CHAPTER 5
Identity and Access Management
This domain includes questions from the following topics:
• Identification methods and technologies
• Authentication methods, models, and technologies
• Discretionary, mandatory, and nondiscretionary models
• Accountability, monitoring, and auditing practices
• Registration and proof of identity
• Identity as a Service
• Threats to access control practices and technologies
Controlling access to resources is a vital element of any information security program. Controlling who can access what and when helps protect information assets and company resources from unauthorized modification and disclosure. Thus, access controls address all three services in the AIC triad—availability, integrity, and confidentiality—be they technical, physical, or administrative in nature. Security professionals should understand the principles behind access controls to ensure their adequacy and proper implementation.
Q QUESTIONS
1. Which of the following does NOT correctly describe a directory service?
A. It manages objects within a directory by using namespaces.
B. It enforces security policy by carrying out access control and identity management functions.
C. It assigns namespaces to each object in databases that are based on the X.509 standard and are accessed by LDAP.
D. It allows an administrator to configure and manage how identification takes place within the network.
2. Hannah has been assigned the task of installing web access management (WAM) software. What is the best description for what WAM is commonly used for?
A. Control external entities requesting access through X.500 databases
B. Control external entities requesting access to internal objects
C. Control internal entities requesting access through X.500 databases
D. Control internal entities requesting access to external objects
3. There are several types of password management approaches used by identity management systems. Which of the following reduces help-desk call volume, but is also criticized for the ease with which a hacker could gain access to multiple resources if a password is compromised?
A. Management password reset
B. Self-service password reset
C. Password synchronization
D. Assisted password reset
4. In the United States, federal agencies must adhere to Federal Information Processing Standard (FIPS) 201-2 “Personal Identity Verification,” which discusses technical measures of authentication for federal employees and contractors. This standard must be followed in order to ensure which of the following?
A. That government employees are properly cleared for the work assigned
B. That government employees are only allowed access to data of their clearance level
C. That the identity of the government employee has been appropriately verified
D. That the data that government employees have access to has been appropriately classified
5. Which of the following does NOT describe privacy-aware role-based access control?
A. It is an example of a discretionary access control model.
B. Detailed access controls indicate the type of data that users can access based on the data’s level of privacy sensitivity.
C. It is an extension of role-based access control.
D. It should be used to integrate privacy policies and access control policies.
6. Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between systems on different security domains. SAML allows for the sharing of authentication information, such as how authentication took place, entity attributes, and what the entity is authorized to access. SAML is most commonly used in web-based environments that require single sign-on (SSO) capability. Which of the following has a correct definition associated with the corresponding SAML component?
A. Two SAML assertions are used (authentication, authorization) that indicate that an SAML authority validated a specific subject.
B. SAML assertions are most commonly used to allow for identity federation and distributed authorization.
C. SAML binding specification describes how to embed SAML messages within the TCP and UDP protocols.
D. SAML profiles define how SAML messages, assertions, and protocols are to be implemented in SSL and TLS.
7. Brian has been asked to work on the virtual directory of his company’s new identity management system. Which of the following best describes a virtual directory?
A. Meta-directory
B. User attribute information stored in an HR database
C. Virtual container for data from multiple sources
D. A service that allows an administrator to configure and manage how identification takes place
8. Which of the following accurately describes Identity as a Service (IDaaS)?
A. A form of single sign-on (SSO) that spans multiple entities in an enterprise
B. A form of SSO that spans multiple independent enterprises
C. A way to provide SSO without multiple forms of authentication
D. A way to demonstrate identity without having to sign on
9. Which of the following correctly describes a federated identity and its role within identity management processes?
A. A nonportable identity that can be used across business boundaries
B. A portable identity that can be used across business boundaries
C. An identity that can be used within intranet virtual directories and identity stores
D. An identity specified by domain names that can be used across business boundaries
10. Security countermeasures should be transparent to users and attackers. Which of the following does NOT describe transparency?
A. User activities are monitored and tracked without negatively affecting system performance.
B. User activities are monitored and tracked without the user knowing about the mechanism that is carrying this out.
C. Users are allowed access in a manner that does not negatively affect business processes.
D. Unauthorized access attempts are denied and logged without the intruder knowing about the mechanism that is carrying this out.
11. What markup language allows for the sharing of application security policies to ensure that all applications are following the same security rules?
A. XML
B. SPML
C. XACML
D. GML
12. The importance of protecting audit logs generated by computers and network devices is highlighted by the fact that it is required by many of today’s regulations. Which of the following does NOT explain why audit logs should be protected?
A. If not properly protected, these logs may not be admissible during a prosecution.
B. Audit logs contain sensitive data and should only be accessible to a certain subset of people.
C. Intruders may attempt to scrub the logs to hide their activities.
D. The format of the logs should be unknown and unavailable to the intruder.
13. Of the following, what is the primary item that a capability table is based upon?
A. A subject
B. An object
C. A product
D. An application
14. Which markup language allows a company to send service requests and the receiving company to provision access to these services?
A. XML
B. SPML
C. SGML
D. HTML
15. There are several different types of centralized access control protocols. Which of the following is illustrated in the graphic that follows?

A. Diameter
B. Watchdog
C. RADIUS
D. TACACS+
16. An access control matrix is used in many operating systems and applications to control access between subjects and objects. What is the column in this type of matrix referred to as?

A. Capability table
B. Constrained interface
C. Role-based value
D. ACL
17. What technology within identity management is illustrated in the graphic that follows?

A. User provisioning
B. Federated identity
C. Directories
D. Web access management
18. There are different ways that specific technologies can create one-time passwords for authentication purposes. What type of technology is illustrated in the graphic that follows?
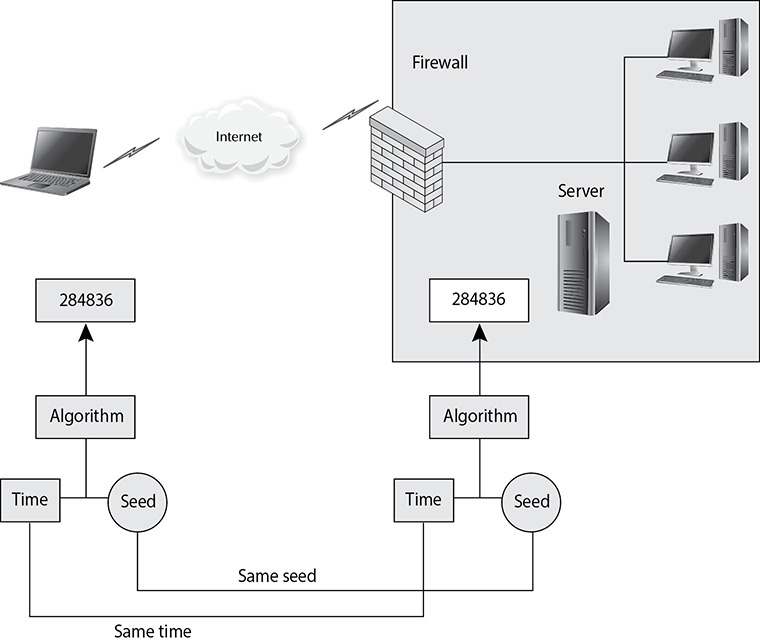
A. Counter synchronous token
B. Asynchronous token
C. Mandatory token
D. Synchronous token
19. Which of the following best describes how SAML, SOAP, and HTTP commonly work together in an environment that provides web services?
A. The security attributes are put into SAML format. The web service request and the authentication data are encrypted in a SOAP message. The message is transmitted in an HTTP connection.
B. The security attributes are put into SAML format. The web service request and the authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection over TLS.
C. The authentication data is put into SAML format. The web service request and authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection.
D. The authentication data is put into SAML format. The HTTP request and the authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection.
20. Jill is establishing a companywide sales program that will require different user groups with different privileges to access information on a centralized database. How should the security manager secure the database?
A. Increase the database’s security controls and provide more granularity.
B. Implement access controls that display each user’s permissions each time they access the database.
C. Change the database’s classification label to a higher security status.
D. Decrease the security so that all users can access the information as needed.
21. Bethany is working on a mandatory access control (MAC) system. She has been working on a file that was classified as Secret. She can no longer access this file because it has been reclassified as Top Secret. She deduces that the project she was working on has just increased in confidentiality and she now knows more about this project than her clearance and need-to-know allows. Which of the following refers to a concept that attempts to prevent this type of scenario from occurring?
A. Covert storage channel
B. Inference attack
C. Noninterference
D. Aggregation
22. A number of attacks can be performed against smart cards. Side-channel is a class of attacks that doesn’t try to compromise a flaw or weakness. Which of the following is NOT a side-channel attack?
A. Differential power analysis
B. Microprobing analysis
C. Timing analysis
D. Electromagnetic analysis
23. Emily is listening to network traffic and capturing passwords as they are sent to the authentication server. She plans to use the passwords as part of a future attack. What type of attack is this?
A. Brute-force attack
B. Dictionary attack
C. Social engineering attack
D. Replay attack
24. Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover users’ passwords?
A. Increase the clipping level.
B. Lock out an account for a certain amount of time after the clipping level is reached.
C. After a threshold of failed login attempts is met, the administrator must physically lock out the account.
D. Choose a weaker algorithm that encrypts the password file.
25. Phishing and pharming are similar. Which of the following correctly describes the difference between phishing and pharming?
A. Personal information is collected from victims through legitimate-looking websites in phishing attacks, while personal information is collected from victims via e-mail in pharming attacks.
B. Phishing attacks point e-mail recipients to a form where victims input personal information, while pharming attacks use pop-up forms at legitimate websites to collect personal information from victims.
C. Victims are pointed to a fake website with a domain name that looks similar to a legitimate site’s domain name in a phishing attack, while victims are directed to a fake website as a result of a legitimate domain name being incorrectly translated by the DNS server in a pharming attack.
D. Phishing is a technical attack, while pharming is a type of social engineering.
26. There are several types of intrusion detection systems (IDSs). What type of IDS builds a profile of an environment’s normal activities and assigns an anomaly score to packets based on the profile?
A. State-based
B. Statistical anomaly–based
C. Misuse-detection system
D. Protocol signature–based
27. A rule-based IDS takes a different approach than a signature-based or anomaly-based system. Which of the following is characteristic of a rule-based IDS?
A. Uses IF/THEN programming within expert systems
B. Identifies protocols used outside of their common bounds
C. Compares patterns to several activities at once
D. Can detect new attacks
28. Tom works at a large retail company that recently deployed radio-frequency identification (RFID) to better manage its inventory processes. Employees use scanners to gather product-related information instead of manually looking up product data. Tom has found out that malicious customers have carried out attacks on the RFID technology to reduce the amount they pay on store items. Which of the following is the most likely reason for the existence of this type of vulnerability?
A. The company’s security team does not understand how to secure this type of technology.
B. The cost of integrating security within RFID is cost prohibitive.
C. The technology has low processing capabilities and encryption is very processor intensive.
D. RFID is a new and emerging technology, and the industry does not currently have ways to secure it.
29. Tanya is the security administrator for a large distributed retail company. The company’s network has many different network devices and software appliances that generate logs and audit data. Tanya and her staff have become overwhelmed with trying to review all of the log files when attempting to identify if anything suspicious is taking place within the network. Which of the following is the best solution for this company to implement?
A. Security information and event management
B. Event correlation tools
C. Intrusion detection systems
D. Security event correlation management tools
30. The Logistics Agency of a country’s department of defense is responsible for ensuring that all necessary materials get to the proper locations to support the department’s day-to-day activities. The data that this agency maintains must be protected according to the three main security principles of security controls. For this agency’s responsibilities, which security principle has the highest priority?
A. Confidentiality
B. Integrity
C. Availability
D. Privacy
31. Claudia is the CISO for a global financial institution, overseeing the security of hundreds of millions of bank accounts. Which of the three main security principles should she consider most important when prioritizing the controls her enterprise should deploy?
A. Confidentiality
B. Integrity
C. Availability
D. Authenticity
32. Which of the following is an example of a credential management system, also known as an identity management (IdM) system?
A. A historic log of the activities performed by users once they have presented their credentials to a central authorizing system
B. A database of the credentials that have been registered to each individual in an enterprise, in order to correlate users with usernames and locales
C. A security information and event management (SIEM) system that contains the logs for various credentialing systems in the enterprise, for correlation of activities by ID
D. A Kerberos Key Distribution Center (KDC) that contains the symmetric keys of all the entities and systems in a Kerberos realm, which can be centrally administered to ensure that it is up-to-date with respect to additions and deletions of keys
33. Which of the following attributes is used to biometrically authenticate a user’s identity?
A. Something you know
B. Something you have
C. Something you are
D. Someplace you are
34. Within biometric authentication, what is a Type II error rate?
A. The rate of errors where the system falsely accepts the authentication of an individual who is not who they purport to be
B. The rate of errors where the system falsely rejects the authentication of an individual who is who they purport to be
C. The rate of errors that the system produces where false rejections and false acceptances are equal
D. The rate of errors where the system fails to either accept or reject the authentication of an individual regardless of their validity
35. Which of the following criteria is the most important consideration for the selection and deployment of a biometric authentication system?
A. False acceptance rate (FAR) or Type II error rate
B. False rejection rate (FRR) or Type I error rate
C. Crossover error rate (CER) or equal error rate (EER)
D. Processing speed
36. Though “something you know,” in the form of passwords, is the most common authentication factor still used today, it is considered one of the weakest. This is because passwords are easy for users to share, and relatively easy for adversaries to steal or guess. Which of the following measures is the best way to counter attacks on this form of authentication?
A. Store all passwords in encrypted form only, so that recovering them requires a special key to decrypt them for authentication.
B. Employ a password policy to ensure that passwords are chosen in such a way that they are neither easy for an attacker to guess nor easy for an attacker to brute force.
C. Require that all passwords be composed of a combination of unique characters, regardless of length.
D. Ensure that accounts are locked out after a minimum number of incorrect guesses within a short amount of time.
37. Which of the following is the correct sequence in the Kerberos authentication process with respect to passwords, Key Distribution Centers (KDCs), ticket granting servers (TGSs), ticket granting tickets (TGTs), services, and service tickets?
A. The user provides a username/password to the workstation, the workstation obtains a TGT from the TGS, then subsequently obtains a service ticket from the KDC, which it presents to the service.
B. The workstation obtains a TGT from the KDC, which the user then validates with a password. The TGT is then exchanged for a service ticket from the TGS, which is presented to the service.
C. The user provides a username/password to the workstation, the workstation obtains a TGT from the KDC, then subsequently obtains a service ticket from the TGS, which it presents to the service.
D. The user obtains a service ticket from the service. The user then validates this ticket with a username/password provided to the TGS, which results in a TGT that is further validated by the KDC in a final step.
38. In practical use, which of the following best describes a “session”?
A. Any data exchange between two discrete endpoints, over any arbitrary duration
B. Any authenticated exchange between two parties that is used to carry on a conversation, with a discrete beginning, period of activity, and termination
C. Any discrete period of time that a user is logged into a workstation
D. The volume of data exchanged between two systems during a discrete period of time
39. The use of “resource servers” and “authorization servers” to enable a “client” web service (such as LinkedIn) to access a “resource owner” (such as Google) for federated authorization is a hallmark of what open standard?
A. OpenID
B. SAML
C. SSO
D. OAuth
40. Which of the following is NOT true of OpenID Connect (OIDC)?
A. It is mainly used as an open standards–based single sign-on (SSO) mechanism between disparate platforms within an enterprise environment.
B. It is layered on the OAuth protocol to allow both authentication and authorization in a transparent way for client resource requests.
C. It supports three flows: authorization code flow, implicit flow, and hybrid flow.
D. It involves browser redirections from the OpenID provider back to the relying party using authorization codes.
41. Which of the following attributes are added beyond traditional access control mechanisms (RBAC, MAC, and DAC) in order to implement ABAC?
A. Subjects
B. Objects
C. Actions
D. Context
QUICK ANSWER KEY
1. C
2. B
3. C
4. C
5. A
6. B
7. C
8. B
9. B
10. A
11. C
12. D
13. A
14. B
15. A
16. D
17. B
18. D
19. C
20. A
21. C
22. B
23. D
24. B
25. C
26. B
27. A
28. C
29. A
30. A
31. B
32. D
33. C
34. A
35. D
36. B
37. C
38. B
39. D
40. A
41. D
ANSWERS A
1. Which of the following does NOT correctly describe a directory service?
A. It manages objects within a directory by using namespaces.
B. It enforces security policy by carrying out access control and identity management functions.
C. It assigns namespaces to each object in databases that are based on the X.509 standard and are accessed by LDAP.
D. It allows an administrator to configure and manage how identification takes place within the network.
![]() C. Most enterprises have some type of directory that contains information pertaining to the company’s network resources and users. Most directories follow a hierarchical database format, based on the X.500 standard (not X.509), and a type of protocol, as in Lightweight Directory Access Protocol (LDAP), that allows subjects and applications to interact with the directory. Applications can request information about a particular user by making an LDAP request to the directory, and users can request information about a specific resource by using a similar request. A directory service assigns distinguished names (DNs) to each object in databases based on the X.500 standard that are accessed by LDAP. Each distinguished name represents a collection of attributes about a specific object and is stored in the directory as an entry.
