CHAPTER 3
Components of Cryptography
We’ll Cover
When talking about cryptography, it is important to understand how things fit together from a high level. The first couple chapters discussed the key (no pun intended) terms in the world of cryptography. We have explored the diverse and exciting history of cryptography (at least to me it is, and hopefully by the end of this text you will be fired up as well) to see how the technology has been applied over the years.
As we know, cryptography is both an art and a science that deals specifically with protecting and preserving information, both in the area of integrity and confidentiality. With the technology in play, any individual unaware of the method used to transform the information cannot alter or view the content. We have also seen that the information being encrypted can be anything—it’s just a matter of how we transform the information using our desired method.
The basic components of cryptography (or at least the key terms) were discussed in the first chapter, but what we didn’t talk about is how everything fits together. I gave you the terms and the background history of the art so you could get a sense of the diverse ways it has been applied as well as an understanding of the events it has been involved in over the years.
This chapter explores the various components of cryptography, discusses how they fit together, and provides examples. It also explains what each component means and why you should care.
Cryptography: Taking a Look Back and Looking Forward
Throughout our journey into cryptography, we start at the basics and then move to complex topics before noticing just how simple things really are—or, as I like to say, we go “there and back again” during our journey. Although cryptography, as you will learn, is used for many different things and in many diverse applications, it uses the same basic parts we discussed back the first chapter. Thanks to popular culture, encryption is one of the best known (although only somewhat grasped) techniques by the public, but the mechanics are not well understood. Nor does the majority of the public even know just how much lurks behind the scenes.
IMHO
Although I enjoy a good movie, don’t get the idea that the stuff you see in movies or TV is anything close to what you will enjoy in this book. I will do my best to make things interesting and exciting, but it won’t be as dramatic as in the movies. You may have seen characters such as “Q” from the James Bond series or heard hacking terminology used in TV series such as Warehouse 13, but it just doesn’t portray the technology the correct way with more emphasis on drama than the science itself. The way encryption is depicted makes for great entertainment, but nothing more. I know that most of you won’t have any aha moments from reading this book, but I just felt it was my place to point this out to dispel any misconceptions.
This is where you, my friend, start on your journey—by gaining an understanding of the components (and minutiae) that make up the world of cryptography. Along the way, you will gain an understanding of how confidentiality and integrity of all sorts of information are preserved by the different aspects of crypto.
IMHO
Cryptography means “secret writing” in Latin, and the body of knowledge is concerned with just that—writing in code as well as concealing and guarding information. Far too often people hear “cryptography” and think of encryption. Although that thinking is partially correct, it does not cover everything in the field, as you will learn.
Encryption
Encryption, as you now know, takes information and converts it to an unreadable format that can be reversed. This process can only be reversed under a very specific set of conditions that will allow the encrypted information to be decrypted. If the information cannot be readily reversed when you are given the correct instructions and combination, then it isn’t very useful.
How information is specifically transformed from one format to another is a discussion we will have later in this book. What we want to concentrate on first is the mechanics of the process and what goes into making encryption a reality for us. I’m sure you’re asking yourself, “Why wait?” The answer is simple: You should understand how the process and components work together at a high level before we dive down deep and explore how everything functions.
Encryption is absolutely ideal for protecting information from unauthorized disclosure if it is used correctly.
So now that you know what encryption is, you need to fully understand what it can and cannot do. I think this is an important subtopic to discuss before we start putting the pieces together. I want you to keep in mind the strengths and weaknesses of each system we discuss so you understand where you may effectively use a system and where you may not.
Your Plan
In this chapter, you should remember what each component does because the terminology I use here is the same as in earlier chapters. I also want you to focus on what these pieces do when they are all placed in front of you and assembled into a solution. Focusing on each of these components will provide you several benefits, but in particular I want you to think about each of the following components:
Additionally, I want you to think of the following points when considering of the encryption process and the components that comprise it:
Keep these points and questions in mind as you go through this chapter (and the entire book), as they will help you focus your thinking and serve you well later. Now, let’s get to work, young Padawan.
Visiting an Old Friend
Previously we discussed a system known as the Caesar, or Caesar’s Cipher. This system was an only-cryptographic mechanism that was used by Julius Caesar himself, which is where it gained its name. Although the cipher was not originally invented by Caesar, he made extensive use of the process when sending orders to and from his commanders in the field. The process used by the cipher is very simple by today’s standards, using a variation of a process known as a substitution cipher. Let’s take a look again at this cipher before we delve into things a bit further. Understanding the cipher will reap huge benefits for us later.
