- CISSP in 21 Days Second Edition
- CISSP in 21 Days Second Edition
- Credits
- About the Author
- About the Reviewer
- www.PacktPub.com
- Preface
- 1. Day 1 – Security and Risk Management - Security, Compliance, and Policies
- 2. Day 2 – Security and Risk Management - Risk Management, Business Continuity, and Security Education
- 3. Day 3 – Asset Security - Information and Asset Classification
- 4. Day 4 – Asset Security - Data Security Controls and Handling
- 5. Day 5 – Exam Cram and Practice Questions
- 6. Day 6 – Security Engineering - Security Design, Practices, Models, and Vulnerability Mitigation
- 7. Day 7 – Security Engineering - Cryptography
- 8. Day 8 – Communication and Network Security - Network Security
- An overview of communication and network security
- Network architecture, protocols, and technologies
- Open System Interconnect (OSI) model
- OSI layers and security
- Application layer protocols and security
- Presentation layer protocols and security
- Summary
- Sample questions
- 9. Day 9 – Communication and Network Security - Communication Security
- An overview of communication security
- Security in communication channels
- Attacks on communication networks
- Preventing or mitigating communication network attacks
- Summary
- Sample questions
- 10. Day 10 – Exam Cram and Practice Questions
- 11. Day 11 – Identity and Access Management - Identity Management
- 12. Day 12 – Identity and Access Management - Access Management, Provisioning, and Attacks
- 13. Day 13 – Security Assessment and Testing - Designing, Performing Security Assessment, and Tests
- An overview of security assessment and testing
- Security assessment and test strategies
- Security controls
- Summary
- Sample questions
- 14. Day 14 – Security Assessment and Testing - Controlling, Analyzing, Auditing, and Reporting
- 15. Day 15 – Exam Cram and Practice Questions
- 16. Day 16 – Security Operations - Foundational Concepts
- An overview of operations security
- The physical security design
- Physical and operations security controls
- Operations/facility security
- Protecting and securing equipment
- Computer investigations
- Summary
- Sample questions
- 17. Day 17 – Security Operations - Incident Management and Disaster Recovery
- 18. Day 18 – Software Development Security - Security in Software Development Life Cycle
- 19. Day 19 – Software Development Security - Assessing effectiveness of Software Security
- 20. Day 20 – Exam Cram and Practice Questions
- 21. Day 21 – Exam Cram and Mock Test
Q1. An interface test is done to ascertain:
- Pressure, temperature, and environment conditions
- Metrics for code coverage
- The round-trip time of a request response
- Security during interactions between user to interfaces and interface to modules
Q2. Identity management includes:
- The enrollment of user identifiers
- The provisioning or deprovisioning of user identities to different systems
- Whenever there is a change in user information then updating all associated accounts
- All of the above
Q3. When an identified vulnerability is not published by the application vendor then it is called:
- Zero-day vulnerability
- Zero-day exploit
- Zero-day logic bomb
- Zero-day threat
Q4. Which one of the following is not a password attack?
- Dictionary attack
- Brute force attack
- Code attack
- Hybrid attack
Q5. The reverse of a use case test is a:
- Vulnerability case test
- Penetration case test
- Nonuse case test
- Misuse case test
Q6. A person, process, or technology component that either seeks access or controls the access is called:
- Subject
- Object
- Data
- Control
Q7. Synthetic transactions are generally used for:
- Performance monitoring and directly associated with the availability tenet
- Performance monitoring and directly associated with the confidentiality tenet
- Performance monitoring and directly associated with the integrity tenet
- Performance monitoring and directly associated with authentication
Q8. Imitating a trusted entity, thereby making the system trust this imitated entity, is known as:
- Scanning
- Sniffing
- Spoofing
- Monitoring
Q9. Identify the true statements pertaining to access control from the following (this is a drag-and-drop type of question. Here, and for similar drag-and-drop questions, you can draw a line from the list of answers from the left to the empty box on the right).
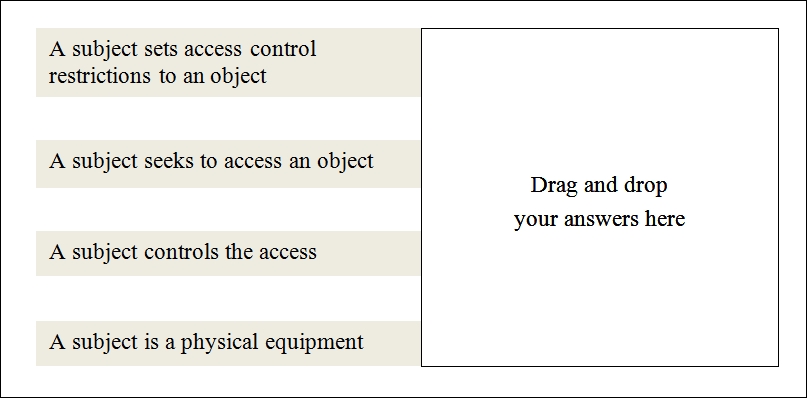
Q10. Which one of the following choices in an audit trail that is unlikely to be contained in the access log file pertaining to physical access?
- Access attempts
- Access results such as success or failure
- Locations accessed
- Access control list
-
No Comment
