Chapter 1
Security and Risk Management
This chapter covers the following topics:
Security Terms: Concepts discussed include confidentiality, integrity, and availability (CIA); auditing and accounting; non-repudiation; default security posture; defense in depth; abstraction; data hiding; and encryption.
Security Governance Principles: Concepts discussed include security function alignment, organizational processes, organizational roles and responsibilities, security control frameworks, and due care and due diligence.
Compliance: Concepts discussed include contractual, legal, industry standards, and regulatory compliance and privacy requirements compliance.
Legal and Regulatory Issues: Concepts discussed include computer crime concepts, major legal systems, licensing and intellectual property, cyber crimes and data breaches, import/export controls, trans-border data flow, and privacy.
Professional Ethics: Ethics discussed include (ISC)2 Code of Ethics, Computer Ethics Institute, Internet Architecture Board, and organizational code of ethics.
Security Documentation: Documentation types include policies, processes, procedures, standards, guidelines, and baselines.
Business Continuity: Concepts discussed include business continuity and disaster recovery concepts, scope and plan, and BIA development.
Personnel Security Policies and Procedures: Policies and procedures discussed include candidate screening and hiring; employment agreements and policies; onboarding and offboarding processes; vendor, consultant, and contractor agreements and controls; compliance policy requirements; privacy policy requirements, job rotation, and separation of duties.
Risk Management Concepts: Concepts discussed include asset; asset valuation; vulnerability; threat; threat agent; exploit; risk; exposure; countermeasure; risk appetite; attack; breach; risk management policy; risk management team; risk analysis team; risk assessment; implementation; control categories; control types; control assessment, monitoring, and measurement; reporting and continuous improvement; and risk frameworks.
Geographical Threats: Concepts discussed include internal versus external threats, natural threats, system threats, human threats, and politically motivated threats.
Threat Modeling: Concepts discussed include threat modeling concepts, threat modeling methodologies, identifying threats, potential attacks, and remediation technologies and processes.
Security Risks in the Supply Chain: Concepts discussed include risks associated with hardware, software, and services; third-party assessment and monitoring; minimum security requirements; and service-level requirements.
Security Awareness, Education, and Training: Concepts discussed include levels required, methods and techniques, and periodic content reviews.
The Security and Risk Management domain addresses a broad array of topics including the fundamental information security principles of confidentiality, integrity and availability, governance, legal systems, privacy, the regulatory environment, personnel security, risk management, threat modeling, business continuity, supply chain risk, and professional ethics. Out of 100% of the exam, this domain carries an average weight of 15%, which is the highest weight of all the eight domains. So, pay close attention to the many details in this chapter!
Information security governance involves the principles, frameworks, and methods that establish criteria for protecting information assets, including security awareness. Risk management allows organizations to identify, measure, and control organizational risks. Threat modeling allows organizations to identify threats and potential attacks and implement appropriate mitigations against these threats and attacks. These facets ensure that security controls that are implemented are in balance with the operations of the organization. Each organization must develop a well-rounded, customized security program that addresses the needs of the organization while ensuring that the organization exercises due care and due diligence in its security plan. Acquisitions present special risks that management must understand prior to completing acquisitions.
Security professionals must take a lead role in their organization’s security program and act as risk advisors to management. In addition, security professionals must ensure that they understand current security issues and risks, governmental and industry regulations, and security controls that can be implemented. Professional ethics for security personnel must also be understood. Security is an ever-evolving, continuous process, and security professionals must be watchful.
Business continuity and disaster recovery ensures that the organization can recover from any attack or disaster that affects operations. Using the results from the risks assessment, security professionals should ensure that the appropriate business continuity and disaster recovery plans are created, tested, and revised at appropriate intervals.
In this chapter, you will learn how to use the information security governance and risk management components to assess risks, implement controls for identified risks, monitor control effectiveness, and perform future risk assessments.
Foundation Topics
Security Terms
When implementing security and managing risk, there are several important security principles and terms that you must keep in mind: confidentiality, integrity, and availability (CIA); auditing and accounting; non-repudiation; default security posture; defense in depth; abstraction; data hiding; and encryption.
CIA
The three fundamentals of security are confidentiality, integrity, and availability (CIA), often referred to as the CIA triad. Although the CIA triad is being introduced here, each principle of the triad should be considered in every aspect of security design. The CIA triad could easily be discussed in any domain of the CISSP exam.
Most security issues result in a violation of at least one facet of the CIA triad. Understanding these three security principles will help security professionals ensure that the security controls and mechanisms implemented protect at least one of these principles.
Every security control that is put into place by an organization fulfills at least one of the security principles of the CIA triad. Understanding how to circumvent these security principles is just as important as understanding how to provide them.
A balanced security approach should be implemented to ensure that all three facets are considered when security controls are implemented. When implementing any control, you should identify the facet that the control addresses. For example, RAID addresses data availability, file hashes address data integrity, and encryption addresses data confidentiality. A balanced approach ensures that no facet of the CIA triad is ignored.
Confidentiality
To ensure confidentiality, you must prevent the disclosure of data or information to unauthorized entities. As part of confidentiality, the sensitivity level of data must be determined before putting any access controls in place. Data with a higher sensitivity level will have more access controls in place than data at a lower sensitivity level. Identification, authentication, and authorization can be used to maintain data confidentiality.
The opposite of confidentiality is disclosure. Encryption is probably the most popular example of a control that provides confidentiality.
Integrity
Integrity, the second part of the CIA triad, ensures that data and systems are protected from unauthorized modification or data corruption. The goal of integrity is to preserve consistency, specifically:
Data integrity: Implies information is known to be good, and that the information can be trusted as being complete, consistent, and accurate.
System integrity: Implies that a system will work as intended.
The opposite of integrity is corruption. Hashing can be used to prove (or disprove) data integrity.
Availability
Availability means ensuring that information, systems, and supporting infrastructure are operating and accessible when needed. The two main instances in which availability is affected are (1) when attacks are carried out that disable or cripple a system and (2) when service loss occurs during and after disasters. Each system should be assessed in terms of its criticality to organizational operations. Controls should be implemented based on each system’s criticality level.
Availability is the opposite of destruction or isolation. Fault-tolerant technologies, such as RAID or redundant sites, are examples of controls that help improve availability.
Auditing and Accounting
Auditing and accounting are two related terms in organizational security. Auditing is the internal process of providing a manual or systematic measurable technical assessment of a system or application, while accounting is the logging of access and use of information resources. Accountability is the process of tracing actions to the source. Security professionals can perform audits of user or service accounts, account usage, application usage, device usage, and even permission usage. The purpose of internal auditing is to provide accountability. Regular audits should be carried out to ensure that the security policies in place are enforced and being followed. Accounting then is used to determine what changes need to be made.
Organizations should have a designated party who is responsible for ensuring that auditing and accounting of enterprise security are being completed regularly. While computer security audits can be performed by internal personnel, such as corporate internal auditors, the audits may also need to be completed by federal or state regulators, external auditors, or consultants.
Keep in mind that in many contexts auditing can also be a third-party activity whereby an organization gains independent assurance based on evidence. With this type of auditing, the third party is usually assessing an organization’s compliance with standards or other organizations’ guidelines.
Non-Repudiation
Non-repudiation is the assurance that a sender cannot deny an action. This is usually seen in electronic communications where one party denies sending a contract, document, or email. Non-repudiation means putting measures in place that will prevent one party from denying it sent a message.
A valid digital signature gives a recipient reason to believe that the message was created by a known sender (authentication), that the sender cannot deny having sent the message (non-repudiation), and that the message was not altered in transit (integrity).
Default Security Posture
An organization’s approach to information security directly affects its access control strategy. For a default security posture, organizations must choose between the allow-by-default or deny-by-default options. As implied by its name, an allow-by-default posture permits access to any data unless a need exists to restrict access. The deny-by-default posture is much stricter because it denies any access that is not explicitly permitted. Government and military institutions and many commercial organizations use a deny-by-default posture.
Today few organizations implement either of these postures to its fullest. In most organizations, you see some mixture of the two. Although the core posture should guide the organization, organizations often find that this mixture is necessary to ensure that data is still protected while providing access to a variety of users. For example, a public website might grant all HTTP and HTTPS content, but deny all other content.
Defense in Depth
A defense-in-depth strategy refers to the practice of using multiple layers of security between data and the resources on which it resides and possible attackers. The first layer of a good defense-in-depth strategy is appropriate access control strategies. Access controls exist in all areas of an information systems (IS) infrastructure (more commonly referred to as an IT infrastructure), but a defense-in-depth strategy goes beyond access control. It also considers software development security, asset security, and all other domains of the CISSP realm.
Figure 1-1 shows an example of the defense-in-depth concept.

Abstraction
Abstraction is the process of taking away or removing characteristics from something to reduce it to a set of essential characteristics. Abstraction usually results in named entities with a set of characteristics that help in their identification. However, unnecessary characteristics are hidden. Abstraction is related to both encapsulation and data hiding.
Data Hiding
Data hiding is the principle whereby data about a known entity is not accessible to certain processes or users. For example, a database may collect information about its users, including their name, job title, email address, and phone number, that you want all users to be able to access. However, you may not want the public to be able to access their Social Security numbers, birthdate, or other protected personally identifiable information (PII). Encapsulation is a popular technique that provides data hiding.
Encryption
Encryption is the process of converting information or data into a code, especially to prevent unauthorized access. Data can be encrypted while at rest, in transit, and in use. Encryption is covered in more detail in Chapter 3, “Security Architecture and Engineering.”
Security Governance Principles
Corporate governance is the system by which organizations are directed and controlled. Governance structures and principles identify the distribution of rights and responsibilities. As applied to information cybersecurity, governance is the responsibility of leadership to
Determine and articulate the organization’s desired state of security
Provide the strategic direction, resources, funding, and support to ensure that the desired state of security can be achieved and sustained
Maintain responsibility and accountability through oversight
Organizations should use security governance principles to ensure that all organizational assets are protected. Organizations often use best practices that are established by organizations, such as National Institute of Standards and Technology (NIST) or Information Technology Infrastructure Library (ITIL). Because information technology is an operational necessity, management must take an active role in any security governance initiative.
Security governance assigns rights and uses an accountability framework to ensure appropriate decision making. It must ensure that the framework used is aligned with the business strategy. Security governance gives directions, establishes standards and principles, and prioritizes investments. It is the responsibility of the organization’s board of directors and executive management.
The IT Governance Institute (ITGI) issued the Board Briefing on IT Governance, 2nd Edition, which is available from the Information Systems Audit and Control Association’s (ISACA’s) website at www.isaca.org/Knowledge-Center/Research/ResearchDeliverables/Pages/Board-Briefing-on-IT-Governance-2nd-Edition.aspx. It provides the following definition for IT governance:
IT governance is the responsibility of the board of directors and executive management. It is an integral part of enterprise governance and consists of the leadership and organizational structures and processes that ensure that the organization’s IT sustains and extends the organization’s strategies and objectives.
According to this publication, IT governance covers strategic alignment, value delivery, risk management, resource management, and performance measurement. It includes checklists and tools to help an organization’s board of directors and executive management ensure IT governance.
Security governance principles include security function alignment, organizational processes, organizational roles and responsibilities, security control frameworks, and due care and due diligence.
Security Function Alignment
The security function must align with the business strategy, goals, mission, and objectives of the organization. Every information security decision must be informed by organizational goals and be in alignment with strategic objectives. When strategically aligned, security functions as a business enabler that adds value.
It is critical that organizations implement a threat modeling program (which we will discuss later in this chapter), continually reassess the threat environment, including new adversaries, and proactively adapt their information security program.
Organizational Strategies and Goals
The organizational security strategy and goals must be documented. Security management protects organizational assets using physical, administrative, and logical controls. While management is responsible for the development of the organization’s security strategy, security professionals within the organization are responsible for carrying it out. Therefore, security professionals should be involved in the development of the organizational security strategy and goals.
A strategy is a plan of action or a policy designed to achieve a major or overall aim. Goals are the desired results from the security plan. A security management team must address all areas of security, including protecting personnel, physical assets, and data, when designing the organization’s security strategy and goals. The strategy and goals should change over time as the organization grows and changes and the world changes, too. Years ago, organizations did not need to worry about their data being stolen over the Internet. But today, the Internet is one of the most popular mediums used to illegally obtain confidential organizational data.
Organizational Mission and Objectives
The organization’s mission and objectives should already be adopted and established by organizational management or the board of directors. An organization’s security management team must ensure that any security strategy and goals fit with the mission and objectives of the organization. Information and the assets that support the organization’s mission must be protected as part of the security strategy and goals.
The appropriate policies, procedures, standards, and guidelines must be implemented to ensure that organizational risk is kept within acceptable levels. Security professionals will advise management on organizational risks. Organizational risk is also affected by government regulations, which may force an organization to implement certain measures that they had not planned. Weighing the risks to the organization and choosing whether to implement security controls are ultimately the job of senior management.
Security management ensures that risks are identified and adequate controls are implemented to mitigate the risks, all within the context of supporting the organizational mission and objectives.
Business Case
A business case is a formal document that gives the reasons behind an organizational project or initiative and usually includes financial justification for a project or an initiative. The security management team should develop a formal business case for the overall security assessment of an organization. Once the organization’s security assessment is complete and its business case has been created, management will decide how to proceed.
At that point, other business cases for individual security projects will need to be developed. For example, if management wants the security management team to ensure that the organization’s internal network is protected from attacks, the security management team may draft a business case that explains the devices that need to be implemented to meet this goal. This business case may include firewalls, intrusion detection systems (IDSs), access control lists (ACLs), and other devices, and it should detail how the devices will provide protection.
Security Budget, Metrics, and Effectiveness
The chief security officer (CSO) or other designated high-level manager prepares the organization’s security budget, determines the security metrics, and reports on the effectiveness of the security program. This officer must work with other subject matter experts (SMEs) to ensure that all security costs are accounted for, including development, testing, implementation, maintenance, personnel, and equipment. The budgeting process requires an examination of all risks and ensures that security projects with this best cost/benefit ratio are implemented. Projects that take longer than 12–18 months are long-term and strategic and require more resources and funding to complete.
Security metrics provide information on both short- and long-term trends. By collecting these metrics and comparing them on a day-to-day basis, a security professional can determine the daily workload. When the metrics are compared over a longer period of time, the trends that occur can help to shape future security projects and budgets. Procedures should state who will collect the metrics, which metrics will be collected, when the metrics will be collected, and what the thresholds are that will trigger corrective actions. Security professionals should consult with the information security governance frameworks listed later in this chapter, particularly ISO/IEC 27004:2016 and NIST 800-55 Rev. 1, for help in establishing metrics guidelines and procedures.
Although the security team should analyze metrics on a daily basis, periodic analysis of the metrics by a third party can ensure the integrity and effectiveness of the security metrics by verifying the results of the internal team. Data from the third party should be used to improve the security program and security metrics process.
Resources
If the appropriate resources are not allocated to an organization’s security function, even the best-laid security plans will fail. These resources include, but are not limited to, security personnel, devices, and controls. As discussed in the “Security Budget, Metrics, and Effectiveness” section, resource allocation is limited based on the security budget. Risk analysis helps an organization determine which security resources are most important and which are not necessary. But keep in mind that as the security function of the organization is constantly changing, so should the resource allocation to the security function change as needed. What may have been cost-prohibitive last year may become a necessity this year, and what may have been a necessity a few years ago may now be considered outdated and may not provide the level of protection you need. For this reason, security professionals should continuously revisit the risk analysis process to determine what improvements can be made in the security function of an organization.
Security professionals should also understand what personnel resources are needed to support any security function. This may include, but is not limited to, data owners, system administrators, network administrators, IT technicians, software developers, law enforcement, and accounting officers. The size of the organization will influence the availability of resources to any organizational security function. Security professionals should work to build relationships with all personnel resources to ensure a successful security program.
Organizational Processes
To understand organizational processes, organizations must determine the work needed to accomplish a goal, assign those tasks to individuals, and arrange those individuals in a decision-making organizational structure. The end result of documenting the processes is an organization that consists of unified parts acting in harmony to execute tasks to achieve goals. But all organizations go through periods of growth and decline. Often during these periods, organizations will go through acquisitions, mergers, and divestitures. In addition, governance committees will be formed to help improve the organization and its processes.
Acquisitions and Divestitures
An acquisition occurs when one organization purchases another, and a merger occurs when two organizations decide to join together to become one organization. In both cases, they can be considered friendly or hostile.
Security professionals should bring several considerations to the attention of management to ensure that organizational security does not suffer as a result of an acquisition or a merger. The other organization may have new data and technology types that may need more protection than is currently provided. For example, the acquired organization may allow personnel to bring their own devices and use them on the network. While a knee-jerk reaction may be to just implement the same policy as in the current organization, security professionals should assess why the personal devices are allowed and how ingrained this capability is in the organization’s culture.
Another acquisition or merger consideration for security professionals is that the staff at the other organization may not have the appropriate security awareness training. If training has not been given, it may be imperative that security awareness training be deployed as soon as possible to the staff of the acquired company.
When acquisitions or mergers occur, usually a percentage of personnel are not retained. Security professionals should understand any threats from former personnel and any new threats that may arise due to the acquisition or merger. Security professionals must understand these threats so they can develop plans to mitigate the threats.
As part of a merger or acquisition, technology is usually integrated. This integration can present vulnerabilities that the organization would not have otherwise faced. For example, if an acquired company maintains a legacy system because personnel need it, the acquiring organization may need to take measures to protect the legacy system or to deploy a new system that will replace it.
Finally, with an acquisition or a merger, new laws, regulations, and standards may need to be implemented across the entire new organization. Relationships with business partners, vendors, and other entities also need to be reviewed. Security professionals must ensure that they properly advise management about any security issues that may arise.
A divestiture, which is the opposite of an acquisition, occurs when part of an organization is sold off or separated from the original organization. A divestiture impacts personnel because usually a portion of the personnel goes with the divestiture.
As with acquisitions, with divestitures, security professionals should bring certain considerations to the attention of management to ensure that organizational security does not suffer. Data leakage may occur as a result of exiting personnel. Personnel who have been laid off as a result of the divestiture are of particular worry. Tied to this is the fact that the exiting personnel have access rights to organizational assets. These access rights must be removed at the appropriate time, and protocols and ports that are no longer needed should be removed or closed.
Security professionals should also consider where the different security assets and controls will end up. If security assets are part of the divestiture, steps should be taken to ensure that replacements are implemented prior to the divestiture, if needed. In addition, policies and procedures should be reviewed to ensure that they reflect the new organization’s needs.
Whether an organization is going through an acquisition, a merger, or a divestiture, it is vital that security professionals be proactive to protect the organization.
Governance Committees
A governance committee recruits and recommends members of an organization’s governing board (e.g., board of directors or trustees). The governance committee should be encouraged to include among the board members individuals who understand information security and risks.
A board committee (generally the audit or enterprise risk management committee) is generally tasked with the oversight of information security. Management-level security professionals should make themselves available for briefings as well as establish a direct line of communication with the designated committee.
Organizational Roles and Responsibilities
Although all organizations have layers of responsibility within the organization, cybersecurity is generally considered the responsibility of everyone in the organization. This section covers the responsibilities of the different roles within an organization.
Board of Directors
An organization’s board of directors includes individuals who are nominated by a governance committee and elected by shareholders to ensure that the organization is run properly. The loyalty of the board of directors should be to the shareholders, not high-level management. Members of the board of directors should maintain their independence from all organizational personnel, especially if the Sarbanes-Oxley (SOX) Act or Gramm-Leach-Bliley Act (GLBA) applies to the organization.
Note
All laws that are pertinent to the CISSP exam are discussed later in this chapter. Keep in mind that for testing purposes, security professionals only need to understand the types of organizations and data that these laws affect.
Senior officials, including the board of directors and senior management, must perform their duties with the care that ordinary, prudent people would exercise in similar circumstances. This is known as the prudent-man rule. Due care and due diligence, discussed later in this chapter, also affect members of the board of directors and high-level management.
Management
High-level management has the ultimate responsibility for preserving and protecting organizational data. High-level management includes the CEO, CFO, CIO, CPO, and CSO. Other management levels, including business unit managers and business operations managers, have security responsibilities as well.
The chief executive officer (CEO) is the highest managing officer in any organization and reports directly to the shareholders. The CEO must ensure that an organization grows and prospers.
The chief financial officer (CFO) is the officer responsible for all financial aspects of an organization. Although structurally the CFO might report directly to the CEO, the CFO must also provide financial data for the shareholders and government entities.
The chief information officer (CIO) is the officer responsible for all information systems and technology used in the organization and reports directly to the CEO or CFO. The CIO usually drives the effort to protect company assets, including any organizational security program.
The chief privacy officer (CPO) is the officer responsible for private information and usually reports directly to the CIO. As a newer position, this role is still considered optional but is becoming increasingly popular, especially in organizations that handle lots of private information, including medical institutions, insurance companies, and financial institutions.
The chief security officer (CSO) is the officer who leads any security effort and reports directly to the CEO. Although this role is considered optional, this role must solely be focused on security matters. Its independence from all other roles must be maintained to ensure that the organization’s security is always the focus of the CSO. This role implements and manages all aspects of security, including risk analysis, security policies and procedures, incident handling, security awareness training, and emerging technologies.
Security professionals should ensure that all risks are communicated to executive management and the board of directors, if necessary. Executive management should maintain a balance between acceptable risk and business operations. While executive management is not concerned with the details of any security implementations, the costs or benefits of any security implementation and any residual risk after such implementation will be vital in ensuring their buy-in to the implementation.
Business unit managers provide departmental information to ensure that appropriate controls are in place for departmental data. Often business unit managers are classified as the data owner for all departmental data. Some business unit managers have security duties. For example, the business operations department manager would be best suited to oversee the security policy development.
Audit Committee
An audit committee evaluates an organization’s financial reporting mechanism to ensure that financial data is accurate. This committee performs an internal audit and engages independent auditors as needed. Members of this committee must obtain appropriate education on a regular basis to ensure that they can oversee financial reporting and enforce accountability in the financial processes.
Data Owner
The main responsibility of the data or information owner is to determine the classification level of the information he owns and to protect the data for which he is responsible. This role approves or denies access rights to the data. However, the data owner usually does not handle the implementation of the data access controls.
The data owner role is usually filled by an individual who understands the data best through membership in a particular business unit. Each business unit should have a data owner. For example, a human resources department employee better understands the human resources data than an accounting department employee.
Data Custodian
The data custodian implements the information classification and controls after they are determined by the data owner. Although the data owner is usually an individual who understands the data, the data custodian does not need any knowledge of the data beyond its classification levels. Although a human resources manager should be the data owner for the human resources data, an IT department member could act as the data custodian for the data.
System Owner
A system owner owns one or more systems and must ensure that the appropriate controls are in place on those systems. Although a system has a single system owner, multiple data owners can be responsible for the information on the system. Therefore, system owners must be able to manage the needs of multiple data owners and implement the appropriate procedures to ensure that the data is secured.
System Administrator
A system administrator performs the day-to-day administration of one or more systems. These day-to-day duties include adding and removing system users and installing system software.
Security Administrator
A security administrator maintains security devices and software, including firewalls, antivirus software, and so on. The main focus of the security administrator is security, whereas the main focus of a system administrator is the system availability and the main focus of the network administrator is network availability. The security administrator reviews all security audit data.
Security Analyst
A security analyst analyzes the security needs of the organization and develops the internal information security governance documents, including policies, standards, and guidelines. The role focuses on the design of security, not its implementation.
Application Owner
An application owner determines the personnel who can access an application. Because most applications are owned by a single department, business department managers usually fill this role. However, the application owner does not necessarily perform the day-to-day administration of the application. This responsibility can be delegated to a member of the IT staff because of the technical skills needed.
Supervisor
A supervisor manages a group of users and any assets owned by this group. Supervisors must immediately communicate any personnel role changes that affect security to the security administrator.
User
A user is any person who accesses data to perform their job duties. Users should understand any security procedures and policies for the data to which they have access. Supervisors are responsible for ensuring that users have the appropriate access rights.
Auditor
An auditor monitors user activities to ensure that the appropriate controls are in place. Auditors need access to all audit and event logs to verify compliance with security policies. Both internal and external auditors can be used.
Security Control Frameworks

