systems, referred to as smart locks, allow for granular roles and rules-based access control of physical security along with user access auditing. This makes it very easy to revoke user access quickly to a secure area by deleting the access code and not having to collect a “key or access card.” It is also a detective control and allows for effective auditing to account for who accessed secured areas.
Locks can also be used to secure a wide range of devices. Device locks can be used to secure ports and laptops. Employees who are issued laptops should be given a laptop-locking device. Although data security is important, the security of the device should also be considered; it takes only a moment for someone to take a laptop or other mobile device. Device locks can help protect physical assets and signal to employees your concern that devices issued to them should be protected.
Caution
Although locks are important to use to secure laptops, it’s also important to use encryption because the data is most likely worth more than the hardware.
Many organizations don’t change locks frequently. Others fail to require terminated employees to return keys. Some locks even have master keys. This option allows a supervisor or housekeeper to bypass use of the normally required key and gain entry. Finally, there is the issue of lock picking. Although locks can be used to deter and delay, all locks are subject to attack.
Keep in mind that a lock is a deterrent and not a preventive control. Most locks keep out honest people and should work as a layer of security in your overall security solution. Even high-end Simplex locks have been bypassed with strong magnets.
Lock Picking
Lock picking is one way to bypass the security intended by a lock. Although not the fastest way to break in, it does offer a stealthy way to bypass the locks, and might mask from the victim that a security violation has occurred. If you have any doubts whether lock picking is a common hacker skill, check out any of the large hacking conferences such as DEF CON. This yearly hacker conference usually has presentations and contests devoted to lock picking. Deviant Ollam has a list of lock picking resources at deviating.net/lockpicking/.
Lock-picking is basically the manipulation of a lock’s components to open it without a key. The basic components used to pick locks are:
![]() Tension wrenches—These are not much more than a small angled flathead screwdriver. They come in various thicknesses and sizes.
Tension wrenches—These are not much more than a small angled flathead screwdriver. They come in various thicknesses and sizes.
![]() Picks—Just as the name implies, these are similar to a dentist’s pick. They are small, angled, and pointed.
Picks—Just as the name implies, these are similar to a dentist’s pick. They are small, angled, and pointed.
Together, these tools can be used to pick a lock. One basic technique is scrubbing or raking. Scrubbing is the act of scraping the pins quickly with a pick while the tension wrench is used to place a small amount of force on the lock. Some of the pins will be placed in a mechanical bind and will be stuck in the unlocked position. With practice, this can be done quickly so that all the pins stick and the lock disengages. Key-bumping is another lock-picking technique that has gained notoriety. Key-bumping is performed by using a key for a specific brand of lock that has been cut to the number nine position. This is the lowest possible cut for the key, as shown in Figure 3.4. Notice how the inner 4 ridges are lower than what is normal.
The key is inserted into the lock and slight pressure is applied while the key is tapped (bumped). A search of YouTube will return many videos if you would like to learn more about key-bumping. This transference of force causes the pins to jump inside of the cylinder so that the lock is disengaged.
Other tools to bypass locks include:
![]() Lock pick sets—These vary in price and design, and might contain anything from a couple of tools to more than two dozen various picks and tension wrenches.
Lock pick sets—These vary in price and design, and might contain anything from a couple of tools to more than two dozen various picks and tension wrenches.
![]() Electric lock pick guns—These devices attempt to speed up manual lock picking by working somewhat like an electric toothbrush or an electric knife.
Electric lock pick guns—These devices attempt to speed up manual lock picking by working somewhat like an electric toothbrush or an electric knife.
![]() Tubular picks—These are designed to pick tubular locks. These locks are the same kind as used on Kryptonite bicycle locks, which were thought to be highly secure until 2004, when someone demonstrated that the lock could be opened with a Bic pen. The same issue exists with Kensington-style laptop locks. These are sometime refered to as ACE locks.
Tubular picks—These are designed to pick tubular locks. These locks are the same kind as used on Kryptonite bicycle locks, which were thought to be highly secure until 2004, when someone demonstrated that the lock could be opened with a Bic pen. The same issue exists with Kensington-style laptop locks. These are sometime refered to as ACE locks.
![]() Lock shims—Formed pieces of thin, stiff metal that can be inserted into the latch of a padlock and used to push back the locking mechanism.
Lock shims—Formed pieces of thin, stiff metal that can be inserted into the latch of a padlock and used to push back the locking mechanism.
Employee Access Control
Where employees go and what they do is of importance to the organization. Such information is critical not only for monitoring access control, but also for reconstructing events following an intrusion, theft, or attack.
Caution
It is unfortunate but true that cleaning crews are sometimes overlooked as potential security threats. They are typically around after everyone else leaves and they have full access to the facility. Unlocked computers can make a tempting and easy target. One of the editors of this book shared the story of how the cleaning crew of his former employer shared badges and often had friends or relatives fill in for them for a day or two using the same badge.
