Introduction
Microsoft Internet Information Services (IIS) is a web server available on Windows Server, as well as on Windows desktop systems. On Windows Server, it is considered a server role, and it is installed using the roles and features components. As a web server, IIS can run multiple web sites on multiple ports using multiple protocols. It can be managed locally or remotely through the graphical tool IIS Manager. Configuration information is stored in .xml configuration files that can be manipulated with command-line tools. Access to IIS web sites can be controlled in several ways, including filtering by properties of the client or the request. Authentication of remote clients can be done via HTTP basic authentication but can also take place using Windows authentication methods. Web sites can be protected by SSL using self-signed certificates, certificates signed by a local signing server, or by a commercial Certificate Authority. Customizable logging to plaintext log files is provided, and PowerShell can be used to parse these logs.
ModSecurity is a web application firewall that functions with IIS in much the same fashion as ModSecurity with Apache on Linux systems.
Installation
IIS 7.5 on Windows Server 2008 R2 (and Windows 7)
IIS 8.0 on Windows Server 2012 (and Windows 8)
IIS 8.5 on Windows Server 2012 R2 (and Windows 8.1)
IIS 10 on Windows Server 2016 (and Windows 10)
The installation of IIS on Windows Server is done by adding a new role to the server; this is the same technique used to install Active Directory (Chapter 6) or Windows file servers (Chapter 13). To install IIS, from Server Manager (Figure 6-1) select Add Roles and Features, or from Initial Configuration Tasks (Figure 6-4) select Add roles, then choose Web Server (IIS). Windows Server 2012, 2012 R2, and 2016 prompt the user to install the IIS Management console. Though it is possible to manage IIS remotely through another instance of the IIS Management console, it is reasonable to install it on the server alongside IIS.
HTTP Redirection
Custom Logging
Logging Tools
Request Monitor
Basic Authentication
IP and Domain Restrictions
URL Authorization
Windows Authentication
Management Service (user is prompted to add additional required components)
These are included on the example servers presented in this chapter. On a production system, only those additional role services that are required should be installed.
IIS Manager

Internet Information Services (IIS) Manager on Windows Server 2016
When IIS Manager launches on Windows Server 2012 or later, the user is asked if they want to remain connected to the latest web platform components.
The navigation pane initially connects to the local server and shows the sites enabled on that server. Some settings, like those for worker processes, are only global, but most can be set either globally, on a per-site basis, or on a per-directory basis.
Managing Multiple Web Servers from IIS Manager
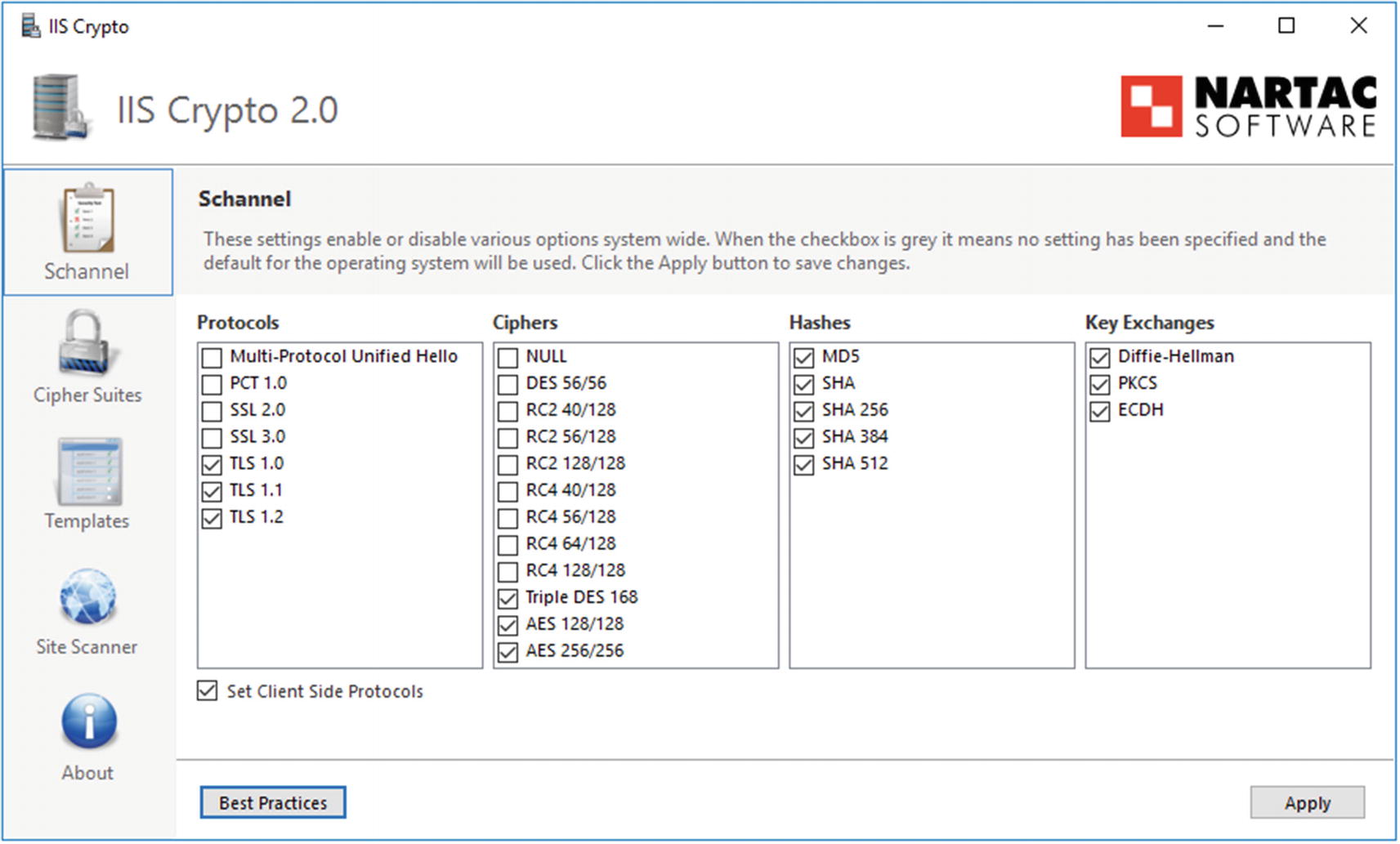
Configuring the Web Management Service on Windows Server 2016
Though this process starts the web management service, it does not configure the service to start on boot. To do so on Windows Server 2012 or later, launch Services from the Tools menu on Server Manager. On Windows Server 2008 R2, from the Start Menu navigate Administrative Tools ➤ Services. In either case, choose the entry for Web Management Service, and change the Startup type to Automatic.