IMHO
Something I find extremely cool—or scary, depending on how you look at it—is the fact the Julius Caesar was reportedly able to encrypt and decrypt messages using his cipher in his head. Because the cipher is very simple, this may not seem like that big of deal to you, but you may not be considering everything. Let’s just say for kicks that I gave you an encrypted message, any message, and shifted the letters some number of spaces and you knew ahead of time it was three spaces to the left. Now I write you the Gettysburg Address in this code. Would you be able to read the message without pausing or even thinking about it? Could you read the message so easily that if I was listening to you and not looking at the writing I would think it was written in plain English? Maybe some of you out there could, but that doesn’t take away from the fact that it is an amazing skill to have—something that few individuals have.
Oh Caesar, those of us who are about to encrypt salute you!
The Caesar Cipher has been around for over 2,000 years, but it still provides us with a great mechanism to illustrate the concepts we need. Julius Caesar used this process to encrypt or encode his messages to his commanders in the field for the same reason the military today does—to keep sensitive information private. Although the cipher is simple in design and implementation, it is still in use today, and in fact is the one that most school children would be familiar with because it has appeared in countless puzzle game books and cereal boxes over the years.
Simply put, the process Caesar used was one that shifted each letter some number of spaces to the left (for example, Y would become B, and R would shift to U). Although the process could use any shift amount, Caesar settled on a shift of three spaces, but he could have used any number, positive or negative, in theory. It was effective at keeping secrets at the time because anyone encountering the message would most likely assume it was in a foreign language—if they could even read at all. Figure 3-1 shows that the Caesar Cipher fits in as the component doing the actual encryption process.
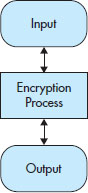
Figure 3-1 The encryption process. The Caesar Cipher would be placed in the middle step.
Let’s look at some examples. Guess the keyshift I used in each and in which direction I went.
Got that one? Let’s try another one. Remember, though, I may not be using the same key shift for each (wouldn’t want you to get too comfortable, young apprentices).
Let’s do one more, but pay closer attention to what I have done.
Is that a tricky one? If it is, go back and look again at each letter individually to see how many spaces to the left I shifted each letter. Does the shift match? Look carefully: This type of trick can be used to make decoding just a little more difficult.
So with this knowledge in hand, let’s have you try some of your own. Practice with the Caesar Cipher so you can understand it a little better. Let’s try a set of puzzles based on the Caesar Cipher, use a shift of three to the right, and put your answers in the boxes below each letter.
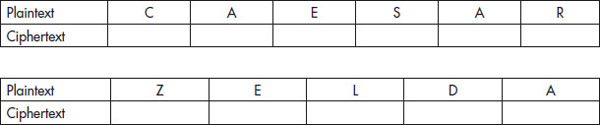
Now that you have done that, let’s go the other way with some ciphertext that has been encrypted using the Caesar Cipher. I want you to reverse the encryption process, assuming that the encryption has been done using the three-spaces-to-the-right method.
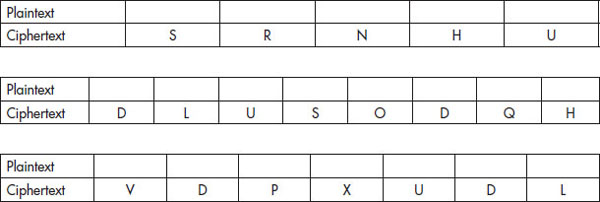
If you are having problems decrypting the ciphertext in these examples, remember what the Caesar Cipher does: It shifts the characters three spaces to the right to encrypt. This means that to decrypt you need to shift the ciphertext three spaces to the left to reverse the process.
In this next set, I am going to give you some plaintext and a keyshift that I want you to use to create some ciphertext. So put on your crypto hat and let’s have some fun. Remember that a keyshift that is preceded with a sign plus is a shift to the right, whereas one preceded with a minus sign is to the left. If you reach the end of the alphabet, continue your count from the beginning of the alphabet.
Do this first one with a keyshift of +6.
For this one, I want you to use a keyshift of -3.
