CHAPTER 10
Selecting the Best Course of Action
This chapter includes questions on the following topics:
• How to diagnose incidents by examining network symptoms
• How to diagnose incidents by examining host symptoms
• How to diagnose incidents by examining application symptoms
Unfortunately, in the real world, when issues appear, they are not isolated but rather mixed together with the routine chaos and normal “buzz” of a production environment. Moreover, issues might not come at you one at a time. Instead, one issue might overlap with another, at least partly due to symptoms and timing. Your challenge, should you choose to accept it as a certified CySA+, is to diagnose those issues. This chapter is focused on diagnosing problems and determining the myriad of symptoms that point us to them.
Diagnosing a problem, or incident, starts with identifying what’s wrong or different in your environment. Obviously, to be able to identify what’s different, you must first have a solid understanding of what’s right or normal in your environment. That “normal” is also called the baseline. The steps on how to get a baseline are not covered in detail in this chapter, because it’s assumed that the baseline for your environment is already established and understood. This should be done before an incident occurs in order for you to have a point of comparison. So, on the assumption you have something to compare it to, you can diagnose your incident by what’s changed in your environment.
What this chapter does cover is diagnosing your full environment, including the network, the hosts, and their applications. Each of these areas offers a variety of telltale behaviors and points to examine. This chapter focuses on the assortment of symptoms found in these areas.
Q QUESTIONS
1. Which of the following bandwidth-consumption behaviors strongly indicates something suspicious?
A. Higher-than-normal bandwidth, every day, at the same time
B. Higher-than-normal bandwidth once, during off-peak hours
C. Lower-than-normal bandwidth used during peak hours
D. Higher-than-normal bandwidth used during peak hours
2. Your SIEM alerts you to an unusual amount of ARP queries. This is indicative of what sort of behavior?
A. Rogue device on the network
B. Scan sweeps
C. Unauthorized privileges
D. Unauthorized software
3. What is a property of network usage that suggests a rogue device on the network?
A. Repeated failed remote logins
B. Beaconing
C. Failed connection attempts on the legitimate wireless access points
D. Unrecognized MAC addresses logged on legitimate access points
4. With regard to peer-to-peer network communication, which of the following observations should a cybersecurity analyst be concerned with as abnormal? (Choose all that apply.)
A. Host-to-host connections using an unprivileged account
B. Host-to-host connections using a privileged account
C. Local user connecting to a print server on another subnet
D. Client/server connections with high numbered client ports
5. A network engineer is responding to users complaining the network is slow. Looking at the blinking lights, the engineer notices considerable activity from the HR file server. What would be the network engineer’s next step?
A. Unplug the network cable at the switch going to the file server.
B. Monitor usage and compare it against the baseline.
C. Alert the CIO to the traffic spike.
D. Sample the traffic using a packet analyzer.
6. A cybersecurity analyst has a suspicion about a system’s behavior, but reviewing logs and baseline performance of that system has proven nothing. Finally, the analyst decides to investigate network traffic, based on a hunch. The analyst starts with an endpoint analysis. The analyst sorts the traffic log first by internal source address, then by destination address, and finally by time. What evidence is the analyst clearly searching for?
A. Beaconing.
B. Anomalous activity.
C. Network memory consumption.
D. This is not a search; rather, the analyst is creating a new baseline.
7. A user notices the workstation seems louder than normal—not necessarily fan noise, but the hard drive is constantly “working” without the user installing or moving any files. When the analyst asks if any other system behavior is occurring, the user replies the system seems a bit slower as well. What might be an issue the system is experiencing?
A. Processor consumption
B. Drive capacity consumption
C. Memory consumption
D. Network bandwidth consumption
8. Figure 10-1 shows a portion of active connections on the author’s desktop. The output is presented in the following order: protocol, local address, foreign address, connection state, and process ID. At the same time, the author opens Task Manager and takes note of a few running applications and their processes’ IDs, as detailed in Figure 10-2. Which of these processes might the author want to investigate further?