Many organizations have developed security management frameworks and methodologies to help guide security professionals. These frameworks and methodologies include security program development standards, enterprise and security architect development frameworks, security controls development methods, corporate governance methods, and process management methods. Frameworks, standards, and methodologies are often discussed together because they are related. Standards are accepted as best practices, whereas frameworks are practices that are generally employed. Standards are specific, while frameworks are general. Methodologies are a system of practices, techniques, procedures, and rules used by those who work in a discipline. In this section we will cover all three as they relate to security controls.
This section discusses the following frameworks and methodologies and explains where they are used:
ISO/IEC 27000 Series
Zachman Framework
TOGAF
DoDAF
MODAF
SABSA
COBIT
NIST 800 Series
HITRUST CSF
CIS Critical Security Controls
COSO
OCTAVE
ITIL
Six Sigma
CMMI
CRAMM
Top-down versus bottom-up approach
Security program life cycle
Note
Organizations should select the framework, standard, and/or methodology that represents the organization in the most useful manner, based on the needs of the stakeholders.
ISO/IEC 27000 Series
The International Organization for Standardization (ISO), often incorrectly referred to as the International Standards Organization, joined with the International Electrotechnical Commission (IEC) to standardize the British Standard 7799 (BS7799) to a new global standard that is now referred to as ISO/IEC 27000 Series. While technically not a framework, ISO 27000 is a security program development standard on how to develop and maintain an information security management system (ISMS).
The 27000 Series includes a list of standards, each of which addresses a particular aspect of ISMSs. These standards are either published or in development. The following standards are included as part of the ISO/IEC 27000 Series at the time of this writing:
27000:2018—Published overview of ISMSs and vocabulary
27001:2013—Published ISMS requirements
27002:2013—Published code of practice for information security controls
27003:2017—Published guidance on the requirements for an ISMS
27004:2016—Published ISMS monitoring, measurement, analysis, and evaluation guidelines
27005:2011—Published information security risk management guidelines
27006:2015—Published requirements for bodies providing audit and certification of ISMS
27007:2017—Published ISMS auditing guidelines
27008:2011—Published guidelines for auditors on information security controls
27009:2016—Published sector-specific application of ISO/IEC 27001 guidelines
27010:2015—Published information security management for inter-sector and inter-organizational communications guidelines
27011:2016—Published telecommunications organizations information security management guidelines
27013:2015—Published integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1 guidance
27014:2013—Published information security governance guidelines
27016:2014—Published ISMS organizational economics guidelines
27017:2015—Published code of practice for information security controls based on ISO/IEC 27002 for cloud services
27018:2014—Published code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
27019:2017—Published information security controls for the energy utility industry guidelines
27021:2017—Published competence requirements for information security management systems professionals
27023:2015—Published mapping the revised editions of ISO/IEC 27001 and ISO/IEC 27002
27031:2011—Published information and communication technology readiness for business continuity guidelines
27032:2012—Published cybersecurity guidelines
27033-1:2015—Published network security overview and concepts
27033-2:2012—Published network security design and implementation guidelines
27033-3:2010—Published network security threats, design techniques, and control issues guidelines
27033-4:2014—Published securing communications between networks using security gateways
27033-5:2013—Published securing communications across networks using virtual private networks (VPNs)
27033-6:2016—Published securing wireless IP network access
27034-1:2011—Published application security overview and concepts
27034-2:2015—Published application security organization normative framework guidelines
27034-5:2017—Published application security protocols and controls data structure guidelines
27034-6:2016—Published case studies for application security
27035-1:2016—Published information security incident management principles
27035-2:2016—Published information security incident response readiness guidelines
27036-1:2014—Published information security for supplier relationships overview and concepts
27036-2:2014—Published information security for supplier relationships common requirements guidelines
27036-3:2013—Published information and communication technology (ICT) supply chain security guidelines
27036-4:2016—Published guidelines for security of cloud services
27037:2012—Published digital evidence identification, collection, acquisition, and preservation guidelines
27038:2014—Published information security digital redaction specification
27039:2015—Published IDS selection, deployment, and operations guidelines
27040:2015—Published storage security guidelines
27041:2015—Published guidance on assuring suitability and adequacy of incident investigative method
27042:2015—Published digital evidence analysis and interpretation guidelines
27043:2015—Published incident investigation principles and processes
27050-1:2016—Published electronic discovery (eDiscovery) overview and concepts
27050-3:2017—Published code of practice for electronic discovery
27799:2016—Published information security in health organizations guidelines
These standards are developed by the ISO/IEC bodies, but certification or conformity assessment is provided by third parties.
Note
The numbers after the colon for each standard stand for the year that the standard was published. You can find more information regarding ISO standards at https://www.iso.org. All ISO standards are copyrighted and must be purchased to obtain detailed information in the standards.
Zachman Framework
The Zachman Framework, an enterprise architecture framework, is a two-dimensional classification system based on six communication questions (What, Where, When, Why, Who, and How) that intersect with different perspectives (Executive, Business Management, Architect, Engineer, Technician, and Enterprise). This system allows analysis of an organization to be presented to different groups in the organization in ways that relate to the groups’ responsibilities. Although this framework is not security oriented, using this framework helps you to relay information for personnel in a language and format that is most useful to them.
The Open Group Architecture Framework (TOGAF)
TOGAF, another enterprise architecture framework, helps organizations design, plan, implement, and govern an enterprise information architecture. TOGAF is based on four interrelated domains: technology, applications, data, and business.
Department of Defense Architecture Framework (DoDAF)
DoDAF is an architecture framework that organizes a set of products under eight views: all viewpoint (required) (AV), capability viewpoint (CV), data and information viewpoint (DIV), operation viewpoint (OV), project viewpoint (PV), services viewpoint (SvcV), standards viewpoint (STDV), and systems viewpoint (SV). It is used to ensure that new DoD technologies integrate properly with the current infrastructures.
British Ministry of Defence Architecture Framework (MODAF)
MODAF is an architecture framework that divides information into seven viewpoints: strategic viewpoint (StV), operational viewpoint (OV), service-oriented viewpoint (SOV), systems viewpoint (SV), acquisition viewpoint (AcV), technical viewpoint (TV), and all viewpoint (AV).
Sherwood Applied Business Security Architecture (SABSA)
SABSA is an enterprise security architecture framework that is similar to the Zachman Framework. It uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). It is a risk-driven architecture. See Table 1-1.
Table 1-1 SABSA Framework Matrix
Viewpoint |
Layer |
Assets (What) |
Motivation (Why) |
Process (How) |
People (Who) |
Location (Where) |
Time (When) |
|---|---|---|---|---|---|---|---|
Business |
Contextual |
Business |
Risk model |
Process model |
Organizations and relationships |
Geography |
Time dependencies |
Architect |
Conceptual |
Business attributes profile |
Control objectives |
Security strategies and architectural layering |
Security entity model and trust framework |
Security domain model |
Security-related lifetimes and deadlines |
Designer |
Logical |
Business information model |
Security policies |
Security services |
Entity schema and privilege profiles |
Security domain definitions and associations |
Security processing cycle |
Builder |
Physical |
Business data model |
Security rules, practices, and procedures |
Security mechanism |
Users, applications, and interfaces |
Platform and network infrastructure |
Control structure execution |
Tradesman |
Component |
Detailed data structures |
Security standards |
Security tools and products |
Identities, functions, actions, and ACLs |
Processes, nodes, addresses, and protocols |
Security step timing and sequencing |
Facilities Manager |
Operational |
Operational continuity assurance |
Operation risk management |
Security service management and support |
Application and user management and support |
Site, network, and platform security |
Security operations schedule |
Control Objectives for Information and Related Technology (COBIT)
COBIT 5 is a security controls development framework that documents five principles:
Meeting stakeholder needs
Covering the enterprise end-to-end
Applying a single integrated framework
Enabling a holistic approach
Separating governance from management
These five principles drive control objectives categorized into seven enablers:
Principles, policies, and frameworks
Processes
Organizational structures
Culture, ethics, and behavior
Information
Services, infrastructure, and applications
People, skills, and competencies
It also covers the 37 governance and management processes that are needed for enterprise IT.
National Institute of Standards and Technology (NIST) Special Publication (SP) 800 Series
The NIST 800 Series is a set of documents that describe U.S. federal government computer security policies, procedures, and guidelines. While NIST publications are written to provide guidance to U.S. government agencies, other organizations can and often do use them. Each SP within the series defines a specific area. Some of the publications included as part of the NIST 800 Series at the time of this writing are as follows:
SP 800-12 Rev. 1: Introduces information security principles.
SP 800-16 Rev. 1: Describes information technology/cybersecurity role-based training for federal departments, agencies, and organizations.
SP 800-18 Rev. 1: Provides guidelines for developing security plans for federal information systems.
SP 800-30 Rev. 1: Provides guidance for conducting risk assessments of federal information systems and organizations, amplifying the guidance in SP 800-39.
SP 800-34 Rev. 1: Provides guidelines on the purpose, process, and format of information system contingency planning development.
SP 800-35: Provides assistance with selecting, implementing, and managing IT security services through the IT security services life cycle.
SP 800-36: Provides guidelines for choosing IT security products.
SP 800-37 Rev. 1: Provides guidelines for applying the risk management framework to federal information systems (Rev. 2 pending).
SP 800-39: Provides guidance for an integrated, organization-wide program for managing information security risk.
SP 800-50: Identifies the four critical steps in the IT security awareness and training life cycle: (1) awareness and training program design; (2) awareness and training material development; (3) program implementation; and (4) post-implementation. It is a companion publication to NIST SP 800-16 Rev. 1.
SP 800-53 Rev. 4: Provides a catalog of security and privacy controls for federal information systems and a process for selecting controls (Rev. 5 pending).
SP 800-53A Rev. 4: Provides a set of procedures for conducting assessments of security controls and privacy controls employed within federal information systems.
SP 800-55 Rev. 1: Provides guidance on how to use metrics to determine the adequacy of in-place security controls, policies, and procedures.
SP 800-60 Vol. 1 Rev. 1: Provides guidelines for mapping types of information and information systems to security categories.
SP 800-61 Rev. 2: Provides guidelines for incident handling.
SP 800-82 Rev. 2: Provides guidance on how to secure Industrial Control Systems (ICS), including Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCSs), and other control system configurations, such as Programmable Logic Controllers (PLCs).
SP 800-84: Provides guidance on designing, developing, conducting, and evaluating test, training, and exercise (TT&E) events.
SP 800-86: Provides guidelines for integrating forensic techniques into incident response.
SP 800-88 Rev. 1: Provides guidelines for media sanitization.
SP 800-92: Provides guidelines for computer security log management.
SP 800-101 Rev. 1: Provides guidelines on mobile device forensics.
SP 800-115: Provides guidelines for information security testing and assessment.
SP 800-122: Provides guidelines for protecting the confidentiality of PII.
SP 800-123: Provides guidelines for general server security.
SP 800-124 Rev. 1: Provides guidelines for securing mobile devices.
SP 800-137: Provides guidelines for an Information Security Continuous Monitoring (ISCM) program.
SP 800-144: Provides guidelines on security and privacy in public cloud computing.
SP 800-145: Provides the NIST definition of cloud computing.
SP 800-146: Describes cloud computing benefits and issues, presents an overview of major classes of cloud technology, and provides guidelines on how organizations should consider cloud computing.
SP 800-150: Provides guidelines for establishing and participating in cyber threat information sharing relationships.
SP 800-153: Provides guidelines for securing wireless local area networks (WLANs).
SP 800-154 (Draft): Provides guidelines on data-centric system threat modeling.
SP 800-160: Provides guidelines on system security engineering.
SP 800-161: Provides guidance to federal agencies on identifying, assessing, and mitigating information and communication technology (ICT) supply chain risks at all levels of their organizations.
SP 800-162: Defines attribute-based access control (ABAC) and its considerations.
SP 800-163: Provides guidelines on vetting the security of mobile applications.
SP 800-164: Provides guidelines on hardware-rooted security in mobile devices.
SP 800-167: Provides guidelines on application whitelisting.
SP 800-175A and B: Provide guidelines for using cryptographic standards in the federal government.
SP 800-181: Describes the National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework (NICE Framework).
SP 800-183: Describes the Internet of Things (IoT).
Note
For many of the SPs in the preceding list, you will simply need to know that the SP exists. For others, you need to understand details about the SP. Some NIST SPs will be covered in more detail later in this chapter or in other chapters. Refer to the index in this book to determine which SPs are covered in more detail.
HITRUST CSF
HITRUST is a privately held U.S. company that works with healthcare, technology, and information security leaders to establish the Common Security Framework (CSF) that can be used by all organizations that create, access, store, or exchange sensitive and/or regulated data. It was written to address the requirements of multiple regulations and standards. Version 9.1 was released in February, 2018. It is primarily used in the healthcare industry.
This framework has 14 control categories:
0.0: Information Security Management Program
1.0: Access Control
2.0: Human Resources Security
3.0: Risk Management
4.0: Security Policy
5.0: Organization of Information Security
6.0: Compliance
7.0: Asset Management
8.0: Physical and Environmental Security
9.0: Communications and Operations Management
10.0: Information Systems Acquisition, Development, and Maintenance
11.0: Information Security Incident Management
12.0: Business Continuity Management
13.0: Privacy Practices
Within each control category, objectives are defined and assigned levels based on their compliance with documented control standards.
CIS Critical Security Controls
The Center for Internet Security (CIS) released Critical Security Controls version 7 that lists 20 CIS controls. The first 5 controls eliminate the vast majority of an organization’s vulnerabilities. Implementing all 20 controls will secure an entire organization against today’s most pervasive threats. The 20 controls are as follows:
Inventory and control of hardware assets
Inventory and control of software assets
Continuous vulnerability management
Controlled use of administrative privileges
Secure configuration for hardware and software on mobile devices, laptops, workstations, and servers
Maintenance, monitoring, and analysis of audit logs
Email and web browser protections
Malware defenses
Limitation and control of network ports, protocols, and services
Data recovery capabilities
Secure configurations for network devices, such as firewalls, routers, and switches
Boundary defense
Data protection
Controlled access based on the need to know
Wireless access control
Account monitoring and control
Implement a security awareness training program
Application software security
Incident response and management
Penetration tests and red team exercises
The CIS Critical Security Controls provide a mapping of these controls to known standards, frameworks, laws, and regulations.
Committee of Sponsoring Organizations (COSO) of the Treadway Commission Framework
COSO is a corporate governance framework that consists of five interrelated components: control environment, risk assessment, control activities, information and communication, and monitoring activities. COBIT was derived from the COSO framework. COSO is for corporate governance; COBIT is for IT governance.
Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE)
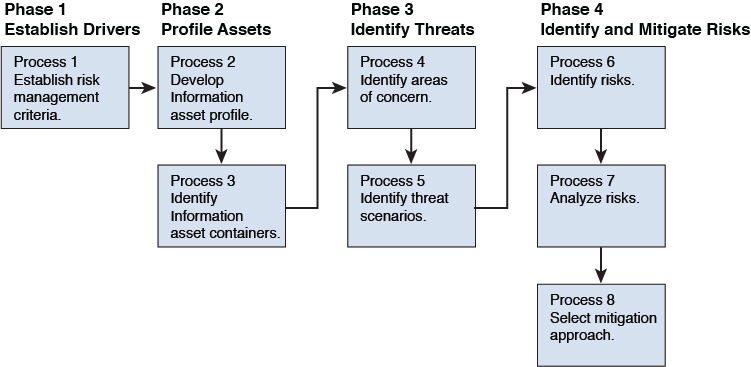
OCTAVE, which was developed by Carnegie Mellon University’s Software Engineering Institute, provides a suite of tools, techniques, and methods for risk-based information security strategic assessment and planning. Using OCTAVE, an organization implements small teams across business units and IT to work together to address the organization’s security needs. Figure 1-2 shows the phases and processes of OCTAVE Allegro, the most recent version of OCTAVE.
Information Technology Infrastructure Library (ITIL)
ITIL is a process management development standard developed by the Office of Management and Budget in OMB Circular A-130. ITIL has five core publications: ITIL Service Strategy, ITIL Service Design, ITIL Service Transition, ITIL Service Operation, and ITIL Continual Service Improvement. These five core publications contain 26 processes. Although ITIL has a security component, it is primarily concerned with managing the service-level agreements (SLAs) between an IT department or organization and its customers. As part of the OMB Circular A-130, an independent review of security controls should be performed every three years.
Table 1-2 lists the five ITIL version 3 core publications and the 26 processes within them.
Table 1-2 ITIL v3 Core Publications and Processes
ITIL Service Strategy |
ITIL Service Design |
ITIL Service Transition |
ITIL Service Operation |
ITIL Continual Service Improvement |
Strategy Management |
Design Coordination |
Transition Planning and Support |
Event Management |
Continual Service Improvement |
Service Portfolio Management |
Service Catalogue |
Change Management |
Incident Management |
|
Financial Management for IT Services |
Service Level Management |
Service Asset and Configuration Management |
Request Fulfillment |
|
Demand Management |
Availability Management |
Release and Deployment Management |
Problem Management |
|
Business Relationship Management |
Capacity Management |
Service Validation and Testing |
Access Management |
|
|
IT Service Continuity Management |
Change Evaluation |
|
|
|
Information Security Management System |
Knowledge Management |
|
|
|
Supplier Management |
|
|
|
Six Sigma
Six Sigma is a process improvement standard that includes two project methodologies that were inspired by Deming’s Plan–Do–Check–Act cycle. The DMAIC methodology includes Define, Measure, Analyze, Improve, and Control. The DMADV methodology includes Define, Measure, Analyze, Design, and Verify. Six Sigma was designed to identify and remove defects in the manufacturing process, but can be applied to many business functions, including security.
Note
The Deming cycle is discussed in more detail later in this chapter.
Figures 1-3 and 1-4 show both of the Six Sigma methodologies.


Capability Maturity Model Integration (CMMI)
Capability Maturity Model Integration (CMMI) is a process improvement approach that addresses three areas of interest: product and service development (CMMI for development), service establishment and management (CMMI for services), and product service and acquisition (CMMI for acquisitions). CMMI has five levels of maturity for processes: Level 1 Initial, Level 2 Managed, Level 3 Defined, Level 4 Quantitatively Managed, and Level 5 Optimizing. All processes within each level of interest are assigned one of the five levels of maturity.
CCTA Risk Analysis and Management Method (CRAMM)
CRAMM is a qualitative risk analysis and management tool developed by the UK government’s Central Computer and Telecommunications Agency (CCTA). A CRAMM review includes three steps:
Identify and value assets.
Identify threats and vulnerabilities and calculate risks.
Identify and prioritize countermeasures.
Note
No organization will implement all of the aforementioned frameworks or methodologies. Security professionals should help their organization pick the framework that best fits the needs of the organization.
Top-Down Versus Bottom-Up Approach
In a top-down approach, management initiates, supports, and directs the security program. In a bottom-up approach, staff members develop a security program prior to receiving direction and support from management. A top-down approach is much more efficient than a bottom-up approach because management’s support is one of the most important components of a security program.
Security Program Life Cycle
Any security program has a continuous life cycle and should be assessed and improved constantly. The security program life cycle includes the following steps:
Plan and Organize: Includes performing risk assessment, establishing management and steering committee, evaluating business drivers, and obtaining management approval.
Implement: Includes identifying and managing assets, managing risk, managing identity and access control, training on security and awareness, implementing solutions, assigning roles, and establishing goals.
Operate and Maintain: Includes performing audits, carrying out tasks, and managing SLAs.
Monitor and Evaluate: Includes reviewing auditing and logs, evaluating security goals, and developing improvement plans for integration into the Plan and Organize step (step 1).
Figure 1-5 shows a diagram of the security program life cycle.


Due Care and Due Diligence
Due care and due diligence are two related terms that organizations must understand as they relate to the security of the organization and its assets and data.
Due care is the standard of care that a prudent person would have exercised under the same or similar conditions. In the context of security, due care means that an organization takes reasonable measures to protect its information assets, systems, and supporting infrastructure. This includes making sure that the correct policies, procedures, and standards are in place and being followed.
Due care is all about action. Organizations must institute the appropriate protections and procedures for all organizational assets, especially intellectual property. In due care, failure to meet minimum standards and practices is considered negligent. If an organization does not take actions that a prudent person would have taken under similar circumstances, the organization is negligent.
Due diligence is the act of investigation and assessment. Organizations must institute the appropriate procedures to determine any risks to organizational assets. Due diligence then provides the information necessary to ensure that the organization practices due care. Without adequate due diligence, due care cannot occur.
Due diligence includes employee background checks, business partner credit checks, system security assessments, risk assessments, penetration tests, and disaster recovery planning and testing. NIST SP 800-53 Rev. 4, discussed earlier in this chapter, in the “Security Control Frameworks” section, provides guidance for implementing security controls that will help with due diligence.
Both due care and due diligence have bearing on the security governance and risk management process. As you can see, due diligence and due care are codependent. When due diligence occurs, organizations will recognize areas of risk. Examples include an organization determining that regular personnel do not understand basic security issues, that printed documentation is not being discarded appropriately, and that employees are accessing files to which they should not have access. When due care occurs, organizations take the areas of identified risk and implement plans to protect against the risks. For the identified due diligence examples, due care examples to implement include providing personnel security awareness training, putting procedures into place for proper destruction of printed documentation, and implementing appropriate access controls for all files.
Compliance
Compliance involves being in alignment with standards, guidelines, regulations, and/or legislation. An organization must comply with governmental laws and regulations. However, compliance with standards bodies and industry associations can be considered optional in some cases, while it is mandatory for contractual obligations (like Payment Card Industry Data Security Standard) and certification requirements (like ISO 27001).
All security professionals must understand security and privacy standards, guidelines, regulations, and laws. Usually these are industry specific, meaning that the standards, guidelines, regulations, and laws are based on the type of business the organization is involved in. A great example is the healthcare industry. Due to the Health Insurance Portability and Accountability Act (HIPAA), healthcare organizations must follow regulations regarding how to collect, use, store, and protect PII. Often consideration must be given to local, regional, state, federal, and international governments and bodies.
Organizations and the security professionals that they employ must determine which rules they must comply with. An organization should adopt the most strict rules to which it must comply. If rules conflict with each other, organizations must take the time to determine which rule should take precedence. This decision could be based on data type, industry type, data collection method, data usage, or individual residence of those on whom they collect PII.
Any discussion of compliance would be incomplete without a discussion of a risk management approach referred to as governance, risk management, and compliance (GRC). Governance covers core organizational activities, authority within the organization, organizational accountability, and performance measurement. Risk management identifies, analyzes, evaluates, and monitors risk. Compliance ensures that organizational activities comply with established rules. Each of the three separate objectives accepts input from and supplies input to the other objectives. The GRC relationship is shown in Figure 1-6.

As part of the discussion of compliance, security professionals must understand legislative and regulatory compliance and privacy requirements.
Contractual, Legal, Industry Standards, and Regulatory Compliance
No organization operates within a bubble. All organizations are affected by laws, regulations, and compliance requirements. Organizations must ensure that they comply with all contracts, laws, industry standards, and regulations. Security professionals must understand the laws and regulations of the country or countries they are working in and the industry within which they operate. In many cases, laws and regulations are written in a manner whereby specific actions must be taken. However, there are cases where laws and regulations leave it up to the organization to determine how to comply.
The United States and European Union both have established laws and regulations that affect organizations that do business within their area of governance. While security professionals should strive to understand laws and regulations, security professionals may not have the level of knowledge and background to fully interpret these laws and regulations to protect their organization. In these cases, security professionals should work with legal representation regarding legislative or regulatory compliance.
Note
Specific laws and regulations are discussed later, in the “Privacy” subsection of the “Legal and Regulatory Issues” section of this chapter.
Privacy Requirements Compliance
Privacy requirements compliance is primarily concerned with the confidentiality of data, particularly PII. PII is increasingly coming under attack in our modern world. Almost daily, a new company, organization, or even government entity announces that PII on customers, employees, or even government agents has been compromised. These compromises damage the reputation of the organization and also can lead to liability for damages.
Both the U.S. government and the European Union have enacted laws, regulations, and directives on the collection, handling, storage, and transmission of PII, with the goal of protecting the disclosure of this data to unauthorized entities.
Security professionals are responsible for ensuring that management understands the requirements and the possible repercussions of noncompliance. Staying up to date on the latest developments regarding PII is vital.
Legal and Regulatory Issues
The legal and regulatory issues that affect organizations today have vastly expanded with the usage of computers and networks. Gone are the days when physical security of data was the only worry. With technological advances come increasing avenues of attack. This section discusses computer crime concepts, major legal systems, licensing and intellectual property, cyber crimes and data breaches, import/export controls, trans-border data flow, and privacy.
Computer Crime Concepts
Computer crimes today are usually made possible by a victim’s carelessness. If a computer crime has occurred, proving criminal intent and causation is often difficult. Investigating and prosecuting computer crimes is made even more difficult because evidence is mostly intangible. Further affecting computer crime investigation is the fact that obtaining a trail of evidence of activities performed on a computer is hard.