Badges, Tokens, and Cards
Tokens, cards, and keys are another means of physical access control. Chapter 8, “Identity and Access Management,” covers these issues in much more depth, but the physical characteristics and use of these controls are discussed here.
Table 3.6 details common types of access cards and badges.
Physical access control cards can be separated into two broad categories: dumb cards and smart cards. Dumb cards are those that contain no electronics and are used at many different organizations. These cards often include an individual’s photo to verify a person’s right to be in a particular area. These photo ID cards are really just a form of identity badge. Photo badges are effective only if inspected by guards and controls are put in place to ensure that they are inspected at key points in and around a facility.
The second type of access control is a smart card. European countries widely use smart card technology in credit cards, whereas the United States just started to implement them in late 2015. Smart cards are much more versatile than photo cards. Smart cards can make entry decisions electronically. These devices can be configured in several different ways. Some require only that the user get close to the access-control device. These proximity readers don’t require the user to physically insert the card. Some identification technologies use RFID. Others require user activation, such as requiring the user to input a key code. One example of a deployed smart card is the Common Access Card (CAC) used by the U.S. Department of Defense. CACs are considered to be dual-factor—also known as multi-factor or strong authentication—and are also used with a public key infrastructure (PKI).
Some organizations provide card users with two key codes. One key code is used for normal access, whereas the second is used as a silent hostage alarm or duress alarm. The silent hostage alarm code allows an employee to gain access, but also silently alerts the authorities of a hostage situation.
Caution
High-security facilities have a history of mandating that employees make sure their badges are not visible after leaving the workplace to go home or out to lunch. This is an effective control for any organization that uses badges to reduce social engineering or targeting of specific vehicles, briefcases, laptops, tablets, smartphones, etc.
RFID Tags
RFID tags are another emerging trend in the field of physical access control. RFID tags are extremely small electronic devices composed of a microchip and an antenna. These devices transmit small amounts of information. RFID tags can be designed in different ways:
![]() Active—Active tags have a battery or power source used to power the microchip and constantly transmit a weak signal.
Active—Active tags have a battery or power source used to power the microchip and constantly transmit a weak signal.
![]() Passive—These devices have no battery. They are powered by an RFID reader/transponder, which generates an electromagnetic wave that induces a current in the RFID tag.
Passive—These devices have no battery. They are powered by an RFID reader/transponder, which generates an electromagnetic wave that induces a current in the RFID tag.
![]() Semipassive—These hybrid devices have a battery to power the microchip, but still transmit data by harnessing energy from the reader.
Semipassive—These hybrid devices have a battery to power the microchip, but still transmit data by harnessing energy from the reader.
RFID tags are manufactured in various sizes, down to dust particle size—their placement possibilities are endless. The United States military has conducted trials to test the possibilities of using RFID tags to control vehicle traffic at military locations. Some states are considering embedding RFID tags in license and automobile registrations so that passing police cars can be alerted about out-of-date registrations. Many countries are starting to use RFID tags in passports. The U.S. Federal Drug Administration (FDA) has approved an RFID tag that will be used to prevent the possibility of wrong-site, wrong-procedure, and wrong-patient surgeries. Government officials have advocated that these devices become standard issue for firefighters, police officers, and emergency rescue individuals because their jobs place them in situations in which their identification could be lost or destroyed.
Attacks against these devices are on the rise. To learn more, see rfidiot.org. Expect to see continued usage and exploitation of these devices in the coming years.
Biometric Access Controls
Biometric controls are discussed extensively in Chapter 8. Because they are used for premises control, they should be mentioned here. The fascinating thing about biometric controls is that they are based on a physiological attribute or behavioral characteristic of an individual. As an example, one consulting job I had was with a government agency that took security seriously. This agency implemented two-factor authentication by means of an access card and biometric sensor. As if these two were not enough, I was also weighed while in the mantrap before being allowed access to the data center. These are some of the primary types of biometric systems: All biometric data collected from humans is turned into binary data, formatted, then hashed and stored in a reference file. When a user goes to authenticate, the user’s biometric sample is collected again, hashed using the same algorithm, and compared to the reference filed; a match to a certain degree is required for access.
![]() Fingerprint scan—Widely used for access control to facilities and or items, such as laptops, smartphones and some tablets. This control works by distinguishing up to 40 details about the peaks, valleys, and ridges of the user’s fingerprint. Most systems only attempt to match between six and a dozen points because the more points that are used the more chance of a false rejection; however, the lower the number of points the more chance of a false acceptance.
Fingerprint scan—Widely used for access control to facilities and or items, such as laptops, smartphones and some tablets. This control works by distinguishing up to 40 details about the peaks, valleys, and ridges of the user’s fingerprint. Most systems only attempt to match between six and a dozen points because the more points that are used the more chance of a false rejection; however, the lower the number of points the more chance of a false acceptance.
