CHAPTER 10
Quantum Cryptography
We’ll Cover
Well now, friends, in this chapter we venture into an area that is exciting, complex, and mysterious—quantum cryptography. Unlike previously discussed forms of cryptography, this system leaves behind the purely mathematical and logic-based approaches for new ones that mix in the “magic” from the world of physics and the properties of matter.
Simply put, quantum cryptography is based on our current knowledgebase of the world of quantum physics, where we have developed new cryptosystems that cannot be defeated—or at least not using current methods. In theory, this new system cannot be defeated without the knowledge that both parties possess. So what does it take to implement this type of system? Let’s look at the name itself to get an idea. Quantum refers to behaviors that happen at the subatomic level involving particles and waves, and we use that knowledge to build an extremely strong cryptographic system.
Before we get into that, let’s talk about some situations and why the new approach is so important as well as how it came about and how it works.
So What Is Quantum Cryptography?
Quantum cryptography is a new wrinkle in the world of cryptography—one that introduces fascinating possibilities. The technique is a method used to secure information through the application of quantum mechanics.
The field of quantum mechanics is one the deals with the study of matter at the atomic and subatomic levels as well as the study of energy at these scales. The normal field of physics deals with matter at the macroscopic level, whereas quantum deals with matter at the other end of the spectrum, which is the infinitesimally small. The study of matter and energy at this scale will not only yield a better understanding of matter and energy, but helps explain how activity at this level could impact everyday life. Additionally, the principles learned from our study and application of quantum mechanics opens doors to whole new worlds of cryptographic systems.
This new spin on the field of cryptography seeks to revolutionize the security of data between parties by changing how several core components of traditional cryptography are accomplished.
Sometimes quantum cryptography goes by the name quantum key distribution, or QKD, which may give you a clue as to how it works.
Quantum cryptography, also known as quantum key distribution (QKD), is a method of secure data encryption and transmission using quantum mechanics. Using QKD, two parties can create a shared random bit string known only to them, which can be used as a key to encrypt and decrypt messages.
Before we get into exactly what this means to us, let’s look at the problems associated with traditional cryptography, as described in earlier sections of this book.
Traditional Cryptography: A Quick Review
Up to this point in this text, we have been discussing mostly traditional and classical forms of cryptography as well as public key systems. These systems emphasize protecting the privacy of sensitive information through the use of a key, and they apply the mechanism of information manipulation without regard to the secrecy of the mechanism itself.
We have looked at numerous ways of encrypting information, including the Enigma machine, Caesar cipher, and Vigenère cipher. Each one of these types of systems uses a different mechanism or process to convert plaintext to ciphertext, and back, but the end result and goal are the same: keeping data private. Even with systems such as the Enigma, which was big and clunky by today’s standards, the process conceptually is the same.
Notice a constant theme with all the ciphers and systems we have discussed so far in regard to their core function: It is the key. Any system we have covered requires and algorithm and a key to process data from one state to another, with the key being the most critical to the operation. As you’ve learned, with any system the key is the most critical item needed; in fact, without the proper key it becomes extremely difficult (depending on key strength, of course) to decrypt a message, even if the algorithm is known to the public at large. Also note that the key is critical for maintaining the secrecy of data in both symmetric and asymmetric systems.
Remember that some algorithms can have literally millions of potential keys, which would make finding the correct one extremely tough. This does not include any of the advanced cracking techniques discussed in our code-breaking chapter because these techniques will meet with varying levels of success depending on the design of the system.
Although we have a huge number of algorithms in both the asymmetric and symmetric categories, they all use some form of key. Any algorithm that is considered to be strong will have seemingly limitless numbers of keys available, making an exhaustive search of the keyspace nearly impossible (although still technically possible nonetheless). In the world of quantum cryptography, the way keys are generated and transmitted puts a new “spin” on this paradigm.
In asymmetric or public-key cryptography, two keys are generated that are interrelated mathematically. By using this process, we discovered that anyone who wants to send an encrypted message can use one key to do so, with the other key being kept secret or private. Using this system, someone can send an encrypted message that can only be decrypted by the intended recipient.
