Chapter 20
Controlling File Transfer and Blocking the Spread of Malware
As a security professional, you might not want your users to download and open random files from the Internet. While you allow your users to visit certain websites, you might want to block their attempts to download files from the sites they visit or to upload files to external websites. Unsafe downloads can spread viruses, malware, exploit kits, and other dangers on your network, and they can make the entire network vulnerable to various types of attacks. Likewise, to comply with the policy of your organization, you might not want your users to upload any particular types of files to the Internet from your corporate network.
The Firepower system enables you to block the download and upload of files based on file type (extension) and suspicious activity (malware).
File Policy Essentials
To govern the transfer of a file within a network, the Firepower System offers a standalone policy known as a file policy. A file policy allows you detect any file type, such as media files (.mp3, .mpeg), executable files (.exe, .rpm), and so on. In addition, an FTD device can analyze a file for potential malware when the file traverses a network. By design, FTD can detect and block files with a particular type before it performs lookups for malware.
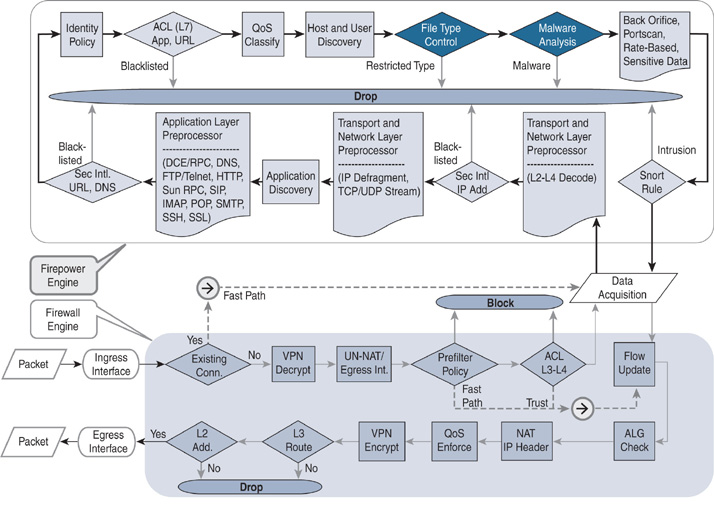
Figure 20-1 shows an architectural diagram of the Firepower engine. The figure highlights both components of a file policy—file type control and malware analysis—which are described in the following sections.
File Type Detection Technology
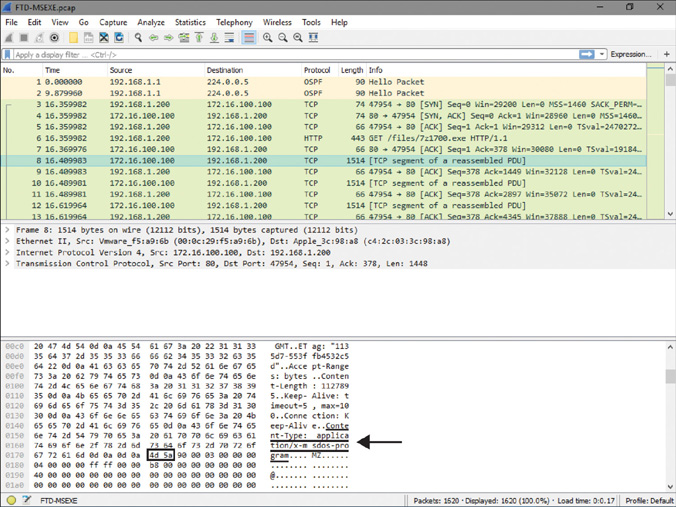
The Firepower System uses special metadata about a file, known as a magic number, to identify the file format. A magic number is a sequence of unique numbers that are encoded within files. When a file traverses a network, FTD can match the magic numbers from the stream of packets to determine the format of a file. For example, for a Microsoft executable (MSEXE) file, the magic number is 4D 5A. To find this number, Snort uses the following rule on FTD:
file type:MSEXE; id:21; category:Executables,Dynamic Analysis Capable,Local
Malware Analysis Capable; msg:"Windows/DOS executable file "; rev:1; content:
| 4D 5A|; offset:0;
Figure 20-2 demonstrates the magic number on a TCP packet. This packet is captured when a client downloads an executable file from a website. After completing the TCP three-way handshake, the server (172.16.100.100) sends this information to the client (192.168.1.200).
Malware Analysis Technology
To empower a network with the latest threat intelligence, Cisco has integrated the Advanced Malware Protection (AMP) technology with the Firepower System. AMP enables an FTD device to analyze a file for potential malware and viruses while the file traverses a network. To expedite the analysis process and to conserve resources, FTD can perform both types of malware analysis—local and dynamic. Let’s take a look at the technologies behind them.
Figure 20-3 illustrates the purposes of any interactions between the Firepower System and the Cisco clouds.
FTD calculates the SHA-256 hash value (Secure Hash Algorithm with 256 bits) of a file and uses the value to determine a disposition. The FMC performs a lookup on the cached disposition before it sends a new query to the AMP cloud. It provides a faster lookup result and improves overall performance. Depending on the action you select on a file policy, a Firepower system can perform additional advanced analysis in the following order:
![]() Spero analysis: The Spero analysis engine examines the MSEXE files only. It analyzes the structure of an MSEXE file and submits the Spero signature to the cloud.
Spero analysis: The Spero analysis engine examines the MSEXE files only. It analyzes the structure of an MSEXE file and submits the Spero signature to the cloud.
![]() Local analysis: FTD uses two types of rulesets for local analysis: high-fidelity rules and preclassification rules. The FMC downloads high-fidelity malware signatures from Talos and disseminates the rulesets to FTD. FTD matches the patterns and analyzes files for known malware. It also uses the file preclassification filters to optimize resource utilization.
