An important characteristic of program maturity is continuous monitoring by management. This means leaders of the program establish performance indicators, aligned with management’s expectations, and these indicators are reviewed regularly. In the Program Review for Information Security Assurance (PRISMA), these actions are captured in the measured and managed categories. Metrics are developed, and management reviews performance of the program, to confirm that it meets the organization’s needs. The National Institute for Standards and Technology (NIST) special publication (SP) 800-137 1 was created to outline how federal agencies should develop continuous monitoring. These guidelines are useful for developing continuous monitoring inside any organization, and it is especially important for monitoring the performance of the incident response program. The key pieces of continuous monitoring include
Defining a continuous monitoring strategy
Establishing a continuous monitoring program
Implementing the program
Analyzing and reporting findings
Responding to findings
Reviewing and updating the strategy and program
So even here, where a process is established to continually monitor the security program and, more specifically, the incident response program, a step exists to review and update the program responsible for the review and update to key processes. This pushes the program toward a data-driven model. Evaluating performance against established benchmarks, adjusting where necessary, and monitoring progress period by period are keys to effectiveness.
In this scenario, in which the NIST Cybersecurity Framework was adopted as the foundation of the cybersecurity program, continuous monitoring focuses on the Detect, Respond, and Recover Functions.
To understand how to apply NIST (SP) 800-137 , this chapter steps through the fundamental concepts and processes of continuous monitoring. Then these concepts are applied to the cybersecurity environment discussed in Chapters 2 and 3.
Components of Continuous Monitoring
Define a monitoring strategy.
Establish the monitoring program.
Implement the monitoring program.
Analyze and report findings.
Review findings.
Review and update the continuous monitoring strategy.
NIST (SP) 800-137 aligns with the risk management program guidelines published in (SP) 800-37. The assumption is that a risk analysis and assessment were conducted, and the entity identified security measures to reduce risks to an acceptable level and is monitoring the operation of the security measures. This is the last step constituting risk management. Cyber risk managers select controls based on expected gains in risk reduction due to effective operation of security measures. The only way to know if these security measures are operating as expected is monitoring the control processes through various means discussed in this chapter. Detection, response, and recovery risks may be present, and controls are selected within these functions to reduce these risks. Examples of these include failure to detect malicious activity on end points, incident response plans not reviewed in a timely manner, and undocumented recovery processes, all of which can allow threat actors to successfully compromise the confidentiality, integrity, and availability of digital assets. When controls are put in place to address these issues, confirming that the controls are operating is necessary.
The Organizational Tiers
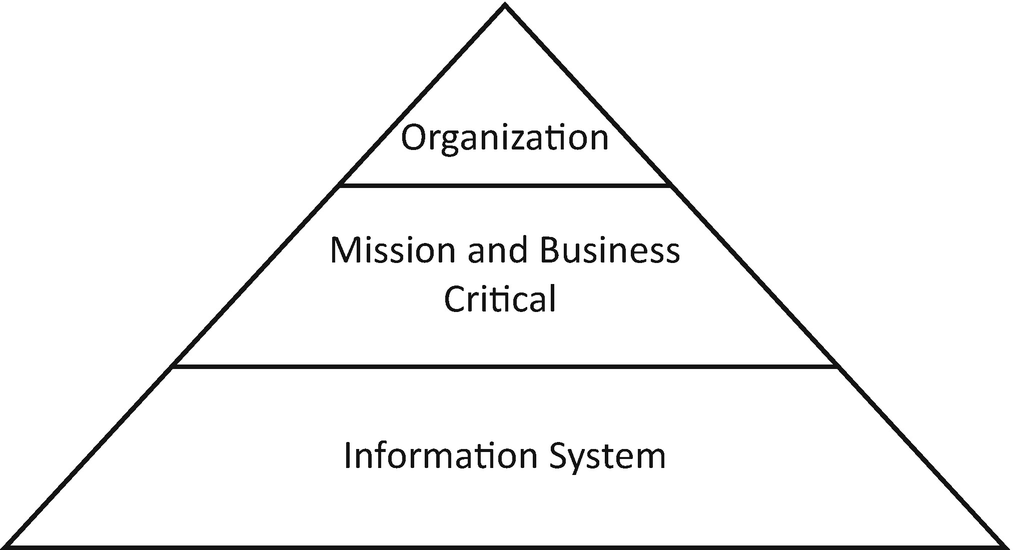
Key audiences identified in NIST (SP) 800-137
The members of these three focus areas view the data collected during continuous monitoring differently.