To manage a remote system, from IIS Manager on the local system, select File ➤ Connect to a Server. Provide the required credentials for the remote server, specifying the domain for the user name if appropriate. In the default setting, the server uses SSL/TLS with a self-signed certificate to protect the communication. A user that connects may be warned that the certificate was issued to a different server. The user has the option of connecting to the remote server; the user can also view the remote certificate and install it locally as trusted. Depending on the remote server, the user may be prompted to add one or more additional features, including the Microsoft web management client. Connections can be saved; from the File menu select File ➤ Save Connections. Once the connection is made, a node for the new web server appears in the IIS Manager navigation pane (cf. Figure 15-5).
Enabling Remote Management on Servers Without a GUI
If the remote server does not have a graphical interface, then IIS Manager cannot be used to enable the remote management service. Instead, the remote management service needs to be enabled from the command line.
Web Sites
Microsoft IIS includes a default web site when it is installed with the name “Default Web Site”; it appears in the IIS Manager navigation pane under the Sites node (Figure 15-1). The web site name can be changed by right-clicking on the site in IIS Manager then selecting Rename.
The contents of a web site can be seen by changing IIS Manager to content view at the bottom of the page. The contents of the default web site are stored in the directory C:inetpubwwwroot. One of the entries in the action pane for a web site in IIS Manager is Explore; this brings up Windows File Manager opened to the directory in the file system that contains the web site. User access controls (UAC) prevent most simple techniques to edit the contents of the default directory. Even a domain administrator cannot simply right-click in File Explorer to create a new file in C:inetpubwwwroot, nor can they edit an existing document in that directory in Notepad and save it back.1
Adding a Second Web Site
Single IP address, single hostname, single web site
Single IP address, single hostname, multiple ports, multiple web sites
Single IP address, multiple hostnames, multiple web sites
Multiple IP addresses, multiple hostnames, multiple web sites
An administrator that wants to configure IIS to serve a second web site can start from IIS Manager, right-click on the name of the server in the navigation pane, and select Add Web Site. In the resulting dialog box (Figure 15-3), a name for the web site needs to be chosen; this is the name that appears in IIS Manager. The physical path is the location of the web site in the file system. This directory needs to be manually created; one reasonable location is inside the directory C:inetpub. When a web site is created, IIS can be configured to access the web site as a particular user; however, the default, which uses pass-through authentication, is reasonable.