Local analysis: FTD uses two types of rulesets for local analysis: high-fidelity rules and preclassification rules. The FMC downloads high-fidelity malware signatures from Talos and disseminates the rulesets to FTD. FTD matches the patterns and analyzes files for known malware. It also uses the file preclassification filters to optimize resource utilization.
![]() Dynamic analysis: The dynamic analysis feature submits a captured file to the threat grid sandbox for dynamic analysis. A sandbox environment can be available in the cloud or on premises. Upon analysis, the sandbox returns a threat score—a scoring system for considering a file as potential malware. A file policy allows you to adjust the threshold level of the dynamic analysis threat score. Thus, you can define when an FTD device should treat a file as potential malware.
Dynamic analysis: The dynamic analysis feature submits a captured file to the threat grid sandbox for dynamic analysis. A sandbox environment can be available in the cloud or on premises. Upon analysis, the sandbox returns a threat score—a scoring system for considering a file as potential malware. A file policy allows you to adjust the threshold level of the dynamic analysis threat score. Thus, you can define when an FTD device should treat a file as potential malware.
Dynamic analysis provides an option called capacity handling that allows a Firepower system to store a file temporarily if the system fails to submit the file to a sandbox environment. Some of the potential reasons for such a failure would be communication issues between Firepower and the sandbox (cloud or on premises), exceeding the limit for file submission, and so on.
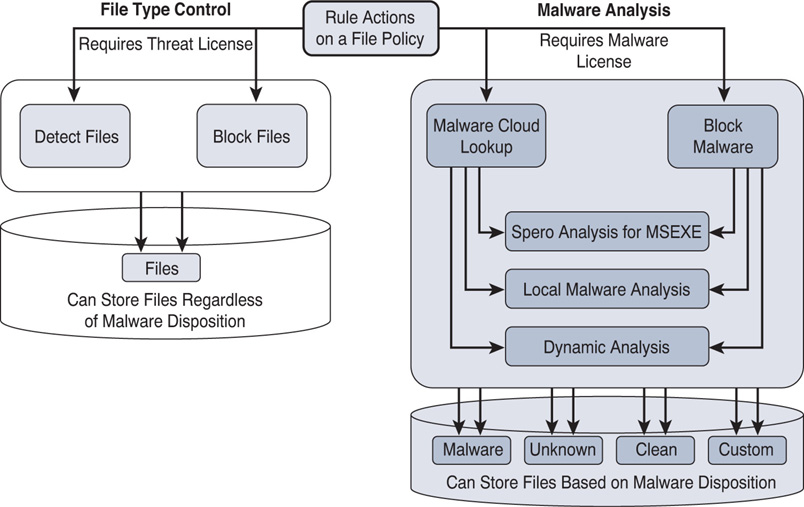
Figure 20-4 shows an architectural workflow of the malware analysis techniques on a Firepower system.
Licensing Capability
With the installation of a Threat license, a Firepower system automatically enables the file type control. This means that if you are currently using the security intelligence and intrusion prevention features on an FTD device, you should be able to control the transfer of a particular file type without the need for any new license. However, to perform a malware analysis, Firepower requires an additional license, known as a Malware license.
Figure 20-5 shows the actions and features you can enable by using the Threat and Malware licenses.
Table 20-1 summarizes the differences between the capabilities of a Threat license and a Malware license.
Table 20-1 Differences Between a Threat License and a Malware License
Best Practices for File Policy Deployment
You should consider the following best practices when you configure a file policy:
![]() When you want to block a file by using file policy, use the Reset Connection option. It allows an application session to close before the connection times out by itself.
When you want to block a file by using file policy, use the Reset Connection option. It allows an application session to close before the connection times out by itself.
![]() If you want to download a captured file to your desktop, make sure you take extra precautions on your desktop before you download. The file might be infected with malware that could be harmful to your desktop.
If you want to download a captured file to your desktop, make sure you take extra precautions on your desktop before you download. The file might be infected with malware that could be harmful to your desktop.
![]() Keep the file size limit low to improve performance. An access control policy allows you to limit the file size. It can impact the following activities:
Keep the file size limit low to improve performance. An access control policy allows you to limit the file size. It can impact the following activities:
![]() Sending a file to the cloud for dynamic analysis
Sending a file to the cloud for dynamic analysis
![]() Storing a file locally
Storing a file locally
![]() Calculating the SHA-256 hash value of a file
Calculating the SHA-256 hash value of a file
![]() In case of a communication failure between the Firepower System and the Cisco clouds, FTD can hold the transfer of a file for a short period of time when the file matches a rule with the Block Malware action. Although this holding period is configurable, Cisco recommends that you use the default value.
In case of a communication failure between the Firepower System and the Cisco clouds, FTD can hold the transfer of a file for a short period of time when the file matches a rule with the Block Malware action. Although this holding period is configurable, Cisco recommends that you use the default value.
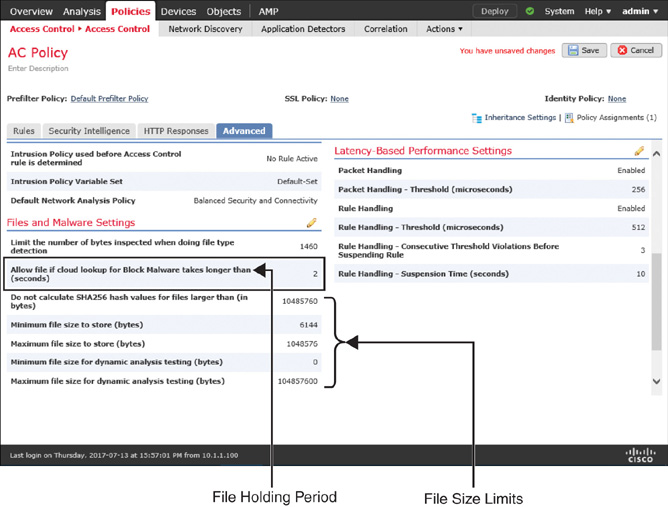
Figure 20-6 displays the advanced settings of an access control policy in which you can define the file holding period and file size limits.