Tier 1—The Organization
Governance lives at the Organization tier. Policy- and strategy-related identification, mitigation, and monitoring of risks belong in Tier 1 and are communicated to Tiers 2 and 3. The metrics delivered to members of this tier are used to make decisions supporting risk management and governance of the entity.2
Tier 2—Mission and Business Critical
Members of management responsible for key business processes are accountable for mitigating risks affecting those processes.
Tier 3—Information System
Implemented correctly
Operate effectively
Produce the desired outcome
NIST highlights security alerts, incidents occurred, and threat activity as metrics collected by Tier 3.
How Continuous Monitoring Works
The purpose of continuous monitoring is to guide the entity to make decisions based on risk.3 For incident response, the goal is risk-based decision making based on the risks of not detecting events and insufficient responses to events. That means entities must test cybersecurity controls, understand the effectiveness of the controls and report on the effectiveness of the controls. This process works via the components identified previously that make up continuous response.
The Continuous Monitoring Strategy
Developing a continuous monitoring strategy is about nothing more than identifying the necessary data, frequency, and reporting methods for leaders at each tier, so that they can make decisions. Each tier may collect similar data and similar frequencies but it may also need additional information based on the requirements of the tier.
Tier 1 and Tier 2

Policy and procedural elements necessary to implement the continuous monitoring strategy
Tier 3
Here, at the system level, the security controls in place operate at all three levels. The data collected and used by the system is derived from system controls identified and placed into operation at Tiers 1 and 2. The Information System level implements the process and written procedures to meet the strategic objectives defined. These control processes, like all the other control process at each tier, are assessed for effectiveness, according to the risk management needs of the organization.
