Understanding the Threats
An IT staff must anticipate and prepare for a wide range of system threats. The following sections examine common threats, how IT teams traditionally tried to mitigate threat risks, and how cloud-based solutions may further mitigate risks. It is very difficult, if not impossible, to restore a business to 100 percent following a disaster. Businesses, as such, will define a recovery point objective (RPO) that specifies the level to which data must be restored and a recovery time objective (RTO) that specifies the maximum downtime that can occur before the company must resume operations.
One of the first steps to develop a disaster-recovery plan is to identify the assets (people, processes, and things) that you want to protect and the corresponding risks to each asset. The risk to an asset is the probability that an identified threat will occur and the impact of such occurrence. With this list in hand, you can then prioritize the steps you must perform to protect the asset. Often, you cannot eliminate totally every risk. In such cases, you should seek to mitigate (or minimize) the risk. For example, you cannot eliminate a hacker’s ability to guess a system password. However, by using strong passwords, you mitigate the risk. In addition, there may be times when a risk has such a low probability of occurring and that the impact of the risk is so low that you simply accept the risk. Finally, there may be times when you can transfer a risk to someone else. For example, you may choose to insure your buildings against fire or obtain malware insurance.
Threat: Disk Failure
Disk drives are mechanical devices, and as such they will eventually wear out and fail. Further, other threats, such as fire, flood, theft, or power surges, can result in the loss of disk-based data. Even newer, nonmechanical, solid-state drives can fail.
All mechanical devices have an associated mean time between failure (MTBF) rating. For a disk drive, the MTBF may be 500,000 hours of use (about 8 years). That said, it is important that you understand how manufacturers calculate the MTBF. To start, the manufacturer may begin running 1000 disk drives. When the first disk drive fails, the manufacturer will note the time—let’s say after 500 hours (less than a month). The manufacturers then multiply that time by the number of devices that they tested to determine the MTBF:
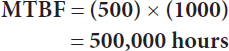
It’s important to note that no device in the group ran near the 500,000 hours!
Traditional Risk Mitigation for Disk Failure
The first and foremost risk mitigation for disk failure is to have up-to-date disk backups. If a disk fails, the company can simply replace the disk and restore the backup. That implies, of course, that the cause of the disk failure (fire, smoke, flood, or theft) did not also damage the disk backup. To reduce such risk, most companies store their disk backups at an off-site storage facility.
The problem with the remote tape backup system is that it takes time. To start, the company may need to purchase a replacement disk. Then the company must install and format the disk for use. Finally, the company’s tape storage facility must locate and return the tape that contains the data. To reduce the potential need to retrieve and store a tape backup, companies turned to multiple disk storage solutions.
RAID-Protected Storage.
Today, many data centers use of a redundant array of independent(or inexpensive) disks (RAID) to reduce the impact of disk failure. A RAID system contains multiple disk drives. Rather than simply store a file on one drive, the RAID system stores the data across several drives. In addition, the RAID system stores data that can be used to reconstruct the file if one of the drives fail. In this way, if a disk drive fails, no file recovery is required from the tape backup. Instead, the IT staff can simply replace the failed disk and the RAID system will rebuild the disk’s contents on the fly!
It is important to note that RAID systems do not eliminate the need for disk backups. If fire, flood, or theft occurs, the entire contents of all the RAID drives may be lost. In such a case, the tape backup of the drives becomes the data restoration solution.
Cloud-Based Data Storage and Backup Solutions
Chapter 6 examined cloud-based data storage in detail. As you learned, cloud-based storage not only lets users access their data from any place, at any time, and often with any device, but it also provides enhanced data replication. As shown in FIGURE 10-1, many cloud-based data storage systems automatically replicate cloud-based data at a second off-site, cloud-based facility. In this way, if one of the RAID-based cloud devices fail, the cloud-based data provider can immediately failover to the redundant device.