Fulfilling Prerequisites
The following items are necessary for a successful file policy deployment:
![]() Make sure to install an appropriate license. To control the transfer of a particular file type, only a Threat license is necessary. To perform malware analysis, an additional Malware license is required.
Make sure to install an appropriate license. To control the transfer of a particular file type, only a Threat license is necessary. To perform malware analysis, an additional Malware license is required.
![]() A file policy uses the adaptive profile feature. Make sure the feature is enabled in the advanced settings of an access control policy (see Figure 20-7).
A file policy uses the adaptive profile feature. Make sure the feature is enabled in the advanced settings of an access control policy (see Figure 20-7).
![]() Make sure the Enable Automatic Local Malware Detection Updates option is checked (see Figure 20-8). It allows the FMC to communicate with Talos cloud every 30 minutes. When a new ruleset is available, the FMC downloads it to enrich the local malware analysis engine.
Make sure the Enable Automatic Local Malware Detection Updates option is checked (see Figure 20-8). It allows the FMC to communicate with Talos cloud every 30 minutes. When a new ruleset is available, the FMC downloads it to enrich the local malware analysis engine.
![]() A file policy leverages the application detection functionality to determine whether an application is capable of carrying a file. Make sure a network discovery policy is deployed to discover applications. To learn about application detection and control, read Chapter 19, “Discovering Network Applications and Controlling Application Traffic.”
A file policy leverages the application detection functionality to determine whether an application is capable of carrying a file. Make sure a network discovery policy is deployed to discover applications. To learn about application detection and control, read Chapter 19, “Discovering Network Applications and Controlling Application Traffic.”
Configuring a File Policy
Deployment of a file policy is a multistep process. First, you need to create a file policy and add any necessary file rules to it. A file rule allows you to select the file type category, application protocol, direction of transfer, and action. However, you cannot add any source or destination details on a file rule. To assign network addresses, you need to create an access rule within an access control policy and invoke the file policy within the access rule.
Creating a File Policy
To create a file policy, follow these steps:
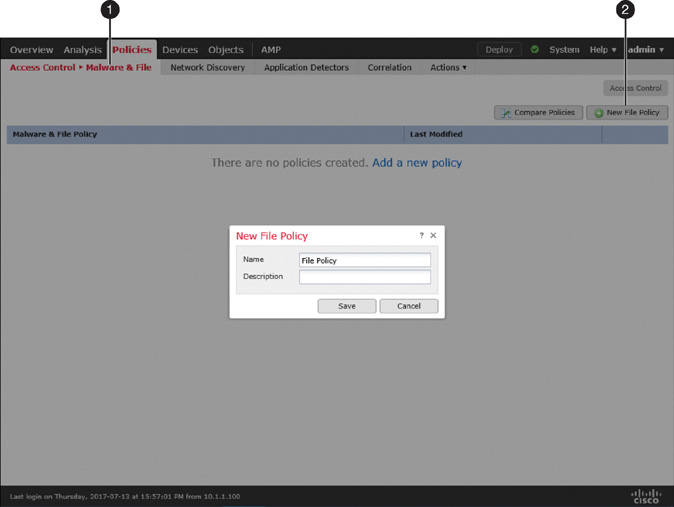
Step 1. Navigate to Policies > Access Control > Malware & File. The Malware & File Policy page appears.
Step 2. Click the New File Policy button, and the New File Policy window appears (see Figure 20-9).
Step 3. Give a name to the policy and click the Save button. The file policy editor appears.
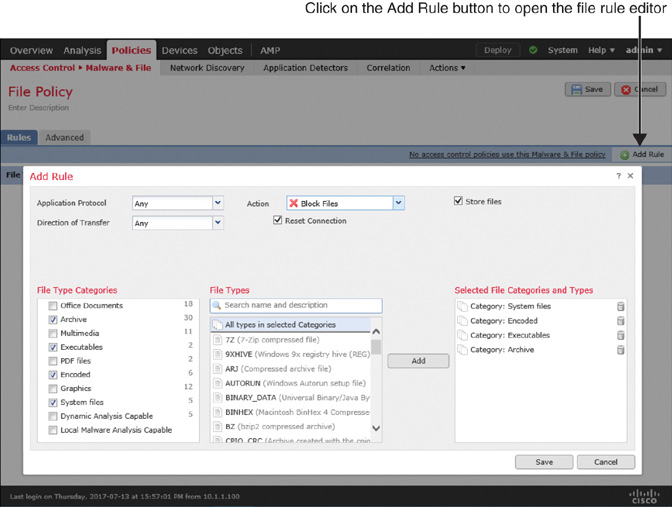
Step 4. Click the Add Rule button. The file rule editor appears.
Step 5. Select Any from the Application Protocol dropdown to detect files over multiple application protocols.
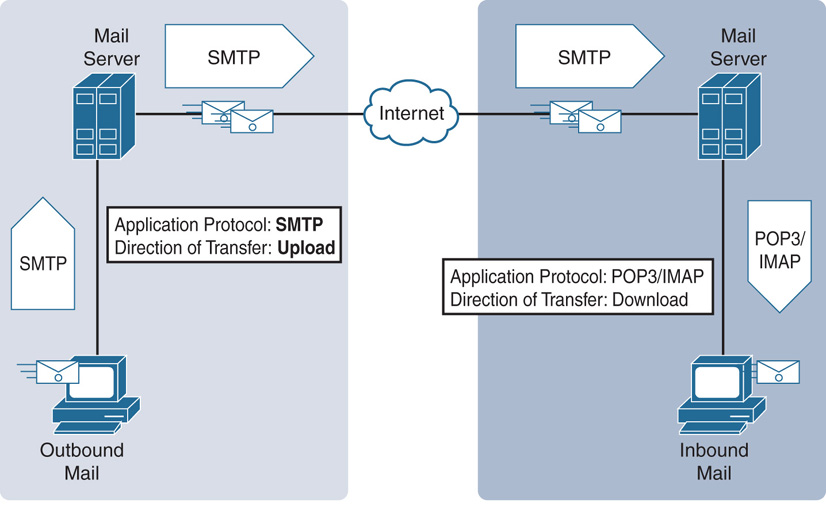
Step 6. Make a selection from the Direction of Transfer dropdown. Depending on the underlying application protocol for a file transfer, the direction can be limited. For example, the HTTP, FTP or NetBIOS-ssn (SMB) protocol allows any direction—upload or download. However, SMTP (upload only) and POP3/IMAP (download only) support unidirectional transfer.