For this one, use a keyshift of +4.
Use a keyshift of -4.
Now that you have done some encryption firsthand (and I am proud of you; you have taken the first steps on the road to insanity and enlightenment), you now can see how the basic encryption process works. Let’s reverse it now and see how you do (I’ll be watching).
In this next set of exercises, I want you to take the ciphertext and reverse the message into plaintext, given the key only.
If you see yourself coming up with garbage or nonsensical results when you are attempting to uncover the plaintext, really pay attention to the keyshift value and what it does. Your answer is there.
Key shift +4 to encrypt.
Key shift -2 to encrypt.
Key shift +4 to encrypt.
IMHO
If you got garbage when decrypting these messages, you may have missed the detail or clue I left you. I admit I played a little trick, but it was meant to make you think a little more and see if you were paying attention. Remember we’re working with ciphertext. So what is ciphertext? Earlier in this text it was defined as a message that is already encrypted. Now look at the keyshift I attached to each table. I said that the keyshift represents how may spaces had been shifted on the original plaintext to encrypt. You are being asked here to decrypt, so that means you must use the opposite direction. In other words, plus will become minus, and minus will become plus.
Let’s look at one final set of examples. This may be an advanced exercise, but what the heck. I think you may be able to handle this early on and take the title “Junior Codebreaker” and earn yourself a spot at the 2020 code-breaking Olympics (it could happen).
I am going to provide you with a set of encrypted messages using the Caesar Cipher and let you see if you can figure it out. I won’t pull any funny business—the messages will all be in English and will use the same keyshift all the way in each example.
VJKU DQQM KU CYGUQOG CPF KU YQTVJ GXGTZ RGPPA
HQFUATWLRQ LV IWQ
FODSZQUJPO JT FBTZ JT JU OPU
Good luck with these exercises. While completing them, keep with a mind to detail as you learn the process of one of our simpler systems.
Here’s what you saw with the Caesar Cipher:
Figure 3-2 shows you again how these components fit together.
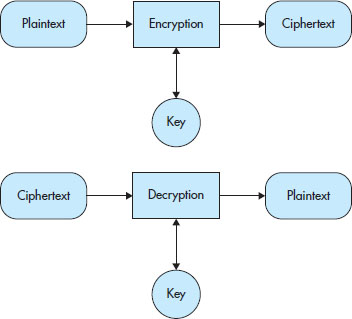
Figure 3-2 The encryption/decryption process and the relationships of the components.
IMHO
Yes, I know I gave these definitions already an earlier chapter, but I’m introducing them again here because I want to use and apply them to the Caesar Cipher to help you understand the process from both a theoretical and practical viewpoint. Why else do you think I had you do those puzzles here?
Dissecting the Caesar Cipher
Let’s take a second look at the Caesar Cipher, with the caveat that we are going to apply the terms from earlier to the system now that you have gone through it on your own.
First, let’s talk about what the plaintext was in the examples. Plaintext is the words (or in the advanced examples, the phrases) I gave you prior to encryption by the process. In my examples, I used words and simple text, but in the real world this information could be anything—alphanumeric or otherwise.
IMHO
Again, I want you to remember that plaintext is not necessarily plain, as the name may imply. Plaintext is just a term that refers to anything that is entering the encryption process—whether it is just text or something else altogether. In our earlier examples and exercises, the plaintext was just that—plain old text. However, I wanted to make sure you were not too fixated on the term and drawing a one-to-one relationship between the words plaintext and text.
The next item we need to look at is the algorithm. Cryptographic algorithms are nothing more than a set of processes and rules or other methodologies used to transform information from one state to another, and then back again when needed (at least in the case of encryption and the decryption process). Algorithms are designed to protect and/or conceal information so that we (as the intended recipient or sender) can have a level of comfort that what we are sending or receiving was not seen or altered by anyone else not authorized to possess or view it.
IMHO
I would like to point out that not all algorithms are used to conceal information from outside parties. In fact, although most algorithms are associated with encryption and decryption, they are not the only ones available, nor are they the only ones you will encounter in this text. Another type of algorithm you will encounter later is used specifically to detect alterations in information. We call this type of algorithm a “hashing algorithm.”