In Actual Practice
Some descriptions of public key cryptography use the example of a mailbox. In this example, we would have the mailman in possession of a key that opens the mailboxes of everyone so that he can put the mail in those boxes. The other party would be the individual who owns the mailbox. That person can open their box and would be the only person who could do so.
In traditional cryptography, which we call symmetric cryptography, only one key is utilized by all parties involved in the communication. Although all parties will possess the key and be able to use it to encrypt and decrypt, it will not be shared freely. At the same time, the algorithm can be freely shared with everyone, even those not involved in the communication (for all the reasons we mentioned back in the previous chapters). The message itself will remain safely protected in its encrypted form as long as the key is kept secret.
One of the biggest problems with shared-key cryptography is the key. How do two different parties agree on a key safely? If we just look at two parties, we need to figure out how they can agree upon a key and share it with one another without anyone else viewing or capturing it. Of course, if the parties are in close proximity, this is not a problem, but move a ZIP Code or two away, and now it becomes a concern. Additionally, if you wish to change the key regularly, you must have a process in place that is easily repeatable—which again could be problematic for reasons mentioned earlier in the book. Although we have this capability in place for cryptography already, quantum methods solves the problem much more effectively than existing methods.
Logic initially states that with traditional cryptography, we could send a message with the key information, but then how does the message with the key stay protected? Should this message be encoded then, too? If it is encoded, then again the problem becomes one of how to agree upon a key once more. This process illustrates one of the largest problems with shared-key or traditional cryptography. In the case of working with keys, this is one of the many issues with key distribution.
Eavesdropping is one of the great challenges of cryptology: How do we keep unwanted parties from obtaining secret information? After all, if it was okay for just anyone to hear, there would be no need to encrypt a message in the first place.
IMHO
Remember, even though shared-key cryptography has flaws, it is still in major use due to its increased performance over public-key systems when working with bulk data. Quantum cryptography will offer many benefits over current systems, but it is unlikely to phase out current systems “overnight.”
If we look at the alternative to the traditional systems we have explored, we have public-key cryptography. As you know, public-key cryptography utilizes a pair of keys known as the public and private key pair, which has advantages over shared-key systems. As we’ve discussed previously, shared-key systems have the inherent challenge of key transfer.
LINGO
Asymmetric algorithms use public and private keys generated when a user or party joins a system that uses a public-key algorithm.
So why call the keys public and private? Simply put, it is a question of distribution. The public key is published someplace where those who need it can get ahold of it, and the private is held by the person it was originally issued to and kept secret. By using this method of key distribution, we are in effect eliminating the need for the secrecy of the key in transit; the “exposed” key, or public key, travels across the wire and is available to everyone. It is the private key that stays secret, and subsequently stays in possession of the owner. Of course, we can’t leave it at that because the keys must be associated to the people they are assigned to in order to be trusted and authentic. How we do this association is something we discuss later, so let’s just concentrate on the algorithms at this point.
What you should be asking right now is, how does the two-key system work? First of all, the two keys are linked mathematically to one another, which is an important detail. Although in theory it may be possible to derive a private key from the public key, we can conquer this problem by engineering a system in such a way that deriving one key from another is difficult to do. This can be done in a number of ways, but one of the more common ways is to rely on a complex mathematical equation that is easy to perform one way and not the other. However, what if we had another way of handling key management?
LINGO
Remember, public-key cryptosystems are examples of zero-knowledge proof, which is a fancy way of saying that you have a means of verifying something is true without having direct knowledge. Consider this: You can verify someone has a private key by using the correct public key to reverse whatever they have done with the private. Because both keys are mathematically related, one key can reverse anything done with the other without the private key needing to be revealed.
So this system may seem ideal considering that we no longer have to worry about key distribution, right? Well, young padawan, we must look at another matter relating to the keys. When we talk about this problem, first consider that to achieve the same level of strength between asymmetric and symmetric systems, we need to have a 2,034-bit key on average for asymmetric, whereas in symmetric we need only a 128-bit key. Additionally, because of the way the algorithms work, asymmetric systems can be at least a factor of 1,000 times slower than symmetric systems. It is for this reason specifically that asymmetric is used where small amounts of data are present and not where large or bulk data is expected.
