You can use the information in this introduction to learn about the types of interfaces supported on Cisco routers and access servers and to locate configuration information for various types of interfaces.
For a complete description of the interface commands used in this book, see Chapter 4, "Configuring Interface Commands." To locate documentation of other commands that appear in this introduction, you can search online at www.cisco.com .
This introduction contains general information that applies to all interface types; it includes the following sections:
Interface Types Supported on Cisco Routers
Understanding Interface Configuration
Understanding Subinterfaces
Configuring Features Available on Any Interface
Understanding OIR
Understanding Fast Switching Support
Monitoring and Maintaining the Interface
For examples of configuration commands shown in this introduction, see the section "Interface Configuration Examples" later in this chapter.
For information about a specific type of interface, refer to the chapter indicated here:
|
For this interface type… |
And these tasks… |
See this chapter… |
|---|---|---|
|
LAN interfaces |
Configure an Ethernet or Fast Ethernet interface Configure Fast EtherChannel Configure a Fiber Distributed Data Interface Configure a hub interface Configure a LAN Extender interface Configure a Token Ring interface | |
|
Serial interfaces |
Configure a High-Speed Serial Interface Configure a synchronous serial interface Configure a channelized T3 interface processor Configure PA-E3 and PA-2E3 serial port adapters Configure PA-T3 and PA-2T3 serial port adapters Configure a Packet OC-3 interface Configure automatic protection switching of packet-over-SONET circuits Configure serial interfaces for CSU/DSU service modules Configure a low-speed serial interface | |
|
Virtual (or logical) interfaces |
Configure a loopback interface Configure a null interface Configure a tunnel interface |
Cisco routers support two types of interfaces: physical and virtual interfaces. The types of physical interfaces on a device depend on its interface processors or port adapters. The virtual interfaces that Cisco routers and access servers support include subinterfaces and IP tunnels.
Cisco routers and access servers support the following types of interfaces:
Asynchronous serial
Asynchronous Transfer Mode (ATM)
Automatic protection switching (APS) of packet-over-SONET (POS)
Channelized E1
Channelized T1
Channelized T3
Dialer
Ethernet
Fast Ethernet
Fiber Distributed Data Interface (FDDI)
Fractional T1/T1
High-Speed Serial Interface (HSSI)
ISDN Basic Rate Interface (BRI)
ISDN Multiple Basic Rate Interface (MBRI)
ISDN Primary Rate Interface (PRI)
LAN Extender
Loopback
Low-speed serial
Null
Packet OC-3
PA-E3 and PA-2E3
PA-T3 and PA-2T3
Synchronous serial
Token Ring
Tunnel
In addition, the Cisco IOS software supports subinterfaces. For hardware technical descriptions and information about installing interfaces, refer to the hardware installation and maintenance publication for your product. For command descriptions and usage information, see Chapter 4, "Configuring Interface Commands."
These general instructions apply to all interface configuration processes. Begin interface configuration in global configuration mode. To configure an interface, follow these steps:
Use the configure EXEC command at the privileged EXEC prompt to enter global configuration mode.
Start configuring the interface by using the interface command. Identify the interface type followed by the number of the connector or interface card. These numbers are assigned at the time of installation (at the factory) or when the cards are added to a system. You can display these numbers using the show interfaces EXEC command. A report is provided for each interface that the device supports, as shown in the following partial sample display.
Router# show interfaces Serial 0 is administratively down, line protocol is down Hardware is MCI Serial MTU 1500 bytes, BW 1544 Kbit, DLY 20000 usec, rely 255/255, load 1/255 Encapsulation HDLC, loopback not set, keepalive set (10 sec)Use the show hardware EXEC command to see a list of the system's software and hardware.
To begin configuring serial interface 0, you add the following line to the configuration file:
interface serial 0
Note
It is not necessary to add a space between the interface type and interface number. For example, in the preceding line you can specify either serial 0 or serial0. The command will work either way.
Follow each interface command with the interface configuration commands your particular interface requires. The commands you use define the protocols and applications that will run on the interface. The commands are collected and applied to the interface command until you use another interface command or a command that is not an interface configuration command, or until you type the Ctrl-Z sequence to get out of configuration mode and return to privileged EXEC mode.
Once an interface is configured, you can check its status by using the EXEC Show Commands listed in the tables in the "Monitoring and Maintaining the Interface" section later in this chapter.
Note
Configuring channelized T1 and E1 interfaces requires additional steps. When you configure channelized T1 or channelized E1, you must first define the channels and the time slots that comprise the channels. Use the controller t1 and the channel-group controller configuration commands; then configure the virtual serial interfaces using the interface serial global configuration commands.
Configuring multiple virtual interfaces, or subinterfaces, on a single physical interface allows greater flexibility and connectivity on the network. A subinterface is a mechanism that allows a single physical interface to support multiple logical interfaces or networks. That is, several logical interfaces or networks can be associated with a single hardware interface. Subinterfaces are implemented in various WAN and LAN protocols, including ATM, Frame Relay, SMDS, X.25, and Novell IPX.
Note
The Cisco IOS software can support a maximum of 300 interfaces and subinterfaces.
The following sections describe optional tasks that you can perform on any type of interface:
Adding a Description for an Interface
Configuring MOP
Controlling Interface Hold-Queue Limits
Setting Bandwidth
Setting Interface Delay
Adjusting Timers
Limiting Transmit Queue Size
Adjusting Maximum Packet Size or MTU Size
You can add a description about an interface to help you remember what is attached to it. This description is meant solely as a comment to help identify what the interface is being used for. The description will appear in the output of the following commands: show configuration, show system:running-config, and show interfaces. When you add a description for a T1 controller interface, it will appear in the output of the show controllers t1 and show system:running-config commands.
To add a description for any interface except a T1 or E1 controller interface, use the following command in interface configuration mode. To add a description for a T1 or E1 controller in Cisco 4500 series, Cisco 7200 series, or Cisco 7500 series routers, use the following command in controller configuration mode:
|
Command |
Purpose |
|---|---|
|
description string |
Adds a description for an interface. |
For examples of adding interface descriptions, see the section "Interface Description Examples" later in this chapter.
