Chapter 3
Cloud Planning

CERTIFICATION OBJECTIVES
3.01 Cloud Feasibility
3.02 Solving Business Problems with the Cloud
3.03 Cloud Migration Strategies
![]() Two-Minute Drill
Two-Minute Drill
Q&A Self Test
This chapter emphasizes the importance of planning the use of cloud computing services. New companies can adopt cloud computing with relative ease, while organizations already using on-premises solutions have more to consider.
In this chapter, we explore how to determine whether or not cloud services address business needs, how to choose the correct cloud services, and how to plan a cloud migration strategy.
CERTIFICATION OBJECTIVE 3.01
Cloud Feasibility
Like all business endeavors, the adoption of cloud computing requires careful analysis, planning, and testing. Formulating a solid business plan and identifying how business needs are addressed by technology play important roles in a successful cloud adoption strategy. When assessing the feasibility of extending IT services beyond existing on-premises solutions, an organization needs to identify the potential benefits that cloud computing offers. Some of these benefits might include
![]() Less up-front capital costs
Less up-front capital costs
![]() Quicker deployment of IT services
Quicker deployment of IT services
![]() More time to focus on using IT to solve business problems, instead of focusing on configuring the technology
More time to focus on using IT to solve business problems, instead of focusing on configuring the technology
![]() Quicker time to market for products and services
Quicker time to market for products and services
The current and future needs of the organization must be factored in, such as the capability to add users to e-mail systems, the capability to deploy more virtual machines, the capacity to increase cloud storage—this cloud scalability fits in well with capacity planning. A technical gap analysis is used to identify whether current IT solutions properly address business needs, such as determining that cloud-stored data must reside in data centers within national boundaries. If not, the analysis results can identify what needs to be changed, such as moving cloud storage within national boundaries or switching to a cloud service provider (CSP) that supports this option. In this example, a business gap analysis is also applicable since the IT cloud solutions map to business process requirements.
A point of contact needs to be established when reporting to stakeholders as cloud adoption progresses. Affected stakeholders can included end users of cloud services, IT teams supporting cloud services, and management.
As an example, let’s say current on-premises file server data will be migrated to a cloud-based file sharing system. Affected users must be notified of this change to ensure their continued file access, and a method of reporting on the status of the migration must be established. CSPs provide audit and log functionality for all aspects of cloud resource management, including the migration of data to the cloud.
Feasibility Study
A feasibility study factors in items such as technical constraints, regulatory compliance, and cost to determine whether a proposed solution has a realistic chance at succeeding.
Documentation can aid in determining how realistic and practical (feasible) a proposed cloud computing solution will be in addressing business needs. As discussed in Chapter 1, CSP service level agreements (SLAs) define expected uptime for specific cloud services. CSP compliance web pages show which security and data privacy standards the CSP supports.
Network and data flow diagrams are important in showing how IT systems and data will interact with one another, such as using a site-to-site VPN tunnel to link on-premises IT services to a public CSP service. Other relevant documentation types include
![]() Change management
Change management
![]() Resource management
Resource management
![]() Configuration management
Configuration management
![]() Standard operating procedures
Standard operating procedures
For instance, automating the management of storage resources in the cloud might now be done using command-line tools such as Microsoft PowerShell using scripts or templates, where previously this task was handled using on-premises proprietary storage solution tools. The various types of documentation and diagrams are useful not only during a feasibility study but also during solution implementation and future troubleshooting.
Cloud Pilot Program
Whereas a cloud feasibility study addresses general questions such as “Can our organization use cloud computing to more efficiently use technology to serve business needs,” a pilot program actually implements a cloud service on a small scale for purposes of evaluating the service.
Think of pilot programs as being more specific to how feasibility can be measured. For example, a pilot program could consist of five users (a control group) from a department using cloud services to do their jobs for a period of time while others continue to use on-premises IT services. The results of conducting pilot programs are then reported to relevant stakeholders to determine the feasibility of implementing the cloud services on a larger scale.

Make sure you know the difference between a feasibility study and a pilot program.
CERTIFICATION OBJECTIVE 3.02
Solving Business Problems with the Cloud
Organizations don’t use technology because the gadgets are cool. They use technology to solve business problems and to save money. Money can be saved with right-sizing, which strives to use IT infrastructure efficiently, such as reducing the number of virtual machines supporting an application when requests slow down, otherwise known as scaling in (see Chapter 1).
Map Computing Requirements to Cloud Services
Planning for the use of cloud computing means looking at the organization’s current and future anticipated IT needs and then finding services in the cloud that fulfill those needs. For example, if your organization needs to quickly test custom software application changes, deploying application containers in the cloud might be faster and cheaper than deploying virtual machines. This is true because an application container, unlike a VM, does not contain an entire operating system; instead, it simply uses an underlying operating system that is already running.