A site’s bindings include the protocol (http or https), IP address, port, and hostname. All must match a request for the page to be served.

Adding a second web site named Secondary Web Site running HTTP on TCP/8080 on Windows Server 2016
Creating a web site on a non-standard port (like TCP/8080 as in this example) does not automatically open the port in the firewall; this needs to be done manually.
If a server has multiple external IP addresses, then IIS can serve separate web sites on each address. Suppose, for example, that a host has two IP addresses: 10.0.5.112 with the DNS name ananke.ad.jupiter.test, and 10.0.5.114 with the DNS name thebe.ad.jupiter.test. To create a web site for thebe.ad.jupiter.test, right-click on the name of the server in the IIS Manager navigation pane, select Add Web Site, then add a new site, specifying the site name (Thebe), physical path (C:inetpubwww-thebe), binding type (http), the IP address (10.0.5.114), and the port (TCP/80). A client that browses to ananke.ad.jupiter.test gets the IP address 10.0.5.112 from their DNS server and then gets the web page for ananke; a client that browses to thebe.ad.jupiter.test gets the IP address 10.0.5.114 from their DNS server and then gets the web page for thebe.
Default Documents
If no document is specified in a URL, then IIS attempts to return a default document. There are five default documents; in order, they are Default.htm, Default.asp, index.htm, index.html, and then iisstart.htm. When IIS looks for a default document, it looks through this list in the specified order. It does not go on to the next item in the list until it is satisfied that the current list item does not exist. An administrator can change the default documents and their order, either server-wide or for a web site. From IIS Manager, navigate to either the server or the site, double-click on Default Document, and make the desired changes.
Directory Requests
If a directory is requested and no default page exists, then IIS returns a 403 error. This behavior can be changed at the server or site level through IIS Manager via Directory Browsing. IIS allows the administrator to return a directory listing instead of the 403 error and can select which information is included in the directory listing, including the date, time, size, and extension for each file.
Error Messages
When IIS needs to return an error to the client, by default it returns different error messages for local requests and remote requests. This behavior is configured through IIS Manager, in the Error Pages feature. The action pane hyperlink Edit Feature Settings allows the administrator to use detailed errors, custom errors, or vary depending on the request source. The main body in the setting links to the various, language-specific custom error pages. By default, these are in C:inetpubcusterr, with separate subdirectories depending on the language.

Detailed error messages provided by IIS 10 on Windows Server 2016
Virtual Directories
A virtual directory is a URL path that is mapped to a portion of the file system. One way to create a virtual directory for a site is to select the site from the navigation pane of IIS Manager, then use the hyperlink View Virtual Directories from the action pane. This presents a page that shows the virtual directories for the site; the action pane then has hyperlinks to view the settings for existing virtual directories or to create a new virtual directory.
To create a new virtual directory, choose the location in the file system, as well as the alias for the virtual directory. This is the path clients take to reach the directory. As an example, if an administrator on the site server.test creates a virtual directory with the physical path C:WebData and the alias Subdirectory, then the URL http://server.test/Subdirectory/page.htm serves its content from the file C:WebDatapage.htm.
It is possible that a single directory in the file system is mapped to multiple virtual directories in multiple web sites, all with different URLs.
Command-Line Tools
Windows includes the command-line tool appcmd.exe to administer Windows IIS from the command line. This tool is not located in the system path but resides in the directory C:WindowsSystem32inetsrvappcmd.exe. The tool requires administrative privileges and must be run from an elevated command prompt.
Allowable Command and Object combinations for appcmd.exe
Command | Object |
|---|---|
list set add delete start stop | site |
list set add delete | app |
list set add delete start stop recycle | apppool |
list set add delete | vdir (virtual directories) |
list set search lock unlock clear reset migrate | config |
list | wp (worker processes) |
list | request |
list set add delete install uninstall | module (web server modules) |
list add delete restore | backup |
list configure inspect | trace |
This server is running three web sites. The first is the default, listening on all unassigned addresses on TCP/80. The second is the alternate web site listening only on 10.0.5.112, TCP/8080. The third web site is listening on the server’s second IP address 10.0.5.114 on TCP/80.
From IIS Manager, navigate to the Thebe web site and view the list of default documents to see that home.html has been added to the top of the list.
Navigate to alternate web site in IIS Manager and examine the settings for directory browsing to confirm that the changes have been made.