One of the biggest problems with public-key systems is that it relies on high-order mathematical operations and the sheer size of the numbers used to transform the message along with the algorithm. The numbers generated and used can easily reach extremely large proportions, which can make them both strong and extremely hard to handle by modern computing systems. What’s more, they can be made so that in order to understand each bit of output data, you have to also understand every other bit as well. This means that to crack a 128-bit key, the possible numbers used can reach upward of 1038 power. That’s a lot of possible numbers to find that one correct key needed to decode a message.
In Actual Practice
Something that I didn’t really mention earlier is that the keys used in modern cryptographic systems are so extremely large that it would take a billion computers working in parallel, with each processing a billion calculations per second, a trillion years to uncover the correct key. For those who are protecting information with a public-key system, this is great news because it makes code breaking that much more difficult. However, the current computing systems will be replaced with what are known as “quantum computers” in the future; these computers (which exploit the properties of physics on the immensely small quantum scale) will represent a threat to cryptographic strength. Due to their design, these computers will be able to perform calculations and operate at speeds no computer in use could possibly attain under any circumstance. So the codes that would take a trillion years to break with conventional computers could possibly be cracked in much less time with quantum computers, maybe taking the proverbial “blink of an eye” to do the same work.
Finding a Solution via Quantum Mechanics
So how does quantum cryptography address these issues with current cryptographic systems? The solution has been provided via the fascinating world of quantum physics. Through the use of the powerful and unique nature of matter, down at the smallest levels, researchers have found ways to exchange information not possible before. But before you can understand how quantum cryptography works, we must also take a quick look at the field of quantum mechanics. Let me first give you an overview of what quantum cryptography does before we get into how and whys it functions.
So How Does Quantum Cryptography Work?
Quantum cryptography also goes by the name quantum key distribution (QKD), which is essentially just a method of securing data using the power of quantum mechanics. Using this new powerful form of encryption, it now becomes possible for parties to share information to be used as a key that will remain known only to them without fear of eavesdropping.
Although methods such those that have been developed in public key system rely on advanced and complex mathematical functions, they cannot identify or guarantee the security of a key. Because QKD relies on a fundamental property of nature, it is far superior with regard to security.
As with traditional methods, the fundamental cryptographic requirements and operations still remain; quantum cryptography is focused on generating and distributing a key. Once this key is generated, it can be used with any given encryption algorithm during the encryption and decryption process. Although the range of algorithms that can be used is fairly broad, the one that is most commonly used is the one-time pad, because it has been proven secure when used with a secret random key.
Quantum cryptography is radically different from existing methods, to say the least. In fact, it offers an advantage that current cryptographic methods cannot—the ability to detect eavesdropping or someone trying to determine the key. This particular ability owes to something that is fundamental to the field of quantum mechanics—namely, that any attempt to measure a system will alter the system in some way. Applying this to quantum cryptography means that anyone trying to obtain the key must eavesdrop and attempt to recover the key through some means of measurement, meaning that very real and detectable changes to the system will occur. By transmitting important information in this way, it is therefore possible to detect eavesdropping.
So how does this work? I don’t promise that this will be simple to explain, and some of you who know quantum mechanics may argue with my description, but that’s fine. This is a book on cryptography and not physics, so we will simplify as much as possible to make it accessible for all of us who are mere mortals.
One of the cornerstones of physics is known as the Uncertainty Principle. Simply stated, the principle states that we are limited to what we can know about a quantum system. In layman’s terms, it means that we can understand one of two things: either the position of an object or the momentum of an object (object in this case being a particle of matter such as an electron). You can know one item or the other, but not both at the same time because measuring one will impact the other in some way.
In Actual Practice
In the physics world, the principle I am describing, rather crudely, is known as the Heisenberg Uncertainty Principle. Werner Heisenberg was a German physicist who won the Nobel Prize for Physics in 1932 for the “Creation of Quantum Mechanics.”