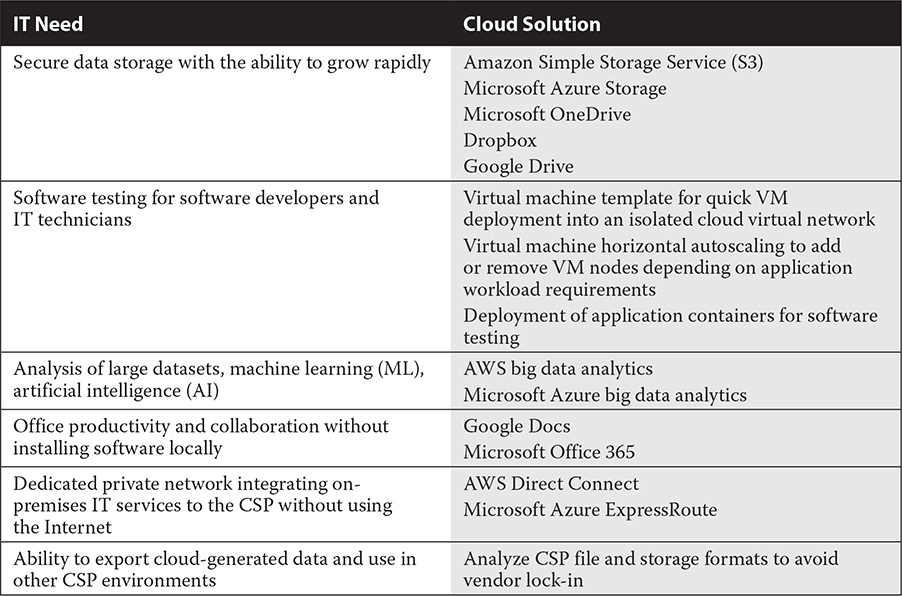
Table 3-1 shows a sample of common IT needs and corresponding cloud solutions.
TABLE 3-1 Common Computing Needs and Cloud Solutions
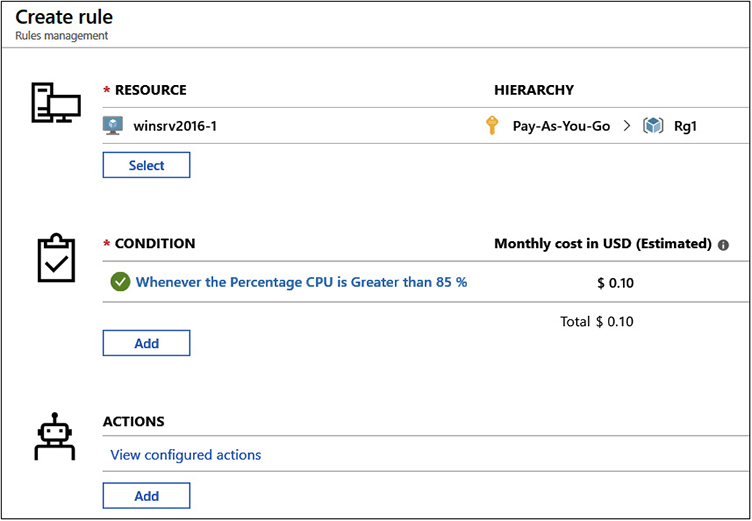
Using cloud services is one thing, but logging and monitoring usage is also crucial for continuous improvement over time. You can configure alerts so that you are notified, for example, if the average CPU utilization of a virtual machine exceeds a given percentage value within a specific time frame, as shown in Figure 3-1.
FIGURE 3-1 Configuring a Microsoft Azure alert rule
Data Sovereignty and Privacy
Cloud computing services run on physical hardware that exists somewhere in a data center. The location of that data center can play a crucial role in determining if a specific CSP or cloud service should be used.
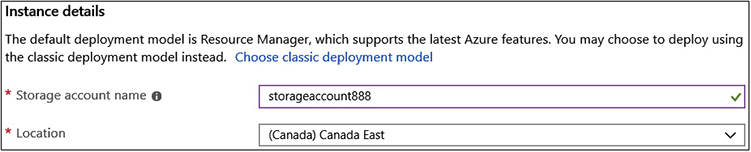
Upon creation, cloud services generally let the creator specify a location (or region) into which a cloud resource will be deployed, as shown in Figure 3-2. Organizations may need to ensure sensitive data resides in data centers within national boundaries for legal or regulatory compliance. Data sovereignty refers to keeping sensitive data within national boundaries to control jurisdictional rule of law related to data.
FIGURE 3-2 Deploying a Microsoft Azure storage account in the Canada East region
Data privacy has become a global issue due to the global nature of the Internet. Personally identifiable information (PII) refers to any piece of information or combination of pieces of information that can uniquely identify an individual. Examples of PII include
![]() Social Security number
Social Security number
![]() E-mail address
E-mail address
![]() IP address
IP address
![]() Street address
Street address
![]() Mother’s maiden name
Mother’s maiden name
Protected health information (PHI) refers to any piece of medically related information about an individual. Protection of PII and PHI normally requires encryption to provide data confidentiality. Examples of PHI include
![]() Blood type
Blood type
![]() Prescribed medications
Prescribed medications
![]() Past medical procedures
Past medical procedures
![]() Health insurance coverage
Health insurance coverage
![]() Medical procedure payment history
Medical procedure payment history
PII and PHI, as well as payment card information, must be protected both on premises and in the cloud. The following discussion provides further details on a few data privacy standards that might affect an organization’s decision regarding whether it should engage the services of a particular CSP.
