6
Define ISO 27001 Mandatory Requirements
After spending some time on data protection, we are back to our beloved ISO 27001. This time, we’ll go past the tip of the iceberg to see what’s hidden, and we’ll spend some time (the whole chapter) better understanding ISO 27001 requirements
The main topics here will be related to iSMS: the meaning of PDCA, project objectives and estimates, team building, project development and selections of controls to be used, and many more.
We will cover the following topics in this chapter:
- ISO 27001 operations
- ISO 27001 support requirements (or Clause 7)
ISO 27001 operations
The iSMS constitutes a benchmark in the implementation of a corporate security controls framework and can become one of the fundamental pillars in guaranteeing a structured, continuous, and risk-oriented approach across the entire entity
Correctly weighing the perimeter of applicability, the necessary resources and skills, and strong support from senior management are the key elements for the success of the iSMS.
The most obvious benefits of an iSMS model are the following:
- It allows you to have an overall vision of corporate security that goes beyond the perimeter of IT security, also including people and processes
- It is an adaptive model that adapts to the temporal evolution of threats and therefore to the rapid changes typical of today’s information systems
- It returns a correct view of the state of security and thus becomes the fundamental tool for optimizing the allocation of budget, directing it toward initiatives that give a greater return in terms of risk reduction
- Implementing this control model allows us, in many cases, to also respond to external regulatory constraints that normally require a series of measures that are nothing more than a subset of the possible controls of the framework
- In fact, the application of controls allows an effective tool for corporate security governance, and ISO/IEC 27001 is undoubtedly one of the most complete standards, consisting of an innumerable collection of indications and controls that must be carefully selected or declined by choosing the relevant and feasible measures for the organization
The ISO 27001 standard – what it is and what requirements it establishes
Annex A of ISO/IEC 27001 contains the objectives and controls, or the thematic areas considered and the controls to be applied (the 14 thematic areas are then broken down into lower-level controls, more details of which are provided in ISO/IEC27002). The areas, or domains, of the whole ISO/IEC 27001 are broken up into the following 14 controls:
- A.5: Information security policy
- A.6: Organization of information security
- A.7: Human resource security
- A.8: Asset management
- A.9: Access control
- A.10: Cryptography
- A.11: Physical and environmental security
- A.12: Operation security
- A.13: Communications security
- A.14: System acquisition, development, and maintenance
- A.15: Supplier relationships
- A.16: Information security incident management
- A.17: Information security aspects of business continuity management
- A.18: Compliance
Each of these sections then contains subareas that provide directives without, however, providing stringent specifications on the security measures that must be chosen and used in a specific case.
How to structure an iSMS
With regard to what has been said previously, the impact of iSMS crosses widespread across the entire organization, so top management support is a fundamental prerequisite to starting the project.
Having said that, it is possible to break down the project into different phases. Let’s analyze them in detail.
Structuring an iSMS – project objective and estimate
This is the first step of the project in which it is necessary to estimate the scope of the project and calculate the construction and maintenance costs.
The size and maturity of the company determine very different approaches: we could consider the basic perimeter at the beginning of the implementation, thus including only the network equipment related to the company (of course including devices in use by remote workers, if any ), systems at greatest risk, and consider gradually enlarging in subsequent project waves, including social accounts, cloud computing and remote repositories
Other variables to consider are support from other structures and offices of the company, aside from the security offices, touching many areas of the company, including the human resources office, legal, and purchases.
Having the right commitment from all the actors involved and from management will be essential to the success of the project.
ISO 27001 relies on continuous improvement and, even if not directly explained in the standard. It will therefore be possible to choose Plan-Do-Check-Act (PDCA, known also as Deming Cycle) as the best iterative methodology.

Figure 6.1 – Plan-Do-Check-Act
PDCA consists of a continuous implementation aimed at constant improvement for effective and adaptive management that follows the evolution of the information system. The four phases of PDCA are described as follows:
- Plan: Establish the iSMS plan by defining its perimeter and objectives, carry out the risk assessment, and establish the plan and procedures for risk management.
- Do: Implement the iSMS plan. The procedure becomes operational.