Because of these computer crime issues, it is important that security professionals understand the following computer crime concepts:
Computer-assisted crime
Computer-targeted crime
Incidental computer crime
Computer prevalence crime
Hackers versus crackers
Computer-Assisted Crime
A computer-assisted crime occurs when a computer is used as a tool to help commit a crime. This type of crime could be carried out without a computer but uses the computer to make committing the crime easier. Think of it this way: Criminals can steal confidential organizational data in many different manners. This crime is possible without a computer. But when criminals use computers to help them steal confidential organizational data, then a computer-assisted crime has occurred.
Computer-Targeted Crime
A computer-targeted crime occurs when a computer is the victim of an attack that’s sole purpose is to harm the computer and its owner. This type of crime could not be carried out without a computer being used. Computer crimes that fit into this category include denial-of-service (DoS) and buffer overflow attacks.
Incidental Computer Crime
An incidental computer crime occurs when a computer is involved in a computer crime without being the victim of the attack or the attacker. A computer being used as a zombie in a botnet is part of an incidental computer crime.
Computer Prevalence Crime
A computer prevalence crime occurs due to the fact that computers are so widely used in today’s world. This type of crime occurs only because computers exist. Software piracy is an example of this type of crime.
Hackers Versus Crackers
Hacker and cracker are two terms that are often used interchangeably in media but do not actually have the same meaning. Hackers are individuals who attempt to break into secure systems to obtain knowledge about the systems and possibly use that knowledge to carry out pranks or commit crimes. Crackers, on the other hand, are individuals who attempt to break into secure systems without using the knowledge gained for any nefarious purposes.
In the security world, the terms white hat, gray hat, and black hat are more easily understood and less often confused than the terms hackers and crackers. A white hat does not have any malicious intent. A black hat has malicious intent. A gray hat is considered somewhere in the middle of the two. A gray hat will break into a system, notify the administrator of the security hole, and offer to fix the security issues for a fee.
Computer Crime Examples
Now that you understand the different categories of computer crime and the individuals that perpetuate the crimes, it is appropriate to give some examples of computer crimes that are prevalent today.
Through social engineering tactics, hackers often scare users/victims into installing fake or rogue antivirus software on their computers. Pop-up boxes tell the user that a virus infection has occurred and that by clicking the button in the pop-up box, the user can purchase and install the antivirus software to remove the virus. If the user clicks the button, he or she unknowingly infects the computer with malware. Web browsers today deploy mechanisms that allow users to block pop-up messages. However, this has the drawback of sometimes preventing wanted pop-ups. Simply configuring an exception for the valid pop-up sites is better than disabling a pop-up blocker completely.
Ransomware is a special category of software that attempts to extort money out of possible victims. One category of ransomware encrypts the user’s data until a payment is made to the attacker. Another category reports to the user that his or her computer has been used for illegal activities and that a fine must be paid to prevent prosecution. But in this case, the “fine” is paid to the attacker, posing as a government official or law enforcement agency. In many cases, malware continues to operate in the background even after the ransomware has been removed. This malware often is used to commit further financial fraud on the victim.
Scareware is a category of software that locks up a computer and warns the user that a violation of federal or international law has occurred. As part of this attack, the banner or browser redirects the user to a child pornography website. The attacker claims to be recording the user and his or her actions. The victim must pay a fine to have control of the computer returned. The line between scareware and ransomware is so fine that it is often hard to distinguish between the two.
These are only a few examples of computer attacks, and attackers are coming up with new methods every day. It is a security professional’s duty to stay aware of the newest trends in this area. If a new method of attack is discovered, security professionals should take measures to communicate with users regarding the new attack as soon as possible. In addition, security professionals should ensure that security awareness training is updated to include any new attack methods. End-user education is one of the best ways to mitigate these attacks.
Major Legal Systems
Security professionals must understand the different legal systems that are used throughout the world and the components that make up the systems.

These systems include the following:
Civil code law
Common law
Criminal law
Civil/tort law
Administrative/regulatory law
Customary law
Religious law
Mixed law
Civil Code Law
Civil code law, developed in Europe, is based on written laws. It is a rule-based law and does not rely on precedence in any way. The most common legal system in the world, civil code law does not require lower courts to follow higher court decisions.
Note
Do not confuse the civil code law of Europe with the United States civil/tort laws.
Common Law
Common law, developed in England, is based on customs and precedent because no written laws were available. Common law reflects on the morals of the people and relies heavily on precedence. In this system, the lower court must follow any precedents that exist due to higher court decisions. This type of law is still in use today in the United Kingdom, the United States, Australia, and Canada.
Today, common law uses a jury-based system, which can be waived so the case is decided by a judge. Common law is divided into three systems: criminal law, civil/tort law, and administrative/regulatory law.
Criminal Law
Criminal law covers any actions that are considered harmful to others. It deals with conduct that violates public protection laws. But the prosecution must provide guilt beyond a reasonable doubt. The plaintiff is usually the civil body, such as the state or federal government, that establishes the law that is violated. In criminal law, guilty parties might be imprisoned and/or fined. Criminal law is based on common law and statutory law. Statutory law is handed down by federal, state, or local legislating bodies.
Civil/Tort Law
Civil law deals with wrongs that have been committed against an individual or organization. A defendant is liable for damages to the victim (plaintiff) if the defendant had a duty of care to the victim, breached that duty (was negligent), and was the actual cause of harm to the victim. Under civil law, the victim is entitled to seek compensatory, punitive, and statutory damages. Compensatory damages are those that compensate the victim for his losses. Punitive damages are those that are handed down by juries to punish the liable party. Statutory damages are those that are based on damages established by laws.
In civil law, the liable party has caused injury to the victim. Civil laws include economic damages, liability, negligence, intentional damage, property damage, personal damage, nuisance, and dignitary torts.
In the United States, civil law allows senior officials of an organization to be held liable for any civil wrongdoing by the organization. So if an organization is negligent, the senior officials can be pursued by any parties that were wronged.
Administrative/Regulatory Law
In administrative law, standards of performance or conduct are set by government agencies for organizations and industries to follow. Common sectors that are covered by administrative law include public utilities, communications, banking, safety and environmental protection regulations, and healthcare.
Customary Law
Customary law is based on the customs of a country or region. Customary law is not used in most systems in isolation, but rather incorporated into many mixed law systems, such as those used in many African countries, China, and Japan. Monetary fines or public service is the most common form of restitution in this legal system.
Religious Law
Religious law is based on religious beliefs. Although most religious law will be based on a particular religion and its primary written rules, cultural differences can vary from country to country and will affect the laws that are enforced.
Mixed Law
Mixed law combines two or more of the other law types. The most often mixed law uses civil law and common law.
Licensing and Intellectual Property
Intellectual property law is a group of laws that recognizes exclusive rights for creations of the mind. Intellectual property is a tangible or intangible asset to which the owner has exclusive rights.

The intellectual property covered by this type of law includes the following:
Patent
Trade secret
Trademark
Copyright
Software piracy and licensing issues
Digital rights management (DRM)
This section explains these types of intellectual properties and the internal protection of these properties.
Patent
A patent is granted to an individual or company to cover an invention that is described in the patent’s application. When the patent is granted, only the patent owner can make, use, or sell the invention for a period of time, usually 20 years. Although it is considered one of the strongest intellectual property protections available, the invention becomes public domain after the patent expires, thereby allowing any entity to manufacture and sell the product.
Patent litigation is common in today’s world. You commonly see technology companies, such as Apple, Microsoft, Hewlett-Packard, and Google, filing lawsuits regarding infringement on patents (often against each other). For this reason, many companies involve a legal team in patent research before developing new technologies. Being the first to be issued a patent is crucial in today’s highly competitive market.
Any product that is produced that is currently undergoing the patent application process will usually be identified with the Patent Pending seal, shown in Figure 1-7.

Trade Secret
A trade secret ensures that proprietary technical or business information remains confidential. A trade secret gives an organization a competitive edge. Trade secrets include recipes, formulas, ingredient listings, and so on that must be protected against disclosure. After the trade secret is obtained by or disclosed to a competitor or the general public, it is no longer considered a trade secret.
Most organizations that have trade secrets attempt to protect these secrets using nondisclosure agreements (NDAs). These NDAs must be signed by any entity that has access to information that is part of the trade secret. Anyone who signs an NDA will suffer legal consequences if the organization is able to prove that the signer violated it.
Trademark
A trademark ensures that a symbol, sound, or expression that identifies a product or an organization is protected from being used by another organization. This trademark allows the product or organization to be recognized by the general public.
Most trademarks are marked with one of the designations shown in Figure 1-8.

If the trademark is not registered, an organization should use a capital TM. If the trademark is registered, an organization should use a capital R that is encircled.
Copyright
A copyright ensures that a work that is authored is protected for any form of reproduction or use without the consent of the copyright holder, usually the author or artist who created the original work. A copyright lasts longer than a patent. Although the U.S. Copyright Office has several guidelines to determine the amount of time a copyright lasts, the general rule for works created after January 1, 1978, is the life of the author plus 70 years.
In 1996, the World Intellectual Property Organization (WIPO) standardized the treatment of digital copyrights. Copyright management information (CMI) is licensing and ownership information that is added to any digital work. In this standardization, WIPO stipulated that CMI included in copyrighted material cannot be altered.
The symbol shown in Figure 1-9 denotes a work that is copyrighted.

Software Piracy and Licensing Issues
To understand software piracy and licensing issues, professionals should understand the following terms that are used to differentiate between the types of software available:
Freeware: Software available free of charge, including all rights to copy, distribute, and modify the software.
Shareware: Software that is shared for a limited time. After a certain amount of time (the trial period), the software requires that the user purchase the software to access all the software’s features. This is also referred to as trialware.
Commercial software: Software that is licensed by a commercial entity for purchase in a wholesale or retail market.
Software piracy is the unauthorized reproduction or distribution of copyrighted software. Although software piracy is a worldwide issue, it is much more prevalent in Asia, Europe, Latin America, and Africa/Middle East. Part of the problem with software piracy stems from the cross-jurisdictional issues that arise. Obtaining the cooperation of foreign law enforcement agencies and government is often difficult or impossible. Combine this with the availability of the hardware needed to create pirated software and the speed with which it can be made, and you have a problem that will only increase over the coming years.
Security professionals and the organizations they work with must ensure that the organization takes measures to ensure that employees understand the implications of installing pirated software. In addition, large organizations might need to utilize an enterprise software inventory application that will provide administrators with a report on the software that is installed.
Internal Protection
As mentioned earlier in this chapter, employees are the greatest threat for any organization. For this reason, organizations should take measures to protect confidential resources from unauthorized internal access. Any information that is part of a patent, trade secret, trademark, or copyright should be marked and given the appropriate classification. Access controls should be customized for this information, and audit controls should be implemented that alert personnel should any access occur. Due care procedures and policies must be in place to ensure that any laws that protect these assets can be used to prosecute an offender.
Digital Rights Managements (DRM)
Hardware manufacturers, publishers, copyright holders, and individuals use DRM to control the use of digital content. This often also involves device controls.
First-generation DRM software controls copying. Second-generation DRM controls executing, viewing, copying, printing, and altering works or devices.
The U.S. Digital Millennium Copyright Act (DMCA) of 1998 imposes criminal penalties on those who make available technologies whose primary purpose is to circumvent content protection technologies. DRM includes restrictive license agreements and encryption. DRM protects computer games and other software, documents, ebooks, films, music, and television.
In most enterprise implementations, the primary concern is the DRM control of documents by using open, edit, print, or copy access restrictions that are granted on a permanent or temporary basis. Solutions can be deployed that store the protected data in a central or decentralized model. Encryption is used in the DRM implementation to protect the data both at rest and in transit.
Cyber Crimes and Data Breaches
A data breach is any incident in which information that is considered private or confidential is released to unauthorized parties. Organizations must have a plan in place to detect and respond to these incidents in the correct manner. Simply having an incident response plan is not enough, though. An organization must also have trained personnel who are familiar with the incident response plan and have the skills to respond to any incidents that occur.
A cyber crime is any criminal activity that is carried out by means of computers or the Internet. Computer crime concepts are covered earlier in this chapter. The U.S. Federal Bureau of Investigation (FBI) is the lead federal agency for investigating cyber attacks by criminals, overseas adversaries, and terrorists. Cyber crimes are becoming more commonplace, more dangerous, and more sophisticated. According to the FBI, the key priorities are computer and network intrusions, and the related priorities are going dark, identity theft, and online predators. The FBI has launched multiple initiatives and partnerships to help in their fight against cyber crime, including the Internet Crime Complaint Center (IC3), the Cyber Action Team (CAT), and the National Cyber-Forensics & Training Alliance (NCFTA).
Note
Going dark means that those charged with protecting our people are not always able to access evidence needed to prosecute crime and prevent terrorism even with lawful authority. While they have the legal authority to intercept and access communications and information pursuant to court order, law enforcement officials often lack the technical ability to do so.
Import/Export Controls
Many organizations today develop trade relationships with organizations that are located in other countries. Organizations must be aware of the export and import laws of the countries of both the source and destination countries. Encryption technologies are some of the most restricted technologies in regard to import and export laws. Although the United States does limit the export of encryption technologies for national security reasons, other countries, such as China and Russia, limit the import of these same technologies because the countries do not want their citizens to have access to them. Publicly available technology and software are exempt from most export laws, except for encryption technologies.
Any organization that engages in export and import activities with entities based in other countries should ensure that legal counsel is involved in the process so that all laws and regulations are followed. In addition, the organization should implement the appropriate controls to ensure that personnel do not inadvertently violate any import and export laws, regulations, or internal corporate policies.
Trans-Border Data Flow
In today’s world, data is moved across national borders. Trans-border data transfers allow organizations and industries to digitally share information in a much quicker manner than in the past. As data moves from server to server and across networks, the data location and the location of the data host must be considered. Data is subject to the laws and legal systems of every jurisdiction along its route.
Jurisdiction is the power or right of a legal or political agency to exercise its authority over a person, subject matter, or territory. It gets even more complicated because jurisdiction can be affected when the organization that owns the data is in one country while the data itself is stored in a facility in another country. Security professionals must oversee the privacy and data protection laws of all jurisdictions that may affect the organization. For this reason, security professionals should develop a detailed data flow map for all organizational processes.
Cloud computing presents its own risks because often it is hard to determine exactly where the data is stored. Organizations that store data in the cloud should work with their cloud service providers to ensure that all application laws and regulations regarding the security and privacy of data are followed.
Privacy
Privacy is the right of an individual to control the use of their personal information. When considering technology and its use today, privacy is a major concern of users. This privacy concern usually covers three areas: which personal information can be shared with whom, whether messages can be exchanged confidentially, and whether and how one can send messages anonymously. Privacy is an integral part of any security measures that an organization takes.
As part of the security measures that organizations must take to protect privacy, PII must be understood, identified, and protected. Organizations must also understand the privacy laws that governments have adopted. Finally, organizations must ensure that they comply with all laws and regulations regarding privacy.
Personally Identifiable Information (PII)
PII is any piece of data that can be used alone or with other information to identify a single person. Any PII that an organization collects must be protected in the strongest manner possible. PII includes full name, identification numbers (including driver’s license number and Social Security number), date of birth, place of birth, biometric data, financial account numbers (both bank account and credit card numbers), and digital identities (including social media names and tags).
Keep in mind that different countries and levels of government can have different qualifiers for identifying PII. Security professionals must ensure that they understand international, national, state, and local regulations and laws regarding PII. As the theft of this data becomes even more prevalent, you can expect more laws to be enacted that will affect your job.
A complex listing of PII is shown in Figure 1-10.


Laws and Regulations
Security professionals are usually not lawyers. As such, they are not expected to understand all the specifics of the laws that affect their organization. However, security professionals must be aware of the laws and at a minimum understand how those laws affect the operations of their organization. For example, a security professional at a healthcare facility would need to understand all security guidelines in the Health Insurance Portability and Accountability Act (HIPAA) as well as the Patient Protection and Affordable Care Act (PPACA) and Health Care and Education Reconciliation Act of 2010, commonly known as Obamacare.
This section discusses many of the laws that will affect a security professional. For testing purposes, you need not worry about all the details of the law. You simply need to understand the law’s name(s), purpose, and the industry it affects (if applicable).
Note
CISSP candidates should ensure that they understand privacy laws and import/export/trans-border data flow regulations. As privacy is becoming more important in today’s world, it is likely that the CISSP exam will shift to more thoroughly encompass this issue.
Sarbanes-Oxley (SOX) Act
The Public Company Accounting Reform and Investor Protection Act of 2002, more commonly known as the Sarbanes-Oxley (SOX) Act, affects any organization that is publicly traded in the United States. It controls the accounting methods and financial reporting for the organizations and stipulates penalties and even jail time for executive officers.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA, also known as the Kennedy-Kassebaum Act, affects all healthcare facilities, health insurance companies, and healthcare clearinghouses. It is enforced by the Office of Civil Rights of the Department of Health and Human Services. It provides standards and procedures for storing, using, and transmitting medical information and healthcare data. HIPAA overrides state laws unless the state laws are stricter. HIPAA was amended by the Health Care and Education Reconciliation Act of 2010. However, the majority of the amendments from the Health Care and Education Reconciliation Act of 2010 do not affect the rules for the security or privacy of healthcare data as set forth in HIPAA.
Gramm-Leach-Bliley Act (GLBA) of 1999
GLBA affects all financial institutions, including banks, loan companies, insurance companies, investment companies, and credit card providers. It provides guidelines for securing all financial information and prohibits sharing financial information with third parties. This act directly affects the security of PII.
Computer Fraud and Abuse Act (CFAA) of 1986
CFAA affects any entities that might engage in hacking of “protected computers” as defined in the act. It was amended in 1989, 1994, 1996; in 2001 by the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (USA PATRIOT) Act; in 2002; and in 2008 by the Identity Theft Enforcement and Restitution Act. A “protected computer” is a computer used exclusively by a financial institution or the U.S. government or used in or affecting interstate or foreign commerce or communication, including a computer located outside the United States that is used in a manner that affects interstate or foreign commerce or communication of the United States. Due to the interstate nature of most Internet communication, any ordinary computer has come under the jurisdiction of the law, including cellphones. The law includes several definitions of hacking, including knowingly accessing a computer without authorization; intentionally accessing a computer to obtain financial records, U.S. government information, or protected computer information; and transmitting fraudulent commerce communication with the intent to extort.
Federal Privacy Act of 1974
The Federal Privacy Act of 1974 affects any computer that contains records used by a federal agency. It provides guidelines on collection, maintenance, use, and dissemination of PII about individuals that is maintained in systems of records by federal agencies on collecting, maintaining, using, and distributing PII.
Federal Intelligence Surveillance Act (FISA) of 1978
FISA affects law enforcement and intelligence agencies. It was the first act to give procedures for the physical and electronic surveillance and collection of “foreign intelligence information” between “foreign powers” and “agents of foreign powers” and only applied to traffic within the United States. It was amended by the USA PATRIOT Act of 2001, the FISA Amendments Act of 2008, and the USA Freedom Act of 2015.
Electronic Communications Privacy Act (ECPA) of 1986
ECPA affects law enforcement and intelligence agencies. It extended government restrictions on wiretaps from telephone calls to include transmissions of electronic data by computer and prohibited access to stored electronic communications. It was amended by the Communications Assistance to Law Enforcement Act (CALEA) of 1994, the USA PATRIOT Act of 2001, and the FISA Amendments Act of 2008.
Computer Security Act of 1987
The Computer Security Act of 1987 was superseded by the Federal Information Security Management Act (FISMA) of 2002. This act was the first law written to require a formal computer security plan. It was written to protect and defend any of the sensitive information in the federal government systems and provide security for that information. It also placed requirements on government agencies to train employees and identify sensitive systems.
United States Federal Sentencing Guidelines of 1991
The United States Federal Sentencing Guidelines of 1991 affects individuals and organizations convicted of felonies and serious (Class A) misdemeanors. It provides guidelines to prevent sentencing disparities that existed across the United States.
Communications Assistance for Law Enforcement Act (CALEA) of 1994
CALEA affects law enforcement and intelligence agencies. It requires telecommunications carriers and manufacturers of telecommunications equipment to modify and design their equipment, facilities, and services to ensure that they have built-in surveillance capabilities. This allows federal agencies to monitor all telephone, broadband Internet, and Voice over IP (VoIP) traffic in real time.
Personal Information Protection and Electronic Documents Act (PIPEDA)
PIPEDA affects how private sector organizations collect, use, and disclose personal information in the course of commercial business in Canada. The act was written to address European Union (EU) concerns over the security of PII in Canada. The law requires organizations to obtain consent when they collect, use, or disclose personal information and to have personal information policies that are clear, understandable, and readily available.
Basel II
Basel II affects financial institutions. It addresses minimum capital requirements, supervisory review, and market discipline. Its main purpose is to protect against risks the banks and other financial institutions face. It is an international accord, and compliance is not mandatory.
Federal Information Security Management Act (FISMA) of 2002
FISMA affects every federal agency. It requires the federal agencies to develop, document, and implement an agency-wide information security program.
Economic Espionage Act of 1996
The Economic Espionage Act of 1996 covers a multitude of issues because of the way the act was structured. But for the purposes of the CISSP exam, this act affects companies that have trade secrets and any individuals who plan to use encryption technology for criminal activities. A trade secret does not need to be tangible to be protected by this act. Per this law, theft of a trade secret is now a federal crime, and the U.S. Sentencing Commission must provide specific information in its reports regarding encryption or scrambling technology that is used illegally.
USA PATRIOT Act of 2001
The USA PATRIOT Act affects law enforcement and intelligence agencies in the United States. Its purpose is to enhance the investigatory tools that law enforcement can use, including email communications, telephone records, Internet communications, medical records, and financial records. When this law was enacted, it amended several other laws, including FISA and the ECPA of 1986.
Although the USA PATRIOT Act does not restrict private citizen use of investigatory tools, exceptions include if the private citizen is acting as a government agent (even if not formally employed), if the private citizen conducts a search that would require law enforcement to have a warrant, if the government is aware of the private citizen’s search, or if the private citizen is performing a search to help the government.
Health Care and Education Reconciliation Act of 2010
The Health Care and Education Reconciliation Act of 2010 affects healthcare and educational organizations. For the CISSP exam, understand that this act increased some of the security measures that must be taken to protect healthcare information.
USA Freedom Act of 2015
The USA Freedom Act of 2015 reauthorizes parts of the USA PATRIOT Act but dissolves its notorious bulk data collection of Americans’ phone records and Internet metadata.
Employee Privacy Issues and Expectation of Privacy
Employee privacy issues must be addressed by all organizations to ensure that the organization is protected. However, organizations must give employees the proper notice of any monitoring that might be used. Organizations must also ensure that the monitoring of employees is applied in a consistent manner. Many organizations implement a no-expectation-of-privacy policy that the employee must sign after receiving the appropriate training. Keep in mind that this policy should specifically describe any unacceptable behavior. Companies should also keep in mind that some actions are protected by the Fourth Amendment. Security professionals and senior management should consult with legal counsel when designing and implementing any monitoring solution.
European Union
The EU has implemented several laws and regulations that affect security and privacy. The EU Principles on Privacy include strict laws to protect private data. The EU’s Data Protection Directive provides direction on how to follow the laws set forth in the principles. The EU then created the Safe Harbor Privacy Principles to help guide U.S. organizations in compliance with the EU Principles on Privacy. Some of the guidelines include the following:
Data should be collected in accordance with the law.
Information collected about an individual cannot be shared with other organizations unless given explicit permission by the individual.
Information transferred to other organizations can be transferred only if the sharing organization has adequate security in place.
Data should be used only for the purpose for which it was collected.
Data should be used only for a reasonable period of time.
Note
Do not confuse the term safe harbor with data haven. According to the EU, a safe harbor is an entity that conforms to all the requirements of the EU Principles on Privacy. A data haven is a country that fails to legally protect personal data with the main aim being to attract companies engaged in the collection of the data.
The Safe Harbor Privacy Principles were replaced by the EU-US Privacy Shield. It provided a framework for transatlantic personal data exchanges for commercial purposes between the European Union and the United States.
The EU Electronic Security Directive defines electronic signature principles. In this directive, a signature must be uniquely linked to the signer and to the data to which it relates so that any subsequent data change is detectable. The signature must be capable of identifying the signer.
Beginning on May 25, 2018, the members of the EU should begin applying the General Data Protection Regulation (GDPR). The GDPR applies to EU-based organizations that collect or process the personal data of EU residents and to organizations outside the EU that monitor behavior or offer goods and services to EU residents. It gives a wider definition of personal and sensitive data to include online identifiers and genetic and biometrics data, such as cookies, IP address, health information, biometric data, and genetic information. The GDPR affects service providers that process personal data on behalf of an organization, including cloud services, call centers, and payroll services. It strengthens individual privacy rights to include the following:
Valid consent: Organizations must follow stricter rules for consent as a legal basis for processing.
Transparency: Organizations must be transparent regarding what information is collected and how the information is processed.
Correction: Organizations must allow individuals to correct inaccurate personal data.
Erasure: Organizations must allow individuals to request that their personal data be erased under certain conditions.
Data portability: Organizations must allow individuals to move personal data from one service provider to another.
Automated processing: Organizations must not use automated processing as the sole decision maker.
Under GDPR, organizations are obligated to provide accountability by maintaining a record of all data processing activities. A Data Protection Impact Assessment (DPIA) is mandatory if processing activity is likely to result in a high risk to an individual’s rights. Organizations must keep personal data secure through “appropriate technical and organizational measures.” Organizations must report data breaches to the regulator within 72 hours of discovery. Organizations that are public authorities, monitoring individuals on a large scale, or processing sensitive data must name a data protection officer. For all other organizations, a data protection officer is recommended but not required. Finally, data transfer outside the EU is allowed only if appropriate safeguards are in place.
Organizations that do not comply with GDPR can be levied with fines up to 20 million Euros. In addition, they may have to compensate victims for damage claims. Finally, noncompliance may result in reputational damage and consumer loss of trust.
To learn more details regarding the GDPR, refer to https://www.itgovernance.co.uk/data-protection-dpa-and-eu-data-protection-regulation.
Professional Ethics
Ethics for any profession are the right and wrong actions that are the moral principle of that occupation. Security professionals, particularly those who hold the CISSP certification, should understand the ethics that are published by the International Information Systems Security Certification Consortium (ISC)2, the Computer Ethics Institute, the Internet Architecture Board (IAB), and the organization they are employed by.
(ISC)2 Code of Ethics
(ISC)2 provides a strict Code of Ethics for its certificate holders. All certificate holders must follow the Code of Ethics. Any reported violations of the code are investigated. Certificate holders who are found to be guilty of violation will have their certification revoked.
The four mandatory canons for the Code of Ethics are as follows:
Protect society, the common good, necessary public trust and confidence, and the infrastructure.
Act honorably, honestly, justly, responsibly, and legally.
Provide diligent and competent service to principals.
Advance and protect the profession.
Any certificate holders are required to report any actions by other certificate holders that they feel are in violation of the Code. If a certificate holder is reported, a peer review committee will investigate the actions and make a decision as to the certificate holder’s standing.
Certification is a privilege that must be earned and maintained. Certificate holders are expected to complete certain educational requirements to prove their continued competence in all aspects of security. They are also expected to promote the understanding and acceptance of prudent information security measures.
Computer Ethics Institute
The Computer Ethics Institute created the Ten Commandments of Computer Ethics. The following list summarizes these ten ethics:
Do not use a computer for harm.
Do not interfere with the computer work of other people.
Do not snoop around in the computer files of other people.
Do not use a computer to steal.
Do not use a computer to lie.
Do not install and use licensed software unless you have paid for it.
Do not use another person’s computer unless you have permission or have paid the appropriate compensation for said usage.
Do not appropriate another person’s intellectual output.
Consider the consequences of the program you are writing or the system you are designing.
Always use a computer in ways that ensure consideration and respect of other people and their property.
Internet Architecture Board
The IAB oversees the design, engineering, and management of the Internet. This board meets regularly to review Internet standardization recommendations. Internet ethics is just a small part of the area they cover. Ethics statements issued by the IAB usually detail any acts that they deem irresponsible. These actions include wasting resources, destroying data integrity, compromising privacy, and accessing resources that users are not authorized to access.
Request for Comments (RFC) 1087, called Ethics and the Internet, is the specific IAB document that outlines unethical Internet behavior. Refer to http://tools.ietf.org/html/rfc1087 for more information.
Organizational Code of Ethics
Organizations should develop an internal ethics statement and ethics program. By adopting a formal statement and program, the organization is stressing to its employees that they are expected to act in an ethical manner in all business dealings.
Several laws in the United States can affect the development and adoption of an organizational ethics program. If an organization adopts an ethics program, the liability of the organization is often limited, even when the employees are guilty of wrongdoing, provided the organization ensures that personnel have been instructed on the organization’s ethics.
Security Documentation
Within an organization, information security governance consists of several documents that are used to provide comprehensive security management. Data and other assets should be protected mainly based on their value and sensitivity. Strategic plans guide the long-term security activities (3–5 years or more). Tactical plans achieve the goals of the strategic plan and are shorter in length (6–18 months).
Because management is the most critical link in the computer security chain, management approval must be obtained as part of the first step in forming and adopting an information security policy. Senior management must complete the following steps prior to the development of any organizational security policy:
Define the scope of the security program.
Identify all the assets that need protection.
Determine the level of protection that each asset needs.
Determine personnel responsibilities.
Develop consequences for noncompliance with the security policy.
By fully endorsing an organizational security policy, senior management accepts the ownership of an organization’s security. High-level polices are statements that indicate senior management’s intention to support security.
After senior management approval has been obtained, the first step in establishing an information security program is to adopt an organizational information security statement. The organization’s security policy comes from this organizational information security statement. The security planning process must define how security will be managed, who will be responsible for setting up and monitoring compliance, how security measures will be tested for effectiveness, who is involved in establishing the security policy, and where the security policy is defined.