General Data Protection Regulation (GDPR)
Because data privacy is such a common theme, lawmakers around the world have been scrambling to create a framework of rules to protect the collection, retention, use, and sharing of private data. The GDPR is a legislative act of the European Union (EU) that is intended to put control of PII into the data owner’s hands.
The GDPR states that individuals are entitled to clear communication and consent regarding how their personal data will be collected and used. Individuals also have the right to access their collected data and to ensure its accuracy.
The GDPR applies to organizations within the EU that collect and process personal data, and it applies to any entity located outside the EU that processes personal data of EU citizens.
Health Insurance Portability and Accountability Act (HIPAA)
In the United States, HIPAA is designed to keep individuals’ health information protected from unauthorized access and use. American healthcare providers and health plans must comply with HIPAA regulations using methods such as
![]() Strong user and device authentication
Strong user and device authentication
![]() Data encryption
Data encryption
![]() Data integrity checking to detect tampering
Data integrity checking to detect tampering
![]() Ongoing monitoring to detect potential security breaches
Ongoing monitoring to detect potential security breaches
Like all rules, there are exceptions. Consider the example of people participating in a medical study in which each person consents to having activity-monitoring devices attached to their body. If the collected data from multiple users is analyzed and summarized, then HIPAA may not apply. Any medically related information that can be traced back to an American citizen could be subject to HIPAA.
Payment Card Industry Data Security Standard (PCI DSS)
Merchants dealing with payment cards such as debit and credit cards must adhere to the PCI DSS framework. Unlike some other data privacy standards, such as GDPR and HIPAA, PCI DSS is not limited to a country or group of countries; it is international.
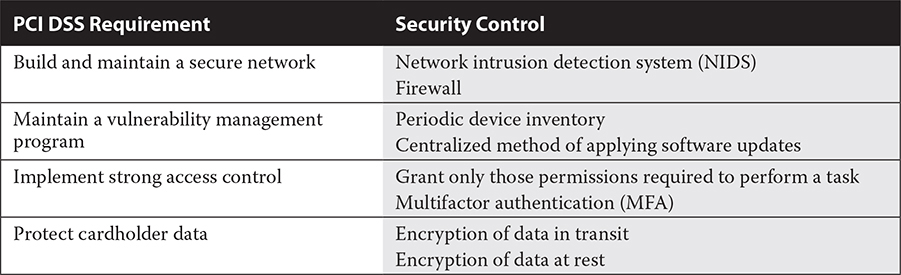
Protecting cardholder data could require securing the transmission and storage of that information, if it is being stored at all. Much of PCI DSS consists of general recommendations; it’s up to IT security experts to determine the best security control to mitigate risks. The other thing to consider is that compliance details vary from one card type to the next (Visa, MasterCard, American Express). Table 3-2 provides a subset of PCI DSS security requirements and solutions.
TABLE 3-2 PCI DSS Requirements and Suggested Security Controls
From a security analyst standpoint, auditing IT environments for PCI DSS can include
![]() Identifying cardholder data
Identifying cardholder data
![]() Assessing existing security controls
Assessing existing security controls
![]() Remediation through reconfiguration or the use of new security controls
Remediation through reconfiguration or the use of new security controls
![]() Reporting on Compliance (RoC) for PCI DSS audits
Reporting on Compliance (RoC) for PCI DSS audits
CERTIFICATION OBJECTIVE 3.03
Cloud Migration Strategies
After an organization has completed a feasibility study, followed by pilot programs to test specific cloud solution viability, and has determined that, yes, moving IT services from on premises to the cloud does make sense, it can focus on cloud migration strategies. An important consideration when choosing a migration strategy is that it can also help fulfill disaster recovery and business continuity planning by replicating data to the cloud in various regions so that a disaster does not destroy all copies of the data.
Remember, with cloud computing, depending on the services you deploy, there is a shared responsibility between you, the cloud customer, and the CSP. For instance, if you deploy virtual machines in the cloud, it’s up to you to manage them, including patching the OS, but the underlying physical hypervisor hardware, storage, and network infrastructure on which the virtual machines run is the responsibility of the CSP, who, in this context, can also be referred to as a managed service provider (MSP).
Most cloud migrations use a phased approach. In simple terms, it could consist of the following phases:
1. Evaluate on-premises candidates for cloud migration.
2. Place IT systems and data in the cloud.
3. Synchronize data between on premises and the cloud.
4. After a period of time during which cloud adoption is successful, decommission the on-premises IT systems and data.
Of course, you might never decommission the on-premises components, which results in running a hybrid cloud solution.
