Delivery of technology solutions is where the rubber meets the road. In industry and in government, technology solutions exist only to enhance organizational processes to better meet the acquirer’s strategies and objectives. This requires a persistent focus on measuring the critical dimensions of your work, the supplier’s delivery capability, and the deliverables. You manage the overall delivery by keeping a keen eye on handling business and technical risks throughout any project or program. You must coordinate all the stakeholders while addressing all the facets of your acquisition projects. Only a well-orchestrated team of acquirer and supplier personnel can deliver the desired value-added solution without disrupting the acquirer’s business or mission.
This chapter looks at the challenges of managing suppliers compared with performing the technical development yourself (recall hidden truth number 5, “Understand the difference between managing and performing,” as discussed in Chapter 1). To do that, we describe the struggles, ideas, and discoveries of Matt Vauban, a seasoned executive within an acquisition organization, along with Steve Reiter, who has managed acquisition projects for years, and Paula Ressel, the internal customer. The supplier’s perspectives are represented by Kristin Wells and George Taylor, who work for a key supplier. These fictitious characters are engaged in active outsourcing. The goal of the acquirer is to manage the supplier to achieve results while retaining accountability for the overall outcome of the acquisition projects.
This chapter focuses first on integrated project management. Our goal is to set the foundation for the things that acquirers, even when they are just starting out on the improvement journey toward excellence, should keep in mind when managing delivery of solutions. We highlight how to involve the relevant stakeholders according to an executable delivery process. Although integrated project management has its greatest impact when an acquirer has reached a certain level of process maturity, the practices and ideas help guide all acquirers.
We then turn our attention to the critical, but underappreciated, craft of configuration management. It takes numerous people to make outsourced projects successful, so it is critical to know where all the assets that make up a technology solution are stored. In addition, successful acquirers carefully monitor and control their projects by making targeted, concise, and actionable measurements. We cover such a set of measures and offer ideas about applying them. The chapter concludes with a discussion of going live with acquired products and services.
Successful projects are usually planned very carefully. Delayed or canceled projects, however, almost always exhibit planning failures. The most common planning failures include (1) not dealing effectively with changing requirements, (2) not anticipating staff hiring and turnover, (3) not allotting time for detailed requirements analysis, and (4) not allotting sufficient time for design and code inspections, testing, integration, and defect correction.
You need to involve all the relevant acquisition, technical, support, and operational stakeholders throughout the project. It’s your task to ensure that all the stakeholders coordinate and cooperate to the maximum extent possible. Depending on the scope and risk of the project, coordination efforts with the supplier organization can be significant.
When Matt briefed the hidden truths to the board of directors and other senior managers, he was surprised that it created such a stir. “They all want us to get moving fast, delivering solutions like clockwork,” he says to Paula. He pauses and then continues.
Matt: How can we get all our ducks in a row? We always agree to a plan with the stakeholders and suppliers, but then we seem to make a new plan every other week because “something happened.”
Paula: I think I know what you mean.
Matt: We forget about this, that, and the other—we don’t get the supplier agreement signed, or we forget about that cost or this task. So the replanning—or worse, rebaselining of the plan—continues on and on. I remember one project that we had to replan five times.
Paula: Five times? That’s a lot.
Matt: What happens is, we don’t recognize that a particular plan is in jeopardy. So then the suppliers just respond to that confusion and sometimes add to it. It throws us for a loop, and we end up in a vicious cycle of planning and replanning.
But I’ve seen planning work, too. It takes a lot of preparation. We have to hammer out clear business objectives and agree to them up front, so everyone knows how they will be measured. You have the business participation, buy-in, and agreement on the team, including our suppliers. As a team, we gather around and build an integrated plan and process and give it the chance to execute flawlessly.
Acquirers of technology solutions must keep in mind the overall picture and then continuously reinforce and improve the integration of acquirer, supplier, and stakeholder activities. Paula describes what it’s like when a team hasn’t achieved the desired level of integration.
Tip
Synchronize early, and adjust the technical constraints along with the capability of the supply base.
Paula: The problem seems to be that we adopt a throw-it-over-the-wall mentality. For instance, sometimes we have fairly detailed design constraints, and we lock them down before the suppliers are even on board. When the suppliers come along, they’re focused on design, development, or configuration. But this is after we’ve tried to freeze our requirements through ironclad supplier agreements.
Matt: I see what you mean. We establish the requirements and design constraints somewhat in isolation, so the supplier’s delivery processes are slow and require a lot of rework. And that eats up a significant amount of our resources.
Paula: I just attended a review of one of our key projects, where we didn’t even start looking for a supplier until many months into the project.
Another problem is that our technical experts make assumptions about COTS components and new technologies, and then it turns out they’re not available. So anything they’ve done based on those assumptions is now dead.
And of course, our suppliers are experiencing an upheaval in their business environment, so they’ve been consolidating like mad, which has eliminated some delivery centers and components from the supply base. And the design assumed a certain level of process capability that the suppliers didn’t possess. So we have a real mismatch between our requirements and what the suppliers can deliver.
Steve is also sitting in on the meeting.
Steve: Do you have any ideas for dealing with all this?
Paula: The only hope we have is truly integrated project management. Instead of executing all the work sequentially, we need to establish a set of standard processes that rely on early action by the suppliers. It will take precise and intense communication between our teams and the supplier teams. Plus, our relationship with suppliers must support and reinforce the early and frequent exchange of ideas, requirements, and constraints.
Achieving integrated project management requires an approach that is new to most organizations. You must make certain that your preferred technologies and your choices about your overall technology environment are aligned with the supplier’s system processes and delivery capabilities, and you must do this early enough in the overall process that the two parties can influence and shape one another in a timely and effective way. You can examine suppliers’ qualifications early in the process as requirements and technical constraints emerge. The suppliers can begin to participate in early discussions aimed at obtaining firsthand information about potential problems and opportunities inherent in the design trade-offs you present.
However, people who work on technology projects don’t have to reinvent the wheel. After you have documented some processes, procedures, templates, or guidelines, projects can leverage your organizational process and tailor it to their specific needs. A defined process not only covers the technical aspects of system delivery but also addresses organizational acquisition guidance, regulations, instructions, and practices that are established for use across projects. The project’s processes logically sequence acquirer activities and supplier deliverables (as identified in the supplier agreement) to deliver a product that meets the requirements. Examples of integrated project activities include proposal evaluation, supplier selection, development and management of supplier agreements, and acceptance of supplier deliverables.
Although all processes must be aligned with the acquisition strategy, this alignment is particularly important if you plan to make processes available for projects so that they can tailor them. Markets and technologies are dynamic, and time is a critical element of competition. Therefore, deeper, more intensive acquirer-supplier integration is crucial for effectively delivering solutions.
Steve picks up the dialog about integrated project management.
Steve: You’re right, Paula. It will require decisive actions to break up our functional silos and seamlessly integrate with our suppliers. Look at the systems engineering group, for example. Integrated project management would let us define design constraints that take the supplier’s capabilities into account, and at the same time work with our acquisition strategy. This also means that the supplier’s delivery processes must consistently live up to the capability and performance we need.
An integrated work environment fosters careful and practical planning.
Steve: We really need to think through how to put together an integrated plan. For instance, one problem I see is that we don’t put enough time and thought into how to deploy a technical solution. We put a lot of thought and design into the product, but not into the deployment. But when you think about it, what good is a so-called solution if it only sits on the shelf?
Paula: What we need is to not get distracted. It’s easy to fall into the trap of excessive multitasking and convince ourselves that working really hard on a bunch of things means it’s all good. We end up working on everything and not getting anything done.
Developing an integrated project plan requires an in-depth understanding of your and the supplier’s capabilities. For instance, projects are often asked to accelerate the delivery schedule. If you can’t accelerate work on your side, the relationship with the supplier comes into play. In a long-term acquirer-supplier relationship, the supplier might provide additional short-term capability without adding cost to help the acquirer out of a difficult situation.
Steve: A couple years back, we had many different suppliers who didn’t necessarily want to accommodate our schedule changes. Often the squeaky wheel gets the grease. If our suppliers had another customer with a bigger contract or a more prestigious project, they got the most high-powered resources. So our suppliers weren’t very flexible. They wouldn’t just say, “Oh, yeah, you can change this activity or deliverable by a week. No problem. We don’t care.” We corrected this situation by establishing more mutually beneficial, medium- to long-term relationships with our suppliers.
Tip
To achieve flexible, high-performance processes, maintain clearly defined, positive relationships with your suppliers.
Kristin confirms Steve’s observation.
Kristin: If you have a one-shot relationship, you go in with the attitude, “What’s the project? What’s the margin I have to hit to make the acquirer happy enough that we get the next project?” This results in a very short-term focus, with minimum synergy. But when you have a strategic relationship, things change drastically. The analogy I like to use is going out to dinner with a bunch of friends. Sometimes you buy at a fast food restaurant, and sometimes they buy at the high-end steak house, but sometimes it’s the opposite. It balances out. If there’s trust between you and everyone understands that it’s a strategic relationship, suppliers can put the date on the table without worrying that the acquirer’s purchasing group is going to say, “I can squeeze out another 1 percent.”
Steve: I’m not sure I follow you.
Kristin: For us, integrated planning is in the program domain, not the purchasing domain. We’d be happy to have your program or project managers discuss the size of the management reserve. Our concern is always that the purchasing person is going to say, “I’ve been advised to cut another 3 percent, and I’m going to do that no matter how if affects execution.” Then we get concerned about putting the date on the table.
Steve: Can you give me an example?
Kristin: Well, let’s look at a fixed-price contract. We’re basically exposing our programming buffer for things that can go wrong. If we have a program that costs $1 million, we put in a 15 percent margin, because we know we need that. That’s the first line item that’ll disappear when purchasing gets involved. When that’s gone, what do we do? We try to factor all of that gray area into the detailed project plan. So we can look at that project plan and say, “Okay, if it really explodes, this is the worst case scenario.” To a certain extent, we can use that built-in buffer to manage our risk.
Many acquirers (especially their purchasing departments) are tempted to dip into the project’s management reserve or buffer and suggest that reducing the buffer is a painless way of reducing the planned project cost and delivery time. But this is a myth. Project buffers protect critical tasks from the project’s inherent risk. Project buffers can consist of, for instance, additional resources that become available when you need to protect a critical task, or they may provide additional monies to buy capacity or capability to keep the project on track. Reducing the project buffer has no impact on project execution time; all it reduces are the chances that the promised delivery date will be missed, and potentially it causes excessive replanning.
Therefore, you should not cut the project buffer. Instead, clearly identify the risk associated with every project activity, and then size the project buffer according to the aggregate project risk. This practice not only makes the project risk visible but also provides a single convenient indicator for the impact of the risk on the project.
Tip
Establish and frequently convene acquirer-supplier forums or councils at all levels of the organization.
In an integrated project environment, acquirers communicate with suppliers on a variety of issues common to both organizations throughout the project. This communication requires that you establish forums and create a context in which two-way communication is effective: You must comprehend issues of “manufacturability” or system delivery processes, foster skills in developing robust design constraints that exploit manufacturing capability, and be prepared to trim designs accordingly. Similarly, suppliers must be oriented toward customer satisfaction: They must comprehend issues of product performance and total cost of ownership and must be prepared to deliver and develop a solution that allows the design to achieve its objectives in the intended environment.
Kristin: As suppliers, we really have to step beyond our traditional organizational boundaries. We have to make a concentrated effort to solve the problem from the acquirer’s business perspective. The challenge is that sometimes it’s easier for a supplier to look at it only from a technology perspective. But we can’t become complacent. And that’s where we need help from the acquirer to understand the parameters we can apply to a particular solution.
Matt: We’ll all be winners, or we’ll all be losers. My people and the suppliers’ people must form a high-performance team.
Matt’s incisive statement brings home the point. Successful acquirers attempt to maximize cooperation among stakeholders. In other words, the acquirer involves and integrates all relevant stakeholders, and the supplier agreement provides the basis for managing the supplier’s involvement. Kristin agrees.
Kristin: You’d like everyone to get on board at the beginning of a project and agree. “Here’s what we’re doing, and here’s the road map we’re following.” It’s like when you get on an airplane and they announce, “This is the plane going to Spokane.” Every once in a while you hear somebody say, “Spokane!? That’s not where I’m headed.” And they grab their stuff and get out of there. If they have any sense, they’re glad the airline makes this announcement on every flight.
Matt: I hear you. We spend our time discussing why a project exploded rather than spend a fraction of that time up front to ensure that it doesn’t explode!
Kristin: The problem we run into all the time is that acquirers focus on “Let’s get going” and don’t spend a day or an hour to establish an integrated plan that gets us closer to successfully executing the project. This situation is aggravated when we start a project and the acquirer’s program manager says, “I didn’t know the supplier agreement said that.” Um, have you ever read the agreement? I’ll tell you, the worst is when they say, “Well no, I don’t even have a copy of it. Why would I? That’s what purchasing is for.” Yikes! That’s when you know you’re in trouble.
Involving all stakeholders throughout the project is critical.
Tip
Be persistent when it comes to ensuring that all the right stakeholders are engaged and accountable.
Paula: The stakeholders need to be involved. If they’re not, we need to stop a project until we get them involved across the board. Otherwise, they’ll show up when it’s time to go live with the technical solution. Then you’ll get their ideas, intentions, and requirements.
Steve laughs.
Steve: And then you get to start the project over—believe me, you don’t want to be that project manager.
This gets tricky in a large organization where lots of tasks are delegated. For instance, some of our systems are fairly complex. They require big changes in business processes at the site where the system will be installed. If you don’t engage the right stakeholders from that specific site, you get to the end of your project and then find out this is not what they wanted.
Depending on the scope and risk of the project, your coordination effort among stakeholders and with the supplier can be significant. To integrate the effort across functions and suppliers, you need to add specific activities that support cross-functional work. For example, a supplier might build prototypes to support your desire to develop richer customer understanding early in the process. To complete the loop, the supplier participates with your personnel when interacting with customers to strengthen and deepen their understanding of the experience that the product will create.
The supplier aligns its system delivery processes with your acquisition processes early in the project and, if necessary, collaborates with you to tailor processes. Moreover, prototype testing and evaluation are conducted jointly by all the functions involved in development.
All these interactions happen only when an integrated plan is in place that establishes clear accountability. George offers a comment.
George: What finally made it work was when Steve came on the scene and demanded the accountability of all players—his project team and all the suppliers. He insisted on everybody understanding their role and accountabilities, along with the accountability of every other role on the project. That’s what Steve does so well.
Kristin: At every meeting, Steve went around the room and everyone had to give their yes or no on the decisions and their level of confidence that the decision would be carried out successfully. People don’t like to do that. In any case, Steve’s message was clear: If you didn’t feel accountable, you’d be gone.
The CMMI-ACQ provides specific processes for handling difficulties you might have with integrated project work. It attacks problems at their root and starts you on a path to improving your project execution. The Integrated Project Management process area focuses on establishing and managing projects and involving the relevant stakeholders according to an integrated and defined process that is tailored from your organization’s set of standard processes (see Table 4-1).