In this section, we discuss the Caesar Cipher due to its relative simplicity, which makes it easy to understand at this stage in the game. You will find later on, though, that algorithms can and do get extremely complex, but the concepts we will cover here will give you a strong foundation to build upon when learning about the others later on.
Let’s take a look at the Caesar Cipher and dissect it to see what the algorithm looks like. According to historical records (from the Roman historian Suetonius, as a matter of fact), Caesar simply replaced each letter in a message with the letter that is three places further down the alphabet. The process is not that complex, but it did work at that time. We can see how this works by looking at the following table, where the first row represents our regular alphabet and the second row represents Caesar Cipher and how it encrypts the standard alphabet.
In the world of cryptography, the original alphabet is commonly known as the plaintext alphabet. The second row is what is known as a ciphertext alphabet, which reflects the new positioning of the characters after a keyshift has been applied. In actuality, this ciphertext alphabet is used to substitute new characters in place of the original plaintext characters. In fact, this type process, as used in the Caesar Cipher, is the reason that the process is sometimes called the Caesar Shift Cipher.
If we wanted to write this process down in some sort of code, we could write it as a formula. Keep in mind that the cipher shifts the letters by three spaces to the right; this makes the process simple to represent as an equation (sorry about the math):
X+Y=Z
Where X equals the original location of the letter in plaintext
Where Y equals the number of spaces to move the letter
Where Z equals the new location of the letter in ciphertext
Here’s an example that shows what the Caesar Cipher specifically looks like:
X+3=Z
Where X equals the original location of the letter in plaintext
Where 3 equals the number of spaces to move the letter
Where Z equals the new location of the letter in ciphertext
Let’s think about this formula a bit in both its original form and in Caesar’s form, with three as the number of spaces. You can see the formula is essentially the same, except for this minor replacement. Does this mean that we can use any number in the position of Y? Yes, it does in fact. Let’s look at something known as ROT13.
ROT13 is a variation of the letter substitution that we have already been using with one variation where the letters are shifted 13 spaces instead of three. Much like the previous cipher, the encryption is done with a shift of 13, but it is reversed with that same amount in the opposite direction. For example, the phrase
live long and prosper
translates to the following in ROT13:
yvir ybat naq cebfcre
Another example is the following famous phrase:
veni, vidi, vici
Shift the characters 13 spaces and you get the following result:
irav, ivqv, ivpv
Let’s have you try some examples of ROT13 to see how it works:
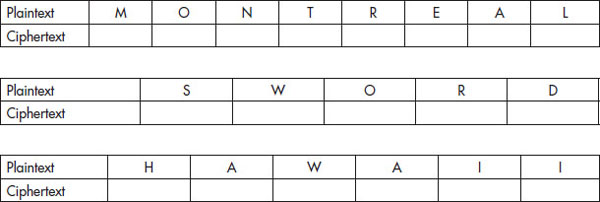
You can encrypt or decrypt a message using ROT13 using the same number. You could go 13 forward or 13 back and arrive at the same result. This property is only one of the many reasons that ROT13 is used as an example of a weak cryptographic scheme.
Much like Caesar’s Cipher before, ROT13 functions the same way, but with the difference being the number spaces used. Much like the previous cipher, the algorithm provides little-to-no cryptographic security because it is so simple and easy to figure out. In fact, the ROT13 is commonly considered a weak encryption strategy and, as such, is not used alone, but it may be combined with other mechanisms when it is used.
In Actual Practice
As an interesting piece of trivia, ROT13 was used in newsgroups way back when to hide offensive content such as dirty jokes or to hide items such as spoilers for movies or TV shows.
People would post jokes online, something like the following:
Cnffjbeqf ner yvxr haqrejrne. Lbh qba’g funer gurz, lbh qba’g unat gurz ba lbhe zbavgbe be haqre lbhe xrlobneq, lbh qba’g rznvy gurz, be chg gurz ba n jrofvgr, naq lbh zhfg punatr gurz irel bsgra.
This would translate to:
Passwords are like underwear. You don’t share them, you don’t hang them on your monitor or under your keyboard, you don’t email them, or put them on a website, and you must change them very often.
ROT13 was chosen because it’s a known system that’s easy to work with and is the only system that allows the same value to encrypt as to decrypt a message. Additionally, ROT13 was commonly supported by software applications such as newsreaders at the time.