If it helps you visualize this a bit better, let’s use a variation of one of Heisenberg’s famous thought experiments. Imagine, if you will, a pool table that represents the boundaries for our model. In the center of this table is a lone pool ball. As part of our experiment we want to take a picture that shows the position of the pool ball (electron). To take this picture, we will bounce a particle of light off of the pool ball; to represent this particle we will use another pool ball. When we roll one pool ball at the other, no matter how gently, the system is altered when the two touch. In the case of the first pool ball, its position will be altered in some manner by the impact of the second ball. Learning about the ball’s position would create uncertainty in its velocity, and the act of measurement would produce the uncertainty needed to satisfy the principle.
Another physicist by the name of Schrödinger also had a famous experiment commonly known as Schrödinger’s Cat. In this experiment, a box with a cat inside is placed in front of the observer. Until the observer actually opens the box, the cat is both alive and dead at the same, but once the box is opened the cat is either alive or dead. The outcome in this experiment is affected by the observer and only occurs once an observation is made; until then, all possibilities exist. Figure 10-1 shows Schrödinger’s Cat experiment.
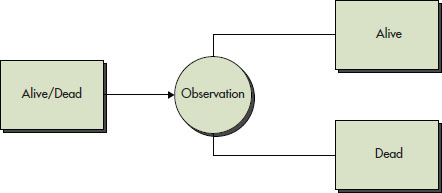
Figure 10-1 Schrödinger’s Cat experiment
In the physics world, when all possibilities exist like they do in Schrödinger’s example (alive or dead) prior to observation, this is a state of “superposition.” This is an interesting concept, to say the least, if applied to real-world situations we can relate to. For example, if I was standing at the end of a long hallway with ten closed doors, we could use these doors to represent all the possible choices you could make. If you came up to me (and I had my back to the hallway) I could tell you to open and go through one of the ten doors. If I didn’t turn around to look and observe which door you went through, a superposition would exist where you went through all 10 doors because I had not made the observation to determine which one you went through.
Objects can exist in this so-called “superposition” until we observe them directly to tell which event happened. Once that observation is made, reality (or at least our reality) collapses around that event and the other possibilities are inaccessible to us.
So let’s go a little deeper into this and talk about photons. Although many of us think of photon torpedoes from Star Trek when we hear the word photons, the term actually refers to a particle. Specifically, the photon is a measure of light that has no mass that can exist in many different states at once (something known as a wave function). Essentially what we are saying is that a photon spins in all directions at the same time, and is said to be in an unpolarized state. Figure 10-2 shows photon spin in action.
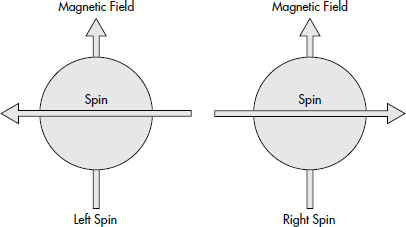
Figure 10-2 Spin of a photon
In Actual Practice
Light is made of particles known as photons, and these photons were at the center of a fundamental argument in physics. For years, physicists argued that light was either a particle or a wave. In one camp, we had those who thought light was made up of particles, and in the other camp, we had those who thought it was a series of waves. The problem was that light didn’t neatly fit into either classification. However, Einstein was able to work with other physicists to resolve the issue.
Photons were determined to be both a particle and a wave due to several unique properties. We won’t get into how and why this was determined; we will simply accept this fact for this chapter. Two interesting properties of photons are that they have no mass and carry no charge.
Photons are also what are emitted or absorbed by an atom when an electron changes its orbit (but let’s not go too far).
In case you’re wondering, the supercool technical description of a photon is “a discrete bundle or quantum of energy.” According to the laws of science, photons are always on the move, and when placed within a vacuum, they exhibit a constant speed (the speed of light) to all who observe them.
My brain hurts….
When we use photons for encryption, we can take advantage of this wave function property and Heisenberg’s principle. In current implementations of quantum cryptography, photons are generated using light-emitting diodes (LEDs) to create unpolarized light. Because LEDs have the ability to create a photon at a time instead of an explosion of photons, this allows us to implement our system. Via the use of what is known as a “polarization filter,” a photon can be induced to take on only one of the states mentioned earlier, thus making it polarized. For example, we could use a filter to polarize all the particles to have a horizontal spin instead of a random spin.