Figure 20-10 explains the reasons for unidirectional transfer with the SMTP, POP3, and IMAP protocols. While SMTP is used for outbound transfers, POP3/IMAP is used to download incoming emails and any attachments.
Step 7. Select the file type categories you want to block, and click Add to add them to the rule. You can also search for a specific file type directly.
Step 8. Select an action from the Action dropdown. The following options are available:
Note
A file policy does not evaluate a file rule based on its position; rather, it uses the order of actions. The order of actions is Block Files, Block Malware, Malware Cloud Lookup, and Detect Files. When performing an advanced analysis, FTD engages Spero analysis, local malware analysis, and dynamic analysis, successively—if you have enabled all of them in a particular file rule.
![]() Detect Files: This action detects a file transfer and logs it as a file event without interrupting the transfer.
Detect Files: This action detects a file transfer and logs it as a file event without interrupting the transfer.
![]() Block Files: This action blocks certain files—depending on the file formats selected on a file rule.
Block Files: This action blocks certain files—depending on the file formats selected on a file rule.
Tip
If you want to block a file, select the Reset Connection option. It allows an application session to close before the connection times out by itself.
![]() Figure 20-11 displays a file rule that blocks the transfer of any system, executable, encoded, and archive files without analyzing them for malware. According to the configuration, when a file matches this rule, FTD stores the file on local storage and sends reset packets to terminate any associated connection.
Figure 20-11 displays a file rule that blocks the transfer of any system, executable, encoded, and archive files without analyzing them for malware. According to the configuration, when a file matches this rule, FTD stores the file on local storage and sends reset packets to terminate any associated connection.
![]() Figure 20-12 shows the creation of two file rules. The first rule blocks system, encoded, executable, and archive files with reset packets and stores the blocked file in local storage. The second rule detects the graphic, PDF, multimedia, and Office document files but does not block or store them as they traverse the network.
Figure 20-12 shows the creation of two file rules. The first rule blocks system, encoded, executable, and archive files with reset packets and stores the blocked file in local storage. The second rule detects the graphic, PDF, multimedia, and Office document files but does not block or store them as they traverse the network.
![]() Malware Cloud Lookup: This action enables an FTD device to perform malware analysis locally and remotely. FTD allows an uninterrupted file transfer regardless of the malware disposition.
Malware Cloud Lookup: This action enables an FTD device to perform malware analysis locally and remotely. FTD allows an uninterrupted file transfer regardless of the malware disposition.
![]() Block Malware: This action performs the same tasks as the Malware Cloud Lookup action, with an addition of blocking the original file if the disposition is determined to be malware.
Block Malware: This action performs the same tasks as the Malware Cloud Lookup action, with an addition of blocking the original file if the disposition is determined to be malware.
Note
When you select the Malware Cloud Analysis or Block Malware action, the Firepower System offers various analysis methods. Read the previous section for more information on malware analysis methodologies.
Figure 20-13 shows another option for a file rule (which requires a Malware license). This rule enables an FTD device to block the transfer of a file and to store it locally if the file has one of three criteria: infected with malware, disposition is unknown, or matches a custom detection list. When blocking the file transfer, FTD sends reset packets to terminate any associated connection. This rule does not allow an FTD device to store a file if the file appears to be clean. It prevents storage from getting full of clean or benign files.
Step 9. Optionally, on the Advanced tab, you can enable additional features for advanced analysis and inspection. Figure 20-14 shows the advanced settings of a file policy. For example, here you can adjust the threshold level of the dynamic analysis threat score, enable inspection for the archived contents, define the depth of inspection for a nested archive file, and so on.
Step 10. Click the Save button on the policy editor to save the changes on the file policy.
Applying a File Policy
To apply a file policy on an FTD device, you need to create an access rule within an access control policy and invoke the file policy in the access rule. Here are the detailed steps:
Step 1. Navigate to Policies > Access Control > Access Control. The available access control policies appear. You can modify one of the existing policies or click New Policy to create a new one.
Step 2. On the policy editor page, use the pencil icon to modify an existing access rule to invoke a file policy. If there are no rules created, click the Add Rule button to create a new access rule.
Step 3. On the rule editor window, go to the Inspection tab. You will notice dropdowns for Intrusion Policy, Variable Set, and File Policy. Figure 20-15 shows the dropdowns on the Inspection tab. The file policy you configured earlier should populate here, under the File Policy dropdown.