Table 4-1. Integrated Project Management Goal 1: Practices and Tips
CMMI-ACQ Process Area: Integrated Project Management | ||
1. Goal: The project is conducted using a defined process that is tailored from the organization’s set of standard processes. | ||
Practices | Tips | |
1.1 | Establish and maintain the project’s defined process. |
|
1.2 | Use the organizational process assets and measurement repository for estimating and planning the project’s activities. |
|
1.3 | Establish and maintain the project’s work environment based on the organization’s work environment standards. | |
1.4 | Integrate the project plan and the other plans that affect the project to describe the project’s defined process. | |
1.5 | Manage the project using the project plan, the other plans that affect the project, and the project’s defined process. | |
1.6 | Contribute work products, measures, and documented experiences to the organizational process assets. | |
According to the CMMI-ACQ, a project’s defined process addresses all activities, tasks, templates, procedures, and guidelines that a project needs to execute to acquire and maintain the technology solution (Table 4-1, practice 1.1). The product-related life-cycle processes—for instance, support processes—are developed concurrently with the product. The project’s defined process must satisfy the project’s contractual and operational needs, opportunities, and constraints. A project’s defined process is designed to provide a best fit for the project’s needs and is based on the following factors:
Customer requirements
Product and component requirements
Commitments
Organizational process needs and objectives
Operational environment
Business environment
Project managers usually select a life-cycle model from those available in the organization’s library of process assets. One approach is to contact another project manager who has executed a similar acquisition and who can help you select a subset of standard processes that best fit the needs of the project.
Some activities, templates, checklists, and guidelines might apply to a project only to some degree or in a modified form. Modifying the standard processes to fit a specific project is what we mean by tailoring. Typically, you provide tailoring guidelines to support the project when defining its processes. Some acquirers even provide “pretailored” versions to simplify and expedite tailoring.
To develop a realistic plan, you must understand the relationships among the various tasks and work products of the defined process and the roles fulfilled by the stakeholders (Table 4-1, practice 1.2). When the results of previous planning and execution are available, use them as predictors of the relative scope and risk of the effort you’re estimating. To arrive at accurate estimates during project planning, successful acquirers typically do the following:
Use appropriate historical data from the current project or similar projects.
Account for and record similarities and differences between the current project and the historical projects.
Independently validate the historical data.
Record the reasoning, assumptions, and rationale used to select the historical data.
To support the desired level of performance and reliability, it is critical to establish an appropriate work environment for the project (Table 4-1, practice 1.3). An appropriate work environment comprises the facilities, tools, and equipment people need to perform their jobs effectively. As with any other product, the critical aspects of the work environment are driven by requirements. You should explore the work environment’s functionality and operations with the same rigor as you do for any other product development.
Depending on the scope of the outsourcing endeavor and the type of the technology solution, you might maintain your own environments for integrating, verifying, and validating the delivered technology solutions. Acquirers that productize and sell technology to their customers, or those that develop technology solutions in-house in addition to acquiring them, often prefer to establish their own integration and test environments. In contrast, organizations that rely solely on suppliers to provide (and maintain) technology solutions tend to hold their suppliers responsible for creating and maintaining integration and testing environments. This situation more closely resembles the purchase of commodities, where buyers pay to use the product but don’t expend their own resources to ensure the product’s quality.
Your integrated plan addresses additional planning activities such as incorporating the project’s defined process, coordinating with relevant stakeholders, using organizational process assets, incorporating plans for peer reviews, and establishing objective entry and exit criteria for tasks (Table 4-1, practices 1.4–1.6). For you to continuously improve, projects must contribute to your process asset library, which documents lessons learned on projects and programs. Your process asset library is also a repository for storing process and product measures.
You manage and coordinate stakeholder involvement according to the project’s integrated and defined process (see Table 4-2, practice 2.1). You manage the supplier’s involvement according to the supplier agreement.
Table 4-2. Integrated Project Management Goal 2: Practices and Tips
CMMI-ACQ Process Area: Integrated Project Management | ||
2. Goal: Coordination and collaboration of the project with relevant stakeholders is conducted. | ||
Practices | Tips | |
2.1 | Manage the involvement of the relevant stakeholders in the project. |
|
2.2 | Participate with relevant stakeholders to identify, negotiate, and track critical dependencies. |
|
2.3 | Resolve issues with relevant stakeholders. | |
Acquirers conduct frequent reviews with stakeholders (Table 4-2, practice 2.2) and typically establish milestones for each critical dependency in the project schedule. Tracking the critical dependencies typically includes the following activities:
Evaluating the impact of late and early completion on future activities and milestones
Resolving actual and potential problems with the responsible parties whenever possible
Escalating to the appropriate level the actual and potential problems not resolvable by the responsible individual or group
Inevitably, communication issues arise that require you to work even more closely with the stakeholders (Table 4-2, practice 2.3). In some cases, it might be necessary to escalate to the appropriate stakeholder managers any issues that cannot be resolved. You should anticipate this scenario and define clear, concise escalation procedures that are well understood by all stakeholders.
Most people take configuration management (CM) for granted, but you will suffer great misery if your acquisition artifacts, products, and services aren’t version controlled, stored, and easily accessible so that you can get to them when you need them. Only too quickly you will find yourself looking for the famous needle in the haystack.
Paula: We’re ready to kick off an enhancement project for the financial system. Where are all the artifacts we created for the last release? Where are the requirements specification, the release plans, the detailed design, the test cases and test results? Where is everything?
Steve, the project manager, wishes he hadn’t picked up the phone. Now he’s scrambling to answer Paula’s piercing questions.
Tip
Treat configuration items as organizational assets, and tag them to the technical solution throughout its use.
Steve: Give me a couple of hours, Paula, and I’ll e-mail them to you.
After Steve snaps his cell phone shut, his face brightens. He thinks, “I’ll call George Taylor.” As the supplier’s project manager, George delivered the first release of the financial system. Steve places the call.
Steve: George, I need all the artifacts from the first release of the new financial system. Can you send them PDQ?
Silence greets Steve on the other end of the line. “Did I lose the connection?” he wonders. Finally George speaks.
George: Well, as far as I can remember you kept the master copies. We have a policy to scrap all deliverables after the customer approves them.
Steve’s heart sinks. He thinks, “I should’ve told Paula weeks, not hours. We’ll have to conduct an archeological dig or, worse, re-create almost everything.” He’s determined to never let this happen again. He pulls together his team along with representatives from supplier organizations to discuss configuration management.
Steve: Thanks for coming, everyone. We all know the purpose of configuration management. We want to establish and maintain the integrity of our acquirer work products and the solution. For every project, for every technical solution, we have to do some CM to maintain our documentation, and you suppliers have to do some to develop and operate the technical solution. Let’s define who’s responsible for keeping what, and how we can store and retrieve project artifacts.
Your approach to configuration management depends on acquisition-specific factors such as the acquisition approach, the number of suppliers, the design responsibility, the support concept, and associated costs and risks. Configuration items can vary widely in complexity, size, and type, from COTS software to a test metric or project plan.
Steve: When we first tried to designate items for CM, we ended up with a long, long list. We all looked at each other. “What do we do now?” We didn’t have the funds to apply rigorous CM to everything, nor does it make sense to carry this overhead for each program. In the end, the solution we came up with was simple and pragmatic—a kind of Occam’s razor for CM. We designate only the minimum number of items we need to sustain a technical solution in the intended environment as configuration items. This resulted in very few acquirer-created items, and a well-defined list of supplier deliverables. For instance, on our side we concentrate on the requirements, design constraints, acceptance tests, and supplier agreement.
Tip
Designate artifacts as configuration items only if they are necessary to maintain the technical solution.
Typically, any item required for product support and designated for separate procurement is a configuration item, along with acquirer work products provided to suppliers (for example, solicitation packages and technical standards). Paula, the internal customer for the current acquisition project, speaks up.
Paula: This approach to CM also made us rethink how we deal with information and data throughout the project life cycle. We used to be very document-centric. Our drive to minimize and reuse configuration items requires us to carefully examine whether a document is necessary or whether its content wouldn’t be better stored in a database so that we can run a report to retrieve it. In other words, we now pursue a more data-centered approach.
To avoid unexpected costs to procure, reformat, and receive configuration items from the supplier, you need to identify configuration items early and incorporate them into the integrated project plan. For acquirers, this includes considering how configuration items are shared between the acquirer and supplier and among relevant stakeholders. If you allow a supplier to use its CM system, you are responsible for implementing security and access control procedures. In many cases, an alternative solution is for the acquirer to grant physical possession of acquirer-created configuration items. In turn, the supplier gives the acquirer access to supplier deliverables.
Tip
Store configuration items with the responsible party and as close as possible to their primary use.
Steve: We heavily debated where to store our configuration items. Some folks started out with the belief that all items must be in our physical possession. Well, after we analyzed this, it turned out to be very costly and a bureaucratic nightmare. It would have created countless handoffs, a complicated system of oversight, and multiple approvals for even the simplest transaction. In our multisupplier environment, this would have seriously impeded direct supplier-to-supplier interaction. Every transaction would have required us as the acquirer to serve as a middle layer to physically take possession of a supplier deliverable before it could be transferred from one supplier to the next.
Paula: That would have been a headache.
Steve: That’s right. For instance, in my group we use one supplier to develop the technical solution and another set of suppliers to host and maintain it. The development supplier would have to work with a designated person on my staff to provide them with, let’s say, the source code. That person would then have to provide the code to the hosting supplier. Any questions, issues, and interactions always required each supplier to interface with my acquisition team, who in turn would have to negotiate a set of action items on behalf of one supplier with another supplier.
Paula: A big hunk of time and resources.
Steve: So we said, “Why not encourage direct supplier-to-supplier interaction and only require acquirer approval when appropriate?” This way, my team could focus on more value-added activities. Eventually, all the acquisition teams agreed on an answer. First, no item is stored in more than one place. Keeping with the principle of storing a configuration item with the responsible party and as close as possible to its primary use, we also decided to keep many items with the suppliers, since they perform all development and maintenance work in our outsourced model. So in our own CM, we only store acquirer-created work-in-progress and sensitive deliverables. It’s more of a document management system.
Paula: Yes, and suppliers are contractually required to maintain their work-in-progress documents, code, and supplier deliverables in their CM systems. The hosting and maintenance suppliers store the production version and required prior versions of the code and associated documents.
If a CM system is shared between acquirer and supplier, then the supplier agreement must specify the clear responsibility for managing the configuration items, baselines, security, access restrictions, and backup and restore processes. You must ensure that the supplier agreement specifies the CM requirements for the supplier (e.g., status reporting and providing configuration audit results).
The supplier agreement should also specify appropriate acquirer rights to the supplier deliverables, in addition to the requirements for delivery or access. For instance, you typically maintain the right to access configuration data at any level to implement planned or potential design changes and support options. Configuration management of legacy systems should be addressed on a case-by-case basis as design changes are contemplated.
Tip
In the supplier agreement, clearly specify access and required security of the configuration management system.
When do you create a baseline for the configuration items? Steve ponders this question for a while.
Steve: You have to carefully decide when to lock down a set of items, because after you declare a baseline you can only adjust it through change control. You don’t want to end up in change control hell, but you also don’t want to baseline too late and lose all visibility into project activities and how artifacts develop and change.
Paula: How do you strike a happy medium?
Steve: Over the years, I’ve found it useful to tie baselines to major approvals or milestones in a project. For example, we create baselines for our own work products to mark agreement on the description of the project, requirements, funding, schedule, and performance parameters and to make a commitment to manage the program to those baselines. I’m talking about work products such as contractual requirements and acceptance criteria that are related to the product baseline managed by the supplier. We also review and approve the product baselines created by the supplier and contractually tie them to supplier payments.
With regard to the technical solution, you maintain configuration control of your requirements, and the supplier performs configuration management of the technical solution (e.g., establishing and maintaining the product baseline). In this way, you retain the authority and responsibility for approving any design changes that affect the product’s ability to meet contractual requirements. The supplier manages other design changes.
Tip
Use an artifact’s value and its risk to the project to determine its required level of change control.
The level of control is typically selected based on project objectives, risk, and the value of the configuration item to the project. Levels of control can range from informal control (simply tracking changes made when you are developing the configuration items or when supplier work products are delivered or made accessible to you) to formal configuration control using baselines that can be changed only as part of a formal CM process. Although the supplier may manage configuration items on your behalf, you are responsible for approval and control of changes to such configuration items.
Change requests can be initiated either by you or by the supplier. Changes that affect your work products and supplier deliverables as defined in the supplier agreement are typically handled through your CM process. You analyze the impact of submitted change requests on the supplier agreements.
Steve: All of our acquisition project teams and all of our suppliers have to follow the same change control process. The intent is to ensure smooth changes. The suppliers implement any requested changes, so we require them to log and track all changes in their area of responsibility. However, before work on a change request can begin, the change request must be approved by the relevant change control board. Each CCB consists of members from our organization, customers, and suppliers. The CCB ensures that all important viewpoints are considered when evaluating and prioritizing a change request.
The CMMI-ACQ provides specific recommendations on how you can optimize configuration management as an acquirer of technology solutions. Configuration management specifically focuses on establishing and maintaining the integrity of work products using configuration identification, control, status accounting, and audits (see Table 4-3).
Table 4-3. Configuration Management Goal 1: Practices and Tips
1. Goal: Baselines of identified work products are established. | ||
Practices | Tips | |
1.1 | Identify the configuration items, components, and related work products that will be placed under configuration management. |
|
1.2 | Establish and maintain a configuration management and change management system for controlling work products. |
|
1.3 | Create or release baselines for internal use and for delivery to the customer. |
|
An acquirer typically designates work products or supplier deliverables as configuration items when they’re critical to the project, are used by two or more groups, or are expected to change over time either because of errors or changes in requirements (Table 4-3, practice 1.1). Each configuration item has a responsible owner. In addition, each item has a unique identifier. Frequently, projects also specify important characteristics of each item for easier classification and retrieval.
To avoid unexpected costs to procure, reformat, and deliver configuration items from the supplier, you conduct your planning for managing configuration items—including during transition to operations and support—as part of project planning. Include plans and the infrastructure for managing these items within the project teams and between the acquirer, supplier, operational users, and other relevant stakeholders. You need to clearly define when each configuration item is placed under CM. Sample criteria include the following:
To store configuration items with the responsible party and as close as possible to their primary use, you need to designate a CM system (Table 4-3, practice 1.2). Such a system describes the storage media, the procedures, and the tools for accessing the system. Sometimes this system also includes the tools for recording and accessing change requests. In addition to storing and retrieving configuration items, you include contractual provisions to ensure the necessary sharing and transfer of configuration items between you and the supplier.
You review and approve the release of the product baselines created by the supplier (Table 4-3, practice 1.3). A baseline is a set of specifications or work products that has been formally reviewed and agreed on. Thereafter it serves as the basis for further development or delivery and can be changed only through change control procedures. You also create baselines for acquirer work products to mark the agreement on the description of the project, requirements, funding, schedule, and performance parameters and to make a commitment to manage the program to those baselines. To create or release baselines of configuration items, a project must obtain authorization from the change control board.
Consistently tracking changes to baselined configuration items is critical for acquirer and supplier (see Table 4-4, practice 2.1). Change requests address not only new or changed requirements but also failures and defects in the work products. You analyze the impact that submitted change requests will have on the supplier agreements. You also determine the impact that the change will have on the work product, related work products, and schedule and cost.
