Chapter 7. Evading Security Measures
This chapter covers the following CEH exam objectives:
• Understand how IDS/IPS work
• Articulate methods for evading IDS/IPS
• Identify classifications of firewalls
• Be able to describe methods to circumvent firewalls
• Comprehend honeypots
• Explain VPNs
Intrusion Detection Systems
Evading security measures might seem like a rather odd thing for an ethical hacker/penetration tester to do. Nevertheless, it is an essential part of a penetration test. Hopefully, the security mechanisms in place are all properly configured and robust, thus preventing you from evading them. However, if they are not, it would be much better for you to find and fix these identified issues than for a malicious hacker to find them.
Types of IDSs
IDSs (intrusion detection systems) are now an integral part of cybersecurity. They are a common defensive technology. Basically, an IDS inspects all inbound and outbound activity on a particular machine or network. The IDS is looking at particular factors to determine if there are likely intrusion attempts. The way an IDS works is primarily with one of the following methodologies or a combination thereof:
• Signature matching: An IDS typically has a set of signatures of known attacks. The IDS scans traffic, seeking to see if any of those signatures exist. This approach yields very few, if any, false positives and false negatives; however, it will miss any attack that is not in its signature matching database. An IDS can have four possible responses in signature matching:
• True positive: The system has deemed some traffic as an intrusion, and it is indeed an intrusion indicator.
• False positive: The system has deemed some traffic is an intrusion, but it is not really an intrusion.
• True negative: The system has deemed the traffic not an intrusion but rather normal traffic–and this is correct.
• False negative: The system has deemed the traffic not an intrusion, but it really is. The system is wrong.
• Anomaly detection: This approach looks for behavior that is outside the expected bounds of normal behavior—for example, excessive data transfer, odd hours of activity, or any other anomalous activity. This approach can catch new attacks and attacks that are not in any signature database. However, it also yields false positives and false negatives.
• Protocol anomaly detection: In this approach, models are constructed to explore anomalies in the way vendors deploy the TCP/IP specification.
There are several categories of anomalies. File system anomalies can include new unexplained files, unexplained changes in file size, and unexplained changes in file permissions. Network anomalies can include sudden changes in network logs, repeated login attempts, and connections from unexplained locations. System anomalies can include missing logs, slow system performance, and modifications to system software and/or configuration files.
IDSs can be classified in several ways. One way is host-based versus network-based IDSs. A host-based IDS (HIDS) is used to protect a single host/computer. A network-based IDS (NIDS) is used to protect an entire network or network segment. The issue of how to detect possible attacks is the same with HIDSs and NIDSs. A more pertinent differentiating classification is passive versus active IDSs. Those are described in the following subsection.
Passive IDSs
A passive IDS monitors suspicious activity and logs it. It does not take any action to block the suspicious traffic. In some cases, an IDS may notify the administrator of the activity in question. This is the most basic type of IDS. Any modern system should have, at a minimum, a passive IDS along with the firewall, antivirus, and other basic security measures. This is a layered, or defense-in-depth, approach.
Active IDSs
An active IDS, also called an IPS (intrusion prevention system), logs suspicious traffic, and it also takes the additional step of shutting down the suspect communication. Some people contend that passive IDSs are no longer useful. That is not correct. An IDS can have false positives and false negatives, as discussed earlier in this chapter in regard to anomaly detection. A false positive would lead to legitimate traffic being blocked.
Deciding between active and passive IDSs requires risk analysis. Is it a greater risk to accidentally block legitimate traffic (false positive) or to possibly allow an attack (false negative).
Snort
A number of vendors supply IDSs, and each of them has unique strengths and weaknesses. Which system is best for your environment depends on many factors, including the network environment, the security level required, budget constraints, and the skill level of the person who will be working directly with the IDS. One popular open-source IDS is Snort, which can be downloaded for free from www.snort.org.
Snort is emphasized on the CEH exam. It is a command line tool. Table 7.1 lists some of the commonly used Snort commands.
Table 7.1 Commonly Used Snort Commands

A Snort installation screen is shown in Figure 7.1.
Figure 7.1 Snort Installation: Choose Components Screen
The basic execution of Snort is shown in Figure 7.2.
Figure 7.2 Executing Snort
Much Snort usage involves configuring Snort and including rules. Fortunately, Snort has a complete manual available online, at http://manual-snort-org.s3-website-us-east-1.amazonaws.com.
The CEH exam won’t ask you to create Snort rules, but you must have a general understanding of these rules. Basic guidelines for creating Snort rules are:
• Snort's rule engine enables custom rules to meet the needs of the network.