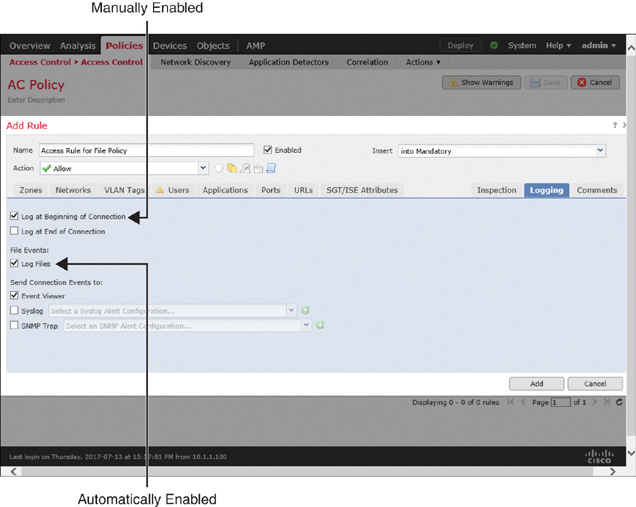
Step 4. Choose a policy from the File Policy dropdown. Doing so automatically enables logging for the file event. You can verify it by viewing the settings on the Logging tab (see Figure 20-16). To view events for each connection that matches a particular access rule condition, you can manually enable Log at Beginning of Connection.
Step 5. Click the Add button to save the changes. You are returned to the access control policy editor page. If you are editing an existing access rule, you can click the Save button instead.
Step 6. On the access control policy editor page, select a default action. You cannot select a file policy as the default action of an access control policy. You can only invoke a file policy within an individual access rule.
Step 7. Finally, click Save to save the changes, and click Deploy to deploy the configuration to the FTD device.
Verification and Troubleshooting Tools
A file policy can generate two types of events: file events and malware events. FTD generates a file event when it detects or blocks a certain type of file without a malware lookup. FTD generates a malware event when it performs an analysis for malware or blocks a file due to malware disposition.
The following sections of this chapter demonstrate the operation of both policies—file type detection and malware analysis. In this scenario, a client downloads files with two different formats—Microsoft executable (MSEXE) file format and Portable Document Format (PDF). As a security engineer, you need to verify whether a file policy is operational and whether the transfer of files complies with the active file policy.
Figure 20-17 shows the topology that is used in the configuration examples in this chapter. To demonstrate various scenarios, the client computer (192.168.1.200) downloads different files from a web server (172.16.100.100), and the FTD device in the LAN acts on them.
Analyzing File Events
Using a web browser on your client computer, you can attempt to download two files—7z1700.exe and userguide.pdf—from a web server. If the FTD device is running the following file policy, it should block the download of the 7z1700.exe file and allow and detect the download of userguide.pdf.
Figure 20-18 shows the currently enabled rules on a file policy. The first rule detects and blocks files in four categories, and the second rule only detects files in four different categories.
Navigate to Files > File Events to view the file events. By default, the FMC shows the File Summary page. However, to find useful contextual information about file events, you should also check the Table View of File Events page.
Figure 20-19 confirms the blocking and detection of an MSEXE file and a PDF file. Because the Block Files action does not perform malware analysis, the Disposition column is blank.
Figure 20-20 shows detailed information about the detected and blocked files and their associated source and destination hosts. The SHA256 and Threat Score columns are blank because the FTD device does not perform any kind of malware analysis but detects file type only.
Figure 20-21 shows the data of file events visually in various widgets. To find this dashboard, go to Overview > Dashboards > Files Dashboard.
If you do not see a file event that you expected to see, you can use the CLI to debug the action of a file rule and verify the operation of a file policy. If you run the system support firewall-engine-debug command while you attempt to transfer a file, you see detailed logs associated with file inspection and analysis.
Example 20-1 shows the detailed debugging messages that appear when a client computer attempts to download the executable file 7z1700.exe and the FTD device blocks it due to the actions Block Files, Reset Connection, and Store Files.
Example 20-1 Blocking a Microsoft Executable (MSEXE) File
! First, run the debug command and specify necessary parameters.
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
! Now, begin the transfer of an executable file.
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 using HW or preset rule order 2,
'Access Rule for File Policy', action Allow and prefilter rule 0
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 URL SI:
ShmDBLookupURL("http://172.16.100.100/files/7z1700.exe") returned 0
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File Policy verdict is Type,
Malware, and Capture
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Unknown,
fileAction Block, flags 0x00203500, and type action Reject for type 21 of
instance 0
! At this stage, the file is being transferred through the FTD. The following
messages appear after the file is stored on the FTD. FTD blocks the file transfer
as soon as it detects the end-of-file marker on a packet.
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File type storage finished within
signature using verdict Reject
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of partial file with flags 0x00203500 and status Exceeded Max Filesize
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Reject and
flags 0x00203500 for partial file of instance 0
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 File type event for file named
7z1700.exe with disposition Type and action Block
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 Archive childs been processed No
192.168.1.200-47954 > 172.16.100.100-80 6 AS 4 I 0 Deleting session
^C
Caught interrupt signal
Exiting.
>
Example 20-2 shows the debugging messages that appears when a client computer downloads the file userguide.pdf. FTD generates a log, but it does not block the PDF file because the rule action is Detect Files.
Example 20-2 Detecting a Portable Document Format (PDF) File
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 Starting with minimum 0, id 0 and
SrcZone first with zones -1 -> -1, geo 0(0) -> 0, vlan 0, sgt tag: untagged,
svc 0, payload 0, client 0, misc 0, user 9999997, url , xff
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 match rule order 2, 'Access Rule
for File Policy', action Allow
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 URL SI:
ShmDBLookupURL("http://172.16.100.100/files/userguide.pdf") returned 0
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 Starting with minimum 0, id 0 and
SrcZone first with zones -1 -> -1, geo 0(0) -> 0, vlan 0, sgt tag: untagged, svc
676, payload 0, client 638, misc 0, user 9999997, url http://172.16.100.100/files/
userguide.pdf, xff
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 match rule order 2, 'Access Rule
for File Policy', action Allow
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 allow action
.
<Output omitted for brevity>
.
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 File policy verdict is Type,
Malware, and Capture
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Log, fileAction
Log, flags 0x00001100, and type action Log for type 285 of instance 0
192.168.1.200-58374 > 172.16.100.100-80 6 AS 4 I 0 File type event for file named
userguide.pdf with disposition Type and action Log
.