By polarizing the photons in such a manner, we no longer have the ability to measure them accurately again unless we use the same type of filter. If we were to use a vertical filter instead of a horizontal one, the photon either won’t be passed through or it will be altered. If the photon is altered by the filter, any information attached to the particle is lost. Figure 10-3 shows the transmission process of photons with information attached.
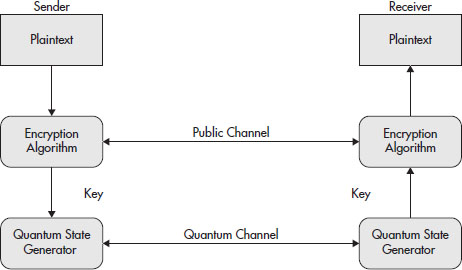
Figure 10-3 The data-transmission process with key exchange
Next comes the most important detail, which I’m sure you’re wondering about: How we can use a particle to carry information, which is the cornerstone of quantum cryptography? For that answer, let’s take a look at a few more things.
Photons as Information Carriers
You already have learned about photons, and the property called “spin,” as well as polarization, but how do photons carry information about a key? In other words, how do we use the spin of a photon to convey information about a key?
Quantum cryptography uses photons to transmit keys. Once a key is transmitted, coding and encoding using the normal secret-key method can take place. But how does a photon become a key? How do you attach information to a photon’s spin?
We now need to examine binary code, but don’t worry: We are not going to do any binary math or anything like that. As you may know, binary is simply 1’s and 0’s in computer speak, with a string of 1’s and 0’s representing an actual message. For example, 101110100001111101 could represent “Master Sword” in plain English. Because a photon can have one of several unique spins, it is a simple matter for us to assign a 1 or 0 to these spins and then interpret them accordingly. When one party transmits the photons, they simply pass the photons through randomly chosen filters and then record the results in turn. It is in this way that the transmitting party will know what results the receiving party should obtain. Figure 10-4 shows binary code assigned to a photon.
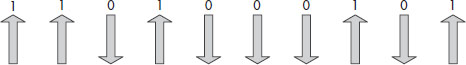
Figure 10-4 Photon spin with binary meaning assigned
Let’s envision a simple thought experiment for a moment—one where two parties (labeled A and B) are communicating. When party A transmits photons using a special LED, they will be passed through an UP, DOWN, LEFT, or RIGHT filter. When party B receives these photons, they will randomly use either the UP, DOWN, LEFT or RIGHT filters themselves. Because party B cannot use these filters simultaneously, they simply use one of the available ones because they have no idea which is the correct one. The intent here is that both sender and receiver are using a specific process, involving photons and filters, to generate a seemingly random string of “identifiable” values. Once the communication or data has been transmitted, both parties can move on to the next phase without encryption.
This next phase is unencrypted due to the way the information has been transmitted in the previous step. In this step, party B contacts party A and informs them of the filters they used and in which sequence. This is where party A will tell party B which filters are correct and which are not. So why is this unencrypted? Well, simply put, nothing can be gleaned from this process by a third party because there is not enough information to determine what is going on without knowing the original measurements and the photons involved. Eavesdropping on this information would be like hearing me tell my best friend he had the right combination to my gym locker, but at no point does either of us say the actual combination (kinda useless to anyone listening, huh?).
Their conversation may sound a little like this:
B: Up A: Correct
B: Up A: Incorrect
B: Down A: Correct
B: Up A: Incorrect
B: Down A: Correct
Note that A is not providing information on the measurements, only the type of filter actually used at each step. By performing the negotiation, party A isn’t saying what the measurements are—only the type of filters used. Therefore, a third party listening in on their conversation can’t determine what the actual photon sequence is—only that it is one of many possibilities. Although B will know which measurements are correct, a third party will not know and therefore will be unable to decode the message.