You can enable Maintenance Operation Protocol (MOP) on an interface by using the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
mop enabled |
Enables MOP. |
You can enable an interface to send out periodic MOP system identification messages on an interface by using the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
mop sysid |
Enables MOP message support. |
Each interface has a hold-queue limit. This limit is the number of data packets that the interface can store in its hold queue before rejecting new packets. When the interface empties one or more packets from the hold queue, it can accept new packets again. You can specify the hold-queue limit of an interface in interface configuration mode by using the following command:
|
Command |
Purpose |
|---|---|
|
hold-queue length {in | out} |
Specifies the maximum number of packets allowed in the hold queue. |
Higher-level protocols use bandwidth information to make operating decisions. For example, IGRP uses the minimum path bandwidth to determine a routing metric. TCP adjusts initial retransmission parameters based on the apparent bandwidth of the outgoing interface. Use the following command in interface configuration mode to set a bandwidth value for an interface:
|
Command |
Purpose |
|---|---|
|
bandwidth kilobits |
Sets a bandwidth value. |
The bandwidth setting is a routing parameter only; it does not affect the physical interface.
Higher-level protocols might use delay information to make operating decisions. For example, IGRP can use delay information to differentiate between a satellite link and a land link. To set a delay value for an interface, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
delay tens-of-microseconds |
Sets a delay value for an interface. |
Setting the delay value sets an informational parameter only; you cannot adjust the actual delay of an interface with this configuration command.
To adjust the frequency of update messages, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
keepalive [seconds] |
Adjusts the frequency with which the Cisco IOS software sends messages to itself (Ethernet and Token Ring) or to the other end (HDLC-serial and PPP-serial links) to ensure that a network interface is alive for a specified interface. |
You also can configure the keepalive interval, the frequency at which the Cisco IOS software sends messages to itself (Ethernet and Token Ring) or to the other end (HDLC-serial or PPP-serial), to ensure that a network interface is alive. The interval in some previous software versions was 10 seconds; it is now adjustable in one-second increments down to one second. An interface is declared down after three update intervals have passed without receiving a keepalive packet.
When adjusting the keepalive timer for a very low bandwidth serial interface, large packets can delay the smaller keepalive packets long enough to cause the line protocol to go down. You might need to experiment to determine the best value.
You can control the size of the transmit queue available to a specified interface on the MCI and SCI cards. To limit the size, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
tx-queue-limit number |
Limits the size of the transmit queue. |
Each interface has a default maximum packet size or maximum transmission unit (MTU) size. This number generally defaults to 1500 bytes. On serial interfaces, the MTU size varies, but cannot be set smaller than 64 bytes. To adjust the maximum packet size, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
mtu bytes |
Adjusts the maximum packet size or MTU size. |
Caution
Changing an MTU size on a Cisco 7500 series router results in recarving of buffers and resetting of all interfaces. The following message is displayed:%RSP-3-Restart:cbus complex.
The online insertion and removal (OIR) feature—supported on the Cisco 7200 series and the Cisco 7500 series routers only—allows you to remove and replace interface processors while the system is online. You can shut down the interface processor before removal and restart it after insertion without causing other software or interfaces to shut down.
Note
Do not remove or install more than one interface processor at one time. After a removal or installation, observe the LEDs before continuing.
You do not need to notify the software that you are going to remove or install an interface processor. When the route processor is notified by the system that an interface processor has been removed or installed, it stops routing and scans the system for a configuration change. All interface processors are initialized, and each interface type is verified against the system configuration; then the system runs diagnostics on the new interface. There is no disruption to normal operation during interface processor insertion or removal.
Only an interface of a type that has been configured previously will be brought online; others require configuration. If a newly installed interface processor does not match the system configuration, the interface is left in an administratively down state until the system operator configures the system with the new interfaces.
Hardware (MAC-level) addresses for all interfaces on the Cisco 7500 series routers are stored on an electronically erasable programmable read-only memory (EEPROM) component in the Route Processor (RP) instead of on the individual interface boards. On the Cisco 7500 series routers, an address allocator in the EEPROM contains a sequential block of 40 addresses (5 interface slots times a maximum of 8 possible ports per slot); each address is assigned to a specific slot and port address in the chassis, regardless of how the interfaces are configured. On the Cisco 7200 series, hardware addresses are stored in a midplane EEPROM that supports 1024 addresses per box.
Storage of hardware addresses in EEPROM allows interfaces to be replaced online without requiring the system to update switching tables and data structures. Regardless of the types of interfaces installed, the hardware addresses do not change unless you replace the system RP. If you do replace the RP, the hardware addresses of all ports change to those specified in the address allocator on the new RP.
Switching is the process by which packets are forwarded. The Cisco IOS software supports multiple methods of switching. Cisco routers fast switch Layer 2 Forwarding (L2F) traffic. In stack group environments in which some L2F traffic is offloaded to a powerful router, fast switching provides improved scalability.
You can perform the tasks in the following sections to monitor and maintain the interfaces:
Monitoring Interface and Controller Status
Monitoring the T1 or E1 Controller
Monitoring and Maintaining CSU/DSU Service Modules
Monitoring the LAN Extender Interface
Monitoring and Maintaining a Hub
Monitoring Tunnels
Clearing and Resetting the Interface
Shutting Down and Restarting the Interface
Configuring Loopback Detection
Running Interface Loopback Diagnostics
Enabling Loopback Testing of Fractional T1/T1
The software contains commands that you can use at the EXEC prompt to display information about the interface, including the version of the software and the hardware, the controller status, and statistics about the interfaces. The following table lists some of the interface monitoring commands. (You can display the full list of show commands by using the show ? command at the EXEC prompt.) These commands are fully described in Chapter 4, "Configuring Interface Commands."