A. Dropbox.exe
B. chrome.exe
C. notepad.exe
D. WINWORD.EXE

Figure 10-1 Outbound connections

Figure 10-2 Running processes
9. The cybersecurity analyst hears of recent news about a new worm traveling through the company network, installing a bot that mines digital currency. Because the mining software is installed under a random name, running as a random process, there are few known signatures to search for. What might be a likely symptom that could point to infected systems?
A. Processor consumption
B. Unexpected output
C. Unusual traffic spikes
D. Introduction of new accounts
10. In regard to stopping unauthorized software from being installed on a system, which approach is the most effective?
A. Software blacklisting
B. Standardized desktop images and privileges
C. Software whitelisting
D. Host-based intrusion detection and antivirus
11. An application is experiencing apparent memory issues. The symptoms are fairly straightforward, resulting in the application terminating. Occasionally an error pop-up appears with a vague message about a buffer address. From what you see, what is the next course of action?
A. Perform a memory dump
B. Back up the disk
C. Ensure drivers are up to date
D. Capture a packet sample
12. After recovering from an incident, a company decides to invest in a data loss prevention (DLP) solution as well as printers to subtly watermark documents from certain workstations. What do you think was the host-related issue the company experienced during the incident?
A. Unauthorized privileges
B. Service interruption
C. Unusual traffic spikes
D. Data exfiltration
13. A new file server is made available to employees. The server’s capacity is expected to be sufficient for three years. Within two weeks, users complain the file server isn’t as responsive as it used to be. What’s more, a file called MB2TB.exe has been spotted in every folder. What might be a likely issue?
A. Bandwidth consumption
B. Processor consumption
C. Drive capacity consumption
D. Memory consumption
14. A user has raised a support ticket because of an unexpected dialog box on his Windows 10 laptop. He wasn’t concerned at first, because the pop-up seems a legitimate Windows prompt, as seen in Figure 10-3. However, the user cannot understand why the pop-up appears, given there seems no connection to his actions. Treating this as an incident, where would you investigate further?
A. User account “Randy.”
B. Admin account.
C. Application’s publisher.
D. This is not an incident but rather a legitimate User Access Control prompt.
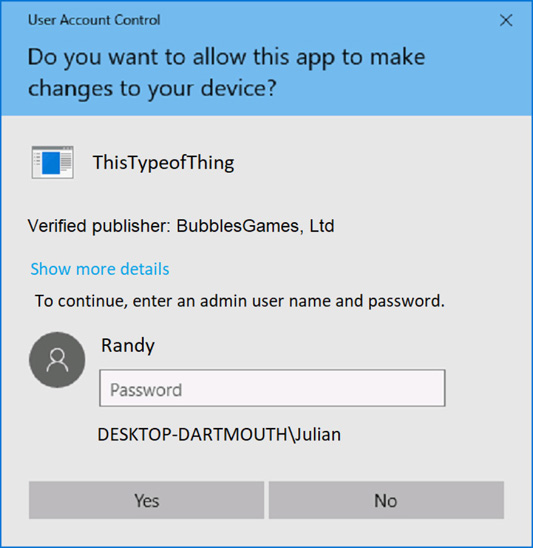
Figure 10-3 User Access Control dialog box
15. A contractor has borrowed an older company laptop and has been using it with no issues for months. Recently the contractor came in, asking for a new laptop because his is “acting weird.” When asked for specifics, the contractor mentioned his application sometimes freezes, the browser goes to different websites, and other strange things start happening. What might be the best course of action?
A. Ensure the OS and applications are patched.
B. Increase the size of the hard drive; add more memory.
C. Create the contractor a new account.
D. Back up his data and perform a fresh, updated system install.
16. A security team member alerts you that a new domain account has been created, but there is no documented account request. Further, there is no legitimate way the account could be created without you or the team member’s assistance. In fact, a quick look shows you the new user account has a session active now on a local host. What is your first step?
A. Fire the team member.
B. Log off the user session.
C. Isolate the host.
D. Reset the account password.
17. An important file that lists numbered bank accounts is tightly controlled, including a process for making any changes to that file. Although the file has no documented changes made in months, an analyst has determined its hashed value was changed sometime between today and last week. What would cause a different hash?