![]() Palm scan—Analyzes characteristics associated with the user’s palm, such as the creases, grooves, and ridges. A palm scan also includes the fingerprint of the fingers on the hand being scanned. If a match is found, the individual is allowed access.
Palm scan—Analyzes characteristics associated with the user’s palm, such as the creases, grooves, and ridges. A palm scan also includes the fingerprint of the fingers on the hand being scanned. If a match is found, the individual is allowed access.
![]() Hand geometry—Another biometric system that uses the unique geometry of a user’s hand to determine the user’s identity. Looks specifically at the shape, length, and width of the hand, knuckles, and fingers.
Hand geometry—Another biometric system that uses the unique geometry of a user’s hand to determine the user’s identity. Looks specifically at the shape, length, and width of the hand, knuckles, and fingers.
![]() Iris scan—An eye-recognition system that is very accurate because it has over 400 points of reference. Looks at the color of the eye surrounding the pupil. Iris scanning examines the crypts, furrows, ridges, striations, ligaments, and collarette. This is considered to be the most accurate form of biometric.
Iris scan—An eye-recognition system that is very accurate because it has over 400 points of reference. Looks at the color of the eye surrounding the pupil. Iris scanning examines the crypts, furrows, ridges, striations, ligaments, and collarette. This is considered to be the most accurate form of biometric.
![]() Retina scan—Another eye-recognition system that is considered accurate for identification. However, these blood vessels can change with diseases, such as glaucoma.
Retina scan—Another eye-recognition system that is considered accurate for identification. However, these blood vessels can change with diseases, such as glaucoma.
![]() Facial scan—Uses points of comparison like hand geometry and performs a mathematical comparison with the face prints it holds in a database to allow or block access.
Facial scan—Uses points of comparison like hand geometry and performs a mathematical comparison with the face prints it holds in a database to allow or block access.
Regardless of what biometric method is used, each follows a similar usage pattern:
1. Users must first enroll in the system—Enrollment is not much more than a process of allowing the system to take one or more samples for later comparison.
2. A user requests to be authenticated—Statistics collected during enrollment are used to compare to data scanned during the user’s authentication request.
3. A decision is reached—A match allows the user access, whereas a discrepancy between causes the user to be denied access.
Environmental Controls
Heat can be damaging to computer equipment. This is why most data centers are kept at temperatures of around 70°F. Higher and lower temperatures can reduce the useful life of electronic devices. But temperature should not be your only concern. High humidity can cause electronics to corrode and low humidity increases the risk of static electricity. What might feel like only a small shock to human touch can totally destroy electronic components. Grounding devices such as antistatic wrist bands and antistatic flooring can be used to reduce the possibility of damage.
Heating, Ventilating, and Air Conditioning
Do you know what can be hotter than Houston in the summer? A room full of computers without sufficient HVAC. Data centers, or any areas that are full of computer or electrical equipment, are going to generate heat. Modern electronic equipment is very sensitive to heat and can tolerate temperatures of only 110°F to 115°F degrees without permanent damage to circuits.
Data centers should have HVAC systems separate from the HVAC of the rest of the facility. The HVAC should maintain positive pressurization and ventilation. This controls contamination by pushing air outside. This is especially important in case of fire because it ensures that smoke will be pushed out of the facility instead of being pulled in.
Security management should know who is in charge of the HVAC system and how they can be contacted. Intake vents should be protected so that contaminates cannot be easily spread. These systems must be controlled to protect organizations and their occupants from chemical and biological threats. HVAC systems generate water; this can be as a gas (affecting humidity) or as a liquid (encouraging growth of mold, structural damage, and decay). As previously mentioned, high humidity causes rust and corrosion. Low humidity can increase the risk of static electricity. The ideal humidity for a data center is between 35% and 45%.
Caution
The American Society of Heating, Refrigerating, and Air-conditioning Engineers (ASHRAE) has expanded the allowable temperatures for data centers in an effort to promote green environmental practices and to provide a wider range of allowed temperatures.
Electrical Power
Electrical power, like HVAC, is a resource that most of us take for granted. Residents of the United States are lucky, but large portions of the world live without dependable electrical power. Even areas that have dependable power can be subject to line noise or might suffer from electromagnetic interference (EMI). Electrical motors and other electronic devices can cause EMI. You might have noticed that fluorescent lights can also cause electrical problems; this phenomenon is known as radio frequency interference (RFI). Table 3.7 lists some other power anomalies.
Luckily, power conditioners, surge protectors, and uninterruptible power supplies can provide clean power. Although most of the time we seek this clean power, there are other times when we need to kill electricity quickly. This is especially true if someone is electrocuted, or if there is a danger of water coming into direct contact with power sources. National fire protection codes require that you have an emergency power off (EPO) switch located near server room exit doors to kill power quickly if needed. These switches are easy to recognize because they are in the form of a big red button.
Caution
The EPO switch should have a plastic cover installed to prevent anyone from accidentally pressing it.