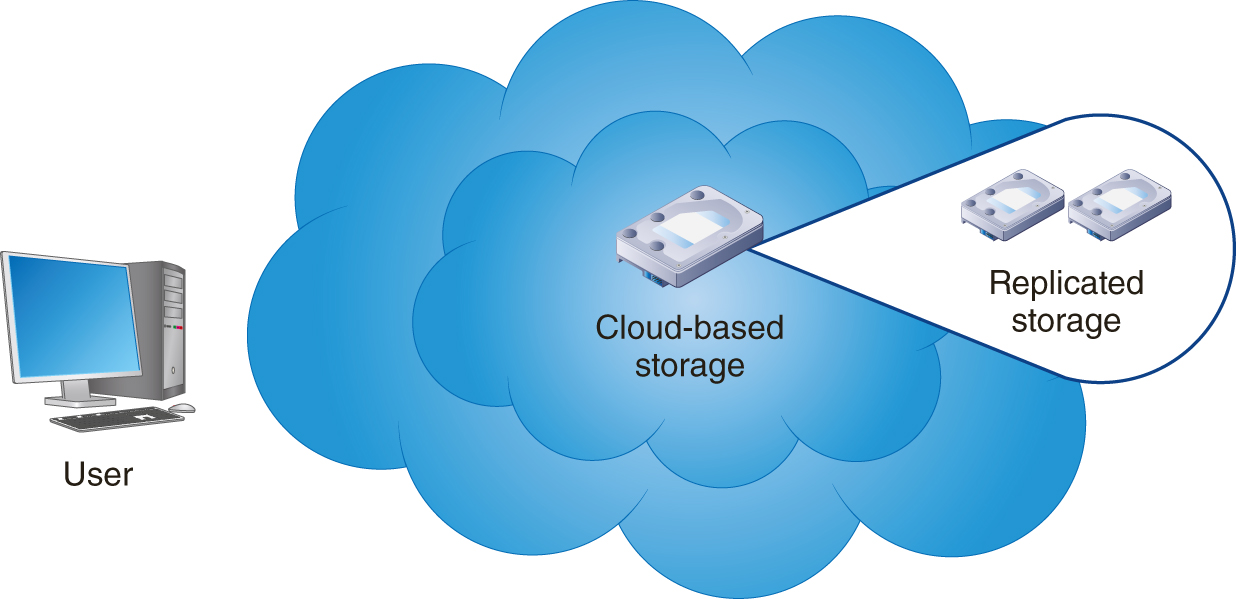
FIGURE 10-1 Most cloud-based data storage facilities provide automatic data replication to another cloud-based data repository.
Further, as discussed in Chapter 6, many cloud-based facilities now use a RAID-like file system, which produces recovery data the facility can use in the event of a device failure.
Cloud-Based Data Backups
Chapter 6 examined the role of cloud-based backups in detail. Because cloud-based backups reside at a remote storage facility, the backups immediately introduce a level of protection. Then, because the backup files are immediately available from any device, anywhere, the backups reduce potential downtime because no time is needed to find, retrieve, and restore a tape backup from a traditional backup storage facility.
Threat: Power Failure or Disruption
Computers are sensitive electronic devices. When a computer loses power, the user’s current unsaved data is lost. Further, an electrical spike can permanently damage the computer’s electronic components, rendering the device unusable or destroying disk-based data. Although power blackouts can be caused by storms, accidents, or acts of terrorism, the more common power brownout is typically more damaging. And, unfortunately, power brownouts can be quite common, especially in the hot summer months when electrical demands spike.
Traditional Power Loss Risk Mitigation
To reduce the risk of an electrical surge damaging a computer and its peripherals, most users plug their computers and devices into a surge suppressor. Although the surge suppressor can prevent damaging power spikes from reaching the computer’s electronic components, the surge suppressor cannot help against power loss. If a power loss occurs, the user’s unsaved work will be lost.
To reduce the risk of lost work, many users plug their devices into an uninterruptible power supply (UPS). Most UPS devices provide 10 to 15 minutes of battery backup power, which gives users time to save their work and shut down their systems in a conventional way. FIGURE 10-2 shows a surge suppressor and a UPS.
