Chapter 9
Practice Test 1
-
NIST SP800-53 discusses a set of security controls as what type of security tool?
- A configuration list
- A threat management strategy
- A baseline
- The CIS standard
-
Ed has been tasked with identifying a service that will provide a low-latency, high-performance, and high-availability way to host content for his employer. What type of solution should he seek out to ensure that his employer’s customers around the world can access their content quickly, easily, and reliably?
- A hot site
- A CDN
- Redundant servers
- A P2P CDN
-
Which one of the following is not a function of a forensic device controller?
- Preventing the modification of data on a storage device
- Returning data requested from the device
- Reporting errors sent by the device to the forensic host
- Blocking read commands sent to the device
-
Mike is building a fault-tolerant server and wishes to implement RAID 1. How many physical disks are required to build this solution?
- 1
- 2
- 3
- 5
-
Which Kerberos service generates a new ticket and session keys and sends them to the client?
- KDC
- TGT
- AS
- TGS
-
Communication systems that rely on start and stop flags or bits to manage data transmission are known as what type of communication?
- Analog
- Digital
- Synchronous
- Asynchronous
-
What type of motion detector uses high microwave frequency signal transmissions to identify potential intruders?
- Infrared
- Heat-based
- Wave pattern
- Capacitance
-
Susan sets up a firewall that keeps track of the status of the communication between two systems, and allows a remote system to respond to a local system after the local system starts communication. What type of firewall is Susan using?
- A static packet filtering firewall
- An application-level gateway firewall
- A stateful packet inspection firewall
- A circuit-level gateway firewall
Questions 9–11 refer to the following scenario:
Ben owns a coffeehouse and wants to provide wireless Internet service for his customers. Ben’s network is simple and uses a single consumer grade wireless router and a cable modem connected via a commercial cable data contract. Using this information about Ben’s network, answer the following questions.
-
How can Ben provide access control for his customers without having to provision user IDs before they connect while also gathering useful contact information for his business purposes?
- WPA2 PSK
- A captive portal
- Require customers to use a publicly posted password like “BensCoffee.”
- Port security
-
Ben intends to run an open (unencrypted) wireless network. How should he connect his business devices?
- Run WPA2 on the same SSID.
- Set up a separate SSID using WPA2.
- Run the open network in Enterprise mode.
- Set up a separate wireless network using WEP.
-
After implementing the solution from the first question, Ben receives a complaint about users in his cafe hijacking other customers’ web traffic, including using their usernames and passwords. How is this possible?
- The password is shared by all users, making traffic vulnerable.
- A malicious user has installed a Trojan on the router.
- A user has ARP spoofed the router, making all traffic broadcast to all users.
- Open networks are unencrypted, making traffic easily sniffable.
-
Which one of the following is not a mode of operation for the Data Encryption Standard?
- CBC
- CFB
- OFB
- AES
-
Tom is tuning his security monitoring tools in an attempt to reduce the number of alerts received by administrators without missing important security events. He decides to configure the system to only report failed login attempts if there are five failed attempts to access the same account within a one-hour period of time. What term best describes the technique that Tom is using?
- Thresholding
- Sampling
- Account lockout
- Clipping
-
Sally has been tasked with deploying an authentication, authorization, and accounting server for wireless network services in her organization, and needs to avoid using proprietary technology. What technology should she select?
- OAuth
- RADIUS
- TACACS
- TACACS+
-
An accounting clerk for Christopher’s Cheesecakes does not have access to the salary information for individual employees but wanted to know the salary of a new hire. He pulled total payroll expenses for the pay period before the new person was hired and then pulled the same expenses for the following pay period. He computed the difference between those two amounts to determine the individual’s salary. What type of attack occurred?
- Aggregation
- Data diddling
- Inference
- Social engineering
-
Alice would like to have read permissions on an object and knows that Bob already has those rights and would like to give them to herself. Which one of the rules in the Take-Grant protection model would allow her to complete this operation if the relationship exists between Alice and Bob?
- Take rule
- Grant rule
- Create rule
- Remote rule
-
During a log review, Danielle discovers a series of logs that show login failures:
Jan 31 11:39:12 ip-10-0-0-2 sshd[29092]: Invalid user admin from remotehost passwd=aaaaaaaa Jan 31 11:39:20 ip-10-0-0-2 sshd[29098]: Invalid user admin from remotehost passwd=aaaaaaab Jan 31 11:39:23 ip-10-0-0-2 sshd[29100]: Invalid user admin from remotehost passwd=aaaaaaac Jan 31 11:39:31 ip-10-0-0-2 sshd[29106]: Invalid user admin from remotehost passwd=aaaaaaad Jan 31 20:40:53 ip-10-0-0-254 sshd[30520]: Invalid user admin from remotehost passwd=aaaaaaadWhat type of attack has Danielle discovered?
- A pass-the-hash attack
- A brute-force attack
- A man-in-the-middle attack
- A dictionary attack
-
What property of a relational database ensures that two executing transactions do not affect each other by storing interim results in the database?
- Atomicity
- Isolation
- Consistency
- Durability
-
Kim is the system administrator for a small business network that is experiencing security problems. She is in the office in the evening working on the problem and nobody else is there. As she is watching, she can see that systems on the other side of the office that were previously behaving normally are now exhibiting signs of infection. What type of malware is Kim likely dealing with?
- Virus
- Worm
- Trojan horse
- Logic bomb
-
Which one of the following attack types takes advantage of a vulnerability in the network fragmentation function of some operating systems?
- Smurf
- Land
- Teardrop
- Fraggle
-
Which of the following sequences properly describes the TCP 3-way handshake?
- SYN, ACK, SYN/ACK
- PSH, RST, ACK
- SYN, SYN/ACK, ACK
- SYN, RST, FIN
-
Which one of the following technologies is not normally a capability of Mobile Device Management (MDM) solutions?
- Remotely wiping the contents of a mobile device
- Assuming control of a nonregistered BYOD mobile device
- Enforcing the use of device encyrption
- Managing device backups
-
Jim is implementing an IDaaS solution for his organization. What type of technology is he putting in place?
- Identity as a Service
- Employee ID as a service
- Cloud based RADIUS
- OAuth
-
Gina recently took the CISSP certification exam and then wrote a blog post that included the text of many of the exam questions that she experienced. What aspect of the (ISC)2 code of ethics is most directly violated in this situation?
- Advance and protect the profession.
- Act honorably, honestly, justly, responsibly, and legally.
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Provide diligent and competent service to principals.
-
Gordon is conducting a risk assessment for his organization and determined the amount of damage that flooding is expected to cause to his facilities each year. What metric has Gordon identified?
- ALE
- ARO
- SLE
- EF
-
Greg would like to implement application control technology in his organization. He would like to limit users to installing only approved software on their systems. What type of application control would be appropriate in this situation?
- Blacklisting
- Graylisting
- Whitelisting
- Bluelisting
-
Frank is the security administrator for a web server that provides news and information to people located around the world. His server received an unusually high volume of traffic that it could not handle and was forced to reject requests. Frank traced the source of the traffic back to a botnet. What type of attack took place?
- Denial of service
- Reconaissance
- Compromise
- Malicious insider
-
In the database table shown here, which column would be the best candidate for a primary key?
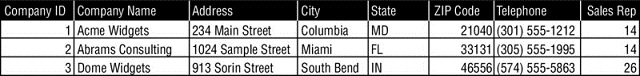
- Company ID
- Company Name
- ZIP Code
- Sales Rep
-
Information about an individual like their name, Social Security number, date and place of birth, or their mother’s maiden name is an example of what type of protected information?
- PHI
- Proprietary Data
- PII
- EDI
-
Bob is configuring egress filtering on his network, examining traffic destined for the Internet. His organization uses the public address range 12.8.195.0/24. Packets with which one of the following destination addresses should Bob permit to leave the network?
- 12.8.195.15
- 10.8.15.9
- 192.168.109.55
- 129.53.44.124
-
How many possible keys exist in a cryptographic algorithm that uses 6-bit encryption keys?