Another application of ROT13 that may surprise you is that it was actually used in early browsers (specifically Netscape Communicator) back in 1999. The mechanism was used to store email passwords from the browser. Later in 2001, another vendor of e-books was found to be encrypting their documents with ROT13 and using the scheme in production.
One final example comes to us from the Windows XP world, where the scheme is used to encrypt some of the registry keys within Windows itself.
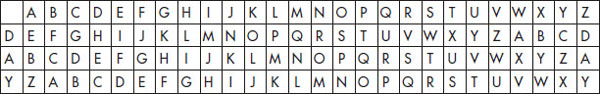
Caesar Cipher and ROT13 look simple, right? Well, let’s kick it up a notch and look at a system that’s a little more complex: the Vigenère cipher. This cipher builds on the Caesar cipher by using multiple shifted alphabets to encrypt information instead of the single one used in the Caesar cipher. For example, look at the following table:

This square is an example of what is known as a tabula recta, Vigenère table, or Vigenère square. As you can see, the table consists of the entire alphabet written out 26 times, with each row shifted to the left, making up each one of the potential Caesar ciphers. Depending on the point on the cryptographic process, a different alphabet is used. The alphabet you would use is based on a repeating keyword you would choose going in. For example, let’s use the word “day.”
Our plaintext for this exercise will be
JULIUS CAESAR
The resulting ciphertext would be
NVKMVR GBDWBQ
Let’s see how I arrived at this as the ciphertext, which is actually very simple. First, look at the plaintext phrase, which is Julius Caesar. Using this phrase, we locate our first letter across the top portion and then line it up with the first letter in the side column. Our second letter we locate in the top row and then line it up with the second letter in the side column. We keep doing this as we rotate through the letters time after time until the phrase is completely encrypted.
IMHO
The Vigenère cipher was so well designed that the mechanism was only broken 200 years later, and by the time of the U.S. Civil War it was considered to be severely compromised and not suitable for important secrets.
In the case of the Confederacy, they made things easier for the Union by using the same code words over and over again.
As you can see, the phrase that’s the code is used on the left-hand side and is used as the seed or start for each cipher alphabet. With a little bit of effort, you can create your own Vigenère cipher and encrypt your own messages.
In Actual Practice
The origin of the Vigenère cipher can be traced back all the way to the Italian genius Leon Alberti, who was born in 1404. Later in life Alberti became a polymath, with expertise as a painter, composer, poet, and philosopher. He also was responsible for designing Rome’s first Trevi fountain and having written De Re Aedificatoria, which is one of the first printed books on the subject of architecture.
Coincidentally, he also is responsible for one of the most significant developments in encryption in about a thousand years, although he failed to develop it to its full extent. This came later at the hands of several famous figures, including Johannes Trithemius, Giovanni Porta, and finally Blaise de Vigenère.
I’ll let you play with the Vigenère cipher on your own, but I am confident you will have some fun with this more advanced algorithm or encryption mechanism.
So let’s talk about the algorithms in a generic sense now that we have looked at some examples. Algorithms, for serious applications at least, are much more complex and powerful than what is seen here in our two examples. The following is an example of another encryption algorithm known as RSA, which is in a larger family of algorithms known as asymmetric or public key algorithms. I have provided some extra information, just to show how things look “under the hood.” Don’t get too caught up in the numbers and other details.
P = 61  first prime number (destroy this after computing E and D)
first prime number (destroy this after computing E and D)
Q = 53  second prime number (destroy this after computing E and D)
second prime number (destroy this after computing E and D)
PQ = 3233  modulus (give this to others)
modulus (give this to others)
E = 17  public exponent (give this to others)
public exponent (give this to others)
D = 2753  private exponent (keep this secret!)
private exponent (keep this secret!)
Your public key is (E,PQ).
Your private key is D.
The encryption function is:
The decryption function is:
LINGO
Algorithms are formulas used to describe and define the encryption and decryption process. Many different types exist, with varying levels of complexity and different potential applications as well as accompanying strengths and weaknesses.
So now that you know what an algorithm does (or at least what you need to know for right now), let’s talk about a few things. First, algorithms exist for many applications and at many different strengths, so you will never need to create or otherwise develop your own. In fact, it is highly unlikely you will ever even have the chance to create your own or even want that chance. You will most likely be in charge of selecting the appropriate encryption algorithm or cryptosystem to use in a given application or situation. Here are some factors you may consider:
Let’s now add something else into the discussion of algorithms—namely, Kerckhoffs’ Principle. This principle, which is considered to be a guideline, calls for several steps to be taken when creating or evaluating a new algorithm. As we go through the items that are part of this principle, keep in mind that they are not laws—there are no fines or other penalties for not following them.