Lift and Shift
While some customized IT solutions may need to be redesigned to work in the cloud, other solutions can be moved from the on-premises IT configurations into the cloud with little to no modification. Commercial off-the-shelf (COTS) software often lends itself to a lift and shift migration strategy from on premises to the cloud, whereas customized, resource-intensive solutions typically do not. Lift and shift migrations are often referred to as rehosting migrations. Rebuilding IT systems to work in the cloud is referred to as refactoring, which is central to the rip and replace migration strategy discussed in the next section.

Be prepared to answer exam questions that test your knowledge of the difference between lift and shift migrations versus refactoring.
Large Datasets
If you have large on-premises datasets, your cloud migration strategy might include employing CSP large data transfer services such as AWS Snowball. With AWS Snowball, a secured storage device is sent to your location, your data is copied (with 256-bit encryption) to the device, and the device is shipped back to AWS, where the data is then copied into the AWS cloud. Transferring very large amounts of data (think petabytes) over the Internet sometimes is not feasible, even with the fastest Internet connections, because it would take too long. It might also be too expensive or not sufficiently secure.
Physical to Virtual (P2V)
Physical on-premises servers can be migrated into the cloud as virtual machines. This process is referred to as physical to virtual (P2V) migration and normally occurs through an agent installed on the physical server that communicates with a management console. The agent analyzes the hardware and OS configuration so that the virtualized environment is configured accordingly. The opposite, meaning migrating a virtual machine to a physical host, is referred to as virtual to physical (V2P).
You might also consider a P2V migration if you want to run a private cloud on your own equipment by virtualizing existing physical servers. The free VMware Converter tool can be used to perform P2V migrations for physical Windows and Linux hosts.
Virtual to Virtual (V2V)
This one is interesting; most folks assume that V2V means migrating on-premises VMs to the cloud, which is correct. This can be much quicker than deploying a brand-new VM in the cloud and configuring it to meet your needs.
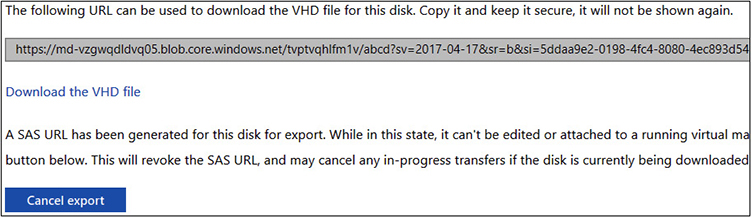
But V2V can also mean migrating cloud-based VMs back to the premises when required. For example, Microsoft Azure VMs use virtual hard disks (VHDs). You can download VHDs from Azure, as shown in Figure 3-3, and then create on-premises VMs using the downloaded VHDs.
FIGURE 3-3 Downloading a Microsoft Azure VM VHD file
Rip and Replace
The previous section discussed the notion of refactoring IT solutions—essentially, rebuilding an IT solution to suit a cloud environment. That’s precisely what the rip and replace migration strategy entails, and it’s often used to migrate customized, complex IT solutions for which there is no functional equivalent service available in the cloud.
CSPs offer a wide variety of infrastructure and development solutions to facilitate rip and replace migrations, including
![]() Cloud-based server-less programmatic functions that don’t require setting up the underlying infrastructure
Cloud-based server-less programmatic functions that don’t require setting up the underlying infrastructure
![]() Web application deployment slots to swap out testing and production versions of a web application
Web application deployment slots to swap out testing and production versions of a web application
![]() Message queues to allow software components to communicate even if they are not running at the same time
Message queues to allow software components to communicate even if they are not running at the same time
![]() Integration with software developer tools such as Microsoft Visual Studio
Integration with software developer tools such as Microsoft Visual Studio
![]() Templates to quickly deploy load-balanced app-testing environments
Templates to quickly deploy load-balanced app-testing environments
EXERCISE 3-1
Run an On-Premises Cloud Migration Assessment for Microsoft SQL Server
In this exercise, you will download, install, and run the Microsoft Data Migration Assistant. This exercise relies on having an on-premises Microsoft SQL Server reachable over the network.
1. Download the free Microsoft Data Migration Assistant tool from https://www.microsoft.com/en-us/download/details.aspx?id=53595.
2. Run the MSI installer and accept all installation defaults. On the last installation screen, shown in Figure 3-4, check the Launch Microsoft Data Migration Assistant check box and click Finish.
FIGURE 3-4 Launch the Microsoft Data Migration Assistant after installation

3. In the left-hand navigation pane of the Data Migration Assistant, click the + sign to create a new migration assessment (see Figure 3-5).