- 12
- 16
- 32
- 64
-
What problem drives the recommendation to physically destroy SSD drives to prevent data leaks when they are retired?
- Degaussing only partially wipes the data on SSDs.
- SSDs don’t have data remanence.
- SSDs are unable to perform a zero fill.
- The built-in erase commands are not completely effective on some SSDs.
-
GAD Systems is concerned about the risk of hackers stealing sensitive information stored on a file server. They choose to pursue a risk mitigation strategy. Which one of the following actions would support that strategy?
- Encrypting the files
- Deleting the files
- Purchasing cyberliability insurance
- Taking no action
-
How should samples be generated when assessing account management practices?
- They should be generated by administrators.
- The last 180 days of accounts should be validated.
- Sampling should be conducted randomly.
- Sampling is not effective, and all accounts should be audited.
-
The International Safe Harbor Privacy Principles includes seven tenets. Which of the following lists correctly identifies all seven?
- Awareness, selection, control, security, data integrity, access, enforcement
- Notice, choice, onward transfer, security, data integrity, access, enforcement
- Privacy, security, control, notification, data integrity, access, enforcement
- Submission, editing, updates, confidential, integrity, security, access
-
In what type of software testing does the attacker have complete knowledge of the system implementation prior to beginning the test?
- Black box
- Blue box
- Gray box
- White box
-
What type of log is shown in the figure?
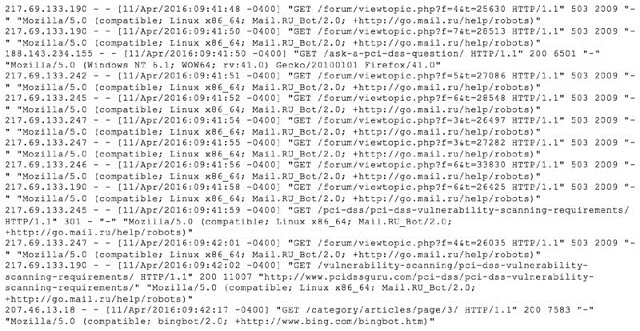
- Firewall log
- Change log
- Application log
- System log
-
Captain Crunch, famous phone phreak, was known for using a toy whistle to generate the 2600 Hz tones that phone trunk systems used to communicate. What is the common name for a phreaking tool with this capability?
- A black box
- A red box
- A blue box
- A white box
-
When an attacker calls an organization’s help desk and persuades them to reset a password for them due to the help desk employee’s trust and willingness to help, what type of attack succeeded?
- A human Trojan
- Social engineering
- Phishing
- Whaling
-
When a user attempts to log into their online account, Google sends a text message with a code to their cell phone. What type of verification is this?
- Knowledge-based authentication
- Dynamic knowledge–based authentication
- Out-of-band identity proofing
- Risk-based identity proofing
-
What mathematical operation, when substituted for the blank lines shown here, would make the equations correct?
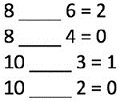
- MOD
- XOR
- NAND
- DIV
Questions 42–44 refer to the following scenario:
The organization that Ben works for has a traditional onsite Active Directory environment that uses a manual provisioning process for each addition to their 350-employee company. As the company adopts new technologies, they are increasingly using Software as a Service applications to replace their internally developed software stack.
Ben has been tasked with designing an identity management implementation that will allow his company to use cloud services while supporting their existing systems. Using the logical diagram shown here, answer the following questions about the identity recommendations Ben should make.
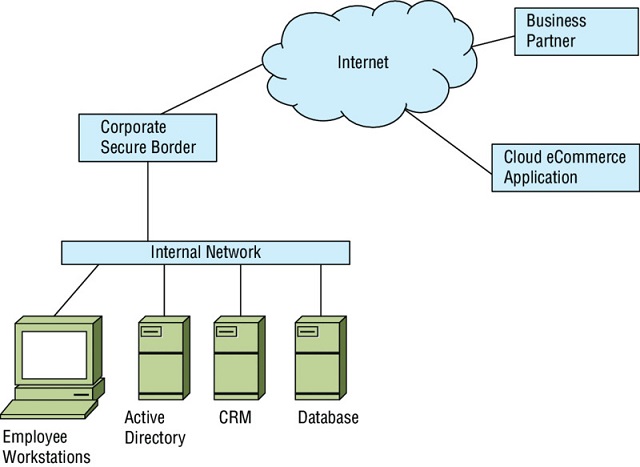
-
If availability of authentication services is the organization’s biggest priority, what type of identity platform should Ben recommend?
- Onsite
- Cloud based
- Hybrid
- Outsourced
-
If Ben needs to share identity information with the business partner shown, what should he investigate?
- Single sign-on
- Multifactor authentication
- Federation
- IDaaS
-
What technology is likely to be involved when Ben’s organization needs to provide authentication and authorization assertions to their e-commerce cloud partner?
- Active Directory
- SAML
- RADIUS
- SPML
-
Dave is responsible for password security in his organization and would like to strengthen the security of password files. He would like to defend his organization against the use of rainbow tables. Which one of the following techniques is specifically designed to frustrate the use of rainbow tables?
- Password expiration policies
- Salting
- User education
- Password complexity policies
-
Which one of the following is a single system designed to attract attackers because it seemingly contains sensitive information or other attractive resources?
- Honeynet
- Darknet
- Honeypot
- Pseudoflaw
-
When evaluating biometric devices, what is another term used to describe the equal error rate?
- FAR
- FRR
- CER
- ERR
-
A smart card is an example of what type of authentication factor?
- Type 1
- Type 2
- Type 3
- Type 4
-
Sean suspects that an individual in his company is smuggling out secret information despite his company’s careful use of data loss prevention systems. He discovers that the suspect is posting photos, including the one shown here, to public Internet message boards. What type of technique may the individuals be using to hide messages inside this image?

- Watermarking
- VPN
- Steganography
- Covert timing channel
-
Roger is concerned that a third-party firm hired to develop code for an internal application will embed a backdoor in the code. The developer retains rights to the intellectual property and will only deliver the software in its final form. Which one of the following languages would be least susceptible to this type of attack because it would provide Roger with code that is human-readable in its final form?
- JavaScript
- C
- C++
- Java
-
Jesse is looking at the
/etc/passwdfile on a system configured to use shadowed passwords. What should she expect to see in the password field of this file?- Plaintext passwords
- Encrypted passwords
- Hashed passwords
- x
-
Ping of Death, Smurf attacks, and ping floods all abuse features of what important protocol?
- IGMP
- UDP
- IP
- ICMP
-
What principle states that an individual should make every effort to complete his or her responsibilities in an accurate and timely manner?
- Least privilege
- Separation of duties
- Due care
- Due diligence
-
Cable modems, ISDN, and DSL are all examples of what type of technology?
- Baseband
- Broadband
- Digital
- Broadcast
-
What penetration testing technique can best help assess training and awareness issues?
- Port scanning
- Discovery
- Social engineering
- Vulnerability scanning
-
Bill implemented RAID level 5 on a server that he operates using a total of three disks. How many disks may fail without the loss of data?
- 0
- 1
- 2
- 3
-
Data is sent as bits at what layer of the OSI model?
- Transport
- Network
- Data Link
- Physical
-
Bert is considering the use of an infrastructure as a service cloud computing partner to provide virtual servers. Which one of the following would be a vendor responsibility in this scenario?
- Maintaining the hypervisor
- Managing operating system security settings
- Maintaining the host firewall
- Configuring server access control
-
When Ben records data, then replays it against his test website to verify how it performs based on a real production workload, what type of performance monitoring is he undertaking?
- Passive
- Proactive
- Reactive
- Replay
-
What technology ensures that an operating system allocates separate memory spaces used by each application on a system?
- Abstraction
- Layering
- Data hiding
- Process isolation
-
Alan is considering the use of new identification cards in his organization that will be used for physical access control. He comes across a sample card and is unsure of the technology. He breaks it open and sees the following internal construction. What type of card is this?