C. Most enterprises have some type of directory that contains information pertaining to the company’s network resources and users. Most directories follow a hierarchical database format, based on the X.500 standard (not X.509), and a type of protocol, as in Lightweight Directory Access Protocol (LDAP), that allows subjects and applications to interact with the directory. Applications can request information about a particular user by making an LDAP request to the directory, and users can request information about a specific resource by using a similar request. A directory service assigns distinguished names (DNs) to each object in databases based on the X.500 standard that are accessed by LDAP. Each distinguished name represents a collection of attributes about a specific object and is stored in the directory as an entry.
![]() A is incorrect because objects within hierarchical databases are managed by a directory service. The directory service allows an administrator to configure and manage how identification, authentication, authorization, and access control take place within the network. The objects within the directory are labeled and identified with namespaces, which is how the directory service keeps the objects organized.
A is incorrect because objects within hierarchical databases are managed by a directory service. The directory service allows an administrator to configure and manage how identification, authentication, authorization, and access control take place within the network. The objects within the directory are labeled and identified with namespaces, which is how the directory service keeps the objects organized.
![]() B is incorrect because directory services do enforce the configured security policy by carrying out access control and identity management functions. For example, when a user logs into a domain controller in a Windows environment, the directory service (Active Directory) determines what network resources she can and cannot access.
B is incorrect because directory services do enforce the configured security policy by carrying out access control and identity management functions. For example, when a user logs into a domain controller in a Windows environment, the directory service (Active Directory) determines what network resources she can and cannot access.
![]() D is incorrect because directory services do allow an administrator to configure and manage how identification takes place within the network. It also allows for the configuration and management of authentication, authorization, and access control.
D is incorrect because directory services do allow an administrator to configure and manage how identification takes place within the network. It also allows for the configuration and management of authentication, authorization, and access control.
2. Hannah has been assigned the task of installing web access management (WAM) software. What is the best description for what WAM is commonly used for?
A. Control external entities requesting access through X.500 databases
B. Control external entities requesting access to internal objects
C. Control internal entities requesting access through X.500 databases
D. Control internal entities requesting access to external objects
![]() B. Web access management (WAM) software controls what users can access when using a web browser to interact with web-based enterprise assets. This type of technology is continually becoming more robust and experiencing increased deployment. This is because of the increased use of e-commerce, online banking, content providing, web services, and more. The basic components and activities in a web access control management process are as follows:
B. Web access management (WAM) software controls what users can access when using a web browser to interact with web-based enterprise assets. This type of technology is continually becoming more robust and experiencing increased deployment. This is because of the increased use of e-commerce, online banking, content providing, web services, and more. The basic components and activities in a web access control management process are as follows:
1. User sends in credentials to web server.
2. Web server requests the WAM platform to authenticate the user. WAM authenticates against the LDAP directory and retrieves authorizations from the policy database.
3. User requests to access a resource (object).
4. Web server verifies that object access is authorized and allows access to the requested resource.
![]() A is incorrect because a directory service should be carrying out access control in the directory of an X.500 database—not web access management software. The directory service manages the entries and data and enforces the configured security policy by carrying out access control and identity management functions. Examples of directory services include Active Directory and NetIQ eDirectory. While web-based access requests may be to objects held within a database, WAM mainly controls communication between web browsers and servers. The web servers should communicate to a back-end database, commonly through a directory service.
A is incorrect because a directory service should be carrying out access control in the directory of an X.500 database—not web access management software. The directory service manages the entries and data and enforces the configured security policy by carrying out access control and identity management functions. Examples of directory services include Active Directory and NetIQ eDirectory. While web-based access requests may be to objects held within a database, WAM mainly controls communication between web browsers and servers. The web servers should communicate to a back-end database, commonly through a directory service.
![]() C is incorrect because a directory service should be carrying out access control for internal entities requesting access to an X.500 database using the LDAP. This type of database provides a hierarchical structure for the organization of objects (subjects and resources). The directory service develops unique distinguished names for each object and appends the corresponding attribute to each object as needed. The directory service enforces a security policy (configured by the administrator) to control how subjects and objects interact. While web-based access requests may be to objects held within a database, WAM mainly controls communication between web browsers and servers. WAM was developed mainly for external-to-internal communication, although it can be used for internal-to-internal communication also. Answer B is the best answer out of the four provided.
C is incorrect because a directory service should be carrying out access control for internal entities requesting access to an X.500 database using the LDAP. This type of database provides a hierarchical structure for the organization of objects (subjects and resources). The directory service develops unique distinguished names for each object and appends the corresponding attribute to each object as needed. The directory service enforces a security policy (configured by the administrator) to control how subjects and objects interact. While web-based access requests may be to objects held within a database, WAM mainly controls communication between web browsers and servers. WAM was developed mainly for external-to-internal communication, although it can be used for internal-to-internal communication also. Answer B is the best answer out of the four provided.
![]() D is incorrect because WAM software is most commonly used to control external entities requesting access to internal objects; not the other way around, as stated by the answer option. For example, WAM may be used by a bank to control its customers’ access to back-end account data.
D is incorrect because WAM software is most commonly used to control external entities requesting access to internal objects; not the other way around, as stated by the answer option. For example, WAM may be used by a bank to control its customers’ access to back-end account data.
3. There are several types of password management approaches used by identity management systems. Which of the following reduces help-desk call volume, but is also criticized for the ease with which a hacker could gain access to multiple resources if a password is compromised?
A. Management password reset
B. Self-service password reset
C. Password synchronization
D. Assisted password reset
![]() C. Password synchronization is designed to reduce the complexity of keeping up with different passwords for different systems. Password synchronization technology can allow users to maintain a single password across multiple systems by transparently synchronizing the password to other systems and applications. This reduces help-desk call volume. One criticism of this approach is that since only one password is used to access different resources, now the hacker only has to figure out one credential set to gain unauthorized access to all resources.
C. Password synchronization is designed to reduce the complexity of keeping up with different passwords for different systems. Password synchronization technology can allow users to maintain a single password across multiple systems by transparently synchronizing the password to other systems and applications. This reduces help-desk call volume. One criticism of this approach is that since only one password is used to access different resources, now the hacker only has to figure out one credential set to gain unauthorized access to all resources.
![]() A is incorrect because there is no such thing as a management password reset. This answer is a distracter. The most common password management approaches are password synchronization, self-service password reset, and assisted password reset.
A is incorrect because there is no such thing as a management password reset. This answer is a distracter. The most common password management approaches are password synchronization, self-service password reset, and assisted password reset.
![]() B is incorrect because self-service password reset does not necessarily deal with multiple passwords. However, it does help reduce the overall volume of password-related help-desk calls. In the case of self-service password reset, users are allowed to reset their own passwords. For example, when a user forgets his password, he may be prompted to answer questions that he identified during the registration process. If the answer he gives matches the information he provided during registration, then he is granted the ability to change his password.
B is incorrect because self-service password reset does not necessarily deal with multiple passwords. However, it does help reduce the overall volume of password-related help-desk calls. In the case of self-service password reset, users are allowed to reset their own passwords. For example, when a user forgets his password, he may be prompted to answer questions that he identified during the registration process. If the answer he gives matches the information he provided during registration, then he is granted the ability to change his password.
![]() D is incorrect because assisted password reset does not necessarily deal with multiple passwords. It reduces the resolution process for password issues by allowing the help desk to authenticate a user before resetting her password. The caller must be identified and authenticated through the password management tool before the password can be changed. Once the password is updated, the system that the user is authenticating to should require the user to change her password again. This would ensure that only she (and not she and the help-desk person) knows her password. The goal of an assisted password reset product is to reduce the cost of support calls and ensure that all calls are processed in a uniform, consistent, and secure fashion.
D is incorrect because assisted password reset does not necessarily deal with multiple passwords. It reduces the resolution process for password issues by allowing the help desk to authenticate a user before resetting her password. The caller must be identified and authenticated through the password management tool before the password can be changed. Once the password is updated, the system that the user is authenticating to should require the user to change her password again. This would ensure that only she (and not she and the help-desk person) knows her password. The goal of an assisted password reset product is to reduce the cost of support calls and ensure that all calls are processed in a uniform, consistent, and secure fashion.
4. In the United States, federal agencies must adhere to Federal Information Processing Standard (FIPS) 201-2 “Personal Identity Verification,” which discusses technical measures of authentication for federal employees and contractors. This standard must be followed in order to ensure which of the following?
A. That government employees are properly cleared for the work assigned
B. That government employees are only allowed access to data of their clearance level
C. That the identity of the government employee has been appropriately verified
D. That the data that government employees have access to has been appropriately classified
![]() C. FIPS 201-2 specifies the U.S. government standards for Personal Identity Verification (PIV), giving varying requirements of assurance. Access by government employees and contracted agents to restricted information hinges on their level of clearance and their need to know it, but first and foremost the government requires assurance that the individual is who they say they are.
C. FIPS 201-2 specifies the U.S. government standards for Personal Identity Verification (PIV), giving varying requirements of assurance. Access by government employees and contracted agents to restricted information hinges on their level of clearance and their need to know it, but first and foremost the government requires assurance that the individual is who they say they are.
![]() A is incorrect because government employees must be properly cleared for the information that they are granted access to, but prior to such access, their true identity must be available for review and affirmation.
A is incorrect because government employees must be properly cleared for the information that they are granted access to, but prior to such access, their true identity must be available for review and affirmation.
![]() B is incorrect because government employees must only be allowed access to information that they are cleared to know and have a need to access. But again, this must be based on a specified level of assurance that the clearance they possess is valid.
B is incorrect because government employees must only be allowed access to information that they are cleared to know and have a need to access. But again, this must be based on a specified level of assurance that the clearance they possess is valid.
![]() D is incorrect because classification of data is not directly related to Personal Identity Verification.
D is incorrect because classification of data is not directly related to Personal Identity Verification.
5. Which of the following does NOT describe privacy-aware role-based access control?
A. It is an example of a discretionary access control model.
B. Detailed access controls indicate the type of data that users can access based on the data’s level of privacy sensitivity.
C. It is an extension of role-based access control.
D. It should be used to integrate privacy policies and access control policies.
![]() A. A system that uses discretionary access control (DAC) enables the owner of the resource to specify which subjects can access specific resources. This model is called discretionary because the control of access is based on the discretion of the owner. Many times department managers, or business unit managers, are the owners of the data within their specific department. Being the owner, they can specify who should have access and who should not. Privacy-aware role-based access control is an extension of role-based access control (RBAC). There are three main access control models: DAC, mandatory access control (MAC), and RBAC. Privacy-aware role-based access control is a type of RBAC, not DAC.
A. A system that uses discretionary access control (DAC) enables the owner of the resource to specify which subjects can access specific resources. This model is called discretionary because the control of access is based on the discretion of the owner. Many times department managers, or business unit managers, are the owners of the data within their specific department. Being the owner, they can specify who should have access and who should not. Privacy-aware role-based access control is an extension of role-based access control (RBAC). There are three main access control models: DAC, mandatory access control (MAC), and RBAC. Privacy-aware role-based access control is a type of RBAC, not DAC.
![]() B is incorrect because privacy-aware role-based access control is based on detailed access controls that indicate the type of data that users can access based on the data’s level of privacy sensitivity. Other access control models, such as MAC, DAC, and RBAC, do not lend themselves to protect the level of privacy of data, but the functions that users can carry out. For example, managers may be able to access a privacy folder, but there needs to be more detailed access control that indicates, for example, that they can access customers’ home addresses but not Social Security numbers. The industry has advanced to needing much more detail-oriented access control when it comes to sensitive privacy information as in Social Security numbers and credit card data, which is why privacy-aware role-based access control was developed.
B is incorrect because privacy-aware role-based access control is based on detailed access controls that indicate the type of data that users can access based on the data’s level of privacy sensitivity. Other access control models, such as MAC, DAC, and RBAC, do not lend themselves to protect the level of privacy of data, but the functions that users can carry out. For example, managers may be able to access a privacy folder, but there needs to be more detailed access control that indicates, for example, that they can access customers’ home addresses but not Social Security numbers. The industry has advanced to needing much more detail-oriented access control when it comes to sensitive privacy information as in Social Security numbers and credit card data, which is why privacy-aware role-based access control was developed.
![]() C is incorrect because privacy-aware role-based access control is an extension of role-based access control. Access rights are determined based on the user’s role and responsibilities within the company, and the level of privacy of the data they need access to.
C is incorrect because privacy-aware role-based access control is an extension of role-based access control. Access rights are determined based on the user’s role and responsibilities within the company, and the level of privacy of the data they need access to.
![]() D is incorrect because the languages used for privacy policies and access control policies should be either the same or integrated when using privacy-aware role-based access control. The goal of the use of privacy-aware role-based access control is to make access control much more detailed and focused on privacy-related data, thus it should be using the same type of terms and language as the organization’s original access control policy and standards.
D is incorrect because the languages used for privacy policies and access control policies should be either the same or integrated when using privacy-aware role-based access control. The goal of the use of privacy-aware role-based access control is to make access control much more detailed and focused on privacy-related data, thus it should be using the same type of terms and language as the organization’s original access control policy and standards.
6. Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authentication and authorization data between systems on different security domains. SAML allows for the sharing of authentication information, such as how authentication took place, entity attributes, and what the entity is authorized to access. SAML is most commonly used in web-based environments that require single sign-on (SSO) capability. Which of the following has a correct definition associated with the corresponding SAML component?
A. Two SAML assertions are used (authentication, authorization) that indicate that an SAML authority validated a specific subject.
B. SAML assertions are most commonly used to allow for identity federation and distributed authorization.
C. SAML binding specification describes how to embed SAML messages within the TCP and UDP protocols.
D. SAML profiles define how SAML messages, assertions, and protocols are to be implemented in SSL and TLS.
![]() B. SAML provides a model to allow two parties to share authentication information about one entity. The two parties are considered the service provider and the identity provider. The identity provider asserts information about the principal, such as whether or not the subject has been authenticated or has a particular attribute. The service provider uses the information supplied by the identity provider to make access decisions, including but not limited to, whether or not to trust the identity provider’s assertion. By trusting the identity provider’s information, the service provider can provide services without requiring the principal to authenticate again. This framework allows for federated identification and distributed authentication across domains.
B. SAML provides a model to allow two parties to share authentication information about one entity. The two parties are considered the service provider and the identity provider. The identity provider asserts information about the principal, such as whether or not the subject has been authenticated or has a particular attribute. The service provider uses the information supplied by the identity provider to make access decisions, including but not limited to, whether or not to trust the identity provider’s assertion. By trusting the identity provider’s information, the service provider can provide services without requiring the principal to authenticate again. This framework allows for federated identification and distributed authentication across domains.
![]() A is incorrect because there are three kinds of SAML assertions (authentication, attribute, authorization) that indicate an SAML authority validated a specific subject. Authentication assertion validates that the subject was authenticated by an SAML authority through a specific manner. For example, an assertion might indicate that Sam Long was authenticated on a specific date, at a specific time, through the use of a digital certificate, and authentication is valid for 30 minutes. The asserting party sends this authentication data to the relying party so that the subject can be authenticated on the relying party’s system and the subject does not need to log in again.
A is incorrect because there are three kinds of SAML assertions (authentication, attribute, authorization) that indicate an SAML authority validated a specific subject. Authentication assertion validates that the subject was authenticated by an SAML authority through a specific manner. For example, an assertion might indicate that Sam Long was authenticated on a specific date, at a specific time, through the use of a digital certificate, and authentication is valid for 30 minutes. The asserting party sends this authentication data to the relying party so that the subject can be authenticated on the relying party’s system and the subject does not need to log in again.
![]() C is incorrect because the SAML binding specification describes how to embed SAML messages within communications or messaging protocols to allow for SAML request-response message exchange. SAML bindings define how these message exchanges take place in application layer protocols (e.g., SOAP, HTTP), not transport layer protocols such as TCP and UDP. The SAML specification defines the SAML protocol, which is an XML-based request and response protocol for processing SAML assertions. This means that this specification pertains to a packet’s payload data, which works at the application layer of the OSI model. Transport layers are at a lower part of the network stack and have no direct interaction with this XML specification.