FIGURE 3-5 Create a new assessment or migration
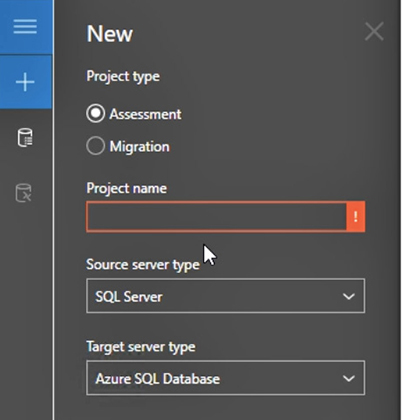
4. With the Assessment radio button selected (the default), name the project HfxProj1.
5. Ensure that the Source Server Type field is set to SQL Server and the Target Server Type field is set to Azure SQL Database, and then click Create and click Next. (Note that after the assessment indicates success, you could come back here and choose the Migration radio button to actually perform a SQL Server data migration.)
6. Specify the name of your on-premises SQL Server and the appropriate authentication type. If somebody else set up the SQL Server, get this information from that person.
7. Click Connect and select one or more databases to run the assessment against. Click Add.
8. Click the Start Assessment button in the bottom right of the screen.
9. After the assessment concludes, review the results to determine if the on-premises SQL database can be easily migrated to Azure.
INSIDE THE EXAM
Databases
Although not listed in the official exam objectives, the CompTIA Cloud Essentials+ CLO-002 exam expects you to be familiar with basic database terminology.
Most CSPs support the managed deployment of SQL databases such as MySQL, Oracle SQL Database, and Microsoft SQL Server. Remember, managed services take care of the underlying virtual machines and storage for you. This is often referred to as Database as a Service (DBaaS).
Most CSPs also support a variety of NoSQL database types. Unlike SQL, NoSQL does not use a rigid database schema, or blueprint, of exactly what type of data can be stored.
CERTIFICATION SUMMARY
This chapter discussed factors to consider when planning the adoption of cloud computing services.
You have been exposed to the importance of ensuring that CSP service offerings address business needs. A business gap analysis assesses the current state of a business process and the desired state. A technical gap analysis identifies the current technical configuration of a current solution compared to the desired configuration to efficiently support business processes. If a feasibility study determines that a proposed cloud solution can realistically succeed in meeting business needs, then further detailed testing is done on a small scale via pilot programs, which test exactly how feasibile proposed cloud solutions are.
You learned how planning the use of cloud services includes determining how deployed cloud solutions will be monitored to ensure the best performance and security possible. Alerts can be configured so that notifications of detected anomalies are sent to cloud administrators.
You also learned about sensitive individual data and data privacy in the cloud and how related laws and regulations can influence the use and configuration of cloud services. You learned that personally identifiable information (PII) refers to any individual or combination of details that can uniquely identify an individual, such as street address or Social Security number. Protected health information (PHI) is similar to PII but differs in that the details are medically related.
You have been exposed to data privacy standards such as the European Union’s General Data Protection Regulation (GDPR), the American Health Insurance Portability and Accountability Act (HIPAA), and the international Payment Card Industry Data Security Standard (PCI DSS).
Finally, you learned about cloud migration strategies, including lift and shift versus rip and replace. You also learned about migrating virtual machines to physical nodes (V2P) and migrating physical nodes to virtual machines (P2V).
 TWO-MINUTE DRILL
TWO-MINUTE DRILL
Cloud Feasibility
![]() A cloud feasibility study determines whether or not cloud computing can address business needs.
A cloud feasibility study determines whether or not cloud computing can address business needs.
![]() Cloud pilot programs implement proposed cloud solutions on a small scale; results must be analyzed to determine success or failure before deploying on a larger scale.
Cloud pilot programs implement proposed cloud solutions on a small scale; results must be analyzed to determine success or failure before deploying on a larger scale.
Solving Business Problems with the Cloud
![]() Current and future computing needs must be accounted for in the cloud.
Current and future computing needs must be accounted for in the cloud.
![]() Right-sizing uses cloud resources efficiently while reducing costs.
Right-sizing uses cloud resources efficiently while reducing costs.
![]() Scaling in refers to the removal of virtual machines supporting an application, normally due to reduced application requests.
Scaling in refers to the removal of virtual machines supporting an application, normally due to reduced application requests.
![]() Mapping computing needs to cloud services requires a thorough understanding of CSP service offerings.
Mapping computing needs to cloud services requires a thorough understanding of CSP service offerings.
![]() Organizations in certain industries and some government agencies might be bound by data privacy standards, laws, and regulations such as GDPR, HIPAA, or PCI DSS.
Organizations in certain industries and some government agencies might be bound by data privacy standards, laws, and regulations such as GDPR, HIPAA, or PCI DSS.
![]() Data sovereignty refers to keeping sensitive data within national boundaries to control jurisdictional rule of law related to data.
Data sovereignty refers to keeping sensitive data within national boundaries to control jurisdictional rule of law related to data.
![]() Personally identifiable information (PII) is any combination of sensitive data that can be traced back to an individual.
Personally identifiable information (PII) is any combination of sensitive data that can be traced back to an individual.
![]() Protected health information (PHI) is any combination of medically related data that can be traced back to an individual.
Protected health information (PHI) is any combination of medically related data that can be traced back to an individual.