• A single snort rule must be contained on a single line as the Snort rule parser does not handle rules on multiple lines.
• A Snort rule has two logical parts:
• Rule header: Identifies the rule’s actions (i.e., what to do), such as alerts, log, pass, activate, dynamic, etc.
• Rule options: Identifies the rule’s alert messages.
A sample rule is shown in Figure 7.3.
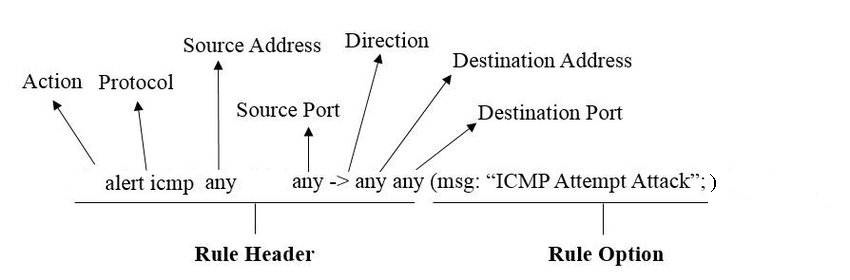
Figure 7.3 Sample Snort Rule
When creating Snort rules, you can take three actions:
• Alert: Generate an alert and then log the packet.
• Log: Log the packet/item.
• Pass: Just drop/ignore the packet.
There are three protocols available for Snort to analyze:
• TCP
• UDP
• ICMP
Snort rules also can use a direction operator. For example, the <> in Figure 7.3 means bidirectional. You can also list port numbers or even any port. Consider the following examples:
• Log TCP any any -> 192.168.1.0/24 :1024: Log TCP traffic from any port going to ports less than or equal to 1024.
• Log TCP any any -> 192.168.1.0/24 1:1024: Log TCP traffic coming from any port and destination ports ranging from 1 to 1024.
While Snort is a command line tool, and the CEH exam will focus on the command line, there have been a number of third-party graphical user interfaces (GUI) developed for Snort. A few of the most popular GUIs are listed here:
• Snowl: https://snowl.io
• Placid: http://www.gnu.msn.by/directory/All_Packages_in_Directory/Placid.html
• Sguil: https://bammv.github.io/sguil/index.html
• Snorby: https://github.com/Snorby/snorby
Other IDSs
While Snort is well known and emphasized on the CEH exam, there are other IDSs/IPSs. One is OSSIM (Open Source SIEM), which, as the name suggests, is primarily an SIEM (system information event manager). However, it also includes threat detection capabilities. It is offered by the company Alien Vault and is available at: https://sourceforge.net/projects/os-sim/.
The following are a few other IDSs:
• Check Point IPS Software Blade: https://www.checkpoint.com/quantum/intrusion-prevention-system-ips/
• Cisco Secure IPS: https://www.cisco.com/c/en/us/products/security/ngips/index.html
• FortiGate IPS: https://www.fortinet.com
• McAfee Host Intrusion Prevention for Desktops: https://www.mcafee.com/enterprise/en-us/products/host-ips-for-desktop.html
• OSSEC: https://www.ossec.net
• Cyberoam Intrusion Prevention System: http://www.cyberoam.ca/idp.html
• CrowdStrike Falcon X: https://www.crowdstrike.com
• Security Onion: https://securityonionsolutions.com
There are also IDSs/IPSs for mobile devices, including:
• Intruder Detector Wi-Fi: https://play.google.com/store/apps/details?id=sim.system.monitorsistema&hl=en_IE
• zIPS: https://www.zimperium.com/zips-mobile-ips
• Intrusion Detection PRO: https://play.google.com/store/apps/details?id=com.app.roberto.intrusiondetectionpro&hl=en_US&gl=US
• Darktrace: https://play.google.com/store/apps/details?id=com.darktrace.darktrace&hl=en_US&gl=US
Intrusions
In addition to IDSs/IPSs, there is the issue of the intrusions themselves. What precisely is an IDS/IPS trying to detect or prevent? The CEH curriculum divides intrusions into three subcategories that are detailed in the following subsections.
Exam Alert
Objective You should be able to differentiate the various types of intrusions for the CEH exam.
Network Intrusions
Network intrusions are what people normally think of when they think of intrusions. One of the clearest indicators of a network intrusion is any connection that cannot be explained. Another is any sudden ingress or egress of data that cannot otherwise be explained. Beyond these rather obvious signs, there are less obvious ones, such as repeated failed login attempts or repeated probes and scans. Such signs may not indicate a current intrusion but the likelihood of one coming.