Access Control
An administrator can deny access to the server, a web site, or a directory (including a virtual directory) by IP address range. This is done via the IP and Domain Restrictions role; this role must be manually added during IIS installation. Navigate to the component (server, site, or directory) in IIS Manager, then select IP Address and Domain Restrictions.
The action pane hyperlink Edit Feature Settings is used to determine the default response; this is set to allow access by unspecified clients by default. Access can be allowed or denied, either by IP address or by IP address range.

IP Address and Domain Restrictions on Windows Server 2012 R2
On Windows Server 2008 R2 systems, if IP address and domain restrictions deny a request, then the client receives a 403 Forbidden error. On Windows Server 2012 and later, the Edit Feature Settings hyperlink in the action pane allows the administrator to set the deny action type as well as the default access policy. Choices include Unauthorized (returns 401 Unauthorized), Forbidden (returns 403 Forbidden), Not Found (returns 404 Not Found), or Abort (which resets the connection).
Windows Server 2012 and later also allow for dynamic IP address restrictions. A client’s IP address can be blocked if they exceed a specified number of concurrent requests, or if they exceed a number of requests in a specified time period. These settings are available from the action pane through the hyperlink Edit Dynamic Resolution Settings.
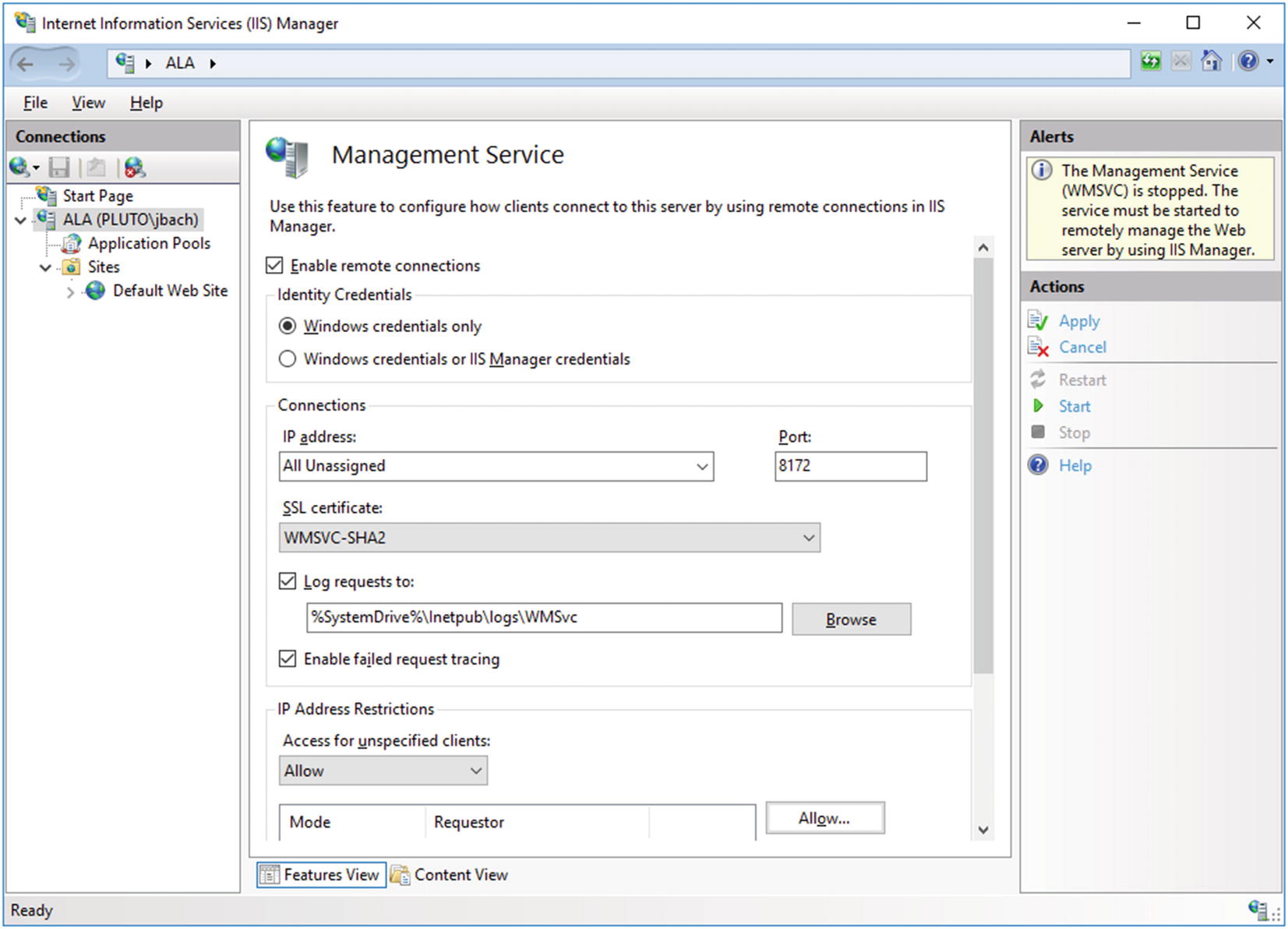
Request Filtering
An administrator can configure IIS to filter requests based on the URL, the HTTP verb (e.g., GET, POST, HEAD, PUT) or even portions of the file system using request filtering.