- Smart card
- Proximity card
- Magnetic stripe
- Phase-two card
-
Mark is planning a disaster recovery test for his organization. He would like to perform a live test of the disaster recovery facility but does not want to disrupt operations at the primary facility. What type of test should Mark choose?
- Full interruption test
- Checklist review
- Parallel test
- Tabletop exercise
-
Which one of the following is not a principle of the Agile approach to software development?
- The best architecture, requirements, and designs emerge from self-organizing teams.
- Deliver working software infrequently, with an emphasis on creating accurate code over longer timelines.
- Welcome changing requirements, even late in the development process.
- Simplicity is essential.
-
During a security audit, Susan discovers that the organization is using hand geometry scanners as the access control mechanism for their secure data center. What recommendation should Susan make about the use of hand geometry scanners?
- They have a high FRR, and should be replaced.
- A second factor should be added because they are not a good way to reliably distinguish individuals.
- The hand geometry scanners provide appropriate security for the data center and should be considered for other high-security areas.
- They may create accessibility concerns and an alternate biometric system should be considered.
-
Colleen is conducting a business impact assessment for her organization. What metric provides important information about the amount of time that the organization may be without a service before causing irreparable harm?
- MTD
- ALE
- RPO
- RTO
-
An attack that changes a symlink on a Linux system between the time that an account’s rights to the file are verified and the file is accessed is an example of what type of attack?
- Unlinking
- Tick/tock
- setuid
- TOC/TOU
-
An authentication factor that is “something you have,” and that typically includes a microprocessor and one or more certificates, is what type of authenticator?
- A smart card
- A token
- A Type I validator
- A Type III authenticator
-
What term best describes an attack that relies on stolen or falsified authentication credentials to bypass an authentication mechanism?
- Spoofing
- Replay
- Masquerading
- Modification
-
What speed is a T1 line?
- 64 Kbps
- 128 Kbps
- 1.544 Mbps
- 44.736 Mbps
-
Owen recently designed a security access control structure that prevents a single user from simultaneously holding the role required to create a new vendor and the role required to issue a check. What principle is Owen enforcing?
- Two-person control
- Least privilege
- Separation of duties
- Job rotation
-
Denise is preparing for a trial relating to a contract dispute between her company and a software vendor. The vendor is claiming that Denise made a verbal agreement that amended their written contract. What rule of evidence should Denise raise in her defense?
- Real evidence rule
- Best evidence rule
- Parol evidence rule
- Testimonial evidence rule
-
While Lauren is monitoring traffic on two ends of a network connection, she sees traffic that is inbound to a public IP address show up inside of the production network bound for an internal host that uses an RFC 1918 reserved address. What technology should she expect is in use at the network border?
- NAT
- VLANs
- S/NAT
- BGP
-
Which of the following statements about SSAE-16 is not true?
- It mandates a specific control set.
- It is an attestation standard.
- It is used for external audits.
- It uses a framework, including SOC 1, SOC 2, and SOC 3 reports.
-
What does a constrained user interface do?
- It prevents unauthorized users from logging in.
- It limits the data visible in an interface based on the content.
- It limits the access a user is provided based on what activity they are performing.
- It limits what users can do or see based on privileges.
-
Greg is building a disaster recovery plan for his organization and would like to determine the amount of time that it should take to restore a particular IT service after an outage. What variable is Greg calculating?
- MTO
- RTO
- RPO
- SLA
-
In object-oriented programming, what type of variable exists only once and shares the same value across all instances of an object?
- Instance variable
- Member variable
- Class variable
- Global variable
-
What type of fire extinguisher is useful against liquid-based fires?
- Class A
- Class B
- Class C
- Class D
-
The company Chris works for has notifications posted at each door reminding employees to be careful to not allow people to enter when they do. Which type of controls best describes this?
- Detective
- Physical
- Preventive
- Directive
-
Which one of the following principles is not included in the International Safe Harbor Provisions?
- Access
- Security
- Enforcement
- Nonrepudiation
-
What group is eligible to receive safe harbor protection under the terms of the Digital Millennium Copyright Act (DMCA)?
- Music producers
- Book publishers
- Internet service providers
- Banks
-
Alex is the system owner for the HR system at a major university. According to NIST SP 800-18, what action should he take when a significant change occurs in the system?
- He should develop a data confidentiality plan.
- He should update the system security plan.
- He should classify the data the system contains.
- He should select custodians to handle day-to-day operational tasks.
Questions 82–84 refer to the following scenario:
Alex has been with the university he works at for over 10 years. During that time, he has been a system administrator and a database administrator, and he has worked in the university’s help desk. He is now a manager for the team that runs the university’s web applications. Using the provisioning diagram shown here, answer the following questions.
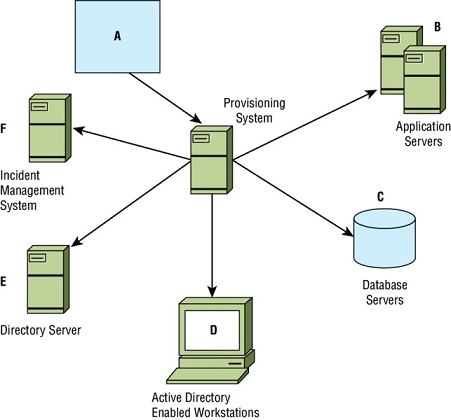
-
If Alex hires a new employee and the employee’s account is provisioned after HR manually inputs information into the provisioning system based on data Alex provides via a series of forms, what type of provisioning has occurred?
- Discretionary account provisioning
- Workflow-based account provisioning
- Automated account provisioning
- Self-service account provisioning
-
Alex has access to B, C, and D. What concern should he raise to the university’s identity management team?
- The provisioning process did not give him the rights he needs.
- He has excessive privileges.
- Privilege creep may be taking place.
- Logging is not properly enabled.
-
When Alex changes roles, what should occur?
- He should be de-provisioned and a new account should be created.
- He should have his new rights added to his existing account.
- He should be provisioned for only the rights that match his role.
- He should have his rights set to match those of the person he is replacing.
-
Robert is reviewing a system that has been assigned the EAL2 evaluation assurance level under the Common Criteria. What is the highest level of assurance that he may have about the system?
- It has been functionally tested.
- It has been structurally tested.
- It has been formally verified, designed, and tested.
- It has been semiformally designed and tested.
-
Adam is processing an access request for an end user. What two items should he verify before granting the access?
- Separation and need to know
- Clearance and endorsement
- Clearance and need to know
- Second factor and clearance
-
During what phase of the electronic discovery reference model does an organization ensure that potentially discoverable information is protected against alteration or deletion?
- Identification
- Preservation
- Collection
- Production
-
Nessus, OpenVAS, and SAINT are all examples of what type of tool?
- Port scanners
- Patch management suites
- Port mappers
- Vulnerability scanners
-
Harry would like to access a document owned by Sally stored on a file server. Applying the subject/object model to this scenario, who or what is the object of the resource request?
- Harry
- Sally
- File server
- Document
-
What is the process that occurs when the session layer removes the header from data sent by the transport layer?
- Encapsulation
- Packet unwrapping
- De-encapsulation
- Payloading
-
Which of the following tools is best suited to testing known exploits against a system?
- Nikto
- Ettercap
- Metasploit
- THC Hydra
-
What markup language uses the concepts of a Requesting Authority, a Provisioning Service Point, and a Provisioning Service Target to handle its core functionality?
- SAML
- SAMPL
- SPML
- XACML
-
What type of risk assessment uses tools such as the one shown here?
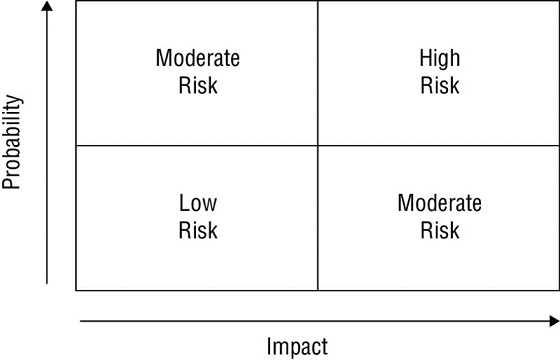
- Quantitative
- Loss expectancy
- Financial
- Qualitative
-
MAC models use three types of environments. Which of the following is not a mandatory access control design?
