THE FOLLOWING COMPTIA IT FUNDAMENTALS EXAM OBJECTIVES ARE COVERED IN THIS CHAPTER:
- 1.2 Identify common programs, applications and their purpose
- Types
- Productivity Software
- Word processing
- Spreadsheet software
- Email software
- Basic database software
- PDF viewers/creators
- Presentation software
- Desktop publishing software
- Personal Information Manager
- Remote desktop software
- Collaboration Software
- Online workspace
- Document storage/sharing
- Screen sharing software
- Video conferencing software
- Instant messaging software
- Email software
- Utility Software
- Specialized Software
- CAD
- Graphic design
- Medical
- Scientific
- Financial
- Gaming
- Entertainment
- Open source vs. commercial
- Productivity Software
- Platforms
- Mobile
- Desktop
- Web-based
- Common file types
- Types
- 1.3 Given a scenario, use software management best practices
- 1.4 Identify the following alternative technologies and their purpose
- VoIP
- Telepresence
 All of the hardware and the operating system in computers just provide a base for what you really want to use computers for, and that's to run software applications. You want your computer to help you do something—often a lot of somethings—such as writing a letter, creating a presentation, managing your taxes, or playing a game. Thanks to the myriad of software titles out there, you can do all of these things and even more, quite often doing more than one of them at one time.
All of the hardware and the operating system in computers just provide a base for what you really want to use computers for, and that's to run software applications. You want your computer to help you do something—often a lot of somethings—such as writing a letter, creating a presentation, managing your taxes, or playing a game. Thanks to the myriad of software titles out there, you can do all of these things and even more, quite often doing more than one of them at one time.
Applications are the second major classification of software (after operating systems), and that is the focus of this chapter. Topics will range from the types of applications you use to common file types to properly installing, uninstalling, and updating your programs. As part of this chapter, I will also group in the third classification of software, which is drivers. As you will learn later in this chapter, drivers are specialized software applications that let your operating system talk to your hardware.
By the end of this chapter, you will be familiar with several types of software available for use. You will also be able to recognize a large number of common file types and install, update, and uninstall applications, drivers, and your operating system. Software truly makes that box of parts sitting in front of you useful, so let's begin!
Common Software Applications and File Types
There are a lot of different software applications in the world—a lot. I wouldn't even know where to begin if asked to count them. The good news is if you want a piece of software that helps you accomplish a specific task, whether that task be productive or entertaining, you can probably find it. To make understanding software easier, in this section I'll lump applications into four different categories: productivity, collaboration, utility, and specialized.
Before getting into the types of applications and common file types, though, let's spend a little time talking about some key concepts related to how software works on computers.
Key Software Concepts
I'm going to go out on a not-so-shaky limb here and guess that you have used software before. If you have even touched a computer or a smartphone, you have. And the fact that you are reading this book means you're interested in computers, so it's an easy guess to get right. What you might not have done, though, is to take a step back and think about all of the things that need to happen for that application to run properly.

Throughout this chapter, I will use the terms software, application, and program interchangeably.
You're probably used to double-clicking or tapping an icon and having that program open or the file opening in the right program. How does that happen? First, ask yourself the question, what does the application talk to? It talks to the operating system, which talks to the hardware. If you need to save a file, the application tells the OS that you need to save the file, and the OS talks to the hard drive to make it happen. Because of this process, the most critical thing for an app to run right is for it to be able to talk to the OS. This is why you will see software made for Windows, or for Mac OS X, or for another operating system. Software vendors might have different versions for different OSs, but software written for Windows will not work on a Mac, and vice versa.
Software Platforms
Let's broaden the Mac OS X versus Windows example a bit. We can say that Mac OS X and Windows are two different software platforms, because they require applications to be programmed differently. Taking that idea to the next level, there are generally three types of platforms that an application can belong to: desktop, mobile, and web-based. Applications written for the desktop and mobile platforms reside on that local computer's hard drive and are executed locally.

For purposes of software platforms, the desktop group also includes laptops.
Web-based applications run on a server somewhere else, and your computer will connect to it and run it just like it's local. A great example of this is Google Docs, which comes with Chromebooks. The app itself is based on Google's cloud, and your Chromebook needs an Internet connection to be able to run the app. The good news is you don't need to worry about installing or updating the application, because Google does that for you. The bad news is you need to always have an Internet connection to use those apps or save files. In today's world this isn't usually a show-stopper, but there are places and times where you will be without the life-giving powers of the Internet.
Another difference between platforms is where you can find or buy new applications. For the desktop platforms, you can buy software at a brick-and-mortar store or download it from the Internet. Mobile devices have their own application store. For example, you can go to the App Store for iOS, Google Play for Android, or BlackBerry World for BlackBerry OS. Figure 4.1 shows an image of Apple's App Store.

You can see in Figure 4.1 that there are apps you can purchase, as well as a category for free apps, the ability to search for apps, and an area to update the apps currently on your device. My phone has six apps with available updates that I should probably install. Buying an app from one of these stores will download that software to your device.
Chromebooks also allow you to add apps via the Chrome Web Store. Keep in mind, though, that these apps, just like other Chromebook apps, are run from the cloud and not your local computer.

In Figure 4.1 you might have noticed that there are categories for free apps as well as ones you pay for. The free ones are called freeware, whereas the ones you purchase are considered commercial. And just like OSs, you will run into some apps that are open source. Open source apps are generally distributed as freeware, but free apps might not necessarily be open source. Commercial apps are generally neither free nor open source.
File Extensions
Let's paraphrase the question I asked in the “Key Software Concepts” section: You double-click an icon and the program opens, or you click a document and the right app opens—how does this happen? The answer is file extensions.
All files on a computer have filenames. You've seen them before, items like AcroRD32.exe, resume.doc, finances.xls, or summervaca.jpg. The file extension is the “dot whatever” part at the end, and it tells the operating system what to do with the file.

The old FAT file system influenced filenames for quite some time. In FAT, filenames were limited to an 8.3 (“eight dot three”) file-naming standard, meaning that the filename itself could be no more than eight characters followed by a period and then a three-character extension. It forced you to be very creative with filenames, because if you had something you wanted to call “Toys Western Division Profit Forecast for 2015” you might end up with something like twdpf15.xls. To someone not familiar with your work, that would look like gibberish. Today's predominant file systems do not have this limitation, although you will find that most file extensions are still three or four characters.
The file system knows that certain extensions are to directly execute a program—these are called executables. Table 4.1 lists some common executable file extensions you should know.
TABLE 4.1 Common executable file extensions
| Extension | Use |
| .exe | Short for “executable,” it tells the OS to run the program. Most Windows desktop programs use this extension. |
| .msi | For installation and removal of software within Windows. Opening an .msi file actually launches msiexec.exe, which reads the .msi file and does what it says. .msi files use Windows Installer, so think of it as standing for “Microsoft Installation.” |
| .app | Executes a program within OS X (as .exe does in Windows). |
| .bat | Batch file. Used to execute multiple commands from the Windows command prompt (cmd.exe) within one file. |
| .scexe | Self-extracting firmware updates that Hewlett-Packard (HP) produces, commonly associated with Linux machines. |

Never open an executable file you are sent via email or are otherwise unfamiliar with. Doing so is a good way to spread viruses.
Based on Table 4.1, you can see that if you're in Windows and you double-click an icon named excel.exe, it will open up Microsoft Excel, or winword.exe will open up Microsoft Word. What about files with different extensions? Why is it that if I double-click my resume.doc file, Word opens? (Not that we're complaining here, but how does the OS know to do that?) The OS keeps a list of known file extensions and associates them with specific applications. For example, if you open anything with a .doc extension, the OS knows that it needs to open Microsoft Word to read that file.
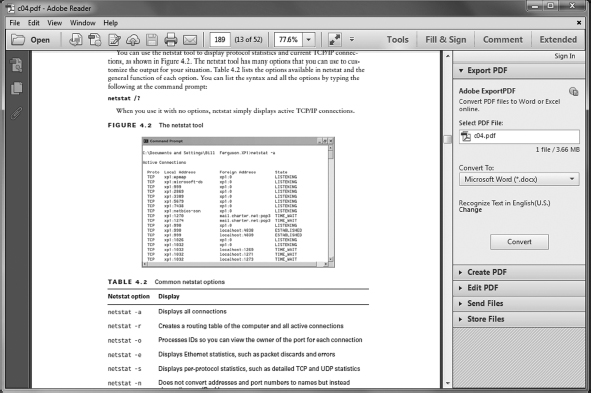
In Windows, you can go to Control Panel ![]() Programs to see and configure associations. Once in Programs, look for Default Programs and then a setting called “Make a file type always open in a specific program.” That will open the Set Associations window, like the one shown in Figure 4.2.
Programs to see and configure associations. Once in Programs, look for Default Programs and then a setting called “Make a file type always open in a specific program.” That will open the Set Associations window, like the one shown in Figure 4.2.
FIGURE 4.2 Set Associations window

In Figure 4.2, you can see that there are actually quite a few different file extensions associated with Microsoft Word. If you wanted to change the association, you would highlight the extension and click the Change Program button. We will talk more about specific file extensions and the applications they are associated with throughout this chapter.
Productivity Software
The first group of software types that we will talk about is productivity software. The group gets its name because, well, it's designed to make you more productive. The software in this section will help you get more work done and hopefully make that work easier as well.
Word Processing Software
Word processing software is one of the most common types of applications used by business and home users alike. With this software, you can create everything from simple letters or resumes to detailed reports and flyers.
The most popular word processing program on the market today is Microsoft Word, which is part of the Microsoft Office suite. Figure 4.3 shows a simple Word document.

Within a word processor, you will have the ability to change fonts and styles; insert pictures, shapes, and tables; and manage many different facets of the document's appearance.
Of course, there are several other word processing programs out there, some of which are free and others that are not. Among the commercial offerings are Word Perfect and Corel Write. Free options include Google Docs, AbiWord, Jarte, and Writer from www.OpenOffice.org. Each one has slightly different menus and features, but in general they all do the same thing. With features, sometimes you get what you pay for. In addition, the biggest issue you might run into is compatibility between formats. It's not guaranteed that a Microsoft Word document will be readable in WordPerfect or Jarte, or anything else for that matter. For the most part, you won't run into any problems with simpler documents, but more complicated files with unique features can pose problems. Compatibility can also be influenced by the format you save it in. Simple text (.txt) files are more compatible across platforms than .docx files are. Table 4.2 lists some common file extensions for word processing software.
TABLE 4.2 Word processing file extensions
| Extension | Use |
| .txt | Basic text file. Almost all word processors will open this, from the basic Notepad in Windows to Microsoft Word, and most other commercial and free apps as well. Generally, very few configuration options (such as fonts or inserting images) are available. |
| .rtf | Rich text format. A fairly basic document format developed by Microsoft and generally more compatible than .doc files. |
| .doc/.docx | Microsoft Word files. .docx files are newer and support more features than older .doc files. |
The file extensions in Table 4.2 are the only ones on the CompTIA IT Fundamentals exam objectives, but know that other extensions exist too. For example, WordPerfect typically uses the .wpd extension, AbiWord uses .abw, and OpenOffice can use several, such as .odt, .ott, and .sxw.