A. New account added
B. Unauthorized changes made
C. Different hash generator used
D. Drive capacity increased
QUICK ANSWER KEY
1. B
2. B
3. D
4. A, B
5. B
6. A
7. C
8. C
9. A
10. C
11. A
12. D
13. C
14. A
15. D
16. D
17. B
A IN-DEPTH ANSWERS
1. Which of the following bandwidth-consumption behaviors strongly indicates something suspicious?
A. Higher-than-normal bandwidth, every day, at the same time
B. Higher-than-normal bandwidth once, during off-peak hours
C. Lower-than-normal bandwidth used during peak hours
D. Higher-than-normal bandwidth used during peak hours
![]() B is correct. A single instance of higher-than-normal bandwidth consumption outside the “work day” is the most suspect. However, although it doesn’t necessarily guarantee suspicious behavior, such bandwidth consumption is worth investigating further.
B is correct. A single instance of higher-than-normal bandwidth consumption outside the “work day” is the most suspect. However, although it doesn’t necessarily guarantee suspicious behavior, such bandwidth consumption is worth investigating further.
![]() A, C, and D are incorrect. A is incorrect because if such higher bandwidth consumption is happening every day, then that has become the new normal. Investigating further is prudent but unlikely necessary. C is incorrect because lower-than-normal bandwidth could point to other issues, such as network disruption. D is incorrect because higher bandwidth consumption during the work day is not necessarily abnormal.
A, C, and D are incorrect. A is incorrect because if such higher bandwidth consumption is happening every day, then that has become the new normal. Investigating further is prudent but unlikely necessary. C is incorrect because lower-than-normal bandwidth could point to other issues, such as network disruption. D is incorrect because higher bandwidth consumption during the work day is not necessarily abnormal.
2. Your SIEM alerts you to an unusual amount of ARP queries. This is indicative of what sort of behavior?
A. Rogue device on the network
B. Scan sweeps
C. Unauthorized privileges
D. Unauthorized software
![]() B is correct. A spike in ARP queries would indicate someone or some process is conducting a scan. This would warrant additional action and investigation.
B is correct. A spike in ARP queries would indicate someone or some process is conducting a scan. This would warrant additional action and investigation.
![]() A, C, and D are incorrect. The ARP queries indicate a scan, which may or may not be originating from a rogue device, unauthorized software, or unauthorized privileges.
A, C, and D are incorrect. The ARP queries indicate a scan, which may or may not be originating from a rogue device, unauthorized software, or unauthorized privileges.
3. What is a property of network usage that suggests a rogue device on the network?
A. Repeated failed remote logins
B. Beaconing
C. Failed connection attempts on the legitimate wireless access points
D. Unrecognized MAC addresses logged on legitimate access points
![]() D is correct. Unrecognized MAC addresses indicate unrecognized or unauthorized devices.
D is correct. Unrecognized MAC addresses indicate unrecognized or unauthorized devices.
![]() A, B, and C are incorrect. A is incorrect because repeated failed logins don’t suggest a rogue device. B is incorrect because beaconing indicates a possibly compromised system keeping in contact with a malicious actor or system outside the network. C is incorrect because failed connection attempts don’t indicate a rogue device, except perhaps in the case where connections are only allowed from whitelisted MAC addresses.
A, B, and C are incorrect. A is incorrect because repeated failed logins don’t suggest a rogue device. B is incorrect because beaconing indicates a possibly compromised system keeping in contact with a malicious actor or system outside the network. C is incorrect because failed connection attempts don’t indicate a rogue device, except perhaps in the case where connections are only allowed from whitelisted MAC addresses.
4. With regard to peer-to-peer network communication, which of the following observations should a cybersecurity analyst be concerned with as abnormal? (Choose all that apply.)
A. Host-to-host connections using an unprivileged account
B. Host-to-host connections using a privileged account
C. Local user connecting to a print server on another subnet
D. Client/server connections with high numbered client ports
![]() A and B are correct. Host-to-host connections are fairly uncommon. Such peer-to-peer communication can suggest an attacker moving laterally from one compromised system to another.
A and B are correct. Host-to-host connections are fairly uncommon. Such peer-to-peer communication can suggest an attacker moving laterally from one compromised system to another.
![]() C and D are incorrect. C is incorrect because a local workstation connecting to any print server is hardly abnormal. D is incorrect because client/server connections typically originate with the client using a high port number.