Uninterruptible Power Supply
Because computers have become an essential piece of technology, downtime of any significant duration can be devastating to an organization. Power outages can happen and businesses must be prepared to deal with the situation. Uninterruptible power supplies (UPS) are one of the primary means of meeting this challenge. Two categories of UPS exist:
![]() Online system—An online system uses AC power to charge a bank of DC batteries. These batteries are held in reserve until power fails. At that time, a power inverter converts the DC voltage back to AC for the computer systems to use. These systems are good for short-term power outages. Many have a software component that can perform a graceful shutdown.
Online system—An online system uses AC power to charge a bank of DC batteries. These batteries are held in reserve until power fails. At that time, a power inverter converts the DC voltage back to AC for the computer systems to use. These systems are good for short-term power outages. Many have a software component that can perform a graceful shutdown.
![]() Standby system—This type of system monitors a power line for a failure. When a failure is sensed, backup power is switched on. This system relies on generators or power subsystems to keep computers running for longer power outages.
Standby system—This type of system monitors a power line for a failure. When a failure is sensed, backup power is switched on. This system relies on generators or power subsystems to keep computers running for longer power outages.
Most standby generators run on diesel fuel or natural gas:
![]() Diesel fuel—Should maintain at least 12 hours of fuel.
Diesel fuel—Should maintain at least 12 hours of fuel.
![]() Natural gas—Suitable for areas that have a good supply of natural gas and are geologically stable.
Natural gas—Suitable for areas that have a good supply of natural gas and are geologically stable.
Equipment Life Cycle
Even when you have done all the right things, performed preventative maintenance, kept equipment at the right operating temperature, and used surge protectors, equipment will eventually cease to function. This is why many companies choose to maintain service-level agreements (SLA).
ExamAlert
An SLA is a contract with a hardware vendor that provides a certain level of protection. For a fee, the vendor agrees to repair or replace the equipment within the contracted time.
You need to know two important statistics when purchasing equipment or when attempting to calculate how long the equipment will last. First is the mean time between failure (MTBF), which is used to calculate the expected lifetime of a device. The higher the MTBF is, the better. The second value is the mean time to repair (MTTR). The MTTR is an estimate of how long it takes to repair the equipment and get it back into use. For MTTR, lower numbers are better.
Fire Prevention, Detection, and Suppression
A fire needs three things: oxygen, heat, and fuel. When all three items are present, a fire can ignite and present a lethal threat, as shown in the fire tetrahedron in Figure 3.5. Fires can be devastating to people and facilities. Saving human lives should always be your first priority. As a CISSP candidate, it’s important to understand that proper precautions, preparation, and training must be performed to help save lives and limit potential damage.
Fire prevention is one of the key items that must be addressed to have an effective proactive defense against fires. A big part of prevention is making sure people are trained and know how to prevent potential fire hazards. Corporate policy must define how employees will be trained to deal with fires.
Fire drills are another important part of building a good security policy. Fire drills should be periodic, yet random. Employees should have a designated area to go to in a safe zone outside the facility. Supervisors or others should be in charge of the safe zones, and responsible for performing an employee head count to ensure that everyone is present and accounted for. After the drill, employees should be badged in on the way back into the facility to deter social engineering and piggyback attacks.
Fire-Detection Equipment
Having plans and procedures to carry out in case of a fire is only part of the overall fire-prevention program. Companies should make sure they have appropriate and functioning fire-detection equipment so that employees can be alerted to possible danger. Fire detectors can work in different ways and can be activated by the following:
![]() Heat—A heat-activated sensor is triggered when a predetermined temperature is reached or when the temperature rises quickly within a specified time period. The rate-of-rise type of sensor produces more false positives.
Heat—A heat-activated sensor is triggered when a predetermined temperature is reached or when the temperature rises quickly within a specified time period. The rate-of-rise type of sensor produces more false positives.
![]() Smoke—A smoke-activated sensor can be powered by a photoelectric optical detector or by a radioactive smoke-detection device.
Smoke—A smoke-activated sensor can be powered by a photoelectric optical detector or by a radioactive smoke-detection device.
![]() Flame—A flame-activated sensor is the most expensive of the three types discussed. It functions by sensing either the infrared energy associated with flame or the pulsation of flame.
Flame—A flame-activated sensor is the most expensive of the three types discussed. It functions by sensing either the infrared energy associated with flame or the pulsation of flame.
Fire Suppression
Just being alerted to a fire is not enough. Employees need to know what to do and how to handle different types of fires. A fire can be suppressed by removing heat, fuel, or oxygen. Fires are rated according to the types of materials burning. Although it might be acceptable to throw some water on smoldering paper, it would not be a good idea to throw water on a combustible metal fire; water on a metal fire can actually make the fire spread. Table 3.8 lists fire classes and their corresponding suppression methods.