System Intrusions
There are many signs of system intrusions—things that are often called indicators of compromise (IoC). IoCs including things like short, incomplete, or missing logs; slow performance that is unexplained; any unexplained modifications to system software or configuration files; and system problems such as reboots and crashing. Essentially, any time a system is behaving outside normal parameters, you must at least consider system compromise.
File Intrusions
File system intrusions are a subset of system intrusions, but they are common enough to warrant their own category on the CEH exam. Some of the signs of file system intrusions include the presence of any program or file that cannot be explained, unexplained changes in file sizes or missing files, and any unexplained change in any file or folder permissions.
Note that all three categories of intrusions use the term unexplained. Just because you have an increase in network traffic, or changes in file permissions, or some other anomaly does not mean it is a sign of an intrusion. If you can find a legitimate explanation for the behavior, then it is not an indicator of intrusion. This is what makes IDSs/IPSs so tricky, and it is why they often yield false positives and false negatives.
Exam Alert
Objective Make certain you understand how IDSs and IPSs work. This is very likely to be on the CEH exam.
Firewalls and Honeypots
A firewall is a barrier. It blocks some traffic and allows other traffic. The most common place to encounter a firewall is between a network and the outside world. Nevertheless, firewalls on individual computers and between network segments are also quite common. At a minimum, a firewall will filter incoming packets based on specific parameters, such as packet size, source IP address, protocol, and destination port. Linux and Windows both have built-in firewalls. So there is no reason for an individual computer not to have a firewall configured and turned on.
In an organizational setting, a minimum of a dedicated firewall between your network and the outside world is required. This might be a router that also has built-in firewall capabilities. Router manufacturers such as Cisco and Juniper include firewall capabilities.
Firewalls can be classified based on physical configuration. There are just a few configurations:
• Bastion host: This is a computer system designed and configured to protect network resources from attack. Traffic entering or leaving the network passes through the firewall. There are two interfaces: a public interface directly connected to the internet and a private interface connected to the internal network.
• Multi-homed: A firewall with two or more interfaces allows further subdivision of the network based on the specific security objectives of the organization.
• Screened host: A screened subnet or DMZ (an additional zone) may contain hosts that offer public services. The DMZ responds to public requests and has no hosts accessed by the private network. The private zone cannot be accessed by internet users. A DMZ is essentially two firewalls. One of the firewalls is a barrier to the outside world, and the other is a barrier to the organizational network. Between the two are placed public-facing things such as web servers and email servers. For some time now, most routers have had DMZ ports. Whatever is plugged into that port is in a DMZ, so the router effectively has two firewalls built in.
Physical configuration is only one way to consider firewalls. There are various types of firewalls and variations on those types. However, most firewalls can be grouped into one of the categories discussed in the following subsections.
Networks firewalls often perform another function: network address translation (NAT). NAT basically replaces the private IP address on outgoing packets with the public IP address of the gateway router so that the packets can be routed through the internet.
Packet Filtering
Basic packet filtering is the simplest form of firewall. It involves looking at packets and checking to see if each packet meets the firewall rules. For example, it is common for a packet filtering firewall to consider three questions:
• Is this packet using a protocol that the firewall allows?
• Is this packet destined for a port that the firewall allows?
• Is the packet coming from an IP address that the firewall has not blocked?
These are three very basic rules. Some packet filter firewalls check additional rules. But what is not checked is the preceding packets from that same source. Essentially, each packet is treated as a singular event, without reference to the preceding conversation. This makes packet filtering firewalls quite susceptible to some DoS attacks, such as SYN floods.
Stateful Packet Inspection Firewalls
A SPI (stateful packet inspection) firewall examines each packet and denies or permits access based not only on the examination of the current packet but also on data derived from previous packets in the conversation. The firewall is therefore aware of the context in which a specific packet was sent. This makes such a firewall far less susceptible to ping floods and SYN floods, as well as less susceptible to spoofing. For example, if a firewall detects that the current packet is an ICMP packet and a stream of several thousand packets have been continuously coming from the same source IP address, the firewall will see that this is clearly a DoS attack, and it will block the packets.
A stateful packet inspection firewall can also look at the actual contents of a packet, which allows for some very advanced filtering capabilities. Most high-end firewalls use the stateful packet inspection method; when possible, this is the recommended type of firewall.
Application Gateways
An application gateway (also known as application proxy or application-level proxy) is a program that runs on a firewall. When a client program, such as a web browser, establishes a connection to a destination service, such as a web server, it connects to an application gateway, or proxy. The client then negotiates with the proxy server in order to gain access to the destination service. In effect, the proxy establishes the connection with the destination behind the firewall and acts on behalf of the client, hiding and protecting individual computers on the network behind the firewall. This process actually creates two connections. There is one connection between the client and the proxy server, and there is another connection between the proxy server and the destination.