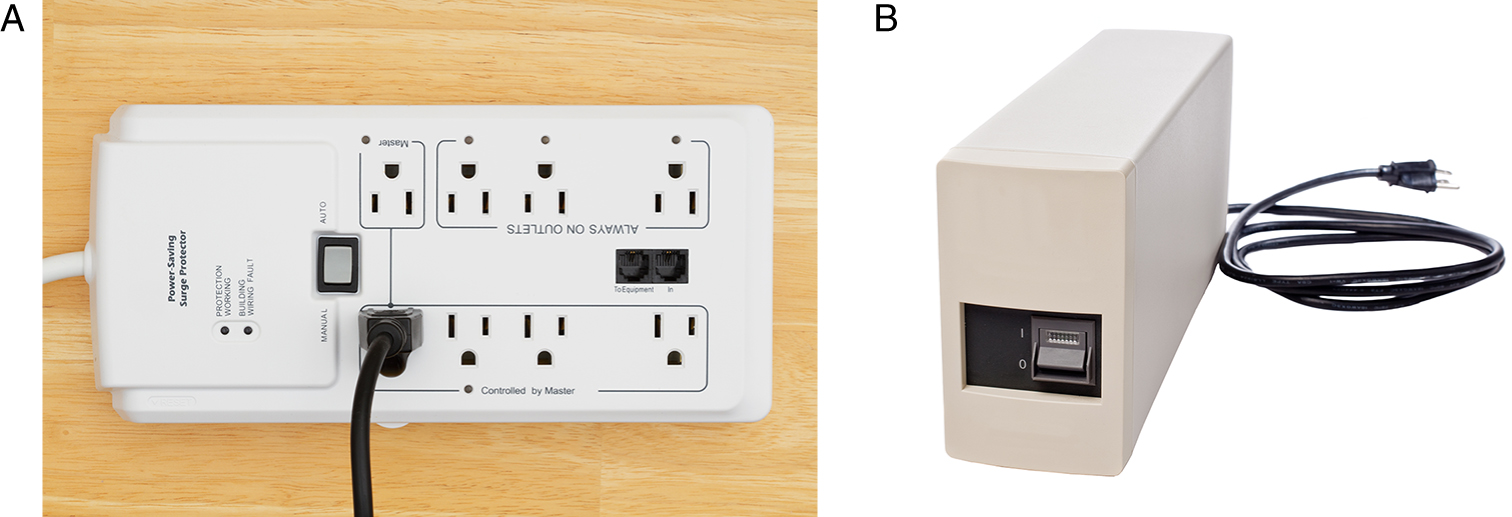
FIGURE 10-2 Users plug devices into surge suppressors to protect the devices from power spikes. A UPS provides users with a few minutes of battery backup power so the users can save their work and shut down their systems in an orderly way. A. Photo of UPS plug into surge protector strip. B. Photo of backup system.
A. © karen roach/Shutterstock. B. © David W. Leindecker/Shutterstock.
Within a data center, as you can imagine, it would be physically impossible to plug every device into its own UPS. Further, within a data center, a loss of power also means a loss of critical air conditioning to cool the devices. To mitigate risks from power loss, some data centers use very large UPS-like devices that provide a period of battery power to all of the powered devices. Further, as shown in FIGURE 10-3, if the power outage lasts a long time, the data center can switch to a large diesel-powered generator to drive power.

FIGURE 10-3 Many data centers have diesel-powered generators to produce power in the event of a long-term outage.
© Radovan1/Shutterstock.
Colocation of Data Resources.
Colocation is the process of replicating key data processing, data storage, and possibly telecommunications equipment at a second remote facility. In other words, a company will duplicate its data center at a second facility. The advantage of colocation is that if one data center fails, the system can immediately fail over to the second facility. The disadvantage of colocation is cost. Not only does the company have to replicate its equipment, but it must also pay for the power, air conditioning, and staffing for a second facility.
Colocation is one way to reduce the risk of power failure. It is not enough to simply locate the second facility across the street or even across town. One must place the second facility across the country to eliminate the impact of storms, attacks, or power grid failures.