Tip
Hint on ABCD—think of them in the order of frequency of occurrence. Paper more than liquid, liquid more than electric, electric more than metal.
The two primary methods of corporate fire suppression include water sprinklers and gas discharge systems. Water is easy to work with, widely available, and nontoxic. Gas discharge systems are better suited for areas where humans are not present. Both suppression systems are discussed next.
Water Sprinklers
Water sprinklers are an effective means of extinguishing Class A fires. The disadvantage of using sprinkler systems is that water is damaging to electronics. Four variants of sprinkler systems are available:
![]() Dry pipe—As the name implies, this sprinkler system contains no standing water. The line contains compressed air. When the system is triggered the clapper valve opens, air flows out of the system, and water flows in (see Figure 3.6). The benefit of this type of system is that it reduces the risk of accidental flooding and gives some time to cover or turn off electrical equipment. These systems are also great for cold-weather areas, unmanned warehouses, and other locations where freezing temperatures could freeze any water standing in the system.
Dry pipe—As the name implies, this sprinkler system contains no standing water. The line contains compressed air. When the system is triggered the clapper valve opens, air flows out of the system, and water flows in (see Figure 3.6). The benefit of this type of system is that it reduces the risk of accidental flooding and gives some time to cover or turn off electrical equipment. These systems are also great for cold-weather areas, unmanned warehouses, and other locations where freezing temperatures could freeze any water standing in the system.
![]() Wet pipe—Wet pipe systems are widely used and are ready for activation. This system is charged and full of water. When triggered, only the affected sprinklers activate. Wet pipe systems are not triggered by smoke, and they are more prone to leaks and accidental discharge. The next time you are staying in a hotel, take a look around and you’ll probably see this type of system. Wet pipe systems typically use some type of fusible link that allows discharge after the link breaks or melts.
Wet pipe—Wet pipe systems are widely used and are ready for activation. This system is charged and full of water. When triggered, only the affected sprinklers activate. Wet pipe systems are not triggered by smoke, and they are more prone to leaks and accidental discharge. The next time you are staying in a hotel, take a look around and you’ll probably see this type of system. Wet pipe systems typically use some type of fusible link that allows discharge after the link breaks or melts.
![]() Pre-action—This is a combination system. Pipes are initially dry and do not fill with water until air pressure is reduced. Even then, the system will not activate until a secondary mechanism triggers. The secondary mechanism might be some type of fusible link similar to what is used in a wet pipe system. The advantage of pre-action systems is that the design provides an extra level of control that reduces the chance of accidental triggering.
Pre-action—This is a combination system. Pipes are initially dry and do not fill with water until air pressure is reduced. Even then, the system will not activate until a secondary mechanism triggers. The secondary mechanism might be some type of fusible link similar to what is used in a wet pipe system. The advantage of pre-action systems is that the design provides an extra level of control that reduces the chance of accidental triggering.
![]() Deluge—This is similar to a dry pipe system, except that after the system is triggered, there is no holding back the water. A large volume of water will cover a large area quickly. If your company builds booster rockets for supplies being shuttled to the International Space Station, this might be a preferred suppression system.
Deluge—This is similar to a dry pipe system, except that after the system is triggered, there is no holding back the water. A large volume of water will cover a large area quickly. If your company builds booster rockets for supplies being shuttled to the International Space Station, this might be a preferred suppression system.
Halon
Sometimes we become smug in our belief that the products we create can do no harm. During the industrial revolution, asbestos was hailed as a miracle fiber. By the 1920s, it was discovered that it caused major health problems. Halon has a similar history. Originally used in computer rooms for fire suppression, halon was considered the perfect fire suppression method. Halon mixes easily with air, doesn’t harm computer equipment, and once dissipated, halon leaves no solid or liquid residue. Halon is unique in that it does not remove or reduce any of the three necessary components of a fire; instead, halon interferes with the fire’s chemical reaction. There are two types of halon:
![]() Halon 1211—This type is found in portable extinguishers and is stored as a liquid.
Halon 1211—This type is found in portable extinguishers and is stored as a liquid.
![]() Halon 1301—This version is used in fixed flooding systems and is stored as a gaseous agent.
Halon 1301—This version is used in fixed flooding systems and is stored as a gaseous agent.
The Montreal Protocol of 1987 designated halon as an ozone-depleting substance. Halon is 3–10 times more damaging to the ozone layer than CFCs. Other issues with halon exist. If it is deployed in concentrations of greater than 10% and in temperatures of 900°F or more, it degrades into hydrogen fluoride, hydrogen bromide, and bromine. This toxic brew is not something that people should be breathing.
If you currently have a halon fire-suppression system, you can leave it in place, but there are strict regulations on reporting discharges. Laws also govern the removal and disposal of halon fire-suppression systems. Some of the more ecological and less toxic EPA-approved replacements for halon include:
![]() FM-200
FM-200
![]() CEA-410
CEA-410
![]() NAF-S-III
NAF-S-III
![]() FE-13
FE-13
![]() Low-pressure water mist
Low-pressure water mist
![]() Argonite
Argonite
Alarm Systems
Although this chapter is focused on physical security, there is a range of technical controls that can be used to enhance physical security. Alarm systems are one such control.