- Check: This is the monitoring and correction phase of the iSMS plan, which is carried out through internal audits, and the results are reported to top management.
- Act: Maintain and improve the plan through corrective actions.
PCDA is adopting the aforementioned cycle because it reflects the evolutionary nature of threats. As threats and risks change they require continuous re-evaluation and adaptation, in order to reach the ultimate company goal: Ensure the adequate containment of the overall risk, below an established threshold. We cannot set an arbitrary risk threshold, as company risk appetites may differ.
Structuring an iSMS – team building
This is the project phase in which the team responsible for managing the project estimates the necessary effort.
An iSMS requires strong knowledge and experience of the ISO 27001 and its implementation should be followed by professionals who have a background of working on projects of this type and at the same time will need senior managers with sufficient authority to orchestrate all the resources and structures involved.
Structuring an iSMS – project development and selection of controls
First of all, it is necessary to identify controls, processes, and procedures that already regulate the scope within which ISO 27001 is to be implemented and all the assets and actors involved: customers, data, partners, offices, and so on.
Once these entities have been identified, it will be necessary to select the controls to be implemented and all the necessary metrics that will serve monitoring purposes.
As ISO 27001 is devoted to any kind of company, the selection of controls and how to interpret and implement them cannot be specific because they depend on the sector in which the company operates, its size, the technologies it uses, and the resources that the company has to implement and manage these controls.
In fact, it is necessary to pay close attention to how many controls to use to ensure you do not jeopardize the psychological acceptability of users and not overload the operational processes. Remember that implementing controls can affecting a company at all levels, at every department. Therefore, it is imperative to work on a few controls at a time.
Structuring an iSMS – project development and documentation system
Once the scope and controls have been established, the management of the iSMS will have to be included in the business processes, and then the PDCA quality management process should be tailored accordingly, formalizing it by following a fairly lean document system that includes at least one policy, a standard, and an operational guide.
Structuring an iSMS – project development and risk analysis
At the heart of the iSMS is the risk analysis and assessment process, which allows you to assess the riskiness of threats and therefore establish possible countermeasures.
In this case, the suggestion is to adopt an approach already used in the company, if present, or to create a new one that is simple enough so as not to make the project excessively complicated.
Being able to identify relevant threats and weigh them accurately is a very difficult aspect and typically requires coordinated work between security specialists.
Without going into excessive detail, the risk analysis phases must be as follows:
- Risk identification: This is the phase in which the possible risks must emerge, which, if they materialize, would lead to a compromise in terms of the integrity, confidentiality, or availability of data.
- Risk measurement: Once the possible risks have been identified, they must be weighed according to the impact they would have on the organization. They can be both quantifiable, such as monetary impacts (usually in the case of material losses), and immaterial, as in the case of damage to reputation.
- Risk weighting: In this step, the results of the previous phase are compared with the risk criteria to establish the priorities and methods of risk treatment.
Ultimately, therefore, it is decided how to intervene when risk is encountered and how to proceed. The options are as follows:
- Accept the risk if it is not believed to substantially affect the overall risk
- Transfer the risk, where possible, if, for example, it is easier than having to compensate for it with mitigation actions
- Cancel the risk, for example, by decommissioning a service if the cost of correcting the risk is excessive compared to the actual benefit that this service entails
- Mitigate the risk or implement one or more controls in order to bring the risk back to a value that is considered acceptable
Structuring an iSMS – assessment
Periodically, it is important to schedule iSMS review and monitoring phases to evaluate its effectiveness and adherence to controls with respect to the context of current threats that could be significantly modified over time.
From this point of view, the quality of the audit and the metrics chosen become the key points for evaluating the project. In particular, the more the metrics are an objective and significant measure of the control in question, the more truthful and simple the analysis will be to carry out.
One of the most important clauses of ISO 27001 is Clause 7 because it sets the standards for implementation (related to training, the implementation team (if internal), and so on). Let’s see the requirements in detail.