<Output omitted for brevity>
^C
Caught interrupt signal
Exiting.
>
Analyzing Malware Events
In this section, when you attempt to download the same MSEXE file 7z1700.exe as before by using a web server, you will notice different behavior on the FTD device because it applies a different rule action—Block Malware instead of Block Files. You will analyze the following scenarios in this section:
![]() The FMC is unable to communicate with the cloud.
The FMC is unable to communicate with the cloud.
![]() The FMC performs a cloud lookup.
The FMC performs a cloud lookup.
![]() FTD blocks malware.
FTD blocks malware.
Figure 20-22 shows a file rule that blocks the transfer of any malicious files. When FTD determines that a file is a malicious file, this rule allows an FTD device to store the file in local storage and send reset packets to terminate any associated connection. To conserve disk space, files with clean disposition are not stored.
The FMC Is Unable to Communicate with the Cloud
After deploying a file policy with the Block Malware rule action, you can attempt to download the same MSEXE file 7z1700.exe as before but now using a web server. Unlike in the previous section, where you used file type detection, you will find the FTD to calculate the SHA-256 checksum of the file. FTD later attempts to perform a cloud lookup for the hash value.
Figure 20-23 shows a file event (table view) for downloading the same 7z1700.exe file. Because the file policy enables malware analysis, FTD calculates the SHA-256 hash value. However, the cloud lookup process times out.
Figure 20-24 shows the summary view of the file events. Due to the cloud lookup timeout, malware disposition is listed as Unavailable.
Example 20-3 demonstrates that the FTD device is able to calculate the SHA-256 checksum locally. However, when it sends the calculated hash value for a lookup, the query times out (due to a communication failure to the Cisco cloud). This leads the FMC to display the disposition as Unavailable.
Example 20-3 The FMC Calculates SHA-256 Hash Value but Is Unable to Complete a Lookup
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 using HW or preset rule order 2,
'Access Rule for File Policy', action Allow and prefilter rule 0
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 URL SI: ShmDBLookupURL("h
ttp://172.16.100.100/files/7z1700.exe") returned 0
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File policy verdict is Type,
Malware, and Capture
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Unknown,
fileAction Malware Lookup, flags 0x01BDDA00, and type action Stop for type 21 of instance 0
! Next, FTD calculates the SHA-256 hash value of the file, which is
2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d.
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Unknown
and flags 0x01BDDA00 for partial file of instance 0
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature cache query returned Cache Miss for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d with disposition Cache Miss, spero Cache Miss, severity 0, and transmit
Not Sent
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Pending
and flags 0x01BDDA00 for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d of instance 0
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature cache query
returned Cache Miss for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d with disposition Cache Miss, spero Cache Miss, severity 0, and transmit
Not Sent
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Pending
and flags 0x01BDDA00 for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d of instance 0
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 File malware event for
2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d named 7z1700.exe
with disposition Cache Miss and action Timeout
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 Archive childs been processed No
192.168.1.200-58466 > 172.16.100.100-80 6 AS 4 I 0 Deleting session
^C
Caught interrupt signal
Exiting.
>
To find the root cause of a lookup failure, you can analyze the syslog messages on the FMC. To view the messages, you can use any convenient Linux commands, such as less, cat, or tail, as needed. Note that the timestamps of messages use coordinated universal time (UTC).
Tip
Cloud Lookup Timeout in the Action column indicates that the FMC is unable to connect to the cloud. When you see this, check whether the management interface of the FMC is connected to the Internet. If the Internet connectivity is operational, then make sure the FMC can resolve a DNS query.
Example 20-4 shows various states of the FMC cloud communication. The syslog messages are automatically generated by the Firepower software. To view them in real time, you can use the tail command with the -f parameter.
Example 20-4 Analyzing Syslog Messages for FMC Communications to the Cloud
admin@FMC:~$ sudo tail -f /var/log/messages
Password:
.
<Output is omitted for brevity>
.
! If FMC is connected to the internet, but fails to resolve a DNS query, the
following error message appears in the Syslog.
.
[timestamp] FMC stunnel: LOG3[3953:140160119551744]: Error resolving 'cloud-sa.amp.
sourcefire.com': Neither nodename nor servname known (EAI_NONAME)
.
! After you fix any communication issues, FMC should be able to connect to the
cloud. The following Syslog messages confirm a successful connection.
.
[timestamp] FMC SF-IMS[25954]: [26657] SFDataCorrelator:FireAMPCloudLookup [INFO]
cloud server is cloud-sa.amp.sourcefire.com
[timestamp] FMC SF-IMS[25954]: [26657] SFDataCorrelator:imcloudpool [INFO] connect
to cloud using stunnel
.
! Once the FMC is connected to the cloud, it begins the registration process. The
following messages confirm successful registrations to the Cisco Clouds.
.
[timestamp] FMC SF-IMS[25954]: [26657] SFDataCorrelator:FireAMPCloudLookup [INFO]
Successfully registered with fireamp cloud
[timestamp] FMC SF-IMS[25954]: [25954] SFDataCorrelator:FileExtract [INFO]
Successfully registered with sandbox cloud
.
! Upon successful registration, FMC is able to perform cloud lookup and obtains
updates. The following messages confirm a successful check for malware database
update.
.
[timestamp] FMC SF-IMS[25275]: [25275] CloudAgent:CloudAgent [INFO] ClamUpd, time to
check for updates
.
[timestamp] FMC SF-IMS[25275]: [25298] CloudAgent:CloudAgent [INFO] Nothing to do,
database is up to date
.
Figure 20-25 shows the DNS setting on an FMC management interface. To find this page, go to System > Configuration and select Management Interfaces. Make sure the FMC can communicate with the configured DNS server and resolve a domain name using this DNS server.
