CHAPTER 1
Applying Reconnaissance Techniques
This chapter includes questions on the following topics:
• Approaches to conducting reconnaissance
• Tasks involved in identifying and reconnoitering a target
• Variables affecting reconnaissance efforts
• Common tools used for discovery or reconnaissance
As a cybersecurity analyst, you’ll need the knowledge and skills to carry out a variety of tasks. Those tasks include configuring and using threat detection tools, performing data analysis, as well as interpreting the results to identify vulnerabilities, threats, and risks to an organization. The end goal is to secure and protect the resources within the organization. Those resources include the servers, network, and data as well as the user accounts accessing and using it all.
Protecting resources starts with vulnerability management, or knowing what weaknesses exist and applying appropriate measures to minimize them. Risk management is an ongoing process. To begin, you need to identify and evaluate the assets—or in the attacker’s perspective, the targets. The first part, identifying what targets exist, is done through reconnaissance. To perform reconnaissance, you need to apply several techniques and employ a variety of tools. And that is what this chapter is all about.
Q QUESTIONS
1. Which of the following is not an example of reconnaissance or gathering information of the target company through open source intelligence?
A. Using LinkedIn and other social media to gather e-mail addresses of top executives
B. Performing passive reconnaissance by capturing packets and scanning ports
C. Monitoring job sites to learn what technologies are used
D. Performing DNS harvesting of company network data from external DNS servers
2. What is the name of the command-line version of Wireshark?
A. nmap
B. tcpdump
C. Nessus
D. TShark
3. You’re at an employee’s workstation. You need to quickly determine what other machines this system is talking to. You don’t have time to install extra tools. What command-line utility and command-line switch will reveal connections between this workstation and others?
A. tcpdump -i -eth0
B. nikto -host
C. netstat -a
D. nbtstat -A
4. You suspect an employee’s workstation may be the source of malicious traffic. Which of the following steps is the best course of action to determine both the type of traffic and this workstation’s participation in the traffic?
A. Set up packet capturing on a network device upstream from the workstation.
B. Set up packet capturing on the suspect workstation.
C. Set up packet capturing on a small group of servers identified as targets.
D. Install antivirus software on the suspect workstation.
5. At a few employee workstations, including a suspect system, you bring up a command window and type arp -a to display the cached entries of hostnames and IP addresses, as well as those IPs resolved to a MAC address. At first glance, today’s entries seem normal. However, you know for a fact these MAC addresses are not how they were or should be. This illustration shows what the cache was before the suspicious behavior:

And this illustration shows today’s new cached entries:

Notice the differences between the illustrations. From these differences, which is the suspect system and what technique is being used?
A. DNS poisoning, and both Alan and Gail’s systems are attacking.
B. ARP poisoning, and Alan’s system is the attacker.
C. ARP poisoning, and Gail’s system is the attacker.
D. ARP poisoning, and Sam’s system is the attacker.
6. Utilizing search sites as well as professional and social media sites with the goal of gathering contact information is an example of what?
A. CVSS
B. OSINT
C. Social engineering
D. Phishing
7. A small business is concerned about the threat of social media profiling on its employees. Which of the following actions could you take to best mitigate the threat?
A. Demonstrate phishing examples to the users.
B. Increase the level of detail in the system logs.
C. Review the social media application logs with management.
D. Review job site listings with HR and systems administrators.
8. Which of the following is not an example of a virtualization technology?
A. Containers
B. Software-defined networking
C. Mirroring
D. Hypervisors
9. Which of the following is a Type 2 hypervisor?
A. VMware Player
B. Microsoft Hyper-V
C. VMware ESX
D. Kernel-based Virtual Machine
10. Which of the following is not an actual cloud computing technology?
A. IaaS
B. SaaS
C. PaaS
D. SDN
11. You are tasked with scanning across the network space 192.168.2.x and identifying what operating systems are presently running. Select the correct tool and command-line switch necessary to determine what operating systems are running on that subnet.