I have talked about Google Docs before and how it's run from Google's cloud. Microsoft has introduced a cloud-based version of its popular Office software as well, called Office 365. It gives you fully functional versions of Office software and works on workstations, tablets, and Android-based phones. You buy a subscription to use it (either monthly or yearly) and store files online just as you would with Google Docs.
Spreadsheet Software
Spreadsheets serve an important niche, which is for managing numbers and small quantities of data, and are almost as popular as word processing programs. In fact, most office “suites” of software bundle word processing and spreadsheet applications together, along with basic database and presentation software. Microsoft Office includes Word (for documents) and Excel (for worksheets), and OpenOffice has Writer and Calc. Other versions include Quattro Pro, Google Sheets, and Gnumeric (for Windows and Linux). The .xls and .xlsx extensions are associated with Microsoft Excel; Figure 4.4 shows a basic Excel worksheet.

Spreadsheet software is mostly used for the management of numbers or lists of data. You can have it do math for you using formulas, sort data, create charts and graphs, and perform relatively complex data manipulation tasks using macros. If you have more sizeable data management needs, then it's more efficient to use database software.
Email Software
Email is by far and away the most commonly used productivity application today. The vast majority of people with computers or mobile devices use it daily. It's so prevalent that it can be a distraction for people; we could argue that it actually hurts productivity for some users. Regardless of if you think you can't live without email, or if you find the number of messages you get to be overwhelming, email is an entrenched part of our society.

Because email software lets us collaborate with other users, it's also listed in the CompTIA IT Fundamentals exam objectives under Collaboration Software.
In order to use email, you need an email client. Email clients let you send and receive messages, manage your contacts and calendar, and assign yourself tasks with deadlines, and it will give you reminders when you need to follow up on something.
Most businesses will use one of two commercial email clients: Microsoft Outlook or IBM Notes (formerly Lotus Notes). There are literally dozens of other email clients that you can install on your computer, such as Eudora, GNUMail, and Mozilla Thunderbird. If you have an email account through your company, university, or other organization, you will likely use one of these clients and connect to an email server managed by that organization.
If you use Outlook and Microsoft Office, they synchronize pretty well together. Formatting Outlook emails is very similar to using Microsoft Word, and Outlook also links seamlessly with Microsoft's instant messaging software, which we'll talk about later in this chapter.
There are lots of free Internet email services that you can use as well. Examples include Gmail, Yahoo! Mail, AOL Mail, Outlook.com, and Mail.com. Each has different features and peculiarities. Most have the ability to use an instant messenger, link to your social media accounts, and work on your mobile device. Oftentimes, you also get presented with copious amounts of advertising. But they're free.
Basic Database Software
Databases come in all shapes and sizes, from small systems that hold a few hundred records to massive behemoths that hold hundreds of millions of records. Here, we'll focus on the smaller, more user-friendly variety.

Database management is a lucrative career for many IT professionals.
In its simplest form, a database doesn't look like much more than a spreadsheet. It contains data in a logical structure, which should make it easy to access. Databases can be a lot more complex, though, with multiple tables interacting with each other to produce the data you need to use. Here are some basic database terms to be familiar with:
Tables These are what look like worksheets, which contain your data. One database can (and often does) have multiple tables. Each row in a table is called a record. If you want to link multiple tables together, you need to structure the data in such a way that it makes it easy to identify which records belong with each other, such as with a customer identifier.
Forms Forms are how data is entered into and often viewed from your database. You don't need forms to have a database, but they make database management a lot easier. For example, you can have one form that lets customer service agents enter in new client information, whereas another form lets a manager review all new clients entered in the last week.
Reports Reports are generated to answer specific questions. For example, a manager could have an automatic report that generates the list of new clients in the last week, as opposed to viewing the list in a form.
Queries Queries are the real power of databases. They let you mine through your data to find the specific information you need. If you have a database with millions of records, queries are the only realistic way you will find anything useful.
Macros and Modules Macros and modules let you add functionality to your database. For example, if you want to do a monthly cleanup of all records older than a certain date, you can automate that by creating a module. For anything that you would have to run manually, you can probably create a macro to make the process faster.
You would want to go with a database instead of a spreadsheet if any of the following are true:
- You have too much data to manage in a spreadsheet.
- You have multiple users who need to access and regularly update the data.
- You allow customers to access any of the data, such as checking inventory levels through a website.
- Your data needs security measures.
As with other applications, there are plenty of basic database choices on the market, some free and some commercial. Microsoft Access comes with the Office Suite, and OpenOffice contains a database solution called Base. The key when looking for database software is to ensure that it's relatively easy to use, can expand to meet your storage needs, and has the security you require.

The most popular large-scale database provider is Oracle. Microsoft also has a popular large database platform called SQL Server.
PDF Viewers and Creators
The .pdf file format, short for Portable Document Format, was created in the early 1990s by software maker Adobe Systems. Adobe's goal was to create a document format that would work regardless of the computer platform the user had, such as Windows, Mac OS, UNIX, or Linux. Instead of needing software such as Microsoft Word, which might or might not run on your computer, you needed a .pdf reader, such as Adobe Reader (called Acrobat Reader back then), which could be installed on any OS. Usually, .pdf files are documents, but they can be flyers, worksheets, presentations, or really anything you want them to be. Some organizations use .pdf files as a very basic way to do desktop publishing.
For most of its history, the .pdf format was proprietary and owned by Adobe. In 2008, they decided to relinquish control and make it an open standard, managed by the International Organization for Standardization (ISO), which is a volunteer organization that establishes international standards.
Background on ISO
ISO might seem like it should be abbreviated IOS, but it's an international organization with three official languages: English, French, and Russian. The organization's name would require different acronyms when translated into each of the languages, so they settled on ISO. Some of the more common standards they are known for are ISO 9000, quality management; ISO 27001, information security management; ISO 14000, environmental management; and ISO 22000, food safety management. ISO isn't a policing organization, so they can't enforce standards. Compliance is accomplished more through peer pressure; showing that you are ISO-compliant indicates to potential business partners that you take quality (or information security, or whatever) seriously, so you are a legitimate business partner.
The method to read a .pdf file hasn't changed much since the early 1990s—you still need a .pdf reader. Adobe Reader is distributed free, and there are other free readers on the market as well. Most web browsers (both workstation and mobile) either have the ability to read .pdf files natively or have a module you can download to make it happen.
One of the nice features of .pdf files is that normally when you distribute them, they are read-only. Other people can't modify the files unless they have .pdf editing software, and even then you can set passwords to protect the file's contents. Another cool feature is that you can enable the .pdf file for people to edit certain parts of it. For example, say that you are distributing a form to clients, and you want them to enter in their name and address, as well as choose from several options that they might be interested in (by checking boxes). You could create a .pdf file that lets users edit those fields but not the rest of the document.
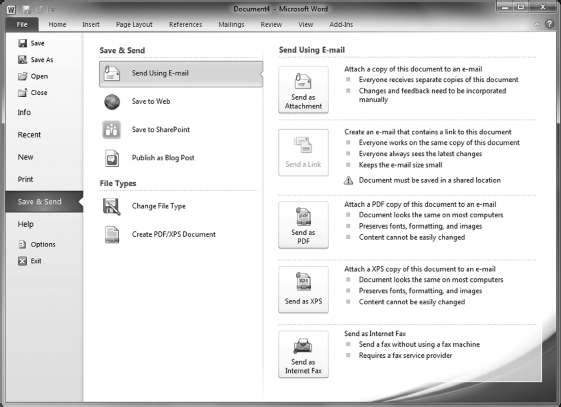
To create or edit a .pdf file you need special software called a PDF creator. The most popular creator is Adobe Acrobat, and there are several versions available. You will also find numerous free PDF converters online that will take existing documents and convert them for you. Others will convert .pdf back to a format such as .doc, but usually you need to pay for software that does this. Finally, Microsoft Office 2010 and newer have a feature that lets you generate a .pdf file directly from the application. As shown in Figure 4.5, if you go to the File menu and navigate to Save & Send, you have two options for creating PDFs—one to create a PDF/XPS document and the other to attach a PDF copy of the document in an email. Or, you can choose Save As and then select PDF. Figure 4.6 shows what a PDF file looks like inside the viewer.
FIGURE 4.5 Creating a PDF file from Word 2010
PDF viewers are commonly used, and there's no reason to not have one installed on your computer. Exercise 4.1 has you download Adobe Reader and install it on your computer.
Downloading and Installing Adobe Reader
- Go to the website https://get.adobe.com/reader.
- Optional: Deselect the check box to install McAfee Security Scan Plus.
- Click the Install Now button.
- Choose where to save the installation file. (Many times I choose the Desktop, because then it's very easy to find.)
- Double-click the installation file.
- If you get a security warning dialog box, click Run.
- Depending on your version of Windows and your security settings, you might have Windows Access Control ask you if it's okay for Adobe to make changes to your system. Click Yes to continue.
- Follow the Adobe Reader installation procedure.
- When it's complete, you will have an icon on your desktop to launch the Reader.
Presentation Software
You might find yourself in a situation where a meeting is coming up, and you need to convey a message to a group of people. Presentation software is designed to help you do that by letting you put your ideas down in slides and then share a full-screen slide show from your computer.
Within your presentation, you can add text, graphs, charts, pictures, and shapes; embed videos for playback; and even create special effects such as having text fade in or out and adding sound. You can also set it up such that the slides transition after a set amount of time. Some people do this and set up a recording of the presentation, to create what amounts to a presentation video to send to others.
As with other software types, you have plenty of presentation packages available, free and commercial, locally installed or web-based. Microsoft PowerPoint comes as part of the Microsoft Office suite and is a commonly used piece of presentation software. OpenOffice's equivalent is called Impress, and a popular Mac version is Keynote. Figure 4.7 shows you what editing a basic presentation in PowerPoint could look like. The .ppt and .pptx file extensions are associated with PowerPoint.
FIGURE 4.7 Microsoft PowerPoint