ISO 27001 support requirements (or Clause 7)
In this part, we will focus in depth on Clause 7, which is fundamental because it deals with training and resources. It applies to people, infrastructure, and the environment just as much as it does to physical resources, materials, and equipment. This clause focuses on acquiring the necessary resources, personnel, and infrastructure to build, deploy, maintain, and continuously enhance the iSMS. It addresses the need for competence, awareness, and communication to support the iSMS, and might involve, for instance, providing training and access to staff. This article also stipulates that all individuals working for a company must be aware of its information security policy, how they contribute to its success, and the consequences of failing to comply. Additionally, the company must ensure that internal and external communications pertinent to information security and the iSMS are conveyed effectively. This entails determining what must be conveyed to whom, when, and how.
Tip
Please consider that, once implemented, ISO 27001 has to be maintained too. Therefore, your organization requires someone that is able to improve the value of the certification. Remember the PDCA or Deming cycle? Let’s imagine this with the example of a bicycle: once you jump on and start to cycle, it (you complete the first PDCA cycle) is quite difficult to keep the bicycle steady and at a good speed. After a few meters, you will be pedaling at a faster pace and the handlebars will be more stable, and, in a perfect world, you will be steady forever. Of course, in real life, it works differently: there are traffic lights, pedestrians, cars, and so on that inhibit our progress, but our ride continues.
Organizations must assess the degree of recorded information required for iSMS control. Controlling access to recorded information is also emphasized, reflecting the significance of information security. In your company, there is also a renewed emphasis on knowledge as a vital resource. When designing your quality targets, the present capacity and capability of your resources, as well as those you may need to acquire from external suppliers/partners, will be a crucial concern. This section of the standard specifies the prerequisites for establishing and operating an iSMS. Included in Section 7 are the following:
- 7.1 – Resources required to establish and operate an iSMS
- 7.2 – Competency
- 7.3 – Awareness
- 7.4 – Communication
- 7.5 – Documented information
7.1 – Resources required to establish and operate an iSMS
The company must select and provide the necessary resources for establishing, implementing, maintaining, and continuously improving the information security management system.
Clause 7.1 includes information about the selection and allocation of resources to establish and manage an iSMS, as well as the requirements for ongoing awareness for all personnel executing work within the scope of the iSMS and under the authority of the organization. A sufficient amount of resources must be allocated to the creation, implementation, maintenance, and ongoing enhancement of the iSMS. It is sufficient that roles, duties, and authority be clearly defined and owned – assuming that the appropriate amount of resources will be deployed – but it does not demand that the iSMS be staffed with full-time personnel. Clause 7.1, which serves as an overview of the resources promise, is followed by more detailed criteria in the following clauses
- 7.2 – Competence of the support resources for ISO 27001
- 7.3 – Awareness of the people doing the work for the iSMS to meet ISO 27001
- 7.4 – Communication (this clause is about communicating the iSMS to the interested parties internally and externally)
- 7.5 – Documented information about the iSMS to demonstrate it conforms to the ISO 27001 standard
Having access to the necessary resources at the appropriate time is a crucial factor in the success of an iSMS deployment. Remember that each iSMS position holder needs to be competent in their function. Therefore, it is essential to recall the essential duties and resources you will need. This relates to the iSMS’s installation and operations. Core roles will presumably include the following:
- The iSMS owner, typically a senior manager.
- Members of the governance forum, regardless of its titles.
- The individual responsible for managing information security inside the organization.
- Those accountable for diverse operational operations that influence information security. This covers operational support professionals, including server and network support teams, service desk workers, and human resources management people.
- The iSMS internal auditor.
- The person entrusted with ensuring that the iSMS complies with the standard.
- The person responsible for reporting iSMS performance to upper management.
During implementation planning, there are many questions that must be presented and answered, such as the following:
- What skills do we require?
- Do we have access to these capabilities? If not, can we recruit somebody who does? Can we hire them on a contract basis?
- What internal training and development is needed to retain the requisite competencies over the long term?
These issues are mostly concerned with verifying the availability of the requisite capabilities. Included are inquiries about recording the desired capabilities, determining the present competency set, and establishing potential methods to resolve any competency gaps. Typically, gaps are remedied as follows:
- By hiring – acquiring permanent resources with the appropriate skill set
- By acquiring temporary contract resources
- By developing in-house capabilities via training and mentorship
The decisions about these alternatives will rely on the magnitude of the skill gap and whether the competencies are necessary for the iSMS’s adoption or continuous operation.