A. nikto -Version 192.168.2.0
B. nmap -O 192.168.2.0/24
C. syslog -network 192.168.2.0-192.168.2.254
D. netstat -a 192.168.2.0 /24
12. Referring to Figure 1-1, select from the following actions what the person’s likely intentions are.
A. Assessing what web vulnerabilities are present
B. Inventorying the web configuration settings
C. Locating the host web server from the network
D. Reviewing the web server’s HTTP methods

Figure 1-1 Running nikto at the command line
13. A company has suffered a recent incident where a print server was infected with malware and began aggressively scanning other machines on the network. The malware-infected server was identified only after a significant number of other machines were experiencing issues. Although the problem was contained, the timing was an issue. The company asks you to suggest how responding to problems like this could be done more quickly. What do you suggest?
A. The company should review the firewall rules for areas to improve.
B. The company should install an IDS on the network.
C. The company should install an IPS on the network.
D. The company should scan for further vulnerable print servers.
14. What is a primary challenge to using cloud storage versus on-premises storage?
A. On-premises storage doesn’t permit mobile access.
B. Expensive software licensing and hardware for cloud services.
C. Cloud resources put more emphasis on identity management.
D. Limited options for cloud computing.
15. Wireshark and tcpdump are examples of what kind of application?
A. Syslog aggregators
B. Packet analyzers
C. Intrusion detection systems
D. Port scanners
16. Which of the following is not included when capturing packet headers but is provided with full packet capture?
A. Source address
B. Payload
C. Protocol flags
D. Destination address
17. Which of the following statements is not true when it comes to syslog?
A. Syslog supports a broad range of devices and events.
B. Messages can be aggregated into a single, nonhierarchical feed.
C. Devices are polled for messages, echoing back to a syslog server.
D. The syslog protocol and messaging come native in most firewalls and network devices as well as most *nix systems.
18. A company is frustrated by its firewall’s inability to catch higher-level malicious attacks, such as SQL injection and cross-site scripting (XSS). The firewall is unable to distinguish between valid HTTP traffic and malicious attacks when such traffic traverses the firewall on port 80. What do you see as the primary limitation of the firewall?
A. The firewall is an application-layer firewall, unable to identify the higher-layer data.
B. The firewall needs to be partnered with an IDS or IPS.
C. The firewall rules need to be reviewed and likely changed.
D. The firewall is a layer 3 or 4 device and should be replaced with an application-layer device.
19. If an attacker is using nmap to map the network topology, which of the returned states of the port scans provides the least information?
A. Unfiltered
B. Filtered
C. Closed
D. Open
20. What would be an appropriate tool for performing service discovery on a large network?
A. An IDS (but no IPS) placed anywhere on the servers’ local subnet
B. A HIDS placed on a target server
C. Any tool able to review firewall logs or router ACLs
D. A port scanner
21. When you’re capturing packets on a wireless network versus a wired network, which of the following statements are true? (Choose all that apply.)
A. Using promiscuous mode to view all packets applies on both wired and wireless networks.
B. Being in monitor mode allows for the capture of all 802.11 activity, without connection to the access point.
C. Wireless signals can be relatively limited beyond a physical presence such as a fence.
D. Strong, secure encryption provides no protection against data exposed via eavesdropping.
QUICK ANSWER KEY
1. B
2. D
3. C
4. B
5. D
6. B
7. A
8. C
9. A
10. D
11. B
12. A
13. C
14. C
15. B
16. B
17. C
18. D
19. B
20. D
21. A, B
A IN-DEPTH ANSWERS
1. Which of the following is not an example of reconnaissance or gathering information of the target company through open source intelligence?
A. Using LinkedIn and other social media to gather e-mail addresses of top executives
B. Performing passive reconnaissance by capturing packets and scanning ports
C. Monitoring job sites to learn what technologies are used
D. Performing DNS harvesting of company network data from external DNS servers
![]() B is correct. Capturing packets and scanning ports are not examples of passive reconnaissance. Scanning ports is considering active reconnaissance. If your activities could create entries in a log, then those actions are not passive.
B is correct. Capturing packets and scanning ports are not examples of passive reconnaissance. Scanning ports is considering active reconnaissance. If your activities could create entries in a log, then those actions are not passive.