Cloud Migration Strategies
![]() Lift and shift cloud migrations involve moving IT systems and data from on premises to the cloud with little or no changes.
Lift and shift cloud migrations involve moving IT systems and data from on premises to the cloud with little or no changes.
![]() Commercial off-the-shelf (COTS) solutions lend themselves to the lift and shift strategy.
Commercial off-the-shelf (COTS) solutions lend themselves to the lift and shift strategy.
![]() Rip and replace cloud migrations involve refactoring or redesigning IT solutions to suit the cloud environment.
Rip and replace cloud migrations involve refactoring or redesigning IT solutions to suit the cloud environment.
![]() You can migrate physical nodes to virtual machines using a physical to virtual (P2V) migration.
You can migrate physical nodes to virtual machines using a physical to virtual (P2V) migration.
![]() You can migrate virtual machines to physical nodes using a virtual to physical (V2P) migration.
You can migrate virtual machines to physical nodes using a virtual to physical (V2P) migration.
 SELF TEST
SELF TEST
The following questions will help you measure your understanding of the material presented in this chapter. As indicated, some questions may have more than one correct answer, so be sure to read all the answer choices carefully.
Cloud Feasibility
1. You need to perform a general analysis to determine if cloud computing will address business needs. What should you perform?
A. Pilot program
B. Feasibility study
C. Phased cloud migration
D. Disaster recovery planning
2. Which term best relates to analyzing test results to identify shortfalls where cloud solutions might not address specific computing requirements?
A. Pilot program
B. Feasibility study
C. Disaster recovery planning
D. Gap analysis
3. You would like to automate the deployment of a cloud-based software testing environment. What should you use? (Choose two.)
A. Command-line scripting
B. Gap analysis
C. GUI deployment tools
D. Templates
4. Which activity determines whether an implemented cloud solution will address business requirements?
A. Pilot program
B. Feasibility study
C. Gap analysis
D. Cloud migration
Solving Business Problems with the Cloud
5. What makes the use of application containers more desirable to developers than virtual machines?
A. Quicker startup time
B. Better security
C. More network options
D. Support for MFA
6. When scaling in for a cloud-based web application, what are you doing?
A. Decreasing the compute power
B. Increasing the compute power
C. Removing virtual machine instances
D. Adding virtual machine instances
7. You need a dedicated network circuit to link your on-premises network to the cloud. Which of the following options provide this capability? (Choose two.)
A. Microsoft Azure ExpressRoute
B. AWS DirectConnect
C. Microsoft Azure Virtual Network Gateway
D. AWS Snowball
8. Which of the following is most closely related to sensitive medical information?
A. PHI
B. PII
C. COTS
D. SLA
9. Which data privacy standard is a legislative act of the European Union?
A. HIPAA
B. PCI DSS
C. GDPR
D. COTS
10. Your manager instructs you to deploy cloud-stored data only within Canada. Which term best describes this scenario?
A. Disaster recovery planning
B. Load balancing
C. Service level agreement
D. Data sovereignty
Cloud Migration Strategies
11. What is the first phase of a cloud migration?
A. Migrate data to the cloud
B. Perform an on-premises cloud readiness assessment
C. Synchronize on-premises and cloud data
D. Decommission on-premises IT systems
12. Which cloud migration strategy is best suited for commercial off-the-shelf software?
A. Rip and replace
B. On-premises assessment
C. Lift and shift
D. Rip and shift
13. What is another term commonly used to describe the rip and replace migration strategy?
A. Refactoring
B. Migrating
C. Replication
D. Reproducing
14. Which AWS service is designed to allow physical storage appliances to transfer large volumes of on-premises data to the cloud?
A. AWS Direct Connect
B. AWS Snowball
C. Amazon S3
D. Amazon EC2
15. Which type of migration converts a physical server to a virtual machine?
A. V2V
B. V2P
C. P2P
D. P2V
 SELF TEST ANSWERS
SELF TEST ANSWERS
Cloud Feasibility
1. ![]() B. A feasibility analysis is the first type of analysis to determine, in general terms, whether or not a cloud solution is realistic and practical.
B. A feasibility analysis is the first type of analysis to determine, in general terms, whether or not a cloud solution is realistic and practical.
![]() A, C, and D are incorrect. Pilot programs are focused on whether an implemented solution solves business problems on a small scale and can also identify shortcomings. A phased cloud migration uses a structured approach to assess on-premises cloud readiness before migrating IT systems and data. Disaster recovery planning in the context of cloud computing normally refers to replicating data to various geographical locations.
A, C, and D are incorrect. Pilot programs are focused on whether an implemented solution solves business problems on a small scale and can also identify shortcomings. A phased cloud migration uses a structured approach to assess on-premises cloud readiness before migrating IT systems and data. Disaster recovery planning in the context of cloud computing normally refers to replicating data to various geographical locations.
2. ![]() D. A gap analysis identifies shortcomings between a requirement and a proposed solution.