Use the following commands in EXEC mode:
|
Command |
Purpose |
|---|---|
|
show async status show interfaces async |
Displays the status of the asynchronous interface. |
|
show compress |
Displays compression statistics on a serial interface. |
|
show controllers [bri | cbus | fddi | lance | mci | serial | token] |
Displays current internal status information for the interface controller cards. |
|
show controllers cbus |
Displays information about the Switch Processor (SP) controller on the Cisco 7500 series routers. |
|
show controllers [e1 | ethernet | fastethernet | fddi | serial | t1 | token] |
Displays current internal status information for the interface controller cards. |
|
show controllers [ethernet | fastethernet | fddi | serial | token] |
Displays current internal status information for the interface controller cards on the Cisco 7200 series and Cisco 7500 series routers. |
|
show diagbus [slot] |
Displays diagnostic information about the controller, interface processor, and port adapters associated with a specified slot of a Cisco 7200 series or Cisco 7500 series router. |
|
show interfaces[type number] [first] [last] [accounting] show interfaces[type slot/port] [accounting] show interfaces[type slot/port-adapter/port] [accounting] |
If accounting is configured, displays the number of packets of each protocol type that has been sent through the interface. Displays the number of packets for Cisco 7500 series with a POS Interface Processor. Displays the number of packets for the Cisco 7500 series with VIP or VIP2 cards. |
|
show interfaces posi [slot/port] |
Displays information about the Cisco 7500 series with a POS Interface Processor. |
|
show interfaces async [number] [accounting] |
Displays the number of packets of each protocol type that has been sent through the asynchronous serial line. |
|
show system:running-config |
Displays the currently running configuration in RAM. |
|
show rif |
Displays the current contents of the routing information field (RIF) cache. |
|
show protocols |
Displays the global (systemwide) and interface-specific status of any configured Level 3 protocol. |
|
show version |
Displays the hardware configuration, the software version, the names and sources of configuration files, and the boot images. |
This section applies to channelized T1 or E1 interfaces. Because the T1 or E1 link itself is viewed as the controller, use the following commands in EXEC mode to display information about activity on the T1 or E1 line:
|
Command |
Purpose |
|---|---|
|
show controller t1 |
Displays information about the T1 link. |
|
show controller e1 |
Displays information about the E1 link. |
Alarms, line conditions, and other errors are displayed. The data is updated every 10 seconds. Every 15 minutes, the cumulative data is stored and retained for 24 hours. This means that, at any one time, up to 96 15-minute accumulations are counted in the data display.
This section describes how to monitor and maintain channel service unit/digital service unit (CSU/DSU) modules. Tasks involved to monitor and maintain service modules are described in these sections:
Performing a Self-Test
Displaying a Performance Report
Performing Loopback Tests
Resetting the CSU/DSU
To perform a self-test on the integrated CSU/DSU, use the following command in privileged EXEC mode:
|
Command |
Purpose |
|---|---|
|
test service-module interface |
Performs a self-test. Specifies the interface type and number. |
This command cannot be used if a DTE, line, or remote loopback is in progress. A series of tests are performed on the CSU/DSU, including a ROM checksum test, a RAM test, an EEPROM checksum test, a flash checksum test, and a DTE loopback with an internal pattern test. This self-test is also performed at power on.
Data transmission is interrupted for five seconds when you issue this command. To view the output of the most recent self-test, enable the show service-module command.
To display the performance report for an integrated CSU/DSU, use one of the following commands in privileged EXEC mode:
|
Command |
Purpose |
|---|---|
|
show service-module interface |
Displays a performance report. Choose either serial interface 1 or 0. |
|
show service-module interface performance-statistics [interval-range] |
Displays the CSU/DSU performance statistics for the past 24 hours. This command applies only to the FT1/T1 module. |
The interval-range value specifies the number of 15-minute intervals displayed in the report. You can choose a range from 1 to 96, where each value represents the CSU/DSU activity performed in that 15-minute interval. For example, a range of 2 to 3 displays the performance statistics for the intervals two and three.
You can loop packets back to the network from the integrated CSU/DSU and loop packets through a local CSU/DSU to a remote CSU/DSU.
To loop data received from the line at the integrated CSU/DSU and loop packets back to the line, use the following commands in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback line |
Performs loopback on the network at a point physically near the CSU/DSU interface. |
|
loopback line payload |
Performs loopback on the network at a point physically near the interface between the CSU/DSU and the router. |
Packets are looped from an incoming network transmission back into the network at a CSU or DSU loopback point.
When the loopback line command is configured on the two-wire, 56-kbps CSU/DSU module or the four-wire, 56/64-kbps CSU/DSU modules installed on a Cisco 2524 or Cisco 2525 router, the network data loops back at the CSU and the router data loops back at the DSU. If the CSU/DSU is configured for switched mode, you must have an established connection to perform a payload-line loopback. When the loopback line payload command is configured, the CSU/DSU module loops the data through the DSU portion of the module. Data is not looped back to the serial interface.
If you enable the loopback line command on the fractional T1/T1 module, the CSU/DSU performs a full-bandwidth loopback through the CSU portion of the module and data transmission through the serial interface is interrupted for the duration of the loopback. No reframing or corrections of bipolar violation errors or cyclic redundancy check (CRC) errors are performed. When you configure the loopback line payload command on the FT1/T1 module, the CSU/DSU performs a loopback through the DSU portion of the module. The loopback line payload command reframes the data link, regenerates the signal, and corrects bipolar violations and Extended Super Frame CRC errors.
When performing a T1-line loopback with Extended Super Framing, communication over the facility's data link is interrupted but performance statistics are still updated. To show interfaces currently in loopback operation, use the show service-module EXEC command.
To loop packets back to DTE from within the local CSU/DSU, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback dte |
Loops packets to DTE. |
Packets are looped from within the CSU/DSU back to the serial interface of the router. Send a test ping to see if the packets successfully looped back. To cancel the loopback test, use the noloopbackdte command.
When using the four-wire, 56/64-kbps CSU/DSU module, an out-of-service signal is transmitted to the remote CSU/DSU.
This command applies only when the remote CSU/DSU device is configured for this function. It is used for testing the data communication channels along with or without remote CSU/DSU circuitry. The loopback is usually performed at the line port, rather than the DTE port, of the remote CSU/DSU.
On the integrated FT1/T1 CSU/DSU module installed on a Cisco 2524 and Cisco 2525 router, the loopback remote full command sends the loopup code to the remote CSU/DSU. The remote CSU/DSU should perform a full-bandwidth loopback through the CSU portion of the module. The loopback remote payload command sends the loopup code on the configured timeslots while maintaining the D4-Extended Super Framing. The remote CSU/DSU performs the equivalent of a loopback line payload request. The remote CSU/DSU loops back only those timeslots that are configured of the remote end. This loopback reframes the data link, regenerates the signal, and corrects bipolar violations and Extended Super Frame CRC errors. The loopback remote smart-jack command sends a loopup code to the remote smart jack. You cannot put the local smart jack into loopback.