Desktop Publishing Software
If you wanted to create your own book or magazine, you would need software to help you do that, and desktop publishing is that software. Desktop publishers aren't limited to complicated offerings, though; they are perfectly capable of creating smaller projects such as pamphlets or flyers for distribution.
With today's software, there has been a blurring of the lines between what desktop publishing software can offer versus word processing applications. The long story short is word processors have gotten to the point where they offer so many features that they are almost as full-featured as desktop publishing packages out there (and in some cases more).
Stop me if you've heard this before, but there are several desktop publishing software packages available, both for free and commercial. Microsoft Office comes with Publisher, and Figure 4.8 shows what it looks like when it opens. Adobe PageMaker, QuarkXPress, and Apple Pages are other popular versions.
FIGURE 4.8 Microsoft Publisher

Perhaps the most obvious difference between Publisher and Word is that Publisher has several more built-in templates that you can choose from. Once you decide which type of document you want to create, editing that file is practically identical to using Word.
One thing that you might use more of with a desktop publisher than a word processor is image files. If you're going to create an eye-catching poster or flyer, you need to include pictures. Pictures are stored with specific file extensions, and some of the most common ones are included in Table 4.3.
TABLE 4.3 Image file extensions
| Extension | Use |
| .jpg | Called a j-peg, and sometimes you will see files with a .jpeg extension. The JPEG standard defines how images are compressed and stored. Very commonly used by digital cameras. |
| .gif | Pronounced with a hard g like the word go, it stands for Graphics Interchange Format. Uses a different compression standard than JPEG. Commonly used on websites. |
| .tiff | Pronounced like a word and sometimes found as just .tif. Stands for Tagged Image File Format. Uses lossless compression, which preserves better image quality than JPEG or GIF. |
| .png | Portable Network Graphics. Designed as a lossless compression format to replace GIF. Very common on websites. |
| .bmp | Short for bitmap. One of the oldest and simplest image formats, usually for lower-quality pictures. |
Any desktop publishing software will recognize all of the image file formats shown here. Most photo editing software will too. Occasionally you will run into photo software that only lets you edit a few of the formats, but again, most will work with any of the extensions in Table 4.3.
Personal Information Manager
If you're someone who finds yourself in a consistent state of disorganization, personal information manager (PIM) software could be just what you need. Here are some of the things that PIM software can help you organize:
- Address books
- Lists (including tasks)
- Important calendar dates
- Reminders
- Email and instant message archives
- Files, documents, photos, and videos
- Notes from meetings
If the previous list sounds like a lot of the things that you can manage in Microsoft Outlook or IBM Notes, you are right; those programs can be considered personal managers. You might also look at the list and think that your smartphone pretty much does all of that for you, and you'd also be correct. Part of the heritage of smartphones includes the personal digital assistant (PDA) such as the Palm Pilot, and so smartphones can do these things too.
In addition to your email software or your smartphone, you can find specialized software packages branded as personal information managers. Most will manage everything included in the bulleted list and will also serve as a personal diary and note-taker. A few examples are EssentialPIM, Pimero, WinPIM, MyInfo, and Chandler Project, which is shown in Figure 4.9.

Remote Desktop Software
Remote desktop software serves two purposes. One, it allows you to work on a remote computer just as if you were sitting at it. For instance, let's say you are at home and your work computer is in the next area code (and powered on), but you need to email a co-worker a file in the next five minutes or both of you get fired. Remote desktop software can let you connect to the remote machine and work as if you were sitting at it. Two, it can give someone else the ability to control your computer. Why on Earth would you let anyone do that? Perhaps you need to call technical support to fix an issue. Using remote desktop, the tech support agent can take control of your system and perform the necessary steps to troubleshoot the problem rather than having to explain the steps to you. Regardless of how computer savvy you are, this is probably much more efficient.
In order to run a remote desktop, you obviously need two computers. One system will be the master or the host and the other the slave or the client. The host system will control the client. Getting access to the client computer depends on how you have the remote desktop software configured on it. In the first example we used, you would configure the client to allow access based on a login, typically your work login and password, over a secure Internet connection. In the tech support example, the agent would send a signal to your computer asking for permission to control the system. You would get a pop-up window on your screen asking if you want to grant the remote user control. You give the permission, and control is granted.
Microsoft developed the Remote Desktop Protocol (RDP) for remote management. The client computer must have RDP client software, which is installed by default on all Windows-based computers and is available for most other OSs including OS X, Linux, iOS, and Android. The master computer needs to be running a server version of the software, which Microsoft calls Remote Desktop Connection.
Other popular versions of remote desktop software include LogMeIn, TeamViewer, Chrome Remote Desktop, and RealVNC.

Which Software Should You Choose?
You are consulting for a friend who owns a small business with about 20 employees. She is in the process of standardizing all of the software her employees use. They use a lot of productivity software, specifically presentation software, spreadsheets, and word processing applications. In addition, they quite often share the files with external agencies that collaborate on work with them. Your friend wants to keep costs down, but she also wants seamless integration with her external agencies. What should you advise her to choose?
You have probably two main choices: Microsoft Office or a free version such as OpenOffice. Both of them will provide the functionality that your friend's employees need, and odds are the employees are already familiar with Microsoft Office. The biggest concern might be sharing the files with external agencies. If the external agencies use Microsoft Office, then it will be much better for your friend's company to use it as well. If your friend is less concerned with occasional interoperability issues and more concerned about the bottom line, then the free option might be the better alternative.
Present both options along with pros and cons to your friend so she can make the most informed decision possible.
Collaboration Software
The world is more interconnected today than it has ever been. If you work in an office environment, it's entirely possible that some or all members of your work team will be located in different cities or on different continents. No matter the situation, you still need to get work done effectively as a team, just as if you were sitting in the cubicles next to each other. That's where collaboration software comes into play.
The goal of collaboration software is to blur the lines between those who work right next to you and those who do not. It's sort of fitting then that most collaboration software applications blur the lines between the categories of collaboration software listed in the CompTIA IT Fundamentals exam objectives. Said another way, one software package might be able to provide everything you need for collaboration, including working online, sharing and storing files, sharing screens, having videoconferences, and instant messaging each other. That said, we'll still look at each of the categories of collaboration software individually, mostly to address the specific goals of each type of software.
Document Storage and Sharing
If you are working with colleagues in a different location, being able to quickly and easily access the files your team needs to work on is a big deal. Today, there are multiple cloud-based services that let you store and share documents online. Examples include Google Drive, Microsoft Office Online, Box, Dropbox, Carbonite, IDrive, and OpenDrive. Some are more geared toward online backups, whereas others are focused more on making sharing easier.
Here are some key features to look for when considering online document storage and sharing:
Storage and Upload Maximums How much data will the solution allow you to store, and what is the size limit on the files you upload? This might not be as big of a deal with a small team, but if you are considering a solution for an entire organization, size limits matter.
Backups Is the data backed up? And if so, how often? There would be nothing worse than to trust someone else to manage your data and then to lose it because it hasn't been backed up.
File Synchronization This can be a big deal if multiple people are working on a file at the same time and don't realize it. How does the system know, and what version does it keep? Also, some solutions allow you to keep a virtual copy of those files on your local system. Make sure those are synchronized with the online versions.
File Encryption Are the online files encrypted when they are stored? They had better be. Storing plain-text data on a cloud-based resource is basically asking to have your data stolen.
Maintained Servers Who owns and maintains the company's servers? Do they do it themselves or license it out to a third party such as Google? Companies that own their hardware have more control over that hardware and of course have a vested interest to make sure it runs properly. There's nothing inherently wrong with a company that uses a third party such as Google to manage their cloud, but it does introduce one more player into the mix, which introduces more potential issues.
Security Mechanisms Can you set folder permissions and set different permissions for each folder? You should be able to. In addition, managing the security should be easy for anyone in your organization.
Mobile Platforms It should work with mobile devices, and most online storage and sharing systems do. Almost all online systems will synchronize with mobile devices as well.
Help and Support How accessible is their help and support system? Do they just have email support or can you get live chat if you need it?
There isn't really a one-size-fits-all solution for all business situations. The best idea is to research the different options, weigh the pros and cons, and then choose the best one for your needs.
Videoconferencing Software
The next three types of programs—videoconferencing, screen sharing, and online workspace—are very closely related to each other. In fact, most software that does any of these functions will do all of the functions. It just depends on how you want to use the service.
Videoconferencing is making a call, like a telephone call, to a remote location using your computer. As the name implies, you and the other people on the call can use webcams to see each other, as opposed to just hearing their voices. This type of solution has obvious advantages, but it also means you probably can't take calls lying around home in your pajamas anymore. Well, maybe you can—it depends on your co-workers!
The technology in this area has improved dramatically in recent years, with the goal of some of the higher-end videoconferencing suites to make you feel like you and the people on the other end of the line are actually in the same room. This has been termed telepresence. To make this seem like an authentic experience where everyone is in the same room, special videoconferencing rooms are set up. The rooms at both locations often have the same style of table and chairs and the same décor, including similar artwork and fake plants!
With most videoconferencing software packages, you have the ability to share what's on your screen. You can choose to share all applications or just one specific file. In addition, you will have options such as recording the session and allowing others to annotate on your screen. Recordings can be played back later for people who couldn't make the conference or if you want to review comments made by someone on the call.
There are dozens of software solutions available for those who want videoconferencing. Cisco WebEx, GoToMeeting, Fuze, join.me, and Adobe Connect are some popular commercial options. Free options include Skype, Google Hangouts, FaceTime, and Camfrog. The paid options usually have a Quality of Service (QoS) guarantee, whereas the free ones don't. The free ones might work fine one time and then be plagued by connection issues the next. In addition, the free ones are not as likely to have all of the same features of their commercial counterparts.
One technology that is often seen along with videoconferencing is Voice over Internet Protocol (VoIP). It isn't a specific software package but rather a group of technologies that work to deliver voice communications over the Internet or other data networks. VoIP can give you voice-only transmissions over network cables or video along with voice, all over the same network connection.