C is incorrect because the SAML binding specification describes how to embed SAML messages within communications or messaging protocols to allow for SAML request-response message exchange. SAML bindings define how these message exchanges take place in application layer protocols (e.g., SOAP, HTTP), not transport layer protocols such as TCP and UDP. The SAML specification defines the SAML protocol, which is an XML-based request and response protocol for processing SAML assertions. This means that this specification pertains to a packet’s payload data, which works at the application layer of the OSI model. Transport layers are at a lower part of the network stack and have no direct interaction with this XML specification.
![]() D is incorrect because SAML profiles define how SAML messages, assertions, and protocols are to be implemented in use cases. This specification does not deal with session and transport layer protocols as in SSL and TLS. Each profile within the SAML specification outlines how SAML messages, assertions, and protocols are to be used in specific scenarios. For example, one SAML profile outlines how SAML is to be used to support a single sign-on environment across multiple web applications. This profile defines how an SAML-aware client (i.e., web browser) is to be supported and how identification data is to be managed among multiple service providers.
D is incorrect because SAML profiles define how SAML messages, assertions, and protocols are to be implemented in use cases. This specification does not deal with session and transport layer protocols as in SSL and TLS. Each profile within the SAML specification outlines how SAML messages, assertions, and protocols are to be used in specific scenarios. For example, one SAML profile outlines how SAML is to be used to support a single sign-on environment across multiple web applications. This profile defines how an SAML-aware client (i.e., web browser) is to be supported and how identification data is to be managed among multiple service providers.
7. Brian has been asked to work on the virtual directory of his company’s new identity management system. Which of the following best describes a virtual directory?
A. Meta-directory
B. User attribute information stored in an HR database
C. Virtual container for data from multiple sources
D. A service that allows an administrator to configure and manage how identification takes place
![]() C. A network directory is a container for users and network resources. One directory does not contain (or know about) all of the users and resources within the enterprise, so a collection of directories must be used. A virtual directory gathers the necessary information used from sources scattered throughout the network and stores them in a central virtual directory (virtual container). This provides a unified view of all users’ digital identity information throughout the enterprise. The virtual directory periodically synchronizes itself with all of the identity stores (individual network directories) to ensure the most up-to-date information is being used by all applications and identity management components within the enterprise.
C. A network directory is a container for users and network resources. One directory does not contain (or know about) all of the users and resources within the enterprise, so a collection of directories must be used. A virtual directory gathers the necessary information used from sources scattered throughout the network and stores them in a central virtual directory (virtual container). This provides a unified view of all users’ digital identity information throughout the enterprise. The virtual directory periodically synchronizes itself with all of the identity stores (individual network directories) to ensure the most up-to-date information is being used by all applications and identity management components within the enterprise.
![]() A is incorrect because whereas a virtual directory is similar to a meta-directory, the meta-directory works with one directory, while a virtual directory works with multiple data sources. When an identity management component makes a call to a virtual directory, it has the capability to scan different directories throughout the enterprise, whereas a meta-directory only has the capability to scan the one directory it is associated with.
A is incorrect because whereas a virtual directory is similar to a meta-directory, the meta-directory works with one directory, while a virtual directory works with multiple data sources. When an identity management component makes a call to a virtual directory, it has the capability to scan different directories throughout the enterprise, whereas a meta-directory only has the capability to scan the one directory it is associated with.
![]() B is incorrect because it best describes an identity store. A lot of information stored in an identity management directory is scattered throughout the enterprise. User attribute information (employee status, job description, department, and so on) is usually stored in the HR database; authentication information could be in a Kerberos server; role and group identification information might be in a SQL database; and resource-oriented authentication information can be stored in Active Directory on a domain controller. These are commonly referred to as identity stores and are located in different places on the network. Many identity management products use virtual directories to call upon the data in these identity stores.
B is incorrect because it best describes an identity store. A lot of information stored in an identity management directory is scattered throughout the enterprise. User attribute information (employee status, job description, department, and so on) is usually stored in the HR database; authentication information could be in a Kerberos server; role and group identification information might be in a SQL database; and resource-oriented authentication information can be stored in Active Directory on a domain controller. These are commonly referred to as identity stores and are located in different places on the network. Many identity management products use virtual directories to call upon the data in these identity stores.
![]() D is incorrect because it describes the directory service. The directory service allows an administrator to configure and manage how identification, authentication, authorization, and access control occur within the network. It manages the objects within a directory by using namespaces and enforces the configured security policy by carrying out access control and identity management functions.
D is incorrect because it describes the directory service. The directory service allows an administrator to configure and manage how identification, authentication, authorization, and access control occur within the network. It manages the objects within a directory by using namespaces and enforces the configured security policy by carrying out access control and identity management functions.
8. Which of the following accurately describes Identity as a Service (IDaaS)?
A. A form of single sign-on (SSO) that spans multiple entities in an enterprise
B. A form of SSO that spans multiple independent enterprises
C. A way to provide SSO without multiple forms of authentication
D. A way to demonstrate identity without having to sign on
![]() B. Providers of IDaaS allow their clients to have a form of SSO that works across various otherwise independent accounts for independent vendors. A common example is the ability to use a Google account to create a Facebook page.
B. Providers of IDaaS allow their clients to have a form of SSO that works across various otherwise independent accounts for independent vendors. A common example is the ability to use a Google account to create a Facebook page.
![]() A is incorrect because SSO that spans multiple entities within an enterprise is most commonly provisioned by a public key infrastructure (PKI) such as is provided by Active Directory in a Microsoft environment or via an 802.1X protocol for other technologies.
A is incorrect because SSO that spans multiple entities within an enterprise is most commonly provisioned by a public key infrastructure (PKI) such as is provided by Active Directory in a Microsoft environment or via an 802.1X protocol for other technologies.
![]() C is incorrect because any SSO solution should provide for multifactor authentication.
C is incorrect because any SSO solution should provide for multifactor authentication.
![]() D is incorrect because all demonstrations of identity require authentication to be valid.
D is incorrect because all demonstrations of identity require authentication to be valid.
9. Which of the following correctly describes a federated identity and its role within identity management processes?
A. A nonportable identity that can be used across business boundaries
B. A portable identity that can be used across business boundaries
C. An identity that can be used within intranet virtual directories and identity stores
D. An identity specified by domain names that can be used across business boundaries
![]() B. A federated identity is a portable identity and its associated entitlements that can be used across business boundaries. It allows a user to be authenticated across multiple IT systems and enterprises. Identity federation is based upon linking a user’s otherwise distinct identities at two or more locations without the need to synchronize or consolidate directory information. Federated identity offers businesses and consumers a more convenient way of accessing distributed resources and is a key component of e-commerce.
B. A federated identity is a portable identity and its associated entitlements that can be used across business boundaries. It allows a user to be authenticated across multiple IT systems and enterprises. Identity federation is based upon linking a user’s otherwise distinct identities at two or more locations without the need to synchronize or consolidate directory information. Federated identity offers businesses and consumers a more convenient way of accessing distributed resources and is a key component of e-commerce.
![]() A is incorrect because a federated identity is portable. It could not be used across business boundaries if it was not portable—and that’s the whole point of a federated identity. The world continually gets smaller as technology brings people and companies closer together. Many times, when we are interacting with just one website, we are actually interacting with several different companies—we just don’t know it. The reason we don’t know it is because these companies are sharing our identity and authentication information behind the scenes. This is done to improve ease of use for the user.
A is incorrect because a federated identity is portable. It could not be used across business boundaries if it was not portable—and that’s the whole point of a federated identity. The world continually gets smaller as technology brings people and companies closer together. Many times, when we are interacting with just one website, we are actually interacting with several different companies—we just don’t know it. The reason we don’t know it is because these companies are sharing our identity and authentication information behind the scenes. This is done to improve ease of use for the user.
![]() C is incorrect because a federated identity is meant to be used across business boundaries—not within the organization. In other words, its use extends beyond the organization that owns the user data. Using federated identities, organizations with different technologies for directory services, security, and authentication can share applications, thereby allowing users to sign in to multiple applications with the same user ID, password, etc.
C is incorrect because a federated identity is meant to be used across business boundaries—not within the organization. In other words, its use extends beyond the organization that owns the user data. Using federated identities, organizations with different technologies for directory services, security, and authentication can share applications, thereby allowing users to sign in to multiple applications with the same user ID, password, etc.
![]() D is incorrect because a federated identity is not specified by a domain name. A federated identity is a portable identity and its associated entitlements. It includes the username, password, and other personal identification information used to sign in to an application.
D is incorrect because a federated identity is not specified by a domain name. A federated identity is a portable identity and its associated entitlements. It includes the username, password, and other personal identification information used to sign in to an application.
10. Security countermeasures should be transparent to users and attackers. Which of the following does NOT describe transparency?
A. User activities are monitored and tracked without negatively affecting system performance.
B. User activities are monitored and tracked without the user knowing about the mechanism that is carrying this out.
C. Users are allowed access in a manner that does not negatively affect business processes.
D. Unauthorized access attempts are denied and logged without the intruder knowing about the mechanism that is carrying this out.
![]() A. Unfortunately, security components usually affect system performance in one fashion or another, although many times it is unnoticeable to the user. There is a possibility that if a system’s performance is noticeably slow, this could be an indication that security countermeasures are in place. The reason that controls should be transparent is so that users and intruders do not know enough to be able to disable or bypass them. The controls should also not stand in the way of the company being able to carry out its necessary functions.
A. Unfortunately, security components usually affect system performance in one fashion or another, although many times it is unnoticeable to the user. There is a possibility that if a system’s performance is noticeably slow, this could be an indication that security countermeasures are in place. The reason that controls should be transparent is so that users and intruders do not know enough to be able to disable or bypass them. The controls should also not stand in the way of the company being able to carry out its necessary functions.
![]() B is incorrect because transparency is about activities being monitored and tracked without the user’s knowledge of the mechanism that is doing the monitoring and the tracking. While it is a best practice to tell users if their computer use is being monitored, it is not necessary to tell them how they are being monitored. If users are aware of the mechanisms that monitor their activities, then they may attempt to disable or bypass them.
B is incorrect because transparency is about activities being monitored and tracked without the user’s knowledge of the mechanism that is doing the monitoring and the tracking. While it is a best practice to tell users if their computer use is being monitored, it is not necessary to tell them how they are being monitored. If users are aware of the mechanisms that monitor their activities, then they may attempt to disable or bypass them.
![]() C is incorrect because there must be a balance between security and usability. This means that users should be allowed access—where appropriate—without affecting business processes. They should have the means to get their job done.
C is incorrect because there must be a balance between security and usability. This means that users should be allowed access—where appropriate—without affecting business processes. They should have the means to get their job done.
![]() D is incorrect because you do not want intruders to know about the mechanisms in place to deny and log unauthorized access attempts. An intruder could use this knowledge to disable or bypass the mechanism and successfully gain unauthorized access to network resources.
D is incorrect because you do not want intruders to know about the mechanisms in place to deny and log unauthorized access attempts. An intruder could use this knowledge to disable or bypass the mechanism and successfully gain unauthorized access to network resources.
11. What markup language allows for the sharing of application security policies to ensure that all applications are following the same security rules?
A. XML
B. SPML
C. XACML
D. GML
![]() C. Two or more companies can have a trust model set up to share identity, authorization, and authentication methods. This means that if Bill authenticates to his company’s software, this software can pass the authentication parameters to its partner’s software. This allows Bill to interact with the partner’s software without having to authenticate twice. This can happen through Extensible Access Control Markup Language (XACML), which allows two or more organizations to share application security policies based upon their trust model. XACML is a markup language and processing model that is implemented in XML. It declares access control policies and describes how to interpret them.
C. Two or more companies can have a trust model set up to share identity, authorization, and authentication methods. This means that if Bill authenticates to his company’s software, this software can pass the authentication parameters to its partner’s software. This allows Bill to interact with the partner’s software without having to authenticate twice. This can happen through Extensible Access Control Markup Language (XACML), which allows two or more organizations to share application security policies based upon their trust model. XACML is a markup language and processing model that is implemented in XML. It declares access control policies and describes how to interpret them.
![]() A is incorrect because XML (Extensible Markup Language) is a method for electronically coding documents and representing data structures such as those in web services. XML is not used to share security information. XML is an open standard that is more robust than its predecessor, HTML. In addition to serving as a markup language in and of itself, XML serves as the foundation for other more industry-specific XML standards. XML allows companies to use a markup language that meets their different needs while still being able to communicate with each other.
A is incorrect because XML (Extensible Markup Language) is a method for electronically coding documents and representing data structures such as those in web services. XML is not used to share security information. XML is an open standard that is more robust than its predecessor, HTML. In addition to serving as a markup language in and of itself, XML serves as the foundation for other more industry-specific XML standards. XML allows companies to use a markup language that meets their different needs while still being able to communicate with each other.
![]() B is incorrect because Service Provisioning Markup Language (SPML) is used by companies to exchange user, resource, and service provisioning information, not application security information. SPML is an XML-based framework developed by OASIS with the goal of allowing enterprise platforms (such as web portals and application servers) to generate provisioning requests across multiple companies for the purpose of the secure and quick setup of web services and applications.
B is incorrect because Service Provisioning Markup Language (SPML) is used by companies to exchange user, resource, and service provisioning information, not application security information. SPML is an XML-based framework developed by OASIS with the goal of allowing enterprise platforms (such as web portals and application servers) to generate provisioning requests across multiple companies for the purpose of the secure and quick setup of web services and applications.
![]() D is incorrect because Generalized Markup Language (GML) is a method created by IBM for formatting documents. It describes a document in terms of its parts (chapters, paragraphs, lists, etc.) and their relationship (heading levels). GML was a predecessor to Standard Generalized Markup Language (SGML) and Hypertext Markup Language (HTML).
D is incorrect because Generalized Markup Language (GML) is a method created by IBM for formatting documents. It describes a document in terms of its parts (chapters, paragraphs, lists, etc.) and their relationship (heading levels). GML was a predecessor to Standard Generalized Markup Language (SGML) and Hypertext Markup Language (HTML).
12. The importance of protecting audit logs generated by computers and network devices is highlighted by the fact that it is required by many of today’s regulations. Which of the following does NOT explain why audit logs should be protected?
A. If not properly protected, these logs may not be admissible during a prosecution.
B. Audit logs contain sensitive data and should only be accessible to a certain subset of people.
C. Intruders may attempt to scrub the logs to hide their activities.
D. The format of the logs should be unknown and unavailable to the intruder.
![]() D. Auditing tools are technical controls that track activity within a network, on a network device, or on a specific computer. Even though auditing is not an activity that will deny an entity access to a network or computer, it will track activities so that a security administrator can understand the types of access that took place, identify a security breach, or warn the administrator of suspicious activity. This information can be used to point out weaknesses of other technical controls and help the administrator understand where changes must be made to preserve the necessary security level within the environment. Intruders can also use this information to exploit those weaknesses, so audit logs should be protected through permissions, rights, and integrity controls, as in hashing algorithms. However, the format of systems logs is commonly standardized with all like systems. Hiding log formats is not a usual countermeasure and is not a reason to protect audit log files.
D. Auditing tools are technical controls that track activity within a network, on a network device, or on a specific computer. Even though auditing is not an activity that will deny an entity access to a network or computer, it will track activities so that a security administrator can understand the types of access that took place, identify a security breach, or warn the administrator of suspicious activity. This information can be used to point out weaknesses of other technical controls and help the administrator understand where changes must be made to preserve the necessary security level within the environment. Intruders can also use this information to exploit those weaknesses, so audit logs should be protected through permissions, rights, and integrity controls, as in hashing algorithms. However, the format of systems logs is commonly standardized with all like systems. Hiding log formats is not a usual countermeasure and is not a reason to protect audit log files.
![]() A is incorrect because due care must be taken to protect audit logs in order for them to be admissible in court. Audit trails can be used to provide alerts about any suspicious activities that can be investigated at a later time. In addition, they can be valuable in determining exactly how far an attack has gone and the extent of the damage that may have been caused. It is important to make sure a proper chain of custody is maintained to ensure any data collected can be properly and accurately represented in case it needs to be used for later events such as criminal proceedings or investigations.
A is incorrect because due care must be taken to protect audit logs in order for them to be admissible in court. Audit trails can be used to provide alerts about any suspicious activities that can be investigated at a later time. In addition, they can be valuable in determining exactly how far an attack has gone and the extent of the damage that may have been caused. It is important to make sure a proper chain of custody is maintained to ensure any data collected can be properly and accurately represented in case it needs to be used for later events such as criminal proceedings or investigations.