To loop packets on the integrated FT1/T1 CSU/DSU module, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback remote {full | payload | smart-jack} [0in1 | 1in1 | 1in2 | 1in5 | 1in8 | 3in24 | qrw | user-pattern 24bit-binary value] |
Loops packets at a remote CSU/DSU using the fractional T1/T1 CSU/DSU module. |
Failure to loop up or initiate a remote loopback request could be caused by enabling the noservice-module t1 remote-loopback command or by having an alternate remote-loopback code configured on the remote end. When the loopback is terminated, the result of the pattern test is displayed.
Note
If the FT1/T1 CSU/DSU module is configured to provide internal clocking, the module ceases to generate clocking when it is placed into loopback.
This command applies only when the remote CSU/DSU device is configured for this function. It is used for testing the data communication channels along with or without remote CSU/DSU circuitry. The loopback is usually performed at the line port, rather than the DTE port, of the remote CSU/DSU.
On the two- and four-wire, 56/64-kbps CSU/DSU modules, an active connection is required before a loopup can be initiated while in switched mode. When transmitting V.54 loopbacks, the remote device is commanded into loopback using V.54 messages. Failure to loop up or initiate a remote loopback request could be caused by enabling the no service-module 56k remote-loopback command.
To loop packets at the remote CSU/DSU, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback remote [2047 | 511 | stress-pattern pattern number] |
Loops packets at a remote CSU/DSU using the two- and four-wire, 56/64-kbps CSU/DSU modules. |
To show interfaces currently in loopback operation, use the show interfaces loopback EXEC command.
To reset the CSU/DSU, use the following command in privileged EXEC mode:
|
Command |
Purpose |
|---|---|
|
clear service-module interface |
Resets the CSU/DSU. Specifies the interface type and number. |
Use this command only in severe circumstances (for example, when the router is not responding to a CSU/DSU configuration command).
This command terminates all DTE and line loopbacks that are locally or remotely configured. It also interrupts data transmission through the router for up to 15 seconds. The software performs an automatic software reset in case of two consecutive configuration failures.
The CSU/DSU module is not reset with the clear interface command.
Caution
If you experience technical difficulties with your router and intend to contact customer support, refrain from using this command. The command erases the router's past CSU/DSU performance statistics. To clear only the CSU/DSU performance statistics, issue the clear counters command.
To monitor the LAN Extender interface, the Ethernet interface that resides on the LAN Extender, the serial interface that resides on the LAN Extender, or the serial interface connected to the LAN Extender, use one or more of the following commands at the EXEC prompt:
|
Command |
Purpose |
|---|---|
|
show controllers lex [number] or show controllers lex [slot/port] |
Displays hardware and software information about the LAN Extender. Displays information on the Cisco 7500 series routers. |
|
show interfaces lex number [ethernet | serial] |
Displays statistics about the LAN Extender interface. |
|
show interfaces serial number [accounting] show interfaces serial slot/port [accounting] |
Displays statistics about the serial interface on the host router that is physically connected to the LAN Extender. Displays statistics on the Cisco 7500 series routers. |
You can perform the tasks in the following sections to monitor and maintain the hub:
Shutting Down the Hub Port
Resetting the Hub or Clearing the Hub Counters
Monitoring the Hub
To shut down or disable a hub port, use the following commands beginning in global configuration mode:
|
Command |
Purpose |
|---|---|
|
hub ethernet number port [end-port] |
Specifies the hub number and the hub port (or range of hub ports) and places you in hub configuration mode. |
|
shutdown |
Shuts down the hub port. |
See the examples of shutting down a hub port at the end of Chapter 1, "Configuring LAN Interfaces."
To reset the hub or clear the hub counters, use one of the following commands in EXEC mode:
|
Command |
Purpose |
|---|---|
|
clear hub ethernet number |
Resets and reinitializes the hub hardware. |
|
clear hub counters [ethernet number [port [end-port]]] |
Clears the hub counters displayed by the show hub command. |
You can use any of the following commands in EXEC mode to monitor the IP tunnels you have configured:
|
Command |
Purpose |
|---|---|
|
show interfaces tunnel unit [accounting] |
Lists tunnel interface information. |
|
show protocol route |
Lists the routes that go through the tunnel. |
|
show ip route |
Lists the route to the tunnel destination. |
To clear the interface counters shown with the show interfaces command, use any of the following commands at the EXEC prompt:
|
Command |
Purpose |
|---|---|
|
clear counters [type number] [ethernet | serial] |
Clears the interface counters. |
|
clear counters fastethernet number |
Clears interface counters for the FastEthernet NIM on the Cisco 4000 series or Cisco 4500 series routers. |
|
clear counters [type slot/port] |
Clears interface counters for the Cisco 7200 series routers. |
|
clear counters [type slot/port-adaptor] |
Clears interface counters for the Cisco 7500 series with VIP or VIP2 Interface Processors. |
The clear counters command clears all the current interface counters from the interface unless the optional arguments are specified to clear only a specific interface type from a specific slot and port number.
Note
This command will not clear counters retrieved using SNMP; it will clear only those seen with the EXEC show interfaces command.
Use the following commands in EXEC mode to clear and reset interfaces. Under normal circumstances, you do not need to clear the hardware logic on interfaces.
|
Command |
Purpose |
|---|---|
|
clear interface type number |
Resets the hardware logic on an interface. |
|
clear line [number] |
Resets the hardware logic on an asynchronous serial line. |
|
clear rif-cache |
Clears the entire Token Ring RIF cache. |
You can disable an interface. Doing so disables all functions on the specified interface and marks the interface as unavailable on all monitoring command displays. This information is communicated to other network servers through all dynamic routing protocols. The interface will not be mentioned in any routing updates. On serial interfaces, shutting down an interface causes the DTR signal to be dropped. On Token Ring interfaces, shutting down an interface causes the interface to deinsert from the ring. On FDDIs, shutting down an interface causes the optical bypass switch, if present, to go into bypass mode.
To shut down an interface and then restart it, use the following commands in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
shutdown |
Shuts down an interface. |
|
no shutdown |
Re-enables an interface. |
To check whether an interface is disabled, use the EXEC command show interfaces. An interface that has been shut down is shown as administratively down in the show interfaces command display. See examples in the section "Interface Shutdown Examples" later in this chapter.