Once a connection is established, the application gateway makes all decisions about which packets to forward. Since all communication is conducted through the proxy server, computers behind the firewall are protected.
Essentially, an application gateway is used for specific types of applications, such as database or web server applications. It is able to examine the protocol being used (such as HTTP) for any anomalous behavior and block traffic that might get past other types of firewalls. It is common to have an application gateway that also includes stateful packet inspection.
Probably the most common example of an application gateway is a WAF (web application firewall), which is used for detecting specific web attacks, such as SQL injection, XSS (cross-site scripting), and other web attacks.
There are a number of firewall products that are at least mentioned on the CEH exam, including:
• ZoneAlarm Pro Firewall: https://www.zonealarm.com/software/firewall
• Zscaler: https://www.zscaler.com
• eScan Enterprise Edition: https://www.escanav.com
• Comodo Firewall: https://personalfirewall.comodo.com
• FortiGate Next-Generation Firewall: https://www.fortinet.com/products/next-generation-firewall/mid-range
• Cisco ASA: https://www.cisco.com/c/en/us/products/security/firewalls/index.html
The following firewalls are available for mobile devices:
• DroidWall—Android Firewall: https://code.google.com/archive/p/droidwall/
• aFirewall: https://afirewall.wordpress.com
Next Generation Firewalls (NGFWs)
NGFW (next-generation firewall) is a bit of a catchall term for any firewall that has advanced features. Normally NGFWs incorporate features from more than one type of firewall (for example, application gateway and stateful packet inspection). Furthermore, the usually include other functionality, such as IPSs, antivirus, and, in some cases, even machine learning.
Honeypots
A honeypot is an interesting technology. Essentially, it assumes that an attacker is able to breach your network security, and it would be best to distract that attacker away from your valuable data. Therefore, a honeypot includes a server that has fake data—perhaps an SQL server or Oracle server that is loaded with fake data and that is just a little less secure than your real servers. Then, because none of your actual users ever access this server, monitoring software is installed to alert you when someone does access this server.
A honeypot achieves two goals. First, it takes the attacker’s attention away from the data you wish to protect. Second, it provides what appears to be interesting and valuable data, thus leading the attacker to stay connected to the fake server and giving you time to try to track the attacker. Commercial solutions, such as Specter (www.specter.com), are available to set up honeypots. These solutions are usually quite easy to set up and include monitoring/tracking software. You may also find it useful to check out https://www.imperva.com/learn/application-security/honeypot-honeynet/ for more information on honeypots in general, as well as specific implementations.
Honeypots can be classified in a number of different ways. Common classifications include:
• Low-interaction honeypots: These simulate a limited number of services and don’t require much interaction from the attacker.
• Medium-interaction honeypots: These honeypots simulate a real operating system, complete with applications and services. These honeypots will only respond to specific commands that are preconfigured.
• High-interaction honeypots: These simulate a great many services and applications. They also capture complete information about an attack.
Honeypots can also be divided into categories of production and research. A production honeypot simulates a real production network for an organization. A research honeypot is usually a high-interaction honeypot that is meant to capture substantial information about how an attack is carried out.
There are a number of honeypot products on the internet, including:
• KFSensor: http://www.keyfocus.net/kfsensor/
• elastichoney: https://github.com/jordan-wright/elastichoney
• mysql-honeypotd: https://github.com/sjinks/mysql-honeypotd
• LaBrea: https://labrea.sourceforge.io/labrea-info.html
There are also tools for detecting honeypots. These basically work to determine if the behavior of the target system looks suspicious. A few such tools are:
• Send-Safe Honeypot Hunter: https://send-safe-honeypot-hunter.apponic.com
• hping: http://www.hping.org
Virtual Private Networks
A VPN (virtual private network) enables secure communications over a public network such as the internet. The packets sent back and forth over this connection are encrypted, thus making it private. A VPN essentially emulates a direct network connection. There are several different VPN technologies, but IPsec is very commonly used.
Point-to-Point Tunneling Protocol (PPTP) is the oldest of the protocols used to create VPNs. It was originally designed as a secure extension to Point-to-Point Protocol (PPP). PPTP was originally proposed as a standard in 1996 by the PPTP Forum—a group of companies that included Ascend Communications, ECI Telematics, Microsoft, 3Com, and U.S. Robotics. It adds the features of encrypting packets and authenticating users to the older PPP protocol. It is mentioned here primarily for historical purposes. It is still used, but not widely and is, therefore, not a focus of the CEH exam.
