The Importance of Having a Security Policy
Implementing security solutions without having a security policy (either explicitly defined or at least implied) represents at best a haphazard approach to addressing network security issues. It is preferable to have a network security policy in writing, with input into the policy coming from the groups of stakeholders identified in Chapter 1. Figure 4-2 depicts the impact of security policy on implementation of security solutions.
Figure 4-2. Impact of Security Policy on Security Solutions Implementation
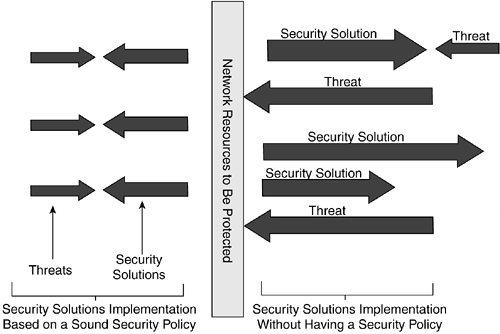
A security policy should define the security goals that an SMB aspires to with respect to its computer network or, in a broader sense, all of its information and technology assets. This definition of security goals creates a framework for the full development of a security policy by facilitating the following:
Identification of assets to be protected
Delineation of threats against the protected assets
Review of the available responses—that is, security solutions—to counter the perceived threats
Creation of rules that users are obliged to follow with respect to the utilization of the protected assets
Development of an action plan in the event of a security breach
Identification of a baseline against which compliance with security procedures can be measured and monitored on an ongoing basis
Identification of trigger mechanisms for updating and reviewing the policy
Based on this framework, a sample security policy follows for a hypothetical SMB called XYZ. XYZ employs a total of 150 people, has two locations in metropolitan areas separated by a distance of about 120 miles (approximately 200 kilometers), and its primary line of business is the design, development, and production of components and subsystems utilized in the space program. XYZ is highly dependent on its network.
The network security policy for XYZ follows.
Security goals:
Ensure network availability 99.9% of the time. There will be approximately 45 minutes of downtime per month for scheduled maintenance.
Maintain maximum confidentiality of production schedules and design documents.
Maintain a high degree of confidentiality of all internal communications.
Identification of assets to be protected:
Entire networking infrastructure within XYZ's facilities (cabling, network switches, engineering and production servers, Internet access routers).
Design documents stored on a storage-area network (SAN).
Ongoing communications regarding business strategy.
Delineation of threats:
Denial of network usage through any means (internal or external). This includes virus and DoS attacks as well as accidental and deliberate tampering with the network infrastructure by unauthorized employees.
Loss of confidential design documents.
Interception of e-mail communications by unauthorized employees.
Security solutions to counter perceived threats:
Firewalls with virus-checking software deployed at multiple Internet access points to counter external penetration and to ensure redundancy in Internet access.
An external VPN to ensure confidentiality of communications between the two locations.
An engineering network, with access to the SAN that stores the design documents, that is completely isolated from the Internet and the production network. Access to the production network from the engineering network is allowed only for the purpose of large file transfers. A special-purpose server becomes disconnected from the production network and is temporarily connected to the engineering network.
Select use of internal VPNs to ensure confidentiality of internal e-mail communications.
Strong authentication, including a strong password policy, use of badges, and biometric authentication. All routers and switches are password protected. Router privileged mode is password protected. ACLs allow access to the routers only from select workstations on the network.
Strong physical security at all servers, SAN, router, and switch locations that requires biometric authentication for access to the designated areas where those devices are kept.
Spare servers, routers, and switches on standby in case of unrecoverable crash.
Power protection for all servers, routers, switches, and select workstations.
High granularity in authorization as a result of effective determination of each employee's network activity.
Intrusion detection scanner to help with development of a baseline for network traffic levels.
Rules regarding protected assets:
No password disclosure or badge swapping is permitted under any circumstances.
No computing devices such as notebook computers, modems, routers, or switches can be brought into the facility without clearance from the IT director.
Any maintenance on critical network components that must performed by an outside contractor has to be done in the presence of an authorized IT staff member.
Use of the Internet and downloading of files is subject to a separate acceptable use policy (AUP) for Internet access.
Action plan in the event of a breach:
Attempt to identify the compromised asset or information as quickly as possible.
Isolate the compromised devices from the rest of the network.
Communicate the situation to people in executive management and keep them apprised of its progress.
Alert local law enforcement if criminal intent is suspected.
Identification of baseline:
Develop a historical baseline using network management tools that identifies traffic levels and device utilization as a function of time.
Develop a baseline of network usage by employees, including login duration, number of login attempts, and hours of usage.
Develop a baseline of any security incidents and their frequency.
Identification of trigger mechanisms for policy review or update:
Emergence of what is considered a new threat, which would typically be reported in the media.
Security breach incident.
Elapse of fixed amount of time—for example, three months.
This policy is based on the components of a security framework that has been developed throughout this chapter. Because each SMB has unique security requirements, this skeletal policy should be tailored to a specific SMB's needs.