![]() A, C, and D are incorrect. A is incorrect because LinkedIn is a site external to the company. You can interact with LinkedIn to gather information about a company without directly interacting with that company. Therefore, this is a form of open source intelligence gathering. C is incorrect because, like LinkedIn, the job sites are presumed to be external to the company. D is incorrect because DNS harvesting involves interacting with DNS servers outside the company’s DNS servers, versus interacting with internal DNS servers.
A, C, and D are incorrect. A is incorrect because LinkedIn is a site external to the company. You can interact with LinkedIn to gather information about a company without directly interacting with that company. Therefore, this is a form of open source intelligence gathering. C is incorrect because, like LinkedIn, the job sites are presumed to be external to the company. D is incorrect because DNS harvesting involves interacting with DNS servers outside the company’s DNS servers, versus interacting with internal DNS servers.
2. What is the name of the command-line version of Wireshark?
A. nmap
B. tcpdump
C. Nessus
D. TShark
![]() D is correct. TShark is the command-line interface of Wireshark.
D is correct. TShark is the command-line interface of Wireshark.
![]() A, B, and C are incorrect. A is incorrect because nmap is a port scanning tool, not a command-line interface to Wireshark. B is incorrect because, although tcpdump is indeed a packet capturing tool, it is not the command-line version of Wireshark. C is incorrect because Nessus is a vulnerability scanning tool, not a command-line packet capturing tool.
A, B, and C are incorrect. A is incorrect because nmap is a port scanning tool, not a command-line interface to Wireshark. B is incorrect because, although tcpdump is indeed a packet capturing tool, it is not the command-line version of Wireshark. C is incorrect because Nessus is a vulnerability scanning tool, not a command-line packet capturing tool.
3. You’re at an employee’s workstation. You need to quickly determine what other machines this system is talking to. You don’t have time to install extra tools. What command-line utility and command-line switch will reveal connections between this workstation and others?
A. tcpdump -i -eth0
B. nikto -host
C. netstat -a
D. nbtstat -A
![]() C is correct. The utility netstat is on the workstation and is already a part of the operating system. Netstat is a command-line utility for viewing network statistics information, such as what connections and protocols are in use. The command-line switch -a will display all connections and listening ports.
C is correct. The utility netstat is on the workstation and is already a part of the operating system. Netstat is a command-line utility for viewing network statistics information, such as what connections and protocols are in use. The command-line switch -a will display all connections and listening ports.
![]() A, B, and D are incorrect. A is incorrect because tcpdump is a packet capturing utility. The -i switch is for specifying an interface. B is incorrect because Nikto is a utility for scanning web vulnerabilities. The command-line switch -host will set the target host by IP or hostname. D is incorrect because the utility nbtstat informs you about NetBIOS connections. Although both nbtstat and netstat are available in most Windows versions, the utility netstat is best for determining all the current network connections.
A, B, and D are incorrect. A is incorrect because tcpdump is a packet capturing utility. The -i switch is for specifying an interface. B is incorrect because Nikto is a utility for scanning web vulnerabilities. The command-line switch -host will set the target host by IP or hostname. D is incorrect because the utility nbtstat informs you about NetBIOS connections. Although both nbtstat and netstat are available in most Windows versions, the utility netstat is best for determining all the current network connections.
4. You suspect an employee’s workstation may be the source of malicious traffic. Which of the following steps is the best course of action to determine both the type of traffic and this workstation’s participation in the traffic?
A. Set up packet capturing on a network device upstream from the workstation.
B. Set up packet capturing on the suspect workstation.
C. Set up packet capturing on a small group of servers identified as targets.
D. Install antivirus software on the suspect workstation.
![]() B is correct. Capturing packets from the suspect workstation will yield complete information regarding this workstation as the source, thus demonstrating both the types of traffic and how the workstation fits into the situation.
B is correct. Capturing packets from the suspect workstation will yield complete information regarding this workstation as the source, thus demonstrating both the types of traffic and how the workstation fits into the situation.