![]() B is incorrect because only the administrator and security personnel should be able to view, modify, and delete audit trail information. No other individuals should be able to view this data, much less modify or delete it. The integrity of the data can be ensured with the use of digital signatures, message digest tools, and strong access controls. Its confidentiality can be protected with encryption and access controls, if necessary, and it can be stored on write-once media to prevent loss or modification of the data. Unauthorized access attempts to audit logs should be captured and reported.
B is incorrect because only the administrator and security personnel should be able to view, modify, and delete audit trail information. No other individuals should be able to view this data, much less modify or delete it. The integrity of the data can be ensured with the use of digital signatures, message digest tools, and strong access controls. Its confidentiality can be protected with encryption and access controls, if necessary, and it can be stored on write-once media to prevent loss or modification of the data. Unauthorized access attempts to audit logs should be captured and reported.
![]() C is incorrect because the statement is true. If an intruder breaks into your house, he will do his best to cover his tracks by not leaving fingerprints or any other clues that can be used to tie him to the criminal activity. The same is true in computer fraud and illegal activity. The intruder will work to cover his tracks. Attackers often delete audit logs that hold this incriminating information. (Deleting such data within audit logs is called scrubbing.) Deleting this information can cause the administrator to not be alerted or aware of the security breach, and can destroy valuable data. Therefore, audit logs should be protected by strict access control.
C is incorrect because the statement is true. If an intruder breaks into your house, he will do his best to cover his tracks by not leaving fingerprints or any other clues that can be used to tie him to the criminal activity. The same is true in computer fraud and illegal activity. The intruder will work to cover his tracks. Attackers often delete audit logs that hold this incriminating information. (Deleting such data within audit logs is called scrubbing.) Deleting this information can cause the administrator to not be alerted or aware of the security breach, and can destroy valuable data. Therefore, audit logs should be protected by strict access control.
13. Of the following, what is the primary item that a capability table is based upon?
A. A subject
B. An object
C. A product
D. An application
![]() A. A capability table specifies the access rights a certain subject possesses pertaining to specific objects. A capability list (also referred to as a capability table) is different from an access control list (ACL) because the subject is bound to the capability table, whereas the object is bound to the ACL. A capability can be in the form of a token, ticket, or key. When a subject presents a capability component, the operating system (or application) will review the access rights and operations outlined in the capability component and allow the subject to carry out just those functions. A capability component is a data structure that contains a unique object identifier and the access rights the subject has to that object. The object may be a file, array, memory segment, or port.
A. A capability table specifies the access rights a certain subject possesses pertaining to specific objects. A capability list (also referred to as a capability table) is different from an access control list (ACL) because the subject is bound to the capability table, whereas the object is bound to the ACL. A capability can be in the form of a token, ticket, or key. When a subject presents a capability component, the operating system (or application) will review the access rights and operations outlined in the capability component and allow the subject to carry out just those functions. A capability component is a data structure that contains a unique object identifier and the access rights the subject has to that object. The object may be a file, array, memory segment, or port.
![]() B is incorrect because an object is bound to an access control list (ACL), not a capability component. ACLs are used in several operating systems, applications, and router configurations. They are lists of subjects that are authorized to access a specific object, and they define what level of authorization is granted. Authorization can be specified to an individual or group. ACLs map values from the access control matrix to the object. Whereas a capability corresponds to a row in the access control matrix, the ACL corresponds to a column of the matrix.
B is incorrect because an object is bound to an access control list (ACL), not a capability component. ACLs are used in several operating systems, applications, and router configurations. They are lists of subjects that are authorized to access a specific object, and they define what level of authorization is granted. Authorization can be specified to an individual or group. ACLs map values from the access control matrix to the object. Whereas a capability corresponds to a row in the access control matrix, the ACL corresponds to a column of the matrix.
![]() C is incorrect because a product can be an object or subject. If a user attempts to access a product (such as a program), the user is the subject and the product is the object. If a product attempts to access a database, the product is the subject and the database is the object. While a product could be a subject in a capability list for example, the best answer is A. A capability list indicates what objects a subject can access and the operations that can be carried out on those objects.
C is incorrect because a product can be an object or subject. If a user attempts to access a product (such as a program), the user is the subject and the product is the object. If a product attempts to access a database, the product is the subject and the database is the object. While a product could be a subject in a capability list for example, the best answer is A. A capability list indicates what objects a subject can access and the operations that can be carried out on those objects.
![]() D is incorrect because this is similar to answer C. If a user attempts to access an application, the user is the subject and the application is the object. If an application attempts to access a database, the application is the subject and the database is the object. While an application could be a subject in a capability list for example, the best answer is A. A capability list indicates what objects a subject can access and the operations that can be carried out on those objects.
D is incorrect because this is similar to answer C. If a user attempts to access an application, the user is the subject and the application is the object. If an application attempts to access a database, the application is the subject and the database is the object. While an application could be a subject in a capability list for example, the best answer is A. A capability list indicates what objects a subject can access and the operations that can be carried out on those objects.
14. Which markup language allows a company to send service requests and the receiving company to provision access to these services?
A. XML
B. SPML
C. SGML
D. HTML
![]() B. Service Provisioning Markup Language (SPML) is a markup language, built on the Extensible Markup Language (XML) framework, that exchanges information about which users should get access to what resources and services. So let’s say that an automobile company and a tire company only allow inventory managers within the automobile company to order tires. If Bob logs in to the automobile company’s inventory software and orders 40 tires, how does the tire company know that this request is coming from an authorized vendor and user with the Inventory Managers group? The automobile company’s software can pass user and group identity information to the tire company’s software. The tire company uses this identity information to make an authorization decision that then allows Bob’s request for 40 tires to be filled. Since both the sending and receiving companies are following one standard (XML), this type of interoperability can take place.
B. Service Provisioning Markup Language (SPML) is a markup language, built on the Extensible Markup Language (XML) framework, that exchanges information about which users should get access to what resources and services. So let’s say that an automobile company and a tire company only allow inventory managers within the automobile company to order tires. If Bob logs in to the automobile company’s inventory software and orders 40 tires, how does the tire company know that this request is coming from an authorized vendor and user with the Inventory Managers group? The automobile company’s software can pass user and group identity information to the tire company’s software. The tire company uses this identity information to make an authorization decision that then allows Bob’s request for 40 tires to be filled. Since both the sending and receiving companies are following one standard (XML), this type of interoperability can take place.
![]() A is incorrect because it is not the best answer to the question. SPML—which is based on XML—allows company interfaces to pass service requests and the receiving company to provision access to these services. This interoperability is made possible because the companies are both using XML, which is a set of rules for electronically encoding documents and web-based communication. XML is also used to encode arbitrary data structures, as in web services. It allows groups or companies to create information formats, like SPML, that enable a consistent means of sharing data.
A is incorrect because it is not the best answer to the question. SPML—which is based on XML—allows company interfaces to pass service requests and the receiving company to provision access to these services. This interoperability is made possible because the companies are both using XML, which is a set of rules for electronically encoding documents and web-based communication. XML is also used to encode arbitrary data structures, as in web services. It allows groups or companies to create information formats, like SPML, that enable a consistent means of sharing data.
![]() C is incorrect because Standard Generalized Markup Language (SGML) was one of the first markup languages developed. It does not provide user access or provisioning functionality. SGML was a standard that defines generalized markup tags for documents. It is a successor to Generalized Markup Language and came long before XML or SPML.
C is incorrect because Standard Generalized Markup Language (SGML) was one of the first markup languages developed. It does not provide user access or provisioning functionality. SGML was a standard that defines generalized markup tags for documents. It is a successor to Generalized Markup Language and came long before XML or SPML.
![]() D is incorrect because Hypertext Markup Language (HTML) was developed to annotate web pages. HTML is a precursor to XML and SGML. HTML provides a means of denoting structural semantics for text and other elements found on a web page. It can be used to embed images and objects and create interactive forms. However, it cannot allow company interfaces to pass service requests and the receiving company to provision access to these services.
D is incorrect because Hypertext Markup Language (HTML) was developed to annotate web pages. HTML is a precursor to XML and SGML. HTML provides a means of denoting structural semantics for text and other elements found on a web page. It can be used to embed images and objects and create interactive forms. However, it cannot allow company interfaces to pass service requests and the receiving company to provision access to these services.
15. There are several different types of centralized access control protocols. Which of the following is illustrated in the graphic that follows?

A. Diameter
B. Watchdog
C. RADIUS
D. TACACS+
![]() A. Diameter is an authentication, authorization, and auditing (AAA) protocol that provides the same type of functionality as RADIUS and TACACS+ but also provides more flexibility and capabilities to meet the new demands of today’s complex and diverse networks. At one time, all remote communication took place over Point-to-Point Protocol (PPP) and Serial Line Internet Protocol (SLIP) connections, and users authenticated themselves through Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP). Technology has become much more complicated and there are more devices and protocols to choose from than ever before. The Diameter protocol allows wireless devices, smart phones, and other devices to be able to authenticate themselves to networks using roaming protocols, Mobile IP, Ethernet over PPP, Voice over IP (VoIP), and others.
A. Diameter is an authentication, authorization, and auditing (AAA) protocol that provides the same type of functionality as RADIUS and TACACS+ but also provides more flexibility and capabilities to meet the new demands of today’s complex and diverse networks. At one time, all remote communication took place over Point-to-Point Protocol (PPP) and Serial Line Internet Protocol (SLIP) connections, and users authenticated themselves through Password Authentication Protocol (PAP) or Challenge Handshake Authentication Protocol (CHAP). Technology has become much more complicated and there are more devices and protocols to choose from than ever before. The Diameter protocol allows wireless devices, smart phones, and other devices to be able to authenticate themselves to networks using roaming protocols, Mobile IP, Ethernet over PPP, Voice over IP (VoIP), and others.
![]() B is incorrect because watchdog timers are commonly used to detect software faults, such as a process ending abnormally or hanging. The watchdog functionality sends out a type of “heartbeat” packet to determine whether a service is responding. If it is not, the process can be terminated or reset. These packets help prevent against software deadlocks, infinite loops, and process prioritization problems. This functionality can be used in AAA protocols to determine whether packets need to be re-sent and whether connections experiencing problems should be closed and reopened, but it is not an access control protocol itself.
B is incorrect because watchdog timers are commonly used to detect software faults, such as a process ending abnormally or hanging. The watchdog functionality sends out a type of “heartbeat” packet to determine whether a service is responding. If it is not, the process can be terminated or reset. These packets help prevent against software deadlocks, infinite loops, and process prioritization problems. This functionality can be used in AAA protocols to determine whether packets need to be re-sent and whether connections experiencing problems should be closed and reopened, but it is not an access control protocol itself.
![]() C is incorrect because Remote Authentication Dial-In User Service (RADIUS) is a network protocol and provides client/server authentication, authorization, and audit for remote users. A network may have access servers, DSL, ISDN, or a T1 line dedicated for remote users to communicate through. The access server requests the remote user’s logon credentials and passes them back to a RADIUS server, which houses the usernames and password values. The remote user is a client to the access server, and the access server is a client to the RADIUS server.
C is incorrect because Remote Authentication Dial-In User Service (RADIUS) is a network protocol and provides client/server authentication, authorization, and audit for remote users. A network may have access servers, DSL, ISDN, or a T1 line dedicated for remote users to communicate through. The access server requests the remote user’s logon credentials and passes them back to a RADIUS server, which houses the usernames and password values. The remote user is a client to the access server, and the access server is a client to the RADIUS server.
![]() D is incorrect because Terminal Access Controller Access Control System Plus (TACACS+) provides basically the same functionality as RADIUS. The RADIUS protocol combines the authentication and authorization functionality. TACACS+ uses a true AAA architecture, which separates each function out. This gives a network administrator more flexibility in how remote users are authenticated. Neither TACACS+ nor RADIUS can carry out these services for devices that need to communicate over VoIP, mobile IP, or other similar types of protocols.
D is incorrect because Terminal Access Controller Access Control System Plus (TACACS+) provides basically the same functionality as RADIUS. The RADIUS protocol combines the authentication and authorization functionality. TACACS+ uses a true AAA architecture, which separates each function out. This gives a network administrator more flexibility in how remote users are authenticated. Neither TACACS+ nor RADIUS can carry out these services for devices that need to communicate over VoIP, mobile IP, or other similar types of protocols.
16. An access control matrix is used in many operating systems and applications to control access between subjects and objects. What is the column in this type of matrix referred to as?

A. Capability table
B. Constrained interface
C. Role-based value
D. ACL
![]() D. Access control lists (ACLs) map values from the access control matrix to the object. Whereas a capability corresponds to a row in the access control matrix, the ACL corresponds to a column of the matrix. ACLs are used in several operating systems, applications, and router configurations. They are lists of subjects that are authorized to access specific objects, and they define what level of authorization is granted. Authorization can be specified to an individual or group. So the ACL is bound to an object and indicates which subjects can access it, and a capability table is bound to a subject and indicates which objects that subject can access.
D. Access control lists (ACLs) map values from the access control matrix to the object. Whereas a capability corresponds to a row in the access control matrix, the ACL corresponds to a column of the matrix. ACLs are used in several operating systems, applications, and router configurations. They are lists of subjects that are authorized to access specific objects, and they define what level of authorization is granted. Authorization can be specified to an individual or group. So the ACL is bound to an object and indicates which subjects can access it, and a capability table is bound to a subject and indicates which objects that subject can access.
![]() A is incorrect because a capability can be in the form of a token, ticket, or key and is a row within an access control matrix. When a subject presents a capability component, the operating system (or application) will review the access rights and operations outlined in the capability component and allow the subject to carry out just those functions. A capability component is a data structure that contains a unique object identifier and the access rights the subject has to that object. The object may be a file, array, memory segment, or port. Each user, process, and application in a capability system has a list of capabilities it can carry out.
A is incorrect because a capability can be in the form of a token, ticket, or key and is a row within an access control matrix. When a subject presents a capability component, the operating system (or application) will review the access rights and operations outlined in the capability component and allow the subject to carry out just those functions. A capability component is a data structure that contains a unique object identifier and the access rights the subject has to that object. The object may be a file, array, memory segment, or port. Each user, process, and application in a capability system has a list of capabilities it can carry out.
![]() B is incorrect because constrained user interfaces restrict users’ access abilities by not allowing them to request certain functions or information or to have access to specific system resources. Three major types of restricted interfaces exist: menus and shells, database views, and physically constrained interfaces. When menu and shell restrictions are used, the options users are given are the commands they can execute. For example, if an administrator wants users to be able to execute only one program, that program would be the only choice available on the menu. If restricted shells were used, the shell would contain only the commands the administrator wants the users to be able to execute.
B is incorrect because constrained user interfaces restrict users’ access abilities by not allowing them to request certain functions or information or to have access to specific system resources. Three major types of restricted interfaces exist: menus and shells, database views, and physically constrained interfaces. When menu and shell restrictions are used, the options users are given are the commands they can execute. For example, if an administrator wants users to be able to execute only one program, that program would be the only choice available on the menu. If restricted shells were used, the shell would contain only the commands the administrator wants the users to be able to execute.
![]() C is incorrect because a role-based access control (RBAC) model, also called nondiscretionary access control, uses a centrally administered set of controls to determine how subjects and objects interact. This type of model lets access to resources be based on the role the user holds within the company. It is referred to as nondiscretionary because assigning a user to a role is unavoidably imposed. This means that if you are assigned only to the Contractor role in a company, there is nothing you can do about it. You don’t have the discretion to determine what role you will be assigned.
C is incorrect because a role-based access control (RBAC) model, also called nondiscretionary access control, uses a centrally administered set of controls to determine how subjects and objects interact. This type of model lets access to resources be based on the role the user holds within the company. It is referred to as nondiscretionary because assigning a user to a role is unavoidably imposed. This means that if you are assigned only to the Contractor role in a company, there is nothing you can do about it. You don’t have the discretion to determine what role you will be assigned.
17. What technology within identity management is illustrated in the graphic that follows?

A. User provisioning
B. Federated identity
C. Directories
D. Web access management
![]() B. A federated identity is a portable identity and its associated entitlements that can be used across business boundaries. It allows a user to be authenticated across multiple IT systems and enterprises. Identity federation is based upon linking a user’s otherwise distinct identities at two or more locations without the need to synchronize or consolidate directory information. Federated identity offers businesses and consumers a more convenient way of accessing distributed resources and is a key component of e-commerce.