Security professionals must understand how information security documents work together to form a comprehensive security plan. Information security governance documents include
Policies
Processes
Procedures
Standards
Guidelines
Baselines
Policies
A security policy dictates the role of security as provided by senior management and is strategic in nature, meaning it provides the end result of security. Policies are defined in two ways: the level in the organization at which they are enforced and the category to which they are applied. Policies must be general in nature, meaning they are independent of a specific technology or security solution. Policies outline goals but do not give any specific ways to accomplish the stated goals. All policies must contain an exception area to ensure that management will be able to deal with situations that might require exceptions.
Policies are broad and provide the foundation for development of processes, standards, baselines, guidelines, and procedures, all of which provide the security structure. Administrative, technical, and physical access controls fill in the security and structure needed to complete the security program.
The policy levels used in information security are organizational security policies, system-specific security policies, and issue-specific security policies. The policy categories used in information security are regulatory security policies, advisory security policies, and informative security policies. The policies are divided as shown in Figure 1-11.


Organizational Security Policy
An organizational security policy is the highest level security policy adopted by an organization. Business goals steer the organizational security policy. An organizational security policy contains general directions and should have the following components:
Define overall goals of security policy.
Define overall steps and importance of security.
Define security framework to meet business goals.
State management approval of policy, including support of security goals and principles.
Define all relevant terms.
Define security roles and responsibilities.
Address all relevant laws and regulations.
Identify major functional areas.
Define compliance requirements and noncompliance consequences.
An organizational security policy must be supported by all stakeholders and should have high visibility for all personnel and be discussed regularly. In addition, it should be reviewed on a regular basis and revised based on the findings of the regular review. Each version of the policy should be maintained and documented with each new release.
System-Specific Security Policy
A system-specific security policy addresses security for a specific computer, network, technology, or application. This policy type is much more technically focused than an issue-specific security policy. It outlines how to protect the system or technology.
Issue-Specific Security Policy
An issue-specific security policy addresses specific security issues. Issue-specific policies include email privacy policies, virus checking policies, employee termination policies, no-expectation-of-privacy policies, and so on. Issue-specific policies support the organizational security policy.
Policy Categories
Regulatory security policies address specific industry regulations, including mandatory standards. Examples of industries that must consider regulatory security policies include healthcare facilities, public utilities, and financial institutions.
Advisory security policies provide instruction on acceptable and unacceptable activities. In most cases, this policy is considered to be strongly suggested, not compulsory. This type of policy usually gives examples of possible consequences if users engage in unacceptable activities.
Informative security policies provide information on certain topics and act as an educational tool.
Processes
A process is a series of actions or steps taken in order to achieve a particular end. Organizations will define individual processes and their relationship to one another. For example, an organization may define a process for how customers enter an online order, how the payment is processed, and how the order is fulfilled after the payment is processed. While each of these processes is separate and includes a list of unique tasks that must be completed, the processes all rely on each other for completion. The process lays out how the goal or task is completed. Processes then lead to procedures.
Procedures
Procedures embody all the detailed actions that personnel are required to follow and encompass the use of computers and other devices. Procedures often include step-by-step lists on how processes, policies, standards, and guidelines are implemented.
Standards
Standards describe how policies will be implemented within an organization. They are mandatory actions or rules that are tactical in nature, meaning they provide the steps necessary to achieve security. Just like policies, standards should be regularly reviewed and revised.
Guidelines
Guidelines are recommended actions that are much more flexible than standards, thereby providing allowance for circumstances that can occur. Guidelines provide guidance when standards do not apply.
Baselines
A baseline is a reference point that is defined and captured to be used as a future reference. Although capturing baselines is important, using those baselines to assess the security state is just as important. Even the most comprehensive baselines are useless if they are never used.
Capturing a baseline at the appropriate point in time is also important. Baselines should be captured when a system is properly configured and fully updated. When updates occur, new baselines should be captured and compared to the previous baselines. At that time, adopting new baselines based on the most recent data might be necessary.
Business Continuity
Business continuity is an organization’s capability to continue delivery of products or services at acceptable predefined levels following a disruptive incident. As part of risk management, security professionals should ensure that the organization prepares appropriate business continuity plans. This section covers business continuity and disaster recovery concepts, business continuity scope and plan, and business impact analysis.
Business Continuity and Disaster Recovery Concepts
Security professionals must be involved in the development of any business continuity and disaster recovery processes.

As a result, security professionals must understand the basic concepts involved in business continuity and disaster recovery planning, including the following:
Disruptions
Disasters
Technological
Human-caused
Natural
Disaster recovery and the disaster recovery plan (DRP)
Continuity planning and the business continuity plan (BCP)
Business impact analysis (BIA)
Contingency plan
Availability
Reliability
Disruptions
A disruption is any unplanned event that results in the temporary interruption of any organizational asset, including processes, functions, and devices. Disruptions are grouped into three main categories: non-disaster, disaster, and catastrophe.
Non-disasters are temporary interruptions that occur due to malfunction or failure. Non-disasters might or might not require public notification and are much easier to recover from than disasters or catastrophes.
A disaster is a suddenly occurring event that has a long-term negative impact on life. Disasters require that the organization publicly acknowledge the event and provide the public with information on how the organization will recover. Disasters require more effort for recovery than non-disasters but less than catastrophes.
A catastrophe is a disaster that has a much wider and much longer impact. In most cases, a disaster is considered a catastrophe if facilities are destroyed, thereby resulting in the need for the rebuilding of the facilities and the use of a temporary offsite facility.
Disasters
A disaster is an emergency that goes beyond the normal response of resources. A disaster usually affects a wide geographical area and results in severe damage, injury, loss of life, and loss of property. Any disaster has negative financial and reputational effects on the organization. The severity of the financial and reputational damage is also affected by the amount of time the organization takes to recover from the disaster.

The causes of disasters are categorized into three main areas according to origin: technological disasters, human-caused disasters, and natural disasters. A disaster is officially over when all business elements have returned to normal function at the original site. The primary concern during any disaster is personnel safety.
Technological Disasters
Technological disasters occur when a device fails. This failure can be the result of device defects, incorrect implementation, incorrect monitoring, or human error. Technological disasters are not usually intentional. If a technological disaster is not recovered from in a timely manner, an organization might suffer a financial collapse.
If a disaster occurs because of a deliberate attack against an organization’s infrastructure, the disaster is considered a human-caused disaster even if the attack is against a specific device or technology. In the past, all technological disasters were actually considered human-caused disasters because technological disasters are usually due to human error or negligence. However, in recent years, experts have started categorizing technological disasters separately from human-caused disasters, although the two are closely related.
Human-Caused Disasters
Human-caused disasters occur through human intent or error. Human-caused disasters include enemy attacks, bombings, sabotage, arson, terrorism, strikes or other job actions, infrastructure failures, personnel unavailability due to emergency evacuation, and mass hysteria. In most cases, human-caused disasters are intentional.
Natural Disasters
Natural disasters occur because of a natural hazard. Natural disasters include flood, tsunami, earthquake, hurricane, tornado, and other such natural events. A fire that is not the result of arson is also considered a natural disaster.
Disaster Recovery and the Disaster Recovery Plan (DRP)
Disaster recovery minimizes the effect of a disaster and includes the steps necessary to resume normal operation. Disaster recovery must take into consideration all organizational resources, functions, and personnel. Efficient disaster recovery will sustain an organization during and after a disruption due to a disaster.
Each organizational function or system will have its own disaster recovery plan (DRP). The DRP for each function or system is created as a direct result of that function or system being identified as part of the business continuity plan (BCP). The DRP is implemented when the emergency occurs and includes the steps to restore functions and systems. The goal of disaster recovery is to minimize or prevent property damage and prevent loss of life. More details on disaster recovery are given later in this chapter.
Continuity Planning and the Business Continuity Plan (BCP)
Continuity planning deals with identifying the impact of any disaster and ensuring that a viable recovery plan for each function and system is implemented. Its primary focus is how to carry out the organizational functions when a disruption occurs.
The BCP considers all aspects that are affected by a disaster, including functions, systems, personnel, and facilities. It lists and prioritizes the services that are needed, particularly the telecommunications and IT functions. More details on continuity planning are given throughout the next few sections.
Business Impact Analysis (BIA)
A business impact analysis (BIA) is a functional analysis that occurs as part of business continuity and disaster recovery. Performing a thorough BIA will help business units understand the impact of a disaster. The resulting document that is produced from a BIA lists the critical and necessary business functions, their resource dependencies, and their level of criticality to the overall organization. More details on the BIA are given later in this chapter in the “BIA Development” section.
Contingency Plan
A contingency plan is sometimes referred to as “Plan B,” because it can be also used as an alternative for action if expected results fail to materialize. Contingency planning is a component of business continuity, disaster recovery, and risk management. Contingency planning is covered in more detail in the “Business Contingency Planning” section later in this chapter.
Availability
As you already know, availability is one of the key principles of the confidentiality, integrity, and availability (CIA) triad and will be discussed in almost every defined CISSP domain. Availability is a main component of business continuity planning. The organization must determine the acceptable level of availability for each function or system. If the availability of a resource falls below this defined level, then specific actions must be followed to ensure that availability is restored.
With regard to availability, most of the unplanned downtime of functions and systems is attributed to hardware failure. Availability places emphasis on technology.
Reliability
Reliability is the ability of a function or system to consistently perform according to specifications. It is vital in business continuity to ensure that the organization’s processes can continue to operate. Reliability places emphasis on processes.
Scope and Plan
As you already know, creating the BCP is vital to ensure that the organization can recover from a disaster or disruptive event. Several groups have established standards and best practices for business continuity. These standards and best practices include many common components and steps.
This section covers the personnel components, the scope, and the business continuity steps that must be completed.
Personnel Components
The most important personnel in the development of the BCP is senior management. Senior management support of business continuity and disaster recovery drives the overall organizational view of the process. Without senior management support, this process will fail.
Senior management sets the overall goals of business continuity and disaster recovery. A business continuity coordinator should be named by senior management and lead the BCP committee. The committee develops, implements, and tests the BCP and DRP. The BCP committee should contain a representative from each business unit. At least one member of senior management should be part of this committee. In addition, the organization should ensure that the IT department, legal department, security department, and communications department are represented because of the vital role that these departments play during and after a disaster.
With management direction, the BCP committee must work with business units to ultimately determine the business continuity and disaster recovery priorities. Senior business unit managers are responsible for identifying and prioritizing time-critical systems. After all aspects of the plans have been determined, the BCP committee should be tasked with regularly reviewing the plans to ensure they remain current and viable. Senior management should closely monitor and control all business continuity efforts and publicly praise any successes.
After an organization gets into disaster recovery planning, other teams are involved.
Scope
To ensure that the development of the BCP is successful, senior management must define the BCP scope. A business continuity project with an unlimited scope can often become too large for the BCP committee to handle correctly. For this reason, senior management might need to split the business continuity project into smaller, more manageable pieces.
When considering the splitting of the BCP into pieces, an organization might want to split the pieces based on geographic location or facility. However, an enterprise-wide BCP should be developed that ensures compatibility of the individual plans.
Business Contingency Planning
Many organizations have developed standards and guidelines for performing business contingency planning. One of the most popular standards is Special Publication (SP) 800-34 Rev. 1 from NIST.

The following list summarizes the steps of SP 800-34 Rev. 1:
Develop contingency planning policy.
Conduct business impact analysis (BIA).
Identify preventive controls.
Create contingency strategies.
Develop a contingency plan.
Conduct contingency plan testing, training, and exercises.
Maintain the plan.
Figure 1-12 shows a more detailed listing of the tasks included in SP 800-34 R1.

NIST 800-34 Rev. 1 includes the following list of the types of plans that should be included during contingency planning:
Business continuity plan (BCP): Focuses on sustaining an organization’s mission/business processes during and after a disruption.
Continuity of operations (COOP) plan: Focuses on restoring an organization’s mission-essential functions (MEFs) at an alternate site and performing those functions for up to 30 days before returning to normal operations.
Crisis communications plan: Documents standard procedures for internal and external communications in the event of a disruption using a crisis communications plan. It also provides various formats for communications appropriate to the incident.
Critical infrastructure protection (CIP) plan: A set of policies and procedures that serve to protect and recover these assets and mitigate risks and vulnerabilities.
Cyber incident response plan: Establishes procedures to address cyber attacks against an organization’s information system(s).
Disaster recovery plan (DRP): An information system–focused plan designed to restore operability of the target system, application, or computer facility infrastructure at an alternate site after an emergency.
Information system contingency plan (ISCP): Provides established procedures for the assessment and recovery of a system following a system disruption.
Occupant emergency plan (OEP): Outlines first-response procedures for occupants of a facility in the event of a threat or incident to the health and safety of personnel, the environment, or property.
Develop Contingency Planning Policy
The contingency planning policy statement should define the organization’s overall contingency objectives and establish the organizational framework and responsibilities for system contingency planning. To be successful, senior management, most likely the CIO, must support a contingency program and be included in the process to develop the program policy. If being applied to a federal agency, the policy must reflect the FIPS 199 impact levels and the contingency controls that each impact level establishes. Key policy elements are as follows:
Roles and responsibilities
Scope as applies to common platform types and organization functions (i.e., telecommunications, legal, media relations) subject to contingency planning
Resource requirements
Training requirements
Exercise and testing schedules
Plan maintenance schedule
Minimum frequency of backups and storage of backup media
Note
FIPS 199 is discussed in more detail later in this chapter.
Conduct the BIA
The BIA purpose is to correlate the system with the critical mission/business processes and services provided and, based on that information, characterize the consequences of a disruption.
Identify Preventive Controls
The outage impacts identified in the BIA may be mitigated or eliminated through preventive measures that deter, detect, and/or reduce impacts to the system. Where feasible and cost effective, preventive methods are preferable to actions that may be necessary to recover the system after a disruption.
Create Contingency Strategies
Organizations are required to adequately mitigate the risk arising from use of information and information systems in the execution of mission/business processes. This includes backup methods, offsite storage, recovery, alternate sites, and equipment replacement.
Develop Contingency Plan
Using the information that has been obtained up to this point, an organization should develop the contingency plan, including backup and recovery solutions. This plan must document the roles and responsibilities of personnel in the organization as part of this plan.
Plan Testing, Training, and Exercises (TT&E)
Testing, training, and exercises for business continuity should be carried out regularly based on NIST SP 800-84. Organizations should conduct TT&E events periodically, following organizational or system changes, or the issuance of new TT&E guidance, or as otherwise needed.
Maintain the Plan
To be effective, the plan must be maintained in a ready state that accurately reflects system requirements, procedures, organizational structure, and policies. As a general rule, the plan should be reviewed for accuracy and completeness at an organization-defined frequency or whenever significant changes occur to any element of the plan.
BIA Development
The BCP development depends most on the development of the BIA. The BIA helps the organization to understand what impact a disruptive event would have on the organization. It is a management-level analysis that identifies the impact of losing an organization’s resources.

The four main steps of the BIA are as follows:
Identify critical processes and resources.
Identify outage impacts, and estimate downtime.
Identify resource requirements.
Identify recovery priorities.
The BIA relies heavily on any vulnerability analysis and risk assessment that is completed. The vulnerability analysis and risk assessment may be performed by the BCP committee or by a separately appointed risk assessment team. The risk assessment process is discussed later in the NIST “SP 800-30 Rev. 1” section.
Identify Critical Processes and Resources
When identifying the critical processes and resources of an organization, the BCP committee must first identify all the business units or functional areas within the organization. After all units have been identified, the BCP team should select which individuals will be responsible for gathering all the needed data and select how to obtain the data.
These individuals will gather the data using a variety of techniques, including questionnaires, interviews, and surveys. They might also actually perform a vulnerability analysis and risk assessment or use the results of these tests as input for the BIA.
During the data gathering, the organization’s business processes and functions and the resources upon which these processes and functions depend should be documented. This list should include all business assets, including physical and financial assets that are owned by the organization, and any assets that provide competitive advantage or credibility.
Identify Outage Impacts, and Estimate Downtime
After determining all the business processes, functions, and resources, the organization should then determine the criticality level of each resource.