To understand this a little better, look at the following example:
1. A sends a photon as UP.
2. B uses a DOWN filter to measure the photon.
3. B will inform A that they used DOWN to measure the photon.
4. A will answer incorrectly.
There will also be points where the conversation will look like this:
1. A sends a photon as DOWN.
2. B uses a DOWN filter to measure the photon.
3. B will inform A that they used DOWN to measure the photon.
4. A will answer correctly.
Once this process has taken place, all of the incorrect answers will be discarded on party B’s side. Once this has been completed, both parties will now have identical strings of polarized photons. Although initially both parties will be left with what is ultimately a set of photons, applying the proper algorithm will convert the spin of the photons into 1’s and 0’s.
Simply put, this now means that what was a string of photons is now something like this:
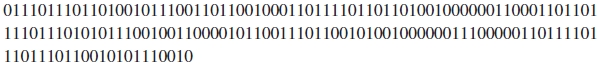
This, in turn, can now be converted into language or whatever it originally happened to be. In our case, the message would translate to:
wisdom courage power
Simple, huh?
But What About Eavesdropping?
One of the main goals of quantum cryptography is to eliminate the threat posed by eavesdropping. Whereas this has always been a problem in traditional cryptography, you will see that in the world of quantum it becomes a non-issue.
First, let’s briefly look at how current cryptographic systems work. In the current systems, a third party, whom we will call Eve, is the one who will perform the eavesdropping (I know, real creative, huh?). Eve will passively obtain the message by listening in using some method, and then she will later on attempt to decode the message using some form of code breaking or cryptanalysis. Figure 10-5 shows the eavesdropping process.
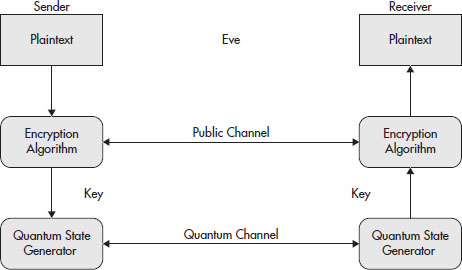
Figure 10-5 The eavesdropping process
In the world of quantum cryptography, we quickly learn that this ceases to be a problem due to the “magic” of the underlying science. As you saw previously, the Heisenberg Uncertainty Principle comes into play when that pesky snoop Eve comes sniffing around again.
Let’s see how this works:
1. A sends B a series of polarized photons.
2. Eve sets up her own filter somewhere to intercept the photons.
3. Not knowing which filters are correct and incorrect, Eve does not know which ones to use.
4. Eve randomly measures polarization of the photons.
5. Eve then passes the same photons on to B using a similar LED as before.
6. Because Eve measured the photons, the sender and receiver will be alerted to her presence.
After Eve has measured the photons by randomly selecting filters to determine their spin, she will pass them down the line to Bob using her own LED with a filter set to the alignment she chose to measure the original photon. She does this to cover up her presence and the fact that she intercepted the photon message. But due to the Heisenberg Uncertainty Principle, Eve’s presence will be detected. By measuring the photons, Eve inevitably altered some of them.
In practice, after the photons have been transmitted and A and B have had their discussion about filters, much like before, the truth would emerge. Because Eve intercepted the message and altered the photons by her interactions, when party A and B go through their “correct” or “incorrect” back and forth, the filters won’t match up, and the eavesdropping would thus be revealed. The differences in their measurements would reveal that a third party has altered the information and that the message was compromised.
A and B could take measures to further protect the data if they so choose by performing a parity check. Specifically, they would check some of the exact results obtained during the transmission to see if they match up with one another. If the chosen samples match, then the message would be considered safe and uncompromised.
The two could discard these discussed measurements and use the remaining secret measurements as their key. If discrepancies are found, they should occur in 50 percent of the parity checks. Because Eve will have altered about 25 percent of the photons through her measurements, they could reduce the likelihood that Eve has the remaining correct information down to a one-in-a-million chance by conducting additional parity checks.
So There Have to Be Problems, Right?
Every new innovation comes with new problems, despite all the neat benefits it offers—and quantum cryptography is no exception. One of the bigger problems tends to be distance—at least right now it is.