D. A gap analysis identifies shortcomings between a requirement and a proposed solution.
![]() A, B, and C are incorrect. Pilot programs are focused on how a solution solves business problems and can also identify shortcomings. A feasibility study is the first type of analysis to determine, in general terms, whether or not a cloud solution is realistic and practical. Disaster recovery in the cloud normally refers to running additional systems and replicating storage to alternative geographical locations.
A, B, and C are incorrect. Pilot programs are focused on how a solution solves business problems and can also identify shortcomings. A feasibility study is the first type of analysis to determine, in general terms, whether or not a cloud solution is realistic and practical. Disaster recovery in the cloud normally refers to running additional systems and replicating storage to alternative geographical locations.
3. ![]() A and D. Command-line scripting using tools such as Microsoft PowerShell can be used to automate cloud resource deployment and management, as can templates. Both options remove the need for cloud technicians to manually deploy cloud resources.
A and D. Command-line scripting using tools such as Microsoft PowerShell can be used to automate cloud resource deployment and management, as can templates. Both options remove the need for cloud technicians to manually deploy cloud resources.
![]() B and C are incorrect. A gap analysis identifies shortcomings between a requirement and a proposed solution. GUI deployment tools do not lend themselves to automation since they require user interaction.
B and C are incorrect. A gap analysis identifies shortcomings between a requirement and a proposed solution. GUI deployment tools do not lend themselves to automation since they require user interaction.
4. ![]() A. Pilot programs are focused on whether an implemented solution solves business problems and can also identify shortcomings.
A. Pilot programs are focused on whether an implemented solution solves business problems and can also identify shortcomings.
![]() B, C, and D are incorrect. A feasibility study is the first type of analysis to determine, in general terms, whether or not a solution is realistic and practical. A gap analysis identifies shortcomings between a requirement and a proposed solution. Cloud migrations are actions that take place after ensuring cloud solutions will address business requirements.
B, C, and D are incorrect. A feasibility study is the first type of analysis to determine, in general terms, whether or not a solution is realistic and practical. A gap analysis identifies shortcomings between a requirement and a proposed solution. Cloud migrations are actions that take place after ensuring cloud solutions will address business requirements.
Solving Business Problems with the Cloud
5. ![]() A. Application containers use the underlying operating system that is already running, whereas a VM contains an entire OS that must be started. Starting a container means starting application software only and not the OS.
A. Application containers use the underlying operating system that is already running, whereas a VM contains an entire OS that must be started. Starting a container means starting application software only and not the OS.
![]() B, C, and D are incorrect. Application containers do not provide more security or options than virtual machines do. Multifactor authentication (MFA) is not an application container feature.
B, C, and D are incorrect. Application containers do not provide more security or options than virtual machines do. Multifactor authentication (MFA) is not an application container feature.
6. ![]() C. With horizontal scaling, scaling in means removing virtual machine instances in response to a decline in application requests.
C. With horizontal scaling, scaling in means removing virtual machine instances in response to a decline in application requests.
![]() A, B, and D are incorrect. Vertical scaling encompasses increasing and decreasing virtual machine compute power. Adding virtual machines is referred to as scaling out.
A, B, and D are incorrect. Vertical scaling encompasses increasing and decreasing virtual machine compute power. Adding virtual machines is referred to as scaling out.
7. ![]() A and B. Microsoft Azure ExpressRoute and AWS Direct Connect are cloud service offerings that allow customers to link their on-premises networks to the cloud using a dedicated private network circuit that does not traverse the Internet.
A and B. Microsoft Azure ExpressRoute and AWS Direct Connect are cloud service offerings that allow customers to link their on-premises networks to the cloud using a dedicated private network circuit that does not traverse the Internet.
![]() C and D are incorrect. The Microsoft Azure Virtual Network Gateway can be used to link Microsoft Azure ExpressRoute circuits or standard site-to-site IPSec VPN devices together. AWS Snowball is a large-scale data transfer service that can be used when network transmission is not feasible.
C and D are incorrect. The Microsoft Azure Virtual Network Gateway can be used to link Microsoft Azure ExpressRoute circuits or standard site-to-site IPSec VPN devices together. AWS Snowball is a large-scale data transfer service that can be used when network transmission is not feasible.
8. ![]() A. Protected health information (PHI) is medically sensitive private information.
A. Protected health information (PHI) is medically sensitive private information.
![]() B, C, and D are incorrect. Personally identifiable information (PII) is any combination of personal data that can be traced back to an individual. Commercial off-the-shelf (COTS) software refers to standard software solutions available to anybody. Service level agreements (SLAs) are contracts between cloud customers and CSPs that detail items such as expected service uptime.
B, C, and D are incorrect. Personally identifiable information (PII) is any combination of personal data that can be traced back to an individual. Commercial off-the-shelf (COTS) software refers to standard software solutions available to anybody. Service level agreements (SLAs) are contracts between cloud customers and CSPs that detail items such as expected service uptime.