Layer 2 Tunneling Protocol (L2TP) was explicitly designed as an enhancement to PPTP. Like PPTP, it works at the data link layer of the OSI model. It has several improvements over PPTP. First, it offers more and varied methods for authentication: PPTP offers two methods (CHAP and EAP), whereas L2TP offers five (CHAP, EAP, PAP, SPAP, and MS-CHAP). L2TP is also often used in conjunction with IPSec.
IPsec (Internet Protocol Security) is widely used and will be mentioned on the CEH exam. You don’t need to know a great deal of technical detail but should have a general understanding of IPsec. One of the differences between IPsec and the other methods is that it encrypts not only the packet data but also the header information. With IPSec you can choose to encrypt just the data packet, or the packet and the header. Furthermore, IPsec includes safeguards against unauthorized retransmission of packets. This is important because one technique that a hacker can use is to simply grab the first packet from a transmission and use it to get his own transmissions to go through. Essentially, the first packet (or packets) has to contain the login data. If you simply re-send that packet(s), you will be sending a valid logon and password that can then be followed with additional packets. IPsec safeguards prevent this from happening.
IPsec operates in one of two modes: Transport mode, in which only the payload is encrypted, and Tunnel mode, in which both data and IP headers are encrypted. This is the protection that was referred to earlier.
Following are some basic IPsec terms:
• Authentication Header (AH): Provides connectionless integrity and data origin authentication for IP packets.
• Encapsulating Security Payload (ESP): Provides origin authenticity, integrity, and confidentiality protection of packets. It offers encryption-only and authentication-only configurations.
• Security associations (SAs): Provide the parameters necessary for AH or ESP operations. SAs are established using ISAKMP.
• Internet Security Association and Key Management Protocol (ISAKMP): Provides a framework for authentication and key exchange.
• Internet Key Exchange (IKE and IKEv2): Is used to set up an SA by handling negotiation of protocols and algorithms and to generate the encryption and authentication keys to be used.
During the initial establishment of an IPsec tunnel, SAs are formed. These SAs have relevant information regarding the encrypted connection, such as what encryption algorithm and what hashing algorithms will be used in the IPsec tunnel. IKE is primarily focused on forming these SAs. ISAKMP allows the two ends of the IPsec tunnel to authenticate to each other and to exchange keys.
SSL/TLS can also be used to create a VPN. Rather than simply encrypting a webpage, the SSL/TLS protocol is used to create a tunnel to a remote server. This is becoming more common, but IPSec is still the most widely used VPN protocol.
IDS Evasion Techniques
Obfuscation
Obfuscating attacks are a class of attacks that are often used and can be quite successful. The concept is simple, but the techniques can be of varying complexity. The idea is to encode a packet so that it is not detected by any signature matching. This can include encrypting packets and adding a string of null values at the end of a packet. This technique is often referred to as creating null operation pointer sleds (nop sleds).
Polymorphic malware can also circumvent signature-based IDSs/IPSs and antivirus software. Polymorphic malware is malware that changes some aspect of itself from time to time. This could be the previously mention nop sled, changing the email content/subject the malware is attached to, or any technique that changes the signature.
Another way to obfuscate is through false-positive generation. Basically, a hacker crafts a number of malicious packets and sends them just to generate alerts. The idea is specifically to generate false positives. The administrators become desensitized, thinking perhaps there is something wrong with the IDS configuration or rules. When the real attack comes, the administrators may believe it is another false positive.
Another way to obfuscate that works well for some attacks is through Unicode character encoding. If an attack is based on specific character strings, as in SQL injection, the characters are encoded so that the IDS might not recognize the attack. This might involve encoding in Unicode or using character functions such as CHR.
Yet another way to obfuscate an attack is to use compression. Compressing an attack, whether it is malware or not, can make it quite difficult for an IDS/IPS to examine the traffic involved. Similarly, simply encrypting traffic will make it difficult—or even impossible—for the IDS/IPS to examine that traffic.
Insertion Attacks
An insertion attack is a method commonly used to try to confuse an IDS. The process basically is an attempt to force the IDS to read invalid packets. For example, an attacker may send one-character packets to the target system, with each packet having a different TTL (Time to Live) value. The IDS intercepts these packets. Due to the varying TTL values, some packets won’t get past the IDS to the target system. This will result in the IDS and the target system having two different character strings.
Denial of Service (DoS) Attacks
DoS attacks are a simple and not particularly eloquent attacks, but they can be effective. IDSs often have centralized logging. Simply flooding an IDS with suspicious-looking packets can cause the device to at least fill up its log and no longer be able to log packets. In some cases, it could even cause the IDS to freeze or lock up.