As part of determining how critical an asset is, you need to understand the following terms:
Maximum tolerable downtime (MTD): The maximum amount of time that an organization can tolerate a single resource or function being down. This is also referred to as maximum period time of disruption (MPTD).
Mean time to repair (MTTR): The average time required to repair a single failed component or device when a disaster or disruption occurs.
Mean time between failure (MTBF): The estimated amount of time a device will operate before a failure occurs. This amount is calculated by the device vendor. System reliability is increased by a higher MTBF and lower MTTR.
Recovery time objective (RTO): The time period after a disaster or disruptive event within which a resource or function must be restored to avoid unacceptable consequences. RTO assumes that an acceptable period of downtime exists. RTO should be smaller than MTD.
Work recovery time (WRT): The amount of time that is needed to verify system and/or data integrity.
Recovery point objective (RPO): The maximum targeted period in which data might be lost from an IT service due to a major incident.
Each organization must develop its own documented criticality levels. A good example of organizational resource and function criticality levels includes critical, urgent, important, normal, and nonessential. Critical resources are those resources that are most vital to the organization’s operation and should be restored within minutes or hours of the disaster or disruptive event. Urgent resources should be restored within 24 hours but are not considered as important as critical resources. Important resources should be restored within 72 hours but are not considered as important as critical or urgent resources. Normal resources should be restored within 7 days but are not considered as important as critical, urgent, or important resources. Nonessential resources should be restored within 30 days.
Each process, function, and resource must have its criticality level defined to act as an input into the DRP. If critical priority levels are not defined, a DRP might not be operational within the timeframe the organization needs to recover.
Identify Resource Requirements
After the criticality level of each function and resource is determined, you need to determine all the resource requirements for each function and resource. For example, an organization’s accounting system might rely on a server that stores the accounting application, another server that holds the database, various client systems that perform the accounting tasks over the network, and the network devices and infrastructure that support the system. Resource requirements should also consider any human resources requirements. When human resources are unavailable, the organization can be just as negatively impacted as when technological resources are unavailable.
Note
Keep in mind that the priority for any CISSP should be the safety of human life. Consider and protect all other organizational resources only after personnel are safe.
The organization must document the resource requirements for every resource that would need to be restored when the disruptive event occurs. This includes device name, operating system or platform version, hardware requirements, and device interrelationships.
Identify Recovery Priorities
After all the resource requirements have been identified, the organization must identify the recovery priorities. Establish recovery priorities by taking into consideration process criticality, outage impacts, tolerable downtime, and system resources. After all this information is compiled, the result is an information system recovery priority hierarchy.
Three main levels of recovery priorities should be used: high, medium, and low. The BIA stipulates the recovery priorities but does not provide the recovery solutions. Those are given in the DRP.
Recoverability
Recoverability is the ability of a function or system to be recovered in the event of a disaster or disruptive event. As part of recoverability, downtime must be minimized. Recoverability places emphasis on the personnel and resources used for recovery.
Fault Tolerance
Fault tolerance is provided when a backup component begins operation when the primary component fails. One of the key aspects of fault tolerance is the lack of service interruption.
Varying levels of fault tolerance can be achieved at most levels of the organization based on how much an organization is willing to spend. However, the backup component often does not provide the same level of service as the primary component. For example, an organization might implement a high-speed T1 connection to the Internet. However, the backup connection to the Internet that is used in the event of the failure of the T1 line might be much slower but at a much lower cost of implementation than the primary T1 connection.
Personnel Security Policies and Procedures
Personnel are responsible for the vast majority of security issues within an organization, whether they realize it or not. For this reason, it is vital that an organization implement the appropriate personnel security policies. Organizations should have personnel security policies and procedures in place that address candidate screening and hiring; employment agreements and policies; onboarding and termination processes; vendor, consultant, and contractor agreements and controls; compliance policy requirements; privacy policy requirements; and job rotation and separation of duties. Security professionals should work with human resources personnel to ensure that the appropriate personnel security policies are in place.
Candidate Screening and Hiring
Personnel screening should occur prior to the offer of employment and might include a criminal history, work history, background investigations, credit history, driving records, substance-abuse testing, reference checks, education and licensing verification, Social Security number verification and validation, and check for inclusion on a suspected terrorist watch list. Each organization should determine the screening needs based on the organization’s needs and the perspective personnel’s employment level. Job descriptions should contain the roles and responsibilities of the job role and any experience or education that is required. If skills must be maintained or upgraded, the job description should list the annual training requirements, especially if specialized security training is needed.
Criminal history checks are allowed under the Fair Credit Reporting Act (FCRA). Employers can request criminal records for most potential employees for the past seven years. If the applicant will be earning more than $75,000 annually, there are no time restrictions on criminal history. Employers need to search state and county criminal records, sex and violent offender records, and prison records. Many companies provide such services for a fee.
Work history should be verified. Former employers should be contacted to confirm dates employed, positions, performance, and reason for leaving. However, security professionals should keep in mind that some companies will only verify the employment term.
Background investigation should research any claim made on the applicant’s application or resume. Verification of the applicant’s claims serves to protect the hiring organization by ensuring that the applicant holds the skills and experience that he or she claims to have. Employees should also be reinvestigated based on their employment level. For example, employees with access to financial data and transactions should undergo periodic credit checks.
Credit history ensures that personnel who are involved in financial transactions for the organization will not be risks for financial fraud. The FCRA and Equal Employment Opportunity Commission (EEOC) provide guidelines that can help human resources personnel in this area. In addition, it is a good idea to involve legal counsel.
Driving records are necessary if the applicant will be operating a motor vehicle as part of his or her job. But often this type of check for other applicants can help reveal lifestyle issues, such as driving under the influence or license suspension, that can cause employment problems later.
Substance-abuse testing will reveal to the employer any drug use. Because a history of drug use can cause productivity and absenteeism, it is always best to perform such testing before offering employment. However, security professionals should ensure that any substance testing is clearly stated as part of the job posting.
Two types of reference checks are performed: work and personal. Work reference checks verify employment history. Personal reference checks contact individuals supplied by the applicant and ask questions regarding the applicant’s capabilities, skills, and personality.
Education and licensing verification is usually fairly easy to complete. Employers can request transcripts from educational institutions. For any licensing or certification, the licensing or certification body can verify the license or certification held.
Social Security number verification and validation can be achieved by contacting the Social Security Administration. Such a check ensures that the Social Security information is accurate. The Social Security Administration will alert you if the Social Security number has been misused, including if the number belongs to a deceased person or a person in a detention facility.
Just as companies exist that can provide criminal history checks, companies have recently started providing services to search federal and international lists of suspected terrorists. Organizations involved in defense, aviation, technology, and biotechnology fields should consider performing such a check for all applicants.
As any security professional knows, the sensitivity of the information that the applicant will have access to should be the biggest determining factor as to which checks to perform. Organizations should never get lax in their pre-employment applicant screening processes.
Employment Agreements and Policies
Personnel hiring procedures should include signing all the appropriate documents, including government-required documentation, a confidentiality agreement, a nondisclosure agreement (NDA), and the acceptable use policy (AUP). The objective of an NDA is to protect data from unauthorized disclosure. NDAs are generally used to establish data ownership, protect information from disclosure, prevent forfeiture of patent rights, and define handling standards including disposal. Annual participation in security awareness training and other compliance requirements should be included as part of the employment agreement.
An AUP details appropriate use of information systems, handling standards, monitoring, and privacy expectations.
An AUP should be written in language that can be easily and unequivocally understood.
By signing the associated agreement, the user acknowledges, understands, and agrees to the stated rules and obligations.
Organizations usually have a personnel handbook and other hiring information that must be communicated to the employee. The hiring process should include a formal verification that the employee has completed all the training. Employee IDs and passwords are issued at this time.
Code of conduct, conflict of interest, and ethics agreements should also be signed at this time. Also, any non-compete agreements should be verified to ensure that employees do not leave the organization for a competitor. Employees should be given guidelines for periodic performance reviews, compensation, and recognition of achievements.
Employee Onboarding and Offboarding Policies
Onboarding is the process of integrating a new employee with a company and culture as well as providing the tools and information he needs to be successful. Onboarding includes the following:
User orientation is the initial task of completing paperwork (including confidentiality and AUP agreements), introductions, and initial training.
User provisioning is the process of creating user accounts and credentials, assigning access rights and permissions, and providing assets.
Each department should have documented procedures related to user onboarding.
Offboarding is the process for transitioning employees out of an organization and is also referred to as termination. Tasks include
Documenting separation details
Tasks and responsibilities prior to departure
Knowledge transfer
Exit interview
Personnel termination must be handled differently based on whether the termination is friendly or unfriendly. Procedures defined by the human resources department can ensure that the organizational property is returned, user access is removed at the appropriate time, and exit interviews are completed. With unfriendly terminations, organizational procedures must be proactive to prevent damage to organizational assets. The security department should be notified early in the process of an unfriendly termination. Unfriendly termination procedures should include system and facility access termination or disabling prior to employee termination notification as well as security escort from the premises.
Vendor, Consultant, and Contractor Agreements and Controls
Organizations often work with vendors, consultants, and contractors. Any third party that is given access to an organization’s facility should be given limited access to the facility and other organizational assets. An organization should implement appropriate controls to ensure that these third parties do not cause security issues. Third parties, even those that visit frequently, should be escorted within the organization’s facility. If a third party needs more permanent access, a background investigation should be performed, and nondisclosure agreements should be implemented. Monitoring any access to the network and information assets should be done using virtual monitoring and audit logs.
Compliance Policy Requirements
Management must also ensure that appropriate security policies are in place during employment. This includes separation of duties, job rotation, and least privilege. Another management control is mandatory vacations, which requires that employees take their vacations and that another employee performs their job duties during that vacation time. Some positions might require employment agreements to protect the organization and its assets even after the employee is no longer with the organization. These agreements can include NDAs, non-compete clauses, AUPs, and code of conduct and ethics agreements.
Privacy Policy Requirements
Personnel expect a certain amount of privacy even in their workplace. Companies should implement a no-expectation-of-privacy policy that details what areas personnel should consider as not being private, including company email, Internet access, and access to high-security areas. Closed-circuit televisions (CCTVs) and other video recording equipment are becoming commonplace in the workplace. It is considered acceptable to conduct video monitoring of parking areas, work areas, and high-security areas. However, using video monitoring in bathrooms, locker rooms, or other areas is never a good idea.
Security professionals should ensure that personnel are regularly reminded of the no-expectation-of-privacy policy of the organization, which is often accomplished using screen banners. In some cases, they may also want to place notification signs in areas where video monitoring occurs.
Job Rotation
Job rotation ensures that more than one person fulfills the job tasks of a single position within an organization. This job rotation ensures that more than one person is capable of performing those tasks, providing redundancy. It is also an important tool in helping an organization to recognize when fraudulent activities have occurred.
Separation of Duties
Separation of duties ensures that one person is not capable of compromising organizational security. Any activities that are identified as high risk should be divided into individual tasks, which can then be allocated to different personnel or departments. When an organization implements adequate separation of duties, collusion between two or more personnel would be required to carry out fraud against the organization. Split knowledge, a variation of separation of duties, ensures that no single employee knows all the details to perform a task. An example would be two individuals knowing parts of a safe combination. Another variation is dual control, which requires that two employees must be available to complete a specific task to complete the job. An example is two managers being required to turn keys simultaneously in separate locations to launch a missile.
Risk Management Concepts

When implementing risk analysis and risk management, it is important to understand the different concepts associated with this area. This section explains the following terms: asset, asset valuation, vulnerability, threat, threat agent, exploit, risk, exposure, countermeasure, risk appetite, attack, and breach.
This section also discusses risk management policy; risk management team; risk analysis team; risk assessment; implementation; control categories; control types; control assessment, monitoring, and measurement; reporting and continuous improvement; and risk frameworks.
Asset and Asset Valuation
An asset is any resource, product, process, system, or other thing that has value to an organization and must be protected. Physical or tangible assets, including equipment or computers, are assets that can be touched. Intangible assets, including information or intellectual property, are assets that hold value to the organization but often cannot be touched in the physical sense. All organizational assets should be documented.
As part of risk management, all documented assets must be assessed for their value to the organization. There are three basic elements used to determine an asset’s value:
The initial and ongoing cost for purchasing, licensing, developing, and maintaining the physical or information asset
The asset’s value to the enterprise’s operations
The asset’s value established on the external marketplace and estimated value of the intellectual property
Many organizations will also factor in additional elements, including the following:
Value of the asset to adversaries
Cost to replace the asset if lost
Operational and productivity costs incurred if the asset is unavailable
Liability issues if the asset is compromised
No matter which elements are used to determine asset valuation, it is important that this information is documented. When new assets are acquired, they should be documented and assessed to add to the risk management plan. In addition, organizations should reassess assets and their value to the organization at least annually.
Vulnerability
A vulnerability is a weakness. Vulnerabilities can occur in software, hardware, or personnel. An example of a vulnerability is unrestricted access to a folder on a computer. Most organizations implement a vulnerability assessment to identify vulnerabilities.
Threat
A threat is the next logical progression in risk management. A threat occurs when vulnerability is identified or exploited and is a potential danger. A threat would occur when an attacker identified the folder on the computer that has an inappropriate or absent ACL.
Threat Agent
A threat is carried out by a threat agent. Continuing with the example, the attacker who takes advantage of the inappropriate or absent ACL is the threat agent. Keep in mind, though, that threat agents can discover and/or exploit vulnerabilities. Not all threat agents will actually exploit an identified vulnerability.
Exploit
An exploit is when a threat agent successfully takes advantage of a vulnerability.
Risk
A risk is the probability that a threat agent will exploit a vulnerability and the impact if the threat is carried out. Risk is expressed in terms of the likelihood and impact of a threat event. The risk in the vulnerability example would be fairly high if the data residing in the folder is confidential. However, if the folder only contains public data, then the risk would be low. Identifying the potential impact of a risk often requires security professionals to enlist the help of subject matter experts.
Exposure
An exposure occurs when an organizational asset is exposed to losses. If the folder with the inappropriate or absent ACL is compromised by a threat agent, the organization is exposed to the possibility of data exposure and loss.
Countermeasure
A control (sometimes called a countermeasure or safeguard) is a tactic, mechanism, or strategy that accomplishes one or more of the following:
Reduces or eliminates a vulnerability
Reduces or eliminates the likelihood that a threat agent will be able to exploit a vulnerability
Reduces or eliminates the impact of an exploit
For our example, a good countermeasure would be to implement the appropriate ACL and to encrypt the data. The ACL protects the integrity of the data, and the encryption protects the confidentiality of the data.
Countermeasures or controls come in many categories and types. The categories and types of controls are discussed in the “Control Categories” and “Control Types” sections later in this chapter.
All the aforementioned security concepts work together in a relationship that is demonstrated in Figure 1-13.
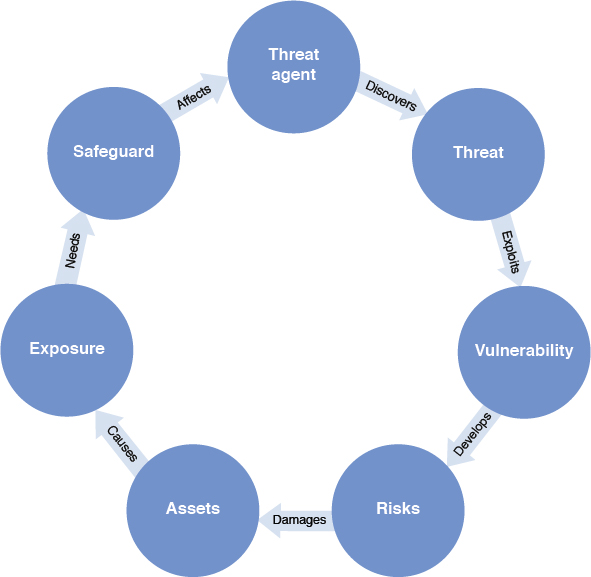
Risk Appetite
Risk appetite is the level of risk an organization is prepared to accept. The risk appetite for an organization can only be defined based on the organization’s needs, and risk appetites will vary from organization to organization.
Attack
An attack is any event that violates an organization’s security or privacy policies. Another word for an attack is an incident. It is important that all attacks are documented and fully analyzed so that the organization can take measures to prevent the attack from happening again. The measures that are taken can also prevent the attack from becoming a breach in the future.
Breach
A breach is an attack that has been successful in reaching its goal. Often, a breach of an organization’s data constitutes a security incident that the organization is legally required to report to affected individuals, regulatory agencies, and sometimes credit reporting agencies and media. It is vital that an organization quickly and effectively respond when an incident does escalate into a data breach. When a data breach has occurred, security professionals should, at minimum, quantify the damage and determine the response.
Risk Management Policy
Senior management must commit to the risk management process. The risk management policy is a formal statement of senior management’s commitment to risk management. The policy also provides risk management direction.
A risk management policy must include the overall risk management plan and list the risk management team and must specifically list the risk management team’s objectives, responsibilities and roles, acceptable level of risk, risk identification process, risk and safeguards mapping, safeguard effectiveness, monitoring process and targets, and future risk analysis plans and tasks.
Risk Management Team
Depending on the size of the organization, the risk management team might be an actual team of employees or might consist only of a single team member. For any organization, the team’s goal is to protect the organization and its assets from risk in the most cost-effective way. Because in most cases the risk management team members are not dedicated solely to risk management, senior management must specifically put a resource allocation measure in place to ensure the success of the risk management process.
Management must also ensure that the members of the risk management team, particularly the team leader, be given the necessary training and tools for risk management. In larger organizations, the team leader should be able to dedicate the majority of his time to the risk management process.
Risk Analysis Team
To perform the most comprehensive risk analysis, the risk analysis team must consist of a representative from as many departments and as many employment levels as possible. Having a diverse risk analysis team ensures that risks from all areas of the organization can be determined.
If the risk analysis team cannot contain members from all departments, the members must interview each department to understand all the threats encountered by that department. During the risk analysis process, the risk analysis team should determine the threat events that could occur, the potential impact of the threats, the frequency of the threats, and the level of confidence in the information gathered.
Risk Assessment
A risk assessment is a tool used in risk management to identify vulnerabilities and threats, assess the impact of those vulnerabilities and threats, and determine which controls to implement. Risk assessment or analysis has four main goals:
Identify assets and asset value.
Identify vulnerabilities and threats.
Calculate threat probability and business impact.
Balance threat impact with countermeasure cost.
Prior to starting the risk assessment, management and the risk assessment team must determine which assets and threats to consider. This process determines the size of the project. The risk assessment team must then provide a report to management on the value of the assets considered. Management can then review and finalize the asset list, adding and removing assets as it sees fit, and then determine the budget of the risk assessment project.
If a risk assessment is not supported and directed by senior management, it will not be successful. Management must define the risk assessment’s purpose and scope and allocate the personnel, time, and monetary resources for the project.
Information and Asset (Tangible/Intangible) Value and Costs
As stated earlier, the first step of any risk assessment is to identify the assets and determine the asset value. Assets are both tangible and intangible. Tangible assets include computers, facilities, supplies, and personnel. Intangible assets include intellectual property, data, and organizational reputation. The value of an asset should be considered in respect to the asset owner’s view. The six following considerations can be used to determine the asset’s value:
Value to owner
Work required to develop or obtain the asset
Costs to maintain the asset
Damage that would result if the asset were lost
Cost that competitors would pay for asset
Penalties that would result if the asset were lost
After determining the value of the assets, you should determine the vulnerabilities and threats to each asset.
Identity Threats and Vulnerabilities
When determining vulnerabilities and threats to an asset, considering the threat agents first is often easiest. Threat agents can be grouped into the following six categories:
Human: Includes both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel
Natural: Includes floods, fires, tornadoes, hurricanes, earthquakes, or other natural disasters or weather events
Technical: Includes hardware and software failure, malicious code, and new technologies
Physical: Includes CCTV issues, perimeter measures failure, and biometric failure
Environmental: Includes power and other utility failure, traffic issues, biological warfare, and hazardous material issues (such as spillage)
Operational: Includes any process or procedure that can affect CIA
When the vulnerabilities and threats have been identified, the loss potential for each must be determined. This loss potential is determined by using the likelihood of the event combined with the impact that such an event would cause. An event with a high likelihood and a high impact would be given more importance than an event with a low likelihood and a low impact. Different types of risk analysis, including quantitative risk analysis and qualitative risk analysis, should be used to ensure that the data that is obtained is maximized.
Risk Assessment/Analysis
Once the risk analysis team is formed, it is time to actually start the risk analysis or assessment process. This process includes two different types of risk analysis: quantitative risk analysis and qualitative risk analysis.
Quantitative Risk Analysis
A quantitative risk analysis assigns monetary and numeric values to all facets of the risk analysis process, including asset value, threat frequency, vulnerability severity, impact, safeguard costs, and so on. Equations are used to determine total and residual risks. The most common equations are for single loss expectancy (SLE) and annual loss expectancy (ALE).

The SLE is the monetary impact of each threat occurrence. To determine the SLE, you must know the asset value (AV) and the exposure factor (EF). The EF is the percent value or functionality of an asset that will be lost when a threat event occurs. The calculation for obtaining the SLE is as follows:
SLE = AV × EF
For example, an organization has a web server farm with an AV of $20,000. If the risk assessment has determined that a power failure is a threat agent for the web server farm and the exposure factor for a power failure is 25%, the SLE for this event equals $5,000.

The ALE is the expected risk factor of an annual threat event. To determine the ALE, you must know the SLE and the annualized rate of occurrence (ARO). The ARO is the estimate of how often a given threat might occur annually. The calculation for obtaining the ALE is as follows:
ALE = SLE × ARO
Using the previously mentioned example, if the risk assessment has determined that the ARO for the power failure of the web server farm is 50%, the ALE for this event equals $2,500. Security professionals should keep in mind that this calculation can be adjusted for different geographical locations. For example, a DNS server located in a small town may have a higher risk of power outage than one in a large city.
Using the ALE, the organization can decide whether to implement controls or not. If the annual cost of the control to protect the web server farm is more than the ALE, the organization could easily choose to accept the risk by not implementing the control. If the annual cost of the control to protect the web server farm is less than the ALE, the organization should consider implementing the control.
Keep in mind that even though quantitative risk analysis uses numeric value, a purely quantitative analysis cannot be achieved because some level of subjectivity is always part of the data. In our example, how does the organization know that damage from the power failure will be 25% of the asset? This type of estimate should be based on historical data, industry experience, and expert opinion.
An advantage of quantitative over qualitative risk analysis is that quantitative uses less guesswork than qualitative. Disadvantages of quantitative risk analysis include the difficulty of the equations, the time and effort needed to complete the analysis, and the level of data that must be gathered for the analysis.
Qualitative Risk Analysis
Qualitative risk analysis does not assign monetary and numeric values to all facets of the risk analysis process. Qualitative risk analysis techniques include intuition, experience, and best practice techniques, such as brainstorming, focus groups, surveys, questionnaires, meetings, and interviews. Although all of these techniques can be used, most organizations will determine the best technique(s) based on the threats to be assessed. Experience and education on the threats are needed.
Each member of the group who has been chosen to participate in the qualitative risk analysis uses his experience to rank the likelihood of each threat and the damage that might result. After each group member ranks the threat possibility, loss potential, and safeguard advantage, data is combined in a report to present to management. All levels of staff should be represented as part of the qualitative risk analysis, but it is vital that some participants in this process have some expertise in risk analysis.
Advantages of qualitative over quantitative risk analysis include qualitative prioritizes the risks and identifies areas for immediate improvement in addressing the threats. Disadvantages of qualitative risk analysis include all results are subjective and a dollar value is not provided for cost-benefit analysis or for budget help.
Most risk analysis includes some hybrid use of both quantitative and qualitative risk analyses. Most organizations favor using quantitative risk analysis for tangible assets and qualitative risk analysis for intangible assets.
Countermeasure (Safeguard) Selection

The criteria for choosing a safeguard is the cost effectiveness of the safeguard or control, for compliance reasons, or to fulfill contractual obligations. Planning, designing, implementing, and maintenance costs need to be included in determining the total cost of a safeguard. To calculate a cost-benefit analysis, use the following equation:
(ALE before safeguard) – (ALE after safeguard) – (Annual cost of safeguard) = Safeguard value
To complete this equation, you have to know the revised ALE after the safeguard is implemented. Implementing a safeguard can improve the ARO but will not completely do away with it. In the example mentioned earlier in the “Quantitative Risk Analysis” section, the ALE for the event is $2,500. Let’s assume that implementing the safeguard reduces the ARO to 10%, so the ALE after the safeguard is calculated as $5,000 × 10% or $500. You could then calculate the safeguard value for a control that costs $1,000 as follows:
$2,500 – $500 – $1,000 = $1,000
Knowing the corrected ARO after the safeguard is implemented is necessary for determining the safeguard value. A legal liability exists if the cost of the safeguard is less than the estimated loss that would occur if the threat is exploited.
Maintenance costs of safeguards are not often fully considered during this process. Organizations should fully research the costs of maintaining safeguards. New staff or extensive staff training often must occur to properly maintain a new safeguard. In addition, the cost of the labor involved must be determined. So the cost of a safeguard must include the actual cost to implement plus any training costs, testing costs, labor costs, and so on. Some of these costs might be hard to identify but a thorough risk analysis will account for these costs.
Inherent Risk Versus Residual Risk
Inherent risk is the risk that an organization could encounter if it decides not to implement any safeguards. As you already know, any environment is never fully secure so you must always deal with residual risk. Residual risk is risk that is left over after safeguards have been implemented. Residual risk is represented using the following equation:
Residual risk = Inherent risk – Countermeasures
This equation is considered to be more conceptual than for actual calculation.
Handling Risk and Risk Response
Risk reduction is the process of altering elements of the organization in response to risk analysis. After an organization understands its total and residual risk, it must determine how to handle the risk.