Table 4-4. Configuration Management Goal 2: Practices and Tips
CMMI-ACQ Process Area: Configuration Management | ||
2. Goal: Changes to the work products under configuration management are tracked and controlled. | ||
Practices | Tips | |
2.1 | Track change requests for the configuration items. |
|
2.2 | Control changes to the configuration items. |
|
Frequently, stakeholders request more changes than can be accommodated within a project. In this case, the change control board consults the relevant stakeholders and decides whether such change requests can be addressed in the next release of the solution; the stakeholders then agree to defer some the proposed changes. This negotiation includes keeping records of the disposition of each change request and the rationale for the decision, including success criteria, a brief action plan if appropriate, and needs met or not met by the change.
You maintain overall control of the configuration of the work product baseline (Table 4-4, practice 2.2). It’s important to control changes to configuration items throughout the life of the product. This control includes tracking the version of each item, approving a new configuration of the solution if necessary, and updating the baseline. For example, authorization to access configuration items may come from the change control board, the project manager, or the customer. Only with the proper authorization are configuration items checked in or checked out of the CM system for review or modification. Changes must be incorporated in a manner that maintains the correctness and integrity of the items. In many cases, this requires reviews to ensure that changes do not cause unintended effects on the baselines (e.g., ensure that the changes have not compromised the safety or security of the system).
To establish and maintain the integrity of baselines, you record CM actions in sufficient detail that the content and status of each item is known and previous versions can be recovered (see Table 4-5, practice 3.1). In addition, projects can ensure the integrity of baselines by following these practices:
Ensuring that relevant stakeholders have access to and knowledge of the configuration status of the items
Specifying the latest version of the baselines
Identifying the version of the configuration items that constitute a particular baseline
Describing the differences between successive baselines
Revising the status and history (i.e., changes and other actions) of each configuration item as necessary
Table 4-5. Configuration Management Goal 1: Practices and Tips
CMMI-ACQ Process Area: Configuration Management | ||
3. Goal: Changes to the work products under configuration management are tracked and controlled. | ||
Practices | Tips | |
3.1 | Establish and maintain records describing configuration items. |
|
3.2 | Perform configuration audits to maintain the integrity of the configuration baselines. |
|
Periodically, you perform configuration audits to confirm that the resulting baselines and documentation conform to a specified standard or requirement (Table 4-5, practice 3.2). The completeness and correctness of the content are based on the requirements as stated in the plan and the disposition of approved change requests.
As an acquirer of technology solutions, you are still subject to the same business and technical risks that you had before the outsourcing deal. A supplier does not (and really cannot) take over liability for consequential damages. So the risk exists one way or another. To successfully execute a project, you must be able to accurately identify and proactively manage risks.
Throughout the life cycle of the project, you continue to manage the risks related to the supplier and the overall project risks. Both you and the supplier must understand the project risks and know how to modify the risk management strategy and plans as the project progresses. Managing a project’s risks requires a close partnership between you and the supplier. Both organizations need to share risk management documentation and develop and execute risk management efforts.
Considering the track record of organizations that implement technology solutions, it is risky business. A variety of sources contributes to the risks that every acquirer must manage.
Steve: In my consulting days, I saw this all the time. The closer you get to the top of an organization—acquirer and supplier alike—the less likely people are to see a risk or its severity. They don’t want to see it. It’s the Icarus effect. When someone bears news of a potential risk, the leaders let them crash and burn. This kind of organization rewards firefighting, daily crisis management, and heroics to complete projects; it punishes people who try to explain why a project is at risk and try to prevent problems. So everybody learns that talking about risks is not condoned, and nobody will sound an alarm when they see a risk. Then bam! The company gets blindsided by critical problems they could have prevented.
Acquirers can’t afford to possess this kind of attitude toward risk. To survive, you must be able to take rational risks. This means accepting the downside of a decision if the payoff is high enough.
Steve: We have very strong support from our leadership team to bring risks forward and then use a structured risk management process to deal with them. We apply this process very early, rigorously, and continuously. It gives us a disciplined environment for decision making and for using resources efficiently.
By employing a disciplined process, acquirers can uncover risks before they occur so that risk-handling activities can be planned and invoked to mitigate adverse impacts on program objectives. The need for early and aggressive risk detection is compounded by the complexity of projects due to the acquirer-supplier relationship. For example, the supplier’s experience of working with the acquirer, the supplier’s financial stability, or the availability of well-defined dispute resolution processes all influence the risk of a project.
Because of the inherent risks of projects attempting to produce a technology solution, especially in an outsourcing environment, it is paramount for any acquirer to document the risks and make them visible. It’s much harder to ignore a risk if it’s documented. Unfortunately, this task is fraught with peril. Your mind can play tricks on you when it comes to admitting risks. Steve explains.
Steve: We’ve built special provisions into our process to make suppliers, projects, and senior managers aware of risks and to compensate for any mind traps. For example, all employees and suppliers are encouraged to always view a project from different perspectives. We never accept the initial definition of a project or program.
Matt: Can you give an example?
Steve: We always try to reframe the problem in various ways. For instance, we pose problems in a neutral, redundant way that combines possible gains and losses, and then we elicit and embrace viewpoints from different stakeholders. The goal is to think about the full context of the project so that we’re less likely to disregard important data. This also helps us in creating recommendations that don’t have contradictory data or hidden risks. We train our employees as well as our suppliers to play devil’s advocate. What if our approach is wrong? How would we know?
For important projects, the teams must bring in an outsider. This person must help the team dispel the disproportionate weight they tend to give to their own biases and the initial impressions formed about the nature of the risk. All this helps us to better judge our risks.
A simple risk assessment works well when a project possesses little data. Typically this is the case when an organization initially establishes an acquisition strategy. As a project or program progresses, however, greater knowledge justifies more detailed risk analysis.
Steve: We use a risk scorecard and update it regularly based on lessons learned over time. If a project goes into the ditch, you do a post-mortem and ask questions: Why did this happen? What could we have done differently to avoid this? And then you incorporate the findings into your risk scorecard.
As you gain experience with the simple risk assessment, you can develop a risk scorecard based on the ten-question risk analysis presented in Chapter 2. This extended question set (see Figure 4-1) has weights or level of impact for each parameter.
Table 4-1. Sample risk assessment
Instead of intuitively assigning a score for each risk parameter, the project team can formulate and answer a series of detailed questions that produce a score. Additionally, the project team may know that some parameters affect overall risk more than others.
Steve: With a risk scorecard, your objective is to quantify the risks you identify. This gives us a deeper, common understanding of the risks and their severity.
The questions, their ratings, and the level of impact reflect an organization’s current capabilities and areas of emphasis. These data will change as the acquisition strategy and core capabilities change. George agrees.
George: We keep a risk log or database, too. We’ve even established a standard format for risk statements: the underlying premise of a condition, and then the predicted consequence. For example, let’s say you have the statement, “If the code base grows in size, we won’t have enough memory.” Well, that isn’t a valid risk statement, because the precursor, which is code growth, isn’t justified. To meet our format, it has to be something like, “On the last three projects executed by our department, final code size was an average of 147 percent above initial estimates; similar results on this project will exceed memory capacity.” See the difference?
The CMMI-ACQ provides specific recommendations on how to identify and analyze risks. Risk management identifies potential problems before they occur so that you can plan and invoke risk-handling activities as needed throughout the life of the product to mitigate adverse impacts on achieving objectives (see Table 4-6).
Table 4-6. Risk Management Goal 2: Practices and Tips
CMMI-ACQ Process Area: Risk Management | ||
2. Goal: Risks are identified and analyzed to determine their relative importance. | ||
Practices | Tips | |
2.1 | Identify and document the risks. |
|
2.2 | Evaluate and categorize each identified risk using the defined risk categories and parameters, and determine its relative priority. |
|
Analyzing risks entails identifying risks from internal and external sources and then evaluating each risk to determine its likelihood and consequences. Identifying potential issues, hazards, threats, and vulnerabilities that could negatively affect work efforts or plans is the basis for sound and successful risk management (Table 4-6, practice 2.1). Risks must be identified and described in an understandable, consistent way before they can be analyzed and managed properly. Risks are documented in a concise statement that includes the context, conditions, and consequences if the risk occurs.
You should follow an organized, thorough approach to seek out probable or realistic risks that might affect your achieving your objectives. To be effective, risk identification should not be an attempt to address every possible event no matter how improbable it may be. Instead, you should follow a disciplined, streamlined approach that uses the categories and parameters developed in your risk management strategy, along with the identified sources of risk. The identified risks form a baseline on which to initiate risk management activities. You should periodically review the list of risks to reexamine possible sources of risk and changing conditions and thereby uncover sources and risks previously overlooked or nonexistent when the risk management strategy was last updated.
Typical methods for identifying risks include the following:
Examine each element of the project work breakdown structure to uncover risks.
Conduct an informal risk assessment using, for instance, a risk taxonomy.
Interview subject matter experts.
Review risk management efforts from similar projects or programs.
Examine lessons-learned documents or databases.
Examine design specifications and agreement requirements.
You can identify some risks by using the categories and parameters developed in your risk management strategy to examine the supplier’s work breakdown structure, product, and processes. You can identify risks in many areas (e.g., requirements, technology, design, testing, vulnerability to threats, life-cycle costs). Examining the project or program in each of these areas can help you develop or refine the acquisition strategy and the risk-sharing structure between you and the supplier.
You should also consider the risks associated with a supplier’s capability (e.g., meeting schedule and cost requirements), including the potential risks to your intellectual capital or security vulnerabilities introduced by using a supplier.
Certain kinds of risks are often missed. These include risks thought to be outside the scope of the project; in fact, even though the project does not control whether they occur, you can mitigate their impact. Examples include the weather, natural or manmade disasters that affect the continuity of operations, political changes, and telecommunications failures.
To the extent that they affect project objectives, cost, schedule, and performance, risks should be examined during all phases of the product life cycle in the intended environment. You may discover potential risks that are outside the scope of the project’s objectives but are vital to customer interests. For example, the risks in development costs, product acquisition costs, cost of spare (or replacement) products, and product disposition (or disposal) costs have design implications. The customer may not have provided requirements for the cost of supporting the fielded product. The customer should be informed of such risks, but it may not be necessary to actively manage those risks. The mechanisms for making such decisions should be examined at project and organization levels and put in place if deemed appropriate, especially for risks that affect the ability to verify and validate the product.
Risk statements are typically documented in a standard format that contains the risk context, conditions, and consequences. The risk context provides additional information so that the intent of the risk can be easily understood. In documenting the context of the risk, you should consider the relative time frame, the circumstances or conditions, and any doubt or uncertainty.
You need to evaluate risks so that you can assign relative importance to each identified risk and determine when appropriate management attention is required (Table 4-6, practice 2.2). Each risk is evaluated and assigned values in accordance with the defined risk parameters, which may include likelihood, consequence (severity of impact), and thresholds. You can integrate the assigned risk parameter values to produce additional measures, such as risk exposure, which can be used to prioritize risks. Often it is useful to aggregate risks based on their interrelationships and then develop options at an aggregate level. When you form an aggregate risk by rolling up lower-level risks, take care that important lower-level risks are not ignored.
You categorize risks into defined risk categories, providing a means to view risks according to their source, taxonomy, or project component. Related or equivalent risks can be grouped for efficient handling. You should document the cause-and-effect relationships between related risks. Your risk categories might include sourcing, contract management, and supplier execution in addition to project management, technology, and requirements.
Acquirers prioritize risks for mitigation. You use clear criteria to determine a relative priority for each risk based on the assigned risk parameters. Your goal is to determine the areas to which risk mitigation resources can be applied with the greatest positive impact to the project or program.
Risks are handled and mitigated, when appropriate, to reduce adverse effects on achieving your objectives.
Steve: You can’t fix everything! You have to ask as objectively as possible, “Which risks are truly important?” You must identify critical risks and watch them for significant changes.
You first identify the most important risks and then decide how many of them you have the resources to mitigate.
Steve: When we decided to get serious about risk management, we started small. I guess you could say this is a risk mitigation approach of sorts. We had already learned that teams new to risk management have trouble dealing with more than ten risks. So we helped each project identify and handle their top ten risks. They periodically reorder their risks by voting or through forced ranking. It’s based on the team’s consensus about the most important parameter at the time, like quality or cost.
You must identify which risks can be accepted (that is, you can live with them if they do become problematic) and which risks can be assigned to someone who is better able to manage them.
Steve: We look at this throughout the project. Most projects use a quick-and-dirty estimate to classify each risk as high, medium, and low impact. Unless the risk has a big impact, such as doubling the budget to deliver this solution, we make it clear to all projects that they really don’t need to quantify impact and probability early. For example, one group filtered out the top five risks for precise analysis during risk planning, and they managed the other risks without further analysis.
Matt: We should emphasize, though, that this doesn’t negate a project’s responsibility to perform risk management as a continuous activity throughout the project life cycle. It’s really helpful to review risks at every regular project meeting. You may get to retire some risks, or you identify new risks that make it onto your top-ten risk list.
Paula adds an important point.
Paula: I’m big on risk reporting—throughout the project, up the chain of command, down the chain of command, and any which way you can go on the org chart. I’ve seen many projects put together a 5 × 5 risk matrix color-coded in red, yellow, and green. This is a great practice, but only if the content is up-to-date. It’s a warning sign—I guess you could say it’s a risk in itself—if a project only updates the risk matrix at the last minute once every three or six months, and coincidentally right before a major program review. That’s just nuts. You can be assured that we’ve developed an arsenal of probing questions about risks to encourage projects to adjust their behavior if necessary and treat risk management as a continuous activity.
The ultimate responsibility for risk management rests with you, but a close partnership between you and your suppliers is crucial if you are to effectively identify and mitigate risks. Both you and the supplier need to share risk information, understand each other’s risk assessments, and develop and execute risk mitigation efforts. You must involve the supplier as early as possible so that you can establish effective risk assessment and reduction. For instance, the supplier has often much deeper insight into the technical risks than you have.
Kristin: Forming a joint acquirer-supplier risk evaluation team is a good way of fostering an effective partnership. This is especially true in the early days of a program, when uncertainty is high and both parties must frequently assess risks. Together with you guys, we form a joint team of subject matter experts who can evaluate the proposed program in detail to identify risks and propose strategies when necessary.
You need to include specific risk assessment and risk-handling tasks in the RFP and subsequent supplier agreement.
The progress of project activities should lower the project’s perceived risk. In fact, when an organization pursues any new technical solution, it must deliberately acquire competencies to reduce risk and ensure success. If successive reviews demonstrate steady or rising project risk, it sends a strong signal that you need to reexamine the project’s viability. In contrast, steadily decreasing risk increases your confidence of a successful outcome. A properly designed and executed risk management process lets you make decisions about the fate of a project, thereby enabling you to make intelligent bets. In general, acquirers are better off receiving risk information early, because it gives them an opportunity to decrease the downside and raise the upside.
Matt: You want to increase your odds. Smart risk mitigation puts you in a position to place your bets anew after projects clear a common milestone. As uncertainties decrease, expenditures can rise and risk is managed.
Steve: We’ve identified a couple of techniques to get a leg up on mitigating risks. One of the most breathtaking successes also turned out to be the simplest. You don’t have to have a new technical solution to effectively resolve business or mission risk. You can use a competitor’s product or a modified version of the product to gauge the customer’s intent. This will teach you quickly if you’re solving the right problem. When we pursue a COTS solution, we take it one step further and use the COTS product as the prototype. Given that we stand the COTS solution up in our hosting environment, this also doubles as an early technical evaluation of the supplier’s product. Prototyping also lets you pick a particularly risky aspect or attribute of the technical solution and expose it to the customers to find out what they really want.