Incorporating Continuous Monitoring into the NIST CSF Environment
The guidelines outlined by NIST are valuable for entities wanting to monitor the environment and confirm that risk management objectives are being met. How does this look in the actual environment? Using the NIST CSF guidelines, monitoring for the purposes of incident response focuses on risks related to detecting, responding to, and recovering from incidents.
What Are the Incident Response Risks?
Chapter 6 discussed the role of preplanning in the incident response program. Plan development and response requires preplanning, focusing on risks to assets the entity deems important. One way to plan for an event is to analyze the risks to assets, which provide clues as to how an event may unfold in the environment.
Vulnerabilities in the Environment
Identified Vulnerabilities Related to the Incident Response Program
Immature end point detection capabilities |
No packet capture solutions in place |
No monitoring of egress points (places where data leaves the entity to outside locations) |
Limited collection of logs and no central location for storage |
Incident response plan not updated in a timely manner |
Incident response team lacks business and executive representation |
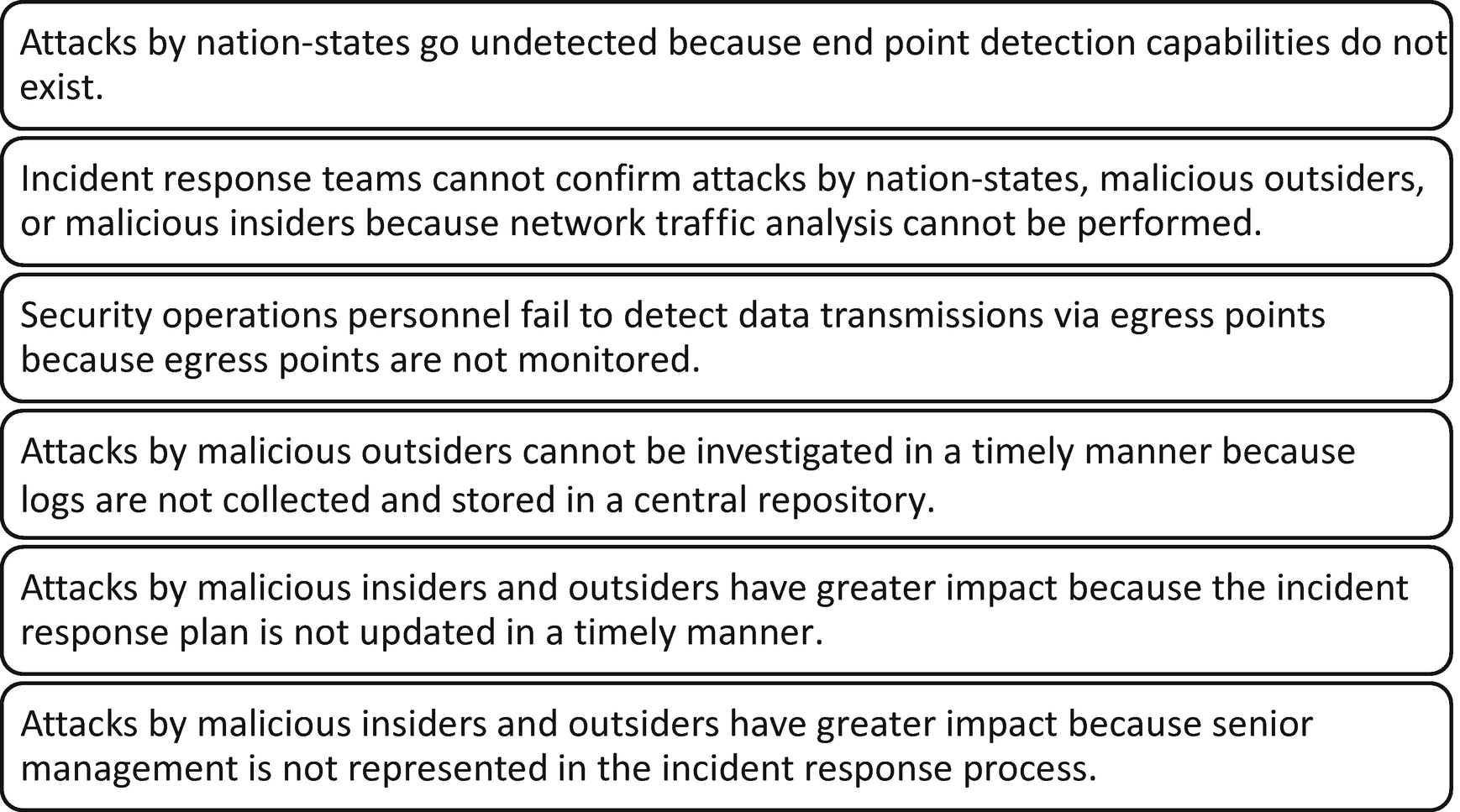
Identified risks affecting desired outcomes of the incident response program
Assigning Security Controls to Reduce the Risks

Control statements written to reduce risks to the incident response program
Defining the Monitoring Strategy
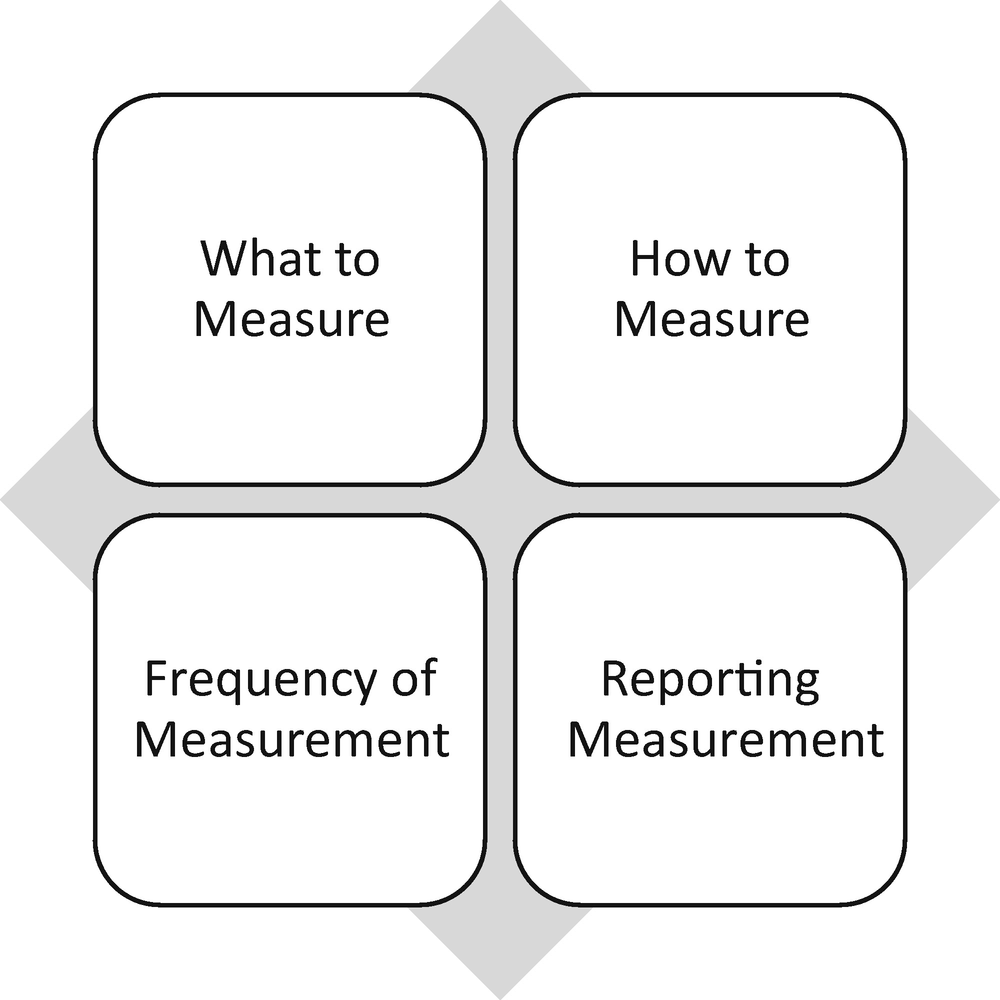
Key decisions of the incident response program monitoring strategy
Establishing and Implementing the Program
This phase requires the entity to assign individual responsibilities for each of the key strategic areas identified in Figure 10-3. The Organization tier establishes metrics with input from the other two tiers. Individual responsibility is assigned for assessment and reporting at the expected frequency.