Session Splicing
Session splicing is a common IDS/IPS avoidance technique. The attack is split into many different packets such that no single packet triggers the IDS. To make this type of attack more effective, the hacker can delay the attack packets by interspersing non-attack packets. This technique can enable the attacker to avoid triggering an advanced IDS/IPS that attempts to reassemble strings of packets to analyze them. You can see this in Figure 7.4.
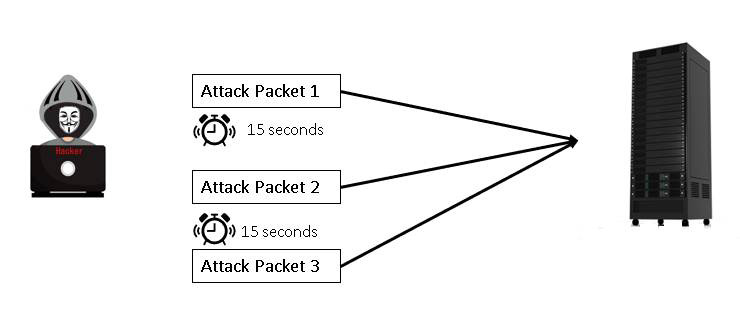
Figure 7.4 Session Splicing
Fragment Attacks
A fragmented attack involves sending fragmented packets. Normally an IDS/IPS has a timeout on reassembling fragments. Often that timeout is about 10 seconds. An attacker might send fragments every 15 seconds in order to get the IDS/IPS to drop the fragment, believing things have timed out, but have the fragment still reach the target and be reassembled. You can see this type of attack in Figure 7.5.
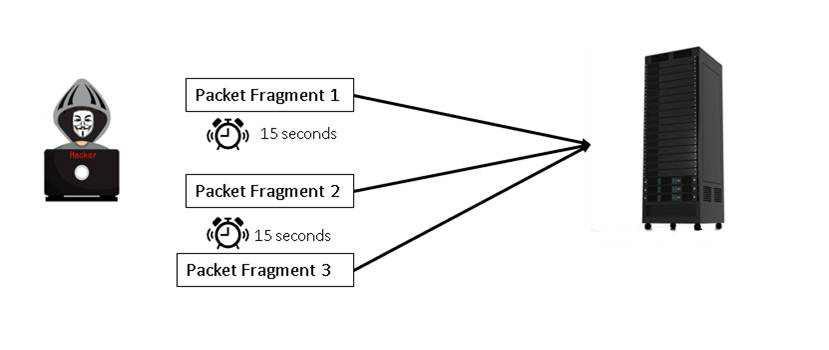
Figure 7.5 Fragment Attack
Overlapping fragments are related to fragment attacks. The attacker generates a series of small fragments, but the fragments have overlapping TCP sequence numbers. Perhaps the first fragment is 90 bytes with sequence number 1, and the second fragment has an overlapping sequence number and 80 bytes. When the target reassembles the fragments, the overlapping TCP sequence numbers could be an issue.
As you can probably surmise, there are quite a few packet fragment tools. These are some examples:
• NetScanTools Pro: https://www.netscantools.com
• Colasoft Packet Builder: https://www.colasoft.com/packet_builder/
• WAN Killer: https://www.solarwinds.com/engineers-toolset/use-cases/traffic-generator-wan-killer
Time to Live Attacks
As you know, network packets have a TTL value, which indicates how many hops the packet should go through in trying to reach the destination before giving up. The default TTL value is often 30 but depends on operating system. An attacker who has some knowledge of the target topology can use the TTL value to their advantage. An example might help illustrate this. Say that an attacker breaks a malicious payload into four fragments. Fragment 1 is sent with a high TTL value, and Fragment 2 is sent with a low TTL value. The IDS receives both fragments, but due to the low TTL on Fragment 2, the target machine may not receive the second packet. Then the attacker sends the third fragment, with a high TTL value. The IDS reassembles these fragments into a single packet, and it appears meaningless to the IDS.
Invalid RST Packet Attacks
The RST flag is used to close or reset a connection. TCP packets use a 16-bit checksum for error checking of both the header and the data. In an invalid RST packet attack, an RST packet is sent to the IDS with an invalid checksum. The target system sees the invalid checksum and drops the packet. However, given that an RST packet indicates a closing session, many IDSs/IPSs stop processing that stream, thinking the TCP communication session has ended. However, targets continue to be sent to the target. This is shown in Figure 7.6.