Moving fast is an additional risk mitigation technique commonly used by successful acquirers.
George: One of the difficulties we ran into with an acquirer was the program manager. She really wanted a big-bang approach—delivering a large chunk of new technology after it was in development for years. We spent a lot of time in highly emotional debates. Of course, we wanted a more phased approach to minimize risk to the business. All this changed when we started working with Steve. He understood exactly what we were saying, and actually drove us toward a more evolutionary, iterative approach. So, you really have to understand the risk to the business, and you have to look at your solution and how you could possibly roll it out and manage the change that’s going to happen. I think this is a critical part of any project.
Controlling the technical risk of integration should be at the forefront of any acquirer’s mind: How do you ensure that the suppliers integrate the various components into a value-added solution and then integrate the technical solution into your environment? Steve has a couple of ideas.
Steve: Like I always say, the more you can make the technology plug-and-play, the better off you’ll be. We work hard on standardizing interfaces between systems so we can reuse them over and over again. We’ve also learned the hard way that you have to focus your energy on those pieces of the solution that really matter. So we specify tighter design constraints for the riskiest interfaces or parts, and give the supplier more leeway on lower-impact components. We also work with our suppliers to integrate solutions as early as possible. As soon as the suppliers have more than one component, the prime supplier forges them into a system weekly, if not daily.
When you close a risk, you document the rationale for closing it, along with successful and unsuccessful actions, assumptions that were proven wrong, mitigation costs, and project savings or return on investment.
Steve: We retain risk information in a database after the risks are closed. This information is a tremendous benefit to the organization on future projects.
The CMMI-ACQ provides specific recommendations on how to handle risks, including developing risk-handling options, monitoring risks, and performing risk-handling activities when defined thresholds are exceeded (see Table 4-7).
Table 4-7. Risk Management Goal 3: Practices and Tips
CMMI-ACQ Process Area: Risk Management | ||
3. Goal: Risks are handled and mitigated, where appropriate, to reduce adverse impacts on achieving objectives. | ||
Practices | Tips | |
3.1 | Develop a risk mitigation plan for the most important risks to the project, as defined by the risk management strategy. |
|
3.2 | Monitor the status of each risk periodically, and implement the risk mitigation plan as appropriate. |
|
You develop and implement risk mitigation plans for selected risks to proactively reduce their potential impact. A critical component of a risk mitigation plan is to develop alternative courses of action, workarounds, and fallback positions, with a recommended course of action for each critical risk (Table 4-7, practice 3.1). The risk mitigation plan for a given risk includes techniques and methods to avoid, reduce, and control the probability of occurrence, the extent of damage incurred should the risk occur (sometimes called a contingency plan), or both. You monitor risks, and when they exceed the established thresholds, you deploy the risk mitigation plans to return the affected effort to an acceptable risk level. If the risk cannot be mitigated, a contingency plan can be invoked. Both risk mitigation and contingency plans are often generated only for selected risks whose consequences are determined to be high or unacceptable; other risks may be accepted and simply monitored.
Options for handling risks typically include alternatives such as the following:
Risk avoidance: changing or lowering requirements while still meeting the customer’s needs
Risk control: taking active steps to minimize risks
Risk transfer: reallocating requirements to lower the risks
Risk monitoring: watching and periodically reevaluating the risk for changes to the assigned risk parameters
Risk acceptance: acknowledging risk but taking no action
Often, especially for high risks, you should generate more than one approach.
In many cases, risks are accepted or watched. Usually you accept a risk when you judge it too unimportant for formal mitigation, or when there appears to be no viable way to reduce it. If a risk is accepted, the rationale for this decision should be documented. Risks are watched when there is an objectively defined, verifiable, and documented threshold of performance, time, or risk exposure (the combination of likelihood and consequence) that will trigger risk mitigation planning or invoke a contingency plan if it is needed. Thresholds for supplier risks that affect the project (e.g., schedule, quality, or risk exposure due to supplier risks) are specified in the supplier agreement, along with escalation actions if the thresholds are exceeded.
Examine risk mitigation activities and assess the benefits they provide versus the resources they will expend. As with any other project activity, you may need to develop alternative plans and assess the costs and benefits of each alternative. You then select the most appropriate plan for implementation. At times the risk activity may be significant and the benefit small, but the risk must be mitigated to reduce the probability of incurring unacceptable consequences.
To effectively control and manage risks during the work effort, follow a proactive program to regularly monitor risks and the status and results of risk-handling actions (Table 4-7, practice 3.2). For that purpose, you establish a schedule or period of performance for each risk-handling activity that includes the start date and anticipated completion date. This requires continued commitment of resources for each plan.
The risk management strategy defines the intervals at which the risk status should be revisited. This activity may result in the discovery of new risks or new risk-handling options that can require replanning and reassessment. In either event, you should compare the acceptability thresholds associated with the risk against the status to determine the need for implementing a risk mitigation plan.
You share selected risks with the supplier. Risks associated specifically with the acquisition process are tracked and then resolved or controlled until mitigated. This monitoring includes risks that may be escalated by the supplier.
Every acquirer uses measures; at a minimum, acquirers of technology solutions count their money. Measures provide data for making decisions and describe the results of those decisions. Measurement is the process that tells an organization how well it is doing what it wants to do. Commonly used measures are geared toward measuring current performance. When you are delivering projects, however, the concern is future performance. Decisions made today are tomorrow’s results.
You need measurement systems that can indicate the expected future results so that you can make appropriate interventions in the present. An effective measurement system monitors individual projects, a program or portfolio of projects, and the process by which they are managed.
As you become more familiar with the concepts that are developed and illustrated in the pages that follow, you need to understand that the perfect process for measuring the success of technology solutions is as yet unknown. The remainder of this chapter describes in detail a current best practice for an acquirer to develop and maintain a measurement capability that enables it to determine the status of its progress and output, the supplier’s progress and output per contractual requirements, and the status of the evolving acquired products. It also covers monitoring and control of your own activities and overseeing the progress and performance of the supplier’s execution according to the project plans.
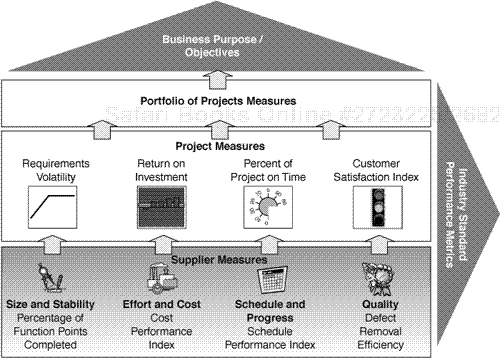
To effectively manage projects, you must have the necessary data or information at your fingertips when you need it. For many organizations, reaching this goal proves elusive. Matt, however, no longer worries about the usual disconnect between the data an acquirer needs to run its business and the data an acquirer has available to make decisions. Matt has what he calls the “House of Measures.” Like an instrument panel in a car, the House of Measures provides critical information in easy-to-read graphics, assembled from data extracted in real time from the acquirer’s measurement databases and, in some instances, directly from the suppliers’ measurement repositories. Let’s see how the House of Measures is built.
Matt: Before we had the House of Measures, taking our pulse was sort of ridiculous. To get the latest project delivery numbers, I would call several people and wait for days—sometimes weeks—for them to compile reports that were out of date by the time they hit my desk. Sometimes it was even worse. We didn’t even have the data collected to answer a basic question about our business. You had to work on guesswork alone, with no real-time data to put you in touch with your business.
Before you can decide what the right measures are, you need to decide what to measure.
Matt: You have to be perfectly clear about the purpose of your endeavor. We’re interested in achieving our economic goals. Our goal is to make money in the end. We acquire software, systems, and IT for this purpose and for this purpose only. We can never forget that. Every action every day is subordinated to achieving our purpose. To keep on track, we have to have measures that let us judge the impact of our decisions. We need to know what levers we need to pull to stay the course or to get back in the fast lane.
Without the right measures, you can start pulling the wrong levers—to use Matt’s analogy—and you go out of business even though all indicators show green, full steam ahead into the abyss.
Creating a good, precise set of measures to predict your success is difficult. It is often difficult to get consensus on how to measure the achievement of acquisition goals and the authoritative source for the measure. Yet getting buy in of key stakeholders and constituents is critical in obtaining a meaningful measurement of project execution. It is equally important to manage this process so that you end up with the few critical measures that truly matter.
Steve: Don’t make too many measures, or you’ll cause what I call “metrics saturation.” You can’t just sprinkle measures like fairy dust over your processes. You have to get your hands on what makes a difference in the overall objective. If projects have to deal with a handful of measures they tend to do very well. If they have to deal with—let’s say—110 metrics, they lose focus. Everything becomes critical, but nothing is important. At best, projects will probably rate “mediocre” in every one of those 110 metrics. So metrics saturation obscures your vision. The project manager loses his focus on the project itself. He starts to worry more about how the metrics are reported and interpreted by management.
So how do you arrive at the few critical measures? Acquiring software, systems, and IT, like any other business activity, works best with timely feedback. Such feedback indicates how a process is functioning and signals the need for intervention. Short-duration, repetitive processes, which are common in manufacturing environments, provide ample opportunities for measuring their efficacy through demonstrated results. But acquisition projects have comparatively long lead times and unrepetitive tasks, and that poses difficulties for acquirers that manage with results data only. You cannot afford to receive status reports only at the completion of a project or significant milestone; you need interim feedback. You must manage the acquisition process itself through results or output measures and progress measures.
Outcome metrics characterize activities’ results by describing how well objectives are accomplished. Progress metrics, in contrast, characterize the current status of activities that are not yet complete. Outcome metrics allow you to look in the rearview mirror. They describe after-the-fact results, whereas progress metrics enable intervention that can affect results.
To get a balanced mix of outcome and progress measures, you need to get a handle on how to use supplier measures. To manage projects, you use supplier-reported measures in addition to your own measures of progress and output. The addition of supplier measures allows you to comprehensively address the measurement objectives and determine the progress and output of the project. Supplier measures are the foundation of the House of Measures (see Figure 4-2).
To build a solid foundation for the House of Measures, you should use accepted standards within the industry when defining measures that the supplier reports to you.
Kristin: It’s frustrating to me—and I believe to every supplier or acquirer—that there is so much variance in the definition and interpretation of measures. Here’s an analogy. Let’s say you take a business trip and want to work out at the hotel’s gym, but first you want to weigh yourself. “Not so fast,” the gym manager says. “First you have to attend our three-day workshop to define the right measure for your needs. Pounds? Grams? Furlongs per fortnight?”
Nobody would accept this in today’s world. Yet, here we are in the technology space redefining the same measures over and over again. Different organizations set up different ways of calculating what “on time” means, what “on budget” means, what “quality” means. One might determine their on-time metric by taking all the projects that have been performed and all the dates and hours that have been allocated. Then they’ll roll up the data and take it and divide one into another to say that we’re actually within 5 percent, or we’re not. Another company will use a completely different calculation.
Steve: How do you deal with that?
Kristin: We actually show acquirers our measurement framework. We share with them the calculations, the terminology, the way they can roll them up. We’re trying to get them to move to a more standard set of measures.
Let’s hope that enough acquirers and suppliers adopt a common set of measurement definitions to increase the efficiency of acquiring technology solutions. However, standard or not, supplier measures must be defined in the supplier agreement. The agreement specifies which measurement data the supplier must provide, in what format, how the data will be collected and stored by the supplier (e.g., a retention period for data), how and how often it will be transferred to the acquirer, and who will have access to the data. Some suppliers may consider some of their data proprietary, so you may need to protect it. Also consider that some of your measurement data (e.g., total project cost data) may be proprietary and should not be shared with suppliers. You need to plan for the collection, storage, and access control of these types of sensitive data.
Tip
Specify measures for project schedule and progress, effort and cost, size and stability, and quality.
Several measures indicated in Figure 4-2 offer a good starting point while the search for better measures continues. The regularly used measures can typically be traced to one or more of these measurement information categories: schedule and progress, effort and cost, size and stability, and quality.
Kristin: There’s a lot of dissent—or lack of credibility, one could say—about how to measure output. Let me give you an analogy. Let’s say you measure your progress over three years. You need to produce 5 tomatoes this year, 10 next year, and 15 the year after that. So now you’re in year 3, and it looks like you’ve tripled your output. That’s terrific. But wait a minute. You also need to look at your units of energy in producing those tomatoes. If your—let’s call it—“effort measure” stayed consistent for those three years, then you have indeed tripled your output. But both measures are useless if you don’t have a quality metric to verify that the tomatoes produced in year 3 are just as good or better than those from year 1, or at least approaching the same levels of quality. All four of those measures—schedule or progress, quality, effort to deliver, and size—have to be there.
It’s frustrating when there is no accepted measure of size.
Kristin: In our organization, we don’t have a good and commonly agreed-upon size measure. We use function points, and I’m very function-point biased, but purely because it’s the only measure we’ve got that has a widely adopted industry standard, an active community, and a credible following. Even if you don’t use formal function-point counters, you’re better off. For instance, we use an informal tool that collects the basic parameters for function-point counting. It’s a way for us to say to the team, “When you’re working with an acquirer, you run this Web-based tool and understand the approximate size of what you’re delivering.” In the next release you use it again, and in the release after that you do the same thing. Over a year, you can go back to a customer and say, “Look, each request that you’ve done has averaged out to be this size, and we’ve improved in these ways as we’ve gone forward,” as opposed to having no idea about size.
Measures can be either base or derived. Data for base measures are obtained by direct measurement. Data for derived measures come from combining the results of two or more base measures. Derived measures are typically expressed as ratios, composite indices, or other aggregate summaries. Often, summary measures are more quantitatively reliable and meaningful than the base measures from which they’re derived. A direct relationship exists between measurement objectives, measurement categories, base measures, and derived measures, as depicted in Table 4-8.
Table 4-8. Measurement Examples
Measurement Information Categories | Sample Base Measures | Sample Derived Measures | |
|---|---|---|---|
Shorter time to delivery | Schedule and Progress |
|
|
Reduced total life-cycle cost | Effort and Cost |
|
|
Deliver specified functionality completely | Size and Stability |
|
|
Improve levels of quality | Quality |
|
|
In some cases, you augment your measures with supplier measures. For instance, your return on investment metric can incorporate the supplier’s cost performance index. In most cases, however, the suppliers’ measures are the primary source of data, especially with regard to the development of the acquired product or service. For instance, for effective management of the project’s quality, size, cost, and schedule, it’s essential to measure and analyze the supplier-provided product or components by using technical performance measures (e.g., amount of new, modified, reused code; percentage of function points completed; defect removal efficiency).
Steve: For each of our significant differentiators [see Chapter 3], we quantitatively define targeted goals, identify the units and methods of measurement, and quantitatively track progress in achieving those goals over time. This also shows us how good a product or service is in satisfying the customer’s needs relative to how those needs are being satisfied today.
Matt: That’s a meaningful number. How do you arrive at it?
Steve: We quantify the differentiators in 5 to 15 parameters. The parameters depend on the differentiators, with one exception: All projects have cost as one of the parameters. We get the cost from those elements that make up the cost of the product rather than relying on its “accounting” value.