B. A federated identity is a portable identity and its associated entitlements that can be used across business boundaries. It allows a user to be authenticated across multiple IT systems and enterprises. Identity federation is based upon linking a user’s otherwise distinct identities at two or more locations without the need to synchronize or consolidate directory information. Federated identity offers businesses and consumers a more convenient way of accessing distributed resources and is a key component of e-commerce.
![]() A is incorrect because user provisioning refers to the creation, maintenance, and deactivation of user objects and attributes as they exist in one or more systems, directories, or applications in response to business processes. User provisioning software may include one or more of the following components: change propagation, self-service workflow, consolidated user administration, delegated user administration, and federated change control. User objects may represent employees, contractors, vendors, partners, customers, or other recipients of a service. Services may include e-mail, access to a database, access to a file server or mainframe, and so on. User provisioning can be a function with federation identification, but this is not what the graphic illustrates.
A is incorrect because user provisioning refers to the creation, maintenance, and deactivation of user objects and attributes as they exist in one or more systems, directories, or applications in response to business processes. User provisioning software may include one or more of the following components: change propagation, self-service workflow, consolidated user administration, delegated user administration, and federated change control. User objects may represent employees, contractors, vendors, partners, customers, or other recipients of a service. Services may include e-mail, access to a database, access to a file server or mainframe, and so on. User provisioning can be a function with federation identification, but this is not what the graphic illustrates.
![]() C is incorrect because while most enterprises have some type of directory that contains information pertaining to the company’s network resources and users, those directories do not commonly spread across different businesses. Most directories follow a hierarchical database format, based on the X.500 standard, and a type of protocol, as in Lightweight Directory Access Protocol (LDAP), that allows subjects and applications to interact with the directory. Applications can request information about a particular user by making an LDAP request to the directory, and users can request information about a specific resource by using a similar request. While directories can work within a federated framework, this is not what the graphic shows.
C is incorrect because while most enterprises have some type of directory that contains information pertaining to the company’s network resources and users, those directories do not commonly spread across different businesses. Most directories follow a hierarchical database format, based on the X.500 standard, and a type of protocol, as in Lightweight Directory Access Protocol (LDAP), that allows subjects and applications to interact with the directory. Applications can request information about a particular user by making an LDAP request to the directory, and users can request information about a specific resource by using a similar request. While directories can work within a federated framework, this is not what the graphic shows.
![]() D is incorrect because web access management (WAM) software controls what users can access when using a web browser to interact with web-based enterprise assets. This type of technology is continually becoming more robust and experiencing increased deployment. This is because of the increased use of e-commerce, online banking, content providing, web services, and more. More complexity comes in with all the different ways a user can authenticate (password, digital certificate, token, and others), the resources and services that may be available to the user (transfer funds, purchase product, update profile, and so forth), and the necessary infrastructure components. The infrastructure is usually made up of a web server farm (many servers), a directory that contains the users’ accounts and attributes, a database, a couple of firewalls, and some routers, all laid out in a tiered architecture.
D is incorrect because web access management (WAM) software controls what users can access when using a web browser to interact with web-based enterprise assets. This type of technology is continually becoming more robust and experiencing increased deployment. This is because of the increased use of e-commerce, online banking, content providing, web services, and more. More complexity comes in with all the different ways a user can authenticate (password, digital certificate, token, and others), the resources and services that may be available to the user (transfer funds, purchase product, update profile, and so forth), and the necessary infrastructure components. The infrastructure is usually made up of a web server farm (many servers), a directory that contains the users’ accounts and attributes, a database, a couple of firewalls, and some routers, all laid out in a tiered architecture.
18. There are different ways that specific technologies can create one-time passwords for authentication purposes. What type of technology is illustrated in the graphic that follows?

A. Counter synchronous token
B. Asynchronous token
C. Mandatory token
D. Synchronous token
![]() D. A synchronous token device synchronizes with the authentication service by using time or a counter as the core piece of the authentication process. If the synchronization is time based, as shown in this graphic, the token device and the authentication service must hold the same time within their internal clocks. The time value on the token device and a secret key are used to create the one-time password, which is displayed to the user. The user enters this value and a user ID into the computer, which then passes them to the server running the authentication service. The authentication service decrypts this value and compares it to the value it expected. If the two match, the user is authenticated and allowed to use the computer and resources.
D. A synchronous token device synchronizes with the authentication service by using time or a counter as the core piece of the authentication process. If the synchronization is time based, as shown in this graphic, the token device and the authentication service must hold the same time within their internal clocks. The time value on the token device and a secret key are used to create the one-time password, which is displayed to the user. The user enters this value and a user ID into the computer, which then passes them to the server running the authentication service. The authentication service decrypts this value and compares it to the value it expected. If the two match, the user is authenticated and allowed to use the computer and resources.
![]() A is incorrect because if the token device and authentication service use counter-synchronization, it is not based on time as shown in the graphic. When using a counter-synchronization token device, the user will need to initiate the creation of the one-time password by pushing a button on the token device. This causes the token device and the authentication service to advance to the next authentication value. This value and a base secret are hashed and displayed to the user. The user enters this resulting value along with a user ID to be authenticated. In either time- or counter-based synchronization, the token device and authentication service must share the same secret base key used for encryption and decryption.
A is incorrect because if the token device and authentication service use counter-synchronization, it is not based on time as shown in the graphic. When using a counter-synchronization token device, the user will need to initiate the creation of the one-time password by pushing a button on the token device. This causes the token device and the authentication service to advance to the next authentication value. This value and a base secret are hashed and displayed to the user. The user enters this resulting value along with a user ID to be authenticated. In either time- or counter-based synchronization, the token device and authentication service must share the same secret base key used for encryption and decryption.
![]() B is incorrect because a token device using an asynchronous token–generating method employs a challenge/response scheme to authenticate the user. This technology does not use synchronization but instead uses discrete steps in its authentication process. In this situation, the authentication server sends the user a challenge, a random value also called a nonce. The user enters this random value into the token device, which encrypts it and returns a value the user uses as a one-time password. The user sends this value, along with a username, to the authentication server. If the authentication server can decrypt the value and it is the same challenge value sent earlier, the user is authenticated.
B is incorrect because a token device using an asynchronous token–generating method employs a challenge/response scheme to authenticate the user. This technology does not use synchronization but instead uses discrete steps in its authentication process. In this situation, the authentication server sends the user a challenge, a random value also called a nonce. The user enters this random value into the token device, which encrypts it and returns a value the user uses as a one-time password. The user sends this value, along with a username, to the authentication server. If the authentication server can decrypt the value and it is the same challenge value sent earlier, the user is authenticated.
![]() C is incorrect because there is no such thing as a mandatory token. This is a distracter answer.
C is incorrect because there is no such thing as a mandatory token. This is a distracter answer.
19. Which of the following best describes how SAML, SOAP, and HTTP commonly work together in an environment that provides web services?
A. The security attributes are put into SAML format. The web service request and the authentication data are encrypted in a SOAP message. The message is transmitted in an HTTP connection.
B. The security attributes are put into SAML format. The web service request and the authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection over TLS.
C. The authentication data is put into SAML format. The web service request and authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection.
D. The authentication data is put into SAML format. The HTTP request and the authentication data are encapsulated in a SOAP message. The message is transmitted in an HTTP connection.
![]() C. As an example, when you log in to your company’s portal and double-click a link (e.g., Salesforce), your company’s portal will take this request and your authentication data and package them up in an Security Assertion Markup Language (SAML) format and encapsulate that data into a Simple Object Access Protocol (SOAP) message. This message would be transmitted over an HTTP connection to the Salesforce vendor site, and once you are authenticated you can interact with the vendor software. SAML packages up authentication data, SOAP packages up web service requests and SAML data, and the request is transmitted over an HTTP connection.
C. As an example, when you log in to your company’s portal and double-click a link (e.g., Salesforce), your company’s portal will take this request and your authentication data and package them up in an Security Assertion Markup Language (SAML) format and encapsulate that data into a Simple Object Access Protocol (SOAP) message. This message would be transmitted over an HTTP connection to the Salesforce vendor site, and once you are authenticated you can interact with the vendor software. SAML packages up authentication data, SOAP packages up web service requests and SAML data, and the request is transmitted over an HTTP connection.
![]() A is incorrect because SAML is an XML-based open standard for exchanging authentication and authorization data between security domains—that is, between an identity provider (a producer of assertions) and a service provider (a consumer of assertions). So authentication data is used with SAML, not security attributes. Also, SOAP encapsulates messages, it does not encrypt them.
A is incorrect because SAML is an XML-based open standard for exchanging authentication and authorization data between security domains—that is, between an identity provider (a producer of assertions) and a service provider (a consumer of assertions). So authentication data is used with SAML, not security attributes. Also, SOAP encapsulates messages, it does not encrypt them.
![]() B is incorrect because authentication data is used with SAML and the transmission does not take place over a TLS connection by default. The transmission can take place over SSL or TLS, but this was not what was outlined in the question.
B is incorrect because authentication data is used with SAML and the transmission does not take place over a TLS connection by default. The transmission can take place over SSL or TLS, but this was not what was outlined in the question.
![]() D is incorrect because SOAP encapsulates web service requests and data, not HTTP. After SOAP encapsulates web service data, it is then encapsulated with HTTP for transmission purposes.
D is incorrect because SOAP encapsulates web service requests and data, not HTTP. After SOAP encapsulates web service data, it is then encapsulated with HTTP for transmission purposes.
20. Jill is establishing a companywide sales program that will require different user groups with different privileges to access information on a centralized database. How should the security manager secure the database?
A. Increase the database’s security controls and provide more granularity.
B. Implement access controls that display each user’s permissions each time they access the database.
C. Change the database’s classification label to a higher security status.
D. Decrease the security so that all users can access the information as needed.
![]() A. The best approach to securing the database in this situation would be to increase the controls and assign very granular permissions. These measures would ensure that users cannot abuse their privileges and that the confidentiality of the information would be maintained. Granularity of permissions gives network administrators and security professionals additional control over the resources they are charged with protecting, and a fine level of detail enables them to give individuals just the precise level of access they need.
A. The best approach to securing the database in this situation would be to increase the controls and assign very granular permissions. These measures would ensure that users cannot abuse their privileges and that the confidentiality of the information would be maintained. Granularity of permissions gives network administrators and security professionals additional control over the resources they are charged with protecting, and a fine level of detail enables them to give individuals just the precise level of access they need.
![]() B is incorrect because implementing access controls that display each user’s permissions each time they access the database is an example of one control. It is not the overall way of dealing with user access to a full database of information. This may be an example of increasing database security controls, but it is only one example, and more would need to be put into place.
B is incorrect because implementing access controls that display each user’s permissions each time they access the database is an example of one control. It is not the overall way of dealing with user access to a full database of information. This may be an example of increasing database security controls, but it is only one example, and more would need to be put into place.
![]() C is incorrect because the classification level of the information in the database was previously determined based on its confidentiality, integrity, and availability levels. These levels do not change simply because more users need access to the data. Thus, you would never increase or decrease the classification level of information when more users or groups need to access that information. Increasing the classification level would only mean a smaller subset of users could access the database.
C is incorrect because the classification level of the information in the database was previously determined based on its confidentiality, integrity, and availability levels. These levels do not change simply because more users need access to the data. Thus, you would never increase or decrease the classification level of information when more users or groups need to access that information. Increasing the classification level would only mean a smaller subset of users could access the database.
![]() D is incorrect because it puts data at risk. If security is decreased so that all users can access it as needed, then users with lower privileges will be able to access data of higher classification levels. Lower security also makes it easier for intruders to break into the database. As stated in answer C, a classification level is not changed just because the number of users who need to access the data increases or decreases.
D is incorrect because it puts data at risk. If security is decreased so that all users can access it as needed, then users with lower privileges will be able to access data of higher classification levels. Lower security also makes it easier for intruders to break into the database. As stated in answer C, a classification level is not changed just because the number of users who need to access the data increases or decreases.
21. Bethany is working on a mandatory access control (MAC) system. She has been working on a file that was classified as Secret. She can no longer access this file because it has been reclassified as Top Secret. She deduces that the project she was working on has just increased in confidentiality and she now knows more about this project than her clearance and need-to-know allows. Which of the following refers to a concept that attempts to prevent this type of scenario from occurring?
A. Covert storage channel
B. Inference attack
C. Noninterference
D. Aggregation
![]() C. Multilevel security properties can be expressed in many ways, one being noninterference. This concept is implemented to ensure that any actions that take place at a higher security level do not affect or interfere with actions that take place at a lower level. So if an entity at a higher security level performs an action, it cannot change the state for the entity at the lower level. If a lower-level entity were aware of a certain activity that took place by an entity at a higher level and the state of the system changed for this lower-level entity, the entity might be able to deduce too much information about the activities of the higher state, which in turn is a way of leaking information.
C. Multilevel security properties can be expressed in many ways, one being noninterference. This concept is implemented to ensure that any actions that take place at a higher security level do not affect or interfere with actions that take place at a lower level. So if an entity at a higher security level performs an action, it cannot change the state for the entity at the lower level. If a lower-level entity were aware of a certain activity that took place by an entity at a higher level and the state of the system changed for this lower-level entity, the entity might be able to deduce too much information about the activities of the higher state, which in turn is a way of leaking information.
![]() A is incorrect because a covert channel allows for the ability to share information between processes that weren’t intended to communicate. Noninterference is a model intended to prevent covert channels along with other malicious ways of communicating. The model looks at the shared resources that the different users of a system will use and tries to identify how information can be passed from a process working at a higher security clearance to a process working at a lower security clearance. If two users are working on the same system at the same time, they will most likely have to share some type of resources. So the model is made up of rules to ensure that User A cannot carry out any activities that can allow User B to infer information she does not have the clearance to know.
A is incorrect because a covert channel allows for the ability to share information between processes that weren’t intended to communicate. Noninterference is a model intended to prevent covert channels along with other malicious ways of communicating. The model looks at the shared resources that the different users of a system will use and tries to identify how information can be passed from a process working at a higher security clearance to a process working at a lower security clearance. If two users are working on the same system at the same time, they will most likely have to share some type of resources. So the model is made up of rules to ensure that User A cannot carry out any activities that can allow User B to infer information she does not have the clearance to know.
![]() B is incorrect because an inference attack refers to Bethany’s ability to infer that the project that she was working on is now Top Secret and has increased in importance and secrecy. The question is asking for the concept that helps to prevent an inference attack. An inference attack occurs when someone has access to some type of information and can infer (or guess) something that she does not have the clearance level or authority to know. For example, let’s say that Tom is working on a file that contains information about supplies that are being sent to Russia. He closes out of that file and one hour later attempts to open the same file. During this time, the file’s classification has been elevated to Top Secret, so when Tom attempts to access it, he is denied. Tom can infer that some type of Top Secret mission is getting ready to take place with Russia. He does not have clearance to know this; thus, it would be an inference attack or “leaking information.”
B is incorrect because an inference attack refers to Bethany’s ability to infer that the project that she was working on is now Top Secret and has increased in importance and secrecy. The question is asking for the concept that helps to prevent an inference attack. An inference attack occurs when someone has access to some type of information and can infer (or guess) something that she does not have the clearance level or authority to know. For example, let’s say that Tom is working on a file that contains information about supplies that are being sent to Russia. He closes out of that file and one hour later attempts to open the same file. During this time, the file’s classification has been elevated to Top Secret, so when Tom attempts to access it, he is denied. Tom can infer that some type of Top Secret mission is getting ready to take place with Russia. He does not have clearance to know this; thus, it would be an inference attack or “leaking information.”
![]() D is incorrect because aggregation is the act of combining information from separate sources. The combination of the data forms new information, which the subject does not have the necessary rights to access. The combined information can have a sensitivity that is greater than that of the individual parts. Aggregation happens when a user does not have the clearance or permission to access specific information but does have the permission to access components of this information. She can then figure out the rest and obtain restricted information.
D is incorrect because aggregation is the act of combining information from separate sources. The combination of the data forms new information, which the subject does not have the necessary rights to access. The combined information can have a sensitivity that is greater than that of the individual parts. Aggregation happens when a user does not have the clearance or permission to access specific information but does have the permission to access components of this information. She can then figure out the rest and obtain restricted information.
22. A number of attacks can be performed against smart cards. Side-channel is a class of attacks that doesn’t try to compromise a flaw or weakness. Which of the following is NOT a side-channel attack?
A. Differential power analysis
B. Microprobing analysis
C. Timing analysis
D. Electromagnetic analysis
![]() B. A noninvasive attack is one in which the attacker watches how something works and how it reacts in different situations instead of trying to “invade” it with more intrusive measures. Examples of side-channel attacks are fault generation, differential power analysis, electromagnetic analysis, timing, and software attacks. These types of attacks are used to uncover sensitive information about how a component works without trying to compromise any type of flaw or weakness. A more intrusive smart card attack is microprobing. Microprobing uses needles and ultrasonic vibration to remove the outer protective material on the card’s circuits. Once this is complete, data can be accessed and manipulated by directly tapping into the card’s ROM chips.