![]() A, C, and D are incorrect. A is incorrect because, although capturing packets is correct, capturing them from the network may miss traffic routed outside of the capturing device. The optimum location for capturing is on the workstation itself. C is incorrect because capturing packets on a few targets would likely mean missing specific traffic to unknown targets. D is incorrect because, although antivirus software might help identify malware, it might not help identify the type of traffic, nor will it answer whether the traffic is associated with any quarantined malware.
A, C, and D are incorrect. A is incorrect because, although capturing packets is correct, capturing them from the network may miss traffic routed outside of the capturing device. The optimum location for capturing is on the workstation itself. C is incorrect because capturing packets on a few targets would likely mean missing specific traffic to unknown targets. D is incorrect because, although antivirus software might help identify malware, it might not help identify the type of traffic, nor will it answer whether the traffic is associated with any quarantined malware.
5. At a few employee workstations, including a suspect system, you bring up a command window and type arp -a to display the cached entries of hostnames and IP addresses, as well as those IPs resolved to a MAC address. At first glance, today’s entries seem normal. However, you know for a fact these MAC addresses are not how they were or should be. This illustration shows what the cache was before the suspicious behavior:

And this illustration shows today’s new cached entries:

Notice the differences between the illustrations. From these differences, which is the suspect system and what technique is being used?
A. DNS poisoning, and both Alan and Gail’s systems are attacking.
B. ARP poisoning, and Alan’s system is the attacker.
C. ARP poisoning, and Gail’s system is the attacker.
D. ARP poisoning, and Sam’s system is the attacker.
![]() D is correct. ARP poisoning is the technique, which is apparent by the changed ARP cache entries, and the second illustration shows Sam’s system as the new target MAC address for traffic intended for Gail and Alan’s systems. Thus, we can assume Sam’s system is the culprit.
D is correct. ARP poisoning is the technique, which is apparent by the changed ARP cache entries, and the second illustration shows Sam’s system as the new target MAC address for traffic intended for Gail and Alan’s systems. Thus, we can assume Sam’s system is the culprit.
![]() A, B, and C are incorrect. A is incorrect because DNS poisoning or DNS spoofing involves spreading illegitimate DNS information, which isn’t evident in the illustration or mentioned in the text. B and C are incorrect because the second illustration shows Sam’s system as the new MAC entry, not Alan’s or Gail’s.
A, B, and C are incorrect. A is incorrect because DNS poisoning or DNS spoofing involves spreading illegitimate DNS information, which isn’t evident in the illustration or mentioned in the text. B and C are incorrect because the second illustration shows Sam’s system as the new MAC entry, not Alan’s or Gail’s.
6. Utilizing search sites as well as professional and social media sites with the goal of gathering contact information is an example of what?
A. CVSS
B. OSINT
C. Social engineering
D. Phishing
![]() B is correct. OSINT, or open source intelligence, refers to gathering information about a target without directly interacting with that target’s infrastructure.
B is correct. OSINT, or open source intelligence, refers to gathering information about a target without directly interacting with that target’s infrastructure.
![]() A, C, and D are incorrect. A is incorrect because CVSS stands for Common Vulnerability Scoring System, which is the industry standard method for ranking vulnerabilities. C is incorrect because social engineering involves interacting with people, not websites. D is incorrect because phishing involves e-mailing potential targets.
A, C, and D are incorrect. A is incorrect because CVSS stands for Common Vulnerability Scoring System, which is the industry standard method for ranking vulnerabilities. C is incorrect because social engineering involves interacting with people, not websites. D is incorrect because phishing involves e-mailing potential targets.
7. A small business is concerned about the threat of social media profiling on its employees. Which of the following actions could you take to best mitigate the threat?
A. Demonstrate phishing examples to the users.
B. Increase the level of detail in the system logs.
C. Review the social media application logs with management.
D. Review job site listings with HR and systems administrators.
![]() A is correct. Phishing e-mails are a common result of targeted social media profiling. Showing users the dangers of phishing might improve their social profiles.
A is correct. Phishing e-mails are a common result of targeted social media profiling. Showing users the dangers of phishing might improve their social profiles.