7.2 – Competency
The organization must identify the requisite competence of all individuals doing work under its control that impacts the performance of information security. It must also guarantee that these individuals are qualified based on their degree, training, or experience. Whenever relevant, it must carry out activities to acquire the required competence, assess the success of those efforts, and keep the requisite documentation as proof of competence. Examples of applicable activities include training, mentorship, or reassignment of present personnel, as well as the recruiting or contracting of competent individuals.
Clause 7.2 of ISO 27001 essentially states that the entity will guarantee it meets the following requirements:
- Assessed the ability of the iSMS personnel whose job might impact its performance
- Has people regarded as qualified based on their applicable education, training, or experience
- Whenever necessary, takes action to obtain the essential competency and assess the efficacy of their activities, and preserved proof for auditing
Clause 7.2 stipulates that all iSMS personnel must be competent in their respective tasks. The supply of training, education, experience, and skills leads to competence. All of these must be addressed while managing human resources. To effectively deploy and sustain an iSMS, supporting resources must be in place.
The organization must do the following:
- Decide who has to have the requisite skills to undertake tasks under its supervision that have an impact on information security performance
- Confirm that these individuals possess the necessary education, skill, or experience to be considered competent
- If necessary, take steps to develop the essential skills and assess their efficacy
- Save pertinent documentation as proof of competency
Tip
Be careful as requirements related to sensitive and private information could interfere with data protection.
Clause 7.2 outlines the requirements for individuals to be aware of their iSMS duties. The expertise and abilities of your workers, vendors, and contractors is crucial to the successful application of information security rules. To guarantee an adequate knowledge and skill basis, you must do the following:
- Specify the needed knowledge and abilities
- Identify who must possess the necessary knowledge and abilities
- Specify how you will evaluate or confirm that the appropriate individuals have the necessary knowledge and abilities