One reason to shut down an interface is if you want to change the electrical interface type or mode of a Cisco 7500 series port online. You replace the serial adapter cable, use software commands to restart the interface, and, if necessary, reconfigure the port for the new interface. At system startup or restart, the FSIP polls the interfaces and determines the electrical interface type of each port (according to the type of port adapter cable attached). However, it does not necessarily repoll an interface when you change the adapter cable online. To ensure that the system recognizes the new interface type, shut down using the shutdown command and reenable the interface after changing the cable. Refer to your hardware documentation for more details.
When an interface has a backup interface configured, it is often desirable that the backup interface be enabled when the primary interface is either down or in loopback. By default, the backup is only enabled if the primary interface is down. By using the down-when-looped command, the backup interface will also be enabled if the primary interface is in loopback. To achieve this condition, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
down-when-looped |
Configures an interface to tell the system it is down when loopback is detected. |
You should not have loopback detection configured when testing an interface with the loopback command because packets will not be transmitted out of the interface that is being tested.
You can use a loopback test on lines to detect and distinguish equipment malfunctions between line and modem or CSU/DSU problems on the network server. If correct data transmission is not possible when an interface is in loopback mode, the interface is the source of the problem. The DSU might have similar loopback functions you can use to isolate the problem if the interface loopback test passes. If the device does not support local loopback, this function will have no effect.
You can specify hardware loopback tests on the Ethernet and synchronous serial interfaces and on all Token Ring interfaces that are attached to CSU/DSUs and that support the local loopback signal. The CSU/DSU acts as a data communications equipment (DCE) device; the router or access server acts as a data terminal equipment (DTE) device. The local loopback test generates a CSU loop—a signal that goes through the CSU/DSU to the line and then back through the CSU/DSU to the router or access server. The ping command can also be useful during loopback operation.
The loopback tests are available on the following interfaces:
HSSI, including the High-Speed Communications Interface (HSCI) card ribbon cable
Cisco Multiport Communications Interface (MCI) and Cisco Serial Communication Interface (SCI) synchronous serial interfaces
MCI and Cisco Multiport Ethernet Controller (MEC) Ethernet interfaces; an Ethernet loopback server is also provided on the Ethernet interfaces
Ethernet loopback server
Channelized E1 interfaces (local loopback only)
Channelized T1 interfaces (local and remote loopback)
Fractional T1/T1 interfaces
Token Ring interfaces
Channelized E1 controller and interface (local loopback only)
Channelized T1 controller and interface (local and remote loopback)
Troubleshooting channelized E1 and channelized T1
The following sections describe each test.
Note
Loopback does not work on an X.21 DTE because the X.21 interface definition does not include a loopback definition.
The HSSI allows you to perform the tasks described in these sections:
Enabling the Loopback Test to the DTE
Enabling the Loopback Test through the CSU/DSU
Enabling the Loopback Test over a Remote DS3 Link
These tests apply only when the device supports them and they are used to check the data communications channels. The tests are usually performed at the line port rather than the DTE port of the remote CSU/DSU.
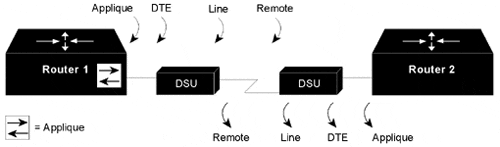
The internal loopback concepts are illustrated in Figure I-1.
You can loop packets to DTE within the CSU/DSU at the DTE interface when the device supports this function. Doing so is useful for testing the DTE-to-DCE cable. To loop the packets to DTE, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback dte |
Loops packets to DTE internally. |
You can loop packets completely through the CSU/DSU to configure a CSU loop when the device supports this feature. Doing so is useful for testing the DCE device (CSU/DSU) itself. To configure a CSU loop, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback line |
Loops packets completely through the CSU/DSU. |
You can loop packets through the CSU/DSU, over the digital signal level 3 (DS3) link, to the remote CSU/DSU, and back. To do so, use the following command in interface configuration mode:
|
Command |
Purpose |
|---|---|
|
loopback remote |
Loops packets through the CSU/DSU to a remote CSU/DSU over the DS3 link. |
This command applies only when the device supports the remote function. It is used for testing the data communication channels. The loopback usually is performed at the line port, rather than the DTE port, of the remote CSU/DSU.
The router software provides an Ethernet loopback server that supports Digital Equipment Corporation (Digital), Intel, and Xerox systems specified by the "blue book," a joint specification written by Digital, Intel, and Xerox that defines the Ethernet protocol. The loopback server responds to forward data loopback messages sent either to the server's MAC address or to the broadcast address. Currently, the Ethernet loopback server does not respond to the loopback assistance multicast address.
Use the Ethernet loopback server to test communications between your internetworking products and Digital systems that do not support the IP ping command, such as DECnet-only VMS systems.
To originate a loop test on your VMS system with a Cisco server, use the Digital Network Control Program (NCP) command loop circuit. For more information about the loop circuit command, consult the DECnet VAX documentation. Cisco network servers support all options that can be specified by the VMS hosts.
Examples are included in this section to illustrate configuration tasks described in this chapter. The following configuration examples are provided:
Enabling Interface Configuration Examples
Interface Description Examples
Interface Shutdown Examples
The following example illustrates how to begin interface configuration on a serial interface. It assigns Point-to-Point Protocol (PPP) encapsulation to serial interface 0.
interface serial 0 encapsulation ppp
The same example on a Cisco 7500 series router requires the following commands:
interface serial 1/0 encapsulation ppp
This example shows how to configure the access server so that it will use the default address pool on all interfaces except interface 7, on which it will use an address pool called lass:
ip address-pool local ip local-pool lass 172.30.0.1 async interface interface 7 peer default ip address lass
The following example illustrates how to add a description about an interface that will appear in configuration files and monitoring command displays:
interface ethernet 0 description First Ethernet in network 1 ip address 101.13.15.78 255.255.255.0
The following example for a Cisco 7500 series router describes an administration network attached to the Ethernet processor in slot 2 at port 4:
interface ethernet 2/4 description 2nd floor administration net
The following example turns off the Ethernet interface in slot 2 at port 4:
interface ethernet 2/4 shutdown
The following example turns the interface back on:
interface ethernet 2/4 no shutdown
The following example shuts down a Token Ring interface:
interface tokenring 0 shutdown
The following example shuts down a T1 circuit number 23 running on a Cisco 7500 series router:
interface serial 4/0:23 shutdown
The following example shuts down the entire T1 line physically connected to a Cisco 7500 series router:
controller t1 4/0 shutdown
The Cisco IOS 12.0 Reference Library books are Cisco documentation that describe the tasks and commands necessary to configure and maintain your Cisco IOS network.