Request filtering, from IIS Manager on Windows Server 2008 R2
Authentication
Whenever a client makes a request of IIS, the server makes an authentication decision to determine if the client is granted access to the resource. These settings can be managed at the server, site, or directory level from IIS Manager using the Authentication settings. Navigate IIS Manager and select a server, site, or directory, then open the Authentication feature. Provided they were added as IIS server roles, anonymous authentication, basic authentication, and Windows authentication are available; Windows server 2012 or later also includes ASP.NET impersonation. At least one authentication mechanism must succeed for a client to be granted access to a requested resource.
Anonymous authentication is the simplest; it provides an identity for anonymous users. If a portion of a site is not meant to be accessed by anonymous users, then anonymous authentication must be disabled for that portion of the site.
Basic authentication is the same RFC 2617 method described in Chapter 14 for Apache systems. Credentials are passed by in essentially plain text by Base64 encoding <user name>:<password>. Basic authentication provides two options; the first is the authentication realm that plays the same role it did on Apache. The second is the default domain used for authentication. If no domain is specified, then windows domain users may need to include their domain name (domainusername) when authenticating.
Windows authentication uses Windows techniques (NTLM or Kerberos) for authentication; these use a challenge-response system that make them more resistant to sniffing and replay attacks.
SSL and TLS
To build a web site that uses SSL/TLS, the system administrator creates a new web site, but chooses https instead of http for the protocol type when selecting the binding. A drop-down box appears that enables the administrator to choose an existing SSL certificate.
Managing Web Server Certificates

Default IIS server certificates on Windows Server 2012 R2
Creating a Self-Signed Certificate
To create a self-signed certificate, select Create Self-Signed Certificate from the action pane (Figure 15-7). On Windows Server 2008 R2, all that needs to be specified is the name of the certificate. Windows Server 2012 and later allow the certificate to be stored either in the Personal store or a Web Hosting store. Although a server can listen on multiple IP addresses with different DNS names, the process of generating a self-signed certificate only generates a certificate for the system’s Windows hostname.
Windows System Certificates

MMC with the certificate snap-in for the local computer on the Windows Server 2008 R2 host elara.ad.jupiter.test, showing its original certificate (WMSvc-ELARA) and a newly created self-signed certificate with the friendly name Elara Self Signed
Trusting a Signing Server
To create an SSL/TLS web site that uses a certificate signed by a local signing server (Chapter 14), the Windows server must first trust the signing server. Copy the certificate (named ca.crt in Chapter 14) from the signing server to the web server. From the certificates’ MMC snap-in for the local computer account, right-click on Trusted Root Certification Authorities, then navigate All Tasks ➤ Import to start the Certificate Import Wizard. Select the certificate from the signing server and import the certificate into the Trusted Root Certification Authorities. On Windows Server 2012 and later, this can also be accomplished by right-clicking on the certificate and selecting Install Certificate; be sure to choose the local machine as the store location. Right-clicking on the certificate in Windows Server 2008 R2 also allows the certificate to be installed, but only for the current user rather than the local machine; this is insufficient for what follows.
Creating a Signed Certificate
To create a signed certificate for SSL/TLS on IIS, from the server certificates page for the server in IIS Manager, select the hyperlink Create Certificate Request from the action pane. The administrator provides the data for the request, beginning with the common name, which should match the DNS name of the server. The administrator chooses a cryptographic service; RSA with 2048 bits is a reasonable choice.
Once the certificate is signed, return it to the server. To complete the process, from the server certificates page for the server in IIS Manager, select the hyperlink Complete Certificate Request. Provide the certificate file (Thebe.crt in the example) and a name for the certificate. This certificate can be used in a new SSL protected web site, or by editing the bindings it can replace an already existing certificate, self-signed or otherwise.