Cloud-Based Power Loss Risk Mitigation
Chapter 3, “Platform as a Service (PaaS),” introduced the concept of cloud-based platform as a service (PaaS) solutions. Likewise, Chapter 4, “Infrastructure as a Service (IaaS),” presented the concept of cloud-based infrastructure as a service (IaaS) solutions. When you consider the expensive infrastructure needed to reduce the impact of power interruption, that alone should make you consider housing the data center off-site within the cloud. Most PaaS and IaaS solution providers have effectively dealt with power loss issues. Remember, such providers can share the infrastructure costs across many customers. Also, most of the providers have colocated facilities on different power grids.
Threat: Computer Viruses
As users surf the web (potentially downloading and installing software) and share drives (such as junk drives), their systems and those in the same network are at risk for a computer virus attack, spyware, and ransomware. It is estimated that within the United States alone, lost productivity time due to computer viruses exceeds $100 billion per year!
Traditional Computer Virus Risk Mitigation
The best defense against computer viruses and spyware is to ensure that every system has antivirus software installed. Most antivirus solutions today automatically update themselves across the web, as often as daily, with the most recent virus and spyware signatures.
Second, many organizations prevent users from installing their own software. Not only does this practice reduce the chance of a computer virus infection, it also aids the company in preventing the installation of software that the company does not own.
Third, as shown in FIGURE 10-4, home users should enable a firewall on their system, either at their router or on the computer itself. Most companies place a firewall outside the network.
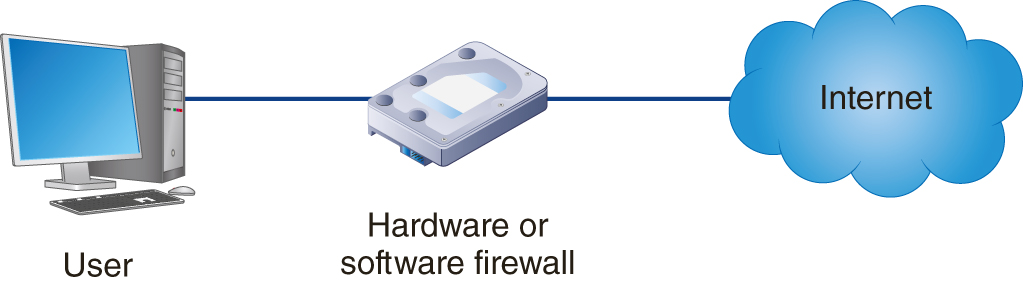
FIGURE 10-4 Home computer users and business users should protect their systems by placing a firewall between the systems and the Internet.
Fourth, companies must train users to not open email attachments in messages they receive from users they do not know.
Cloud-Based Computer Virus Risk Mitigation
In Chapter 8, “Virtualization,” you learned about virtual systems. Many companies now virtualize desktop systems and, in some cases, download an operating system image on demand. A side effect of the virtualization process is a reduced opportunity for a computer virus to make its home within a user’s desktop environment. Further, as you learned in Chapter 9, “Securing the Cloud,” many companies are moving to cloud-based antivirus solutions.
Threat: Fire
Fire can damage computer resources, data stored on disks, and local copies of system backups. If the fire itself does not damage the equipment, the smoke or the process of putting out the fire will.
Traditional Fire Risk Management
Most offices have sprinkler systems, which, as you can imagine, destroy computers when they deploy. Often there is no good way to protect office hardware other than simply to insure it. The goal, when such damage occurs, is to get the users up and running again as soon as possible—business continuity, in other words. That means that system backups must be up to date and must be stored at an off-site location.
Within a data center, you normally won’t find sprinkler systems but rather halon systems based on compounds of carbon and one or more halogens, that stop fire by removing all the oxygen from the room.
Cloud-Based Fire Risk Mitigation
If you house your data center in the cloud, your system will reside in a state-of-the-art data center that provides fire suppression systems and, in most cases, colocated system redundancy. Again, because the PaaS and IaaS solution providers share their costs across many customers, they are able to provide their customers with top-level service at a relatively low cost.
Threat: Floods
During the rainy season, the nightly news often leads with a story about a city or state that is under water due to flooding. Depending on the speed and severity of the flood, companies may have a chance to remove systems from the area before the flood hits. If not, the equipment and the data stored within it is typically lost.