Beyond knowledge of physical security, cybersecurity, computer security, and other kinds of information security, a multitude of talents and experiences is necessary for the effective deployment and continuous administration of an iSMS that is certified to ISO 27001. These include commercial, legal, HR, IT, and goods and services expertise relevant to the scope of business. Developing and maintaining an iSMS is often a team effort. Your auditor will expect you to have documentation outlining your required knowledge and abilities. Where you feel the standards have been met, you must provide documentation such as training certificates, course attendance records, or internal competency evaluations. The majority of firms that currently utilize tools such as training/skills matrices, evaluations, or supplier assessments may meet the need for competence records by increasing the categories covered to include information security.
Tip
Of course, this has to be read differently in case you are using a third-party company to implement ISO 27001, but still, your entity should be able to maintain this certification.
Training
The iSMS mandates that all individuals be competent with regard to their iSMS-related roles. Any identified competence deficiencies must be remedied. However, there is limited iSMS-specific training for certain user groups. The following table lists some of these categories and the sort of training that may be necessary:
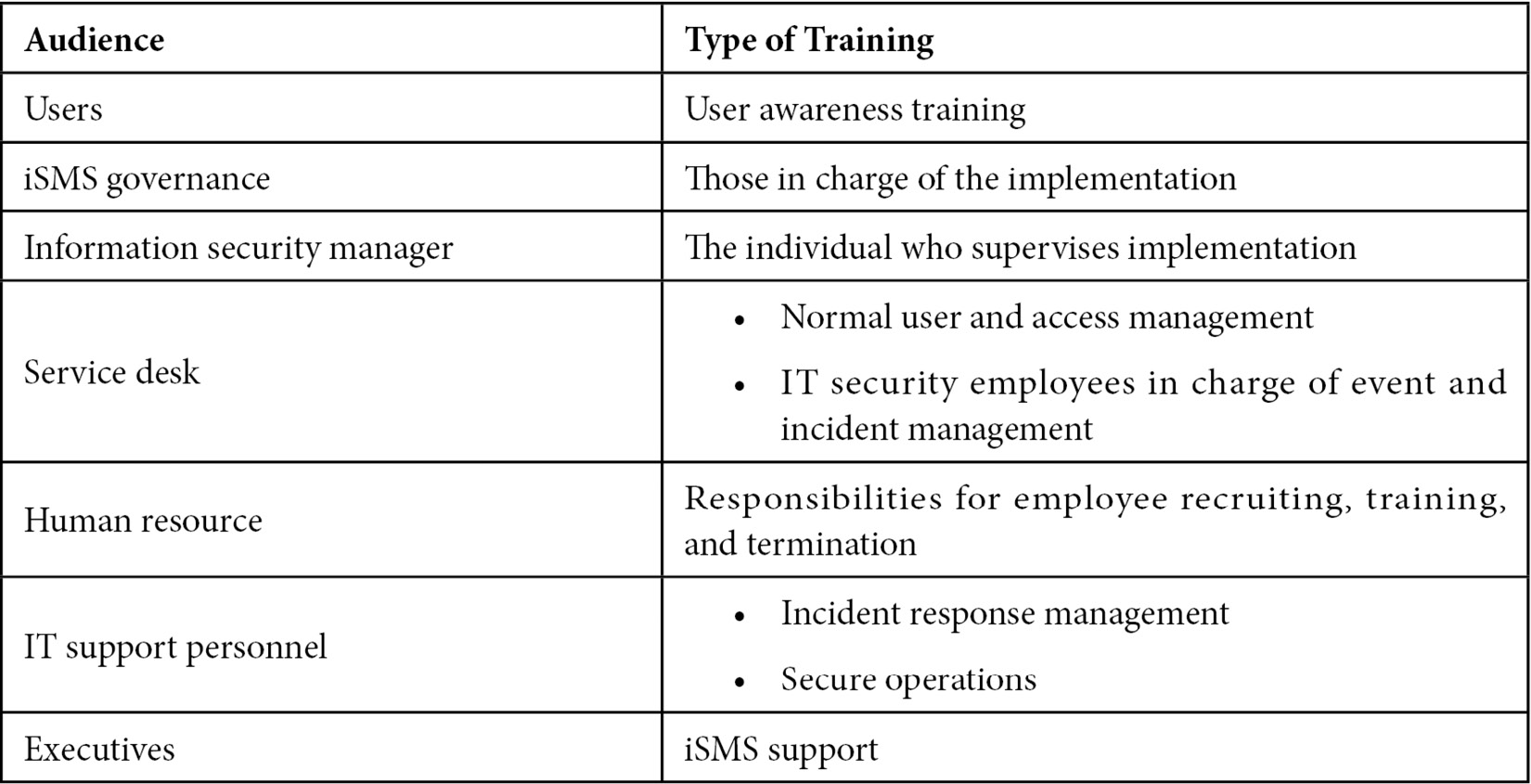
The following should be considered in the training plan:
- User awareness training
- Documentation for governance
- Specialized instructions for important control owner groups:
- Network and server support
- Service desk (user support, incident response)
- Human resources
- Briefings for senior executives and line officers
When establishing a training plan, the following factors must be considered:
- Who is the intended audience?
- What messages are required?
- How will the training/message be delivered – in-person, online, via PowerPoint, or through team briefings?
- When will the training occur and how often it must occur?
- Who will be accountable for planning the training, maintaining the content, and distributing the materials?
- Are evaluations and effectiveness metrics necessary? How about quizzes or surveys?
This sort of data may be collected through a gap analysis. Once this sort of data has been collected, a training program may be designed.
The training program should include the following:
- Who the target demographic is
- Which messages they need
- How the information or instruction will be conveyed
- When the training will take place
- How often training must occur
- Who will be in charge of organizing/delivering the project
- Whether any evaluation methods are necessary and if so, what they would entail
7.3 – Awareness
People performing work under the control of the organization must be aware of its information security policy, their contribution to the effectiveness of the information security management system, including the benefits of improved information security performance, and the consequences of failing to comply with the information security management system requirements.