So for each parameter, our starting point is established, quantified, and compared to the target. Where possible, we also determine the relative rating of any competitive product and the best value that is theoretically or practically achievable. The gap between the theoretical value and our starting point also give us an indication of a project’s technical risk. This gap analysis is not a one-time deal. You need to report the progress toward meeting the targets at each status report and project review.
Because you receive a significant amount of measurement data from the supplier, it is important that you periodically audit how the supplier collects and analyzes this data. The supplier agreement defines the required data analysis and the definition and examples of the measures the supplier must provide.
Tip
Establish practically achievable and theoretically possible (or stretch) targets for each measure.
Having pristine measurement data and project measures is a prerequisite, but it isn’t sufficient for achieving long-term success. You must also consolidate project measures into a portfolio of project measures—program and organizational measures—that help illuminate to what degree you’re accomplishing your purpose through your collection of projects.
The CMMI-ACQ provides specific recommendations on how to develop and sustain a measurement capability to support management information needs (see Table 4-9).
Table 4-9. Measurement and Analysis Goal 1: Practices and Tips
CMMI-ACQ Process Area: Measurement and Analysis | ||
1. Goal: Measurement objectives and activities are aligned with identified information needs and objectives. | ||
Practices | Tips | |
1.1 | Establish and maintain measurement objectives that are derived from identified information needs and objectives. |
|
1.2 | Specify measures to address the measurement objectives. | |
1.3 | Specify how measurement data will be obtained and stored. | |
1.4 | Specify how measurement data will be analyzed and reported. | |
To tightly integrate measurement and analysis into your processes, you specify the objectives of measurement and analysis so that they are aligned with identified information needs and project objectives (Table 4-9, practice 1.1).
Measurement objectives document the purposes of measurements and analyses and specify the kinds of actions that may be taken based on the results. You establish measurement objectives for your activities and work products as well as for supplier deliverables and milestones. Measurement objectives can range from “reduce time to delivery” to “reduce total life-cycle cost of the acquired technology solution” to “improve customer satisfaction.” They must be documented, reviewed by management and other relevant stakeholders, and updated as necessary.
The measurement objectives are refined into specific measures. Candidate measures are categorized and specified by name and unit of measure. To manage projects, you use supplier data (base measures) and supplier-reported derived measures, in addition to measures of your own progress and output (Table 4-9, practice 1.2). Supplier measures must be defined in the supplier agreement, including requirements for the supplier’s measurement collection and the measurement reports to be provided to you. When you specify supplier measures, it is particularly important to specify acceptance criteria for the data to ensure that the intended use of the supplier measures, such as aggregation and analysis by the acquirer, is feasible. To that end, you state measurement specifications in precise and unambiguous terms. They address the following two important criteria:
Communication: What has been measured, how was it measured, what are the units of measure, and what has been included or excluded?
Repeatability: Can the measurement be repeated, given the same definition, to get the same results?
It is equally important to clearly specify how measurement data will be obtained and stored (Table 4-9, practice 1.3). In other words, explicit specifications are made for how, where, and when the data will be collected and retained. You must ensure that appropriate mechanisms are in place to obtain measurement data from the supplier in a consistent way—for instance, how data is to be transferred from the supplier to you. It is critical for you to insist in the supplier agreement on accurate data collection by the supplier. This includes requiring the use of applicable standard report formats and tools for reporting by the supplier.
It’s also critical to clearly define in advance how the measures will be used (Table 4-9, practice 1.4). The analyses must explicitly address the documented measurement objectives, and the results of the measurement analyses must be clearly understandable by its intended audiences. Just as the need for measurement drives data analysis, clarification of analysis criteria can affect the measures in use. Specifications for some measures may be refined further based on the data analysis procedures.
The CMMI-ACQ provides specific recommendations on how to develop and sustain a measurement capability that is tied to information needs and the objectives of the project or program (see Table 4.10).
Table 4.10. Measurement and Analysis Goal 2: Practices and Tips
CMMI-ACQ Process Area: Measurement and Analysis | ||
2. Goal: Measurement results that address identified information needs and objectives are provided. | ||
Practices | Tips | |
2.1 | Obtain specified measurement data. |
|
2.2 | Analyze and interpret measurement data. | |
2.3 | Manage and store measurement data, measurement specifications, and analysis results. | |
2.4 | Report results of measurement and analysis activities to all relevant stakeholders. | |
The proof is in the pudding. You must be able to obtain specified measurement data (Table 4.10, practice 2.1). This requires the use of checks and balances to verify the completeness and integrity of acquirer and supplier measurement data. Checks can include scans for missing data, out-of-bounds data values, and unusual patterns and correlation across measures. Follow up with suppliers if data is not available or data checks indicate potential errors.
Rarely are the results of analyzing measurement data self-evident. For this reason, you use explicitly stated criteria for interpreting the results and drawing conclusions (Table 4.10, practice 2.2). Because suppliers provide important measurement data, it is paramount to discuss the results and preliminary conclusions with them. The results of planned analyses may suggest (or require) additional, unanticipated analyses. In addition, they may identify the need to refine existing measures, to calculate additional derived measures, or even to collect data for additional base measures to properly complete the planned analyses. Similarly, preparing the initial results for presentation may identify the need for additional analyses.
Storing measurement-related data enables the timely and cost-effective future use of historical data and results (Table 4.10, practice 2.3). You protect measurement data provided by the supplier according to the terms outlined in the supplier agreement. The agreement might specify that you must restrict access of a supplier’s measurement data to your employees only. Typically, you store the following measurement data:
Measurement plans
Specifications of measures
Sets of data that have been collected
Analysis reports and presentations
Retention period for data stored
Data acceptance criteria for supplier data
Data sets for derived measures can typically be recalculated and need not be stored. However, it may be appropriate to store summaries based on derived measures (e.g., charts, tables of results, or report prose). Results of interim analyses need not be stored separately if they can be efficiently reconstructed.
Results are reported in a clear and concise manner so that they are understandable, easily interpretable, and clearly tied to identified information needs and objectives. For that purpose, you establish and maintain a standard format for communicating measurement data to stakeholders, including suppliers (Table 4.10, practice 2.4).
The CMMI-ACQ provides specific recommendations on how to quantitatively manage the project’s defined process to achieve the project’s established objectives for quality and process performance (see Table 4-11).
Table 4-11. Quantitative Project Management Goal 1: Practices and Tips
CMMI-ACQ Process Area: Quantitative Project Management | ||
1. Goal: The project is quantitatively managed using quality and process-performance objectives. | ||
Practices | Tips | |
1.1 | Establish and maintain the project’s quality and process-performance objectives. |
|
1.2 | Select the subprocesses that compose the project’s defined process based on historical stability and capability data. | |
1.3 | Select the subprocesses of the project’s defined process that will be statistically managed. | |
1.4 | Monitor the project to determine whether the project’s objectives for quality and process performance will be satisfied, and identify corrective action as appropriate. | |
You establish the project’s quantitative objectives for quality and process performance based on the objectives of the organization and the project’s objectives (Table 4-11, practice 1.1). The quantitative quality and process performance objectives for the supplier are documented in the supplier agreement. You typically expect the supplier to execute its processes and apply its performance models to meet your quality performance objectives.
It’s critical for you to statistically manage those processes that are most critical to the overall process (Table 4-11, practices 1.2 and 1.3). You should pay particular attention to the subprocesses for interacting with a supplier—for example, negotiating a supplier agreement and conducting supplier reviews.
You monitor the performance of selected subprocesses, including those that involve interaction with a supplier, as well as the quality and performance of the supplier deliverables, for adherence to the quality and performance objectives (Table 4-11, practices 1.2 and 1.4). This selective monitoring provides you with insight into project and supplier performance so that you can predict the likelihood of achieving the project’s objectives for quality and process performance. You use this information to manage the risks of the project and to initiate corrective actions in time to preserve the ability to meet the project’s objectives.
The CMMI-ACQ provides specific recommendations on how to quantitatively manage the project’s defined subprocesses (see Table 4-12).
Table 4-12. Quantitative Project Management Goal 2: Practices and Tips
CMMI-ACQ Process Area: Quantitative Project Management | ||
2. Goal: The performance of selected subprocesses within the project’s defined process is statistically managed. | ||
Practices | Tips | |
2.1 | Select the measures and analytic techniques to be used in statistically managing the selected subprocesses. |
|
2.2 | Use the selected measures and analytic techniques to establish and maintain an understanding of the variation of the selected subprocesses. | |
2.3 | Monitor the performance of the selected subprocesses to determine their capability to satisfy their quality and process performance objectives, and identify corrective action as necessary. | |
2.4 | Record statistical and quality management data in the organization’s measurement repository. | |
To support quantitative project management, you need to identify common measures that support statistical management (Table 4-12, practice 2.1). For that purpose, the measure must be an adequate performance indicator of how well the subprocess performs relative to its objectives. The measure must be controllable in that you can change its values by changing how the subprocess is implemented.
To detect the cause of a particular variation, such as an unexpected change in process performance, you typically need to understand variations in process performance and have insight into potential sources of anomalous patterns (Table 4-12, practice 2.2). You monitor process performance by comparing quality and process performance objectives to the established target limits of the measure (Table 4-12, practices 2.3 and 2.4). This comparison provides an appraisal of the process capability for each measured attribute of a subprocess.
You are responsible for monitoring the progress and output of the project. Monitoring and control functions are instituted early in the project during project planning and definition of the acquisition strategy. As the acquisition unfolds, monitoring and controlling are essential to ensure that appropriate resources are being applied and that activities are progressing according to plan.
Matt: We continually face the challenge of determining how to invest in our business. There are always a variety of options you can choose from, depending on your particular strategy—from cost reduction to capacity additions to new business initiatives. Usually, there are more projects and ideas than available funds. We have to continue, redirect, or stop projects in the light of other opportunities.
We accomplish this by staying focused on our strategic goals, which are based on an understanding of what we can be best at. This improves our decision making and allows us to outperform our competitors. Without properly designed measures and reliable monitoring and control of our projects and project portfolio, we wouldn’t be able to demonstrate tangible progress or quickly terminate projects before they consume substantial resources.
After a supplier is selected and a supplier agreement is established, monitoring and control assume a twofold role. You are concerned with (1) continuing to monitor and control acquirer activities and work products while also (2) monitoring and controlling the progress and performance of the supplier’s execution under the supplier agreement and the supplier’s project plans.
Steve: In the supplier agreement, we agree to milestones and deliverables with the supplier. And then we ask for a detailed, resource-loaded WBS that gets the supplier to each of those milestones and deliverables. But we don’t track that detailed plan; instead, we have the supplier track it for us. We track the milestones for deliverables in most cases. However, we conduct detailed weekly and sometimes daily review meetings, where we jointly review progress to plan.
Matt: Can you walk us through that, Steve?
Steve: Sure. I’ll stand up in front of the group. Most of the time, this is a virtual group because the team is distributed all over the globe. So there I am on screen, with a bunch of stickers—red, yellow, and green—and we go through the critical chain of the schedule. “You said these critical activities would be completed today. Did you end today?” “The plan says you’re not supposed to be more than halfway through your resource buffer. What happened? What corrective actions are you taking?” Then based on the standard project measures, we put a sticker on each critical task. So at any given time anybody can walk up to the project schedule or retrieve it from our repository and see at one glance where there are trouble areas. So we don’t take ownership of the supplier’s detailed plan, but we make sure they execute to it and that the project is successful overall.
You use the supplier’s measurement data, reflecting its progress and output, to monitor the supplier’s progress and ensure that it achieves service levels established in the supplier agreement. This task also includes monitoring the availability of resources and the skills and knowledge possessed by the personnel provided by the supplier. In addition to monitoring the status of your own work products, you monitor the fitness of supplier deliverables by establishing and exercising stringent acceptance criteria. You can obtain additional information by analyzing the supplier’s industry research results.
Tip
Consistently manage the trend of critical project parameters through output and progress measures.
Steve: For effective project monitoring and control, you have to have your House of Measures in order. This way, you can see the whole picture and yet focus on which measure—which project parameter—is critical at a given point. So when a project team comes to see me for a review of their progress, I typically pick one measure that I focus in on.
Kristin: It’s like what Matt and his team have done with their House of Measures: “What do you need on the acquirer’s side? What do you need on the supplier’s side? Let’s both figure it out.” To avoid all confusion, we figure out what a normal weekly status chart looks like. Does it only show cost? Does it show cost and effort? Does it show risks? Does it show risk mitigation? Does it show risk trending? That’s one of the things we did together with Matt. A lot of acquirers don’t do this.
Steve confirms Kristin’s ideas.
Steve: It’s not just where you are this week, but it’s the trend. If you want to look at status reports, a lot of them are what I call “stream of consciousness.” This week, we did blah blah blah. That’s great, but were you supposed to do that during week 10 of the project? Or is that what you should have done five weeks ago or three weeks in the future? You have to have some trend to say that there’s a problem and it’s getting worse, or there’s a problem and it’s getting better.
I know I’m preaching to the choir, but a lot of suppliers don’t see that overall picture. Somebody might ask, “Are you on schedule?” Well, I don’t know. How are we tracking schedules? Have I gotten the number of deliverables done that I was supposed to get done? I could be six months into a project before I have a real deliverable. That’s a bad time to find out that we thought we were on schedule for five months and three weeks, and now we’re not.
It’s critical for any acquirer to stay focused and yet consider all relevant measures when monitoring and controlling a program or a portfolio of projects. Based on George’s experience, this isn’t always the case.
Tip
Always keep an eye on all project parameters, and collectively use them to support your decision making.
George: I tend to see more acquirers requesting and looking at percent of project on time, on budget, and sometimes customer satisfaction. Unfortunately, acquirers generally aren’t asking about quality and productivity even though these are the numbers we should be focused on. Acquirers think about a limited set of requirements: “You said it’s going to cost this amount of money. It’s going to take that much time. Just tell me that you’re on track and you’re spending my money as planned to deliver, and I’ll be happy.” If an acquirer can find a way to include quality and productivity, rework becomes visible and can be driven out of the process. Then the measures you ask about naturally improve, customer satisfaction goes up, cycle time goes down, and you can deliver within budget.
Kristin: On some medium- and longer-term contracts, I’ve seen acquirers monitor a simple form of productivity. They tend to add a cost-focused continuous improvement clause. “I want you to do fixed-price maintenance,” or, “I want you to manage my 100-person organization from an enhancement and new development and maintenance point of view.” “I want you to reduce the number of people required by 6 percent next year, 10 percent the year after, and 10 percent the year after that.” “I want you to give me a 30, 40, or 50 percent savings over a 5-year period.”
George prompts Kristin for more information.
George: Okay then, how do they monitor productivity?
Kristin: It’s based on a simple formula that considers something like the number of service requests and the number of workers: “Okay, we gave you 100 service requests this year and you completed them with 100 full-time workers. We’ll give you 100 service requests next year, and you finish them with 90 full-time workers.”
This is a start, but it doesn’t take into account the size and stability of these service requests. Most acquirers are not trying to drive size. They don’t understand the size measure. Unfortunately, this gives them a distorted view of productivity and quality.
In any event, the effective use of measures to monitor and control a project is strongly influenced by the acquirer-supplier relationship.
Tip
Continuously communicate the intent and consequences of project monitoring to acquirer and supplier teams.
Steve: The supplier has to be actively involved in monitoring and controlling the project. If not, you tend to have only limited visibility when making decisions. You run the risk of misinterpreting measures.