An alarm system is made up of many components, including an intrusion detection system, control panel, arming systems, and annunciators. Every time there is an alarm, someone must respond and determine whether the event is real.
Intrusion Detection Systems
This section discusses physical intrusion detection systems (IDS), which are used for detecting unauthorized physical access. You might have seen IDS sensors around windows or attached to doors and not even realized what they were. These sensors can detect the breakage of glass or the opening of doors. Overall, these systems are effective in detecting changes in the environment. Some common types of IDS sensors include:
![]() Audio detection or acoustical detection—These sensors use microphones and listen for changes in the ambient noise level. They are susceptible to false positives.
Audio detection or acoustical detection—These sensors use microphones and listen for changes in the ambient noise level. They are susceptible to false positives.
![]() Dry contact switches—These sensors detect when a door or window is opened.
Dry contact switches—These sensors detect when a door or window is opened.
![]() Electro-mechanical—These sensors trigger on a break in the circuit.
Electro-mechanical—These sensors trigger on a break in the circuit.
![]() Motion detectors—You have probably seen this type of sensor on one of the many security lights sold commercially. Motion detectors can be triggered from audio, radio wave pattern, or capacitance.
Motion detectors—You have probably seen this type of sensor on one of the many security lights sold commercially. Motion detectors can be triggered from audio, radio wave pattern, or capacitance.
![]() Vibration sensors—These sensors use piezoelectric technology to detect vibration and trigger on movement.
Vibration sensors—These sensors use piezoelectric technology to detect vibration and trigger on movement.
![]() Pressure sensitive—These sensors are sensitive to weight. Most measure a change in resistance to trigger the device. Pressure mats are an example of this type of technology.
Pressure sensitive—These sensors are sensitive to weight. Most measure a change in resistance to trigger the device. Pressure mats are an example of this type of technology.
![]() Photoelectric—These sensors use infrared light and are laid out as a grid over an area. If the grid is disturbed, the sensor will detect a change.
Photoelectric—These sensors use infrared light and are laid out as a grid over an area. If the grid is disturbed, the sensor will detect a change.
![]() Passive infrared—These sensors can sense changes in heat generated by humans.
Passive infrared—These sensors can sense changes in heat generated by humans.
ExamAlert
When you encounter intrusion detection questions on the actual exam, note whether the question is referencing a physical intrusion detection system or a logical intrusion detection system.
Sometimes organizations choose not to use IDS solutions because they can produce false positives. A false positive result indicates that a condition is present when it actually is not. Before these systems are deployed, a risk assessment should be performed to determine the true value of these devices to the organization. IDS solutions often are a layer of security used as monitoring tools that alert a security guard for further human inspection to determine further preventative measures to be taken.
Monitoring and Detection
Alarm systems must be monitored and controlled. Either an in-house guard or a third-party company will need to be assigned the task of monitoring the alarm system. Alarm systems use one of four basic designs, as shown in Table 3.9.
Ever notice how movies show the criminal disconnecting the alarm system or maybe even cutting the red wire to disable it? In reality, this doesn’t work. Alarm systems have built-in tamper protection. Any attempt to compromise detection devices, controllers, annunciators, or other alarm components initiates a tamper alarm. Even if power is cut, the alarm will still sound because modern alarm systems are backed up by battery power. Many systems also provide cellular phone backup. The National Fire Protection Association (NFPA) Fire Code 72 standard specifies that a local alarm system must provide 60 hours of battery backup, whereas a central station signaling system is required to provide only 24 hours of backup. In any situation in which the annunciator signals an alarm, Fire Code Standard 72 states that the audible alert should be at least 105 dB and have a visual component for the deaf or hearing-impaired.
Exam Prep Questions
1. You are a security consultant and your client would like you to recommend some commonly used control mechanisms. Which of the following control mechanisms work by means of supplying secret information (such as a key-code or password)?
![]() A. Guards
A. Guards
![]() B. Fences
B. Fences
![]() C. Locks
C. Locks
![]() D. Cameras
D. Cameras
2. You are a security officer and your client has asked you for your recommendation for a physical deterrent mechanism that will discourage casual trespassers. His facility is near a highly populated residential area with many family homes and children. What is the BEST recommendation you can give them from the following options?