Originally, the quantum cryptography system as envisioned in 1989 was able to transmit information over a short distance of 36 centimeters. At this time, distances of 150 kilometers have been reached, which is impressive, but far short of what is needed to be practical. To be useful, the range needs to be substantial. In fact, in theory it should be, but the real world for now poses a limitation.
In the real world, the distance of transmission is so shortened due to environmental interference. Much like Eve in our earlier example, who makes changes to the photons by interacting with them, particles in the real world will get in the way of the photons, thus causing issues. In fact, the photons will bounce off of particles in the environment, and this will impact or affect the polarization they were transmitted in, meaning the information they carry will be altered. Additionally, the longer a photon travels, the more likely it will bump into something along the way.
Recently, a group of Austrian researchers solved (or started to solve) this problem by using Einstein’s work as a guide—something called “spooky action at a distance.” This observation of quantum physics is based on something known as the entanglement of photons. What this refers to is the ability for photons to become dependent on one another after having some interaction. Although we won’t worry about the nature of this entanglement and the specifics of how it happens, we can get into the basics. Entanglement doesn’t mean that particles become physically linked; instead, it means that they become connected in some way that is not currently known to science. When a pair of photons becomes entangled, the two will have the opposite spins of each other. If one particle is measured, then the other’s spin can be accurately inferred. Want know why we call this “spooky”? When these particles are moved apart, whether it is a few feet or a much, much further distance, they still will be linked—distance doesn’t seem to matter. This is much like me and my girlfriend—no matter where I am in the world, if I am happy, she is mad at me (probably because I forgot our anniversary or forgot to take out the trash). Figure 10-6 shows a rough illustration of this relationship (not the girlfriend issue).
Figure 10-6 Quantum entanglement
How does this solve the distance problem? Well, simply put, if photons are entangled and the position of one can be determined by measuring its partner, no matter how far the distance between them, then we can easily send information over long distances without having to worry about the interference of those pesky particles in the environment.
In Actual Practice
Interestingly enough, a team at the Massachusetts Institute of Technology has taken advantage of another property of entanglement. Using their research, they found that two entangled photons will stay linked with a change in one photon being reflected in its opposite. Through careful measurements, they were able to measure a property of a photon and make a well-informed assumption as to what the other properties such as spin would be. By using this method instead of measuring the spin directly, the researchers found that the photon is not adversely affected, so the eavesdropping is impossible to detect.
The method is not ready for the “big time” yet, but the team at MIT suggest it could be perfected and therefore become a threat. However, as we have seen so many times before, technology evolves and countermeasures will be found.
What you have seen here is that traditional systems rely on computational and other systems to make them tough to break. Although these systems work pretty well, the downside is that they cannot absolutely guarantee the security of a key, nor can they fully prevent eavesdropping. Therefore, quantum cryptography is magnitudes more secure than any current method.
Similarly, as with many existing systems, this new form of cryptography is used to generate and later disseminate a key. The algorithm most commonly used with quantum cryptography is the one-time pad, because it has been proven secure when used with a secret random key.
In Actual Practice
Quantum mechanics, and more specifically, cryptography, are already present in the voting systems used in democratic nations, essentially providing substantial protection to the security of the ballots themselves. When the security of the ballots is compromised, so too is the individuals’ right to choose their leaders.
The Swiss manufacturer Quantique developed a system known as “U-sing” that was used in 2007 during parliamentary elections. Information during this election was transmitted using an algorithm that utilized a key generated by quantum cryptography. Due to the magic we have seen so far, this system is nearly unbreakable and therefore the secret ballots remain just that—secret.
We’ve Covered
Quantum cryptography holds major promise and wonder, and will definitely revolutionize the whole idea of secure communications. By leveraging the seemingly mystical and complex properties of quantum mechanics over the traditional mathematical-based approaches, a new level of performance and power is reached. Some systems currently exist that can use this science, and more are becoming available each day, along with regular improvements and upgrades. Expect that within the next few years quantum-based systems will start encrypting some of the most valuable secrets of government and industry.
What is quantum cryptography?
The impact of quantum cryptography
How this new technique will change the field
How the process works
How the process differs from previous techniques
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