George: If you don’t have a good partnership in place with your suppliers, measures can even become destructive. In this situation, as a supplier we’re confronted with behaviors ranging from micro-management to the measures being ignored. It boils down to having the right relationship, the right partnership, and the level of awareness or knowledge that people have of measures.
People think that metrics are just primitives, and you should be able to provide them with data on whatever question comes to their mind. Let’s measure this, and let’s check that, and you end up with 40, 50, 60 measures that are being calculated and controlled. Realistically, you’re still not managing the relationship the right way. If a true partnership exists, excessive measuring should not be occurring. In a partnership, we set joint expectations about monitoring and controlling projects. We define an agreement showing the different measures we have to collect and how they’ll be interpreted.
If a corrective action is required to resolve a deviation from project plans, this action should be defined and tracked to closure. You take corrective action for acquirer deviations and also when supplier execution does not satisfy the supplier agreement or align with project. You may assign some corrective actions to a supplier. When you identify, for example, through your monitoring of measurement data, that supplier progress does not appear to be sufficient to meet a service level defined in the supplier agreement, then you initiate and manage corrective action for the supplier.
Steve: In a productive relationship with a supplier, you share thorny issues that happen throughout the project life cycle. You, as well as the supplier, can be perfectly open about all this, in the altruistic sense, and be able to work with the supplier and say, “Look, we’ve gotten to this stage in the life cycle and we’re having trouble. We’re not going to let you down. We’ll do these things to resolve it and go forward that way.” This doesn’t mean you go soft. If the supplier doesn’t comply appropriately with your corrective actions, then you’ll have to escalate and handle this as a supplier agreement issue or dispute.
The CMMI-ACQ provides specific recommendations about how to monitor the actual performance and progress of the project against the project plan (see Table 4-13). This monitoring begins as soon as a project plan is established. You are also responsible for monitoring the progress and output of the project as a whole, that is, your activities as well as the supplier’s project execution. You monitor the progress of the supplier, including achievement of service levels established in the supplier agreement, by using the supplier’s measurement data about its progress and output.
Table 4-13. Project Monitoring and Control Goal 1: Practices and Tips
1. Goal: Actual performance and progress of the project are monitored against the project plan. | ||
Practices | Tips | |
1.1 | Monitor the actual values of the project planning parameters against the project plan. |
|
1.2 | Monitor commitments against those identified in the project plan. | |
1.3 | Monitor risks against those identified in the project plan. | |
1.4 | Monitor the management of project data against the project plan. | |
1.5 | Monitor stakeholder involvement against the project plan. |
|
1.6 | Periodically review the project’s progress, performance, and issues. | |
1.7 | Review the accomplishments and results of the project at selected project milestones. | |
1.8 | Monitor the transition to operations and support. | |
A project’s documented plan is the basis for monitoring activities, communicating project status, and taking corrective action. You determine progress primarily by comparing project planning parameters to the estimates in the plan at prescribed milestones or control levels within the project schedule or WBS, and identifying significant deviations (Table 4-13, practice 1.1). Project planning parameters include work products and tasks; cost, effort, and schedule; and the knowledge, skills, and experience of project personnel. Attributes of the work products and tasks include size, complexity, weight, form, fit, or function. You document significant deviations that apply either to your project execution or to the supplier’s deviations from the project plan.
You also monitor overall project risk and the commitments made by relevant stakeholders to the plan (Table 4-13, practices 1.2 and 1.3). Many risks are your sole responsibility and may include sensitive information that should not be shared with the supplier (e.g., source selection, competition, internal staffing, or other risks). There can also be risks that require careful coordination with suppliers and appropriate escalation of risks and risk status (e.g., the feasibility of the technology to meet end user performance requirements). Shared risks may affect the mitigation approaches and result in jointly planned mitigations. Moreover, every acquirer needs to ensure that project data is managed against the project plan and that the level of stakeholder involvement aligns with the project plan (Table 4-13, practices 1.4 and 1.5).
It is crucial to monitor the technology solution during the operations and support phases (Table 4-13, practice 1.8). You make adequate provisions through the supplier agreement or in-house organizations to support the acquired technology solution. Typically, you use verification best practices to confirm that the organization, the physical environment, and the operations and support personnel are equipped to execute the operations and support activities.
You review operations and support organizations that have been designated to take responsibility for operation of the technology solution. You need to ensure that the workers have been identified and budgeted and are available when needed. This needs to happen very early and monitored throughout the project. The designated operations and support organizations demonstrate their readiness (capability and capacity) to accept responsibility for the product and to ensure uninterrupted support. In a typical readiness demonstration, the candidate organization executes all the activities of operations. Acquirers tend to use transition readiness criteria and verification and validation practices to determine whether the support organization meets the specified requirements. The criteria also address the readiness of the product for maintenance during the planned product life cycle.
A smooth transition to maintenance also requires monitoring to ensure that those who receive, store, use, and maintain the technology solution are trained. Typically, the supplier develops training materials for the solution it has developed. The training materials and resources to be provided by the supplier are specified in the supplier agreement and should meet the needs of various audiences (e.g., operations staff, support staff, end users). You verify that the training is provided at the appropriate times to the appropriate audiences and determine whether the training is adequate.
To monitor project performance, it is invaluable to conduct periodic progress and milestone reviews to keep stakeholders informed (Table 4-13, practices 1.6 and 1.7). These project reviews can be informal and need not be specified explicitly in the project plans. Reviews cover the results of collected and analyzed measures used for controlling the project.
You and the supplier may coordinate and conduct project reviews jointly. These reviews tend to fall into two categories: management and technical. Management reviews typically include acquirer and supplier measures, critical dependencies, and project risks and issues. Technical reviews are an important oversight tool that you can use to review and evaluate the state of the product and of the project, redirecting activity after the review if necessary.
Technical reviews typically include the following activities:
Reviewing the supplier’s technical activities and verifying that the supplier’s interpretation and implementation of the requirements are consistent with the customer’s interpretation
Ensuring that technical commitments are being met and that technical issues are being communicated and resolved in a timely manner
Obtaining technical information about the supplier’s products
Providing appropriate technical information (e.g., design constraints) and support to the supplier
As a result of project reviews, you identify and document significant issues and deviations from the plan. This includes identifying and documenting both acquirer and supplier issues and deviations. In addition to seeking ways of improving your own performance, use the results of reviews to improve the supplier’s performance and to establish and nurture long-term relationships with preferred suppliers.
Appropriate visibility enables you to take timely corrective action when performance deviates significantly from the plan (see Table 4-14, practice 2.1). A deviation is significant if, when left unresolved, it prevents the project from meeting its objectives. Managing issues and corrective actions is your sole responsibility. The documentation of this effort can include sensitive information that should not be shared with the supplier (e.g., source selection, competition, and internal staffing).
Table 4-14. Project Monitoring and Control Goal 2: Practices and Tips
CMMI-ACQ Process Area: Project Monitoring and Control | ||
2. Goal: Corrective actions are managed to closure when the project’s performance or results deviate significantly from the plan. | ||
Practices | Tips | |
2.1 | Collect and analyze the issues, and determine the corrective actions necessary to address the issues. |
|
2.2 | Take corrective action on identified issues. | |
2.3 | Manage corrective actions to closure. | |
You take decisive corrective action by determining and documenting the appropriate actions needed to address the identified issues (Table 4-14, practice 2.2). If a corrective action is required to resolve variances from project plans, this action should be defined and tracked to closure (Table 4-14, practice 2.3). You also analyze results of corrective actions to determine their effectiveness. In addition, lessons learned as a result of taking corrective action can be used as inputs to planning and risk management processes.
In addition to the project team’s monitoring and control activities, your quality assurance processes provide staff and management with objective insight into processes and associated work products (see Table 4-15). The tips for project monitoring and control apply equally to quality assurance.
Table 4-15. Product and Process Quality Assurance Goal 1 and 2: Practices and Tips
CMMI-ACQ Process Area: Product and Process Quality Assurance | ||
1. Goal: Adherence of the performed process and associated work products and services to applicable process descriptions, standards, and procedures is objectively evaluated. | ||
Practices | Tips | |
1.1 | Objectively evaluate the designated performed processes against the applicable process descriptions, standards, and procedures. |
|
1.2 | Objectively evaluate the designated work products and services against the applicable process descriptions, standards, and procedures. | |
2. Goal: Noncompliance issues are objectively tracked and communicated, and resolution is ensured. | ||
2.1 | Communicate quality issues, and ensure resolution of noncompliance issues with the staff and managers. |
|
2.2 | Establish and maintain records of the quality assurance activities. | |
You evaluate how the project team executes your processes, including interactions with suppliers. In addition, you review evaluation reports provided by suppliers to determine whether the supplier follows its processes. A popular means of doing this is to review recent CMMI maturity or capability ratings. Sufficient process quality assurance will help detect noncompliance issues, which may affect your or the supplier’s ability to successfully deliver the products to the customer as early as possible.
In the supplier agreement, you should retain the right to audit supplier processes if there is an indication that the suppliers are not following acceptable processes. You can review the results of the supplier’s quality assurance activities for selected supplier processes to ensure that the supplier is following its own processes. Typically, some supplier processes are considered critical, such as engineering or verification processes, where the supplier is required (through the supplier agreement) to follow project- or program-specified standards. In exceptional cases, you may directly perform product and process quality assurance for selected supplier processes. You and the supplier periodically share quality assurance issues and findings of mutual interest.
The practices in the Process and Product Quality Assurance process area ensure that planned processes are implemented, and the practices in the Acquisition Verification process area ensure that the specified requirements are satisfied. These two process areas may sometimes address the same work product, but from different perspectives. Projects should take advantage of this overlap to minimize duplicate efforts while taking care to maintain separate perspectives.
The technology solution is shaping up, and the supplier is getting ready to deliver the product. The customers and users are eagerly anticipating the new capability and are ready to use it. With all this anticipation in the air and the significant expenditure of resources by both you and the supplier, no project can afford to fumble this late in the game.
Successful deployment of a technology solution requires all participants to perform their defined roles. The critical components and the important aspects of your management practices must be closely scrutinized to ensure flawless execution. It is paramount to adopt a balanced approach that covers the technical readiness of the solution, its integration into the intended environment, and continued validation that the solution meets customer requirements and user expectations.
When it comes down to it, every acquisition project must be able to answer one question: How can you insert these changes—this technology solution—into its intended environment?
Steve: If you’re very change tolerant or if you’re not working with a mission-critical system, that’s one thing. When you talk about an environment where you’re going twenty-four-seven and you can never take your systems completely down, or maybe the organization just went through a traumatic reorganization, that’s another thing. At the beginning stages of planning, you really need to think through what needs to be done when you deploy your solution. If you do, you can come up with a pretty good process. You can say, “Oh, I’m going to put effort and thought into this and see how this go-live approach works for my organization. Then I can apply that approach for subsequent changes in subsequent systems.” You really want to build on the knowledge you’ve gained. You don’t throw everything out. You want to reuse the successful approaches.
A key ingredient for the successful deployment of technology solutions is its technical readiness. You want to make sure—to verify—that the supplier’s product meets the contractual requirements and is ready to be installed in the intended environment for further integration and user acceptance testing (UAT). Verification is inherently an incremental process, because it occurs throughout the acquisition. You begin by verifying the requirements and plans, and then you verify the evolving work products such as design and test results, and in the end you verify the completed product.
Kristin: Finding and fixing bugs isn’t the most glamorous part of this business, but it sure is one of the most important, if not the most important, factor that separates successful projects from failures. As personal experience and a vast literature tells us, verification—quality control—is the largest cost for many technology projects. And it takes more time than any other activity—40 percent or more of the developers’ time. We carefully balance defect prevention (such as proven design methods) and defect detection (such as testing) to get the best quality for the acquirer of our products.
It is critical that you insist contractually that your suppliers apply proven best practices for verification (e.g., structured coding techniques, peer code reviews) to increase the likelihood that the product will meet the contractual requirements.
Tip
Conduct detailed inspections, such as peer reviews, only on the most important acquirer work products.
It is equally important to find a cost-effective way to consistently and comprehensively verify your own work products and the supplier’s deliverables. Select your work products to verify based on the products’ relative importance to meeting project objectives and requirements and to addressing project risks.
Steve: Initially, we got excited about the potential savings and improved quality we could get from peer reviews. Somebody wrote something. Done. Bingo—you just earned yourself the right to a peer review. As you can imagine, this attitude slowed down the process and bloated our costs. So we took a careful look at what really matters and deserves the extra attention of a structured inspection such as a peer review. Now we only conduct peer reviews on a handful of our work products: requirements, design constraints, project plan, supplier agreement, and user acceptance test plans.
At the same time, Steve was part of an effort to select supplier deliverables for which the supplier must provide verification records such as peer review results.
As with other supplier deliverables, peer review results must meet predefined acceptance criteria. Supplier deliverables are considered delivered only when the acceptance criteria are satisfied. There is no partial credit.
Note that a product can be released in increments. In that case, it’s a good idea to timebox each release. A timebox is essentially a fixed unit of development capacity. The capability to be implemented for a release of the technology solution must fit (be delivered) within a given time frame (e.g., within six weeks) and often within a given cost to the acquirer. The work to be performed in each timebox consists of both a functionality and a quality component. Verification falls into the quality component. By predefining (fixing) the duration of a release, you can better plan for adequate verification of the delivered functionality.
Matt: We run this as an open-book test. All suppliers and our staff know what the acceptance criteria are. There is no mystery. They also know that their payment is tied to meeting those criteria. So if a deliverable has, let’s say, ten acceptance criteria, the supplier must meet all of them within a certain threshold to receive payment for this deliverable.
Testing the supplier’s product is a big part of verification.
Kristin: You need to calculate the risks you’re going to take during testing, because you can’t test everything. So having a good test plan or at least an achievable one that mitigates risk is critical. Due to the complexity and cost involved in testing, we’re always looking at how much change is feasible for us and the acquirer we work with. So you’re trying to group the change, because that minimizes or at least consolidates the areas of the solution that you need to test again.
We’ve made rules, together with acquisition organizations, about what products or product enhancements we would deploy on a monthly basis rather than on a six-month schedule. A key rule is the dependency of a product on all the other products being used by the acquirer. If a product drives many other products—let’s say, hundreds of applications—if the driver product changes, we would have to test the hundreds of applications. We don’t want to do that every month.
Does an acquirer need to test every permutation or combination of every application in the system?
Steve: We need intelligent testing, and we need an understanding of how the product will be used. Let me give you an example from a couple years back. We were doing a major upgrade. It was the biggest system in this division. And we tested the new system in parallel with the system in use for two months, and everything was perfect. We compared all the reports, everything, okay, interfaces, the whole deal. So the first night the new system went live, nothing happened.
Kristin: Nothing happened?
Steve smiles.
Steve: I mean, nothing bad happened.
Kristin: Oh, okay. Whew.
Steve: But wait—there’s more. The second night, I got a call at ten. The system had crashed. I worked all night, and we finally found out what happened. The supplier had populated the test system with data projecting only the next 24 hours of financials. As soon as we exceeded this 24-hour window in the production environment, all kinds of things started to happen—none of them pretty. In this case, a programming phenom from Russia coded for 36 hours straight to alleviate the worst of the problems.
So now we have testing standards that our suppliers must adhere to. These fairly detailed standards give, for instance, very clear direction about what length of time the testing data must cover, depending on the process a product supports.