The FMC Performs a Cloud Lookup
If the FMC is able to resolve a DNS query, it should be able to connect and register with the Cisco clouds as well. Registration with clouds allows the FMC to perform cloud lookups for malware disposition. As of this writing, Cisco uses cloud-sa.amp.sourcefire.com for Advanced Malware Protection (AMP) services.
This section assumes that you have fixed any connectivity or DNS issues you experienced in the last section. Here you will download the MSEXE file 7z1700.exe once again. You should notice a different type of event this time.
Figure 20-26 shows two different actions on file events for downloading the same file. Because the FMC can communicate with the Cisco clouds, FTD returns Malware Cloud Lookup instead of Cloud Lookup Timeout.
You can go to the File Summary view to find the malware dispositions. The Cisco clouds can return one of the following dispositions for a query:
![]() Malware: If Cisco determines that a file is malware
Malware: If Cisco determines that a file is malware
![]() Clean: If Cisco finds no malicious pattern on a file
Clean: If Cisco finds no malicious pattern on a file
![]() Unknown: If Cisco has not assigned a disposition (malware or clean) to a file
Unknown: If Cisco has not assigned a disposition (malware or clean) to a file
Figure 20-27 compares two types of dispositions—unknown and unavailable—for the 7z1700.exe file. Unknown confirms a successful cloud communication with no cloud-assigned category, whereas Unavailable indicates an issue with cloud communication.
Example 20-5 proves that the Firepower System checks its local cached disposition first before it sends the query to the Cisco clouds.
Example 20-5 Firepower Queries Cached Disposition Before Performing a Cloud Lookup
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
! Now, begin the transfer of an executable file.
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 using HW or preset rule order 2,
'Access Rule for File Policy', action Allow and prefilter rule 0
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 URL SI:
ShmDBLookupURL("http://172.16.100.100/files/7z1700.exe") returned 0
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File policy verdict is Type,
Malware, and Capture
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Unknown,
fileAction Malware Lookup, flags 0x01BDDA00, and type action Stop for type 21 of
instance 0
! First, Firepower System checks the cached disposition.
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Unknown
and flags 0x01BDDA00 for partial file of instance 0
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature cache query returned
Cache Miss for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with
disposition Cache Miss, spero Cache Miss, severity 0, and transmit Not Sent
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Pending
and flags 0x01BDDA00 for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d of instance 0
! Here, Firepower System performs a query to the cloud for disposition.
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature cache query returned
Neutral for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with
disposition Neutral, spero Cache Miss, severity 0, and transmit Not Sent
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d for spero with
flags 0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x01BDDA00 and status Exceeded Max Filesize
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Log and
flags 0x01BDDA00 for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d of instance 0
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 File malware event for
2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d named 7z1700.exe
with disposition Neutral and action Malware Lookup
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 Archive childs been processed No
192.168.1.200-58552 > 172.16.100.100-80 6 AS 4 I 0 Deleting session
^C
Caught interrupt signal
Exiting.
>
FTD Blocks Malware
This section shows how to analyze Firepower actions on malware. To emulate a malicious file, this chapter leverages an anti-malware test file available in the European Institute for Computer Antivirus Research (EICAR) website. Cisco does not develop or maintain this test file; however, you can download the latest copy from eicar.org. Alternatively, you can create a test file by your own using a text editor. It consists of the following characters:
X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
Figure 20-28 shows the creation of suspicious.exe, an anti-malware test file. The example uses notepad—a text editor for Microsoft Windows—to create the file. The file simply contains the test string. After you copy the string, save the file in the Windows executable (.exe) format.
To perform an experiment, at first, store the anti-malware test file (suspicious.exe) on a web server in your lab network. Then attempt to download the test file to a client computer by using a web browser. FTD should block the attempt.
Figure 20-29 demonstrates that FTD blocks a client’s attempt to download the suspicious.exe file. The cloud lookup returns a very high threat score for this anti-malware test file, because the cloud detects the test string within the file and considers it malware.
Example 20-6 details the operations of an FTD device when it analyzes a file, performs a cloud lookup, and blocks the file based on its malware disposition.
Example 20-6 Blocking a File Due to Its Malware Disposition
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
! First, client attempts to download the suspicious.exe file using a web browser.
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 using HW or preset rule order 2,
'Access Rule for File Policy', action Allow and prefilter rule 0
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 URL SI: ShmDBLookupURL
("http://172.16.100.100/files/suspicious.exe") returned 0
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File policy verdict is Type,
Malware, and Capture
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Unknown,
fileAction Malware Lookup, flags 0x0025DA00, and type action Stop for type 273 of
instance 0
! Firepower System performs a lookup on cached disposition before sending a query to
the cloud.
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature cache
query returned Cache Miss for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f with disposition Cache Miss, spero Cache Miss,
severity 0, and transmit Sent
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f with flags
0x0025DA00 and status Smaller than Min Filesize
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict
Pending and flags 0x0025DA00 for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f of instance 0
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature cache
query returned Cache Miss for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f with disposition Cache Miss, spero Cache Miss,
severity 0, and transmit Sent
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f with flags 0x0025DA00 and status Smaller than Min Filesize
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict
Pending and flags 0x0025DA00 for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f of instance 0
! At this stage, FMC receives a malware disposition from the cloud. FTD acts on the
file based on the File Policy.
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature cache
query returned Malware for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f with disposition Malware, spero Cache Miss, severity
76, and transmit Sent
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f with flags
0x0025DA00 and status Smaller than Min Filesize
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict
Reject and flags 0x0025DA00 for 275a021bbfb6489e54d471899f7db9d1663f-
c695ec2fe2a2c4538aabf651fd0f of instance 0
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 File malware event for
275a021bbfb6489e54d471899f7db9d1663fc695ec2fe2a2c4538aabf651fd0f named suspicious.
exe with disposition Malware and action Block Malware
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 Archive childs been processed No
192.168.1.200-58566 > 172.16.100.100-80 6 AS 4 I 0 Deleting session
.