B. A noninvasive attack is one in which the attacker watches how something works and how it reacts in different situations instead of trying to “invade” it with more intrusive measures. Examples of side-channel attacks are fault generation, differential power analysis, electromagnetic analysis, timing, and software attacks. These types of attacks are used to uncover sensitive information about how a component works without trying to compromise any type of flaw or weakness. A more intrusive smart card attack is microprobing. Microprobing uses needles and ultrasonic vibration to remove the outer protective material on the card’s circuits. Once this is complete, data can be accessed and manipulated by directly tapping into the card’s ROM chips.
![]() A is incorrect because differential power analysis (DPA) is a noninvasive attack. DPA involves examining the power emissions released during processing. By statistically analyzing data from multiple cryptographic operations, for example, an attacker can determine the intermediate values within cryptographic computations. This can be done without any knowledge of how the target device is designed. Thus, an attacker can extract cryptographic keys or other sensitive information from the card.
A is incorrect because differential power analysis (DPA) is a noninvasive attack. DPA involves examining the power emissions released during processing. By statistically analyzing data from multiple cryptographic operations, for example, an attacker can determine the intermediate values within cryptographic computations. This can be done without any knowledge of how the target device is designed. Thus, an attacker can extract cryptographic keys or other sensitive information from the card.
![]() C is incorrect because a timing analysis is a noninvasive attack. It involves calculating the time a specific function takes to complete its task. Timing analysis attacks are based on measuring how much time various computations take to perform. For example, by observing how long it takes a smart card to transfer key information, it is sometimes possible to determine how long the key is in this instance.
C is incorrect because a timing analysis is a noninvasive attack. It involves calculating the time a specific function takes to complete its task. Timing analysis attacks are based on measuring how much time various computations take to perform. For example, by observing how long it takes a smart card to transfer key information, it is sometimes possible to determine how long the key is in this instance.
![]() D is incorrect because electromagnetic analysis is a noninvasive attack that involves examining the frequencies emitted. All electric currents emit electromagnetic emanations. In smart cards, the power consumption—and, therefore, the electromagnetic emanation field—varies as data is processed. An electromagnetic analysis attempts to make correlations between the data and the electromagnetic emanations in an effort to uncover cryptographic keys or other sensitive information on the smart card.
D is incorrect because electromagnetic analysis is a noninvasive attack that involves examining the frequencies emitted. All electric currents emit electromagnetic emanations. In smart cards, the power consumption—and, therefore, the electromagnetic emanation field—varies as data is processed. An electromagnetic analysis attempts to make correlations between the data and the electromagnetic emanations in an effort to uncover cryptographic keys or other sensitive information on the smart card.
23. Emily is listening to network traffic and capturing passwords as they are sent to the authentication server. She plans to use the passwords as part of a future attack. What type of attack is this?
A. Brute-force attack
B. Dictionary attack
C. Social engineering attack
D. Replay attack
![]() D. A replay attack occurs when an intruder obtains and stores information and later uses it to gain unauthorized access. In this case, Emily is using a technique called electronic monitoring (sniffing) to obtain passwords being sent over the wire to an authentication server. She can later use the passwords to gain access to network resources. Even if the passwords are encrypted, the retransmission of valid credentials can be sufficient to obtain access.
D. A replay attack occurs when an intruder obtains and stores information and later uses it to gain unauthorized access. In this case, Emily is using a technique called electronic monitoring (sniffing) to obtain passwords being sent over the wire to an authentication server. She can later use the passwords to gain access to network resources. Even if the passwords are encrypted, the retransmission of valid credentials can be sufficient to obtain access.
![]() A is incorrect because a brute-force attack is performed with tools that cycle through many possible character, number, and symbol combinations to uncover a password. One way to prevent a successful brute-force attack is to restrict the number of login attempts that can be performed on a system. An administrator can set operating parameters that allow a certain number of failed logon attempts to be accepted before a user is locked out; this is a type of clipping level.
A is incorrect because a brute-force attack is performed with tools that cycle through many possible character, number, and symbol combinations to uncover a password. One way to prevent a successful brute-force attack is to restrict the number of login attempts that can be performed on a system. An administrator can set operating parameters that allow a certain number of failed logon attempts to be accepted before a user is locked out; this is a type of clipping level.
![]() B is incorrect because a dictionary attack involves the automated comparison of the user’s password to files of thousands of words until a match is found. Dictionary attacks are successful because users tend to choose passwords that are short, are single words, or are predictable variations of dictionary words.
B is incorrect because a dictionary attack involves the automated comparison of the user’s password to files of thousands of words until a match is found. Dictionary attacks are successful because users tend to choose passwords that are short, are single words, or are predictable variations of dictionary words.
![]() C is incorrect because in a social engineering attack the attacker falsely convinces an individual that she has the necessary authorization to access specific resources. Social engineering is carried out against people directly and is not considered a technical attack necessarily. The best defense against social engineering is user education. Password requirements, protection, and generation should be addressed in security awareness programs so that users understand why they should protect their passwords and how passwords can be stolen.
C is incorrect because in a social engineering attack the attacker falsely convinces an individual that she has the necessary authorization to access specific resources. Social engineering is carried out against people directly and is not considered a technical attack necessarily. The best defense against social engineering is user education. Password requirements, protection, and generation should be addressed in security awareness programs so that users understand why they should protect their passwords and how passwords can be stolen.
24. Which of the following is the best way to reduce brute-force attacks that allow intruders to uncover users’ passwords?
A. Increase the clipping level.
B. Lock out an account for a certain amount of time after the clipping level is reached.
C. After a threshold of failed login attempts is met, the administrator must physically lock out the account.
D. Choose a weaker algorithm that encrypts the password file.
![]() B. A brute-force attack is an attack that continually tries different inputs to achieve a predefined goal, which can then be used to obtain credentials for unauthorized access. A brute-force attack to uncover passwords means that the intruder is attempting all possible sequences of characters to uncover the correct password. If the account would be disabled (or locked out) after this type of attack attempt took place, this would prove to be a good countermeasure.
B. A brute-force attack is an attack that continually tries different inputs to achieve a predefined goal, which can then be used to obtain credentials for unauthorized access. A brute-force attack to uncover passwords means that the intruder is attempting all possible sequences of characters to uncover the correct password. If the account would be disabled (or locked out) after this type of attack attempt took place, this would prove to be a good countermeasure.
![]() A is incorrect because clipping levels should be implemented to establish a baseline of user activity and acceptable errors. An entity attempting to log in to an account should be locked out once the clipping level is met. A higher clipping level gives an attacker more attempts between alerts or lockout. Decreasing the clipping level would be a good countermeasure.
A is incorrect because clipping levels should be implemented to establish a baseline of user activity and acceptable errors. An entity attempting to log in to an account should be locked out once the clipping level is met. A higher clipping level gives an attacker more attempts between alerts or lockout. Decreasing the clipping level would be a good countermeasure.
![]() C is incorrect because it is not practical to have an administrator physically lock out accounts. This type of activity can easily be taken care of through automated software mechanisms. Accounts should be automatically locked out for a certain amount of time after a threshold of failed login attempts has been met.
C is incorrect because it is not practical to have an administrator physically lock out accounts. This type of activity can easily be taken care of through automated software mechanisms. Accounts should be automatically locked out for a certain amount of time after a threshold of failed login attempts has been met.
![]() D is incorrect because using a weaker algorithm that encrypts passwords and/or password files would increase the likelihood of success of a brute-force attack.
D is incorrect because using a weaker algorithm that encrypts passwords and/or password files would increase the likelihood of success of a brute-force attack.
25. Phishing and pharming are similar. Which of the following correctly describes the difference between phishing and pharming?
A. Personal information is collected from victims through legitimate-looking websites in phishing attacks, while personal information is collected from victims via e-mail in pharming attacks.
B. Phishing attacks point e-mail recipients to a form where victims input personal information, while pharming attacks use pop-up forms at legitimate websites to collect personal information from victims.
C. Victims are pointed to a fake website with a domain name that looks similar to a legitimate site’s domain name in a phishing attack, while victims are directed to a fake website as a result of a legitimate domain name being incorrectly translated by the DNS server in a pharming attack.
D. Phishing is a technical attack, while pharming is a type of social engineering.
![]() C. In both phishing and pharming, attackers can create websites that look very similar to legitimate sites in an effort to collect personal information from victims. In a phishing attack, attackers can provide URLs with domain names that look very similar to the legitimate site’s address. For example, www.amazon.com might become www.amzaon.com. Or use a specially placed @ symbol. For example, [email protected] would actually take the victim to the website notmsn.com and provide the username of www.msn.com to this website. The username www.msn.com would not be a valid username for notmsn.com, so the victim would just be shown the home page of notmsn.com. Now, notmsn.com is a nefarious site created to look and feel just like www.msn.com. The victim feels he is at the legitimate site and logs in with his credentials. In a pharming attack, the victim is given a legitimate domain name, but that domain name is redirected to the attacker’s website as a result of DNS poisoning. When the DNS server is poisoned to carry out a pharming attack, the records have been changed so that instead of sending the correct IP address for www.logicalsecurity.com, it sends the IP address of a legitimate-looking, but fake, website created by the attacker.
C. In both phishing and pharming, attackers can create websites that look very similar to legitimate sites in an effort to collect personal information from victims. In a phishing attack, attackers can provide URLs with domain names that look very similar to the legitimate site’s address. For example, www.amazon.com might become www.amzaon.com. Or use a specially placed @ symbol. For example, [email protected] would actually take the victim to the website notmsn.com and provide the username of www.msn.com to this website. The username www.msn.com would not be a valid username for notmsn.com, so the victim would just be shown the home page of notmsn.com. Now, notmsn.com is a nefarious site created to look and feel just like www.msn.com. The victim feels he is at the legitimate site and logs in with his credentials. In a pharming attack, the victim is given a legitimate domain name, but that domain name is redirected to the attacker’s website as a result of DNS poisoning. When the DNS server is poisoned to carry out a pharming attack, the records have been changed so that instead of sending the correct IP address for www.logicalsecurity.com, it sends the IP address of a legitimate-looking, but fake, website created by the attacker.
![]() A is incorrect because a pharming attack does not commonly involve the collection of information via e-mail. In fact, the benefit of a pharming attack to the attacker is that it can affect a large amount of victims without the need to send out e-mails. Like a phishing attack, a pharming attack involves a seemingly legitimate, yet fake, website. Victims are directed to the fake website because the hostname is incorrectly resolved as a result of DNS poisoning.
A is incorrect because a pharming attack does not commonly involve the collection of information via e-mail. In fact, the benefit of a pharming attack to the attacker is that it can affect a large amount of victims without the need to send out e-mails. Like a phishing attack, a pharming attack involves a seemingly legitimate, yet fake, website. Victims are directed to the fake website because the hostname is incorrectly resolved as a result of DNS poisoning.
![]() B is incorrect because both descriptions are true of phishing attacks. Pharming attacks do not use pop-up forms. However, some phishing attacks use pop-up forms when a victim is at a legitimate website. So if you were at your bank’s actual website and a pop-up window appeared asking you for some sensitive information, this probably wouldn’t worry you, since you were communicating with your actual bank’s website. You may believe the window came from your bank’s web server, so you fill it out as instructed. Unfortunately, this pop-up window could be from another source entirely, and your data could be placed right in the attacker’s hands, not your bank’s.
B is incorrect because both descriptions are true of phishing attacks. Pharming attacks do not use pop-up forms. However, some phishing attacks use pop-up forms when a victim is at a legitimate website. So if you were at your bank’s actual website and a pop-up window appeared asking you for some sensitive information, this probably wouldn’t worry you, since you were communicating with your actual bank’s website. You may believe the window came from your bank’s web server, so you fill it out as instructed. Unfortunately, this pop-up window could be from another source entirely, and your data could be placed right in the attacker’s hands, not your bank’s.
![]() D is incorrect because both attacks are technical ways of carrying out social engineering. Phishing is a type of social engineering with the goal of obtaining personal information, credentials, credit card numbers, or financial data. The attackers lure, or fish, for sensitive data through various different methods, such as e-mail and pop-up forms. Pharming involves DNS poisoning. The attacker modifies the records in a DNS server so that it resolves a hostname into an incorrect IP address. The victim’s system sends a request to a poisoned DNS server, which points the victim to a different website. This different website looks and feels just like the requested website, so the user enters his username and password and may even be presented with web pages that look legitimate.
D is incorrect because both attacks are technical ways of carrying out social engineering. Phishing is a type of social engineering with the goal of obtaining personal information, credentials, credit card numbers, or financial data. The attackers lure, or fish, for sensitive data through various different methods, such as e-mail and pop-up forms. Pharming involves DNS poisoning. The attacker modifies the records in a DNS server so that it resolves a hostname into an incorrect IP address. The victim’s system sends a request to a poisoned DNS server, which points the victim to a different website. This different website looks and feels just like the requested website, so the user enters his username and password and may even be presented with web pages that look legitimate.
26. There are several types of intrusion detection systems (IDSs). What type of IDS builds a profile of an environment’s normal activities and assigns an anomaly score to packets based on the profile?
A. State-based
B. Statistical anomaly–based
C. Misuse-detection system
D. Protocol signature–based
![]() B. A statistical anomaly–based IDS is a behavioral-based system. Behavioral-based IDS products do not use predefined signatures, but rather are put in a learning mode to build a profile of an environment’s “normal” activities. This profile is built by continually sampling the environment’s activities. The longer the IDS is put in a learning mode, in most instances, the more accurate a profile it will build and the better protection it will provide. After this profile is built, all future traffic and activities are compared to it. With the use of complex statistical algorithms, the IDS looks for anomalies in the network traffic or user activity. Each packet is given an anomaly score, which indicates its degree of irregularity. If the score is higher than the established threshold of “normal” behavior, then the preconfigured action will take place.
B. A statistical anomaly–based IDS is a behavioral-based system. Behavioral-based IDS products do not use predefined signatures, but rather are put in a learning mode to build a profile of an environment’s “normal” activities. This profile is built by continually sampling the environment’s activities. The longer the IDS is put in a learning mode, in most instances, the more accurate a profile it will build and the better protection it will provide. After this profile is built, all future traffic and activities are compared to it. With the use of complex statistical algorithms, the IDS looks for anomalies in the network traffic or user activity. Each packet is given an anomaly score, which indicates its degree of irregularity. If the score is higher than the established threshold of “normal” behavior, then the preconfigured action will take place.
![]() A is incorrect because a state-based IDS has rules that outline which state transition sequences should sound an alarm. The initial state is the state prior to the execution of an attack, and the compromised state is the state after successful penetration. The activity that takes place between the initial and compromised state is what the state-based IDS looks for, and it sends an alert if any of the state-transition sequences match its preconfigured rules.
A is incorrect because a state-based IDS has rules that outline which state transition sequences should sound an alarm. The initial state is the state prior to the execution of an attack, and the compromised state is the state after successful penetration. The activity that takes place between the initial and compromised state is what the state-based IDS looks for, and it sends an alert if any of the state-transition sequences match its preconfigured rules.
![]() C is incorrect because a misuse-detection system is simply another name for a signature-based IDS, which compares network or system activity to signatures or models of how attacks are carried out. Any action that is not recognized as an attack is considered acceptable. Signature-based IDSs are the most popular IDS products today, and their effectiveness depends upon regularly updating the software with new signatures, as with antivirus software. This type of IDS is weak against new types of attacks because it can only recognize those that have been previously identified and have had signatures written for them.
C is incorrect because a misuse-detection system is simply another name for a signature-based IDS, which compares network or system activity to signatures or models of how attacks are carried out. Any action that is not recognized as an attack is considered acceptable. Signature-based IDSs are the most popular IDS products today, and their effectiveness depends upon regularly updating the software with new signatures, as with antivirus software. This type of IDS is weak against new types of attacks because it can only recognize those that have been previously identified and have had signatures written for them.
![]() D is incorrect because a protocol signature–based IDS is not a formal IDS. This is a distracter answer.
D is incorrect because a protocol signature–based IDS is not a formal IDS. This is a distracter answer.
27. A rule-based IDS takes a different approach than a signature-based or anomaly-based system. Which of the following is characteristic of a rule-based IDS?