Because the supplier deliverables go through different stages of testing, it is critical that you clearly designate which testing environment is expected for each type of testing.
Tip
Contractually define the required testing environments and the stages of testing they must be used for.
Matt: When we first sat down with our various acquisition teams to discuss testing, we got into a heated debate. Some groups argued for the right to buy equipment to stand up to their own test environments that they and the suppliers would have to use. Other people wanted us to hire an independent testing outfit to eliminate bias, and yet others wanted the suppliers to be responsible for all testing environments since they’re responsible for providing the product. I favor the last option, simply because it ensures clear accountability of the suppliers.
Matt pauses before describing how this works.
Matt: For instance, in the IT area we make the hosting supplier responsible for operating the preproduction environment that the development supplier uses for user acceptance testing. The preproduction environment is a mirror of the intended environment that we use to verify and validate the product prior to deployment.
For hardware we have a certification process. For example, any generic hardware we get, the suppliers know that they can expect to run such and such software, at a minimum. So we try to push onto them a lot of the testing responsibility for the integration of their product with other suppliers’ products and services in our environment. It’s their product. They’re driving it. Suppliers play a critical role in ensuring that the technology solution is ready for deployment.
Steve: We involve suppliers very heavily when we’re making decisions about the readiness of technical solutions and how we measure it. For example, with software, you can count on a few things for sure: The code always has defects. Our suppliers use agreed-upon categories to group these defects. They group them in terms of when they’re going to be fixed and realigned with our deployment dates. We have regular calls with our developer suppliers and with the deployment people as well as all the other relevant stakeholders.
Steve pauses to consult his notes.
Steve: So besides our standard measures, we use readiness dashboards to give everybody a consistent view of whether the solution is ready for prime time.
Matt: I like the dashboard format.
Steve: They’re really useful. They display a collection of metrics and key performance indicators that show the status of the project and where it’s headed. They give people actionable data in an intuitive and insightful format.
So we review those dashboards at all levels of the organization. Say we have a specific site where the acquired product will be used. One critical area might be, “Do you have your change controls approved?” We even ask if they have their change controls submitted. “Have you communicated the timing to your suppliers? Do you have your user acceptance tests and events defined?” We try to have yes/no questions, or questions that call for numbers.
For the high-performing suppliers, it’s basically just a formality. They know what they need to do. For them, it’s more of a last chance to offer up information or concerns. We want to make sure we agree on the code and what we’re getting in the code, make sure it gives us the functionality we need.
The CMMI-ACQ provides specific recommendations about how to ensure that an acquired product, intermediate acquirer work products, and supplier deliverables meet their contractual requirements (see Table 4-16). The Acquisition Verification process area includes selection, inspection, testing, analysis, and demonstration of acquirer work products and supplier deliverables.
Table 4-16. Acquisition Verification Goal 1: Practices and Tips
CMMI-ACQ Process Area: Acquisition Verification | ||
1. Goal: Preparation for verification is conducted. | ||
Practices | Tips | |
1.1 | Select the work products to be verified and the verification methods that will be used for each. |
|
1.2 | Establish and maintain the environment needed to support verification. | |
1.3 | Establish and maintain verification procedures and criteria for the selected work products. | |
Up-front preparation ensures that verification provisions are embedded in the contractual requirements, constraints, plans, budgets, and schedules. Preparation also entails defining support tools, test equipment and software, simulations, prototypes, and facilities.
You select work products to verify based on the products’ relative importance to meeting project objectives and requirements, and to addressing project risks (Table 4-16, practice 1.1). You also select supplier deliverables for which the supplier must provide verification records. The required methods and criteria are described in the supplier agreement. Typical acquirer verification activities include reviewing the solicitation package, supplier agreements, plans, requirements, documents, and design constraints.
In addition to selecting work products for verification, you select the verification methods. This typically begins with the definition of contractual requirements to ensure that the requirements are verifiable. The methods should address reverification to ensure that rework does not cause defects. Suppliers should be involved in your selection process to ensure that the project’s methods are appropriate for the supplier’s environment. To set clear expectations, you establish in the supplier agreement requirements for verification of supplier deliverables. The supplier agreement typically includes the following:
A list of deliverables and other work products that must be verified by the supplier
Applicable standards, procedures, methods, and tools
Criteria for verification of supplier work products
Measurements to be collected and provided by the supplier with regard to verification activities
Reviews of supplier verification results and corrective actions
You must establish an environment to enable verification (Table 4-16, practice 1.2). This environment can be acquired, developed, reused, modified, or a combination of these, depending on the needs of the project. The type of environment depends on the work products selected for verification and the methods applied. The requirements for the environment can vary greatly. For instance, a peer review might require little more than a package of materials, some reviewers, and a room. In contrast, a product verification test might require simulators, emulators, scenario generators, data reduction tools, environmental controls, and interfaces with other systems.
Verification criteria are defined in the supplier agreement to ensure that the work products meet their requirements (Table 4-16, practice 1.3). You generate a set of comprehensive, integrated verification procedures for work products and any COTS products as necessary.
You use the verification methods, procedures, and criteria in the appropriate verification environment to verify the selected work products and any associated maintenance, training, and support services. It’s good to verify acquired products and work products incrementally, because it promotes early detection of problems and can result in the early removal of defects (see Table 4-17, practice 2.1). Incorporating the results of verification into a repair process can save considerable cost for fault isolation and rework.
Table 4-17. Acquisition Verification Goal 2: Practices and Tips
CMMI-ACQ Process Area: Acquisition Verification | ||
2. Goal: Selected work products are verified against their contractual requirements. | ||
Practices | Tips | |
2.1 | Perform verification on the selected work products. |
|
2.2 | Analyze the results of all verification activities. |
|
You must compare actual verification results to established verification criteria to determine whether the results are acceptable (Table 4-17, practice 2.2). For each work product, all available verification results are incrementally analyzed and corrective actions are initiated to ensure that the documented requirements are met for both acquirer and supplier. Corrective actions are typically integrated into project monitoring activities. Because a peer review is one of several verification methods, you should include peer review data in this analysis to ensure that the verification results are analyzed sufficiently. Analysis reports or “as-run” method documentation can indicate that bad results are being caused by problems with the verification methods, verification criteria, or verification environment.
The CMMI-ACQ includes the process area Causal Analysis and Resolution. This process area provides recommendations for identifying the causes of defects and other problems and taking action to prevent them from occurring in the future. When determining which defects to analyze further, you should consider the impact of the defects, the frequency of occurrence, the similarity between defects, the cost of analysis, the time and resources needed to correct the defects, the safety considerations, and so on. Causal analysis is performed by people who have the best understanding of the selected defect or problem being studied.
Before the technology solution goes live and is available to the users, the project team needs to make sure that all involved parties are on the same page. For this, communication throughout the project is critical.
Steve: All the way through a project, you want to take every opportunity you can to validate with the customer and supplier that you’re on track. But with all the preparation, it still comes down to the successful launch and full deployment of the new capability. Your customer satisfaction, a large chunk of your supplier’s payment, and your professional ego are wrapped up in the pivotal events around going live with your product. It’s like you’ve gone through all the rehearsals, and now it’s time to perform.
Consistently delivering a successful premiere—seamlessly inserting new or enhanced technology solutions into your environment—is not without its perils. For instance, you don’t want your project to be the one in which UAT came to mean “user angry at technology” instead of “user acceptance testing.”
George: Surprises during user acceptance testing aren’t pretty. Let me tell you a story. It was in our validation lab for one of our largest automotive clients. We had pushbuttons, industrial controllers, and screens mounted on a table instead of being mounted on a fork truck. The pushbutton and the screen are about three meters apart—the user can walk between the two just like they would in their work environment. So my team tested the system. They’d push the button and then they’d walk over to the screen to see if, for instance, a material request would show up. Then they’d clear the material request, walk back over to the pushbutton, push it again, get another material request, walk over to the screen, and so on and so forth. No problems.
So in comes the user, a woman from one of the customer’s sites. She pushes the button, walks over to the screen, sees that the message came through, clears the screen, walks back to the button, and then hammers it mercilessly—bang, bang, bang, bang, bang—just as fast as she can. The button gives. It breaks. There’s nothing coming through on the screen anymore, the light starts flashing, basically “smoke” comes out of the system.
And my guy says to her, “What did you do that for? Who would ever do something like that?” And she says, “That’s going to happen. Someone’s going to get frustrated, the trucks aren’t going to come, so someone is just going to start hammering this button.”
My guys had never tested this situation, which was very embarrassing for me. Within ten minutes the user could come in and break the system. It’s probably one of the worst UAT stories I could tell. It took us a while to live that one down.
Unfortunately, these UAT surprises are common. Steve adds his favorite one.
Steve: Before I started here, I worked for a cement factory. My team went through this elaborate, sophisticated effort to create a new system to monitor the ingredients to make the best cement there is. They were so confident that this would turn out to be a home run.
So when they had the great unveiling in the cement factory, the first worker that walked up to the system—the system had a fancy touch screen—tries to start the ingredient analysis. But he can’t use the touch screen! How come? Because a safety regulation requires all workers to wear big gloves—think giant oven mitts. He couldn’t manage to hit even one button on the touch screen. And of course, using the touch screen was the only way a user could steer the system.
A key ingredient for successful validation of an acquired product is to have the true customer and users involved throughout the project life cycle. This is especially challenging on projects that have long life cycles.
Tip
Define skill and capability profiles of the users who will participate in user acceptance testing.
George: You need one kind of user, and that’s the right kind. But what happens a lot of times in UAT, the acquisition team or their management might say, “Oh, that’s seven months from now. I don’t know who’ll be available in seven months.” So the acquirer’s side doesn’t plan who to send to UAT because they don’t know what else they’re going to do. So, the week before UAT comes around, and they look around and they say, “Hey, John. You and Susie standing by the water cooler, you’re going to UAT next week.”
Steve: Well, I’ve never done that, but I can see how it happens.
George: It never needs to happen. You write up a profile that captures the agreed-upon skills and capabilities of a potential test user. Okay? You can figure out, do they meet that profile, before folks are asked to participate in UAT. Otherwise, if you’re doing UAT that requires domain knowledge—and in my experience, many products require this for successful UAT—you get inaccurate feedback without the right users, and you’ll spend a lot of money before you get it right.
George pauses for a moment and then continues.
George: Let’s say you’re validating a technology solution for the product development group. You’re building something that supports structural engineering. You couldn’t just send a random person who didn’t know anything about this area, or knew enough about it but didn’t understand that 4,000 metric tons per square inch is a bad answer for the force it takes to open a door.
So, when you find out that the UAT users you have don’t fit the profile, you’re stuck. You’re looking at them and you have to say, “You’re the wrong person for this assignment,” which of course is insulting. So they push back: “Well, I work in this group, I know how the work gets done in this group.” Well, they do, but they don’t know this specific piece. So how can they help us validate the proposed solution if they don’t know the work it will support?
So this is the biggest lesson learned. Ultimately you have to get the right people in the room or in the field to spend the time giving you meaningful feedback.
What can you do to avoid UAT surprises and increase your chances for a smooth go-live of the technology solution? It’s vital to have a time-tested, proactive set of verification procedures and criteria to ensure that the product or component will fulfill its intended use when placed in its intended environment. You need to clearly identify the applicable verification procedures and criteria and then reference these procedures in the solicitation package and supplier agreement.
George: What we’ve created is essentially a manufacturing process for deploying technology solutions. We want to make sure we go live with a solution and live to tell about it. While we want to instill creativity when designing and developing the solution, we encourage all participants to rigorously stay within the deployment script. Everybody must know their roles and perform according to procedure. So even if you find things during deployment that will make the solution a little bit better, you have to be really careful about whether you’ll change the deployment process to make an adjustment. Feature creep is bad enough, but during deployment it’s downright dangerous.
Paula: You’re so right. I can’t tell you how many times we find errors in last-minute tweaking.
George: Now we’re at a point where our deployment process is getting to be almost like how some automotive companies launch a new vehicle: Engineering will evolve the design, and then finally the design is ready for production. When they bring it to a manufacturing plant, the design is done. It’s been tested, and we know it works. Then, we’ll take a vehicle down the manufacturing line to go through the manufacturing process one last time just to verify that the new model will build properly and that our process works. So, eventually, deployment of technology solutions is like a vehicle launch, in that we pilot the technology solution to verify that the build process works and that the deployment process works. At that point we can confidently say that we can do the deployment process over and over again. Standardizing becomes even more important, since we’ve got multiple teams, dispersed globally, deploying the same system.
Steve strongly supports George’s ideas.
Steve: A tightly controlled deployment process is critical. We’re better off doing a staging operation rather than doing an “out of the box” installation at the customer’s site. What we do is, we source all the materials, we take it to an assembly site, rack all the hardware components, load the software, do some elementary testing. Then we’ll wire it all up and connect it to the power and network at the site. This focuses the site team on two items. One, all they have to set up are those pieces we couldn’t preassemble. Two, they can pay close attention to how to migrate from the old product to the new one.
George: That sounds like a great plan.
Steve: I think it’s one of the cleverest things we’ve come up with in a long time. We used to see the same mistakes over and over again, but the common denominator was somebody new was doing something not in the process. So we want to try to have as much repetitive stability as possible.
The closer you get to going live with the new or enhanced product, the more important it is to train the potential users and support personnel to use it. Effective training requires assessment of needs, planning, instructional design, and appropriate training media (e.g., workbooks, software) as well as a repository of training process data. As an organizational process, training has these main components: a managed training development program, documented plans, personnel with appropriate mastery of specific disciplines and other areas of knowledge, and mechanisms for measuring the effectiveness of the training.
Paula: At minimum, we want people to be able to do their jobs without disruption on the day the technology solution goes live. One thing about training is that our primary motto, and we’re fairly rigorous on this, is that during development the supplier creates the training package. It’s tested as part of development and verification of the solution.
George: It sounds like you’ve done a lot with training.
Paula: We’ve used different kinds of training, everything from one-on-one training, on-the-job training, classroom training, multimedia training, and more. We now use a lot of Web-based training. We try to have this in place a short time before go-live so that the users are ready on day one. But then again, sometimes we may supplement that with face-to-face sessions where we call the people in and walk them through the latest changes in detail. This has the advantage of allowing for a dialog between the instructor and the users. Then there are a significant number of technology solutions that we’ve got where the business process changes so that the user training is actually embedded in some process retraining.
When the big go-live day finally arrives, acquirers can only hope that the process plays out like the Vienna Philharmonic performing Strauss at New Year’s—breathtaking, flawless, and smiles on everyone’s faces when it’s finished.
Tip
Open mandatory communication channels for all stakeholders during go-live of the technology solution.
George: Once we start the countdown to go-live, we have a whole process detailed to carry it out. Before we go live, we collect all the information; we have very detailed cut-over plans—minute by minute—that we have done in exhaustive detail and reviewed. So a great deal of work goes into that. Part of it is to make everything very visible.
Steve: Tell us more.
George: So, we have an intense focus on the communication. It’s all about communication. It really is critical—communication of the right things at the right time. Where are the key checkpoints? Where will what testing be done? All this and more, to make sure the deployment is moving as expected. One of the problems I have with people is when they say, “Well, I’m going to use the new solution for 24 hours, and then I’ll find out if things are okay or not.” And you just don’t want to do that. You want to be able to verify and validate that things are working as you expected along the way.