Traditional Flood Risk Mitigation
As with fire, so with flood: The best defense is to have current backups and insured equipment. Within many data centers you will find flood sensors, similar to the one shown in FIGURE 10-5, which sound an alarm if water is detected. These sensors do not exist to detect widespread flooding, but rather water leaking from an on-site pipe break.

FIGURE 10-5 Many data centers use water detection systems to sound alarms if a pipe breaks.
© Catherine.Things/Shutterstock.
Cloud-Based Flood Risk Mitigation
A good rule of thumb is to not place your data center within a flood zone. Historically, most companies had little choice—they had to place their data center near their business offices, often in the same building. Today, however, with cloud-based PaaS and IaaS solutions readily available, the data center can essentially reside anywhere. Thus, the new rule of thumb is to not select a PaaS or IaaS provider located in a flood zone.
Threat: Disgruntled Employees
A disgruntled employee can harm a company by launching a computer virus, changing or deleting files, or exposing system passwords. It is very difficult to defend completely against a disgruntled employee, particularly one who has physical access to systems.
Traditional Disgruntled Employee Risk Mitigation
In the past, businesses protected themselves from disgruntled employees by trying to limit the damage such an employee could cause. First, as previously discussed, companies must ensure that up-to-date backups are in place. Second, the company must use controls to limit the resources that employees can access to only those they need in order to perform their jobs. Then, if an employee is terminated, the company must quickly disable the employee’s access to all systems. Finally, companies often use badges, locked access, and camera monitors with facial recognition to limit the resources to which employees can access.
Cloud-Based Disgruntled Employee Risk Mitigation
Recall Chapter 5, “Identity as a Service (IDaaS).” Companies used the single sign-on process and the cloud to implement identity as a service (IDaaS). In this way, if a company terminates an employee, the company can quickly disable the employee’s access to all systems by simply disabling the employee within the authentication server. Chapter 8, “Virtualization,” examined desktop virtualization. If a company provides employees with a desktop on-demand, most employees (except for the one in charge of desktop images) can do little to harm the system.
Threat: Lost Equipment
Each year, within airports alone, thousands of notebook computers are lost or stolen. When an employee loses a notebook, not only is the computer lost, but also the user’s local data, which may be confidential. Today, with users carrying powerful handheld devices, the opportunity for loss becomes even greater. Given the amount of information a user stores on such a device, identity theft often follows the theft of a device.
Traditional Lost Equipment Risk Mitigation
To reduce the risk of data loss when a device is lost or stolen (or broken), the user must maintain current backups. To reduce access to company sensitive data, many systems require a username and password or biometric sign-on. Although such techniques can be bypassed by an advanced hacker, they will prevent most criminals from accessing data.
Cloud-Based Lost Equipment Risk Mitigation
Typically, the more a company utilizes the cloud, the less risk the company will have with respect to a lost device. If, for example, the user stores (or syncs) key files to a cloud-based data repository, the user is likely to lose only minimal data. Likewise, if the company uses a cloud-based system such as Exchange Online, the user will be without email, calendar, and contact access for only a brief period of time.
Threat: Desktop Failure
Desktop computer, like all devices, may eventually wear out and fail. The cause of failure may be a bad disk drive, motherboard, power supply, and so on. The bottom line is that a user is now without a system.
Traditional Desktop Failure Risk Mitigation
The first step in recovering from a desktop failure is to ensure that current backups of the user’s files exist. Many companies have users store key files on a network disk, which the company can easily back up and later restore. In most companies, a user experiencing the desktop failure will be offline until the IT staff can locate a replacement computer, install and configure software, restore backups of any of the user’s local files, and then make the system available. A few hours of employee downtime can have a significant cost.
Cloud-Based Desktop Failure Risk Mitigation
Chapter 8, “Virtualization,” examined desktop virtualization. If a company delivers the users’ desktops on demand, a user whose system has failed need only stand up, walk to another system, and log in. The employee can then resume work right where he or she left off. Further, if the user stores files in the cloud, he or she can likely access them from any device, and, if necessary, use software such as Office 365 to access and edit the files.