The Cisco IOS software bookset is intended primarily for users who configure and maintain access servers and routers, but are not necessarily familiar with the tasks, the relationship between tasks, or the commands necessary to perform particular tasks.
The Cisco IOS 12.0 Reference Library consists of 11 books, including this one. Each book contains technology-specific configuration chapters with corresponding command reference chapters. Each configuration chapter describes Cisco's implementation of protocols, technologies, and related configuration tasks and contains comprehensive configuration examples. Each command reference chapter complements the organization of its corresponding configuration chapter and provides complete command syntax information.
Cisco IOS 12.0 Solutions for Network Protocols, Volume I: IP, 1-57870-154-6
This book is a comprehensive guide detailing available IP and IP routing alternatives. It describes how to implement IP addressing and IP services. It also describes how to configure support for a wide range of IP routing protocols, including BGP for ISP networks and basic and advanced IP multicast functionality.
Cisco IOS 12.0 Configuration Fundamentals, 1-57870-155-4
This comprehensive guide details Cisco IOS software configuration basics. It offers thorough coverage of router and access server configuration and maintenance techniques. In addition to hands-on implementation and task instruction, this book also presents the complete syntax for router and access server commands and individual examples for each command.
Cisco IOS 12.0 Wide Area Networking Solutions, 1-57870-158-9
This book offers thorough, comprehensive coverage of internetworking technologies, particularly ATM, Frame Relay, SMDS, LAPB, and X.25. It teaches the reader how to configure the technologies in a LAN/WAN environment.
Cisco IOS 12.0 Switching Services, 1-57870-157-0
This book is a comprehensive guide detailing available Cisco IOS switching alternatives. Cisco's switching services range from fast switching and Netflow switching to LAN Emulation. This book describes how to configure routing between virtual LANs (VLANs) and how to effectively configure and implement VLANs on switches.
Cisco IOS 12.0 Multiservice Applications, 1-57870-159-7
This book shows you how to configure your router or access server to support voice, video, and broadband transmission. Cisco's voice and video support is implemented using voice packet technology. In voice packet technology, voice signals are packetized and transported in compliance with ITU-T specification H.323, which is the ITU-T specification for transmitting multimedia (voice, video, and data) across a local-area network (LAN).
Cisco IOS 12.0 Network Security, 1-57870-160-0
This book documents security configuration from a remote site and for a central enterprise or service provider network. It describes AAA, Radius, TACACS+, and Kerberos network security features. It also explains how to encrypt data across enterprise networks. The book includes many illustrations that show configurations and functionality, along with a discussion of network security policy choices and some decision-making guidelines.
Cisco IOS 12.0 Quality of Service, 1-57870-161-9
This comprehensive guide details the available Cisco IOS quality of service (QoS) features. This book suggests benefits you can gain from implementing Cisco IOS QoS features and describes how to effectively configure and implement the various QoS features. Some of the features described in this book include Committed Access Rate (CAR), Weighted Fair Queueing (WFQ), and Weighted Random Early Detection (WRED), as well as many other features.
Cisco IOS 12.0 Solutions for Network Protocols, Volume II: IPX, AppleTalk, and More, 1-57870-164-3
This book is a comprehensive guide detailing available network protocol alternatives. It describes how to implement various protocols in your network. This book includes documentation of the latest functionality for the IPX and AppleTalk desktop protocols as well as the following network protocols: Apollo Domain, Banyan VINES, DECNet, ISO CLNS, and XNS.
Cisco IOS 12.0 Bridging and IBM Networking Solutions, 1-57870-162-7
This book describes Cisco's support for networks in IBM and bridging environments. Support includes transparent and source-route transparent bridging; source-route bridging; remote source-route bridging; data-link switching plus; serial tunnel and block serial tunnel; SDLC and LLC2 parameter; IBM network media translation; downstream physical unit and SNA service point; SNA Frame Relay access support; Advanced Peer-to-Peer Networking; and native client interface architecture.
Cisco IOS 12.0 Dial Solutions, 1-57870-163-5
This book provides readers with real-world solutions and how to implement them on a network. Customers interested in implementing dial solutions across their network environment include remote sites dialing in to a central office, Internet service providers (ISPs), ISP customers at home offices, and enterprise WAN system administrators implementing dial-on-demand routing (DDR).
The Cisco IOS documentation set uses the following conventions:
|
Convention |
Description |
|---|---|
|
^ orCtrl |
Represents the Control key. For example, when you read ^D or Ctrl-D, you should hold down the Control key while you press the D key. Keys are indicated in capital letters but are not case sensitive. |
|
string |
A string is defined as a nonquoted set of characters. For example, when setting an SNMP community string to public, do not use quotation marks around the string; otherwise, the string will include the quotation marks. |
Examples use the following conventions:
|
Convention |
Description |
|---|---|
|
screen |
displayed on the screen. |
|
boldface screen |
Shows an example of information that you must enter. |
|
< > |
Nonprinting characters, such as passwords, appear in angled brackets. |
|
! |
Exclamation points at the beginning of a line indicate a comment line. They are also displayed by the Cisco IOS software for certain processes. |
|
[ ] |
Default responses to system prompts appear in square brackets. |
The following conventions are used to attract the reader's attention:
Caution
Means reader be careful. In this situation, you might do something that could result in equipment damage or loss of data.
Note
Means reader take note. Notes contain helpful suggestions or references to materials not contained in this manual.
Timesaver
Means the described action saves time. You can save time by performing the action described in the paragraph.
Within the Cisco IOS12.0 Reference Library, the term router is used to refer to both access servers and routers. When a feature is supported on the access server only, the term access server is used.
Within examples, routers and access servers are alternately shown. These products are used only for example purposes; that is, an example that shows one product does not indicate that the other product is not supported.