![]() A. Recommend installing an 8′ fence with 3 strands of razor-wire
A. Recommend installing an 8′ fence with 3 strands of razor-wire
![]() B. Recommend a 3′ to 4′ fence
B. Recommend a 3′ to 4′ fence
![]() C. Recommend a 6′ to 7′ fence
C. Recommend a 6′ to 7′ fence
![]() D. Recommend an 8′ fence with a sign that says “No Trespassing”
D. Recommend an 8′ fence with a sign that says “No Trespassing”
3. What is the first priority after determining that there is a fire?
![]() A. Removing valuable assets
A. Removing valuable assets
![]() B. Calling the fire department
B. Calling the fire department
![]() C. Alerting employees to evacuate the building
C. Alerting employees to evacuate the building
![]() D. Informing senior management
D. Informing senior management
4. Doors with electric locks should default to which of the following in case of a power outage?
![]() A. Engaged
A. Engaged
![]() B. Locked
B. Locked
![]() C. Energized
C. Energized
![]() D. Fail-safe
D. Fail-safe
5. Halon was replaced by which of the following?
![]() A. AM-100
A. AM-100
![]() B. AM-200
B. AM-200
![]() C. FM-100
C. FM-100
![]() D. FM-200
D. FM-200
6. You have been asked to illuminate an area of critical importance. What is the correct amount of light to use for this area?
![]() A. 4 feet high, with 1 foot-candle
A. 4 feet high, with 1 foot-candle
![]() B. 6 feet high, with 2 foot-candles
B. 6 feet high, with 2 foot-candles
![]() C. 8 feet high, with 2 foot-candles
C. 8 feet high, with 2 foot-candles
![]() D. 8 feet high, with 4 foot-candles
D. 8 feet high, with 4 foot-candles
7. Gasoline or oil fires should be suppressed by which of the following?
![]() A. Water
A. Water
![]() B. Soda acid
B. Soda acid
![]() C. Dry powder
C. Dry powder
![]() D. Cleaning fluid
D. Cleaning fluid
8. Which of the following water sprinkler systems will not activate until triggered by a secondary mechanism?
![]() A. Dry pipe
A. Dry pipe
![]() B. Wet pipe
B. Wet pipe
![]() C. Preaction
C. Preaction
![]() D. Deluge
D. Deluge
9. Which of the following is a cipher lock?
![]() A. Latches
A. Latches
![]() B. Keypads
B. Keypads
![]() C. Cylinders
C. Cylinders
![]() D. Deadbolts
D. Deadbolts
10. You are a security consultant and your client has complained to you that he keeps experiencing extended periods of low voltage following a blackout that they recently experienced. He has already replaced the power line conditioner devices. What is the most likely event that is occurring?
![]() A. Fault
A. Fault
![]() B. Blackout
B. Blackout
![]() C. Brownout
C. Brownout
![]() D. Static electricity
D. Static electricity
11. Which is not a component of CPTED?
![]() A. Natural access control
A. Natural access control
![]() B. Natural reinforcement
B. Natural reinforcement
![]() C. Natural surveillance
C. Natural surveillance
![]() D. Territorial reinforcement
D. Territorial reinforcement
12. The method of fire suppression used depends on the type of fire that needs to be extinguished. Which of the following fire suppression methods does not suppress any of the fire’s three key elements, and led to the creation of the fire tetrahedron?
![]() A. CO2
A. CO2
![]() B. Halon
B. Halon
![]() C. Water
C. Water
![]() D. A dry pipe system
D. A dry pipe system
13. A differential latching clapper valve is most closely associated with which of the following?
![]() A. Mantrap
A. Mantrap
![]() B. Wet pipe fire suppression
B. Wet pipe fire suppression
![]() C. Shim locks
C. Shim locks
![]() D. Dry pipe fire suppression
D. Dry pipe fire suppression
14. Common access cards make use of which of the following?
![]() A. RFID
A. RFID
![]() B. Smart card
B. Smart card
![]() C. Magnetic strip
C. Magnetic strip
![]() D. Copper strip
D. Copper strip
15. What is the best answer that correctly describes the difference between MTBF and MTTR?
![]() A. The MTBF is the estimated time that a piece of hardware, device, or system will operate before it is fails. The MTTR is an estimate of how long it takes to repair the equipment and get it back into use.
A. The MTBF is the estimated time that a piece of hardware, device, or system will operate before it is fails. The MTTR is an estimate of how long it takes to repair the equipment and get it back into use.
![]() B. MTBF is time that would be required to correct or repair a device in the event it fails and the MTTR is the estimated time that a piece of hardware, device, or system will operate before it fails.
B. MTBF is time that would be required to correct or repair a device in the event it fails and the MTTR is the estimated time that a piece of hardware, device, or system will operate before it fails.
![]() C. The MTBF is a value that can be used to compare devices to one another and also to determine the need for an SLA for a device.
C. The MTBF is a value that can be used to compare devices to one another and also to determine the need for an SLA for a device.
![]() D. There is no need for a company to determine MTBF and the MTTR for assets if they do not live in an area where natural disasters such as hurricanes are not common.
D. There is no need for a company to determine MTBF and the MTTR for assets if they do not live in an area where natural disasters such as hurricanes are not common.