- Hierarchical
- Bracketed
- Compartmentalized
- Hybrid
-
What level of RAID is also called disk striping with parity?
- RAID 0
- RAID 1
- RAID 5
- RAID 10
-
Sally is wiring a gigabit Ethernet network. What cabling choices should she make to ensure she can use her network at the full 1000 Mbps she wants to provide to her users?
- Cat 5 and Cat 6
- Cat 5e and Cat 6
- Cat 4e and Cat 5e
- Cat 6 and Cat 7
-
Which one of the following is typically considered a business continuity task?
- Business impact assessment
- Alternate facility selection
- Activation of cold sites
- Restoration of data from backup
-
Robert is the network administrator for a small business and recently installed a new firewall. After seeing signs of unusually heavy network traffic, he checked his intrusion detection system, which reported that a Smurf attack was under way. What firewall configuration change can Robert make to most effectively prevent this attack.
- Block the source IP address of the attack.
- Block inbound UDP traffic.
- Block the destination IP address of the attack.
- Block inbound ICMP traffic.
-
Which one of the following types of firewalls does not have the ability to track connection status between different packets?
- Stateful inspection
- Application proxy
- Packet filter
- Next generation
-
Which of the following is used only to encrypt data in transit over a network and cannot be used to encrypt data at rest?
- TKIP
- AES
- 3DES
- RSA
-
What type of fuzzing is known as intelligent fuzzing?
- Zzuf
- Mutation
- Generational
- Code based
-
Matthew is experiencing issues with the quality of network service on his organization’s network. The primary symptom is that packets are occasionally taking too long to travel from their source to their destination. What term describes the issue Matthew is facing?
- Latency
- Jitter
- Packet loss
- Interference
-
Which of the following multifactor authentication technologies provides both low management overhead and flexibility?
- Biometrics
- Software tokens
- Synchronous hardware tokens
- Asynchronous hardware tokens
-
What type of testing would validate support for all the web browsers that are supported by a web application?
- Regression testing
- Interface testing
- Fuzzing
- White box testing
-
Kathleen is implementing an access control system for her organization and builds the following array:
- Reviewers: update files, delete files
- Submitters: upload files
- Editors: upload files, update files
- Archivists: delete files
What type of access control system has Kathleen implemented?
- Role-based access control
- Task-based access control
- Rule-based access control
- Discretionary access control
-
Alan is installing a fire suppression system that will kick in after a fire breaks out and protect the equipment in the data center from extensive damage. What metric is Alan attempting to lower?
- Likelihood
- RTO
- RPO
- Impact
-
Alan’s Wrenches recently developed a new manufacturing process for its product. They plan to use this technology internally and not share it with others. They would like it to remain protected for as long as possible. What type of intellectual property protection is best suited for this situation?
- Patent
- Copyright
- Trademark
- Trade secret
-
Ben wants to interface with the National Vulnerability Database using a standardized protocol. What option should he use to ensure that the tools he builds work with the data contained in the NVD?
- XACML
- SCML
- VSML
- SCAP
-
Which of the following is not one of the three components of the DevOps model?
- Software development
- Change management
- Quality assurance
- Operations
-
In the figure shown here, Harry’s request to read the data file is blocked. Harry has a Secret security clearance and the data file has a Top Secret classification. What principle of the Bell-LaPadula model blocked this request?
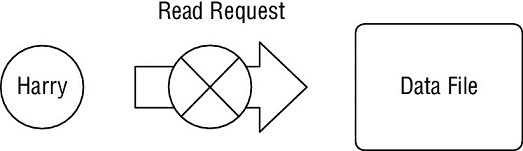
- Simple Security Property
- Simple Integrity Property
- *-Security Property
- Discretionary Security Property
-
Norm is starting a new software project with a vendor that uses an SDLC approach to development. When he arrives on the job, he receives a document that has the sections shown here. What type of planning document is this?
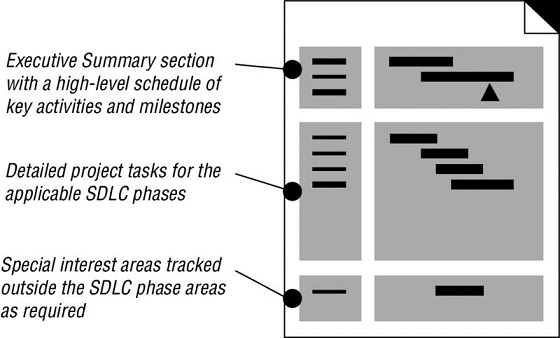
- Functional requirements
- Work breakdown structure
- Test analysis report
- Project plan
-
Kolin is searching for a network security solution that will allow him to help reduce zero-day attacks while using identities to enforce a security policy on systems before they connect to the network. What type of solution should Kolin implement?
- A firewall
- An NAC system
- An intrusion detection system
- Port security
-
Gwen comes across an application that is running under a service account on a web server. The service account has full administrative rights to the server. What principle of information security does this violate?
- Need to know
- Separation of duties
- Least privilege
- Job rotation
-
Which of the following is not a type of structural coverage?
- Statement
- Trace
- Loop
- Data flow
-
Which of the following tools is best suited to the information gathering phase of a penetration test?
- Whois
- zzuf
- Nessus
- Metasploit
Questions 116–118 refer to the following scenario:
During a web application vulnerability scanning test, Steve runs Nikto against a web server he believes may be vulnerable to attacks. Using the Nikto output shown here, answer the following questions.
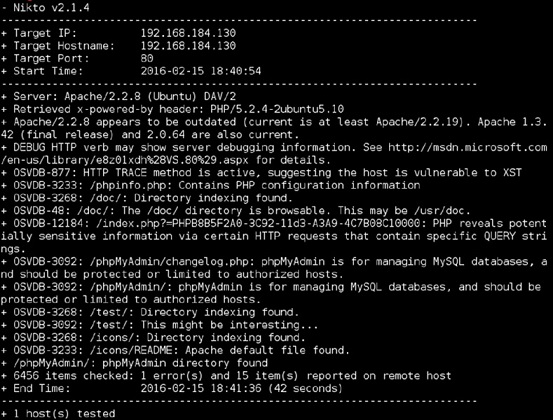
-
Why does Nikto flag the
/testdirectory?- The
/testdirectory allows administrative access to PHP. - It is used to store sensitive data.
- Test directories often contain scripts that can be misused.
- It indicates a potential compromise.
- The
-
Why does Nikto identify directory indexing as an issue?
- It lists files in a directory.
- It may allow for XDRF.
- Directory indexing can result in a denial-of-service attack.
- Directory indexing is off by default, potentially indicating compromise.
-
Nikto lists OSVDB-877, noting that the system may be vulnerable to XST. What would this type of attack allow an attacker to do?
- Use cross-site targeting.
- Steal a user’s cookies.
- Counter SQL tracing.
- Modify a user’s TRACE information.
-
Which one of the following memory types is considered volatile memory?
- Flash
- EEPROM
- EPROM
- RAM
-
Ursula believes that many individuals in her organization are storing sensitive information on their laptops in a manner that is unsafe and potentially violates the organization’s security policy. What control can she use to identify the presence of these files?
- Network DLP
- Network IPS
- Endpoint DLP
- Endpoint IPS
-
In what cloud computing model does the customer build a cloud computing environment in his or her own data center or build an environment in another data center that is for the customer’s exclusive use?
- Public cloud
- Private cloud
- Hybrid cloud
- Shared cloud
-
Which one of the following technologies is designed to prevent a hard drive from becoming a single point of failure in a system?
- Load balancing
- Dual-power supplies
- IPS
- RAID
-
Alice wants to send Bob a message with the confidence that Bob will know the message was not altered while in transit. What goal of cryptography is Alice trying to achieve?