C and D are incorrect. C is incorrect because a local workstation connecting to any print server is hardly abnormal. D is incorrect because client/server connections typically originate with the client using a high port number.
5. A network engineer is responding to users complaining the network is slow. Looking at the blinking lights, the engineer notices considerable activity from the HR file server. What would be the network engineer’s next step?
A. Unplug the network cable at the switch going to the file server.
B. Monitor usage and compare it against the baseline.
C. Alert the CIO to the traffic spike.
D. Sample the traffic using a packet analyzer.
![]() B is correct. The network engineer’s next step is to consider whether or not the activity is normal by monitoring usage and comparing it against the baseline.
B is correct. The network engineer’s next step is to consider whether or not the activity is normal by monitoring usage and comparing it against the baseline.
![]() A, C, and D are incorrect. A is incorrect because unplugging the network cable is clearly wrong. C is incorrect because it’s far too early to escalate the issue to the CIO. D is incorrect because sampling the traffic is likely the course of action after comparing traffic against the baseline.
A, C, and D are incorrect. A is incorrect because unplugging the network cable is clearly wrong. C is incorrect because it’s far too early to escalate the issue to the CIO. D is incorrect because sampling the traffic is likely the course of action after comparing traffic against the baseline.
6. A cybersecurity analyst has a suspicion about a system’s behavior, but reviewing logs and baseline performance of that system has proven nothing. Finally, the analyst decides to investigate network traffic, based on a hunch. The analyst starts with an endpoint analysis. The analyst sorts the traffic log first by internal source address, then by destination address, and finally by time. What evidence is the analyst clearly searching for?
A. Beaconing.
B. Anomalous activity.
C. Network memory consumption.
D. This is not a search; rather, the analyst is creating a new baseline.
![]() A is correct. Judging by the analyst’s traffic analysis, the intention is to identify any beaconing.
A is correct. Judging by the analyst’s traffic analysis, the intention is to identify any beaconing.
![]() B, C, and D are incorrect. B is incorrect because the analyst is sorting traffic a particular way. C is incorrect because the analyst wouldn’t be sorting traffic to identify network memory consumption. D is incorrect because the analyst is searching for a particular clue.
B, C, and D are incorrect. B is incorrect because the analyst is sorting traffic a particular way. C is incorrect because the analyst wouldn’t be sorting traffic to identify network memory consumption. D is incorrect because the analyst is searching for a particular clue.
7. A user notices the workstation seems louder than normal—not necessarily fan noise, but the hard drive is constantly “working” without the user installing or moving any files. When the analyst asks if any other system behavior is occurring, the user replies the system seems a bit slower as well. What might be an issue the system is experiencing?
A. Processor consumption
B. Drive capacity consumption
C. Memory consumption
D. Network bandwidth consumption
![]() C is correct. The scenario is evidence of disk paging, a sign of extreme memory consumption.
C is correct. The scenario is evidence of disk paging, a sign of extreme memory consumption.
![]() A, B, and D are incorrect. A is incorrect because the user mentioned the system is running somewhat slower, but not so much to point to processor consumption. B is incorrect because the drive sounds like it is “paging” due to a memory shortage, not drive capacity shortage. D is incorrect because there was no mention of network issues.
A, B, and D are incorrect. A is incorrect because the user mentioned the system is running somewhat slower, but not so much to point to processor consumption. B is incorrect because the drive sounds like it is “paging” due to a memory shortage, not drive capacity shortage. D is incorrect because there was no mention of network issues.
8. Figure 10-1 shows a portion of active connections on the author’s desktop. The output is presented in the following order: protocol, local address, foreign address, connection state, and process ID. At the same time, the author opens Task Manager and takes note of a few running applications and their processes’ IDs, as detailed in Figure 10-2. Which of these processes might the author want to investigate further?