9. ![]() C. The General Data Protection Regulation (GDPR) is a data privacy legislative act of the European Union.
C. The General Data Protection Regulation (GDPR) is a data privacy legislative act of the European Union.
![]() A, B, and D are incorrect. The Health Insurance Portability and Accountability Act is a U.S. data privacy act related to medical information. Payment Card Industry Data Security Standard (PCI DSS) is a security framework designed to harden the use of cardholder data. Commercial off-the-shelf (COTS) software refers to standard software solutions available to anybody.
A, B, and D are incorrect. The Health Insurance Portability and Accountability Act is a U.S. data privacy act related to medical information. Payment Card Industry Data Security Standard (PCI DSS) is a security framework designed to harden the use of cardholder data. Commercial off-the-shelf (COTS) software refers to standard software solutions available to anybody.
10. ![]() D. Data sovereignty refers to keeping data within geographical boundaries so that specific laws and regulations are applicable.
D. Data sovereignty refers to keeping data within geographical boundaries so that specific laws and regulations are applicable.
![]() A, B, and C are incorrect. Disaster recovery in the cloud normally refers to running additional systems and replicating storage to alternative geographical locations. Load balancing is used to funnel incoming client app requests to the load balancer, which then redirects the request to the least-busy back-end VM that supports the app. Service level agreements (SLAs) are contracts between cloud customers and CSPs detailing items such as expected service uptime.
A, B, and C are incorrect. Disaster recovery in the cloud normally refers to running additional systems and replicating storage to alternative geographical locations. Load balancing is used to funnel incoming client app requests to the load balancer, which then redirects the request to the least-busy back-end VM that supports the app. Service level agreements (SLAs) are contracts between cloud customers and CSPs detailing items such as expected service uptime.
Cloud Migration Strategies
11. ![]() B. When performing a cloud migration, the first task is to conduct an on-premises cloud readiness assessment.
B. When performing a cloud migration, the first task is to conduct an on-premises cloud readiness assessment.
![]() A, C, and D are incorrect. Data migration, synchronization, and the decommissioning of on-premises systems should take place after having a performance and on-premises assessment.
A, C, and D are incorrect. Data migration, synchronization, and the decommissioning of on-premises systems should take place after having a performance and on-premises assessment.
12. ![]() C. A lift and shift migration essentially moves IT solutions to the cloud with little to no modification, which makes it the best strategy for migrating COTS software because it doesn’t require refactoring.
C. A lift and shift migration essentially moves IT solutions to the cloud with little to no modification, which makes it the best strategy for migrating COTS software because it doesn’t require refactoring.
![]() A, B, and D are incorrect. Rip and replace migrations require refactoring an IT solution so that it will work in the cloud, and COTS software doesn’t require refactoring. When performing a cloud migration, the first task is to conduct an on-premises cloud readiness assessment. Rip and shift is not a valid cloud migration strategy.
A, B, and D are incorrect. Rip and replace migrations require refactoring an IT solution so that it will work in the cloud, and COTS software doesn’t require refactoring. When performing a cloud migration, the first task is to conduct an on-premises cloud readiness assessment. Rip and shift is not a valid cloud migration strategy.
13. ![]() A. Rip and replace migrations require refactoring an IT solution so that it will work in the cloud.
A. Rip and replace migrations require refactoring an IT solution so that it will work in the cloud.
![]() B, C, and D are incorrect. These terms do not describe rip and replace migrations.
B, C, and D are incorrect. These terms do not describe rip and replace migrations.
14. ![]() B. AWS Snowball is a large-scale data transfer service that can be used when network transmission is not feasible.
B. AWS Snowball is a large-scale data transfer service that can be used when network transmission is not feasible.
![]() A, C, and D are incorrect. AWS Direct Connect is a cloud service offering that allows customers to link their on-premises networks to the cloud using a dedicated private network circuit that does not traverse the Internet. Amazon S3 is a cloud storage solution. Amazon EC2 is a cloud-based virtual machine solution.
A, C, and D are incorrect. AWS Direct Connect is a cloud service offering that allows customers to link their on-premises networks to the cloud using a dedicated private network circuit that does not traverse the Internet. Amazon S3 is a cloud storage solution. Amazon EC2 is a cloud-based virtual machine solution.
15. ![]() D. Physical to virtual (P2V) refers to the process of using a software agent installed on a physical host to convert it to a virtual machine.
D. Physical to virtual (P2V) refers to the process of using a software agent installed on a physical host to convert it to a virtual machine.
![]() A, B, and C are incorrect. Virtual to virtual (V2V) converts a virtual machine from one virtualization format to another. Virtual to physical (V2P) converts a virtual machine to a physical server. Peer to peer (P2P), in a networking context, refers to a network where each device can act as both a client and a server.
A, B, and C are incorrect. Virtual to virtual (V2V) converts a virtual machine from one virtualization format to another. Virtual to physical (V2P) converts a virtual machine to a physical server. Peer to peer (P2P), in a networking context, refers to a network where each device can act as both a client and a server.