- Confidentiality
- Nonrepudiation
- Authentication
- Integrity
-
What network topology is shown here?
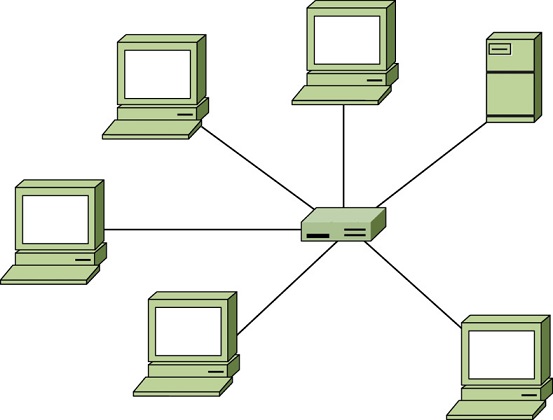
- A ring
- A bus
- A star
- A mesh
-
Monica is developing a software application that calculates an individual’s body mass index for use in medical planning. She would like to include a control on the field where the physician enters an individual’s weight to ensure that the weight falls within an expected range. What type of control should Monica use?
- Fail open
- Fail secure
- Limit check
- Buffer bounds
-
Fred’s data role requires him to maintain system security plans and to ensure that system users and support staff get the training they need about security practices and acceptable use. What is the role that Fred is most likely to hold in the organization?
- Data owner
- System owner
- User
- Custodian
-
Sally is using IPSec’s ESP component in transport mode. What important information should she be aware of about transport mode?
- Transport mode provides full encryption of the entire IP packet.
- Transport mode adds a new, unencrypted header to ensure that packets reach their destination.
- Transport mode does not encrypt the header of the packet.
- Transport mode provides no encryption, only tunnel mode provides encryption.
-
Which one of the following is not a key process area for the Repeatable phase of the Software Capability Maturity Model (SW-CMM)?
- Software Project Planning
- Software Quality Management
- Software Project Tracking
- Software Subcontract Management
-
Ben wants to provide predictive information about his organization’s risk exposure in an automated way as part of an ongoing organizational risk management plan. What should he use to do this?
- KRIs
- Quantitative risk assessments
- KPIs
- Penetration tests
-
In the image shown here, what does system B send to system A at step 2 of the three-way TCP handshake?
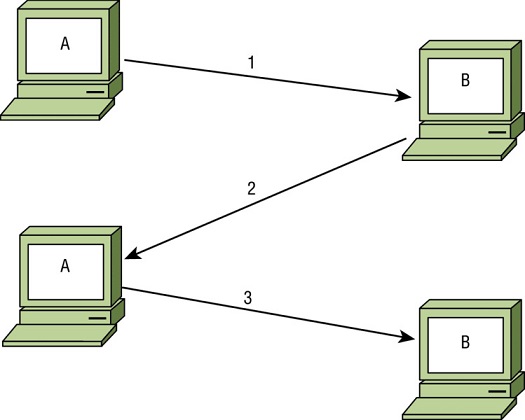
- SYN
- ACK
- FIN/ACK
- SYN/ACK
-
Chris is conducting reconnaissance on a remote target and discovers that pings are allowed through his target’s border firewall. What can he learn by using ping to probe the remote network?
- Which systems respond to ping, a rough network topology, and potentially the location of additional firewalls
- A list of all of the systems behind the target’s firewall
- The hostnames and time to live (TTL) for each pingable system, and the ICMP types allowed through the firewall
- Router advertisements, echo request responses, and potentially which hosts are tarpitted
-
What access management concept defines what rights or privileges a user has?
- Identification
- Accountability
- Authorization
- Authentication
-
Which one of the following is not a classification level commonly found in commercial data classification schemes?
- Secret
- Sensitive
- Confidential
- Public
-
Files, databases, computers, programs, processes, devices, and media are all examples of what?
- Subjects
- Objects
- File stores
- Users
-
Danielle is testing tax software, and part of her testing process requires her to input a variety of actual tax forms to verify that the software produces the right answers. What type of testing is Danielle performing?
- Use case testing
- Dynamic testing
- Fuzzing
- Misuse testing
-
What is the standard term of protection for a copyrighted work by a known author?
- 95 years
- 120 years
- 70 years from the death of the author
- 100 years from the death of the author
-
IP addresses like 10.10.10.10 and 172.19.24.21 are both examples of what type of IP address?
- Public IP addresses
- Prohibited IP addresses
- Private IP addresses
- Class B IP ranges
-
What flaw is a concern with preset questions for cognitive passwords?
- It prevents the use of tokens.
- The question’s answer may be easy to find on the Internet.
- Cognitive passwords require users to think to answer the question, and not all users may be able to solve the problems presented.
- Cognitive passwords don’t support long passwords.
-
In the Clark-Wilson integrity model, what type of process is authorized to modify constrained items?
- CDI
- UDI
- IVP
- TP
-
Kay is selecting an application management approach for her organization. Employees need the flexibility to install software on their systems, but Kay wants to prevent them from installing certain prohibited packages. What type of approach should she use?
- Antivirus
- Whitelist
- Blacklist
- Heuristic
-
Data relating to the past, present, or future payment for the provision of healthcare to an individual is what type of data per HIPAA?
- PCI
- Personal billing data
- PHI
- Personally identifiable information (PII)
-
Yagis, panel, cantennas, and parabolic antennas are all examples of what type of antenna?
- Omnidirectional
- Rubber duck or base antenna
- Signal boosting
- Directional
-
Function, statement, branch, and condition are all types of what?
- Penetration testing methodologies
- Fuzzing techniques
- Code coverage measures
- Synthetic transaction analysis
-
What is the minimum number of people who should be trained on any specific business continuity plan implementation task?
- 1
- 2
- 3
- 5
-
Cameron is responsible for backing up his company’s primary file server. He configured a backup schedule that performs full backups every Monday evening at 9:00 and incremental backups on other days of the week at that same time. How many files will be copied in Wednesday’s backup?

- 1
- 2
- 5
- 6
-
Susan uses a span port to monitor traffic to her production website, and uses a monitoring tool to identify performance issues in real time. What type of monitoring is she conducting?
- Passive monitoring
- Active monitoring
- Synthetic monitoring
- Signature-based monitoring
-
The type of access granted to an object, and the actions that you can take on or with the object, are examples of what?
- Permissions
- Rights
- Priviliges
- Roles
-
Which one of the following would be considered an example of Infrastructure as a Service cloud computing?
- Payroll system managed by a vendor and delivered over the web
- Application platform managed by a vendor that runs customer code
- Servers provisioned by customers on a vendor-managed virtualization platform
- Web-based email service provided by a vendor
Questions 149–151 refer to the following scenario.
Darcy is an information security risk analyst for Roscommon Agricultural Products. She is currently trying to decide whether the company should purchase an upgraded fire suppression system for their primary data center. The data center facility has a replacement cost of $2 million.
After consulting with actuaries, data center managers, and fire subject matter experts, Darcy determined that a typical fire would likely require the replacement of all equipment inside the building but not cause significant structural damage. Together, they estimated that recovering from the fire would cost $750,000. They also determined that the company can expect a fire of this magnitude once every 50 years.
-
Based on the information in this scenario, what is the exposure factor for the effect of a fire on the Roscommon Agricultural Products data center?
- 7.5%
- 15.0%
- 27.5%
- 37.5%
-
Based on the information in this scenario, what is the annualized rate of occurrence for a fire at the Roscommon Agricultural Products data center?
- 0.002
- 0.005
- 0.02
- 0.05
-
Based on the information in this scenario, what is the annualized loss expectancy for a tornado at the Roscommon Agricultural Products data center?
- $15,000
- $25,000
- $75,000
- $750,000
-
Two TCP header flags are rarely used. Which two are you unlikely to see in use in a modern network?
- CWR and ECE
- URG and FIN
- ECE and RST
- CWR and URG
-
Which one of the following is not a tape rotation strategy commonly used in disaster recovery plans?