To see if you are using VoIP, look at where the phone plugs in to the wall. Does it plug into a standard phone jack or a network jack? If it's the latter, you are probably using VoIP.
The biggest advantage of VoIP and teleconferencing is that they help reduce travel costs. Instead of paying to fly people to a remote location for a meeting, you can simply connect with your business partners in another location. Good teleconferencing systems are pretty expensive, but with the travel savings, the systems pay for themselves very quickly.
Screen-Sharing Software
As the name implies, screen-sharing software focuses on sharing the contents of your screen with others. Most of the time this can be accomplished using videoconferencing software; you can share content as well as talk and see the person at the same time. Some instant messaging software programs will also let you share your screen. The same players that provide videoconferencing will give you screen sharing as well.
There are some specific screen-sharing programs that don't have videoconferencing but allow for audioconferencing and also have features like the ability for multiple people to control a mouse cursor on the screen. Screenhero is an example of this, as are Quick Screen Share and Mikogo.
Online Workspace
Online workspace specifically means that multiple people can collaborate on (and make changes to) the same file at the same time. This, of course, involves sharing the screen of the file you are working on with others. Screenhero and Mikogo are two examples of online workspaces. Features include a multiuser whiteboard, session recording, and instant messenger chat.
Instant Messaging Software
Instant messaging is sending a text note to another user in real-time. If you do it on your phone, it's typically referred to as texting. Instant message (IM) software will keep a list of contacts that you have added. Some, such as Microsoft Lync, will synchronize with your Microsoft Outlook address book to make finding connections easier. Many IM programs will also let you share your screen with those who you are chatting with.
There are dozens of IM applications, and most of them are free. In addition to Microsoft Lync, there are Yahoo! Messenger, Google Talk/Google Chat, ICQ, Messages (formerly iChat), Adium, FaceTime, AOL Instant Messenger (AIM), Pidgin, Telegram, Digsby, Trillian, Miranda IM, and many others. The key is the person you want to talk to needs to be on the same system; otherwise, you won't be able to connect. Some, such as Pidgin and Digsby, allow you to connect simultaneously across several messaging networks at the same time.
Utility Software
Many extra services that you can use on a computer are handy to have but are not necessarily ones that help you get your project done or communicate with others. These functions are managed by utility software. None of the programs in this section are mandatory, but all of them are pretty useful.
Anti-Malware
Malware is software that does harm to your computer. Why would software harm your computer? Well, because the unfortunate reality is that there are bad people in this world. It's sad in a way, because many people that are otherwise talented programmers choose to use their skills to harm others. It's reality, though, so you need to do what you can to protect your computer against malware.
The term malware is really a grouping of different types of bad programs. I am sure that many of their names will be familiar to you, such as viruses, worms, spyware, and rootkits. We'll talk about each of these in more detail in Chapter 8, “Security Threats,” but for now we'll just look at how to keep them off your computer.
As the name of this section suggests, you use anti-malware software to keep the malware off of your machine. Some of the more popular programs in the anti-malware arena are Symantec's Norton Security (formerly Norton Antivirus), McAfee, AVG, Avast, Bitdefender, Kaspersky, and Malwarebytes. When choosing a software package, it's important to understand what it specifically protects against. Some apps protect against several types of threats, but others are specifically antivirus or anti-spyware packages. There's nothing wrong with those specialized products, as long as you're aware of the level of protection your computer has.

Just because you have anti-malware installed does not mean you are guaranteed to be virus or spyware free! Still, going without the software is very dangerous for computers with an Internet connection.
How Anti-Malware Works
Generally speaking, anti-malware works by monitoring activity on your computer for any activity that appears suspicious. For example, an antivirus program is generally run in the background on a computer, and it examines all the file activity on that computer. When it detects suspicious activity, it notifies the user of a potential problem and asks the user what to do about it. Some antivirus programs can also make intelligent decisions about what to do. The process of running an antivirus program on a computer is known as inoculating the computer against a virus.

For a listing of most of the viruses that are currently out there, refer to Symantec's AntiVirus Research Center (SARC) at www.symantec.com/security_response/.
These programs have a database of known viruses and the symptoms each one causes. They look for those, as well as signatures, or specific patterns of computer code, that could be suspicious.

Antivirus databases should be updated frequently. About once a week is good, although more often is better. Most antivirus programs will automatically update themselves if configured properly.
While a true antivirus program will scan for viruses, anti-malware programs are a superset of virus scanners and will look for more than just traditional viruses, such as spyware. The operating systems from Microsoft are the ones most affected by spyware, and Microsoft has released Microsoft Security Essentials and Windows Defender to combat the problem. (Microsoft Security Essentials is also available for Windows XP/Vista/7/8).
As with similar programs, for Windows Defender to function properly, you need to keep the definitions current and scan on a regular basis. In Exercise 4.2, you'll run Windows Defender.
Run Windows Defender in Windows 7
- Choose Start
 Control Panel and in the Search Control Panel window, type Windows Defender. Click the link to open it.
Control Panel and in the Search Control Panel window, type Windows Defender. Click the link to open it. - If you are prompted that Defender is not configured, choose to turn it on (this will bring up a User Account Control prompt to continue if UAC is toggled on).
- From the drop-down list next to Help (a question mark in a blue circle), choose Check For Updates (again, if UAC is toggled on, you will be prompted to continue).
- Click Scan.
- Upon completion, the message Your computer is running normally should appear within the frame labeled No Unwanted Or Harmful Software Detected (see Figure 4.10). If anything else appears, resolve those issues.
- Exit Windows Defender.
FIGURE 4.10 Windows Defender report

Configuring Anti-Malware
After you install your software, you need to configure it. For the most part, the default settings for the anti-malware program are going to be sufficient. The biggest thing will be to ensure that the software is set to update automatically. Figure 4.11 shows the main screen of Norton Internet Security.
In Figure 4.11, you can see the security settings to turn on or off, as well as the ability to scan your system immediately and other features. To get to the configuration of updates in this software, I clicked the Settings link next to Computer. It gave me the screen in Figure 4.12, and you can see that automatic updates are on.
Removing Malware
If you think you have an infected computer, you will want to remove the malware. The following discussion presents the information you need to know for removing the bad software:
- Identify malware symptoms. Before doing anything major, it is imperative to first be sure that you are dealing with the right issue. If you suspect malware, then try to identify the type (spyware, virus, and so on) and look for the proof needed to substantiate that it is indeed the culprit.
FIGURE 4.11 Norton Internet Security

- Quarantine the infected system. Once you have confirmed that malware is at hand, then quarantine the infected system to prevent it from spreading the malware to other systems. Bear in mind that malware can spread any number of ways, including through a network connection, email, and so on. The quarantine needs to be complete to prevent any spread.
- Remediate infected systems. The steps taken here depend on the type of malware you're dealing with but should include updating antivirus software with the latest definitions and using the appropriate scan and removal techniques.
- Schedule scans and updates. The odds of the system never being confronted by malware again are slim. To reduce the chances of it being infected again, schedule scans and updates to run regularly.
- Educate the end user. Education should always be viewed as the final step. The end user needs to understand what led to the malware infestation and what to avoid, or look for, in the future to keep it from happening again.
Software Firewalls
A firewall is a hardware or software solution that serves as your network's security guard. They're probably the most important devices on networks that are connected to the Internet. Firewalls can protect you in two ways. They protect your network resources from hackers lurking in the dark corners of the Internet, and they can simultaneously prevent computers on your network from accessing undesirable content on the Internet. At a basic level, firewalls filter network traffic based on rules defined by the network administrator.
FIGURE 4.12 Automatic updates are on


Anti-malware software examines individual files for threats. Firewalls protect you from streams of network traffic that could be harmful to your computer.
Firewalls can be stand-alone “black boxes,” software installed on a server or router, or some combination of hardware and software. In addition to the categorizations of hardware and software, there are two types of firewalls: network based and host based. A network-based firewall is designed to protect a whole network of computers and almost always is a hardware solution with software on it. Host-based firewalls protect only one computer and are almost always software solutions.
How Firewalls Work
To give you fair warning, note that you won't be tested on this section on the CompTIA IT Fundamentals exam. However, it's good basic knowledge to have anyway. And if this is an area that's interesting to you, then you can literally make a career out of network security.
Most network-based firewalls have at least two network connections: one to the Internet, or public side, and one to the internal network, or private side. Some firewalls have a third network port for a second semi-internal network. This port is used to connect servers that can be considered both public and private, such as web and email servers. This intermediary network is known as a demilitarized zone (DMZ).
A firewall is configured to allow only packets (network data) that pass specific security restrictions to get through. By default, most firewalls are configured as default deny, which means that all traffic is blocked unless specifically authorized by the administrator. The basic method of configuring firewalls is to use an access control list (ACL). The ACL is the set of rules that determines which traffic gets through the firewall and which traffic is blocked. ACLs are typically configured to block traffic by IP address, port number, domain name, or some combination of all three. Packets that meet the criteria in the ACL are passed through the firewall to their destination.
Enabling a Software Firewall
Windows comes with its own software firewall called Windows Firewall. There are also numerous software firewalls on the market. I'm not going to get too deep into how to configure Windows Firewall here; we'll play with it more in the “Software Management Best Practices” section later in this chapter. For now, know that turning it on is a good thing to help protect your computer from hackers, and it should be turned on by default.
Windows Firewall is found in Control Panel under System and Security. Figure 4.13 shows what Windows Firewall looks like.
Some third-party security software, such as Norton Internet Security, comes with its own software firewall. In cases where you have those types of programs installed, they will turn off Windows Firewall automatically.
Diagnostic and Maintenance Software
You usually take it for granted that when you push the power button on your computer, it will start up and work without any issues. Even though your system might seem to be working fine, small problems could be lurking under the surface, which could turn into bigger problems down the road.
Most operating systems come with light-duty diagnostic and maintenance software built in. For example, in Chapter 2, “Peripherals and Connectors,” we looked at performance monitoring utilities. These can help you establish a baseline of system performance, and if the performance degrades, it could be a sign of trouble. Other tools can help with routine maintenance too, such as Disk Cleanup (which we talked about in Chapter 2), error checking on hard drives, and disk defragmentation. The latter two are shown in Figure 4.14, which I got to by opening Computer, right-clicking my C: drive, and selecting Properties, then selecting the Tools tab.