![]() B, C, and D are incorrect. B is incorrect because system logs provide no reflection of social media profiling. C is incorrect because management already is aware of the problem, and reviewing application logs accomplishes little here. D is incorrect because job site listings are not the problem.
B, C, and D are incorrect. B is incorrect because system logs provide no reflection of social media profiling. C is incorrect because management already is aware of the problem, and reviewing application logs accomplishes little here. D is incorrect because job site listings are not the problem.
8. Which of the following is not an example of a virtualization technology?
A. Containers
B. Software-defined networking
C. Mirroring
D. Hypervisors
![]() C is correct. Mirroring describes a technique of fault tolerance in storage, or in the case of switch ports, it describes copying network traffic. Mirroring is not a virtualization technology.
C is correct. Mirroring describes a technique of fault tolerance in storage, or in the case of switch ports, it describes copying network traffic. Mirroring is not a virtualization technology.
![]() A, B, and D are incorrect. Containers, software-defined networking (SDN), and hypervisors are all virtualization technologies.
A, B, and D are incorrect. Containers, software-defined networking (SDN), and hypervisors are all virtualization technologies.
9. Which of the following is a Type 2 hypervisor?
A. VMware Player
B. Microsoft Hyper-V
C. VMware ESX
D. Kernel-based Virtual Machine
![]() A is correct. VMware Player is a Type 2 hypervisor, which means it runs from within an operating system.
A is correct. VMware Player is a Type 2 hypervisor, which means it runs from within an operating system.
![]() B, C, and D are incorrect. Microsoft’s Hyper-V, VMware ESX, and Kernel-based Virtual Machine are all Type 1 hypervisors, also called bare-metal hypervisors because the software runs directly on the “bare metal” hardware, not within an OS.
B, C, and D are incorrect. Microsoft’s Hyper-V, VMware ESX, and Kernel-based Virtual Machine are all Type 1 hypervisors, also called bare-metal hypervisors because the software runs directly on the “bare metal” hardware, not within an OS.
10. Which of the following is not an actual cloud computing technology?
A. IaaS
B. SaaS
C. PaaS
D. SDN
![]() D is correct. Although SDN (or software-defined networking) is a virtualization technology, it is not necessarily in the cloud.
D is correct. Although SDN (or software-defined networking) is a virtualization technology, it is not necessarily in the cloud.
![]() A, B, and C are incorrect. A is incorrect because Infrastructure as a Service (IaaS) describes utilizing a complete infrastructure from a service provider. B is incorrect because Software as a Service (SaaS) describes user access to specific applications from a service provider. C is incorrect because Platform as a Service (PaaS) describes running a platform on top of a server operating system.
A, B, and C are incorrect. A is incorrect because Infrastructure as a Service (IaaS) describes utilizing a complete infrastructure from a service provider. B is incorrect because Software as a Service (SaaS) describes user access to specific applications from a service provider. C is incorrect because Platform as a Service (PaaS) describes running a platform on top of a server operating system.
11. You are tasked with scanning across the network space 192.168.2.x and identifying what operating systems are presently running. Select the correct tool and command-line switch necessary to determine what operating systems are running on that subnet.
A. nikto -Version 192.168.2.0
B. nmap -O 192.168.2.0/24
C. syslog -network 192.168.2.0-192.168.2.254
D. netstat -a 192.168.2.0 /24
![]() B is correct. Nmap is capable of detecting operating systems, and the command-line syntax shown is correct.
B is correct. Nmap is capable of detecting operating systems, and the command-line syntax shown is correct.
![]() A, C, and D are incorrect. The utilities nikto, syslog, and netstat are incapable of determining the operating systems.
A, C, and D are incorrect. The utilities nikto, syslog, and netstat are incapable of determining the operating systems.