- Tower of Hanoi
- Key Rotation
- Grandfather, Father, Son
- First In, First Out
-
Fran is a web developer who works for an online retailer. Her boss asked her to create a way that customers can easily integrate themselves with Fran’s company’s site. They need to be able to check inventory in real time, place orders, and check order status programatically without having to access the web page. What can Fran create to most directly facilitate this interaction?
- API
- Web scraper
- Data dictionary
- Call center
-
What type of power issue occurs when a facility experiences a momentary loss of power?
- Fault
- Blackout
- Sag
- Brownout
-
Lauren’s team of system administrators each deal with hundreds of systems with varying levels of security requirements and find it difficult to handle the multitude of usernames and passwords they each have. What type of solution should she recommend to ensure that passwords are properly handled and that features like logging and password rotation occur?
- A credential management system
- A strong password policy
- Separation of duties
- Single sign-on
-
Ed’s Windows system can’t connect to the network and
ipconfigshows the following: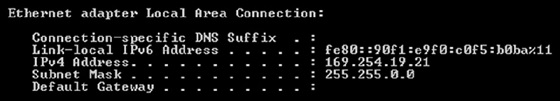
What has occurred on the system?
- The system has been assigned in invalid IP address by its DHCP server.
- The system has a manually assigned IP address.
- The system has failed to get a DHCP address and has assigned itself an address.
- The subnet mask is set incorrectly and the system cannot communicate with the gateway.
-
What term is commonly used to describe initial creation of a user account in the provisioning process?
- Enrollment
- Clearance verification
- Background checks
- Initialization
-
As part of her ongoing duties related to her company’s security program, Susan’s reports to management include the number of repeated audit findings. This information is an example of what type of useful measure?
- Key risk indicator
- Safeguard metrics
- Key performance indicator
- Audit tracking indicators
-
There is a significant conflict between the drive for profit and the security requirements that Olivia’s organization has standardized. Olivia’s role means that decreased usability and loss of profit due to her staff’s inability to use the system is her major concern. What is the most likely role that Olivia plays in her organization?
- Business manager
- Information security analyst
- Data processor
- Mission owner
-
Tom believes that a customer of his Internet service provider has been exploiting a vulnerability in his system to read the email messages of other customers. If true, what law did the customer most likely violate?
- ECPA
- CALEA
- HITECH
- Privacy Act
-
In the ring protection model shown here, what ring contains user programs and applications?
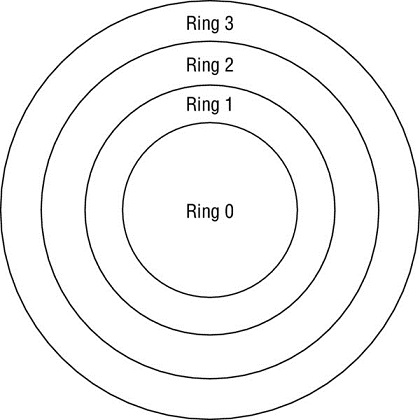
- Ring 0
- Ring 1
- Ring 2
- Ring 3
-
Metrics like the attack vector, complexity, exploit maturity, and how much user interaction is required are all found in what scoring system?
- CVE
- CVSS
- CNA
- NVD
-
In which of the following circumstances does an individual not have a reasonable expectation of privacy?
- Placing a telephone call on your cell phone
- Sending a letter through the U.S. mail
- Sending an email at work
- Retrieving your personal voicemail
-
During which of the following disaster recovery tests does the team sit together and discuss the response to a scenario but not actually activate any disaster recovery controls?
- Checklist review
- Full interruption test
- Parallel test
- Tabletop exercise
-
Susan wants to integrate her website to allow users to use accounts from sites like Google. What technology should she adopt?
- Kerberos
- LDAP
- OpenID
- SESAME
-
Tom is conducting a business continuity planning effort for Orange Blossoms, a fruit orchard located in Central Florida. During the assessment process, the committee determined that there is a small risk of snow in the region but that the cost of implementing controls to reduce the impact of that risk is not warranted. They elect to not take any specific action in response to the risk. What risk management strategy is Orange Blossoms pursuing?
- Risk mitigation
- Risk transference
- Risk avoidance
- Risk acceptance
-
Fred needs to run a network cable for over a kilometer. What wiring option should he choose to ensure that he doesn’t encounter issues?
- 10Base5
- 10BaseT
- STP
- Fiber optic
-
Jack’s organization is a multinational nonprofit that has small offices in many developing countries throughout the world. They need to implement an access control system that allows flexibility and which can work despite poor Internet connectivity at their locations. What is the best type of access control design for Jack’s organization?
- Centralized access control
- Mandatory access control
- Decentralized access control
- Rule-based access control
-
What U.S. government classification label is applied to information that, if disclosed, could cause serious damage to national security, and also requires that the damage that would be caused is able to be described or identified by the classification authority?
- Classified
- Secret
- Confidential
- Top Secret
Questions 171–174 refer to the following scenario.
Mike and Renee would like to use an asymmetric cryptosystem to communicate with each other. They are located in different parts of the country but have exchanged encryption keys by using digital certificates signed by a mutually trusted certificate authority.
-
When the certificate authority (CA) created Renee’s digital certificate, what key was contained within the body of the certificate?
- Renee’s public key
- Renee’s private key
- CA’s public key
- CA’s private key
-
When the certificate authority created Renee’s digital certificate, what key did it use to digitally sign the completed certificate?
- Renee’s public key
- Renee’s private key
- CA’s public key
- CA’s private key
-
When Mike receives Renee’s digital certificate, what key does he use to verify the authenticity of the certificate?
- Renee’s public key
- Renee’s private key
- CA’s public key
- CA’s private key
-
Mike would like to send Renee a private message using the information gained during this exchange. What key should he use to encrypt the message?
- Renee’s public key
- Renee’s private key
- CA’s public key
- CA’s private key
-
Which one of the following tools may be used to directly violate the confidentiality of communications on an unencrypted VoIP network?
- Nmap
- Nessus
- Wireshark
- Nikto
-
How does single sign-on increase security?
- It decreases the number of accounts required for a subject.
- It helps decrease the likelihood users will write down their passwords.
- It provides logging for each system that it is connected to.
- It provides better encryption for authentication data.
-
Which one of the following cryptographic algorithms supports the goal of nonrepudiation?
- Blowfish
- DES
- AES
- RSA
-
Microsoft’s STRIDE threat assessment framework uses six categories for threats: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. If a penetration tester is able to modify audit logs, what STRIDE categories best describe this issue?
- Tampering and information disclosure
- Elevation of privilege and tampering
- Repudiation and denial of service
- Repudiation and tampering
-
RIP, OSPF, and BGP are all examples of protocols associated with what type of network device?
- Switches
- Bridges
- Routers
- Gateways
-
AES-based CCMP and 802.1x replaced what security protocol that was designed as part of WPA to help fix the significant security issues found in WEP?
- TLS
- TKIP
- EAP
- PEAP
-
The government agency that Ben works at installed a new access control system. The system uses information such as Ben’s identity, department, normal working hours, job category, and location to make authorization What type of access control system did Ben’s employer adopt?
- Role-based access control
- Attribute-based access control
- Administrative access control
- System discretionary access control
-
The Low Orbit Ion Cannon (LOIC) attack tool used by Anonymous leverages a multitude of home PCs to attack its chosen targets. This is an example of what type of network attack?
- DDoS
- Ionization
- Zombie horde
- Teardrop
-
Andrew believes that a digital certificate belonging to his organization was compromised and would like to add it to a Certificate Revocation List. Who must add the certificate to the CRL?
- Andrew
- The root authority for the top-level domain
- The CA that issued the certificate
- The revocation authority for the top-level domain
-
Amanda is considering the implementation of a database recovery mechanism recommended by a consultant. In the recommended approach, an automated process will move records of transactions from the primary site to a backup site on an hourly basis. What type of database recovery technique is the consultant describing?