Steve: So what’s in place on the day itself?
George: We have all the various players, every supplier that is involved, their technical personnel, available for immediate contact—if they don’t have to be on-site already—and then a senior management person who can be contacted in the middle of the night if anything is needed from their company. Then when we actually start the system, we give an update on an open phone line every hour. People can just call in and ask questions or listen to the hourly update. At a point in time in the deployment we say, “Is everything ready? Do we turn the final switch?” There is a meeting, and that’s when you get a whole group of people together for that final decision to go live.
Tip
Contractually establish that any significant error found during warranty causes the warranty period to start over.
With the technology solution ready for use, you transfer responsibility for operations and support from the development supplier to the appropriate group. This could be the same supplier or an in-house team on your side. The development supplier, however, is still very much responsible for successfully completing the warranty period for the technology solution. Steve stresses the importance of the warranty period.
Steve: In my experience, with so many different components working together, so many pieces and parts, the warranty period is a lot more important than it used to be. There are so many things that can go wrong. It’s not cost-effective for the supplier to test to the degree that you would have to in order to prevent anything from happening after the solution is installed. So I think the warranty is really important. You hopefully don’t have any major errors or outages, but it’s always possible. If something happens, we hold our suppliers accountable. They’re contractually required to fix any errors that occur during their warranty period. We also insist that any significant error found resets the warranty period, among other penalties. So it’s in our mutual interest to arrive at a high-quality product quickly.
After the warranty period is complete and the responsibility for the technology solution is transferred to the operational and support organizations, you review and analyze the results of the transition activities and determine whether any corrective actions must be completed before closing the project.
The CMMI-ACQ provides specific recommendations on how to demonstrate that an acquired product or service fulfills its intended use when placed in its intended environment (see Table 4-18). Validation demonstrates that the acquired product, as provided, will fulfill its intended use. In other words, validation ensures that the product meets the stakeholders’ intentions and the customer requirements.
Table 4-18. Acquisition Validation Solution Goal 1: Practices and Tips
CMMI-ACQ Process Area: Acquisition Validation | ||
1. Goal: Preparation for validation is conducted. | ||
Practices | Tips | |
1.1 | Select products or services to be validated and the validation methods that will be used for each. |
|
1.2 | Establish and maintain the environment needed to support validation. | |
1.3 | Establish and maintain procedures and criteria for validation. | |
Preparation activities include selecting products and components for validation and establishing and maintaining the validation environment, procedures, and criteria. Products or services are selected for validation on the basis of their importance to stakeholder intentions and customer requirements (Table 4-18, practice 1.1). The items selected for validation may include only the acquired product or may include appropriate levels of the product components that are used by the supplier to build the product. Any product or component—including replacement, maintenance, and training products, to name a few—may be subject to validation.
You should select validation methods early in the project life cycle so that they are clearly understood and agreed to by the relevant stakeholders. Validation methods include the following:
Discussions with the users, perhaps in the context of a formal review
Prototype demonstrations
Functional demonstrations (e.g., system, hardware units, software, service documentation, user interfaces)
Pilots of training materials
Acceptance tests of products and components by end users and other relevant stakeholders
The supplier agreement should capture your expectations of suppliers for participation in validation of the product and components. The requirements for the validation environment are driven by the product or service selected, by the kind of work products being tested (e.g., design, prototype, final version), and by the methods of validation being used (Table 4-18, practice 1.2). The environment may be purchased or may be specified, designed, and built. The environments used for verification and for validation may be considered concurrently to reduce cost and improve efficiency or productivity.
You define validation procedures and criteria to ensure that the product or component fulfills its intended use when used in its intended environment (Table 4-18, practice 1.3). The validation procedures and criteria include validation of maintenance, training, and support services. They also address validation of requirements and the acquired product or service throughout the project life cycle. Typically, you establish formal user acceptance testing procedures and criteria to ensure that the delivered product meets stakeholder intentions before it is deployed in the intended environment. The validation procedures and criteria applicable to the supplier are typically referenced in the solicitation package and supplier agreement.
Validation activities are performed early and incrementally throughout the project life cycle (see Table 4-19, practice 2.1). They can be applied to all aspects of the product in any of its intended environments, such as operation, training, manufacturing, maintenance, and support.
Table 4-19. Acquisition Validation Solution Goal 2: Practices and Tips
CMMI-ACQ Process Area: Acquisition Validation | ||
2. Goal: The products or services are validated to ensure that they are suitable for use in their intended environment. | ||
Practices | Tips | |
2.1 | Perform validation on the selected products or services. |
|
2.2 | Analyze the results of the validation activities. | |
The data resulting from validation tests, inspections, demonstrations, or evaluations are analyzed against the defined validation criteria (Table 4-19, practice 2.2). Analysis reports should indicate whether the stakeholders’ intentions were met; if there are deficiencies, these reports document the degree of success or failure and categorize probable causes of failures. You compare the collected test, inspection, or review results with established acceptance criteria to determine whether to proceed or to address requirements or design issues in the requirements development or technical solution processes. Analysis reports or “as-run” method documentation can indicate that bad validation results are being caused by validation method problems, validation criteria problems, or validation environment problems.
Often, acceptance of supplier deliverables is tied to supplier payments. You must ensure that payment terms defined in the supplier agreement are met and that supplier compensation is linked to supplier progress, as defined in the supplier agreement (see Table 4-20, practice 2.1). You should not make final payment to the supplier until you have certified that all the supplier deliverables meet the contractual requirements and that all acceptance criteria are satisfied. When you encounter nonperformance, exercise the contract provisions for withholding or reducing payments to the supplier to the appropriate degree.
Table 4-20. Acquisition Management Solution Goal 2: Practices and Tips
2. Goal: Establish a productive and cooperative environment to meet the goals of the project. | ||
Practices | Tips | |
2.1 | Receive, review, approve, and remit invoices provided by the supplier. |
|
2.2 | Ensure that the supplier agreement is satisfied before accepting the acquired product. | |
2.3 | Transition the acquired product from the supplier to the acquirer. | |
You ensure that all acceptance criteria are satisfied and that all discrepancies are corrected before final acceptance of the acquired technology solution (Table 4-20, practice 2.2).
Your authorized representative assumes ownership of existing identified supplier products or deliverables tendered, or approves specific services rendered, as partial or complete performance of the supplier agreement by the supplier. You, usually through your authorized supplier agreement or contract administrator, provide the supplier with formal written notice that the supplier deliverables have been accepted or rejected.
Typically, the supplier integrates and packages the products and prepares for the transition to operations and support, including support for business user acceptance, and you oversee the supplier’s activities (Table 4-20, practice 2.3). These expectations and the acceptance criteria for transition to operations and support are included in the solicitation package and the supplier agreement.
After appropriate reviews of the transition activities, you make the product available for use according to the plans for pilot and transition. During this pilot, or initial period of production, you validate that the product is capable and ready for full operational use. During this defined transition or warranty period—for example, 30 days or 90 days for certain information systems—you oversee activities to make sure that the product is operating as planned and identify any corrective actions required. Although the product is in the operational environment, full responsibility for operations and support is not transitioned until this pilot period is complete and any identified corrective actions have been successfully completed. During this defined transition period, you ensure support of the product (for example, you may assign the supplier the responsibility to maintain support during transition).
Responsibility for operations and support of the technology solution is transferred by you to the operations and support organizations, which may be suppliers, only after these organizations demonstrate their capability and capacity to support the product and accept the responsibilities to perform their assigned operations and support processes. You ensure that these organizations understand post-transition service requirements from the supplier.
You maintain oversight responsibilities until the transition activities are complete and the transfer of responsibility for operations and support of the product has been accepted. This includes oversight of any supplier activities, based on the supplier agreement, for the execution of the transition of the product to operations and support.
After the transition is complete and the responsibility is transferred to the operational and support organizations (e.g., at the end of the warranty period for a software product), you review and analyze the results of the transition activities and determine whether any corrective actions (such as process improvement) must be completed before close.
One of the biggest challenges that acquirers face is to successfully collaborate with suppliers throughout the entire acquisition, including the development of design constraints for the project or program. There is a tendency to develop these constraints in a vacuum and make critical assumptions about the availability of certain technologies, COTS or otherwise, or about the suppliers’ processes; the result is a disjointed, slow delivery process that wastes valuable time and resources in rework.
If you haven’t included suppliers in the development process, then having design constraints that are set in stone and enforced by an ironclad supplier agreement isn’t a step toward success. On the contrary, the gap between the acquirer’s and the supplier’s plans and processes becomes a chasm. There’s a saying: “Work smarter, not harder.” If you don’t integrate and manage processes with suppliers, you’re working hard but not working smart.
Achieving integrated project management requires bringing your design choices into conformance with the supplier’s delivery capabilities. After all, one of the main benefits of outsourcing is to leverage the capabilities of the supplier; if you don’t align supplier capabilities with the project, you can never realize this benefit. Integrated project management also focuses on bringing the supplier’s process capabilities into conformance with your design constraints early in the system delivery process, so that the two can influence and shape one another in a timely fashion.
Note, however, that neither acquirers nor suppliers need to develop their processes from scratch in order to achieve alignment. Each organization can tailor existing, standard processes to meet the needs of the specific project. This collaboration effort also goes a long way toward establishing in-depth, long-term relationships with suppliers.
Aligning processes is a good start, but even more is required of acquirers and suppliers that want to integrate their work. Each must walk a mile in the other’s shoes. You must understand the supplier’s perspective on issues such as manufacturability, and suppliers need to comprehend your point of view on performance, total cost of ownership, and the environment in which the product is to be deployed.
Depending on the scope and potential risk of the project, the collaboration effort can be significant. Integration across functions and with suppliers requires that you execute specific activities to support cross-functional work. For example, suppliers build very early system prototypes and test and evaluate them in order to support your desire to develop deeper customer insight early in the process. Similarly, you and your suppliers interact with customers to strengthen and deepen their understanding of the capabilities the product will deliver. The supplier aligns its system delivery processes early in the project and tailors and develops its processes in collaboration with you. In the midst of all this activity, the integrated plan and supplier agreement keeps everyone on the same page and establishes clear roles and accountability for executing the project.
In addition to important documents like the supplier agreement, you need to track, update, and manage other significant artifacts during the acquisition life cycle in order to maintain the integrity of work products and the resulting solution. The act of planning for configuration management requires both you and the supplier to focus on separating the wheat from the chaff. In other words, acquirers and suppliers together must clearly identify the important artifacts to keep and those that are disposable. Not only that, but planning for configuration management includes defining who is responsible for controlling relevant project artifacts and the means by which they will be stored and made accessible for reuse.
Another important consideration is ensuring that the artifacts are formatted using a lowest common denominator so that they are accessible and usable by the acquiring and supplying organizations and any other third parties. Obviously, it is critical to preserve artifacts such as requirements specifications, release plans, detailed designs, acceptance tests, and test results, but if you don’t maintain a tight focus on what’s important the list of items to be managed could grow exponentially, especially if the project is large and complex. Another goal of planning for configuration management, therefore, is to designate only the minimum number of configuration items necessary to sustain a technical solution in the intended environment. This results, hopefully, in a well-defined list of acquirer work products and supplier deliverables to be managed. Minimizing configuration items is a crucial task, because the cost of maintenance and the number of handoffs between organizations can result in spending a large, unexpected chunk of the program budget.
Planning for configuration management head-on is essential, as is facing the risks inherent in every project. Successful acquirers take a rational approach toward managing risk. The biggest business and technical risk is that the solution will not meet the needs of stakeholders. You also assume the risks generated by the relationships that you establish with suppliers. For example, if a supplier is not financially stable or if it does not have strong processes in place to resolve issues, then issues that arise can be detrimental to the acquisition.
When it comes to managing risk, you have a difficult job because most of your risks are business-oriented, not technical. Technical risk is largely governed by science, whereas business risk can be driven by a myriad of internal and external forces, many of which are outside your control. This doesn’t mean, however, that technical risks should be assigned lower criticality. It is important for all risks to be clearly identified, documented, prioritized, and made visible to the appropriate decision makers and stakeholders.
This is often easier said than done, especially in organizational cultures that do not emphasize the reporting of risks or the routing of information to relevant personnel. A stagnant risk management database is a telltale sign that an organization is not attempting to reconcile conflicting risks or to mitigate risks. Risk scorecards and periodic risk assessments are only some of the tools that you can use to ensure that you are staying the course toward risk mitigation.
When it comes to metrics, counting the right things is always better than counting the wrong things or counting just for the sake of counting. Having too many metrics obscures the truly important information and drains both acquirer and supplier teams, who are left to try to generate and interpret the results. To determine which measures are the right ones, you must be able to trace the measurement back to a business or program goal. If the metric doesn’t show progress within the project, program, or organization or reveal the outcome of a specific action, then it lacks value and is raising costs and cutting into the profits offered by outsourcing.
Without metrics or a baseline, an acquisition cannot be managed. Taking no measurements or not having a baseline is akin to people who say, “I’m watching my weight, but I’m not keeping track of how much food I eat or how many calories I burn by exercising.” These dieters will never know whether their efforts were successful until they step on the scale—if indeed they even know what their weight was before they started “watching.” To manage projects, you use supplier-reported measures in addition to your own measures of progress and output. Supplier measures give you the information you need to meet measurement objectives and to assess the project’s progress and output. The supplier agreement defines the measures the supplier must report on, including definitions and sample reports. The task of gathering data from a supplier can be coupled with regular interim reviews of supplier work.
After you have defined the measures, selected a supplier, and let the supplier agreement, you focus on monitoring and controlling the progress of the acquisition on both your side and the supplier’s. It is essential to ensure that resources are applied effectively and that the project moves forward according to plan. In addition to tracking the supplier’s progress, you ensure that the deliverables align with the acceptance criteria you have established. When a project plan goes awry or when a deliverable isn’t up to snuff, sometimes corrective action is required. As with any deviation or changes from the original plan, changes in course must be clearly defined and tracked to closure. Again, the onus is on you to initiate corrective actions for deviations from both your and the supplier’s plans, as is ensuring that issues are resolved.
Both you and the supplier verify deliverables produced by the supplier. The supplier must verify that the product will function in the intended environment, that it is of the specified quality, and that it meets the criteria set forth in the supplier agreement; you must also verify these things. Because you seldom have insight into the low-level technical details of how a system is built or how software code is written, it is important that you find a cost-effective, intelligent way to test supplier deliverables before deployment. This is especially important with mission-critical systems or those that fill a safety or defense purpose where human lives are on the line. It is vital that you have a tested set of processes and criteria to ensure that the deliverable fulfills its specification when deployed in its intended environment. These verification procedures and criteria should be identified and referenced in the solicitation package and supplier agreement.
The processes are in place, the technology developed, and now it’s time to again focus on the people in this equation. It’s vital to ensure that personnel are trained to operate the new product. A system that isn’t used as intended diminishes in value proportionately to the time and effort that were put into development of the unused or unusable features. Or perhaps new, timesaving features are not known to users, who continue to do things the old way. Training is especially important for those systems that involve the safety and security of human life.
In this chapter, we focused primarily on how acquirers and suppliers must work as integrated teams, handling important project assets under configuration management, managing and mitigating risk, measuring for success, and deploying a technical solution. In Chapter 5, we discuss how you can foster and build a culture in which personnel strive to accelerate process improvement efforts.