The following four basic methods are used to handle risk:
Risk avoidance: Terminating the activity that causes a risk or choosing an alternative that is not as risky
Risk transfer: Passing the risk on to a third party, including insurance companies
Risk mitigation: Defining the acceptable risk level the organization can tolerate and reducing the risk to that level
Risk acceptance: Understanding and accepting the level of risk as well as the cost of damages that can occur
Organizations should document all the identified risks and the possible risk responses in a risk register. When an identified risk occurs, security professionals should consult the risk register to determine the steps that should be taken as documented in the risk register.
Implementation
Before implementing any controls that have been chosen as part of the risk analysis process, security professionals must consider the frameworks used for reference, tools deployed, and metrics for managing the controls. These three facets ensure the success of the security architecture. The goal of any risk countermeasure implementation is to improve the organization’s security without negatively impacting performance.
All organizational personnel should be involved in the deployment of countermeasures and controls for risk management. Each individual involved in the implementation will have a unique perspective on the risks of that individual’s position. Documentation and communication across all areas will ensure that each individual business unit’s risk management implementation is as complete as possible.
Control Categories

You implement access controls as a countermeasure to identified vulnerabilities. Access control mechanisms that you can use are divided into seven main categories:
Compensative
Corrective
Detective
Deterrent
Directive
Preventive
Recovery
Any access control that you implement will fit into one or more access control category.
Note
Access controls are also defined by the type of protection they provide. Access control types are discussed in the next section.
Compensative
Compensative controls, also known as compensating controls, are in place to substitute for a primary access control and mainly act as a mitigation to risks. Using compensative controls, you can reduce the risk to a more manageable level. Examples of compensative controls include requiring two authorized signatures to release sensitive or confidential information and requiring two keys owned by different personnel to open a safety deposit box.
Corrective
Corrective controls, also known as correcting controls, are in place to reduce the effect of an attack or other undesirable event. Using corrective controls fixes or restores the entity that is attacked. Examples of corrective controls include installing fire extinguishers, isolating or terminating a connection, implementing new firewall rules, and using server images to restore to a previous state.
Detective
Detective controls, also known as detecting controls, are in place to detect an attack while it is occurring to alert appropriate personnel. Examples of detective controls include motion detectors, intrusion detection systems (IDSs), logs, guards, investigations, and job rotation.
Deterrent
Deterrent controls, also known as deterring controls, deter or discourage an attacker. Via deterrent controls, attacks can be discovered early in the process. Deterrent controls often trigger preventive and corrective controls. Examples of deterrent controls include user identification and authentication, fences, lighting, and organizational security policies, such as an NDA.
Directive
Directive controls, also known as directing controls, specify acceptable practice within an organization. They are in place to formalize an organization’s security directive mainly to its employees. The most popular directive control is an acceptable use policy (AUP) that lists proper (and often examples of improper) procedures and behaviors that personnel must follow. Any organizational security policies or procedures usually fall into this access control category. You should keep in mind that directive controls are only efficient if there is a stated consequence for not following the organization’s directions.
Preventive
Preventive controls, also known as preventing controls, prevent an attack from occurring. Examples of preventive controls include locks, badges, biometric systems, encryption, intrusion prevention systems (IPSs), antivirus software, personnel security, security guards, passwords, and security awareness training.
Recovery
Recovery controls, also known as recovering controls, recover a system or device after an attack has occurred. The primary goal of recovery controls is restoring resources. Examples of recovery controls include disaster recovery plans, data backups, and offsite facilities.
Control Types

Whereas the access control categories classify the access controls based on where they fit in time, access control types divide access controls on their method of implementation. The three types of access controls are
Administrative (management) controls
Logical (technical) controls
Physical controls
In any organization where defense in depth is a priority, access control requires the use of all three types of access controls. Even if you implement the strictest physical and administrative controls, you cannot fully protect the environment without logical controls.
Administrative (Management)
Administrative or management controls are implemented to administer the organization’s assets and personnel and include security policies, procedures, standards, baselines, and guidelines that are established by management. These controls are commonly referred to as soft controls. Specific examples are personnel controls, data classification, data labeling, security awareness training, and supervision.
Security awareness training is a very important administrative control. Its purpose is to improve the organization’s attitude about safeguarding data. The benefits of security awareness training include reduction in the number and severity of errors and omissions, better understanding of information value, and better administrator recognition of unauthorized intrusion attempts. A cost-effective way to ensure that employees take security awareness seriously is to create an award or recognition program.
Table 1-3 lists many administrative controls and includes in which access control categories the controls fit.
Table 1-3 Administrative (Management) Controls
Administrative (Management) Controls |
Compensative |
Corrective |
Detective |
Deterrent |
Directive |
Preventive |
Recovery |
|---|---|---|---|---|---|---|---|
Personnel procedures |
|
|
|
|
|
X |
|
Security policies |
|
|
|
X |
X |
X |
|
Monitoring |
|
|
X |
|
|
|
|
Separation of duties |
|
|
|
|
|
X |
|
Job rotation |
X |
|
X |
|
|
|
|
Information classification |
|
|
|
|
|
X |
|
Security awareness training |
|
|
|
|
|
X |
|
Investigations |
|
|
X |
|
|
|
|
Disaster recovery plan |
|
|
|
|
|
X |
X |
Security reviews |
|
|
X |
|
|
|
|
Background checks |
|
|
X |
|
|
|
|
Termination |
|
X |
|
|
|
|
|
Supervision |
X |
|
|
|
|
|
|
Security professionals should help develop organization policies and procedures to ensure that personnel understand what is expected and how to properly carry out their duties. Applicant evaluation prior to employment is also important to protect the organization. Personnel security, evaluation, and clearances ensure that personnel are given access only to those resources or areas required by their specific roles within the organization. Monitoring and logs ensure that security professionals have a way to analyze behavior. User access should be managed, including user access approval, unique user IDs, periodic reviews of user access, user password processes, and access modification and revocation procedures.
Logical (Technical)
Logical or technical controls are software or hardware components used to restrict access. Specific examples of logical controls include firewalls, IDSs, IPSs, encryption, authentication systems, protocols, auditing and monitoring, biometrics, smart cards, and passwords.
Although auditing and monitoring are logical controls and are often listed together, they are actually two different controls. Auditing is a one-time or periodic event to evaluate security. Monitoring is an ongoing activity that examines either the system or users.
Table 1-4 lists many logical controls and includes in which access control categories the controls fit.
Table 1-4 Logical (Technical) Controls
Logical (Technical) Controls |
Compensative |
Corrective |
Detective |
Deterrent |
Directive |
Preventive |
Recovery |
|---|---|---|---|---|---|---|---|
Password |
|
|
|
|
|
X |
|
Biometrics |
|
|
|
|
|
X |
|
Smart cards |
|
|
|
|
|
X |
|
Encryption |
|
|
|
|
|
X |
|
Protocols |
|
|
|
|
|
X |
|
Firewalls |
|
|
|
|
|
X |
|
IDS |
|
|
X |
|
|
|
|
IPS |
|
|
|
|
|
X |
|
Access control lists |
|
|
|
|
|
X |
|
Routers |
|
|
|
|
|
X |
|
Auditing |
|
|
X |
|
|
|
|
Monitoring |
|
|
X |
|
|
|
|
Data backups |
|
|
|
|
|
|
X |
Antivirus software |
|
|
|
|
|
X |
|
Configuration standards |
|
|
|
|
X |
|
|
Warning banners |
|
|
|
X |
|
|
|
Connection isolation and termination |
|
X |
|
|
|
|
|
Network access, remote access, application access, and computer or device access all fit into this category.
Physical
Physical controls are implemented to protect an organization’s facilities and personnel. Personnel concerns should take priority over all other concerns. Specific examples of physical controls include perimeter security, badges, swipe cards, guards, dogs, man traps, biometrics, and cabling.
Table 1-5 lists many physical controls and includes in which access control categories the controls fit.
Table 1-5 Physical Controls
Physical (Technical) Controls |
Compensative |
Corrective |
Detective |
Deterrent |
Directive |
Preventive |
Recovery |
|---|---|---|---|---|---|---|---|
Fencing |
|
|
|
X |
|
X |
|
Locks |
|
|
|
|
|
X |
|
Guards |
|
|
X |
|
|
X |
|
Fire extinguisher |
|
X |
|
|
|
|
|
Badges |
|
|
|
|
|
X |
|
Swipe cards |
|
|
|
|
|
X |
|
Dogs |
|
|
X |
|
|
X |
|
Man traps |
|
|
|
|
|
X |
|
Biometrics |
|
|
|
|
|
X |
|
Lighting |
|
|
|
X |
|
|
|
Motion detectors |
|
|
X |
|
|
|
|
CCTV |
X |
|
X |
|
|
X |
|
Data backups |
|
|
|
|
|
|
X |
Antivirus software |
|
|
|
|
|
X |
|
Configuration standards |
|
|
|
|
X |
|
|
Warning banner |
|
|
|
X |
|
|
|
Hot, warm, and cold sites |
|
|
|
|
|
|
X |
When controlling physical entry into a building, security professionals should ensure that the appropriate policies are in place for visitor control, including visitor logs, visitor escort, and limitation of visitors’ access to sensitive areas.
Controls Assessment, Monitoring, and Measurement
Security control assessments (SCAs) should be used to verify that the security goals of an organization or a business unit are being met. Vulnerability assessments and penetration tests are considered part of this process and are covered in Chapter 6, “Security Assessment and Testing.” If a security control is implemented that does not meet a security goal, this security control is ineffective. Once the assessment has been conducted, security professionals should use the assessment results to determine which security controls have weaknesses or deficiencies. Security professionals should then work to eliminate the weaknesses or deficiencies.
Security controls should be monitored to ensure that they are always performing in the way expected. As part of this monitoring, security professionals should review all logs. In addition, performance reports should be run and compared with the performance baselines for all security devices and controls. This allows security professionals to anticipate some issues and resolve them before they become critical. The performance measurements that are taken should be retained over time. New baselines need to be captured if significant events or changes occur. For example, if you add 200 new users who will need authentication, you need to capture new authentication baselines to ensure that authentication can still occur in a timely manner. In addition, if you change an authentication setting, such as implementing an account lockout policy, you should monitor the effect that the setting has on performance and security.
Reporting and Continuous Improvement
Security professionals can never just sit back, relax, and enjoy the ride. Security needs are always changing because the “bad guys” never take a day off. It is therefore vital that security professionals continuously work to improve their organization’s security. Tied into this is the need to improve the quality of the security controls currently implemented.
Quality improvement commonly uses a four-step quality model, known as Deming’s Plan–Do–Check–Act cycle. These are the steps in this cycle:
Plan: Identify an area for improvement and make a formal plan to implement it.
Do: Implement the plan on a small scale.
Check: Analyze the results of the implementation to determine whether it made a difference.
Act: If the implementation made a positive change, implement it on a wider scale. Continuously analyze the results.
Other similar guidelines include Six Sigma, Lean, and Total Quality Management. No matter which of these an organization uses, the result should be a continuous cycle of improvement organization-wide.
Risk Frameworks
Risk frameworks can serve as guidelines to any organization that is involved in the risk analysis and management process. Organizations should use these frameworks as guides but should also feel free to customize any plans and procedures they implement to fit their needs.
NIST
To comply with the federal standard, organizations first determine the security category of their information system in accordance with Federal Information Processing Standard (FIPS) Publication 199, Standards for Security Categorization of Federal Information and Information Systems, derive the information system impact level from the security category in accordance with FIPS Publication 200, and then apply the appropriately tailored set of baseline security controls in NIST Special Publication 800-53 Rev. 4.

The NIST risk management framework includes the following steps:
Categorize information systems.
Select security controls.
Implement security controls.
Assess security controls.
Authorize information systems.
Monitor security controls.
These steps implement different NIST publications, including FIPS 199, SP 800-60, FIPS 200, SP 800-53 Rev. 4, SP 800-160, SP 800-53A Rev. 4, SP 800-37, and SP 800-137.
Figure 1-14 shows the NIST risk management framework.

FIPS 199
FIPS 199 defines standards for security categorization of federal information systems. The FIPS 199 nomenclature may be referred to as the aggregate CIA score. This U.S. government standard establishes security categories of information systems used by the federal government.
FIPS 199 requires federal agencies to assess their information systems in the categories of confidentiality, integrity, and availability and rate each system as low, moderate, or high impact in each category. An information system’s overall security category is the highest rating from any category.
A potential impact is low if the loss of any tenet of CIA could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals. This occurs if the organization is able to perform its primary function but not as effectively as normal. This category involves only minor damage, financial loss, or harm.
A potential impact is moderate if the loss of any tenet of CIA could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals. This occurs if the effectiveness with which the organization is able to perform its primary function is significantly reduced. This category involves significant damage, financial loss, or harm.
A potential impact is high if the loss of any tenet of CIA could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals. This occurs if an organization is not able to perform one or more of its primary functions. This category involves major damage, financial loss, or severe harm.
FIPS 199 provides a helpful chart that ranks the levels of CIA for information assets, as shown in Table 1-6.

Table 1-6 Confidentiality, Integrity, and Availability Potential Impact Definitions
CIA Tenet |
Low |
Moderate |
High |
|---|---|---|---|
Confidentiality |
Unauthorized disclosure will have limited adverse effect on the organization. |
Unauthorized disclosure will have serious adverse effect on the organization. |
Unauthorized disclosure will have severe adverse effect on the organization. |
Integrity |
Unauthorized modification will have limited adverse effect on the organization. |
Unauthorized modification will have serious adverse effect on the organization. |
Unauthorized modification will have severe adverse effect on the organization. |
Availability |
Unavailability will have limited adverse effect on the organization. |
Unavailability will have serious adverse effect on the organization. |
Unavailability will have severe adverse effect on the organization. |
It is also important that security professionals and organizations understand the information classification and life cycle. Classification varies depending on whether the organization is a commercial business or a military/government entity.
According to Table 1-6, FIPS 199 defines three impacts (low, moderate, and high) for the three security tenets. But the levels that are assigned to organizational entities must be defined by the organization because only the organization can determine whether a particular loss is limited, serious, or severe.

According to FIPS 199, the security category (SC) of an identified entity expresses the three tenets with their values for an organizational entity. The values are then used to determine which security controls should be implemented. If a particular asset is made up of multiple entities, then you must calculate the SC for that asset based on the entities that make it up. FIPS 199 provides a nomenclature for expressing these values, as shown here:
SCinformation type = {(confidentiality, impact), (integrity, impact), (availability, impact)}
Let’s look at an example of this nomenclature in a real-world example:
SCpublic site = {(confidentiality, low), (integrity, moderate), (availability, high)}
SCpartner site = {(confidentiality, moderate), (integrity, high), (availability, moderate)}
SCinternal site = {(confidentiality, high), (integrity, medium), (availability, moderate)}
Now let’s assume that all of the sites reside on the same web server. To determine the nomenclature for the web server, you need to use the highest values of each of the categories:
SCweb server = {(confidentiality, high), (integrity, high), (availability, high)}
Some organizations may decide to place the public site on a web server and isolate the partner site and internal site on another web server. In this case, the public web server would not need all of the same security controls and would be cheaper to implement than the partner/internal web server.
SP 800-60 Vol. 1 Rev. 1
Security categorization is the key first step in the NIST risk management framework. FIPS 199 works with NIST SP 800-60 to identify information types, establish security impact levels for loss, and assign security categorization for the information types and for the information systems as detailed in the following process:
Identify information types.
Identify mission-based information types based on 26 mission areas, including defense and national security, homeland security, disaster management, natural resources, energy, transportation, education, health, and law enforcement.
Identify management and support information based on 13 lines of business, including regulatory development, planning and budgeting, risk management and mitigation, and revenue collection.
Select provisional impact levels using FIPS 199.
Review provisional impact levels, and finalize impact levels.
Assign system security category.
Let’s look at an example: An information system used for acquisitions contains both sensitive, pre-solicitation phase contract information, and routine administrative information. The management within the contracting organization determines that:
For the sensitive contract information, the potential impact from a loss of confidentiality is moderate, the potential impact from a loss of integrity is moderate, and the potential impact from a loss of availability is low.
For the routine administrative information (non-privacy-related information), the potential impact from a loss of confidentiality is low, the potential impact from a loss of integrity is low, and the potential impact from a loss of availability is low.
The resulting security categories, or SCs, of these information types are expressed as
SC contract information = {(confidentiality, moderate), (integrity, moderate), (availability, low)}
SC administrative information = {(confidentiality, low), (integrity, low), (availability, low)}
The resulting security category of the information system is expressed as
SC acquisition system = {(confidentiality, moderate), (integrity, moderate), (availability, low)}
This represents the high-water mark or maximum potential impact values for each security objective from the information types resident on the acquisition system.
In some cases, the impact level for a system security category will be higher than any security objective impact level for any information type processed by the system.
The primary factors that most commonly raise the impact levels of the system security category above that of its constituent information types are aggregation and critical system functionality. Other factors that can affect the impact level include public information integrity, catastrophic loss of system availability, large interconnecting systems, critical infrastructures and key resources, privacy information, and trade secrets.
The end result of NIST SP 800-60 Vol. 1 Rev 1 is security categorization documentation for every information system. These categories can then be used to complete the business impact analysis (BIA), design the enterprise architecture, design the disaster recovery plan (DRP), and select the appropriate security controls.
SP 800-53 Rev. 4
NIST SP 800-53 Rev. 4 is a security controls development framework developed by the NIST body of the U.S. Department of Commerce.
SP 800-53 Rev. 4 divides the controls into three classes: technical, operational, and management. Each class contains control families or categories.
Table 1-7 lists the NIST SP 800-53 control families.

Table 1-7 NIST SP 800-53 Control Families
Family |
|---|
Access Control (AC) |
Awareness and Training (AT) |
Audit and Accountability (AU) |
Security Assessment and Authorization (CA) |
Configuration Management (CM) |
Contingency Planning (CP) |
Identification and Authentication (IA) |
Incident Response (IR) |
Maintenance (MA) |
Media Protection (MP) |
Physical and Environmental Protection (PE) |
Planning (PL) |
Program Management (PM) |
Personnel Security (PS) |
Risk Assessment (RA) |
System and Services Acquisition (SA) |
System and Communications Protection (SC) |
System and Information Integrity (SI) |
To assist organizations in making the appropriate selection of security controls for information systems, the concept of baseline controls is introduced. Baseline controls are the starting point for the security control selection process described in SP 800-53 Rev. 4 and are chosen based on the security category and associated impact level of information systems determined in accordance with FIPS Publication 199 and FIPS Publication 200, respectively. This publication recommends that the organization assigns responsibility for common controls to appropriate organizational officials and coordinates the development, implementation, assessment, authorization, and monitoring of the controls.

The process in this NIST publication includes the following steps:
Select security control baselines.
Tailor baseline security controls.
Document the control selection process.
Apply the control selection process to new development and legacy systems.
Figure 1-15 shows the NIST security control selection process.
NIST 800-53 Rev. 5 is currently being drafted.
SP 800-160
NIST SP 800-160 defines the systems security engineering framework. It defines, bounds, and focuses the systems security engineering activities, both technical and nontechnical, toward the achievement of stakeholder security objectives and presents a coherent, well-formed, evidence-based case that those objectives have been achieved. It is shown in Figure 1-16.

The framework defines three contexts within which the systems security engineering activities are conducted. These are the problem context, the solution context, and the trustworthiness context.
The problem context defines the basis for a secure system given the stakeholder’s mission, capability, performance needs, and concerns; the constraints imposed by stakeholder concerns related to cost, schedule, risk, and loss tolerance; and other constraints associated with life cycle concepts for the system. The solution context transforms the stakeholder security requirements into system design requirements; addresses all security architecture, design, and related aspects necessary to realize a system that satisfies those requirements; and produces sufficient evidence to demonstrate that those requirements have been satisfied. The trustworthiness context is a decision-making context that provides an evidence-based demonstration, through reasoning, that the system-of-interest is deemed trustworthy based upon a set of claims derived from security objectives.
NIST SP 800-160 uses the same system life cycle processes that were defined in ISO/IEC 15288:2015, as shown in Figure 1-17.

The following naming convention is established for the system life cycle processes. Each process is identified by a two-character designation. Table 1-8 provides a listing of the system life cycle processes and their associated two-character designators.
Table 1-8 System Life Cycle Processes and Codes
ID |
Process |
ID |
Process |
|---|---|---|---|
AQ |
Acquisition |
MS |
Measurement |
AR |
Architecture Definition |
OP |
Operation |
BA |
Business or Mission Analysis |
PA |
Project Assessment and Control |
CM |
Configuration Management |
PL |
Project Planning |
DE |
Design Definition |
PM |
Portfolio Management |
DM |
Decision Management |
QA |
Quality Assurance |
DS |
Disposal |
QM |
Quality Management |
HR |
Human Resource Management |
RM |
Risk Management |
IF |
Infrastructure Management |
SA |
System Analysis |
IM |
Information Management |
SN |
Stakeholder Needs and Requirements Definition |
IN |
Integration |
SP |
Supply |
IP |
Implementation |
SR |
System Requirements Definition |
KM |
Knowledge Management |
TR |
Transition |
LM |
Life Cycle Model Management |
VA |
Validation |
MA |
Maintenance |
VE |
Verification |
Each process listed in Table 1-8 has a unique purpose within the life cycle. Each process has tasks associated with it.
SP 800-37 Rev. 1
NIST SP 800-37 Rev. 1 defines the tasks that should be carried out in each step of the risk management framework as follows:
Step 1. Categorize information system.
Task 1-1: Categorize the information system and document the results of the security categorization in the security plan.
Task 1-2: Describe the information system (including system boundary) and document the description in the security plan.
Task 1-3: Register the information system with appropriate organizational program/management offices.
Step 2. Select security controls.
Task 2-1: Identify the security controls that are provided by the organization as common controls for organizational information systems and document the controls in a security plan (or equivalent document).
Task 2-2: Select the security controls for the information system and document the controls in the security plan.
Task 2-3: Develop a strategy for the continuous monitoring of security control effectiveness and any proposed or actual changes to the information system and its environment of operation.
Task 2-4: Review and approve the security plan.
Step 3. Implement security controls.
Task 3-1: Implement the security controls specified in the security plan.
Task 3-2: Document the security control implementation, as appropriate, in the security plan, providing a functional description of the control implementation (including planned inputs, expected behavior, and expected outputs).
Step 4. Assess security controls.
Task 4-1: Develop, review, and approve a plan to assess the security controls.
Task 4-2: Assess the security controls in accordance with the assessment procedures defined in the security assessment plan.
Task 4-3: Prepare the security assessment report documenting the issues, findings, and recommendations from the security control assessment.
Task 4-4: Conduct initial remediation actions on security controls based on the findings and recommendations of the security assessment report and reassess remediated control(s), as appropriate.
Step 5. Authorize information system.
Task 5-1: Prepare the plan of action and milestones based on the findings and recommendations of the security assessment report excluding any remediation actions taken.
Task 5-2: Assemble the security authorization package and submit the package to the authorizing official for adjudication.
Task 5-3: Determine the risk to organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, other organizations, or the nation.
Task 5-4: Determine if the risk to organizational operations, organizational assets, individuals, other organizations, or the nation is acceptable.
Step 6. Monitor security controls.
Task 6-1: Determine the security impact of proposed or actual changes to the information system and its environment of operation.
Task 6-2: Assess the technical, management, and operational security controls employed within and inherited by the information system in accordance with the organization-defined monitoring strategy.
Task 6-3: Conduct remediation actions based on the results of ongoing monitoring activities, assessment of risk, and outstanding items in the plan of action and milestones.
Task 6-4: Update the security plan, security assessment report, and plan of action and milestones based on the results of the continuous monitoring process.
Task 6-5: Report the security status of the information system (including the effectiveness of security controls employed within and inherited by the system) to the authorizing official and other appropriate organizational officials on an ongoing basis in accordance with the monitoring strategy.
Task 6-6: Review the reported security status of the information system (including the effectiveness of security controls employed within and inherited by the system) on an ongoing basis in accordance with the monitoring strategy to determine whether the risk to organizational operations, organizational assets, individuals, other organizations, or the nation remains acceptable.
Task 6-7: Implement an information system disposal strategy, when needed, which executes required actions when a system is removed from service.
NIST 800-37 Revision 2 is currently being drafted.
SP 800-30 Rev. 1

According to NIST SP 800-30 Rev. 1, common information-gathering techniques used in risk analysis include automated risk assessment tools, questionnaires, interviews, and policy document reviews. Keep in mind that multiple sources should be used to determine the risks to a single asset. NIST SP 800-30 identifies the following steps in the risk assessment process:
Prepare for the assessment.
Conduct assessment.
Identify threat sources and events.
Identify vulnerabilities and predisposing conditions.
Determine likelihood of occurrence.
Determine magnitude of impact.
Determine risk as a combination of likelihood and impact.
Communicate results.
Maintain assessment.
Figure 1-18 shows the risk assessment process according to NIST SP 800-30.
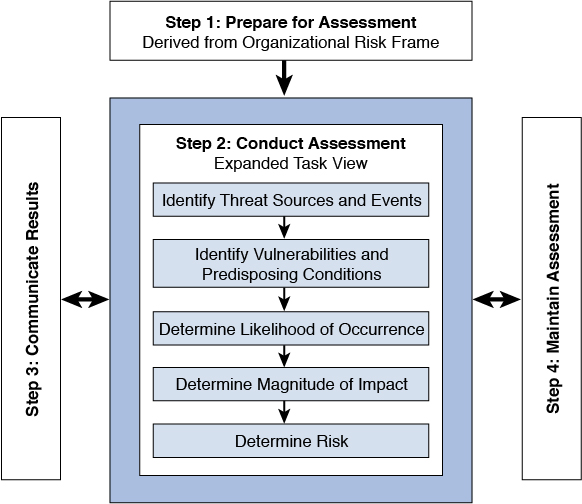
SP 800-39
The purpose of NIST SP 800-39 is to provide guidance for an integrated, organization-wide program for managing information security risk to organizational operations (i.e., mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation resulting from the operation and use of federal information systems. NIST SP 800-39 defines three tiers in an organization.
Tier 1 is the organization view, which addresses risk from an organizational perspective by establishing and implementing governance structures that are consistent with the strategic goals and objectives of organizations and the requirements defined by federal laws, directives, policies, regulations, standards, and missions/business functions. Tier 2 is the mission/business process view, which designs, develops, and implements mission/business processes that support the missions/business functions defined at Tier 1. Tier 3 is the information systems view, which includes operational systems, systems under development, systems undergoing modification, and systems in some phase of the system development life cycle.
Figure 1-19 shows the risk management process applied across all three tiers identified in NIST SP 800-39.