Clause 7.3 is a combination of Competency (Clause 7.2) and Communication (Clause 7.4).
The following information must be known by anybody working for the organization:
- The information security policy
- Their role in enhancing the efficiency of the information security management system, including better information security performance’s advantages
- The effects of failing to adhere to the information security management system requirements
Typically, this will lead to the setup of training and awareness programs aimed at various groups. Awareness of non-compliance with iSMS rules must also be addressed. In addition to assuring the specialized information security competency of key persons, the broader group of workers, suppliers, and contractors must be aware of the fundamental parts of your iSMS. As part of the iSMS implementation, the organization’s employees must collaborate on the design of an information security policy for approval by senior management. Their job should be well understood since it would have been agreed upon and recorded as part of Clause 7.1. This is essential for developing a supportive culture inside the business. All employees, vendors, and independent contractors should be aware of the following:
- That you have an iSMS and the reasons why
- That you have an information security policy and which portions are applicable to them
- What they must do to assist the company in achieving its information security goals and how they may help your firm safeguard its precious information
- Which policies, procedures, and controls are applicable to them and the repercussions of noncompliance
- Awareness and comprehension of the following clauses 6.1 – Risk management, 6.2 – iSMS goals, 9.1 – Wider measurement and evaluation, 9.2 – Internal audits, 9.3 – Management reviews, 10.1 – Non-conformities and remedial measures, as well as continuous improvements in accordance with 10.2. (Continual Improvement)
- This information may often be communicated using current procedures and documentation, such as orientations, employment contracts, toolbox discussions, supplier agreements, staff briefings, and updates
7.4 – Communication
The company must identify the necessity for internal and external information security management system-related communications. While determining the communication system, it must establish what is to be communicated, when it is to be communicated, with whom it is to be communicated, who will communicate, and how communication will be carried out.
Communications are crucial to the iSMS implementation process. By making the program and its benefits evident inside and beyond the company, they assist, gain, and sustain support for the program. Benefits of excellent communications programs include ensuring that information security is not regarded as a side problem and is rather front and center. Good communication tactics extend beyond the deployment phase and into the ongoing operations of the iSMS. Important security dashboards, briefings, and warnings are all components of a robust communications system.
Internal and external communication considered important to the iSMS must be decided, as well as the methods by which they must be carried out, taking into account what must be communicated, by whom, at what time, and to whom. To allow the operations of your iSMS to operate well, you must ensure that your communication activities are well planned and controlled. ISO 27001 specifies them in detail by mandating that you determine the following:
- What must be communicated
- When must it be communicated
- To whom must it be communicated
- Who is accountable for communication
- What the communication processes are
If your communication needs are clearly stated in your organization’s policies, rules, and procedures, you do not need to take any further steps to meet this criterion. If they are not, you should consider documenting your important communication actions in the form of a table or method using the preceding headings. Remember that these papers’ contents must also be transmitted. Similar to the realm of training, good communication involves the identification of target audiences, the methods that may be employed (existing or new), the content, and the frequency of messages. The preceding bullet points uncover these components and enable the construction of an all-encompassing communications strategy. The incorporation of resources from corporate communications departments adds substantial value to this arena. Communication techniques have a crucial role:
- Sustain a commitment to installation and operations in order to garner support for the iSMS
- Continue keeping information security at the forefront
- The creation of a communications strategy facilitates the dissemination of messages
Plans for communications must include the following:
- Which current communication channels may be utilized
- What participation may be expected from corporate communications and other agency groups
- The present levels of assistance within the agency’s core areas and how they could be modified
Clause 7.4 mandates a definitive response to a number of security-related questions:
- Organizations should clearly express their priorities: the need for information security and the need to comply with laws and standards. Communication will handle risk management concerns, new or altered security goals, and vulnerabilities, events, or incidents in order to activate the appropriate response from all parties, most notably the trained individuals who execute the predetermined response. Celebrating accomplishments and commending exemplary security habits have very beneficial impacts. Including security provisions and requirements in the contract is also a method of communicating your needs to service and product suppliers.