Threat: Server Failure
Just as desktop computers can fail, so too can servers. Because most servers today are blade devices, replacing a server is a relatively simple process, as shown in FIGURE 10-6, as long as the company has an extra server available. Because most servers boot from a network-attached storage (NAS) device, the process of getting the new server up and running should be easy.

FIGURE 10-6 Blade server replacement is normally fast and simple. Because most servers boot from a NAS device, only minimal software setup is normally required.
© R.Grothues/Shutterstock.
Traditional Server Failure Risk Mitigation
If a company has a mission-critical application running on a lone server and does not have a replacement server available or, better yet, online, then shame on that company. Device redundancy is the only way to recover quickly from a server failure.
Cloud-Based Server Failure Risk Mitigation
Given not only the cost factors but also the advantages discussed throughout this chapter, most server applications should reside in the cloud with a PaaS or IaaS solution provider. Such providers typically provide 99.999 percent uptime through hardware redundancy and automatic failover.
Threat: Network Failure
Although networks consist primarily of cables and simple switching devices, things can break. For simple networks, the network will remain down until the faulty device or cable is identified and replaced.
Traditional Network Failure Risk Mitigation
For home computer users, when a network fails, users are going to be offline until a fix is applied. If the problem resides within the Internet service provider (ISP), the user can do nothing to resolve the issue. As a solution, some users are purchasing 4G and 5G wireless hotspot devices as a backup method of accessing the Internet.
To avoid the network from becoming a potential single point of failure, some companies bring in a second Internet source from a vendor other than their primary ISP. In this way, if one network provider fails, the company can gain access to the Internet through the backup network. Further, given that the backup network is in place, many companies will use it to load balance their bandwidth demands.
Cloud-Based Network Failure Mitigation
At first consideration, relying on the cloud for application and data storage may make the thought of a network failure quite concerning. However, as you have just read, many companies provide redundant network connections to the Internet to reduce the risk of network failure. The same is true for cloud service providers. Again, most will guarantee 99.999 percent uptime.
Threat: Database System Failure
Most companies today rely on database management systems to store a wide range of data, from customer data, to human resources data, to application-specific data. If a company’s database fails, many applications may also fail.