The risk management process involves the following steps:
Frame risk.
Assess risk.
Respond to risk.
Monitor risk.
NIST Framework for Improving Critical Infrastructure Cybersecurity

The NIST Framework for Improving Critical Infrastructure Cybersecurity provides a cybersecurity risk framework. The framework is based on five framework core functions:
Identify (ID): Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
Protect (PR): Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
Detect (DE): Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
Respond (RS): Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
Recover (RC): Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
Within each of these functions, security professionals should define cybersecurity outcomes closely tied to organizational needs and particular activities. Each category is then divided into subcategories that further define specific outcomes of technical and/or management activities. The function and category unique identifiers are shown in Figure 1-20.

Framework implementation tiers describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the framework. The following four tiers are used:
Tier 1: Partial means that risk management practices are not formalized, and risk is managed in an ad hoc and sometimes reactive manner.
Tier 2: Risk Informed means that risk management practices are approved by management but may not be established as organization-wide policy.
Tier 3: Repeatable means that the organization’s risk management practices are formally approved and expressed as policy.
Tier 4: Adaptive means that the organization adapts its cybersecurity practices based on lessons learned and predictive indicators derived from previous and current cybersecurity activities through a process of continuous improvement.
Finally, a framework profile is the alignment of the functions, categories, and subcategories with the business requirements, risk tolerance, and resources of the organization. A profile enables organizations to establish a roadmap for reducing cybersecurity risk that is well aligned with organizational and sector goals, considers legal/regulatory requirements and industry best practices, and reflects risk management priorities.
The following steps illustrate how an organization could use the framework to create a new cybersecurity program or improve an existing program. These steps should be repeated as necessary to continuously improve cybersecurity.
Prioritize and scope.
Orient.
Create a current profile.
Conduct a risk assessment.
Create a target profile.
Determine, analyze, and prioritize gaps.
Implement the action plan.
An organization may repeat the steps as needed to continuously assess and improve its cybersecurity.
ISO/IEC 27005:2011

According to ISO/IEC 27005:2011, the risk management process consists of the following steps:
Context Establishment: Defines the risk management’s boundary.
Risk Analysis (Risk Identification & Estimation phases): Evaluates the risk level.
Risk Assessment (Risk Analysis & Evaluation phases): Analyzes the identified risks and takes into account the objectives of the organization.
Risk Treatment (Risk Treatment & Risk Acceptance phases): Determines how to handle the identified risks.
Risk Communication: Shares information about risk between the decision makers and other stakeholders.
Risk Monitoring and Review: Detects any new risks and maintains the risk management plan.
Figure 1-21 shows the risk management process based on ISO/IEC 27005:2011.

Open Source Security Testing Methodology Manual (OSSTMM)
The Institute for Security and Open Methodologies (ISECOM) published OSSTMM, which was written by Pete Herzog. This manual covers the different kinds of security tests of physical, human (processes), and communication systems, although it does not cover any specific tools that can be used to perform these tests. It defines five risk categorizations: vulnerability, weakness, concern, exposure, and anomaly. Once a risk is detected and verified, it is assigned a risk assessment value.
COSO’s Enterprise Risk Management (ERM) Integrated Framework
COSO broadly defines ERM as “the culture, capabilities and practices integrated with strategy-setting and its execution, that organizations rely on to manage risk in creating, preserving and realizing value.” The ERM framework is presented in the form of a three-dimensional matrix. The matrix includes four categories of objectives across the top: strategic, operations, reporting, and compliance. There are eight components of enterprise risk management. Finally, the organization, its divisions, and business units are depicted as the third dimension of the matrix for applying the framework. The three-dimensional matrix of COSO’s ERM is shown in Figure 1-22.
A Risk Management Standard by the Federation of European Risk Management Associations (FERMA)
FERMA’s A Risk Management Standard provides guidelines for managing risk in an organization. Figure 1-23 shows FERMA’s risk management process as detailed in A Risk Management Standard.
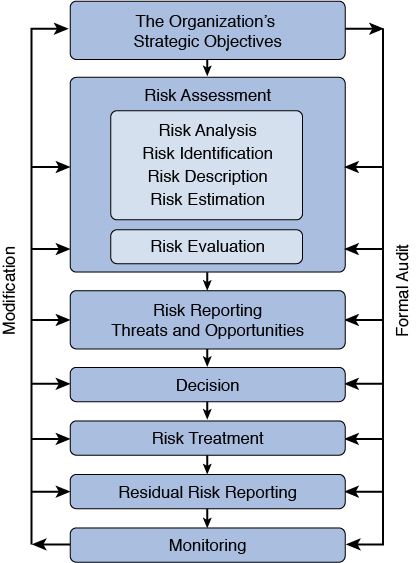
Geographical Threats
Many threats are a function of the geographic location of the office or facility. This section discusses a wide variety of threats and issues, some of which only apply to certain areas. The security professional must be prepared to anticipate and mitigate those issues.
Internal Versus External Threats
When talking about threats to the physical security of assets, we can frame the conversation by threats that appear from outside the organization and those that come from within the organization. Many of the mitigation techniques discussed in the following sections are designed to address maintaining perimeter security or access to the building or room, whereas other techniques are designed to address threats from those who might have some access to the room or building.
For example, an electric fence surrounding the facility is designed to prevent access to the building by those who should not have any access (an external threat), whereas a door lock system on the server room that requires a swipe of the employee card is designed to prevent access by those who are already in the building (an internal threat). Keep this in mind as you read the following sections.
Natural Threats
Many of the physical threats that must be addressed and mitigated are caused by the forces of nature. Building all facilities to withstand the strongest hurricanes, tornadoes, and earthquakes is not economically feasible because in many areas these events happen infrequently if ever. What can be done is to make a realistic assessment of the historical weather conditions of an area and perform a prudent cost/benefit analysis to determine which threats should be addressed and which should be accepted. This section discusses some of the major natural threats.
Hurricanes/Tropical Storms
In certain areas, hurricanes and tropical storms are so frequent and unpredictable that all buildings are required to be capable of withstanding the more moderate instances of these storms. In other areas, doing that makes no sense even though these storms do occur from time to time. The location of the facility should dictate how much is spent in mitigating possible damages from these events.
Tornadoes
Although events of the last few years might seem to contradict this, over the long haul certain areas are more prone to tornadoes than others. A study of the rate and severity of tornadoes in an area from a historical perspective can help to determine measures that make sense for a particular location.
Note
In recent tornado outbreaks, many cellphone towers have been knocked out completely. In rural areas especially, communication with loved ones can be next to impossible. But the problem occurs not just in rural areas. In the Dallas–Fort Worth tornado outbreak in December 2015, it took many individuals up to 48 hours to locate loved ones because of lack of communications. You can imagine how this loss of communication would affect a company, school, or hospital.
Earthquakes
Earthquakes should be treated in the same way as hurricanes, tropical storms, and tornadoes; that is, the location of the specific facility should dictate the amount of preparation and the measures to take to address this risk. For example, facilities in California might give this issue more attention than those in the southeastern United States where these events are extremely rare.
Floods
Always take flooding into consideration because it is an event that can occur with the right circumstances just about anywhere. If at all possible, keep computing systems and equipment off the floor, and build server rooms and wiring closets on raised floors to help prevent damage that could occur in even a small flood.
Volcanoes
Volcanoes, like earthquakes, should be considered if the location warrants. For example, facilities in Hawaii might give this more consideration than facilities in the northeast United States.
System Threats
Some of the threats that exist are not from the forces of nature but from failures in systems that provide basic services, such as electricity and utilities. Although these problems can sometimes arise from events of nature, in this section we discuss guidelines for preparing and dealing with these events, which can occur in any location and in any type of weather conditions.
Electrical
Electricity is the lifeline of the organization and especially in regard to computing systems; outages are not only an inconvenience, but they can also damage equipment and cause loss of data. Moreover, when the plug is pulled, to a large degree the enterprise grinds to a halt in today’s world.
For this reason, all mission-critical systems should have uninterruptible power supplies (UPSs) that can provide power on a short-term basis until the system can be cleanly shut down. In cases where power must be maintained for longer than a matter of minutes, make onsite generators available to provide the power to keep systems running on a longer-term basis until power is restored.
Noise, humidity, and brownouts are also issues that affect the electricity supply. The recommended optimal relative humidity range for computer operations is 40% to 60%. Critical systems must be protected from both power sags and surges. Neither is good for equipment. Line conditioners placed between the system and the power source can help to even out these fluctuations and prevent damage.
Finally, the most prevalent cause of computer center fires is electrical distribution systems. Checking these systems regularly can identify problems before they occur.
Communications
Protecting the physical security of communication, such as email, telephone, and fax systems, is a matter of preventing unauthorized access to the physical communication lines (cables and so on) and physical and logical access to equipment used to manage these systems.
For example, in the case of email, the email servers should be locked away, and access to them over the network must be tightly controlled with usernames and complex passwords.
In the case of fax machines, implementing policies and procedures can prevent sensitive faxes from becoming available to unauthorized persons. In some cases, preventing certain types of information from being transmitted with faxes might be necessary.
Many phone systems now have been merged into the data network using Voice over IP (VoIP). With these systems, routers and switches might be involved in managing the phone system and should be physically locked away and logically protected from network access in the same fashion as email servers. Because email and VoIP both use the data network, ensure that cabling is not exposed to tampering and malicious destruction.
Some additional considerations that can impact disaster recovery are
Maintain fault-tolerant connections to the Internet, such as T1 as the primary connection and a backup fiber connection.
Establish phone connections to employees besides primary organizational phone connections. Know cellphone and home numbers for employee notification.
Establish radio communications over the entire campus with repeater antennas to provide communication during emergencies. Many primary forms of communication (such as phone lines and cellphones) can go down.
Utilities
Some utilities systems, such as gas and water, can be routed into the facility through ducts and tunnels that might provide an unauthorized entry point to the building. Such ducts and tunnels that offer this opportunity should be monitored with sensors and access control mechanisms.
Any critical parts of the systems where cut-off valves and emergency shutdown systems are located should be physically protected from malicious tampering. In some cases covering and protecting these valves and controls using locking cages might be beneficial.
Human-Caused Threats
Although many of the physical threats we face are a function of natural occurrences and random events, some of them are purposeful. This section explores some of the physical threats faced from malicious and careless humans. These threats come from both external forces and internal forces.
Explosions
Explosions can be both intentional and accidental. Intentional explosions can occur as a result of political motivation (covered in more detail in the section “Politically Motivated Threats”) or they can simply be vandalism. Accidental explosions can be the result of a failure to follow procedures and the failure of physical components.
With regard to intentional explosions, the best defense is to prevent access to areas where explosions could do significant damage to the enterprise’s operational components, such as server rooms, wiring closets, and areas where power and utilities enter the building. When an intentional explosion occurs, typically thought has been given to locating the explosive where the most harm can be done, so those areas should get additional physical protection.
Fire
Fires can happen anywhere and thus are a consideration at all times. In Chapter 3, you will learn about both fire suppression and fire detection techniques. Address the threat of fire in the contexts of both an accident and an intentional attack. An auxiliary station alarm might be beneficial in many cases. This mechanism automatically causes an alarm originating in a data center to be transmitted over the local municipal fire or police alarm circuits for relaying to both the local police/fire station and the appropriate headquarters.
Fire extinguishers are classified using the standard system shown in Table 1-9. In Chapter 3, we talk more about fire extinguishers and suppression systems for the various types.
Table 1-9 Fire Extinguisher Classes
Class |
Type of Fire |
|---|---|
Class A |
Ordinary combustibles |
Class B |
Flammable liquids, flammable gases |
Class C |
Electrical equipment |
Class D |
Combustible metals |
Class K |
Cooking oil or fat |
With respect to construction materials, according to (ISC)2, all walls must have a two-hour minimum fire rating in an information processing facility. Knowing that the most prevalent cause of computer center fires is electrical distribution systems is also useful. Regardless of the fire source, the first action to take in the event of a fire is evacuating all personnel.
Vandalism
Vandalism in most cases results in defacement of walls, bathrooms, and such, but when critical components are accessible, it can impact operations. Cut cables and smashed devices are reasons stressed in preventing physical access to these components.
Even when all measures have been taken, vandalism can still cause problems. For example, a purposefully plugged toilet can flood a floor and damage equipment if undetected.
Fraud
In the context of physical security, fraud involves gaining access to systems, equipment, or the facility through deception. For example, a person who enters the facility posing as a serviceman and a person who tailgates and follows an employee through the card system are both forms of fraudulent physical access. Physical access control systems become critical to preventing this type of fraud and the damage it can lead to.
Theft
Preventing physical theft of company assets depends on preventing physical access to the facility. Physical theft is the risk that will most likely affect CIA. For assets that leave the facility, such as laptops, give thought to protecting sensitive data that might exist on them through the use of encryption, preferably through encrypted drives.
Collusion
Collusion occurs when two employees work together to accomplish a theft of some sort that could not be accomplished without their combined knowledge or responsibilities. Use proper separation of duties to prevent a single person from controlling enough of a process to hide their actions.
Limiting the specific accesses of operations personnel forces an operator into collusion with an operator of a different category to have access to unauthorized data. Collusion is much less likely to occur from a statistical standpoint than a single person operating alone. When you consider this fact, the tradeoff in exchanging one danger for another is justified.
Politically Motivated Threats
Although it might seem at times like many more politically motivated threats exist today, these threats have always existed. The enterprise is often unwillingly dragged into these confrontations if they are seen as contributing to whatever the issue of the day might be. These threats can be costly in terms of lost productivity, destruction of company assets, and even physical danger to employees and officers of the company. This section covers some of the major ways these threats can manifest themselves along with measures to take that can lessen or mitigate the risk they present.
An advanced persistent threat (APT) uses a set of stealthy and continuous computer hacking processes, often orchestrated by a person or persons targeting a specific entity. An APT usually targets either private organizations, states, or both for business or political motives.
Strikes
Although strikes might be the least dangerous of the threats in this list, they can still damage the enterprise. In countries like the United States, basic rules of order have been established that prevent the worst of the possible outcomes, but even then an orderly strike can cost productivity and can hurt the image of the company. In other countries, strikes can be much more dangerous, especially when other political issues become intertwined with monetary issues.
Riots
Riots often occur seemingly out of nowhere, although typically an underlying issue explodes at some single incident. These events can be very dangerous as large mobs will often participate in activities that none of the individuals would normally do on their own. Often times the enterprise is seen as a willing participant in some perceived slight or wrong suffered by the rioters. In that case the company and its assets become a large and somewhat easy target.
Civil Disobedience
Civil disobedience is the intentional refusal to obey certain laws, demands, and commands of a government and is commonly, though not always, defined as being nonviolent resistance. One of the typical by-products of this is a disruption of some process to bring attention to the perceived injustice of the law or rule being broken.
It might also manifest itself as an action against some practice by the enterprise that might not be illegal but might be seen by some groups as harmful in some way. When this is the case, the physical security of the facility becomes important as in some cases action might be taken to harm the facility.
Terrorist Acts
Increasingly, the threats of terrorist activity have caused a new focus on not only the security of facilities both at home and abroad but also of the physical safety of workers and officers. In many cases certain industries have found it beneficial to include emergency planning designed to address terrorist acts. Reactions to common scenarios are rehearsed to ensure the best possible outcome in the case of an attack.
Bombing
Bombing of facilities or company assets, once a rare occurrence, is no longer so in many parts of the world today. Increasingly, the enterprise is driven to include such considerations as local disturbance levels and general political unrest in an area before company sites are chosen. In many cases the simple threat of a bomb is enough to engage evacuation plans that are both costly and disruptive. Despite this, evacuation plans that address terrorist threats and bombings have become an integral part of any security policy, especially in certain parts of the world.
Threat Modeling
Earlier in this chapter, in the “Risk Management Concepts” section, we defined vulnerabilities, threats, threat agents, and other concepts. Threat modeling allows an organization to use a structured approach to security and to address the top threats that have the greatest potential impact to the organization first. Threat modeling is used to identify and rate the threats that are most likely to impact an organization.

Threat modeling can be carried out using three different perspectives:
Application-centric threat modeling: This perspective involves using application architecture diagrams to analyze threats.
Asset-centric threat modeling: This perspective involves identifying the assets of an organization and classifying them according to data sensitivity and their intrinsic value to a potential attacker, in order to prioritize risk levels. This method uses attack trees, attack graphs, or displaying patterns to determine how an asset can be attacked.
Attacker-centric threat modeling: This perspective involves profiling an attacker’s characteristics, skills, and motivation to exploit vulnerabilities. Attacker profiles are then used to understand the type of attacker who would be most likely to execute specific types of exploits and implement a mitigation strategy accordingly. Tree diagrams are often used.

No matter which threat modeling method you decide to use, the basic steps in the threat modeling process are as follows:
Identify assets.
Identify threat agents and possible attacks.
Research existing countermeasures in use by the organization.
Identify any vulnerabilities that can be exploited.
Prioritize the identified risks.
Identify countermeasures to reduce the organization’s risk.
Threat Modeling Concepts
When considering threat modeling, security professionals should understand both the attack side and the defense side of any threat. The basic concepts related to the attack side of threat modeling include vulnerability, exploit and attack, attack vector, and threat. The basic concepts related to the defense side of threat modeling include risk, security controls, and security objectives.
Note
Vulnerability, attack, threat, and risk are covered earlier in this chapter in the “Risk Management Concepts” section.
To exploit a vulnerability is to use it to violate security objectives, such as confidentiality, integrity, and availability. The program code or other commands used to exploit a vulnerability are generically referred to as an exploit or an attack. Attacks are either intentional or inadvertent.
An attack vector is a segment of the communication path that an attack uses to access a vulnerability. Each attack vector can be thought of as comprising a source of malicious content, a potentially vulnerable processor of that malicious content, and the nature of the malicious content itself.
Security controls are the management, operational, and technical controls used by information systems to protect the confidentiality, integrity, and availability of the system and its information. All types of security controls were covered earlier in this chapter.
Security objectives are created by organizations to protect the confidentiality, integrity, and availability of assets. Security objectives will vary based on the asset’s value and importance to the organization.
Threat Modeling Methodologies
Threat modeling methodologies have been developed to help organizations to determine the threats that they face and how to best address these threats. Threat methodologies include STRIDE, PASTA, Trike, VAST, and NIST SP 800-154.
STRIDE Model
Developed by Microsoft, STRIDE is a threat classification model that is used to assess the threats in an application. It covers the following six categories:
Spoofing of user identity
Tampering
Repudiation
Information disclosure (privacy breach or data leak)
Denial of service (DoS)
Elevation of privilege
This method usually requires subject matter experts (SMEs) to determine the threats, threat classifications, and relevance of security properties to the elements of a threat model.
Process for Attack Simulation and Threat Analysis (PASTA) Methodology
The PASTA methodology provides a seven-step process for analyzing applications to align business objectives and technical requirements. The steps in the process are as follows:
Business objectives definition
Technical scope definition
Application decomposition
Threat analysis
Vulnerability detection
Attack enumeration
Risk and impact analysis
This method provides a threat identification, enumeration, and scoring process. It is intended to provide an attacker-centric view of the application and infrastructure from which defenders can develop an asset-centric mitigation strategy.
Trike Methodology
Trike is both a methodology and a tool with its basis in a requirements model designed to ensure the level of risk assigned to each asset is classified as acceptable by stakeholders. With this methodology, an implementation model is created and then analyzed to produce a threat model. Risk values are assigned to the identified threats. Mitigating controls are assigned to the vulnerabilities that lead to the identified threats.
The main difference between Trike and STRIDE is that Trike uses a risk-based approach.
Visual, Agile, and Simple Threat (VAST) Model
VAST was created as a result of the shortcomings in the other models and methodologies. VAST threat modeling scales across the infrastructure and entire development portfolio. It is meant to work in an Agile environment and uses both application and operational threat models.
Table 1-10 shows a comparison of the features of the four threat methodologies.
Table 1-10 Threat Modeling Methodology Comparison
What Users Want in a Threat Modeling Methodology |
||||
|
STRIDE |
PASTA |
Trike |
VAST |
|---|---|---|---|---|
Implements application security at design time |
✓ |
✓ |
✓ |
✓ |
Identifies relevant mitigating controls |
✓ |
✓ |
✓ |
✓ |
Directly contributes to risk management |
|
✓ |
✓ |
✓ |
Prioritizes threat mitigation efforts |
|
✓ |
✓ |
✓ |
Encourages collaboration among all stakeholders |
|
|
✓ |
✓ |
Outputs for stakeholders across the organization |
|
|
|
✓ |
Consistent repeatability |
|
|
✓ |
✓ |
Automation of threat modeling process |
|
|
✓ |
✓ |
Integrates into an Agile DevOps environment |
|
|
|
✓ |
Ability to scale across thousands of threat models |
|
|
|
|
NIST SP 800-154

NIST SP 800-154 is a draft publication for data-centric system threat modeling. It includes the following steps:
Identify and characterize the system and data of interest.
Identify and select the attack vectors to be included in the model.
Characterize the security controls for mitigating the attack vectors.
Analyze the threat model.
Most of the actions within the methodology can be addressed in a wide variety of ways in terms of both content (what information is captured) and format/structure (how that information is captured). Organizations should customize as they see fit.
Identifying Threats
Identifying threats and threat actors as part of threat modeling is not much different from identifying threats and vulnerabilities as discussed earlier this chapter, in the “Risk Assessment” section. However, when carrying out threat modeling, you may decide to develop a more comprehensive list of threat actors to assist in scenario development.