- What should the message be like? To generate what is supposed to be communicated, the message should be clear and concise in both form and substance. This section considers the kind of communication channel to relay messages. You may use narration, visuals, metaphors, or cartoons. Messages must be concise and focused on their true objective. You can use any media or way to communicate, but it has to be comprehensive.
- Who is allowed to communicate? Organizations should make clear who is permitted to communicate, particularly with external parties. Top management, the CISO, and the support desk are excellent internal examples. Public relations officers are employed by large corporations to connect with external parties. The communicator should have the requisite authority to ensure that the message will be received with the proper attention and will elicit the desired action or response.
- Who is the recipient? Not all recipients should get every communication. Depending on the categorization of the information, the required technical competence, and the recipient’s position within the company, messages should be tailored to a particular audience. The communication plan should be effective and exclusively target those who will benefit from it or must act based on it, such as users, partners, internal and external service providers, regulatory authorities, and shareholders.
- How should the communication process should be carried out? The first and easiest communication method is the security policy and all the papers that specify what to do (and how to do it) to achieve the policy’s goals. Particularly in the event of accidents and emergencies, messages to any kind of audience (either internal or external) should be planned and authorized. Defined channels (and protocols) should be used to ensure that the message reaches the target audience at the optimal time and with the greatest potential efficacy. Examples include emails, pop-up windows, screensavers, posters, audio messages, meetings, regulations, and directives.
- When are we supposed to communicate? Continuous and event-based communication is required (in reaction to events). To ensure that the message, any message is not forgotten, you need to ensure that it is regularly and repeatedly delivered, for instance, to new starters in the organization as well as at regular intervals to existing staff. You should also be able to alter messages and add new messages, formats, and channels as the scenario demands. Compared to events or crises, communication in regular circumstances might be drastically different.
Plan for internal versus external communication
It is crucial to acknowledge that the communication plan comprises both internal and external components. They will require different considerations to the questions that follow.
The internal communication plan is used by upper management to communicate its aims and commitment to information security. The information security policy, the team within the organization with the essential roles and duties related to security, the awareness strategy, and the general and specialized requirements for responding to incidents are some examples of communication. The internal communication plan should not, however, be unidirectional. Mediums such as telephone and email, for instance, should also be recognized and used to communicate security breaches or emerging vulnerabilities in a bottom-up manner, that is, from on-the-ground users.
The majority of the preceding examples pertain to the internal communication plan, although they also apply to the external communication plan. You may need to communicate with regulatory authorities, public authorities, shareholders, customers, and partners to announce good (success) or bad (failure) occurrences (incidents, accidents, and crises). You will also need a communication plan that answers the answers listed previously in this section. You must be careful with this since you should not reveal or broadcast sensitive information that could worsen your condition.
Depending on the organization’s size and security goals, the formality of the communication plan will vary, being either completely documented as a distinct document or simply expressed in a few phrases within other rules, processes, and plans. So, as long as the required information is communicated to the correct people your solution will be appropriate for your goals and available resources.
7.5 – Documented information
Clause 7.5 discusses the obligations for preserving the relevant papers and records that support the iSMS’s activities. Formal documentation of when things have been approved demonstrates compliance with this provision. For the documented information used to develop and manage your iSMS to be useful, it must meet the following requirements:
- Be accurate
- Be intelligible to those who use it and assist you in complying with regulatory obligations, managing information security risks, and achieving your goals
Access to documented information is controlled so that it cannot be accidentally changed, corrupted, deleted, or accessed by individuals to whom it is not appropriate. Information is deleted in a safe way or returned to its owner when this is a requirement, and you can track changes to information to ensure that the process is in control.
Documentation is necessary to guarantee that procedures are executed in accordance with the management system’s goals. Documentation defines what you will accomplish and gives proof that you have carried out your intentions. The ISO 27001 standard does not define the scope of documentation, which is influenced by a variety of variables. These consist of the following:
- The complexity and interplay of business processes
- The control environment, sometimes influenced by external duties
- The organization’s size and core activities
- The qualifications of personnel
- Other legal or regulatory requirements
Always develop documents with the intended audience in mind. The documentation must be beneficial to the people who will use it. Organizations are required to define and record their procedures as needed. Afterward, they must adhere to their own documents. Say what you do and do what you say.