A. Dropbox.exe
B. chrome.exe
C. notepad.exe
D. WINWORD.EXE
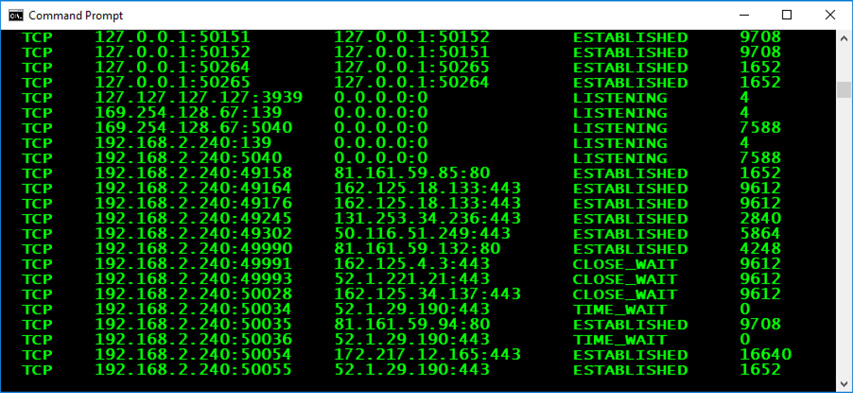
Figure 10-1 Outbound connections
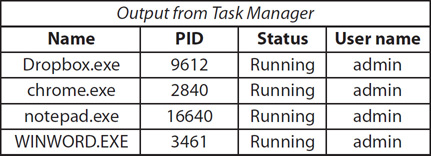
Figure 10-2 Running processes
![]() C is correct. There’s little doubt that notepad.exe maintaining an outbound connection, on port 443 no less, is suspicious. That outbound communication should be investigated further.
C is correct. There’s little doubt that notepad.exe maintaining an outbound connection, on port 443 no less, is suspicious. That outbound communication should be investigated further.
![]() A, B, and D are incorrect. Dropbox and Chrome are expected to have outbound connections. Microsoft Word is not shown in the display of Figure 10-1, but it also might have an outbound connection.
A, B, and D are incorrect. Dropbox and Chrome are expected to have outbound connections. Microsoft Word is not shown in the display of Figure 10-1, but it also might have an outbound connection.
9. The cybersecurity analyst hears of recent news about a new worm traveling through the company network, installing a bot that mines digital currency. Because the mining software is installed under a random name, running as a random process, there are few known signatures to search for. What might be a likely symptom that could point to infected systems?
A. Processor consumption
B. Unexpected output
C. Unusual traffic spikes
D. Introduction of new accounts
![]() A is correct. Because the executable and process names are random, the worm is difficult to locate by name. However, mining software tends to be processor intensive, so that’s a good place for the analyst to start.
A is correct. Because the executable and process names are random, the worm is difficult to locate by name. However, mining software tends to be processor intensive, so that’s a good place for the analyst to start.
![]() B, C, and D are incorrect. B is incorrect because there was no mention of unexpected output. C is incorrect because mining software isn’t likely to produce much network traffic. D is incorrect because no new accounts were mentioned in this scenario.
B, C, and D are incorrect. B is incorrect because there was no mention of unexpected output. C is incorrect because mining software isn’t likely to produce much network traffic. D is incorrect because no new accounts were mentioned in this scenario.
10. In regard to stopping unauthorized software from being installed on a system, which approach is the most effective?
A. Software blacklisting
B. Standardized desktop images and privileges
C. Software whitelisting
D. Host-based intrusion detection and antivirus
![]() C is correct. Whitelisting, or allowing only explicitly listed applications, is the most restrictive method.
C is correct. Whitelisting, or allowing only explicitly listed applications, is the most restrictive method.
![]() A, B, and D are incorrect. A is incorrect because blacklisting particular software as “bad” or unauthorized is effective, but this method relies on knowing every potential piece of software. B is incorrect because having a standard image is good at the start, but if privileges are not restricted, any software could be installed. D is incorrect because using a host-based IDS and antivirus is very effective at stopping known malware, but not necessarily at restricting safe-but-unauthorized software.
A, B, and D are incorrect. A is incorrect because blacklisting particular software as “bad” or unauthorized is effective, but this method relies on knowing every potential piece of software. B is incorrect because having a standard image is good at the start, but if privileges are not restricted, any software could be installed. D is incorrect because using a host-based IDS and antivirus is very effective at stopping known malware, but not necessarily at restricting safe-but-unauthorized software.