Clicking Check Now under Error-Checking will open up a dialog similar to the one in Figure 4.15. You can click Start to have the system scan your hard drive for errors and fix them. You would likely do this only if you're having disk read or write issues.
When Windows writes files to the hard drive, it looks for blocks of space large enough to accommodate the file being written. But because of file edits, moving files, and other OS shenanigans, this sometimes results in files becoming fragmented, or written in different parts of the drive. Excessive fragmentation can slow down hard drive reads and writes. Using Disk Defragmenter, as shown in Figure 4.16, you can rearrange the files on your hard drive to speed performance. In the case of Figure 4.16, you can see that it's automatically scheduled to run on this system, so no defragmentation is needed.
FIGURE 4.14 Hard drive properties


FIGURE 4.16 Disk defragmentation

Other third-party utilities can do a much more thorough assessment of your computer hardware and determine if there are any issues. Figure 4.17 shows the HP Hardware Diagnostic Tools screen, which comes with most HP computers. It's based on a program called PC-Doctor.
FIGURE 4.17 HP hardware diagnostics

Do I Need to Run PC Diagnostic and Maintenance Software?
Here's the scenario: you're sitting at home, surfing the Internet on your home computer. All of a sudden a window pops up, which looks a lot like a window generated by your operating system, warning you that your system has detected slow performance and you should diagnose the issue. The flashing red box beckoning you to click it seems pretty legit. What do you do?
Don't click it.
I have to be honest; I am pretty lukewarm on PC diagnostic and maintenance software. This is one of those areas where a lot of scam software products exist, and it's really hard to tell the good ones from the bad. And I might be old-school, but I get nervous any time an application offers to “scan my system for free.”
I'm not saying that all diagnostic and maintenance programs are scams; some legitimately do detect hardware issues. I just don't want to take the risk that it's not going to download spyware or pop-ups on my computer. Besides, let's say that your hard drive is indeed starting to fail. It's not like you can repair it. You can replace it, but you'll do that when it totally fails anyway. (And if you're backing up your data like you should, then you won't lose anything either.) Or if your RAM is failing, you are going to be getting occasional system errors letting you know there's a problem.
Running utilities that come with your OS to handle occasional maintenance such as defragmentation or removing temporary files that are taking up space is fine. But other than that, you can probably skip diagnostic and maintenance software and not be any worse for the wear.
What happens if you get an error message on your computer and you need to diagnose it? The best answer is Google it. Write down the error message and start typing it into Google. You'll find out what the error means, and likely get several ideas on how to fix the problem. Once again, Google comes to the rescue!
Compression Software
You probably share files with other people quite a lot, and sometimes those files get really big—so big that they can clog up your email pipes and not make it through the server. Other times, you have 20 files you want to share, but you really don't want to have to sit there and attach 20 separate files to an email. Compression software is the solution to both of these dilemmas.

Compressing a file is often called zipping a file, named after one of the compression file extensions, which is .zip.
Compression software removes redundant information within files and by doing so makes them smaller than their original size. You will see different levels of compression based on the type of file you are trying to zip. Text files and worksheets often compress quite a bit, whereas pictures don't usually see much of a size reduction. As noted earlier, compression software can also take multiple files and compress them into the same archive, which can be uncompressed later and the original files retrieved.
The gold standard in compression software for many years has been WinZip. It's a great program, but it's not free. Other popular options include WinRAR, PKZIP, 7-Zip, gzip, and Express Zip. Table 4.4 lists common compression file formats and their use.
TABLE 4.4 File compression formats
| Extension | Use |
| .rar | Compression format introduced by WinRAR program. |
| .tar | Short for tape archive, it's a format used in the UNIX and Linux environments. It's not compressed; a compressed .tar file would have the extension .tar.gz. |
| .zip | The most common compression format, supported by most compression software. Originally created by PKWARE, which makes the PKZIP program. |
| .dmg | Mac OS X disk image files. |
| .iso | Disk image archive files for optical media, such as CD-ROMs. |
| .7z | Compression files generated by the 7-Zip program. |
| .gz | Compression files generated by the gzip program, which is mostly found on UNIX and Linux systems. gzip is the replacement for the compress utility. |
| .jar | Short for Java archive; similar in format to .zip files. Usually used to distribute software programmed in the Java language. |
In Exercise 4.3, you will download and install 7-Zip and create an archive.
Installing and Using 7-Zip
- Go to www.7-zip.org/download.html.
- Click the Download link next to the file you want. For this exercise, I will download the .msi for 64-bit Windows.
- Save the file to your desktop (or other location).
- Double-click the .msi file to begin installation.
- Click the box to accept the License Agreement and click Next.
- Choose where to install the application (the defaults are fine) and then click Next.
- Click Install to begin installation.
- After installation is complete, click Finish to exit the installer.
- Click Start, and you will have the 7-Zip file manager in your applications menu. Click it to open it. You will see a screen similar to the one in Figure 4.18. You can click any folder to navigate to it, or use the up folder arrow to the left of the location bar to move up one level.
FIGURE 4.18 7-Zip file manager

- Navigate to a file or folder you want to add to the zipped archive, and click the green plus (Add) button. It will give you a screen similar to the one in Figure 4.19.
- The defaults are fine to accept, but notice that you have options. The ones you are most likely to use pertain to renaming the file, the level of compression, and password protecting the file.
FIGURE 4.19 7-Zip archive options

- Click OK, and 7-Zip will create the file for you.
- Compare the .7z file to the original. How much smaller is it?
Specialized Software
The final group of software we'll look at is specialized software. This could have also been called the “We couldn't think of a better name” group, but the truth is that each of these could rightfully be its own category. Most of them are designed to give added functionality for specific types of professions, such as graphical designers or medical doctors, but some are purely for fun.
Computer-Aided Design and Graphic Design
Computer-Aided Design (CAD) systems are used by designers of buildings and other structures as well as artists to create two- and three-dimensional drawings. If you're going to build a house, you need blueprints, and odds are they were created by an architect or engineer with a CAD program. AutoCAD is probably the best-known and most full-featured CAD package, but there are versions for novice users as well. For example, HGTV produces the HGTV Ultimate Home Design package that lets you create floorplans for a house, complete with full interior design, landscaping, and decks.
Graphic designers use similar software but obviously specialized for graphics. Practical applications include designing corporate logos, professionally altering photos (Photoshop, anyone?), or designing websites.
Medical and Scientific Software
Professionals in medical and scientific fields often have very specific software needs. If you have visited your doctor or the hospital recently, you've seen that there are computers everywhere. It's likely that those computers are running an electronic medical records (EMR) or electronic health records (EHR) package. These packages hold the patient's medical records but also allow the provider to interface with medical testing equipment such as an electrocardiogram (EKG) kit.
There are also software packages specifically for medical practice management and billing software that helps link to insurance companies. Finally, you might have seen software that lets patients link to their own records, so that when they get medical tests back, they can log in and see their results. Of course, when we're talking about medical records, privacy and security are of the utmost concern, so that's an issue to be aware of as well.
Scientific software can be somewhat universal, such as for statistical testing, or it can be highly specialized. For example, there are software packages that help aid in research in topics from bioinformatics to genetics to nuclear magnetic resonance to computational astronomy. Clearly, the processing power of computers has greatly advanced our knowledge of science.
Financial Software
Financial software has two major divisions: professional use and small business/home use. Professional investors or traders have specialized software packages that allow them to analyze the market and make trading decisions.
For small business owners or home users, there are a number of applications that help manage personal finance, such as Quicken, Microsoft Money, and iCash. Web-based apps are gaining traction in the market, led by Mint and doxo. Most of these programs allow you to set and track budgets, manage your banking, plan investment choices and retirement savings, generate reports, and pay bills automatically.
Tax preparation is another big area for small business and home users who might not want to pay for professional services. TurboTax and H&R Block's tax preparation software are the leaders in this field.
Gaming and Entertainment
For years, there has been a big debate among gamers as to which is better, PCs or consoles such as the PlayStation and Xbox. Now you can introduce mobile gaming into the equation as well, although most serious gamers would scoff and turn up their noses, noting that mobile gaming still has a long way to go.
If money is any indication, then PCs clearly dominate the gaming market. The PC gaming segment is twice the size of the console market, and it's growing, even in the midst of declining overall PC sales. Estimates have the PC gaming market at about a $23–$25 billion industry. So far in this chapter we've talked about all of these great software packages that can help productivity or ward off viruses, but gaming is a huge part of the computer industry.
It doesn't make sense to get too much into the types of games in the market today since they change over time. If you're curious, go to a retailer like Amazon.com and look under their video games section. There are numerous games available in almost every conceivable genre.
In addition to games, we love our computers because they play movies and music. Sure, we can get other devices to do those things too, but computers were made for this kind of stuff. While we're on the subject, we should talk about common video file extensions. For one, they are a test objective, and for two, you might find yourself needing to find the right movie player for the video file type you want to watch. Let's take a look at them in Table 4.5.
TABLE 4.5 Video file extensions
| Extension | Use |
| .mpg | Called an m-peg file, it's short for Moving Picture Experts Group. These are compressed files commonly found on the Internet. Most video players can handle .mpg files. |
| .mp4 | This an MPEG-4 file, or just a newer and better version of .mpg. Again, most video players can handle these files. It has the advantage over .flv of being supported natively on most mobile devices. |
| .flv | This is short for Flash Video, which is a format created by Adobe Systems. It's a competing technology to .mp4 and requires a Flash plug-in to play. It's still a common format on YouTube and Google Video. |
| .wmv | Short for Windows Media Video, it was created by Microsoft. It tends to work better on Windows-based computers than other OSs. |
| .avi | Audio Video Interleave was also developed by Microsoft. Typically it uses less compression than other formats. These files are usually more universally supported than .wmv files. |
Music is a very popular form of electronic entertainment as well. The rise of mobile devices and the relatively small size of audio files have made this combination very lucrative. Table 4.6 lists the information you need to know about audio file extensions.
TABLE 4.6 Audio file extensions
| Extension | Use |
| .mp3 | This is short for MPEG-1 Audio Layer-3, and it's an audio-only compression format created by the Moving Picture Experts Group. It compresses files into about one-twelfth their original size yet maintains near-CD quality sound. |
| .wav | Waveform Audio File Format, or just called “wave,” these are uncompressed files, and as such they have the best sound quality. They are also the largest. |
| .flac | Pronounced “flack,” this is an open-source compression format. It's not widely supported, though, so it's possible that your mobile music player won't read these files. |
| .aac | Advanced Audio Coding was designed as a replacement for .mp3. It produces better sound quality at about the same file size. This is the file format used by iTunes. |
| .m4a | This stands for MPEG-4 Audio, and it uses the same compression as .aac. It's also a replacement for .mp3. Some media players won't play these files unless they are renamed to .mp4. |
The easiest way to see if your file type is supported by your application is simply to try to open the file. If it doesn't work, and you desperately need to open the file, you can find file converters online that will convert it from one format to another.
Software Management Best Practices
Software management isn't too hard, as long as you follow a couple of basic rules—install and uninstall properly and update as needed. If you do those things, you will have relatively few problems with the software on your computer. And if or when you have a scenario where you are having problems with an application, rebooting your computer often takes care of the issue. If the issue keeps coming back, uninstall and reinstall, and you should be back up and running with no problems.
In this section, we will cover best practices for software management. First, we will talk about the stuff you need to think about before installing an application, such as whether it will work with your OS or not. Then, we'll move on to the proper way to install and uninstall features of your operating system, applications, and drivers. Finally, we'll talk about updating or patching software on your system.
Considerations for Installing Software
Before you buy any software, you need to make sure of a few critical things. The first is if the application works with your operating system, and the second is if your hardware is robust enough to support it. In addition, you should also consider the licensing requirements for that software and if your intended use falls within those requirements.
Software Compatibility
Sometimes you will find yourself standing in a store, looking at the box for a new application, and wondering, “Will this work on my computer?”
On the box for each retail application you buy, and in the documentation for each application available for download, you'll find a Minimum System Requirements section. This usually includes a list of compatible OS versions, a minimum processor speed, a minimum amount of RAM, and a minimum amount of hard disk space available. There may also be additional requirements, such as a particular display adapter, the amount of display adapter RAM, or a permanent Internet connection to use the software.
Besides the generic minimum requirements, you would also be wise to research compatibility issues before spending a lot of money on an application. For example, some applications (particularly games) have known problems with certain display adapters.