12. Referring to Figure 1-1, select from the following actions what the person’s likely intentions are.
A. Assessing what web vulnerabilities are present
B. Inventorying the web configuration settings
C. Locating the host web server from the network
D. Reviewing the web server’s HTTP methods
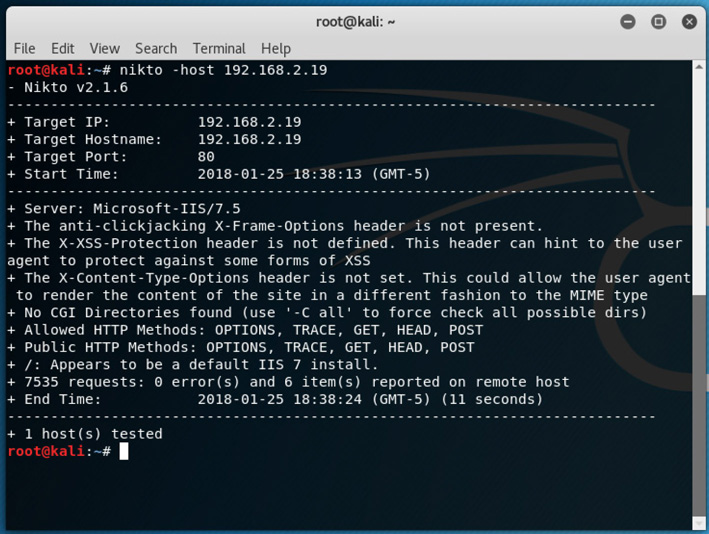
Figure 1-1 Running nikto at the command line
![]() A is correct. The tool shown is Nikto, a web vulnerability scanner. The person used Nikto to scan for vulnerabilities on the web server at address 192.168.2.19.
A is correct. The tool shown is Nikto, a web vulnerability scanner. The person used Nikto to scan for vulnerabilities on the web server at address 192.168.2.19.
![]() B, C, and D are incorrect. B is incorrect because web server configuration settings are not adequately collected. C is incorrect because Nikto is not a network scanner, nor can it identify where is the web server is on a network. D is incorrect because, although Nikto does show the HTTP methods, that’s not its intended purpose.
B, C, and D are incorrect. B is incorrect because web server configuration settings are not adequately collected. C is incorrect because Nikto is not a network scanner, nor can it identify where is the web server is on a network. D is incorrect because, although Nikto does show the HTTP methods, that’s not its intended purpose.
13. A company has suffered a recent incident where a print server was infected with malware and began aggressively scanning other machines on the network. The malware-infected server was identified only after a significant number of other machines were experiencing issues. Although the problem was contained, the timing was an issue. The company asks you to suggest how responding to problems like this could be done more quickly. What do you suggest?
A. The company should review the firewall rules for areas to improve.
B. The company should install an IDS on the network.
C. The company should install an IPS on the network.
D. The company should scan for further vulnerable print servers.
![]() C is correct. An IPS would not only identify the problem but immediately react to contain or eliminate it.
C is correct. An IPS would not only identify the problem but immediately react to contain or eliminate it.
![]() A, B, and D are incorrect. A is incorrect because the problem was not described as originating from outside the firewall. B is incorrect because, although an IDS would identify the problem, it would not address the company’s need for faster response. D is incorrect because, although a good idea, vulnerability scanning would not address the company’s desire for fast response.
A, B, and D are incorrect. A is incorrect because the problem was not described as originating from outside the firewall. B is incorrect because, although an IDS would identify the problem, it would not address the company’s need for faster response. D is incorrect because, although a good idea, vulnerability scanning would not address the company’s desire for fast response.
14. What is a primary challenge to using cloud storage versus on-premises storage?
A. On-premises storage doesn’t permit mobile access.
B. Expensive software licensing and hardware for cloud services.
C. Cloud resources put more emphasis on identity management.
D. Limited options for cloud computing.
![]() C is correct. Identity management becomes ever more important when users are accessing resources away from your control.
C is correct. Identity management becomes ever more important when users are accessing resources away from your control.
![]() A, B, and D are incorrect. A is incorrect because mobile access is not restricted to only cloud resources. B is incorrect because a key benefit of services in the cloud is how inexpensive it is without the need to purchase hardware or upgrades. D is incorrect because cloud computing can take many forms: Infrastructure as a Service, Platform as a Service, or simply Software as a Service.