11. An application is experiencing apparent memory issues. The symptoms are fairly straightforward, resulting in the application terminating. Occasionally an error pop-up appears with a vague message about a buffer address. From what you see, what is the next course of action?
A. Perform a memory dump
B. Back up the disk
C. Ensure drivers are up to date
D. Capture a packet sample
![]() A is correct. In a case where an application is experiencing memory issues, possibly memory overflow, performing a memory dump is a prudent measure. Memory overflow is symptomatic of a malicious attempt at exploiting the application or system.
A is correct. In a case where an application is experiencing memory issues, possibly memory overflow, performing a memory dump is a prudent measure. Memory overflow is symptomatic of a malicious attempt at exploiting the application or system.
![]() B, C, and D are incorrect. B is incorrect because backing up the disk will not capture anything memory related. C is incorrect because it’s unlikely unstable drivers are the issue. D is incorrect because capturing packets from the network is not useful because it’s a “shotgun” approach to investigating. Packet analysis is really only effective when you have a good idea of what you’re looking for.
B, C, and D are incorrect. B is incorrect because backing up the disk will not capture anything memory related. C is incorrect because it’s unlikely unstable drivers are the issue. D is incorrect because capturing packets from the network is not useful because it’s a “shotgun” approach to investigating. Packet analysis is really only effective when you have a good idea of what you’re looking for.
12. After recovering from an incident, a company decides to invest in a data loss prevention (DLP) solution as well as printers to subtly watermark documents from certain workstations. What do you think was the host-related issue the company experienced during the incident?
A. Unauthorized privileges
B. Service interruption
C. Unusual traffic spikes
D. Data exfiltration
![]() D is correct. Given the mention of DLP and watermarks, you can assume there was an incident of sensitive information being removed or exfiltrated.
D is correct. Given the mention of DLP and watermarks, you can assume there was an incident of sensitive information being removed or exfiltrated.
![]() A, B, and C are incorrect. A is incorrect because an incident of unauthorized privileges would result in better account and authorization management. B is incorrect because service interruption, which can also be an application-related issue, would have been handled with added layers of redundancy, fault tolerance, or high availability. C is incorrect because unusual traffic spikes might have affected network design or application control.
A, B, and C are incorrect. A is incorrect because an incident of unauthorized privileges would result in better account and authorization management. B is incorrect because service interruption, which can also be an application-related issue, would have been handled with added layers of redundancy, fault tolerance, or high availability. C is incorrect because unusual traffic spikes might have affected network design or application control.
13. A new file server is made available to employees. The server’s capacity is expected to be sufficient for three years. Within two weeks, users complain the file server isn’t as responsive as it used to be. What’s more, a file called MB2TB.exe has been spotted in every folder. What might be a likely issue?
A. Bandwidth consumption
B. Processor consumption
C. Drive capacity consumption
D. Memory consumption
![]() C is correct. The performance and mysterious file “MB2TB” suggests malware, which greatly consumes drive space.
C is correct. The performance and mysterious file “MB2TB” suggests malware, which greatly consumes drive space.
![]() A, B, and D are incorrect. There’s no suggestion that the network bandwidth, processor, or memory is experiencing a bottleneck. However, the drive capacity does seem tight.
A, B, and D are incorrect. There’s no suggestion that the network bandwidth, processor, or memory is experiencing a bottleneck. However, the drive capacity does seem tight.
14. A user has raised a support ticket because of an unexpected dialog box on his Windows 10 laptop. He wasn’t concerned at first, because the pop-up seems a legitimate Windows prompt, as seen in Figure 10-3. However, the user cannot understand why the pop-up appears, given there seems no connection to his actions. Treating this as an incident, where would you investigate further?
A. User account “Randy.”
B. Admin account.
C. Application’s publisher.
D. This is not an incident but rather a legitimate User Access Control prompt.

Figure 10-3 User Access Control dialog box
![]() A is correct. Investigation should start with the local account “Randy,” as it appears to be the account initiating the attempted install.
A is correct. Investigation should start with the local account “Randy,” as it appears to be the account initiating the attempted install.