Command descriptions use the following conventions:
|
Convention |
Description |
|---|---|
|
boldface |
Indicates commands and keywords that are entered literally as shown. |
|
italics |
Indicates arguments for which you supply values; in contexts that do not allow italics, arguments are enclosed in angle brackets (< >). |
|
[x] |
Keywords or arguments that appear within square brackets are optional. |
|
{x | y | z} |
A choice of required keywords (represented by x, y, and z) appears in braces separated by vertical bars. You must select one. |
|
[x {y | z}] |
Braces and vertical bars within square brackets indicate a required choice within an optional element. You do not need to select one. If you do, you have some required choices. |
Cisco Connection Online (CCO) is Cisco Systems's primary, real-time support channel. Maintenance customers and partners can self-register on CCO to obtain additional information and services.
Available 24 hours a day, 7 days a week, CCO provides a wealth of standard and value-added services to Cisco's customers and business partners. CCO services include product information, product documentation, software updates, release notes, technical tips, the Bug Navigator, configuration notes, brochures, descriptions of service offerings, and download access to public and authorized files.
CCO serves a wide variety of users through two interfaces that are updated and enhanced simultaneously: a character-based version and a multimedia version that resides on the World Wide Web (WWW). The character-based CCO supports Zmodem, Kermit, Xmodem, FTP, and Internet e-mail, and it is excellent for quick access to information over lower bandwidths. The WWW version of CCO provides richly formatted documents with photographs, figures, graphics, and video, as well as hyperlinks to related information.
You can access CCO in the following ways:
WWW: http://www.cisco.com
Telnet: cco.cisco.com
Modem: From North America, 408526-8070; from Europe, 33164464082. Use the following terminal settings: VT100 emulation; databits: 8; parity: none; stop bits: 1; and connection rates up to 28.8kbps.
This section provides helpful tips for understanding and configuring Cisco IOS software using the command-line interface (CLI).
Entering a question mark (?) at the system prompt displays a list of commands available for each command mode. You can also get a list of any command's associated keywords and arguments with the context-sensitive help feature.
To get help specific to a command mode, a command, a keyword, or an argument, use one of the following commands:
|
Command |
Purpose |
|---|---|
|
help |
Obtains a brief description of the help system in any command mode. |
|
abbreviated-command-entry? |
Obtains a list of commands that begin with a particular character string. (No space between the command and the question mark.) |
|
abbreviated-command-entry<Tab> |
Completes a partial command name. |
|
? |
Lists all commands available for a particular command mode. |
|
command ? |
Lists a command's associated keywords. (Space between command and question mark.) |
|
command keyword ? |
Lists a keyword's associated arguments. (Space between the keyword and the question mark.) |
This section provides an example of how to display syntax for a command. The syntax can consist of optional or required keywords. To display keywords for a command, enter a question mark (?) at the configuration prompt or after entering part of a command followed by a space. The Cisco IOS software displays a list of keywords available along with a brief description of the keywords. For example, if you were in global configuration mode, typed the command arap, and wanted to see all the keywords for that command, you would type arap ?.
Table I-1 shows examples of how you can use the question mark (?) to assist you in entering commands. It steps you through entering the following commands:
controller t1 1
cas-group 1 timeslots 1-24 type e&m-fgb dtmf
Table I-1. How to Find Command Options
|
Step |
Command |
Purpose |
|---|---|---|
|
1 |
Router> enable Password: <password> Router# |
Enter the enable command and password to access privileged EXEC commands. You have entered privileged EXEC mode when the prompt changes to |
|
2 |
Router# config terminal
Enter configuration commands, one per
line. End with Ctrl-Z.
Router(config)#
|
Enter global configuration mode. You have entered global configuration mode when the prompt changes to |
|
3 |
Router(config)# controller t1 ? <0-3> Controller unit number Router(config)# controller t1 1 Router(config-controller)# |
Enter controller configuration mode by specifying the T1 controller that you want to configure using thecontroller t1 global configuration command. Enter ? to display what you must enter next on the command line. In this example, you must enter a controller unit number from 0 to 3. You have entered controller configuration mode when the prompt changes to |
|
4 |
Router(config-controller)# ?
Controller configuration commands:
cablelengthSpecify the cable length
for a DS1 link
cas-groupConfigure the specified
timeslots for CAS (Channel Associate
Signals)
channel-groupSpecify the timeslots to
channel-group mapping for an interface
clockSpecify the clock source for a
DS1 link
defaultSet a command to its defaults
descriptionController specific
description
ds0ds0 commands
exitExit from controller
configuration mode
fdlSpecify the FDL standard for a DS1
data link
framingSpecify the type of Framing on
a DS1 link
helpDescription of the interactive
help system
linecodeSpecify the line encoding
method for a DS1 link
loopbackPut the entire T1 line into
loopback
noNegate a command or set its defaults
pri-groupConfigure the specified
timeslots for PRI
shutdownShut down a DS1 link (send
Blue Alarm)
Router(config-controller)#
|
Enter |
|
5 |
Router(config-controller)# cas-group ?