<Output Omitted for Brevity>
.
^C
Caught interrupt signal
Exiting.
>
Overriding a Malware Disposition
If you disagree with a file disposition—whether it is analyzed locally by the FTD device or dynamically by the cloud—the FMC allows you to override an outcome by using a file list. There are two types of file list:
![]() Clean list: If FTD blocks a file due to its malware disposition, you could manually allow the file by adding it to the clean list. This lets the file go through FTD moving forward.
Clean list: If FTD blocks a file due to its malware disposition, you could manually allow the file by adding it to the clean list. This lets the file go through FTD moving forward.
![]() Custom detection list: If the local or dynamic analysis engine identifies a file as clean or unknown and, therefore, FTD allows the file to transfer, you could change this behavior by adding the file to the custom detection list. In the future, if a client attempts to transfer the same file, FTD will block it, regardless of the disposition by the local or dynamic analysis engine.
Custom detection list: If the local or dynamic analysis engine identifies a file as clean or unknown and, therefore, FTD allows the file to transfer, you could change this behavior by adding the file to the custom detection list. In the future, if a client attempts to transfer the same file, FTD will block it, regardless of the disposition by the local or dynamic analysis engine.
In short, the clean list allows you to whitelist a file, whereas you can blacklist a file by adding it to the custom detection list.
To deploy a new file list, the FTD device must be running a file policy with the following rule conditions:
![]() The rule matches the same file type as your selected file format for a file list. For example, if you want to add an executable file to the clean or custom detection list, the rule on a file policy needs to match the executable file types as well.
The rule matches the same file type as your selected file format for a file list. For example, if you want to add an executable file to the clean or custom detection list, the rule on a file policy needs to match the executable file types as well.
![]() The action of the rule is set to one of the malware analysis rules, such as malware cloud lookup or block malware.
The action of the rule is set to one of the malware analysis rules, such as malware cloud lookup or block malware.
Once these conditions are fulfilled, you can add a file to a file list in two ways: by using the right-click context menu or by using a file list object. The context menu allows you to add a file on the fly.
Figure 20-30 shows the addition of the 7z1700.exe file to the custom detection list through the context menu.
Figure 20-31 shows the navigation to the file list object configuration page. Besides adding the files and their SHA hash values, this page allows you to manage any previously added files.
Once you add your desired file to a file list, you can redeploy the file policy to FTD. Then you can attempt to redownload the file you have just added. If you added the file to the custom detection list, the client should no longer be able to download the file.
Figure 20-32 confirms the block of the latest download attempt due to custom detection. This time, FTD blocks the same 7z1700.exe file that was allowed earlier due to unavailable and unknown dispositions.
Example 20-7 displays the debugging messages for a Custom Detection Block event. Here, FTD blacklists the 7z1700.exe file due to its addition to the custom detection list.
Example 20-7 Adding a File to the Custom Detection List Blacklists the File
> system support firewall-engine-debug
Please specify an IP protocol: tcp
Please specify a client IP address: 192.168.1.200
Please specify a client port:
Please specify a server IP address:
Please specify a server port:
Monitoring firewall engine debug messages
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 New session
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 using HW or preset rule order 2,
'Access Rule for File Policy', action Allow and prefilter rule 0
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 allow action
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 URL SI:
ShmDBLookupURL("http://172.16.100.100/files/7z1700.exe") returned 0
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File policy verdict is Type,
Malware, and Capture
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File type verdict Unknown,
fileAction Malware Lookup, flags 0x01BDDA00, and type action Stop for type 21 of
instance 0
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Unknown
and flags 0x01BDDA00 for partial file of instance 0
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File signature blacklist
2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File signature reserved file data
of 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d with flags
0x00A5DA00 and status Exceeded Max Filesize
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File signature verdict Reject
and flags 0x00A5DA00 for 2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485dd-
b307ee982d of instance 0
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 File malware event for
2c8637b812f7a47802f4f91f8bfaccb978df9b62de558d038485ddb307ee982d named 7z1700.exe
with disposition Custom and action Custom Block
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 Archive childs been processed No
192.168.1.200-58588 > 172.16.100.100-80 6 AS 4 I 0 Deleting session
^C
Caught interrupt signal
Exiting.
>
The FMC allows you to track and visualize the path of a file by using the network file trajectory feature. This feature can save you analysis time when you want to determine the spread of a suspicious file. You can look up a particular file by entering its SHA-256 hash value on the Files > Network Trajectory page. Alternatively, on the file event page, you can click a disposition icon in the SHA256 column to open the file trajectory page (as shown in the Figure 20-32).
Figure 20-33 shows the network file trajectory for the 7z1700.exe file. Throughout the exercises on this chapter, the file has gone through various disposition states that you can see on this page.
Summary
Cisco integrates the Advanced Malware Protection (AMP) technology with the Firepower technology. This chapter explains how these technologies work together to help you detect and block the spread of infected files across your network. This chapter also shows the configurations and operations of a file policy on a Firepower system, and it demonstrates various logs and debugging messages that are useful for determining any issues with cloud lookup and file disposition.
Quiz
1. Which of the following does not require a Malware license?
a. Sending a file to the cloud for dynamic analysis
b. Enabling a local analysis engine
c. Performing a cloud lookup without blocking a file
d. Blocking a file transfer based on its file format
2. Which type of analysis requires a connection to the cloud?
a. Spero
b. Sandbox
c. High-fidelity
d. Prefilter
3. Which of the following is recommended?
a. Use the Reset Connection option on a file rule.
b. Avoid storing all the files that FTD detects.
c. Limit the file size for analysis.
d. All of the above.
4. Which of the following is not true?
a. FTD can interrupt traffic in case of a cloud lookup failure.
b. A file policy uses the adaptive profile feature.
c. The FMC sends a query to the cloud to detect a file type.
d. The FMC connects to the cloud to obtain new signatures for malware.