Auguste Kerckhoffs was a Dutch linguist and cryptographer who was professor of languages at the École des Hautes Études Commerciales in Paris in the late 19th century.
Kerckhoffs originally put forth six principles as to the proper and careful design of algorithms:
Although the second point is what is formally known as Kerckhoffs’ Principle, we should cover some of the other principles on this list to fill out your knowledge of algorithms:
What Kerckhoffs’ principles do not directly cover are the topic of a key. Although the third point does mention that the key should be memorable and changeable, it doesn’t mention directly that the strength of the system relies in large part on the secrecy of the key.
Think about this for a moment: Is it practical to change or create an algorithm every time you need to encrypt something? No, absolutely not. Any useful algorithm requires that a new key is able to be selected for each and every use of the system. In order to encrypt/decrypt the plaintext/ciphertext, you need the algorithm and the key used for that particular action. If an encryption algorithm doesn’t use a key, then as soon as you know the decryption algorithm, you can decrypt all the things encrypted with the algorithm.
We can think of the problem in a different way: Is it easier to design a lock that can only ever take one design of key, or is it easier to design a lock that can take many different forms of a key? Designing a lock the first way would be incredibly stupid because you would have to design a new lock each and every time you wanted to lock something up, which is not convenient. This is why the key must be able to be changed easily without great effort.
In Actual Practice
Cryptographic wisdom considers an encryption process secure when the only way to recover a plaintext message from ciphertext is to know or discover the key. Furthermore, this rule should still be true even if every other detail about the encryption process is known. In fact, cryptographers become very concerned about the security of an algorithm when more than a key must be kept secret.
The design and use of a key is important, and indeed a large part of the strength of the cryptosystem depends on this item. A lot of misconceptions exist regarding the key within a cryptosystem, so let’s try to clear things up in this chapter.
As I said in a previous chapter, a key in a strict technical sense is only a discrete piece of information used to determine the specific settings for a given cryptographic operation. This sounds really technical and confusing, but it doesn’t have to be if we look at it in the right way. Let’s look at the key using the analogy of a lock, specifically a combination lock just like you would use on a gym locker. When this lock is designed by the manufacturer, it can have any one of a number of different combinations, but each lock will only have one specific combination that can open it. Just because you know the combination for a specific lock does not in any way mean you know the combination of another lock of the same model. In the encryption world, the key is what is used to produce a meaningful result, and without it one would not be possible.
IMHO
One way to think of a key is like the combination for a lock. You may purchase a hundred combination locks of the same model, but they will all typically have different combinations if they are preset by the manufacturer. Although it is theoretically possible that you may acquire locks with the same combination, this is intended to be highly unlikely.
I personally like the lock analogy in relation to keys because it helps when thinking of the overall encryption process later.
In the cryptographic world, a key is not the same in its purpose, though. Although a lock has a key to open it, a key in the cryptographic world dictates how the process will be performed at any one time. The choice of key is built into the algorithm itself, with a well-designed algorithm having a large keyspace (in other words, a large selection of possible keys). Encryption keys are defined by the algorithm in use at a given time. As the design of a lock that dictates all the possibilities for the shape of a physical key, an algorithm defines the range of keys that can be used.
Think of it this way: Suppose you have a combination lock much like the one you would use to lock up a bike or a gym locker. This hypothetical lock needs (in our case at least) to have a combination of eight digits that will be used by an individual to unlock the lock and open their locker or bike. In this case, we can we can write the parameters of the proposed key down in a pseudo formula as such:
Combination Length: Equal to 8
Valid Digit Range: 0 to 9
With this information in hand, we can see that the combination must be eight digits in length and each digit can only be in the range 0 to 9, inclusive. If we look at the numbers and amount of combinations that are valid, we can calculate that there are 100 million possible arrangements of digits given the information we have.