Managing Remote Servers
The situation for a remotely managed Windows Server is more complex, because Server Certificates is not included in IIS Manager for remotely managed systems.
Creating a Self-Signed Certificate
Trusting a Signing Server
Certificates can be managed remotely through MMC provided SMB traffic is permitted. To do so, use the Microsoft management console (MMC). From the main menu navigate File ➤ Add/Remove Snap-in. From the list of snap-ins, select Certificates, then Add. Choose the computer account and select the name of the remote system. A trusted root certificate can then be imported on the remote system in the same fashion as a local system.
Creating a Certificate Signing Request
The file request.inf used to generate a certificate signing request (.csr) for the Windows 2016 host slepinir.pluto.test
The Subject line includes the FQDN of the remote server (slepinir.pluto.test), the organizational unit (Security Laboratory), the organization (Towson University), the location (Towson), the state (Maryland), and the country (US) that is included with the certificate. These should all be changed to match the characteristics of the server. The FriendlyName is the name that is used to identify the certificate in Windows and should also be changed.
Completing a Certificate Signing Request
Choosing SSL/TLS Protocols and Ciphers
It is possible to customize the protocols and cipher suites used by Windows Server. The configuration information is stored in the registry, in the key HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNEL. For example, to disable the use of SSL 2.0 by default on the server, set the value of HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsSSL 2.0ServerDisabledByDefault to the DWORD 1. However, many of the registry values that control these settings are not included by default and must be manually added; this is the case for the previous value.
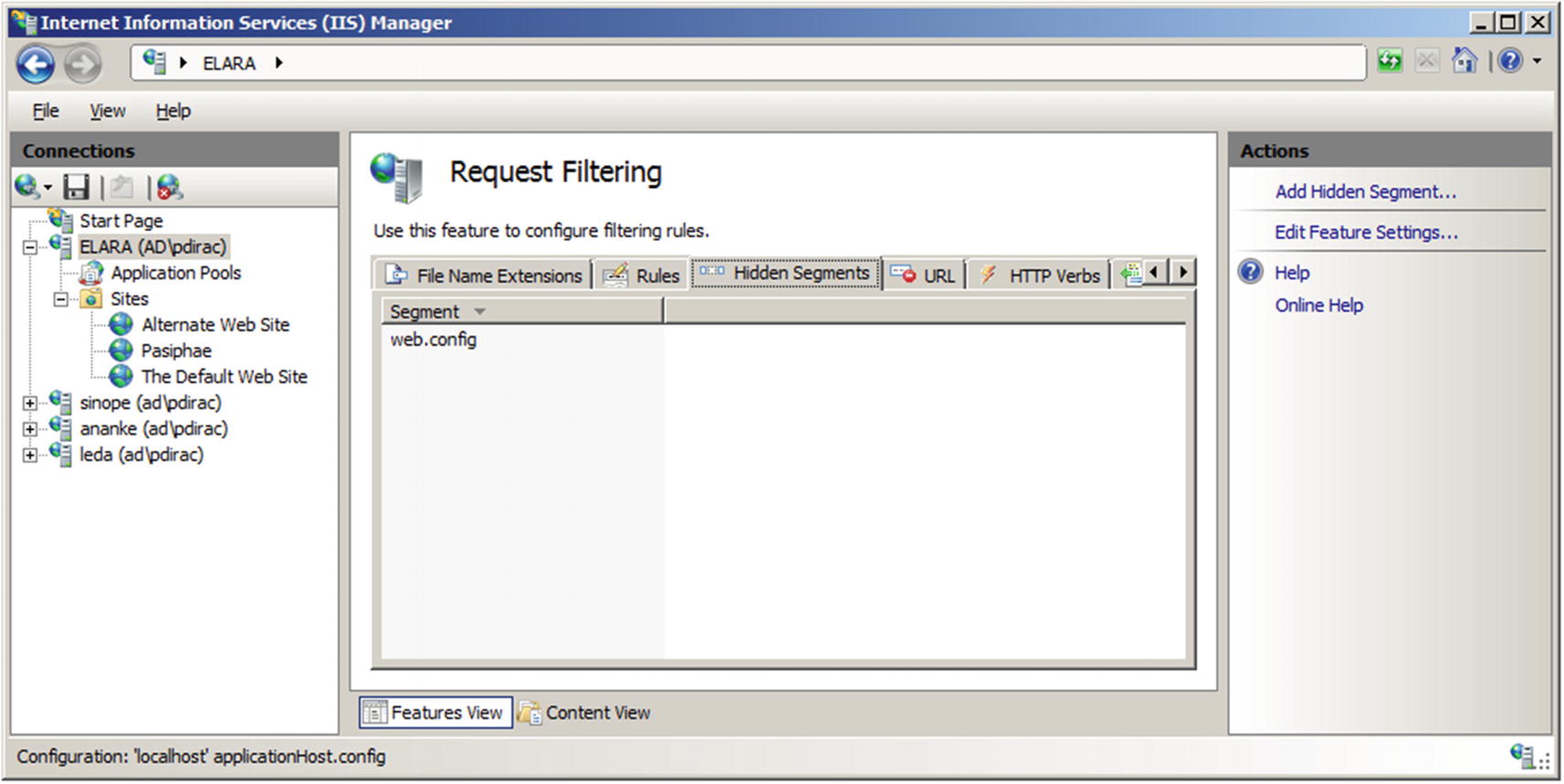
Redirection
Configuring redirection on Windows Server 2016
Logs and Logging
Logging can be configured at the server level or at the site level. To determine the level at which logs are kept, from IIS Manager navigate to the server and select Logging (Figure 15-11). The first option determines whether there is one log file per web site (the default) or one log file for the entire server.
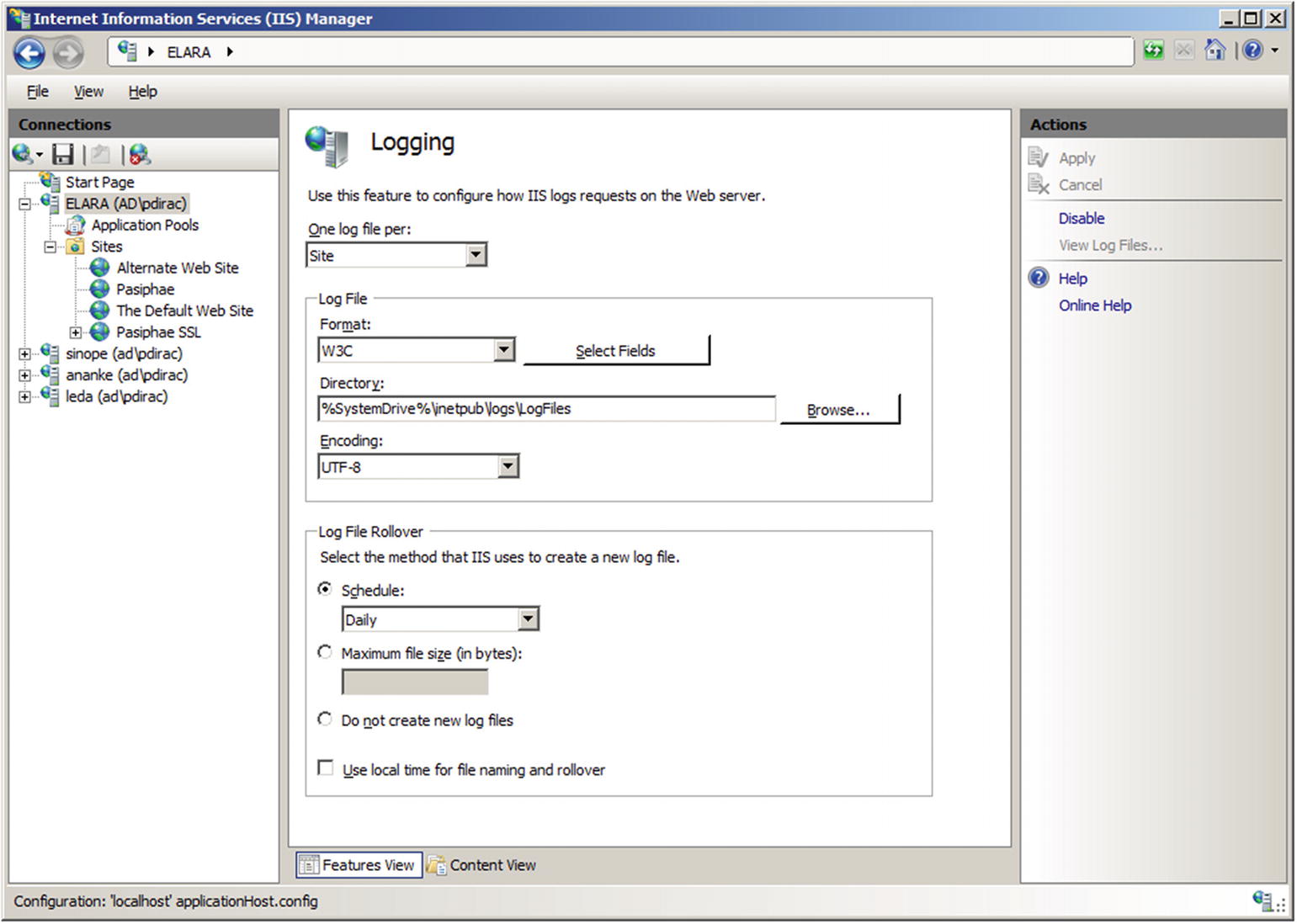
Configuring logging for IIS on Windows Server 2008 R2
Log files can be stored in a variety of formats including the default W3C format. The NCSA format is a fixed format that records remote hostname, username, date, time, request type, HTTP status code, and the number of bytes sent by the server. Items are separated by spaces; time is recorded as local time. The IIS format is an extension of NCSA that also records elapsed time, number of bytes sent, action and target file. The items are separated by commas.