<0-23>Channel number
Router(config-controller)# cas-group
|
Enter the command that you want to configure for the controller. In this example, the cas-group command is used. Enter ? to display what you must enter next on the command line. In this example, you must enter a channel number from 0 to23. Because <cr> is not displayed, it indicates that you must enter more keywords to complete the command. |
|
6 |
Router(config-controller)# cas-group 1 ? timeslotsList of timeslots in the cas- group Router(config-controller)# cas-group 1 |
After you enter the channel number, enter ? to display what you must enter next on the command line. In this example, you must enter the timeslots keyword. Because <cr> is not displayed, it indicates that you must enter more keywords to complete the command. |
|
7 |
Router(config-controller)# cas-group 1 timeslots ? <1-24>List of timeslots which comprise the cas-group Router(config-controller)# cas-group 1 timeslots |
After you enter the timeslots keyword, enter ? to display what you must enter next on the command line. In this example, you must enter a list of timeslots from 1 to 24. You can specify timeslot ranges (for example, 1–24), individual timeslots separated by commas (for example, 1, 3, 5), or a combination of the two (for example, 1–3, 8, 17–24). The 16th time slot is not specified in the command line because it is reserved for transmitting the channel signaling. Because <cr> is not displayed, it indicates that you must enter more keywords to complete the command. |
|
8 |
Router(config-controller)# cas-group 1 timeslots 1-24 ? serviceSpecify the type of service typeSpecify the type of signaling Router(config-controller)# cas-group 1 timeslots 1-24 |
After you enter the timeslot ranges, enter ? to display what you must enter next on the command line. In this example, you must enter the service or type keyword. Because <cr> is not displayed, it indicates that you must enter more keywords to complete the command. |
|
9 |
Router(config-controller)# cas-group 1 timeslots 1-24 type ? e&m-fgbE & M Type II FGB e&m-fgdE & M Type IIFGD e&m-immediate-startE & M Immediate Start fxs-ground-startFXS Ground Start fxs-loop-startFXS Loop Start sas-ground-startSAS Ground Start sas-loop-startSAS Loop Start Router(config-controller)# cas-group 1 timeslots 1-24 type |
In this example, the type keyword is entered. After you enter the type keyword, enter ? to display what you must enter next on the command line. In this example, you must enter one of the signaling types. Because <cr> is not displayed, it indicates that you must enter more keywords to complete the command. |
|
10 |
Router(config-controller)# cas-group 1 timeslots 1-24 type e&m-fgb ? dtmfDTMF tone signaling mfMF tone signaling serviceSpecify the type of service <cr> Router(config-controller)# cas-group 1 timeslots 1-24 type e&m-fgb |
In this example, the e&m-fgb keyword is entered. After you enter the e&m-fgb keyword, enter ? to display what you must enter next on the command line. In this example, you can enter the dtmf, mf, or service keyword to indicate the type of channel-associated signaling available for the e&m-fgb signaling type. Because <cr> is displayed, it indicates that you can enter more keywords or enter <cr> to complete the command. |
|
11 |
Router(config-controller)# cas-group 1 timeslots 1-24 type e&m-fgb dtmf ? dnisDNIS addr info provisioned serviceSpecify the type of service <cr> Router(config-controller)# cas-group 1 timeslots 1-24 type e&m-fgb dtmf |
In this example, the dtmf keyword is entered. After you enter the dtmf keyword, enter ? to display what you must enter next on the command line. In this example, you can enter the dnis or service keyword to indicate the options available for dtmf tone signaling. Because <cr> is displayed, it indicates that you can enter more keywords or enter <cr> to complete the command. |
|
12 |
Router(config-controller)# cas-group 1 timeslots 1-24 type e&m-fgb dtmf Router(config-controller)# |
In this example, enter <cr> to complete the command. |
The Cisco IOS user interface is divided into many different modes. The commands available to you at any given time depend on which mode you are currently in. Entering a question mark (?) at the system prompt allows you to obtain a list of commands available for each command mode.
When you start a session on the router, you begin in user mode, often called EXEC mode. Only a limited subset of the commands is available in EXEC mode. In order to have access to all commands, you must enter privileged EXEC mode. Normally, you must enter a password to enter privileged EXEC mode. From privileged mode, you can enter any EXEC command or enter global configuration mode. Most of the EXEC commands are one-time commands, such as show commands, which show the current status of something, and clear commands, which clear counters or interfaces. The EXEC commands are not saved across reboots of the router.
The configuration modes allow you to make changes to the running configuration. If you later save the configuration, these commands are stored across router reboots. In order to get to the various configuration modes, you must start at global configuration mode. From global configuration mode, you can enter interface configuration mode, subinterface configuration mode, and a variety of protocol-specific modes.
ROM Monitor mode is a separate mode used when the router cannot boot properly. If your router or access server does not find a valid system image when it is booting, or if its configuration file is corrupted at startup, the system might enter read-only memory (ROM) monitor mode.
Table I-2 summarizes the main command modes of the Cisco IOS software.
Table I-2. Summary of Main Command Modes
|
Command Mode |
Access Method |
Prompt |
Exit Method |
|---|---|---|---|
|
User EXEC |
Log in. |
|
Use the logout command. |
|
Privileged EXEC |
From user EXEC mode, use the enable EXEC command. |
|
To exit back to user EXEC mode, use the disable command. To enter global configuration mode, use the configure terminal privileged EXEC command. |
|
Global configuration |
From privileged EXEC mode, use the configure terminal privileged EXEC command. |
|
To exit to privileged EXEC mode, use the exit or end command or press Ctrl-Z. To enter interface configuration mode, enter an interface configuration command. |
|
Interface configuration |
From global configuration mode, enter by specifying an interface with an interface command. |
|
To exit to global configuration mode, use the exit command. To exit to privileged EXEC mode, use the exit command or press Ctrl-Z. To enter subinterface configuration mode, specify a subinterface with the interface command. |
|
Subinterface configuration |
From interface configuration mode, specify a subinterface with an interface command. |
|
To exit to global configuration mode, use the exit command. To enter privileged EXEC mode, use the end command or press Ctrl-Z. |
|
ROM Monitor |
From privileged EXEC mode, use the reload EXEC command. Press the Break key during the first 60 seconds while the system is booting. |
> |
To exit to user EXEC mode, type continue. |
Almost every configuration command also has a no form. In general, use the no form to disable a function. Use the command without the keyword no to re-enable a disabled function or to enable a function that is disabled by default. For example, IP routing is enabled by default. To disable IP routing, specify the noiprouting command and specify ip routing to re-enable it. The Cisco IOS software command references provide the complete syntax for the configuration commands and describes what the no form of a command does.
Configuration commands can also have a default form. The default form of a command returns the command setting to its default. Most commands are disabled by default, so the default form is the same as the no form. However, some commands are enabled by default and have variables set to certain default values. In these cases, the default command enables the command and sets variables to their default values. The Cisco IOS softwarecommand referencesdescribe what the default form of a command does if the command is not the same as the no form.
Enter the copy system:running-config nvram:startup-config command to save your configuration changes to your startup configuration so that they will not be lost if there is a system reload or power outage. For example:
Router# copy system:running-config nvram:startup-config
Building configuration…
It might take a minute or two to save the configuration. After the configuration has been saved, the following output appears:
[OK] Router#
On most platforms, this step saves the configuration to nonvolatile random-access memory (NVRAM). On the Class A Flash file system platforms, this step saves the configuration to the location specified by the CONFIG_FILE environment variable. The CONFIG_FILE variable defaults to NVRAM.