Traditional Database System Failure Risk Mitigation
The first defense in reducing the risk of database failure is to maintain current backups of the database. Most database systems today make the backup process easy and automatic. If the database fails, the IT staff can restore the backup. Unfortunately, the database and the applications that rely on it will be down while the restoration is performed.
To reduce the risk of database downtime as a result of a database failure, companies typically replicate data across two database systems in real time. When an operation updates data within the database, the database replication software will immediately update both database systems, as shown in FIGURE 10-7.
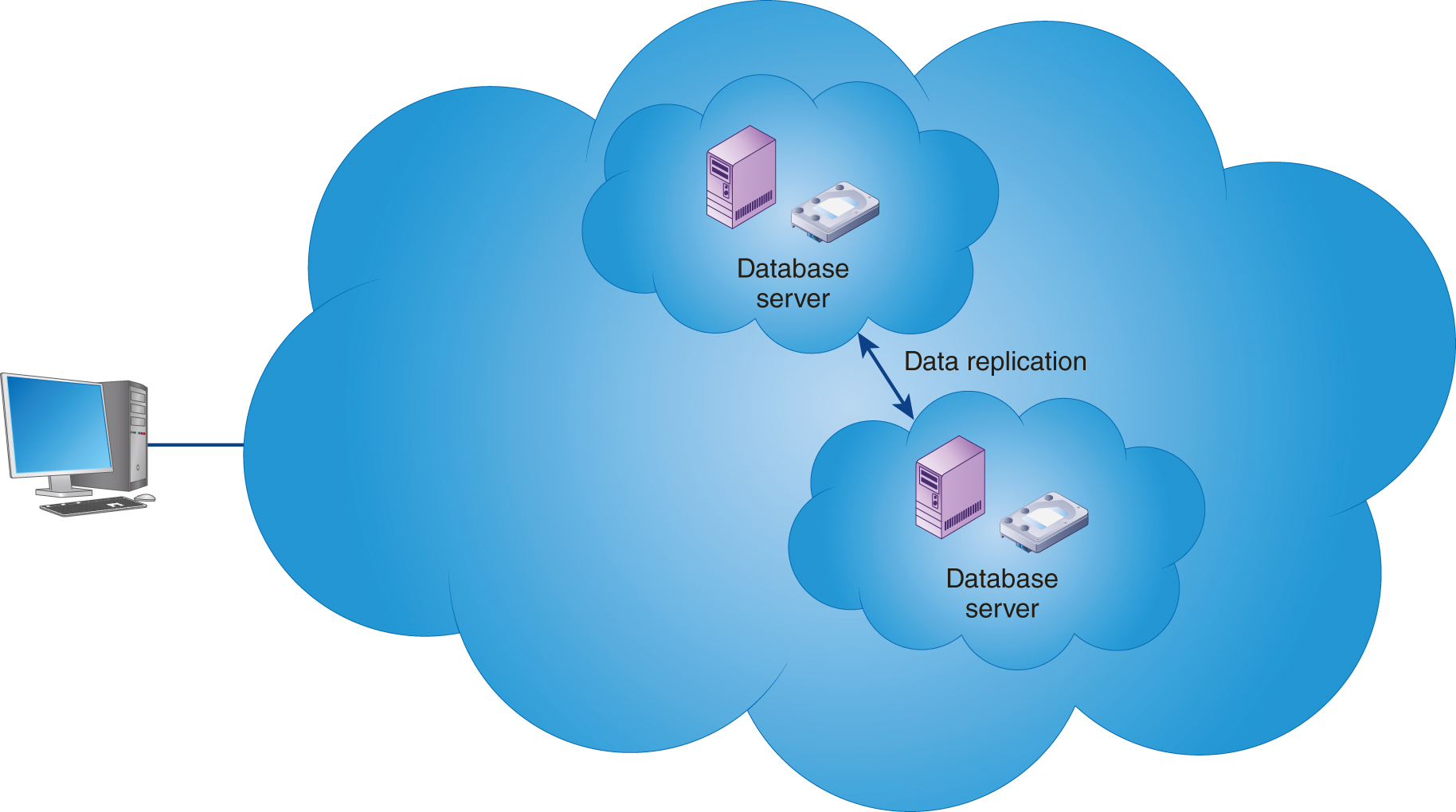
FIGURE 10-7 Database replication creates two live copies of databases on separate servers. If one database fails, the other can immediately take over operations.
Cloud-Based Database System Failure Risk Mitigation
As you just learned, to reduce potential system downtime in the event of a database system failure, many companies replicate the database contents in real time. The disadvantage of database replication is that it requires two servers (ideally in different locations) and may be complicated for developers to initially configure.
Chapter 6, “Data Storage in the Cloud,” discussed cloud-based database management systems in detail. As you learned, most cloud-based database storage providers use transparent database replication. If a database in the cloud fails, the system will failover to the backup database automatically. Further, because replication can occur in both directions, the system can use the second database for load balancing. If data is updated in either system, the change will be replicated to the other system.
Many cloud-service providers offer database-as-a-solution (DBaaS) services, which will provide not only the administration of a cloud-based database in the cloud, but also backups and replication.
Threat: Phone System Failure
Despite the fact that virtually all employees carry a cell phone today, most organizations still maintain phone systems that provide voice mail, conference calling, and call forwarding. If the phone system fails, the company can resort to cell phones. Unfortunately, customers calling in to the company would not know which numbers to call.
Traditional Phone System Failure Risk Mitigation
Historically, there have been few ways outside of redundancy to reduce the impact of a phone system failure. That was the case until the advent of cloud-based phone systems known as call centers as a service (CCaaS).
Cloud-Based Phone System Failure Risk Mitigation
To avoid a single point of failure for phone systems, cloud-based phone systems have now emerged. The cloud-based systems provide the functionality of a traditional phone system and, behind the scenes, provide system replication.