A, B, and D are incorrect. A is incorrect because mobile access is not restricted to only cloud resources. B is incorrect because a key benefit of services in the cloud is how inexpensive it is without the need to purchase hardware or upgrades. D is incorrect because cloud computing can take many forms: Infrastructure as a Service, Platform as a Service, or simply Software as a Service.
15. Wireshark and tcpdump are examples of what kind of application?
A. Syslog aggregators
B. Packet analyzers
C. Intrusion detection systems
D. Port scanners
![]() B is correct. Wireshark and tcpdump are packet capturing and analysis tools. Both will allow you to capture and view packets as well as perform varying levels of analysis on network traffic.
B is correct. Wireshark and tcpdump are packet capturing and analysis tools. Both will allow you to capture and view packets as well as perform varying levels of analysis on network traffic.
![]() A, C, and D are incorrect. Neither Wireshark nor tcpdump perform as a syslog aggregator, an intrusion detection system, or a port scanner. Although Wireshark could technically be set to alert if a particular packet or part of a packet were captured, that is far from its intended purpose.
A, C, and D are incorrect. Neither Wireshark nor tcpdump perform as a syslog aggregator, an intrusion detection system, or a port scanner. Although Wireshark could technically be set to alert if a particular packet or part of a packet were captured, that is far from its intended purpose.
16. Which of the following is not included when capturing packet headers but is provided with full packet capture?
A. Source address
B. Payload
C. Protocol flags
D. Destination address
![]() B is correct. The payload is not captured when only the packet header is captured.
B is correct. The payload is not captured when only the packet header is captured.
![]() A, C, and D are incorrect. The header contains source and destination addresses, protocol flags, TTL, a header checksum, and protocol version—all dependent on the exact protocol in use.
A, C, and D are incorrect. The header contains source and destination addresses, protocol flags, TTL, a header checksum, and protocol version—all dependent on the exact protocol in use.
17. Which of the following statements is not true when it comes to syslog?
A. Syslog supports a broad range of devices and events.
B. Messages can be aggregated into a single, nonhierarchical feed.
C. Devices are polled for messages, echoing back to a syslog server.
D. The syslog protocol and messaging come native in most firewalls and network devices as well as most *nix systems.
![]() C is correct. Syslog does not “poll” devices for event messages. Syslog messages are only sent to a syslog server, with no prompting.
C is correct. Syslog does not “poll” devices for event messages. Syslog messages are only sent to a syslog server, with no prompting.
![]() A, B, and D are incorrect. A is incorrect because a wide variety of devices and types of messages are supported by syslog. B is incorrect because syslog messages are collected and shown as a flat feed. D is incorrect because such network devices and *nix systems do support syslog.
A, B, and D are incorrect. A is incorrect because a wide variety of devices and types of messages are supported by syslog. B is incorrect because syslog messages are collected and shown as a flat feed. D is incorrect because such network devices and *nix systems do support syslog.
18. A company is frustrated by its firewall’s inability to catch higher-level malicious attacks, such as SQL injection and cross-site scripting (XSS). The firewall is unable to distinguish between valid HTTP traffic and malicious attacks when such traffic traverses the firewall on port 80. What do you see as the primary limitation of the firewall?
A. The firewall is an application-layer firewall, unable to identify the higher-layer data.
B. The firewall needs to be partnered with an IDS or IPS.
C. The firewall rules need to be reviewed and likely changed.
D. The firewall is a layer 3 or 4 device and should be replaced with an application-layer device.
![]() D is correct. The problem described seems to point to a standard firewall that’s unable to inspect application-layer traffic. It should be replaced with a capable, application-layer firewall.
D is correct. The problem described seems to point to a standard firewall that’s unable to inspect application-layer traffic. It should be replaced with a capable, application-layer firewall.
![]() A, B, and C are incorrect. A is incorrect because it is a false to claim the application-layer firewall is unable to identify higher-layer data. B is incorrect because, although an IDS/IPS would help, the firewall’s shortcoming is the primary issue here. C is incorrect because the rules are likely not able to address the application-layer issue.