When judging whether you have enough hard disk space, keep in mind that at least 15 to 20 percent of the hard disk space should be left empty to ensure best performance. Don't assume that if your hard disk has 1 GB of space left on it, you can install an application that requires 1 GB of space.
If your system barely meets the requirements in one or more aspects, the application may install but performance may suffer. For example, the application may crash frequently, run slowly, or have poor graphic or sound performance.
If you want to run an older application that is designed for a previous version of Windows, you may find the Compatibility Mode feature in Windows to be useful. This feature enables a newer version of Windows to mimic an older version selectively when it deals with an individual application. For example, an application may require a lower display resolution than Windows 7 or Windows Vista provides; the Compatibility Mode feature can temporarily permit that lower resolution.
Some applications require an Internet connection in order to install them. Depending on the settings of your firewall software (such as Windows Firewall), a warning may appear when the Setup program tries to access the Internet. In most cases, you can click a button to let the firewall know that it's okay to proceed.
You may sometimes have to unblock certain port numbers manually in your firewall software in order to permit an application to access the Internet. (Ports are numbered pathways that help the OS keep Internet traffic routed to the right applications.) The exact steps for blocking and unblocking ports and allowing applications vary depending on the OS and the firewall software. Exercise 4.4 shows you how to do it in Windows 7. (Note that you would go through this process after installing the new software; otherwise the new software would not appear on the list.)
Configuring Windows Firewall
- Open Windows Firewall in Control Panel. To find it, you might need to choose Start
 Control Panel
Control Panel  System And Security and, under the Windows Firewall heading, click Allow A Program Through Windows Firewall.
System And Security and, under the Windows Firewall heading, click Allow A Program Through Windows Firewall. - Change settings, scroll down to the bottom of the list, and click Windows Remote Management. Select the check box to its left, as shown in Figure 4.20. The Home/Work (Private) check box is automatically selected for that entry. This is the basic way to enable a program.
FIGURE 4.20 Windows Firewall allowed programs

- Clear the check box for Windows Remote Management, and click OK. Next, you'll learn how to open a particular port number by creating a new rule.
- Back in the Control Panel's System And Security page, click the Windows Firewall heading.
- In the pane at the left, click Advanced Settings. Advanced information for the firewall appears in the Windows Firewall With Advanced Security window.
- Scroll down to the View And Create Firewall Rules section, and click Outbound Rules.
- Choose Action
 New Rule. The New Outbound Rule Wizard dialog box opens.
New Rule. The New Outbound Rule Wizard dialog box opens. - Select the Port radio button, as shown in Figure 4.21, and click Next.
FIGURE 4.21 New Outbound Rule Wizard

- Select the TCP radio button.
- Select Specific Remote Ports, and type 80 in the text box, as shown in Figure 4.22. Click Next.
FIGURE 4.22 Configuring an outbound port

- Select Allow The Connection, and click Next.
- Leave all three of the check boxes selected (Domain, Private, and Public) and click Next.
- In the Name box, type Open Port 80.
- Click Finish. The rule is created.
- Scroll through the Outbound Rules list, and select the new rule.
- Choose Action
 Delete. In the confirmation dialog box, click Yes.
Delete. In the confirmation dialog box, click Yes. - Close the Windows Firewall With Advanced Security window.
Software Licensing
When you buy an application, you aren't actually buying the application. Instead, you're buying the right to use the application in a limited way as prescribed by the licensing agreement that comes with it. Most people don't read these licensing agreements closely, but suffice it to say that they're pretty slanted in favor of the software manufacturer.
Don't like the terms? Too bad. No negotiation is allowed. If you don't accept the license agreement, your only recourse is to return the software for a refund. (And good luck finding a vendor that will take back an opened box. Still, the software manufacturer is required to take it back and refund your money if you reject the licensing.)
Although the majority of the applications you acquire will probably be commercial products, there are a number of alternatives to commercial software sales. Here are some of the license types you may encounter:
Freeware Freeware is software that is completely free. On the small scale, you can get such software from download sites such as www.download.com or from the creator's personal website. Large companies like Google and Microsoft also sometimes offer products for free, because it serves the company's interests to have lots of people using that software. Examples include Google Chrome and Microsoft Internet Explorer. Freeware doesn't include source code, and users aren't allowed to modify the application.
Open Source This software is freer than free: not only is the application free, but the source code (code used by programmers) is also shared to encourage others to contribute to the future development and improvement of the application. OSs such as Linux and applications like OpenOffice fit this category. Open source software can't be sold, although it can be bundled with commercial products that are sold.
Shareware This is software that provides a free trial, with the expectation that you'll pay for it if you like it and decide to keep it. In some cases, a shareware version isn't the full product; in other cases, it expires after a certain amount of time. Some shareware provides a full and unlimited version, with payment requested on the honor system.
Multiuser This is commercial software that you're allowed to install on more than one computer. For example, some versions of Microsoft Office allow you to install the same copy on two or three PCs.
Single User This is commercial software for which the license restricts installation to a single PC. A common misconception is that a single-user license allows you to install the software on more than one computer as long as you use only one instance at a time, but that's not accurate. Commercial products sometimes have activation systems that lock the software to a specific PC once it's installed, so you can't install it elsewhere.
Concurrent This license allows the software to be installed on many PCs but used concurrently by a smaller number. For example, you may have 1,000 computers with the application installed, but only 100 users can use it simultaneously. This is useful in situations where everyone needs to have an application available, but the application gets very little actual use.
Corporate, Campus, or Site This license permits an organization to install the application on an agreed-upon number of PCs. For example, a school may buy a site license of an antivirus program and allow all students to download and install it freely to ensure that the school's network remains virus free.
If you buy any sort of commercial software, you will receive a product key, which you will need to enter during installation or the first time the application is opened. The product key might be emailed to you, or it could be located on the physical media if you got an installation CD-ROM. Figure 4.23 shows an example of a product key.
FIGURE 4.23 Microsoft product key


How Do I Buy the Right Licenses?
Consider this situation: After talking to your boss about software licenses, you decide to investigate the office productivity software on your department's computers. You are unable to find proper documentation that the correct software licenses were purchased, leading you to wonder whether the company has the right licenses. Your boss wants to avoid any potential legal issues and asks you to go buy enough copies of the latest version of Microsoft Office for the 20 users in your department. What do you do?
The first question to ask yourself is do all 20 people use their computers at the same time? If not, then you might be able to purchase a concurrent license for fewer than 20 users. If there's the possibility of all 20 users needing Office at once, then you definitely need licenses for everyone. You might purchase a corporate license as well. Now that you have figured out what to buy, how do you do it?
One option is to go to the local computer store, load up 20 boxes of Office (if they have that many in stock), and trudge up to the cashier. A second option is to go to Microsoft's volume licensing site at http://www.microsoft.com/licensing/about-licensing/office.aspx to learn about purchasing multiple licenses. Microsoft will direct you to an authorized reseller so you can purchase them; they will email you the list of license numbers to use when installing the software. Now you need just one physical (or downloaded) copy to perform the installation.
Installing and Uninstalling Software
Software manufacturers have smartly made installing their products very easy. They understand that if the average user can't get the software onto their machine, then it won't get used and the company won't make money. The CompTIA IT Fundamentals exam lists three different objectives for installing and uninstalling software. Each requires a slightly different process, and we will cover them all here.
Operating System Features
Most operating system features are installed during the initial installation of the OS. There are some optional features that perhaps not all users need, but you do. For example, if Solitaire is not installed but you are bored at work and need to keep your sanity, you could install the games. (Not that I recommend installing or playing games at work.) Or conversely, if you're the boss and want to keep the slackers in your group from playing Solitaire, then you can remove it.
If you need to manage software that is already installed (and in this case, the OS is), you will do so through Control Panel. Exercise 4.5 walks you through how to do this in Windows 7.
Installing and Uninstalling Operating System Features
- Choose Start
 Control Panel
Control Panel  Programs.
Programs. - Under Programs And Features, choose Turn Windows Features On Or Off. (Note that you will need administrator-level privileges to do this.) You will get a screen like the one in Figure 4.24.
- In this case, the Games box is checked, indicating that this component is installed. To uninstall it, uncheck the box and click OK. You will get a message asking you to wait while Windows makes changes to features. Once the process is complete, the message box will disappear.
- Close Control Panel.
FIGURE 4.24 Turn Windows Features On Or Off