- Electronic vaulting
- Transaction logging
- Remote mirroring
- Remote journaling
-
A process on a system needs access to a file that is currently in use by another process. What state will the process scheduler place this process in until the file becomes available?
- Running
- Ready
- Waiting
- Stopped
-
Which one of the following investigation types has the loosest standards for the collection and preservation of information?
- Civil investigation
- Operational investigation
- Criminal investigation
- Regulatory investigation
-
Sue was required to sign an NDA when she took a job at her new company. Why did the company require her to sign it?
- To protect the confidentiality of their data
- To ensure that Sue did not delete their data
- To prevent Sue from directly competing with them in the future
- To require Sue to ensure the availability for their data as part of her job
-
Susan is concerned about the FAR associated with her biometric technology. What is the best method to deal with the FAR?
- Adjust the CER.
- Change the sensitivity of the system to lower the FRR.
- Add a second factor.
- Replace the biometric system.
-
What length of time does an SOC 2 report typically cover?
- Point in time
- 6 months
- 12 months
- 3 months
-
Which of the following is not a code review process?
- Email pass-around
- Over the shoulder
- Pair programming
- IDE forcing
-
Which one of the following attack types depends on precise timing?
- TOC/TOU
- SQL injection
- Pass the hash
- Cross-site scripting
-
What process adds a header and a footer to data received at each layer of the OSI model?
- Attribution
- Encapsulation
- TCP wrapping
- Data hiding
-
Attackers who compromise websites often acquire databases of hashed passwords. What technique can best protect these passwords against automated password cracking attacks that use precomputed values?
- Using the MD5 hashing algorithm
- Using the SHA-1 hashing algorithm
- Salting
- Double-hashing
-
Jim starts a new job as a system engineer and his boss provides him with a document entitled “Forensic Response Guidelines.” Which one of the following statements is not true?
- Jim must comply with the information in this document.
- The document contains information about forensic examinations.
- Jim should read the document thoroughly.
- The document is likely based on industry best practices.
-
Which one of the following tools is most often used for identification purposes and is not suitable for use as an authenticator?
- Password
- Retinal scan
- Username
- Token
-
Ben needs to verify that the most recent patch for his organization’s critical application did not introduce issues elsewhere. What type of testing does Ben need to conduct to ensure this?
- Unit testing
- White box
- Regression testing
- Black box
-
Tamara recently decided to purchase cyberliability insurance to cover her company’s costs in the event of a data breach. What risk management strategy is she pursuing?
- Risk acceptance
- Risk mitigation
- Risk transference
- Risk avoidance
-
Which of the following is not one of the four canons of the (ISC)2 code of ethics?
- Avoid conflicts of interest that may jeopardize impartiality.
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Act honorably, honestly, justly, responsibly, and legally.
- Provide diligent and competent service to principals.
-
Jim wants to allow a partner organization’s Active Directory forest (B) to access his domain forest’s (A)’s resources but doesn’t want to allow users in his domain to access B’s resources. He also does not want the trust to flow upward through the domain tree as it is formed. What should he do?
- Set up a two-way transitive trust.
- Set up a one-way transitive trust.
- Set up a one-way nontransitive trust.
- Set up a two-way nontransitive trust.
-
Susan’s team is performing code analysis by manually reviewing the code for flaws. What type of analysis are they performing?
- Gray box
- Static
- Dynamic
- Fuzzing
-
The IP address 201.19.7.45 is what type of address?
- A public IP address
- An RFC 1918 address
- An APIPA address
- A loopback address
-
Sam is a security risk analyst for an insurance company. He is currently examining a scenario where a hacker might use a SQL injection attack to deface a web server due to a missing patch in the company’s web application. In this scenario, what is the vulnerability?
- Unpatched web application
- Web defacement
- Hacker
- Operating system
-
Which one of the following categories of secure data removal techniques would include degaussing?
- Clear
- Shrink
- Purge
- Destroy
-
What type of alternate processing facility includes all of the hardware and data necessary to restore operations in a matter of minutes or seconds?
- Hot site
- Warm site
- Cold site
- Mobile site
-
What UDP port is typically used by the syslog service?
- 443
- 514
- 515
- 445
-
Fred finds a packet that his protocol analyzer shows with both PSH and URG set. What type of packet is he looking at, and what do the flags mean?
- A UDP packet; PSH and URG are used to indicate that the data should be sent at high speed
- A TCP packet; PSH and URG are used to clear the buffer and indicate that the data is urgent
- A TCP packet; PSH and URG are used to preset the header and indicate that the speed of the network is unregulated
- A UDP packet; PSH and URG are used to indicate that the UDP buffer should be cleared and that the data is urgent
-
What code review process is shown here?
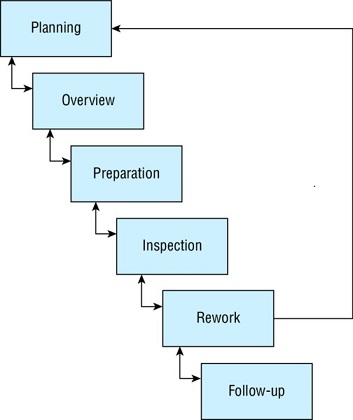
- Static inspection
- Fagan inspection
- Dynamic inspectiom
- Interface testing
-
During a log review, Karen discovers that the system she needs to gather logs from has the log setting shown here. What problem is Karen likely to encounter?
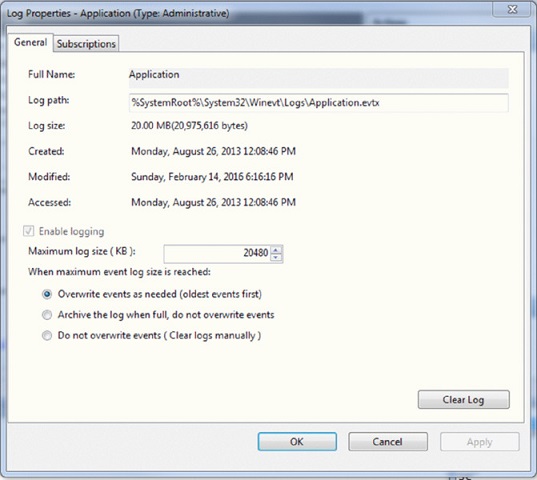
- Too much log data will be stored on the system.
- The system is automatically purging archived logs.
- The logs will not contain the information needed.
- The logs will only contain the most recent 20 MB of log data.
-
The ESP component of IPSec provides what two functions?
- Authentication and integrity
- Confidentiality and authentication
- Nonrepudiation and authentication
- Confidentiality and availability
Questions 210–213 refer to the following scenario.
Alejandro is an incident response analyst for a large corporation. He is on the midnight shift when an intrusion detection system alerts him to a potential brute-force password attack against one of the company’s critical information systems. He performs an initial triage of the event before taking any additional action.
-
What stage of the incident response process is Alejandro currently conducting?
- Detection
- Response
- Recovery
- Mitigation
-
If Alejandro’s initial investigation determines that a security incident is likely taking place, what should be his next step?
- Investigate the root cause.
- File a written report.
- Activate the incident response team.
- Attempt to restore the system to normal operations.
-
As the incident response progresses, during which stage should the team conduct a root cause analysis?
- Response
- Reporting
- Remediation
- Lessons Learned
-
Barry recently received a message from Melody that Melody encrypted using symmetric cryptography. What key should Barry use to decrypt the message?
- Barry’s public key
- Barry’s private key
- Melody’s public key
- Shared secret key
-
After you do automated functional testing with 100 percent coverage of an application, what type of error is most likely to remain?
- Business logic errors
- Input validation errors
- Runtime errors
- Error handling errors
-
During what phase of the incident response process would security professionals analyze the process itself to determine whether any improvements are warranted?
- Lessons Learned
- Remediation
- Recovery
- Reporting
-
What law prevents the removal of protection mechanisms placed on a copyrighted work by the copyright holder?
- HIPAA
- DMCA
- GLBA
- ECPA
-
Linda is selecting a disaster recovery facility for her organization, and she wishes to retain independence from other organizations as much as possible. She would like to choose a facility that balances cost and recovery time, allowing activation in about one week after a disaster is declared. What type of facility should she choose?