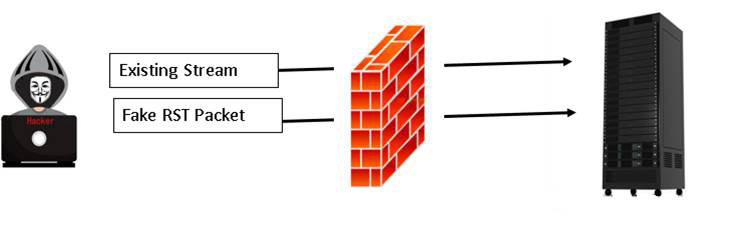
Figure 7.6 RST Attack
Urgency Flag
Any of the flags in a packet header are potentially exploitable. So, it should be no surprise that the URG (urgency) flag is used in attacks. The urgency flag is used to denote a packet that requires urgent processing at the receiving end. If the URG flag is set for a packet, then the urgent pointer field is set to a 16-bit offset value that points to the last byte of urgent data in the segment. This can be used to the attacker's benefits because some IDSs/IPSs don’t consider the urgent pointer and essentially ignore it. An attacker sends various packets, some of which have the urgency flag set. According to RFC 1122, when a TCP segment consists of an urgency pointer, one page of data after the urgent data will be lost. The urgency flag allows the attacker to hide small portions of the packet.
Polymorphism
Polymorphism was mentioned previously, in passing, as one method for circumventing IDSs/IPSs as well as antivirus software. There are many ways to carry out polymorphism, but one specific example is often on the CEH exam: polymorphic shell code. This type of attack essentially encodes the payload with a shell. That shell can be rewritten as often as needed. This means the signature of the malware is constantly changing and hard to detect. One variation of this is the ASCII shell code. An attacker basically wraps the attack in ASCII shell code to make it hard to detect by IDSs/IPSs.
Desynchronization
A desynchronization attack is an interesting attack that is based primarily on how connections are created. The attack begins by sending a SYN (synchronize) packet with an invalid checksum. If the real SYN packet is received after the TCP control block is opened, the IDS may reset the sequence number to match the new SYN packet. Essentially, this attack desynchronizes the traffic to keep the IDS from monitoring the stream. This particular method is pre-connection desynchronization.
There is also post-connection desynchronization. In this case, a post-connection SYN packet is sent with a divergent sequence number. Since there is already a connection, the target host will ignore this SYN packet. The idea is to get the IDS to resynchronize on the fake SYN packet, thus ignoring the actual stream.
Evasion Countermeasures
Remember that, as an ethical hacker, your goal is to improve an organization's security posture. So how might you counter the IDS/IPS evasion techniques described in this chapter? Well, a number of methods can help mitigate these techniques. No single technique will be able to block all or even most IDS/IPS evasion techniques, but by using multiple techniques, you can prevent many of them. These techniques include:
• Look for a nop opcode other than 0x90 to defend against the polymorphic shellcode problem.
• Perform an in-depth analysis of ambiguous network traffic for all possible threats.
• Harden the security of all communication devices, such as modems, routers, switches, etc.
• Ensure that IDSs normalize fragmented packets and allow those packets to be reassembled in the proper order.
• Regularly update the antivirus signature database.
• Block incoming ICMP packets.
• Limit tunneling techniques.
Firewall Evasion Techniques
As with IDSs/IPSs, a hacker may need to evade firewalls. There are specific techniques for doing this. Some techniques are common with IDSs/IPSs, and some are unique to firewalls.
Exam Alert
Objective For the CEH exam, you need to know firewall evasion techniques in detail and be able to differentiate between them. It is not enough to have a general idea of how they work.
Firewall Identification
A number of fairly simple techniques can be used to identify firewalls and other devices. It is important to understand a firewall as much as possible, if the intent is to evade it. Banner grabbing is one of the simplest techniques. The idea is to try to use Telnet to get into a target system and try to grab data. Such an attack looks like this:
Telnet 127.0.0.1 80 HEAD /HTTP/1.0 <enter><enter>
You can also simply use Telnet to get to an IP address and port to see if it is open. Some devices, such as printers, may have Telnet running by default.
There are countermeasures for these identification methods. A few are enumerated here:
• Use false banners.
• Turn off unnecessary services.
• Use the ServerMask tool to disable/change banners.
• Use the Apache2.x mod_headers directive in httpd.conf to change a banner.
• In Apache, turn off ServerSignature in httpd.conf.
• Change file extensions, such as by using the tool PageXchanger in IIS.
Port scanning, which was discussed in Chapters 1, “Reconnaissance and Scanning,” and 2, “Enumeration and Vulnerability Scanning,” can also be used on firewalls to learn what services they are running. Another technique is referred to as firewalking. This technique basically changes the TTL values for packets and sends them to the target. The idea is to locate where firewalls are. The hacker sends a TCP or UDP packet to the targeted firewall with the TTL value set to one hop greater than that of the firewall. If the packet makes it through the gateway, it is forwarded to the next hop, where the TTL value equals 1 and elicits an ICMP “TTL exceeded in transit” message, which lets the hacker know that they got past the firewall.