A. Uses IF/THEN programming within expert systems
B. Identifies protocols used outside of their common bounds
C. Compares patterns to several activities at once
D. Can detect new attacks
![]() A. Rule-based intrusion detection is commonly associated with the use of an expert system. An expert system is made up of a knowledge base, an inference engine, and rule-based programming. Knowledge is represented as rules, and the data to be analyzed is referred to as facts. The knowledge of the system is written in rule-based programming (IF situation THEN action). These rules are applied to the facts, the data that comes in from a sensor, or a system that is being monitored. For example, an IDS pulls data from a system’s audit log and stores it temporarily in its fact database. Then, the preconfigured rules are applied to this data to indicate whether anything suspicious is taking place. In our scenario, the rule states “IF a root user creates File1 AND creates File2 SUCH THAT they are in the same directory THEN there is a call to Administrative Tool TRIGGER send alert.” This rule has been defined such that if a root user creates two files in the same directory and then makes a call to a specific administrative tool, an alert should be sent.
A. Rule-based intrusion detection is commonly associated with the use of an expert system. An expert system is made up of a knowledge base, an inference engine, and rule-based programming. Knowledge is represented as rules, and the data to be analyzed is referred to as facts. The knowledge of the system is written in rule-based programming (IF situation THEN action). These rules are applied to the facts, the data that comes in from a sensor, or a system that is being monitored. For example, an IDS pulls data from a system’s audit log and stores it temporarily in its fact database. Then, the preconfigured rules are applied to this data to indicate whether anything suspicious is taking place. In our scenario, the rule states “IF a root user creates File1 AND creates File2 SUCH THAT they are in the same directory THEN there is a call to Administrative Tool TRIGGER send alert.” This rule has been defined such that if a root user creates two files in the same directory and then makes a call to a specific administrative tool, an alert should be sent.
![]() B is incorrect because a protocol anomaly–based IDS identifies protocols used outside of their common bounds. The IDS has specific knowledge of each protocol that it will monitor. A protocol anomaly pertains to the format and behavior of a protocol. If a protocol is formatted differently or is demonstrating abnormal behavior, then the IDS triggers an alarm.
B is incorrect because a protocol anomaly–based IDS identifies protocols used outside of their common bounds. The IDS has specific knowledge of each protocol that it will monitor. A protocol anomaly pertains to the format and behavior of a protocol. If a protocol is formatted differently or is demonstrating abnormal behavior, then the IDS triggers an alarm.
![]() C is incorrect because a stateful matching IDS compares patterns to several activities at once. It is a type of signature-based IDS, meaning that it does pattern matching, similar to antivirus software. State is a snapshot of an operating system’s values in volatile, semipermanent, and permanent memory locations. In a state-based IDS, the initial state is the state prior to the execution of an attack, and the compromised state is the state after successful penetration. The IDS has rules that outline which state transition sequences should sound an alarm.
C is incorrect because a stateful matching IDS compares patterns to several activities at once. It is a type of signature-based IDS, meaning that it does pattern matching, similar to antivirus software. State is a snapshot of an operating system’s values in volatile, semipermanent, and permanent memory locations. In a state-based IDS, the initial state is the state prior to the execution of an attack, and the compromised state is the state after successful penetration. The IDS has rules that outline which state transition sequences should sound an alarm.
![]() D is incorrect because a rule-based IDS cannot detect new attacks. An anomaly-based IDS can detect new attacks because it doesn’t rely on predetermined rules or signatures, which are only available after security researchers have had time to study an attack. Instead, an anomaly-based IDS learns the “normal” activities of an environment and triggers an alarm when it detects activity that differs from the norm. The three types of anomaly-based IDS are statistical, protocol, and traffic. They are also called behavior or heuristic based.
D is incorrect because a rule-based IDS cannot detect new attacks. An anomaly-based IDS can detect new attacks because it doesn’t rely on predetermined rules or signatures, which are only available after security researchers have had time to study an attack. Instead, an anomaly-based IDS learns the “normal” activities of an environment and triggers an alarm when it detects activity that differs from the norm. The three types of anomaly-based IDS are statistical, protocol, and traffic. They are also called behavior or heuristic based.
28. Tom works at a large retail company that recently deployed radio-frequency identification (RFID) to better manage its inventory processes. Employees use scanners to gather product-related information instead of manually looking up product data. Tom has found out that malicious customers have carried out attacks on the RFID technology to reduce the amount they pay on store items. Which of the following is the most likely reason for the existence of this type of vulnerability?
A. The company’s security team does not understand how to secure this type of technology.
B. The cost of integrating security within RFID is cost prohibitive.
C. The technology has low processing capabilities and encryption is very processor intensive.
D. RFID is a new and emerging technology, and the industry does not currently have ways to secure it.
![]() C. A common security issue with RFID is that the data can be captured as it moves from the tag to the reader and modified. While encryption can be integrated as a countermeasure, it is not common because RFID is a technology that has low processing capabilities and encryption is very processor intensive.
C. A common security issue with RFID is that the data can be captured as it moves from the tag to the reader and modified. While encryption can be integrated as a countermeasure, it is not common because RFID is a technology that has low processing capabilities and encryption is very processor intensive.
![]() A is incorrect because it is not necessarily the best answer here. The company in the question may understand RFID and its common security issues, but security usually has to be integrated within the RFID technology. This means the vendor of the RFID product would have to integrate security into the product, and the available security solutions are commonly limited because RFID tags and readers do not usually have the necessary processing power to carry out the necessary cryptographic functions.
A is incorrect because it is not necessarily the best answer here. The company in the question may understand RFID and its common security issues, but security usually has to be integrated within the RFID technology. This means the vendor of the RFID product would have to integrate security into the product, and the available security solutions are commonly limited because RFID tags and readers do not usually have the necessary processing power to carry out the necessary cryptographic functions.
![]() B is incorrect because the cost of integrating security into RFID products may or may not be a factor. It usually comes down to the limitation of the technology itself, not necessarily the costs involved.
B is incorrect because the cost of integrating security into RFID products may or may not be a factor. It usually comes down to the limitation of the technology itself, not necessarily the costs involved.
![]() D is incorrect because it is not the best answer here. RFID has been around for many years, and many in the industry understand how it works and its security issues. Integrating security into a technology with so many limitations demands real needs and motivation. In most situations the data that is being transferred through RFID is not overly sensitive, so there has not been a true perceived need to integrate security into it. As RFID evolves it will most likely be better equipped to handle security countermeasures, but the industry has not fully gotten to this place yet.
D is incorrect because it is not the best answer here. RFID has been around for many years, and many in the industry understand how it works and its security issues. Integrating security into a technology with so many limitations demands real needs and motivation. In most situations the data that is being transferred through RFID is not overly sensitive, so there has not been a true perceived need to integrate security into it. As RFID evolves it will most likely be better equipped to handle security countermeasures, but the industry has not fully gotten to this place yet.
29. Tanya is the security administrator for a large distributed retail company. The company’s network has many different network devices and software appliances that generate logs and audit data. Tanya and her staff have become overwhelmed with trying to review all of the log files when attempting to identify if anything suspicious is taking place within the network. Which of the following is the best solution for this company to implement?
A. Security information and event management
B. Event correlation tools
C. Intrusion detection systems
D. Security event correlation management tools
![]() A. Today, many organizations are implementing security event management (SEM) systems, also called security information and event management (SIEM) systems. These products gather logs from various devices (servers, firewalls, routers, etc.) and attempt to correlate the log data and provide analysis capabilities. Companies also have different types of solutions on a network (IDS, IPS, antimalware, proxies, etc.) collecting logs in various proprietary formats, which require centralization, standardization, and normalization. Log formats are different per product type and vendor; thus, SIEM puts them into a standardized format for useful reporting.
A. Today, many organizations are implementing security event management (SEM) systems, also called security information and event management (SIEM) systems. These products gather logs from various devices (servers, firewalls, routers, etc.) and attempt to correlate the log data and provide analysis capabilities. Companies also have different types of solutions on a network (IDS, IPS, antimalware, proxies, etc.) collecting logs in various proprietary formats, which require centralization, standardization, and normalization. Log formats are different per product type and vendor; thus, SIEM puts them into a standardized format for useful reporting.
![]() B is incorrect because answer A provides a more accurate portrayal of the needed solution. SEM and SIEM tools zero in on malicious events and provide a centralized management capability. The logs are commonly aggregated onto one system, and the SIEM software “translates” the logs into a standardized format. The standardization allows for the log data to be analyzed and reports generated.
B is incorrect because answer A provides a more accurate portrayal of the needed solution. SEM and SIEM tools zero in on malicious events and provide a centralized management capability. The logs are commonly aggregated onto one system, and the SIEM software “translates” the logs into a standardized format. The standardization allows for the log data to be analyzed and reports generated.
![]() C is incorrect because an intrusion detection system is a product that identifies malicious activities and carries out notification activities. While these types of products may aggregate logs for analysis, they do not have the capability of standardizing log formats from different product types.
C is incorrect because an intrusion detection system is a product that identifies malicious activities and carries out notification activities. While these types of products may aggregate logs for analysis, they do not have the capability of standardizing log formats from different product types.
![]() D is incorrect because it is not the best answer here. An argument can be made that security event correlation management tools is what the correct answer “Security information and event management” is carrying out, but on the exam you will be required to pick the best answer. Security information and event management (SIEM) is the actual term the industry uses for products that provide this type of functionality.
D is incorrect because it is not the best answer here. An argument can be made that security event correlation management tools is what the correct answer “Security information and event management” is carrying out, but on the exam you will be required to pick the best answer. Security information and event management (SIEM) is the actual term the industry uses for products that provide this type of functionality.
30. The Logistics Agency of a country’s department of defense is responsible for ensuring that all necessary materials get to the proper locations to support the department’s day-to-day activities. The data that this agency maintains must be protected according to the three main security principles of security controls. For this agency’s responsibilities, which security principle has the highest priority?
A. Confidentiality
B. Integrity
C. Availability
D. Privacy
![]() A. The three main security principles for any and all security controls are availability, integrity, and confidentiality (AIC). Clearly each of these is a concern for this organization’s mission. However, the confidentiality as to the disposition and location of these materials is of the highest priority. If an adversary were to gain access to knowledge of something as mundane as where large volumes of toilet paper were being shipped, they could infer troop movements in advance of a military offensive action.
A. The three main security principles for any and all security controls are availability, integrity, and confidentiality (AIC). Clearly each of these is a concern for this organization’s mission. However, the confidentiality as to the disposition and location of these materials is of the highest priority. If an adversary were to gain access to knowledge of something as mundane as where large volumes of toilet paper were being shipped, they could infer troop movements in advance of a military offensive action.
![]() B is incorrect because, although an operation could be severely impacted if an adversary were able to compromise the logistical deployment of materials for a military unit by violating the integrity of the data about it, this presupposes a violation of its confidentiality first.
B is incorrect because, although an operation could be severely impacted if an adversary were able to compromise the logistical deployment of materials for a military unit by violating the integrity of the data about it, this presupposes a violation of its confidentiality first.
![]() C is incorrect because, although the availability of military logistics systems is clearly an extremely high priority for a fully functional deployment, in this context the confidentiality of which systems and data are key for any given operation is of even higher priority.
C is incorrect because, although the availability of military logistics systems is clearly an extremely high priority for a fully functional deployment, in this context the confidentiality of which systems and data are key for any given operation is of even higher priority.
![]() D is incorrect because, although privacy is an increasingly important consideration, it is not considered one of the three main security principles, as it is really a specific aspect of confidentiality.
D is incorrect because, although privacy is an increasingly important consideration, it is not considered one of the three main security principles, as it is really a specific aspect of confidentiality.
31. Claudia is the CISO for a global financial institution, overseeing the security of hundreds of millions of bank accounts. Which of the three main security principles should she consider most important when prioritizing the controls her enterprise should deploy?
A. Confidentiality
B. Integrity
C. Availability
D. Authenticity
![]() B. The three main security principles for any and all security controls are availability, integrity, and confidentiality (AIC). Clearly each of these is a concern for Claudia’s organization’s security. However, among these, the integrity of the account data is foremost. Integrity is the assurance that the bank account data has not been altered in an unauthorized way. A compromise of this principle could essentially mean that the account holders’ money has been stolen—that the bank has been robbed.
B. The three main security principles for any and all security controls are availability, integrity, and confidentiality (AIC). Clearly each of these is a concern for Claudia’s organization’s security. However, among these, the integrity of the account data is foremost. Integrity is the assurance that the bank account data has not been altered in an unauthorized way. A compromise of this principle could essentially mean that the account holders’ money has been stolen—that the bank has been robbed.
![]() A is incorrect because, although Claudia must be concerned with the confidentiality of her account holders’ data, most likely to comply with banking and privacy regulations in multiple countries, the threat of an account being modified by an attacker is far greater.
A is incorrect because, although Claudia must be concerned with the confidentiality of her account holders’ data, most likely to comply with banking and privacy regulations in multiple countries, the threat of an account being modified by an attacker is far greater.
![]() C is incorrect because, although certainly Claudia’s bank must be concerned with the availability of both data and systems to support 24/7 transactions, the threat of the unauthorized modification of the 1’s and 0’s the accounts contain (money!) is of greatest concern to a bank.
C is incorrect because, although certainly Claudia’s bank must be concerned with the availability of both data and systems to support 24/7 transactions, the threat of the unauthorized modification of the 1’s and 0’s the accounts contain (money!) is of greatest concern to a bank.
![]() D is incorrect because the authenticity of entities attempting to perform transactions is also a concern, but only in so much as the transactions never result in unauthorized modifications to the account details. This is an integrity issue first and foremost.
D is incorrect because the authenticity of entities attempting to perform transactions is also a concern, but only in so much as the transactions never result in unauthorized modifications to the account details. This is an integrity issue first and foremost.
32. Which of the following is an example of a credential management system, also known as an identity management (IdM) system?
A. A historic log of the activities performed by users once they have presented their credentials to a central authorizing system
B. A database of the credentials that have been registered to each individual in an enterprise, in order to correlate users with usernames and locales
C. A security information and event management (SIEM) system that contains the logs for various credentialing systems in the enterprise, for correlation of activities by ID
D. A Kerberos Key Distribution Center (KDC) that contains the symmetric keys of all the entities and systems in a Kerberos realm, which can be centrally administered to ensure that it is up-to-date with respect to additions and deletions of keys
![]() D. Kerberos is a common solution to credential and identity management, facilitating all the needs of such a system, including the creation of accounts across systems, the assignment of account details and privileges, and the decommissioning of accounts when they are no longer required. It is the core technology behind Microsoft’s Active Directory, which is the most common IdM solution in an enterprise environment.
D. Kerberos is a common solution to credential and identity management, facilitating all the needs of such a system, including the creation of accounts across systems, the assignment of account details and privileges, and the decommissioning of accounts when they are no longer required. It is the core technology behind Microsoft’s Active Directory, which is the most common IdM solution in an enterprise environment.
![]() A is incorrect because, although it is important to be able to review the historical activities of individual users whose credentials have been provisioned by a central authorizing system, this is just one feature of a robust IdM system.
A is incorrect because, although it is important to be able to review the historical activities of individual users whose credentials have been provisioned by a central authorizing system, this is just one feature of a robust IdM system.
![]() B is incorrect because, although the data store of account information is a central feature of a credential management system, the ability to manage this data on a day-to-day basis is the salient feature.
B is incorrect because, although the data store of account information is a central feature of a credential management system, the ability to manage this data on a day-to-day basis is the salient feature.
![]() C is incorrect because, although a SIEM can be useful in tracking the activities of credentialed users across multiple systems in a large environment, its use is dependent upon a centralized credential management system such as Kerberos or Active Directory.
C is incorrect because, although a SIEM can be useful in tracking the activities of credentialed users across multiple systems in a large environment, its use is dependent upon a centralized credential management system such as Kerberos or Active Directory.
33. Which of the following attributes is used to biometrically authenticate a user’s identity?
A. Something you know
B. Something you have
C. Something you are
D. Someplace you are
![]() C. Each of “something you know,” “something you have,” and “something you are” are classic factors of authentication used to validate a user’s claim of identity. Biometric authentication seeks to authenticate a user based on some unique physical attribute of the user, such as a fingerprint, the granularly pixilated color pattern of the iris of the eye, or the digitized pattern of a voice. This is innate to the user, and so comprises “something you are.”
C. Each of “something you know,” “something you have,” and “something you are” are classic factors of authentication used to validate a user’s claim of identity. Biometric authentication seeks to authenticate a user based on some unique physical attribute of the user, such as a fingerprint, the granularly pixilated color pattern of the iris of the eye, or the digitized pattern of a voice. This is innate to the user, and so comprises “something you are.”