Do not enable OS features unless you are sure that you need them! Enabling unused and unnecessary features can potentially open security holes in your system, making it easier for a hacker to exploit your computer.
Applications
You will get applications either on an optical disc or by downloading them from the Internet. Installing an application from a disc is simple. Just pop the disc into the drive, and the Setup program will generally start automatically. If it doesn't, double-click the drive icon for the drive. If that doesn't start the Setup program, it will open a list of files on that disc; locate and double-click the one named Setup (or something similar).
You can also download and install applications. If you download an executable Setup file (usually it will have an .exe or .msi extension), you can double-click that file to start the setup routine.
Occasionally, an application you download may come in a compressed archive, such as a Zip file. In such a case, you must extract the contents of the archive to a new folder on your hard disk and then run the setup from that new folder.
Applications are installed in similar ways regardless of your operating system. For example, most Mac applications come with an installer, similar to Windows. In other cases, you drag the program into the Applications folder. In either case, applications are often delivered in either a .zip file or a disk image, designated with a .dmg file extension. Double-click either of these file types to access the program or installer. Earlier in this chapter, we installed the 7-Zip program. Exercise 4.6 gives you more practice installing applications if you would like it.
Installing Free Applications
- Go to www.download.com, and locate a freeware or shareware program that interests you.
- Download the Setup file for the program.
- Run the Setup file to install the application. If any problems come up, such as system permission or firewall issues, troubleshoot and solve them.
Registering and Activation
Registering software—that is, providing your contact information to the software maker—isn't usually required, but software makers try to make you believe it's in your best interest to do so. In actuality, it's a trade-off. Yes, companies want to collect your personal information for marketing purposes, and yes, they may sell it to a third party. However, if you register, you may be eligible for discounts on new versions, free updates, and other goodies.
Activating software is a different story. Some products, especially expensive ones that are frequently pirated, include activation features that lock the installed copy (by installation key code) to a particular PC, so you can't use it on multiple PCs.
In a nutshell, here's how it works. The software company maintains an online database of all the installation key codes. When you install the software, you're prompted to activate it. (Usually you have 30 days to do so, or a certain number of uses, before it stops working.) The activation program examines the hardware on your system (processor, motherboard model, and so on) and generates a code that describes the general state of the hardware. It then sends that code to the activation server online. If you try to activate the software on a different PC, the activation server compares the hardware code it has on file to the new one coming in, and if they're too different, it assumes you're installing on a different PC and refuses to let you activate the software.
How is this code generated? Manufacturers are very cagey about that, because releasing too much information may give hackers what they need to thwart the system. Generally, a small hardware change on a PC, such as a different network card or display adapter, won't be a problem. However, if you replace the motherboard, the software probably won't reactivate through the automated system.
Most of the manufacturers that use activation allow you to phone in to request an activation reset, and they will give you no grief over it the first few times. But if you repeatedly call to request additional activation chances, they'll probably think you're trying to get around the license agreement and won't let you reset the activation anymore.
Uninstalling Applications
Removing an application that you no longer want can free up disk space. In addition, if that application has a component that runs constantly in the background, removing the application can free up the memory that was previously occupied by that function.
For Mac users, unless the application specifically has a Remove folder/application, you can delete the application by dragging it to the trash. Also delete any ancillary folders or files associated with that application that may be stored in other locations, such as in the Library/Application Support folder. Doing so removes all application files and associated system resources.
With Windows systems, uninstallation is best handled through the Programs section of Control Panel. (If there's an Uninstall command or icon in the folder where the application is stored, that will lead you to the same place.) Open Control Panel and look for the Uninstall A Program option under Programs (you can see it in Figure 4.24). After you click Uninstall A Program, Windows will compile a list of programs for you. Find the application you want to remove and highlight it. Above the applications list, you should have an Uninstall option. Figure 4.25 shows an example. Click Uninstall, and follow the prompts. Using this method is known as a clean uninstallation.
FIGURE 4.25 Uninstalling an application
In Figure 4.25, you can see a Repair option next to Uninstall. If you have an application that is not working properly, you may be able to come here and repair it. If that doesn't work, you will probably need to uninstall and reinstall the program to get it to work properly.

In Uninstall Or Change A Program, you can also identify the software version of the installed applications on your computer.
During the uninstall process, you may be asked whether you want to keep certain data or configuration files. That's up to you. If you plan to reinstall the same application later (for example, if you're uninstalling to try to correct a problem rather than to get rid of the program entirely), you may want to save the configuration files. That's a double-edged sword, though, because if you're uninstalling to try to correct a problem, that problem could possibly be caused by one of those configuration files.
If you're using Linux, then depending on the version you may find different resources. Common versions such as Lubuntu have a Software Center window, as shown in Figure 4.26, where you can view and remove installed applications.
FIGURE 4.26 Lubuntu Software Center

If for some reason you can't uninstall an application using the preferred clean method, you can remove it using a brute-force method that involves manually deleting the program's files and folders and perhaps manually editing Windows Registry to remove the references to it. This is known as an unclean uninstallation.
An unclean uninstall isn't a good idea, because the potential is great for accidentally deleting a file that is essential to some other application or making a change to the Registry that results in other problems. However, sometimes unclean uninstallations happen by accident. For example, you may accidentally delete the folder containing an application, or you may abort the standard Uninstall utility accidentally, resulting in a half-removed, unusable application that won't allow itself to be removed using the utility.
If you need to perform an unclean uninstallation for some reason, here are the basic steps for doing it:
- Make sure the application isn't running. If it has a background component, turn that off.
- Delete the folder containing the program files. It's probably in the C:Program Files folder. If it's a 32-bit application on a 64-bit version of Windows, it may be in the C:Program Files (x86) folder.
- Delete the program's icons or folders from the Start menu. To do so, open the Start menu, right-click the icon or folder, and choose Delete.
- If you have enough information to know what to delete in the Registry, start the Registry Editor (click Start, type regedit, and press Enter) and make the needed changes. Be sure to always back up the Registry before you edit it!

Removing Pop-Up Windows
Several months ago, a friend brought me her computer. She was complaining that Internet browsing was nearly impossible with all of the pop-up windows she was getting. In addition, sometimes when she tried to go to specific websites to shop, she would instead be redirected to other websites. She mentioned that it had only been happening for a few weeks, after she downloaded and installed a new application.
I went into the Software section of Control Panel to see what she had installed. In there, I sorted the apps by install date. It was pretty easy to find the app she had installed. On the same date, three additional applications were also installed that she was not aware of. I used the Uninstall feature to remove the three extra apps, and all of her pop-up and redirection problems disappeared.
There are two morals of the story. First, be careful what you download and install. Second, many software issues in Windows can be easily fixed through Control Panel.
Drivers
A driver, also known as a device driver, is a piece of software written to tell the operating system how to communicate with a specific piece of hardware. Without a driver, the piece of hardware will not function. Usually, the only time you think about drivers is when you install new hardware, such as a printer.
Most of the time when you plug in your new hardware device, your OS will recognize it and begin the driver installation process for you. Sometimes your OS will have a built-in driver that it can use. If not, it will ask you to provide one.
If you have to do it manually, installing a driver is often just like installing an application. Either it will come on a CD-ROM or, more likely, you will download it from the manufacturer's website. It will probably be an .exe file; double-click it and the installation process will begin.
Here are the basic steps to installing a printer driver:
- Once you have connected and powered up the device, boot up the computer and wait for Windows to recognize the device.
- Windows will pop up a screen indicating that it has detected new hardware and is installing it. If it does not have a driver, it will ask you for one. Provide the location of the CD-ROM drive or downloaded driver file.
- Installation will finish.
If the new printer (or other device) isn't automatically detected, you can start the process manually by going to Start ![]() Devices And Printers, which will open a screen similar to the one in Figure 4.27. Click Add A Device or Add A Printer, depending on what you are trying to add.
Devices And Printers, which will open a screen similar to the one in Figure 4.27. Click Add A Device or Add A Printer, depending on what you are trying to add.
FIGURE 4.27 Devices And Printers window

You will specify the type of device, and then Windows will ask you for the driver.
Updating and Patching Software
Newer versions of existing software products are frequently released. These newer versions might fix known bugs with the application, while others will add functionality that didn't exist before. The frequency of version releases depends on the software manufacturer and the severity of the issue. If it's an update or a patch to solve an issue within the program, the manufacturer will provide that update for free.
In this section, we will look at updating and patching OSs, applications (including security software), and drivers. Here we will focus on how often you should update, scheduling updates, and automatic updates.
Updating and Patching Operating Systems
The OS is the platform on which everything else sits, so it's important that it be a stable and reliable platform.

Don't confuse updating with upgrading. Upgrading refers to replacing your current OS with a newer or more feature-rich release. For example, if you have Windows 7 and you install Windows 10 to replace it, that's an upgrade. It's also an upgrade if you go from a more basic to a more advanced version of the same OS, such as from Windows 7 Home Basic to Windows 7 Ultimate Edition. On the other hand, if you apply a free patch from Microsoft that's designed to correct a problem or provide a minor enhancement, that's an update.
You don't always have to have the most recently released OS version, but you do need a version that's current enough so that all the software you want to use runs on it. Whatever version you use, you should make sure all available security updates are applied to it to avoid problems due to viruses, worms, and other exploits.
Most OSs have an automatic update feature, which relieves users of the burden of remembering to look for and install updates. However, occasionally an update may cause a problem on some systems. For example, an update may have an incompatibility with a certain piece of hardware that you've installed, causing it to stop working, or an update may cause an older application to crash. For this reason, some network administrators prefer to keep control of updates themselves on all the PCs they support rather than enabling individual users to choose to download them or not; therefore, they may disable automatic updates on individual PCs.
On a Mac, you control the automatic updates via the Software Update dialog box, shown in Figure 4.28. (Access this from System Preferences on the Dock.) You can specify an interval at which to check for updates (for example, Weekly) and choose whether to download updates automatically.
In Windows, you control automatic updates via the Windows Update section of Control Panel. (It's in the System And Security area.) You can turn updating on/off, manually check for updates, review update history, and more. If updates are available, you can choose to install them or hide the notification of them without installing them (see Figure 4.29).
FIGURE 4.28 Automatic updates on a Mac


When you're installing updates, be aware that some updates require you to reboot the computer when they're finished installing. This can be an inconvenience if you're in the middle of an important project or have many open windows and applications. When an update requires a reboot, you can decline to restart until a more convenient time. If it's an update where a reboot is very important, the OS will remind you until you do it, letting you postpone the next reminder for a certain amount of time, from a few minutes to a few hours.
Although it may seem more convenient to avoid automatic updates because of that pesky restarting directive, there are risks associated with ignoring an available update. Some updates address critical security flaws. If you don't install updates promptly that are designed to protect your system, your PC may be vulnerable to security attacks from the Internet.
Windows Update (or Software Update on the Mac) can also recommend and install updates for certain applications, especially those made by the same company as the OS itself. Also, depending on your hardware, it may be able to make updates for your hardware drivers available, such as a new version of a display-adapter driver or network-adapter driver. In Exercise 4.7 you will configure Windows Update.
Configuring Windows Update
- Open Windows Update in Control Panel. To find it, you might need to choose Start
 Control Panel
Control Panel  System And Security
System And Security  Windows Update. Review whether there are any updates to be installed. (In Figure 4.29, for example, there is one important update shown.)
Windows Update. Review whether there are any updates to be installed. (In Figure 4.29, for example, there is one important update shown.) - Click Change Settings. Options appear for configuring Windows Update, as shown in Figure 4.30. Notice that you can schedule what time these updates occur. If your computer is not on at this time, the update will not run until after you power your system on.
- In the Important Updates section, open the drop-down list and choose Check For Updates But Let Me Choose Whether To Download And Install Them.
- Make sure all the other check boxes are selected except the last one (Show Me Detailed Notifications When New Microsoft Software Is Available).
- Click OK to return to the main Windows Update window.
- Click View Update History. A list of the previously installed updates appears, like the one shown in Figure 4.31. Review this information, noting whether they were successful, their importance, and their dates installed.
- Click the Installed Updates hyperlink near the top of the window. A list of updates appears. From this screen, you could remove an installed update.
- Click one of the updates. An Uninstall button appears at the top of the list. If you wanted to remove this update, you would click Uninstall to begin that process.
FIGURE 4.30 Windows Update settings