Obfuscation
As with IDS/IPS evasion, obfuscation is a common way to avoid firewalls. One method, IP address spoofing, is quite simple. IP address spoofing can be done in two different ways. The first approach is simply to hide the IP address from which the attack is coming. The second approach is to spoof the IP address of a machine that is trusted by the firewall. This method, obviously, requires some level of reconnaissance.
Creating very small packet fragments can cause some of the TCP header information to be fragmented. This fragmentation can prevent the firewall from matching the TCP packet to some signature. This is sometimes called tiny packets.
Using anonymizers to connect to a site is also a way to obfuscate. There are several available:
• Anonymizer: https://www.anonymizer.com
• Boom Proxy: http://www.boomproxy.com
• Spy Surfing: http://www.spysurfing.com
• Proxify: https://proxify.com
• Hide My Ass: https://www.hidemyass.com/en-us/index
• PIA: https://www.privateinternetaccess.com
• K Proxy: https://kproxy.com
• Zend Proxy: https://zendproxy.com
Source Routing
Source routing is a technique for firewall evasion that involves trying to specify the route a packet will take. Source routing allows the sender to specify all or at least part of the packet's route through the network. Without source routing, as the packet passes from one node to another, each router examines the destination IP address and selects the next hop. Basically, in source routing, the sender makes some of these next-hop decisions.
Tunneling
HTTP tunneling is a common technique. Web traffic or HTTP traffic frequently passes through firewalls. So encapsulating data in HTTP may allow an attacker to more readily pass a firewall. This is method of tunneling a bit weak because firewalls often do examine HTTP traffic. There are plenty of tools for tunneling, though, such as HTTPort (https://www.htthost.com/) and Super Network Tunnel (http://www.networktunnel.net/).
There are several types of tunneling:
• ICMP tunneling: Basically, if ICMP is allowed in the network, then tools can be used to send ICMP packets and execute commands. Loki is one such tool, but there are many others. The idea is to send ICMP packets that encapsulate the attack commands.
• ACK tunneling: Basically, the ACK bit is used to acknowledge a session connection or receipt of a packet. Some firewalls don’t check packets with the ACK bit. For this reason, using TCP packets with the ACK bit set will bypass some firewalls. As you might suspect, there are tools to help do this. One is AckCmd.
• Encrypted tunneling: Any communication that is encrypted is likely to be able to avoid examination by a firewall. Using any encrypted protocol such as SSH or HTTPS, if allowed by the firewall, can keep the firewall from analyzing the traffic. Some firewalls are configured to limit tunneling for this very reason.
WAF Bypass
WAFs specifically check for web attacks. Thus, a typical XSS (cross-site scripting) attack is likely to be blocked by a WAF. However, replacing the text with ASCII or hex encoding may make it possible to bypass the WAF. Consider this common XSS script:
<script>alert("XSS”)</script>
This script could be encoded with ASCII values as follows:
<script> String.fromCharCode(88 83 83)</script)
When converted to hex, the script would look like this:
<script> 585353</script>
It is also possible to convert the script tags to ASCII or hex.
Firewall Evasion Tools
As you can probably surmise, there are a number of tools for firewall evasion. The CEH exam often asks about tools, so you should at least being able to identify the following important tools:
• Atelier Web Firewall Tester: http://www.atelierweb.com
• FTester: https://inversepath.com/ftester.html
• Snare Central: https://www.snaresolutions.com/snare-central-8-4/
Firewall Evasion Countermeasures
As discussed earlier in this chapter, in reference to IDSs/IPSs, there are methods that can limit or prevent at least some firewall evasion techniques. The CEH exam will expect you to know these:
• Monitor user access to firewalls and restrict which users can modify the firewall configuration.
• Control physical access to the firewall.
• Set the firewall ruleset to deny all traffic by default and enable only the services required.
• Create a unique user ID to run the firewall services rather than running the services using the administrator or root IDs.
• When possible, block or disable all inbound connections, such as Telnet, FTP, and SSH. In some situations, you cannot do this, but when possible, it should be done.
• Monitor firewall logs at regular intervals and investigate all suspicious log entries found.
Exam Alert
Objective Remember that the goal of an ethical hacker is to improve security. So expect the CEH exam to ask you about countermeasures to any hacking technique.
What Next?
If you want more practice on this chapter's exam objectives before you move on, remember that you can access all of the Cram Quiz questions on the book web page. The next chapter covers web servers and web applications.