Is 100 million a lot? Well, it is and it isn’t. In human terms, the number of keys is a lot, but in the digital world not so much. In fact, many of the stronger algorithms include substantially larger numbers of keys than are possible with our simple example. In cryptography, all the potential key types possible with a particular algorithm are commonly known as the keyspace. Algorithms are designed to provide the greatest amount of protection and as such modern algorithms are designed to have a vast amount of potential keys in order to thwart guessing or brute-force attacks. Figure 3-3 shows the how the keyspace fits in to the picture.
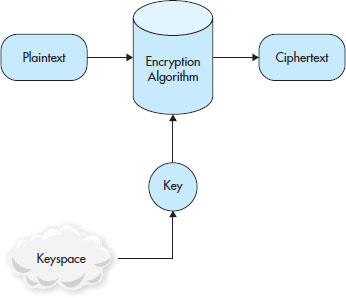
Figure 3-3 Encryption and the involvement of a keyspace
Let’s not get too comfortable, though, and think that the number of keys is a potent defense against attack; it is not the only one. Another factor is key length or size. Key length or size means that as a key gets longer, it offers stronger protection against attacks. Key length together with key size forms a stronger solution and defense against many types of key weaknesses, both by design and through outside attack.
LINGO
Key length or size refers to how “long” a key resulting from an actual algorithm may be, but there is another term referring to length of which you should be aware. This term is bit, as in a key is 40 bits or 1,024 bits.
So do longer keys make a given particular encryption scheme stronger? Well, this can be debated, but the answer is that the length of keys can have a substantial impact on the power and strength of an encryption system. Consider that a cryptosystem developed only 40 years ago with 56-bit keys would now be viewed as much weaker in the face of stronger computing systems. In fact, over the last 30 years as computing power has increased thousands of times, algorithms have had to be developed and strengthened to increase the length of keys and the number of keys available in any given system.
In Actual Practice
As increased computing power showed up on the scene, key lengths had to be increased with more bits being added to the scheme. So how much power does an extra bit add to a scheme? Consider a 56-bit key: Adding a single bit onto this changes it to a 57-bit key, which doubles the strength of the system. adding 10 more bits to make a 66-bit key makes the key 1,024 times stronger than the original 56-bit key.
By the mid-1990s, computing power that had the ability to break many of the shorter keyed cryptosystems became widely available to the public when it had been solely the domain of governments and corporations before. Moving forward 20 years to today’s world, we can see that commodity hardware (or hardware that can be purchased off the shelf) is much more accessible and available than it ever has been before. In fact, many of the computers available today to the consumer are able to process at a minimum 50,000 56-bit keys per second.
So how much does key length make a difference? The following table shows the relative strength of keys compared to one another as well as how long it would take to break each one on different hardware. The second table shows the relative value of each key length.
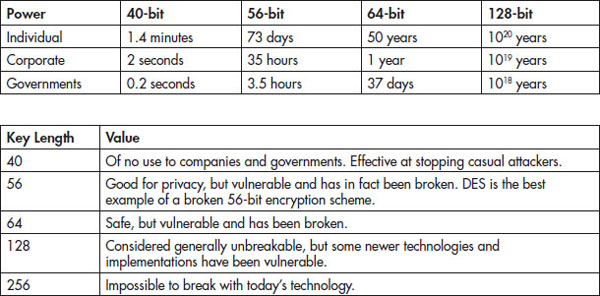
When looking at these two tables, it would seem that a longer key would automatically equal a greater amount of protection, and in many cases this is true. However, there are trade-offs in performance. A longer key generally equates to a longer encrypt/decrypt time. Additionally, the old axiom that says that “if some is good, more is better” is proven wrong here as well in relation to the length of the key and protection. In fact, the length of a key will only result in a stronger algorithm up to a point, and anything after that will just slowly plateau and result in the aforementioned increased processing time.
It may seem that if a long key is good, a longer key is better, but that is definitely not true and not for the reasons I just gave you. It may seem like keys of 4,096 bits are great (and they are used, by the way), so using something around 10,000 bits or longer is better—and we can create dedicated hardware devices that can process these keys effectively. But is it worth it? What we do not have at this point in time is a reasonable motivation to use such excessively long keys. For example, a 128-bit key is “strong enough” to defeat even the majority of the sophisticated brute-force attacks that have been employed today.
We’ve Covered
Components of cryptography
How the various components fit together
The role of keys
Algorithms and ciphers
Managing keys
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