FIGURE 4.31 Windows Update history

- Click the back button (blue left-pointing arrow) to return to the View Update History list, and then click back again to return to Windows Update.
- If there are any updates available that haven't yet been installed, click the hyperlink to view them. The exact wording of the hyperlink depends on the number of updates available; if there is one, it will say 1 important update is available. Review the information about the update. If you decide you want it, select its check box and click OK.
- Close the Control Panel window.
Lubuntu has a program called Update Manager located in System Tools, which functions much like Windows Update and Mac's Software Update. You can see what it looks like in Figure 4.32.
FIGURE 4.32 Lubuntu Update Manager

Clicking the Settings button will let you configure options such as how often the system checks for updates as well as if they are automatically installed or not.
Major updates to the OS are typically rolled out to consumers as a service pack. A service pack is like any other update except for its scope; it typically alters the inner workings of the OS in a deeper way than a regular update.
Updating and Patching Applications
Updating or patching an application generally isn't as critical as the operating system, with the exception of your security software. As I mentioned in the last section, Windows Update and other OS updating software can sometimes find updates for your applications as well. If not, the application manufacturer will release updates and patches as downloadable files on their website. These updates are installed just like the application, with an .exe, .msi, .zip, or other file you open to begin the installation.
Security software is the one major exception. You always want to make sure that your security software is up to date, which includes its definitions library. Earlier in this chapter we looked at Norton Internet Security and its setting for automatic updates. Regardless of the antivirus or other security program you have installed, automatic updates are a good idea. They keep you from forgetting and then ending up having not updated in several months. If you do want to manually control your security updates, it's recommended that you run them at least once per week.
Updating Drivers
Drivers also require infrequent updates. Usually the only time you will want to update a driver is if you are having problems with your hardware. For example, I was having issues with my video card. Occasionally when I would resize windows in Windows, the display would freeze, go black, and then return to normal. I would see an error message stating that my display device driver had stopped responding. I updated the driver and the problem went away.

The best place to get drivers is always the manufacturer's website.
You can get to your device drivers to check for updates in a few different ways. One of the easiest ways in Windows is to open Device Manager by clicking Start and then right-clicking Computer and choosing Manage. Device Manager is in the Computer Management app shown in Figure 4.33.
In Figure 4.33, you can see the hardware devices in the center pane. If you right-click any of the devices, you will get an option that says Update Driver Software. Click that and you will get a screen similar to the one shown in Figure 4.34.
You can let Windows search the Internet for an updated driver, or you can point Windows to the location of a driver if you have downloaded one. If Windows searches and does not find an updated driver, it will let you know. Otherwise you can install it.

FIGURE 4.34 Update Driver Software screen

Another way to manage drivers is to right-click the device and choose Properties. Then go to the Drivers tab, as shown in Figure 4.35. From there you can look at driver details, update the driver, roll back the driver, disable the device, or uninstall the driver.

Occasionally you will run into issues where you install a driver update and it causes more problems than you originally had. In situations like that you can roll back the driver. This basically uninstalls the current version of the driver and reinstalls the previous version. From there, you can continue to troubleshoot the situation as needed.
Summary
In this chapter, I covered a wide range of information on software applications. I started with software concepts, such as the platform the software can run on (which OS as well as desktop, mobile, and web based), compatibility, and file extensions.
Next, you learned about different classifications of software. The first was productivity software, which helps you get your job done. Examples include word processing, spreadsheets, email, presentation software, and desktop publishing. Collaboration software was next, and that includes videoconferencing, online workspaces and storage, and instant messaging. The third category was utility software, which includes the important anti-malware and firewall software apps, as well as diagnostic software and compression programs. The last category we looked at was specialized software, really seven categories in one. Examples included CAD and graphic design; medical, scientific, and financial software; and games and entertainment.
The next major section was on best practices for software management. There, you learned about more details on software compatibility as well as licensing types and requirements. Then, we talked about installing and uninstalling software. Finally, I ended the chapter with patching and updating software on computer systems.
Exam Essentials
Know executable file extensions. Executable file extensions include .exe, .msi, .app, .bat, and .scexe.
Understand examples of productivity software. Productivity software includes word processing, spreadsheets, email, basic databases, PDF viewers and creators, presentation software, desktop publishing, personal information manager, and remote desktop software.
Know document file extensions. Document file extensions include .txt, .rtf, .doc/.docx, .xls/.xlsx, .ppt/.pptx, and .pdf.
Know image file extensions. Image file extensions include .jpg, .gif, .tiff, .png, and .bmp.
Be able to give examples of collaboration software. Collaboration software includes online workspace, document storage and sharing, screen sharing, videoconferencing, instant messaging, and email.
Know some examples of utility software. Utility software includes anti-malware, software firewalls, diagnostic and maintenance software, and compression utilities.
Know file compression formats. File compression formats include .rar, .tar, .zip, .dmg, .iso, .7z, .gz, and .jar.
Understand video file extensions. Video file extensions include .mpg, .mp4, .flv, .wmv, and .avi.
Know the common audio file extensions. Audio file extensions include .mp3, .wav, .flac, .aac, and .m4a.
Understand licensing and activation processes. Software that you purchase comes with a license to use it, which defines how you can use the software and how many people can use it. Some software packages require you to activate them before they will work, linking that software to your computer.
Know how to install and uninstall applications. Installing applications is typically done by double-clicking the .exe or other installation file or by inserting the CD and letting it auto-run. Software manager tools within your OS are generally used to uninstall applications.
Know where to configure OS auto-updates. Windows automatic updates are configured through Windows Update. Macs use Software Update, and while Linux systems can differ, many will have a feature similar to Lubuntu's Update Manager.
Chapter 4 Lab
Chapter 4 introduced a lot of software concepts that are good to know and some that are absolutely critical to the safety of your computer. For this lab, you are going to actually do two separate activities.
First, you should familiarize yourself with software that you have not used before. Most people are familiar with Microsoft Office, but not everyone has seen a competing office suite. So for the first part of the lab, go to www.openoffice.org and download Apache OpenOffice. Install it and open it. In particular, play with Writer and Calc, or whichever Microsoft Office equivalent you are most familiar with. Can you find what you need in the menus? Also, if you have a .doc or an .xls file, see if you can open it in OpenOffice. Does it work like it's supposed to?
For the second part of your lab, you need to make sure that your computer is secure and up to date on its important patches. Here are some steps you can take:
- If you don't have antivirus or anti-malware software, install some! Options are suggested in the chapter, and you can also Google search for recommended options from reputable sources.
- If you do have antivirus software, open it up and see when the last time it updated its definitions was. It should be within the last week. If not, update them.
- Make sure that your OS is scheduled to receive automatic updates. Perhaps you have a good reason why you might not want them installed automatically, but for the most part, installing automatically is the best bet.
Review Questions
- Which of the following file formats were designed to replace .mp3? (Choose two.)
- .mp4
- .flac
- .aac
- .m4a
- Rose opens her software application and gets a message stating that she has only 16 more uses of the product available. Given this scenario, what is her best course of action in order to use it more than 16 additional times?
- Activate the software.
- Register the software.
- Uninstall and reinstall the software.
- Not close the application any more.
- Which of the following file formats indicates a program that can be run on a Macintosh computer?
- .msi
- .bat
- .app
- .prog
- You have just purchased licensed software and want to install it. Which of the following are you required to enter to install this software?
- Your name and contact information
- The product key
- The serial number of your processor
- None of the above
- Which file format is used on optical media, such as CD-ROMs?
- .iso
- .dmg
- .rar
- .zip
- John purchases a single-user software license for an application and installs it on his desktop. Then he installs it on his laptop computer. In this scenario, which of the following statements is true?
- John can use the application on both computers at the same time.
- John can use the application on both computers but only one at a time.
- John can use the application on only one of the computers.
- John can share the application with his friends to install on their computers.
- Which of the following image formats produces the best quality images?
- .tiff
- .bmp
- .jpg
- .gif
- Word processing, spreadsheets, and presentation software are examples of what?
- Productivity software
- Collaboration software
- Utility software
- Operating system add-ins
- Mac OS X disk image files have what extension?
- .osx
- .img
- .dmg
- .iso
- What software is designed to let the OS talk to hardware?
- Driver
- Application
- Patch
- Virtual
- Which one of the following compression file extensions doesn't actually use compression?
- .rar
- .tar
- .7z
- .gz
- When thinking of software compatibility, which two factors matter most? (Choose two.)
- If the software will work with other software on the computer
- If the software will work with the operating system
- If the minimum hardware requirements are met
- If the software comes with automatic updates
- You have just plugged in a new HP printer to your Mac. You can't find a printer driver. What should you do given the circumstances?
- Use the default HP printer driver for Mac OS X.
- Visit Apple's website to download the printer driver.
- Visit HP's website to download the printer driver.
- Run Software Update to automatically install the printer driver.
- Susan wants to play the games that come with Windows on her computer, but they are not on the Start menu. What should she do in this scenario?
- Install the games from Control Panel.
- Install the games from Windows Update.
- Install the games from System Update.
- Delete and reinstall Windows.
- Which of the following file extensions is a worksheet created in a Microsoft spreadsheet application likely to have?
- .spd
- .ppt
- .mss
- .xls
- You just installed an antivirus program on your laptop computer. Given a scenario in which you want to maintain proper levels of security, how often should you update the software?
- At least once a week
- At least once a month
- At least once a year
- Only when a new virus is discovered
- Which file extension is used for files that execute multiple commands from within a Windows command prompt?
- .cmd
- .bat
- .exe
- .scexe
- Your boss calls you on the phone while he is trying to install software. It is telling him that he needs a product key. Where should you tell him to look for it? (Choose two.)
- On the package the installation CD came in
- In an email from the manufacturer
- On the screen in the Options menu
- In Windows Update
- A .ppt file is what type of file?
- Spreadsheet
- Database
- Compression
- Presentation
- Michael receives an email from an unknown user with a file attachment in it that has an .exe extension. What should Michael do in this situation?
- Delete the email.
- Double-click the file to open it.
- Save the file to his desktop and then open it.
- Right-click the file to identify its product key, and then install it.