Answers to Exam Prep Questions
1. C. Locks are one of the most effective and widely used theft deterrents. Locks work by means of supplying secret information, such as a key-code or password. All other answers are incorrect because locks are the most widely used and offer the greatest return on initial investment.
2. B. B is the correct answer as the question asks how to deter casual trespassers. A is not the best answer; while it does meet the intent of your client, it exceeds his expectations for security. Moreover, the razor wire would certainly harm anyone who attempts to climb the fence. Answers C and D are incorrect because while these may keep out an intruder they do not meet the requirements of the client. An 8-foot fence would exceed the requirements of the client.
3. C. The safety of employees should always be your first concern. All other answers are incorrect: Protecting assets (answer A), calling the fire department (answer B), and informing senior management (answer D) should be done only after ensuring the safety of the employees.
4. D. Fail-safe locks are designed to protect employees in case of power loss because they allow employees to exit the facility. If doors are electrically powered, an unlocked (or disengaged) state allows employees to exit and not be locked in. All other answers are incorrect because they would result in employees being locked in. This could have tragic results.
5. D. Halon is a gas that is an effective fire suppressant. It was widely used because it did not leave liquid or solid residue and did not damage computer equipment. The Montreal Protocol of 1987 worked to ban halon in certain countries because it was known to damage the ozone layer. New installations of suppression equipment must deploy alternative fire-suppression methods. FM-200 is the most popular of its replacements.
6. C. The National Institute of Standards and Technologies (NIST) states that for effective perimeter control, buildings should be illuminated 8 feet high, with 2 foot-candles of illumination.
7. B. Gasoline or oil fires should be suppressed by using CO2, soda acid, or halon replacement such as FM-200. Water (answer A) is used for paper or wood fires, dry powder (answer C) is used for metal fires, and cleaning fluid (answer D) is flammable and should not be used on any fire.
8. C. A pre-action fire sprinkler system is a combination system. Pipes are initially dry and do not fill with water until a predetermined temperature is reached. Even then, the system will not activate until a secondary mechanism triggers. Answers A, B, and D are incorrect because they do not require a secondary mechanism to trigger.
9. B. Cipher locks use keypads. All the other answers list preset key locks.
10. C. A brownout is an extended period of low voltage. Answer A is incorrect; a fault is a short period of power loss. Answer B is incorrect; a blackout is a complete loss of power. Answer D is incorrect; static electricity is caused by low humidity.
11. B. Natural reinforcement is not a component of CPTED. CPTED comprises natural access control (answer A), natural surveillance (answer C), and territorial reinforcement (answer D). CPTED is unique in that it considers the factors that facilitate crime and seeks to use the proper design of a facility to reduce the fear and incidence of crime. At the core of CPTED is the belief that physical environments can be structured in such a way as to reduce crime.
12. B. Halon is unique in that it does not work in the same way as most fire suppression agents. Halon interferes with the chemical reaction of the fire and is one reason the fire tetrahedron was created. The other answers are incorrect because water (answer C) removes one of the needed items for a fire, as does carbon dioxide (answer A). A dry pipe system (answer D) is a water suppression system design, and does not hold water continuously.
13. D. A clapper valve is found in fire suppression systems, such as a dry pipe system. It is a simple valve technology that controls the flow of water. It is not found in mantraps or locks.
14. B. A Common Access Card is an example of smart card technology. This means of access control allows for cryptographic signing and PKI, and establishes identity. Answers A, C, and D are incorrect because a CAC does not make use of RFID, magnetic strip, or copper strip technology.
15. A. The MTBF is the lifetime of a device. The MTTR is the time that would be required to correct or repair a device in the event that it fails. Answers B, C, and D are incorrect. Answer B is not the correct description. Answer C describes only part of the correct answer, as it is only an estimate of the failure rate. Answer D is not correct as these values are not affected by natural disasters one way or the other.
Suggested Reading and Resources
Fire safety and equipment information: www.nfpa.org/safety-information/for-consumers/fire-and-safety-equipment
Bollards and other premises-security controls: en.wikipedia.org/wiki/Bollard
Halon alternatives: www.halcyon.com/NAFED/HTML/Halonalt.html
Biometric systems used by U.S. Homeland Security: www.biometrics.gov/ReferenceRoom/FederalPrograms.aspx
Alarm annunciator systems: www.dartelectronicsinc.com/viewtopic.php?f=2&t=6
Perimeter fence design: www.doityourself.com/stry/chainlinkfaq
Fence standards: www.astm.org/Standards/F1553.htm
Gate specifications: www.astm.org/Standards/F2200.htm
Information on RFID technology: www.rfidjournal.com
Lock picking: www.digitaltrash.org/defcon/
Fire suppression methods: www.nbcert.org/firesuppression.htm
Alarm specifications: www.sdmmag.com/articles/85224-horns-strobes-clarifying-code-requirements
CPTED Specifications: www.cptedsecurity.com/cpted_design_guidelines.htm