- Cold site
- Warm site
- Mutual assistance agreement
- Hot site
-
What term is used to describe two-way communications in which only one direction can send at a time?
- Duplex
- Half-duplex
- Simplex
- Suplex
-
What type of penetration testing provides detail on the scope of a penetration test—including items like what systems would be targeted—but does not provide full visibility into the configuration or other details of the systems or networks the penetration tester must test?
- Crystal box
- White box
- Black box
- Gray box
-
Test coverage is computed using which of the following formulas?
- Number of use cases tested/total number of use cases
- Number of lines of code tested/total number of lines of code
- Number of functions tested/total number of functions
- Number of conditional branches tested/Total number of testable branches
-
TCP and UDP both operate at what layer of the OSI model?
- Layer 2
- Layer 3
- Layer 4
- Layer 5
-
Which one of the following goals of physical security environments occurs first in the functional order of controls?
- Delay
- Detection
- Deterrence
- Denial
-
In what type of trusted recovery process does the system recover against one or more failure types without administrator intervention with potential data loss?
- Automated recovery
- Manual recovery
- Automated recovery without undue data loss
- Function recovery
-
Skip needs to transfer files from his PC to a remote server. What protocol should he use instead of FTP?
- SCP
- SSH
- HTTP
- Telnet
-
Ben’s New York–based commercial web service collects personal information from California residents. What does the California Online Privacy Protection Act require Ben to do to be compliant?
- Ben must encrypt all personal data he receives.
- Ben must comply with the EU DPD.
- Ben must have a conspicuously posted privacy policy on his site.
- Ben must provide notice and choice for users of his website.
-
What process is used to verify that a dial-up user is connecting from the phone number they are preauthorized to use in a way that avoids spoofing?
- CallerID
- Callback
- CHAP
- PPP
-
In the diagram shown here of security boundaries within a computer system, what component’s name has been replaced with XXX?
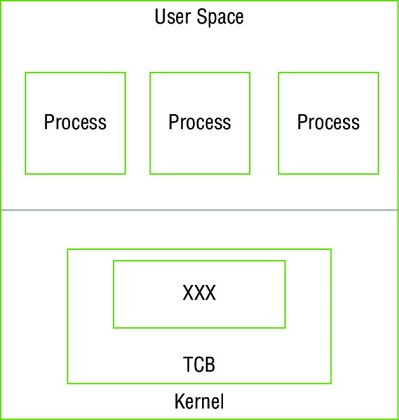
- Reference monitor
- Privileged core
- Security perimeter
- User kernel
-
Why are iris scans preferable to most other types of biometric factors?
- Iris scanners are harder to deceive.
- Irises don’t change as much as other factors.
- Iris scanners are cheaper than other factors.
- Iris scans cannot be easily replicated.
-
Alex has ensured that all of his staff have signed nondisclosure agreements to help protect his organization’s intellectual property and data. What potential issue is Alex working to deal with?
- Data exfiltration
- Personnel retention
- Data breach
- Nonproprietary data sharing
-
Matthew, Richard, and Christopher would like to exchange messages with each other using symmetric cryptography. They want to ensure that each individual can privately send a message to another individual without the third person being able to read the message. How many keys do they need?
- 1
- 2
- 3
- 6
-
Which one of the following is not an example of criminal law?
- Gramm Leach Bliley Act
- Computer Fraud and Abuse Act
- Electronic Communications Privacy Act
- Identity Theft and Assumption Deterrence Act
-
What is the best way to ensure email confidentiality in motion?
- Use TLS between the client and server.
- Use SSL between the client and server.
- Encrypt the email content.
- Use a digital signature.
-
Brenda is analyzing the web server logs after a successful compromise of her organization’s web-based order processing application. She finds an entry in the log file showing that a user entered the following information as his last name when placing an order:
Smith';DROP TABLE orders;--What type of attack was attempted?
- Buffer overflow
- Cross-site scripting
- Cross-site request forgery
- SQL injection
-
What type of policy describes how long data is kept before destruction?
- Classification
- Audit
- Record retention
- Availability
-
What is the goal of the BCP process?
- RTO<MTD
- MTD<RTO
- RPO<MTD
- MTD<RPO
-
During which phase of the incident response process would administrators design new security controls intended to prevent a recurrence of the incident?
- Reporting
- Recovery
- Remediation
- Lessons Learned
-
Bethany received an email from one of her colleagues with an unusual attachment named
smime.p7s. She does not recognize the attachment and is unsure what to do. What is the most likely scenario?- This is an encrypted email message.
- This is a phishing attack.
- This is embedded malware.
- This is a spoofing attack.
Questions 238–241 refer to the following scenario.
Kim is the database security administrator for Aircraft Systems, Inc. (ASI). ASI is a military contractor engaged in the design and analysis of aircraft avionics systems and regularly handles classified information on behalf of the government and other government contractors. Kim is concerned about ensuring the security of information stored in ASI databases.
Kim’s database is a multilevel security database, and different ASI employees have different security clearances. The database contains information on the location of military aircraft containing ASI systems to allow ASI staff to monitor those systems.
-
Kim learned that the military is planning a classified mission that involves some ASI aircraft. She is concerned that employees not cleared for the mission may learn of it by noticing the movement of many aircraft to the region. What type of attack is Kim concerned about?
- Aggregation
- SQL injection
- Inference
- Multilevel security
-
What technique can Kim employ to prevent employees not cleared for the mission from learning the true location of the aircraft?
- Input validation
- Polyinstantiation
- Parameterization
- Server-side validation
-
Kim’s database uniquely identifies aircraft by using their tail number. Which one of the following terms would not necessarily accurately describe the tail number?
- Database field
- Foreign key
- Primary key
- Candidate key
-
Kim would like to create a key that enforces referential integrity for the database. What type of key does she need to create?
- Primary key
- Foreign key
- Candidate key
- Master key
-
Doug is choosing a software development life-cycle model for use in a project he is leading to develop a new business application. He has very clearly defined requirements and would like to choose an approach that places an early emphasis on developing comprehensive documentation. He does not have a need for the production of rapid prototypes or iterative improvement. Which model is most appropriate for this scenario?
- Agile
- Waterfall
- Spiral
- DevOps
-
Which individual bears the ultimate responsibility for data protection tasks?
- Data owner
- Data custodian
- User
- Auditor
-
What should be true for salts used in password hashes?
- A single salt should be set so passwords can be de-hashed as needed.
- A single salt should be used so the original salt can be used to check passwords against their hash.
- Unique salts should be stored for each user.
- Unique salts should be created every time a user logs in.
-
What type of assessment methods are associated with mechanisms and activities based on the recommendations of NIST SP800-53A, the Guide for Assessing Security Controls in Federal Information Systems?
- Examine and interview
- Test and assess
- Test and interview
- Examine and test
-
Which one of the following controls would be most effective in detecting zero-day attack attempts?
- Signature-based intrusion detection
- Anomaly-based intrusion detection
- Strong patch management
- Full-disk encryption
-
The ability to store and generate passwords, provide logging and auditing capabilities, and allow password check-in and check-out are all features of what type of system?
- AAA
- Credential management
- Two-factor authentication
- Kerberos
-
Which one of the following components should be included in an organization’s emergency response guidelines?
- Secondary response procedures for first responders
- Long-term business continuity protocols
- Activation procedures for the organization’s cold sites
- Contact information for ordering equipment
-
When Jim enters his organization’s data center, he has to use a smart card and code to enter, and is allowed through one set of doors. The first set of doors closes, and he must then use his card again to get through a second set, which locks behind him. What type of control is this, and what is it called?
- A physical control; a one-way trapdoor
- A logical control; dual-swipe authorization
- A directive control; one-way access corridor
- A preventive access control; a mantrap
-
What security control may be used to implement a concept known as two-person control?
- Mandatory vacation
- Separation of duties
- Least privilege
- Defense in depth