Analyzing Data and Reporting Findings

Examples of metrics analyzed by the Organization, Mission and Business Critical, and Information System tiers
Responding to Findings
Security-related information collected during monitoring must be responded to. If the time to respond to end point protection events is not satisfactory, the entity adjusts the control process. Perhaps the control needs to be executed by other teams or individuals, or the process should be outsourced. It could be that the capability implemented needs adjustments, to operate effectively. The organization executes this process for each incident response control process.
Reviewing and Updating the Monitoring Program
Are the right metrics assessed?
Is the frequency sufficient?
Is the right information reported?
Where the answers to these questions are no, adjustments are made to the program.
Summary
The incident response program requires effective monitoring to ensure that the program meets the needs of the entity and continues to improve. Entities must identify risks associated with failures of the incident response program, to achieve desired outcomes. These outcomes normally are quick and efficient identification of undesirable events, containing these, eradicating them, and recovering when malicious behavior occurs. Risks of undesirable outcomes are reduced by using security controls and processes. These controls are monitored, based on identified metrics and are assessed at specific intervals. Organization, Business and Mission Critical, and Information System tier leaders assess these controls and report findings at each level. Analysis leads to adjusting the program, as necessary, if performance does not meet the entity’s requirements. This continuous cycle of assessment, reporting, analysis and adjustment allows the incident response program to grow and operate effectively.