![]() B, C, and D are incorrect. B is incorrect because the administrator account likely isn’t compromised. If it were, the software likely would not require the credentials prompt. C is incorrect because the UAC pop-up shows a “verified” publisher. The software appears legitimate. D is incorrect because something is certainly amiss given that the UAC pop-up appears for no reason.
B, C, and D are incorrect. B is incorrect because the administrator account likely isn’t compromised. If it were, the software likely would not require the credentials prompt. C is incorrect because the UAC pop-up shows a “verified” publisher. The software appears legitimate. D is incorrect because something is certainly amiss given that the UAC pop-up appears for no reason.
15. A contractor has borrowed an older company laptop and has been using it with no issues for months. Recently the contractor came in, asking for a new laptop because his is “acting weird.” When asked for specifics, the contractor mentioned his application sometimes freezes, the browser goes to different websites, and other strange things start happening. What might be the best course of action?
A. Ensure the OS and applications are patched.
B. Increase the size of the hard drive; add more memory.
C. Create the contractor a new account.
D. Back up his data and perform a fresh, updated system install.
![]() D is correct. Given the older system was probably poorly managed and behind on patch management, the system might have been compromised. Best approach is to wipe it and start with a new, up-to-date install if the system has the resources.
D is correct. Given the older system was probably poorly managed and behind on patch management, the system might have been compromised. Best approach is to wipe it and start with a new, up-to-date install if the system has the resources.
![]() A, B, and C are incorrect. A is incorrect because although the OS and/or applications are likely not up to date on patching, it might be too late for that course of action. B is incorrect because increasing the hard drive and memory space is a good idea once the system has a fresh install. C is incorrect because creating a new account will not solve the system performance problems.
A, B, and C are incorrect. A is incorrect because although the OS and/or applications are likely not up to date on patching, it might be too late for that course of action. B is incorrect because increasing the hard drive and memory space is a good idea once the system has a fresh install. C is incorrect because creating a new account will not solve the system performance problems.
16. A security team member alerts you that a new domain account has been created, but there is no documented account request. Further, there is no legitimate way the account could be created without you or the team member’s assistance. In fact, a quick look shows you the new user account has a session active now on a local host. What is your first step?
A. Fire the team member.
B. Log off the user session.
C. Isolate the host.
D. Reset the account password.
![]() D is correct. Your first step is to reset that account’s password, quickly followed by logging off the session.
D is correct. Your first step is to reset that account’s password, quickly followed by logging off the session.
![]() A, B, and C are incorrect. A is incorrect because there’s certainly no evidence to suggest the team member is behind this. B is incorrect because this is your second step. If you log off the session, the unauthorized account would probably immediately log back on. Resetting the password first stops the user. C is incorrect because isolating the host would likely cause the unauthorized user to log in from another host.
A, B, and C are incorrect. A is incorrect because there’s certainly no evidence to suggest the team member is behind this. B is incorrect because this is your second step. If you log off the session, the unauthorized account would probably immediately log back on. Resetting the password first stops the user. C is incorrect because isolating the host would likely cause the unauthorized user to log in from another host.
17. An important file that lists numbered bank accounts is tightly controlled, including a process for making any changes to that file. Although the file has no documented changes made in months, an analyst has determined its hashed value was changed sometime between today and last week. What would cause a different hash?
A. New account added
B. Unauthorized changes made
C. Different hash generator used
D. Drive capacity increased
![]() B is correct. Whether the contextual change in the file was due to a new account being added or the account being changed, the file was changed. That change, given the process, was unauthorized and creates a different hash value when calculated.
B is correct. Whether the contextual change in the file was due to a new account being added or the account being changed, the file was changed. That change, given the process, was unauthorized and creates a different hash value when calculated.
![]() A, C, and D are incorrect. A is incorrect because regardless how the file was different, the change to the file was unlikely authorized. C is incorrect because the tool used to generate the hash value should not matter, provided the same hashing algorithm (for example, MD5) is used. D is incorrect because changing the drive capacity would not change the file.
A, C, and D are incorrect. A is incorrect because regardless how the file was different, the change to the file was unlikely authorized. C is incorrect because the tool used to generate the hash value should not matter, provided the same hashing algorithm (for example, MD5) is used. D is incorrect because changing the drive capacity would not change the file.