Standard Fields for the W3C Logging Format. Fields Marked in Italic are Selected by Default.
Date | Server name | URI query | Bytes received | Cookie |
Time | Server IP | Protocol status | Time taken | Referer |
Client IP | Server port | Protocol substatus | Protocol version | |
User name | Method | Win32 status | Host | |
Service name | URI stem | Bytes sent | User agent |
Windows Server 2012 and later allow the administrator to add additional custom fields taken from the request header, the response header, or server variables.
The logs show three GET requests from 10.0.15.22 using Firefox 50.0; the first request was for the root directory, while the second was for Default.htm. Both requests were successfully served. The last request was for Default.htm but passed the GET parameter a=%00. This request received a 404 response.
One field that is included by default in the W3C format is the protocol substatus code. The protocol status code is the HTTP status code http://www.iana.org/assignments/http-status-codes/http-status-codes.xhtml . The protocol substatus is an IIS specific extension, and it is available from Microsoft at http://support.microsoft.com/kb/943891 . In the example, the request with the GET parameter a=%00 received a 404 response with substatus code 19 indicating that the request was denied by a filtering rule.
PowerShell script IISLogAnalysis.ps1 to search IIS W3C format logs for requests blocked by a filtering rule (404.19)
ModSecurity
ModSecurity is available for IIS installations. To install the current version (ModSecurity 2.9.2), the first step is to download and install the Visual C++ Redistributable for Visual Studio 2013;4 it is available from Microsoft either from http://www.visualstudio.com/downloads/download-visual-studio-vs or from http://www.microsoft.com/en-us/download/details.aspx?id=40784 .
This testing rule denies access to any page with a 503 error if any of the request’s arguments contains the string “zzz”. Note that files in the directory C:Program FilesModSecurity IIS are protected by user access controls (UAC).
Once installed, ModSecurity begins to function and protects all the IIS web sites on the server. Visit a site on the web server and pass the string “zzz” as an argument, for example, by making the GET request http://ala.pluto.test/Default.htm?a=zzz. The request should be denied, with the client receiving a 503 Access Denied error. The blocked request is noted in the Windows application log; see Figure 15-12.

Message from ModSecurity in the Windows application log indicating that a request was blocked. Taken from a Windows Server 2008 R2 system.
The installer for ModSecurity includes the OWASP Common Rule Set (CRS) in the directory C:Program FilesModSecurity IISowasp_crs, and the base rules are loaded by default. Other rules can be included by modifying the configuration file.
PowerShell script ModSecurity.ps1 to search the Windows security log for ModSecurity alerts
Compare this result to Figure 15-12.
Notes and References
This does work, though the solution might be considered by some to be inelegant. Once this is done, remote management of the IIS server is enabled in the same way as it was for Windows Server 2012 and later. First, the registry entry HKLMSOFTWAREMicrosoftWebManagementServer, needs to have the value EnableRemoteManagement set to the DWORD 1, and the Web Management Service (WMSVC) needs to be enabled and configured to start. There is no predefined firewall rule for IIS Remote Management on Windows Server 2008 R2; instead, an administrator can create a new rule to allow traffic on TCP/8172 to allow the connections to the remote management service.
Detailed information about the SSL/TLS settings is available from Microsoft, at http://technet.microsoft.com/en-us/library/dn786418.aspx .