A, B, and C are incorrect. A is incorrect because it is a false to claim the application-layer firewall is unable to identify higher-layer data. B is incorrect because, although an IDS/IPS would help, the firewall’s shortcoming is the primary issue here. C is incorrect because the rules are likely not able to address the application-layer issue.
19. If an attacker is using nmap to map the network topology, which of the returned states of the port scans provides the least information?
A. Unfiltered
B. Filtered
C. Closed
D. Open
![]() B is correct. Filtered state means the nmap probe scan was unable to reach the port, to hear back whether the port was open or closed. This would make the attacker’s efforts most difficult in mapping the network topology in order to understand the various network areas such DMZ, perimeter devices, and other key network components.
B is correct. Filtered state means the nmap probe scan was unable to reach the port, to hear back whether the port was open or closed. This would make the attacker’s efforts most difficult in mapping the network topology in order to understand the various network areas such DMZ, perimeter devices, and other key network components.
![]() A, C, and D are incorrect. A is incorrect because unfiltered means nmap was able to reach the port but was unable to determine conclusively whether it was open or closed. The unfiltered state only applies when an ACK scan is being performed, often to map firewall rulesets. C is incorrect because closed means the port was reached and was decidedly closed. D is incorrect because open means the port was reached and was concluded to be open or listening.
A, C, and D are incorrect. A is incorrect because unfiltered means nmap was able to reach the port but was unable to determine conclusively whether it was open or closed. The unfiltered state only applies when an ACK scan is being performed, often to map firewall rulesets. C is incorrect because closed means the port was reached and was decidedly closed. D is incorrect because open means the port was reached and was concluded to be open or listening.
20. What would be an appropriate tool for performing service discovery on a large network?
A. An IDS (but no IPS) placed anywhere on the servers’ local subnet
B. A HIDS placed on a target server
C. Any tool able to review firewall logs or router ACLs
D. A port scanner
![]() D is correct. A port scanner would quickly reveal what ports (and the services behind them) are open and listening on devices on the scanned network.
D is correct. A port scanner would quickly reveal what ports (and the services behind them) are open and listening on devices on the scanned network.
![]() A, B, and C are incorrect. A and B are incorrect because an IDS/HIDS (but not an IPS) should alert on valid services instead of only on detected malware traffic. C is incorrect because reviewing firewall logs and router ACLs will tell about flagged traffic attempts and permitted traffic, but provides little information about services and the systems providing them.
A, B, and C are incorrect. A and B are incorrect because an IDS/HIDS (but not an IPS) should alert on valid services instead of only on detected malware traffic. C is incorrect because reviewing firewall logs and router ACLs will tell about flagged traffic attempts and permitted traffic, but provides little information about services and the systems providing them.
21. When you’re capturing packets on a wireless network versus a wired network, which of the following statements are true? (Choose all that apply.)
A. Using promiscuous mode to view all packets applies on both wired and wireless networks.
B. Being in monitor mode allows for the capture of all 802.11 activity, without connection to the access point.
C. Wireless signals can be relatively limited beyond a physical presence such as a fence.
D. Strong, secure encryption provides no protection against data exposed via eavesdropping.
![]() A and B are correct. A is correct because promiscuous mode, if supported by the wireless card, is what allows the card to process all 802.11 activity, not just traffic targeted to that card. B is correct because monitor mode allows the same visibility to all activity, even without being connected to an access point.
A and B are correct. A is correct because promiscuous mode, if supported by the wireless card, is what allows the card to process all 802.11 activity, not just traffic targeted to that card. B is correct because monitor mode allows the same visibility to all activity, even without being connected to an access point.
![]() C and D are incorrect. C is incorrect because wireless signals are generally not too affected by thin physical structures such as fences. The distance from the access point has more of an effect on signal strength. D is incorrect because strong encryption does indeed protect against eavesdropping when data is gathered. The signal can be collected, but encryption ensures confidentiality.
C and D are incorrect. C is incorrect because wireless signals are generally not too affected by thin physical structures such as fences. The distance from the access point has more of an effect on signal strength. D is incorrect because strong encryption does indeed protect against eavesdropping when data is gathered. The signal can be collected, but encryption ensures confidentiality.