![]() A is incorrect because something a user knows, such as a password, passphrase, or PIN number, is something that can easily be shared among users, and so is not an innate attribute to one user only.
A is incorrect because something a user knows, such as a password, passphrase, or PIN number, is something that can easily be shared among users, and so is not an innate attribute to one user only.
![]() B is incorrect because, likewise, something a user physically possesses, such as a token, card, or physical key, can be easily transferred or stolen. As such it is not necessarily unique to a user.
B is incorrect because, likewise, something a user physically possesses, such as a token, card, or physical key, can be easily transferred or stolen. As such it is not necessarily unique to a user.
![]() D is incorrect because “someplace you are” certainly isn’t innate to the user. It is a newer authentication factor that could be, for example, a geolocation provided by a GPS system or the physicality of a login on console (which places the user in a data center, perhaps). It can be used in multifactor authentication but isn’t particularly useful on its own.
D is incorrect because “someplace you are” certainly isn’t innate to the user. It is a newer authentication factor that could be, for example, a geolocation provided by a GPS system or the physicality of a login on console (which places the user in a data center, perhaps). It can be used in multifactor authentication but isn’t particularly useful on its own.
34. Within biometric authentication, what is a Type II error rate?
A. The rate of errors where the system falsely accepts the authentication of an individual who is not who they purport to be
B. The rate of errors where the system falsely rejects the authentication of an individual who is who they purport to be
C. The rate of errors that the system produces where false rejections and false acceptances are equal
D. The rate of errors where the system fails to either accept or reject the authentication of an individual regardless of their validity
![]() A. The false acceptance rate (FAR) is the rate of Type II errors within a biometric system and represents the rate at which a system accepts impostors who should have been declined access. These are the most critical errors a biometric system should be tuned to minimize.
A. The false acceptance rate (FAR) is the rate of Type II errors within a biometric system and represents the rate at which a system accepts impostors who should have been declined access. These are the most critical errors a biometric system should be tuned to minimize.
![]() B is incorrect because it describes the false rejection rate (FRR), which is the rate of Type I errors within a biometric system and represents the rate at which a system rejects authentic users who should have been granted access. Type I errors are the less critical errors, as they don’t result in an authentication bypass, but they are an annoyance to the user, who must try again to authenticate successfully.
B is incorrect because it describes the false rejection rate (FRR), which is the rate of Type I errors within a biometric system and represents the rate at which a system rejects authentic users who should have been granted access. Type I errors are the less critical errors, as they don’t result in an authentication bypass, but they are an annoyance to the user, who must try again to authenticate successfully.
![]() C is incorrect because it describes the crossover error rate (CER), which is the point in the sensitivity tuning of a biometric system in which the FAR and FRR are equal. The CER is used as a metric of performance for any given biometric system, such that the lower the CER, the more accurate the system can be configured to be.
C is incorrect because it describes the crossover error rate (CER), which is the point in the sensitivity tuning of a biometric system in which the FAR and FRR are equal. The CER is used as a metric of performance for any given biometric system, such that the lower the CER, the more accurate the system can be configured to be.
![]() D is incorrect because the rate at which a system fails to perform altogether, either via FAR or FRR, is not a metric used for performance evaluation of a biometric system, but likely represents a systemic failure.
D is incorrect because the rate at which a system fails to perform altogether, either via FAR or FRR, is not a metric used for performance evaluation of a biometric system, but likely represents a systemic failure.
35. Which of the following criteria is the most important consideration for the selection and deployment of a biometric authentication system?
A. False acceptance rate (FAR) or Type II error rate
B. False rejection rate (FRR) or Type I error rate
C. Crossover error rate (CER) or equal error rate (EER)
D. Processing speed
![]() D. Processing speed is the length of time it takes a biometric system to actually authenticate a user upon the presentation of the body part. Regardless of how well a system can be tuned with respect to FAR, FRR, or CER, unless the system can process a sufficient throughput of individuals in actual deployment, it will become a costly bottleneck. Much as different systems have different thresholds for accuracy, they have differing thresholds for throughput, based on the body part being used for authentication.
D. Processing speed is the length of time it takes a biometric system to actually authenticate a user upon the presentation of the body part. Regardless of how well a system can be tuned with respect to FAR, FRR, or CER, unless the system can process a sufficient throughput of individuals in actual deployment, it will become a costly bottleneck. Much as different systems have different thresholds for accuracy, they have differing thresholds for throughput, based on the body part being used for authentication.
![]() A, B, and C are incorrect because, although all of these measures are critical in consideration of which type of system to deploy, the most critical consideration in the real world is whether or not the system can meet the needs of the users being authenticated and the business mission the system has been deployed to support.
A, B, and C are incorrect because, although all of these measures are critical in consideration of which type of system to deploy, the most critical consideration in the real world is whether or not the system can meet the needs of the users being authenticated and the business mission the system has been deployed to support.
36. Though “something you know,” in the form of passwords, is the most common authentication factor still used today, it is considered one of the weakest. This is because passwords are easy for users to share, and relatively easy for adversaries to steal or guess. Which of the following measures is the best way to counter attacks on this form of authentication?
A. Store all passwords in encrypted form only, so that recovering them requires a special key to decrypt them for authentication.
B. Employ a password policy to ensure that passwords are chosen in such a way that they are neither easy for an attacker to guess nor easy for an attacker to brute force.
C. Require that all passwords be composed of a combination of unique characters, regardless of length.
D. Ensure that accounts are locked out after a minimum number of incorrect guesses within a short amount of time.
![]() B. Employing a comprehensive password policy is the best method for ensuring that the passwords selected by users are as strong as possible against all forms of attack. This includes making them less easy to guess, by prohibiting the use of strings that are associated with knowable attributes of the user, such as names, birth dates, etc. Passwords should include some amount of complexity beyond simple dictionary words as well, which typically requires the use of some special characters to make them less likely to be brute forcible. Most importantly, they should be required to be as long as is practical given the system implementing them. Password aging and periodic strength audits are also best practices.
B. Employing a comprehensive password policy is the best method for ensuring that the passwords selected by users are as strong as possible against all forms of attack. This includes making them less easy to guess, by prohibiting the use of strings that are associated with knowable attributes of the user, such as names, birth dates, etc. Passwords should include some amount of complexity beyond simple dictionary words as well, which typically requires the use of some special characters to make them less likely to be brute forcible. Most importantly, they should be required to be as long as is practical given the system implementing them. Password aging and periodic strength audits are also best practices.
![]() A is incorrect because, although storing passwords in encrypted form only is absolutely required, the encryption used should not be reversible with any key. One-way hashing of passwords satisfies this requirement. Even so, encryption is but one aspect of a salient password policy.
A is incorrect because, although storing passwords in encrypted form only is absolutely required, the encryption used should not be reversible with any key. One-way hashing of passwords satisfies this requirement. Even so, encryption is but one aspect of a salient password policy.
![]() C is incorrect because, as provided in the correct answer explanation, password complexity is a necessary but not sufficient requirement. Enforcing a password length requirement beyond 15 characters at a bare minimum is part of an effective password policy.
C is incorrect because, as provided in the correct answer explanation, password complexity is a necessary but not sufficient requirement. Enforcing a password length requirement beyond 15 characters at a bare minimum is part of an effective password policy.
![]() D is incorrect because account lockout after a small threshold of password guessing activity is also a necessary but insufficient aspect of an effective password policy.
D is incorrect because account lockout after a small threshold of password guessing activity is also a necessary but insufficient aspect of an effective password policy.
37. Which of the following is the correct sequence in the Kerberos authentication process with respect to passwords, Key Distribution Centers (KDCs), ticket granting servers (TGSs), ticket granting tickets (TGTs), services, and service tickets?
A. The user provides a username/password to the workstation, the workstation obtains a TGT from the TGS, then subsequently obtains a service ticket from the KDC, which it presents to the service.
B. The workstation obtains a TGT from the KDC, which the user then validates with a password. The TGT is then exchanged for a service ticket from the TGS, which is presented to the service.
C. The user provides a username/password to the workstation, the workstation obtains a TGT from the KDC, then subsequently obtains a service ticket from the TGS, which it presents to the service.
D. The user obtains a service ticket from the service. The user then validates this ticket with a username/password provided to the TGS, which results in a TGT that is further validated by the KDC in a final step.
![]() C. The user must first authenticate to the workstation with a username and password. These credentials are then forwarded by the workstation to the authentication service (AS) on the KDC, which then returns a TGT encrypted with the TGS’s secret key. Later, when a service is required, the TGT is presented back to the TGS that can authenticate it, and which then returns a service ticket encrypted with the service’s secret key. When the service ticket is presented to the service, mutual authentication can occur: the service knows the user must be authentic, because the user couldn’t have a valid service ticket without having authenticated to the KDC and TGS, and the user knows the service is authentic, because it can decrypt the service ticket.
C. The user must first authenticate to the workstation with a username and password. These credentials are then forwarded by the workstation to the authentication service (AS) on the KDC, which then returns a TGT encrypted with the TGS’s secret key. Later, when a service is required, the TGT is presented back to the TGS that can authenticate it, and which then returns a service ticket encrypted with the service’s secret key. When the service ticket is presented to the service, mutual authentication can occur: the service knows the user must be authentic, because the user couldn’t have a valid service ticket without having authenticated to the KDC and TGS, and the user knows the service is authentic, because it can decrypt the service ticket.
![]() A is incorrect because authentication with the KDC precedes interaction with the TGS.
A is incorrect because authentication with the KDC precedes interaction with the TGS.
![]() B is incorrect because the user must first authenticate with the workstation, so that it has the credentials to authenticate with the KDC.
B is incorrect because the user must first authenticate with the workstation, so that it has the credentials to authenticate with the KDC.
![]() D is incorrect because this sequence is nonsensical and completely out of order.
D is incorrect because this sequence is nonsensical and completely out of order.
38. In practical use, which of the following best describes a “session”?
A. Any data exchange between two discrete endpoints, over any arbitrary duration
B. Any authenticated exchange between two parties that is used to carry on a conversation, with a discrete beginning, period of activity, and termination
C. Any discrete period of time that a user is logged into a workstation
D. The volume of data exchanged between two systems during a discrete period of time
![]() B. In most practical uses of the word, a “session” implies some initial form of authentication between two parties, be it between a user and a workstation or between two systems on a network. Subsequent to the authentication phase at the session’s initiation, the two parties carry on an exchange of data interactively, and then terminate the exchange when the session is no longer required, most commonly through mutual agreement. A session therefore has a discrete beginning, period of interactive activity, and a discrete termination.
B. In most practical uses of the word, a “session” implies some initial form of authentication between two parties, be it between a user and a workstation or between two systems on a network. Subsequent to the authentication phase at the session’s initiation, the two parties carry on an exchange of data interactively, and then terminate the exchange when the session is no longer required, most commonly through mutual agreement. A session therefore has a discrete beginning, period of interactive activity, and a discrete termination.
![]() A is incorrect because this definition, although loosely accurate, misses the most common components of mutual initiation/authentication and termination. Though the duration may be arbitrary in length, it is commonly discretely limited.
A is incorrect because this definition, although loosely accurate, misses the most common components of mutual initiation/authentication and termination. Though the duration may be arbitrary in length, it is commonly discretely limited.
![]() C is incorrect because a user logging into a workstation can certainly be considered a session by this definition, but it is a special case. Sessions can transpire between systems and services equally.
C is incorrect because a user logging into a workstation can certainly be considered a session by this definition, but it is a special case. Sessions can transpire between systems and services equally.
![]() D is incorrect because, although data will be exchanged during any session, the volume of it is not what defines a session, but rather the conversational nature of the exchange.
D is incorrect because, although data will be exchanged during any session, the volume of it is not what defines a session, but rather the conversational nature of the exchange.
39. The use of “resource servers” and “authorization servers” to enable a “client” web service (such as LinkedIn) to access a “resource owner” (such as Google) for federated authorization is a hallmark of what open standard?
A. OpenID
B. SAML
C. SSO
D. OAuth
![]() D. OAuth is an open standard for website-to-website authorization (not authentication). It is used to allow an account that a user is authenticated to on one site to access resources on another third-party site.
D. OAuth is an open standard for website-to-website authorization (not authentication). It is used to allow an account that a user is authenticated to on one site to access resources on another third-party site.
![]() A is incorrect because OpenID is an open standard not for authorization but for authentication by a third-party site that maintains the actual credentials for that user. It involves a “relying party” and an OpenID “provider.”
A is incorrect because OpenID is an open standard not for authorization but for authentication by a third-party site that maintains the actual credentials for that user. It involves a “relying party” and an OpenID “provider.”
![]() B is incorrect because the Security Assertion Markup Language (SAML) is an XML-based standard for conveying authentication in a federated identity management system, commonly from business to business.
B is incorrect because the Security Assertion Markup Language (SAML) is an XML-based standard for conveying authentication in a federated identity management system, commonly from business to business.
![]() C is incorrect because single sign-on (SSO), although also an authentication mechanism, is not an open standard and is typically managed and used within a single enterprise for heterogeneous system access.
C is incorrect because single sign-on (SSO), although also an authentication mechanism, is not an open standard and is typically managed and used within a single enterprise for heterogeneous system access.
40. Which of the following is NOT true of OpenID Connect (OIDC)?
A. It is mainly used as an open standards–based single sign-on (SSO) mechanism between disparate platforms within an enterprise environment.
B. It is layered on the OAuth protocol to allow both authentication and authorization in a transparent way for client resource requests.
C. It supports three flows: authorization code flow, implicit flow, and hybrid flow.
D. It involves browser redirections from the OpenID provider back to the relying party using authorization codes.
![]() A. OAuth, OpenID, and OIDC are all open protocols and standards for use in authentication and authorization across, rather than within, enterprises to facilitate federated identity management (IdM).
A. OAuth, OpenID, and OIDC are all open protocols and standards for use in authentication and authorization across, rather than within, enterprises to facilitate federated identity management (IdM).
![]() B is incorrect because it is a true statement that OIDC is layered on OAuth 2.0, extending it to be able to provide authorization for third-party services, transparently to the user, in addition to authentication.
B is incorrect because it is a true statement that OIDC is layered on OAuth 2.0, extending it to be able to provide authorization for third-party services, transparently to the user, in addition to authentication.
![]() C is incorrect because it is a true statement that OIDC supports the three flows. Authorization code flow provides an authorization code to the relying party, which is then used to directly request an ID token from the identity provider (IdP). Implicit flow provides the relying party with the ID token directly, which is passed through the user’s browser. Hybrid flow uses a combination of the two.
C is incorrect because it is a true statement that OIDC supports the three flows. Authorization code flow provides an authorization code to the relying party, which is then used to directly request an ID token from the identity provider (IdP). Implicit flow provides the relying party with the ID token directly, which is passed through the user’s browser. Hybrid flow uses a combination of the two.
![]() D is incorrect because it is a true statement that OIDC involves browser redirections from the OpenID provider back to the relying party using authorization codes (in hybrid flows, as described in option C, previously).
D is incorrect because it is a true statement that OIDC involves browser redirections from the OpenID provider back to the relying party using authorization codes (in hybrid flows, as described in option C, previously).
41. Which of the following attributes are added beyond traditional access control mechanisms (RBAC, MAC, and DAC) in order to implement ABAC?
A. Subjects
B. Objects
C. Actions
D. Context
![]() D. Traditional methods such as role-based access control (RBAC), mandatory access control (MAC), and discretionary access control (DAC) each rely on categories of subjects and objects, and assign actions that can be performed based on combinations of the two. Attribute-based access control (ABAC) includes contexts, such as the time of day, the state or phase of a project, and other contextual events, in order to provide further granularity to which objects can be accessed by which subjects, when, and how.
D. Traditional methods such as role-based access control (RBAC), mandatory access control (MAC), and discretionary access control (DAC) each rely on categories of subjects and objects, and assign actions that can be performed based on combinations of the two. Attribute-based access control (ABAC) includes contexts, such as the time of day, the state or phase of a project, and other contextual events, in order to provide further granularity to which objects can be accessed by which subjects, when, and how.
![]() A is incorrect because subjects (which users and systems) and their clearance levels are employed by all access control systems.
A is incorrect because subjects (which users and systems) and their clearance levels are employed by all access control systems.
![]() B is incorrect because objects (files, folders, processes, and other resources) and their classification or sensitivity labels are employed by all access control systems.
B is incorrect because objects (files, folders, processes, and other resources) and their classification or sensitivity labels are employed by all access control systems.
![]() C is incorrect because actions that can be performed (read, write, execute, etc.) are also employed by all access control systems.
C is incorrect because actions that can be performed (read, write, execute, etc.) are also employed by all access control systems.