Security professionals should analyze all the threats to identify all the actors who pose significant threats to the organization. Examples of the threat actors include both internal and external actors, such as the following:
Internal actors
Reckless employee
Untrained employee
Partner
Disgruntled employee
Internal spy
Government spy
Vendor
Thief
External actors
Anarchist
Competitor
Corrupt government official
Data miner
Government cyber warrior
Irrational individual
Legal adversary
Mobster
Activist
Terrorist
Vandal
These actors can be subdivided into two categories: non-hostile and hostile. Of the actors listed above, three are usually considered non-hostile: reckless employee, untrained employee, and partner. All the other actors should be considered hostile.
An organization needs to analyze each of these threat actors according to set criteria. The organization should give each threat actor a ranking to help determine which ones should be analyzed. Examples of some of the most commonly used criteria include the following:
Skill level: None, minimal, operational, adept
Resources: Individual, team, organization, government
Visibility: Overt, covert, clandestine, don’t care
Objective: Copy, destroy, injure, take, don’t care
Outcome: Acquisition/theft, business advantage, damage, embarrassment, technical advantage
Based on these criteria, the organization must then determine which of the actors it wants to analyze. For example, the organization may choose to analyze all hostile actors who have a skill level of adept and resources of organization or government. Then the list is consolidated to include only the threat actors that fit all these criteria.
Next, the organization must determine what it really cares about protecting. Often this determination is made using some sort of business impact analysis. Once the vital assets are determined, the organization should then select the scenarios that could have a catastrophic impact on the organization by using the objective and outcome values from the threat actor analysis and the asset value and business impact information from the impact analysis.
Potential Attacks
To identify the potential attacks that can occur, an organization must create scenarios that can be fully analyzed. For example, an organization may decide to analyze a situation in which a hacktivist group performs prolonged DoS attacks, causing sustained outages to damage an organization’s reputation. Then a risk assessment should be made for each scenario. (Risk assessment is discussed earlier in this chapter.)
Once all the scenarios are determined, the organization should develop an attack tree for each potential attack. The attack tree should include all the steps and/or conditions that must occur for the attack to be successful. The organization then needs to map security controls to the attack trees.
To determine what security controls can be used, an organization needs to look at industry standards, including NIST SP 800-53 Rev. 4 (discussed earlier in this chapter). Finally, the controls need to be mapped back to the attack tree to ensure that controls are implemented at as many levels of the attack as possible.
Note
Specific attacks are discussed throughout this book. Cryptanalytic attacks are covered in Chapter 3, “Security Architecture and Engineering.” Network attacks are covered in Chapter 4, “Communication and Network Security.” Access control attacks are covered in Chapter 5, “Identity and Access Management (IAM).”
Remediation Technologies and Processes
Security professionals should be prepared as part of any threat modeling to analyze the threats, examine the security controls in place, and make recommendations on remediation technologies and processes. Remediation technologies may simply be used to provide additional protection against an identified threat. In developing remediation processes, however, security professionals or auditors need to analyze internal processes, identify the weakness(es) in the current processes, and revise the current processes or develop new ones that better protect against identified threats. For example, after analyzing the process for being issued a new password, a security professional might realize that it is possible for an attacker to have an internal user’s password reset. The security professional might then establish a process whereby users must provide some identification factors prior to having their password reset.
Security Risks in the Supply Chain
Earlier we discussed corporate acquisitions. This section discusses the security risks in acquiring hardware, software, and services. As part of this discussion, this section covers third-party assessment and monitoring, minimum security requirements, and service-level requirements.
Risks Associated with Hardware, Software, and Services
Organizations acquire hardware, software, and services as part of day-to-day business. The supply chain for tangible property is vital to every organization. An organization should understand all risks for the supply chain and implement a risk management program that is appropriate for it. But the supply chain does not just involve tangible property, such as hardware. It can include information, software, and services as well.
Some of these acquisitions have built-in security mechanisms. However, these security mechanisms are not enough to fully protect the acquisitions. In addition, any security mechanisms need to be regularly updated and perhaps even replaced with more recent, stronger security mechanisms.
Security professionals should be involved in any hardware, software, and service acquisition to ensure that security is an integral part of the decision. If no security advocate is part of the acquisition process, acquisitions are often made that actually put the organization at risk.
As part of the related security considerations, security professionals should develop baseline requirements for acquisitions, train personnel to adapt to security changes with new acquisitions, use common security terms and definitions for acquisitions, and develop a strategy to ensure that acquisitions are minimized.
Third-party Assessment and Monitoring
For many organizations, a third party ensures that an organization complies with industry or governmental standards and regulations. This third party performs analysis of organizational operations and any other area dictated by the certifying or regulating organization. The third party reports all results of its findings to the certifying or regulating organization. The contract with the third party should stipulate that any findings or results should only be communicated with the organization that is being analyzed and with the regulating organization. A third party may also provide assessment and monitoring services as part of an organization’s regular security policy.
A member of high-level management usually manages this process so that the third party is given access as needed. As part of this analysis, the third party might need to perform an onsite assessment, a document exchange, or a process/policy review.
Onsite Assessment
An onsite assessment involves a team from the third party. This team needs access to all aspects of the organization under regulation. This assessment might include observing employees as they perform their day-to-day duties, reviewing records, reviewing documentation, and other tasks. Management should delegate a member of management to which the team can make formal requests.
Document Exchange/Review
A document exchange/review involves transmitting a set of documents to the third party. The process used for the document exchange must be secure on both ends of the exchange.
Process/Policy Review
A process/policy review focuses on a single process or policy within the organization and ensures that the process or policy follows regulations.
Other Third-Party Governance Issues
Third-party governance may apply when an organization employs third parties to provide services to an organization. An example of this is using a public cloud solution, such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS). When using a third-party partner like this, a security professional must ensure that the organization obtains the appropriate SLA. In addition, the security professional must help the organization ensure that the third party implements appropriate due diligence in all aspects that affect the organization. This assurance can be provided only by inspection, review, and assessment of the third-party provider. Finally, a security professional should be aware of any countries or individuals that may have jurisdiction over the third party’s systems.
Minimum Service-Level and Security Requirements
Minimum service-level requirements document the minimum level of service that a provider must maintain. The minimum service-level requirements are usually spelled out in a service-level agreement. SLAs should include provisions that provide minimum performance metrics and noncompliance penalties.
Security professionals should also define the minimum security requirements for any acquisitions made by the organization. For computers, this may be best enforced using network access control (NAC), which defines and implements policies that describe how to secure access to network nodes by devices when they initially attempt to access the network. If a device attempts to connect and does not meet the minimum requirements, it is either denied access or placed on a quarantined network to protect the internal organizational network.
For each different acquisition type, it may be necessary to define separate security policies. For example, mobile devices that are not used may need to be locked in a file cabinet or safe. Keys for company vehicles should not be kept out in the open where they are easy to obtain. Computers that are located in a high-traffic area may need some sort of mechanism that locks the device to the desk. The security controls vary just as much as the acquisition types.
Service-Level Requirements
SLAs are agreements about the ability of a support system to respond to problems within a certain timeframe while providing an agreed level of service. These agreements can be internal between departments or external with service providers. Agreeing on the speed at which various problems are addressed introduces some predictability to the response to problems; this ultimately supports the maintenance of access to resources. The following are some examples of what may be included in an SLA:
Loss of connectivity to the DNS server must be restored within a 30-minute period.
Loss of connectivity to Internet service must be restored within a 5-hour period.
Loss of connectivity of a host machine must be restored within an 8-hour period.

Before an SLA can be written and signed, organizations must negotiate the service-level requirements. If an organization does not have carefully documented requirements, it cannot be sure that the SLA from the vendor will fulfill its needs. Requirements that need to be documented include the following:
Description of service
Hours of service needed
Service interruption process
Availability requirements
Maintenance requirements and allowed downtime
Workload expected
Performance expected
Security professionals need to work with business unit managers when services must be obtained from a third party to ensure that the service-level requirements are documented.
Security Education, Training, and Awareness
Security awareness training, security training, and security education are three terms that are often used interchangeably but are actually three different things. Awareness training reinforces the fact that valuable resources must be protected by implementing security measures.
Levels Required
Security training teaches personnel the skills to enable them to perform their jobs in a secure manner. Awareness training and security training are usually combined as security awareness training, which improves user awareness of security and ensures that users can be held accountable for their actions. Security education is more independent and is targeted at security professionals who require security expertise to act as in-house experts for managing the security programs. Awareness training is the what, security training is the how, and security education is the why.
Security awareness training should be developed based on the audience. In addition, trainers must understand the corporate culture and how it will affect security. The audiences you need to consider when designing training include high-level management, middle management, technical personnel, and regular staff.
For high-level management, the security awareness training must provide a clear understanding of potential risks and threats, effects of security issues on organizational reputation and financial standing, and any applicable laws and regulations that pertain to the organization’s security program. Middle management training should discuss policies, standards, baselines, guidelines, and procedures, particularly how these components map to the individual departments. Also, middle management must understand their responsibilities regarding security. Technical staff should receive technical training on configuring and maintaining security controls, including how to recognize an attack when it occurs. In addition, technical staff should be encouraged to pursue industry certifications and higher education degrees. Regular staff need to understand their responsibilities regarding security so that they perform their day-to-day tasks in a secure manner. With regular staff, providing real-world examples to emphasize proper security procedures is effective.
Personnel should sign a document that indicates they have completed the training and understand all the topics. Although the initial training should occur when personnel is hired, security awareness training should be considered a continuous process, with future training sessions occurring annually at a minimum.
Methods and Techniques
Security education and training can be delivered in a variety of ways. Most mandatory awareness training that must be delivered to all personnel would be best delivered over a digital medium. Many companies specialize in the delivery of security awareness training courses over the Internet, and often these courses can be customized to fit the needs and cover the specific policies of your organization.
Another common method of delivery is live or video-on-demand training. This is particularly useful when providing specialized training to technical personnel. Organizations should ensure that the training they select for technical personnel is up to date with the latest security issues and vulnerability testing and penetration testing techniques. Technical personnel must receive training in the tools that they will regularly use.
No matter the medium selected, it is the responsibility of the organization to ensure that the training covers all of the organization’s policies and any repercussions for noncompliance.
Periodic Content Reviews
New security issues and threats are always cropping up in today’s society. As a result, security professionals should review all the security awareness training and ensure that it is updated to address new security issues and threats. This review should be scheduled to occur at regular intervals.
Exam Preparation Tasks
As mentioned in the section “About the CISSP Cert Guide, Third Edition” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 9, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 1-11 lists a reference of these key topics and the page numbers on which each is found.

Table 1-11 Key Topics for Chapter 1
Key Topic Element |
Description |
Page Number |
|---|---|---|
Paragraph |
Security control frameworks |
|
Security Program Life Cycle |
||
List |
Computer crime concepts |
|
List |
Major legal systems |
|
List |
Licensing and intellectual property |
|
PII List |
||
List |
Information security documents |
|
Levels and Categories of Security Policies |
||
List |
Business continuity and disaster recovery concepts |
|
Paragraph |
Causes of disasters |
|
List |
NIST SP 800-34 Rev. 1 contingency planning steps |
|
List |
BIA steps |
|
List |
Critical asset terms |
|
Section |
Risk Management Concepts |
|
Paragraph |
SLE calculation |
|
Paragraph |
ALE calculation |
|
Paragraph |
Countermeasure selection |
|
List |
Risk handling methods |
|
List |
Access control categories |
|
List |
Access control types |
|
List |
NIST risk management framework steps |
|
FIPS 199 Confidentiality, Integrity, and Availability Potential Impact Definitions |
||
Paragraph |
FIPS 199 security category (SC) of an identified entity explanation |
|
NIST SP 800-53 Control Families |
||
List |
NIST SP 800-53 baseline control process |
|
NIST System Life Cycle Processes and Stages |
||
Paragraph |
NIST SP 800-30 risk assessment process |
|
Paragraph |
NIST Framework for Improving Critical Infrastructure Cybersecurity core functions |
|
List |
ISO/IEC 27005:2011 risk management process |
|
List |
Threat modeling perspectives |
|
List |
Threat modeling process |
|
List |
NIST SP 800-154 data-centric system threat modeling steps |
|
Paragraph |
Threat actors |
|
Paragraph |
SLA requirements documentation |
Complete the Tables and Lists from Memory
Print a copy of Appendix A, “Memory Tables,” or at least the section from this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
annualized loss expectancy (ALE)
annualized rate of occurrence (ARO)
business continuity plan (BCP)
Communications Assistance for Law Enforcement Act (CALEA) of 1994
Computer Fraud and Abuse Act (CFAA) of 1986
continuity of operations plan (COOP)
critical infrastructure protection (CIP) plan
digital rights management (DRM)
Economic Espionage Act of 1996
Electronic Communications Privacy Act (ECPA) of 1986
Federal Information Security Management Act (FISMA) of 2002
Federal Intelligence Surveillance Act (FISA) of 1978
Gramm-Leach-Bliley Act (GLBA) of 1999
Health Care and Education Reconciliation Act of 2010
Health Insurance Portability and Accountability Act (HIPAA)
HITRUST Common Security Framework (CSF)
information system contingency plan (ISCP)
issue-specific security policy
maximum tolerable downtime (MTD)
mean time between failure (MTBF)
organizational security policy
Personal Information Protection and Electronic Documents Act (PIPEDA)
personally identifiable information (PII)
recovery point objective (RPO)
system-specific security policy
The Open Group Architecture Framework (TOGAF)
United States Federal Sentencing Guidelines of 1991
Answer Review Questions
1. Which security principle is the opposite of disclosure?
Integrity
Availability
Confidentiality
Authorization
2. Which of the following controls is an administrative control?
Security policy
CCTV
Data backups
Locks
3. What is a vulnerability?
The entity that carries out a threat
The exposure of an organizational asset to losses
An absence or a weakness of a countermeasure that is in place
A control that reduces risk
4. Which framework uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual)?
Six Sigma
SABSA
ITIL
ISO/IEC 27000 series
5. Which group of threat agents includes hardware and software failure, malicious code, and new technologies?
Human
Natural
Environmental
Technical
6. Which term indicates the monetary impact of each threat occurrence?
ARO
ALE
EF
SLE
7. What is risk avoidance?
Risk that is left over after safeguards have been implemented
Terminating the activity that causes a risk or choosing an alternative that is not as risky
Passing the risk on to a third party
Defining the acceptable risk level the organization can tolerate and reducing the risk to that level
8. Which security policies provide instruction on acceptable and unacceptable activities?
Informative security policies
Regulatory security policies
System-specific security policies
Advisory security policies
9. Which organization role determines the classification level of the information to protect the data for which he is responsible?
Data owner
Data custodian
Security administrator
Security analyst
10. Which type of crime occurs when a computer is used as a tool to help commit a crime?
Computer-assisted crime
Incidental computer crime
Computer-targeted crime
Computer prevalence crime
11. Which access control type reduces the effect of an attack or another undesirable event?
Compensative control
Preventive control
Detective control
Corrective control
12. What is the first stage of the security program life cycle?
Plan and Organize
Implement
Operate and Maintain
Monitor and Evaluate
13. Which of the following frameworks is a two-dimensional model that intersects communication interrogatives (What, Why, Where, and so on) with various viewpoints (Planner, Owner, Designer, and so on)?
SABSA
Zachman Framework
TOGAF
ITIL
14. Which management officer implements and manages all aspects of security, including risk analysis, security policies and procedures, training, and emerging technologies?
CPO
CFO
CSO
CIO
15. Which of the following do organizations have employees sign in order to protect trade secrets?
Trademark
Patent
DRM
NDA
16. Which type of access control type is an acceptable use policy (AUP) most likely considered?
Corrective
Detective
Compensative
Directive
17. What is the legal term used to describe an organization taking all reasonable measures to prevent security breaches and also taking steps to mitigate damages caused by successful breaches?
Due care
Due diligence
Default security posture
Qualitative risk analysis
18. Which threat modeling perspective profiles malicious characteristics, skills, and motivation to exploit vulnerabilities?
Application-centric
Asset-centric
Attacker-centric
Hostile-centric
19. Which of the following is NOT a consideration for security professionals during mergers and acquisitions?
New data types
New technology types
Cost of the merger or acquisition
The other organization’s security awareness training program
20. What is the first step of CRAMM?
Identify threats and vulnerabilities
Identify and value assets
Identify countermeasures
Prioritize countermeasures
21. Which of the following is the process of taking away or removing characteristics from something in order to reduce it to a set of essential characteristics?
Auditing
Accounting
Non-repudiation
Abstraction
22. Which specific plan focuses on restoring an organization’s mission-essential functions (MEFs) at an alternate site and performing those functions for up to 30 days before returning to normal operations?
Continuity of operations plan
Business continuity plan
Crisis communications plan
Cyber incident response plan
23. Which of the following is an information system–focused plan designed to restore operability of the target system, application, or computer facility infrastructure at an alternate site after an emergency?
Occupant emergency plan
Disaster recovery plan
Information system contingency plan
Critical infrastructure protection plan
24. Which of the following is a segment of the communication path that an attack uses to access a vulnerability?
Breach
Threat agent
Attack vector
Countermeasure
25. Which of the following is a six-category threat classification model developed by Microsoft to assess the threats in an application?
VAST
Trike
PASTA
STRIDE
26. What is the first step of the NIST SP 800-154 draft publication for data-centric system threat modeling?
Identify and select the attack vectors to be included in the model.
Identify and characterize the system and data of interest.
Analyze the threat model.
Characterize the security controls for mitigating the attack vectors.
Answers and Explanations
1. c. The opposite of disclosure is confidentiality. The opposite of corruption is integrity. The opposite of destruction is availability. The opposite of disapproval is authorization.
2. a. A security policy is an administrative control. CCTV and locks are physical controls. Data backups are a technical control.
3. c. A vulnerability is an absence or a weakness of a countermeasure that is in place. A threat occurs when a vulnerability is identified or exploited. A threat agent is the entity that carries out a threat. Exposure occurs when an organizational asset is exposed to losses. A countermeasure or safeguard is a control that reduces risk.
4. b. SABSA uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). Six Sigma is a process improvement standard that includes two project methodologies that were inspired by Deming’s Plan–Do–Check–Act cycle. ITIL is a process management development standard that has five core publications: ITIL Service Strategy, ITIL Service Design, ITIL Service Transition, ITIL Service Operation, and ITIL Continual Service Improvement. The ISO/IEC 27000 Series includes a list of standards, each of which addresses a particular aspect of information security management.
5. d. Technical threat agents include hardware and software failure, malicious code, and new technologies. Human threat agents include both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel. Natural threat agents include floods, fires, tornadoes, hurricanes, earthquakes, or other natural disasters or weather events. Environmental threat agents include power and other utility failure, traffic issues, biological warfare, and hazardous material issues (such as spillage).
6. d. Single loss expectancy (SLE) indicates the monetary impact of each threat occurrence. Annualized rate of occurrence (ARO) is the estimate of how often a given threat might occur annually. Annual loss expectancy (ALE) is the expected risk factor of an annual threat event. Exposure factor (EF) is the percent value or functionality of an asset that will be lost when a threat event occurs.
7. b. Risk avoidance is terminating the activity that causes a risk or choosing an alternative that is not as risky. Residual risk is risk that is left over after safeguards have been implemented. Risk transfer is passing the risk on to a third party. Risk mitigation is defining the acceptable risk level the organization can tolerate and reducing the risk to that level.
8. d. Advisory security policies provide instruction on acceptable and unacceptable activities. Informative security policies provide information on certain topics and act as an educational tool. Regulatory security policies address specific industry regulations, including mandatory standards. System-specific security policies address security for a specific computer, network, technology, or application.
9. a. The data owner determines the classification level of the information to protect the data for which he or she is responsible. The data custodian implements the information classification and controls after they are determined. The security administrator maintains security devices and software. The security analyst analyzes the security needs of the organizations and develops the internal information security governance documents.
10. a. A computer-assisted crime occurs when a computer is used as a tool to help commit a crime. An incidental computer crime occurs when a computer is involved in a computer crime without being the victim of the attack or the attacker. A computer-targeted crime occurs when a computer is the victim of an attack in which the sole purpose is to harm the computer and its owner. A computer prevalence crime occurs due to the fact that computers are so widely used in today’s world.
11. d. A corrective control reduces the effect of an attack or other undesirable event. A compensative control substitutes for a primary access control and mainly acts as mitigation to risks. A preventive control prevents an attack from occurring. A detective control detects an attack while it is occurring to alert appropriate personnel.
12. a. The four stages of the security program life cycle, in order, are as follows:
Plan and Organize
Implement
Operate and Maintain
Monitor and Evaluate
13. b. The Zachman Framework is a two-dimensional model that intersects communication interrogatives (What, Why, Where, and so on) with various viewpoints (Planner, Owner, Designer, and so on). It is designed to help optimize communication between the various viewpoints during the creation of the security architecture.
14. c. The chief security officer (CSO) is the officer that leads any security effort and reports directly to the chief executive officer (CEO). The chief privacy officer (CPO) is the officer responsible for private information and usually reports directly to the chief information officer (CIO). The chief financial officer (CFO) is the officer responsible for all financial aspects of an organization. The CFO reports directly to the CEO and must also provide financial data for the shareholders and government entities. The CIO is the officer responsible for all information systems and technology used in the organization and reports directly to the CEO or CFO.
15. d. Most organizations that have trade secrets attempt to protect these secrets using nondisclosure agreements (NDAs). These NDAs must be signed by any entity that has access to information that is part of the trade secret. A trademark is an intellectual property type that ensures that the symbol, sound, or expression that identifies a product or an organization is protected from being used by another. A patent is an intellectual property type that covers an invention described in a patent application and is granted to an individual or company. Digital rights management (DRM) is used by hardware manufacturers, publishers, copyright holders, and individuals to control the use of digital content. This often also involves device controls.
16. d. The most popular directive control is an acceptable use policy (AUP) that lists proper (and often examples of improper) procedures and behaviors that personnel must follow. Corrective controls are in place to reduce the effect of an attack or other undesirable event. Examples of corrective controls include installing fire extinguishers and implementing new firewall rules. Detective controls are in place to detect an attack while it is occurring to alert appropriate personnel. Examples of detective controls include motion detectors, IDSs, or guards. Compensative controls are in place to substitute for a primary access control and mainly act as a mitigation to risks. Examples of compensative controls include requiring two authorized signatures to release sensitive or confidential information and requiring two keys owned by different personnel to open a safety deposit box.
17. a. Due care is a legal term that is used when an organization took all reasonable measures to prevent security breaches and also took steps to mitigate damages caused by successful breaches. Due diligence is a legal term that is used when an organization investigated all vulnerabilities. The default security posture is the default security posture used by the organization. An allow-by-default security posture permits access to any data unless a need exists to restrict access. A deny-by-default security posture is much stricter because it denies any access that is not explicitly permitted. Qualitative risk analysis is a method of analyzing risk whereby intuition, experience, and best practice techniques are used to determine risk.
18. c. Attacker-centric threat modeling profiles an attacker’s characteristics, skills, and motivation to exploit vulnerabilities. Application-centric threat modeling uses application architecture diagrams to analyze threats. Asset-centric threat modeling uses attack trees, attack graphs, or displaying patterns to determine how an asset can be attacked. Hostile describes one of two threat actor categories: non-hostile and hostile.
19. c. A security professional should not be concerned with the cost of a merger or an acquisition. A security professional should only be concerned with issues that affect security and leave financial issues to financial officers.
20. b. CRAMM review includes three steps:
Identify and value assets.
Identify threats and vulnerabilities and calculate risks.
Identify and prioritize countermeasures.
21. d. Abstraction is the process of taking away or removing characteristics from something to reduce it to a set of essential characteristics. Auditing is the process of providing a manual or systematic measurable technical assessment of a system or application. Accounting is the process whereby auditing results are used to hold users and organizations accountable for their actions or inaction. Non-repudiation is the assurance that a user cannot deny an action.
22. a. A continuity of operations plan (COOP) is a plan that focuses on restoring an organization’s mission-essential functions (MEFs) at an alternate site and performing those functions for up to 30 days before returning to normal operations. A business continuity plan (BCP) is a plan that focuses on sustaining an organization’s mission/business processes during and after a disruption A crisis communications plan is a plan that documents standard procedures for internal and external communications in the event of a disruption using a crisis communications plan. It also provides various formats for communications appropriate to the incident. A cyber incident response plan is a plan that establishes procedures to address cyber attacks against an organization’s information system(s).
23. b. A disaster recovery plan (DRP) is an information system–focused plan designed to restore operability of the target system, application, or computer facility infrastructure at an alternate site after an emergency. An occupant emergency plan (OEP) is a plan that outlines first-response procedures for occupants of a facility in the event of a threat or incident to the health and safety of personnel, the environment, or property. An information system contingency plan (ISCP) provides established procedures for the assessment and recovery of a system following a system disruption. A critical infrastructure protection (CIP) plan is a set of policies and procedures that serve to protect and recover assets and mitigate risks and vulnerabilities.
24. c. An attack vector is a segment of the communication path that an attack uses to access a vulnerability. A breach is an attack that has been successful in reaching its goal. A threat is carried out by a threat agent. Not all threat agents will actually exploit an identified vulnerability. A countermeasure reduces the potential risk. Countermeasures are also referred to as safeguards or controls.
25. d. Developed by Microsoft, STRIDE is a threat classification model that is used to assess the threats in an application. It covers the following six categories:
Spoofing of user identity
Tampering
Repudiation
Information disclosure (privacy breach or data leak)
Denial of service (DoS)
Elevation of privilege
The Visual, Agile, and Simple Threat (VAST) Model was created as a result of the shortcomings in the other models and methodologies. VAST threat modeling scales across the infrastructure and entire development portfolio. Trike is both a methodology and a tool with its basis in a requirements model designed to ensure the level of risk assigned to each asset is classified as acceptable by stakeholders. The Process for Attack Simulation and Threat Analysis (PASTA) methodology provides a seven-step process for analyzing applications to align business objectives and technical requirements. It is intended to provide an attacker-centric view of the application and infrastructure from which defenders can develop an asset-centric mitigation strategy.
26. b. NIST SP 800-154 is a draft publication for data-centric system threat modeling. It includes the following steps:
Identify and characterize the system and data of interest.
Identify and select the attack vectors to be included in the model.
Characterize the security controls for mitigating the attack vectors.
Analyze the threat model.
Most of the actions within the methodology can be addressed in a wide variety of ways in terms of both content (what information is captured) and format/structure (how that information is captured).