The following criteria apply to procedures that are not explicitly documented:
- The process is methodical
- Communicated
- Understood
- Applied
- Effective
Documentation, however, does need management. This management comprises document approvals, standards for accessibility and readability, and other specifications mentioned in Clause 7.5 of the standard.
Internal or external sources may be the origin of your documented information; thus, your control procedures must handle documented information from both sources. Companies with effective document control often have one or more of the following in place:
- A single individual or a small group responsible for ensuring that new/modified papers are examined prior to issuance, are kept in the correct place, and are removed from circulation when superseded, and that a record of charges is maintained
- Automated processes and controls included in an electronic document management system
- Effortless electronic data backup and paper file archiving/storage procedures
- Strong staff understanding of document management, record-keeping, and information access/retention regulations
As we have provided a summary of the clause, now we will detail every subclause.
7.5.1 – General
The term documented information, which will be used several times throughout this chapter, now encompasses both the documents and records definitions from the previous version of the ISO 27001 standard.
This modification was intended to assist with the administration of papers and records mandated by the standard, as well as those deemed vital to the iSMS’s functioning by the organization. It should also be emphasized that the quantity and scope of recorded information required by an organization will vary based on its size, activities, goods, and services, the complexity of its processes and their interrelationships, and the expertise of its employees.
7.5.2 – Developing and revising
The standard stipulates that information generated or updated within the scope of the iSMS must be appropriately recognized and characterized, taking into consideration how the content is presented and the medium through which this is done. All recorded information must be subjected to appropriate review and approval processes to verify its suitability.
7.5.3 – Management of recorded data
The standard says that recorded information required by the iSMS, as well as the standard itself, must be accessible, usable, and sufficiently safeguarded against destruction or loss of integrity and identity, regardless of its internal or external origin. For the correct management of recorded information, the organization must provide distribution, retention, access, use, retrieval, preservation, and storage methods, as well as control and disposal procedures.
Documented information required by the information security management system and by ISO 27001 documentation must be appropriately checked to ensure (note: the originating clauses are in brackets):
- iSMS scope (documents) (4.3)
- High-level information security policy (documents) (5.2)
- Risk assessment methodology (documents) (6.1.2)
- Risk assessment report and risk treatments (record) (6.1.2, 6.13, 8.2, 8.3)
- Statement of applicability (documents) (6.1.3 d)
- Information security objectives (documents)( 6.2)
- Evidence of competencies (record) (7.2)
- Documented information as required by the iSMS (documents and record) (7.5.1 b)
- Documents and records required by ISO 27001 (documents and record)( 7.5.1 a)
- Monitoring and measurement results (record)( 9.1)
- Internal audit program aid results (record) (9.2)
- Results of management review (record) (9.3)
- Non-conformances and results and corrective action (record) (10.1)
Tip
The terms in bold are the respective clauses of Annex A of ISO 27001. Concerning non-conformance, ISO defines them as “the failure to meet one or more requirements that are outlined throughout the mandatory clauses.”
The distinction between a document and a record is that records are time-stamped proof of activity. Periodically, documents are examined and updated. Typically, they are versioned. In addition to the records mentioned previously, other relevant documents may include the following:
- Evidence of the risk owner’s consent for specified controls or risk acceptance
- Visitor records, including CCTV photos and access logs
- Security incident logs and root cause analysis
- Rectifications and enhancements
Tip
I think you imagine a truckload of documentation to be prepared and ready, but a high percentage of the companies I personally assessed needed “only” the paperwork required to fulfill the criteria of clauses 4 to 10 consisting of around 25 to 35 pages in total (excluding title pages and version control, I mean the version number). Among them are the outcomes of the management review, the internal audit report, the risk assessment, and the performance evaluations. This amount of pages for clauses 4 through 10 is generally intended to be independent of the organization’s size; nonetheless, bigger organizations have additional paperwork related to, for example, performance management and internal auditing.
The second major sort of documentation is information security policies, which are more diverse. 20 to 40 pages of documentation have been required for the ISO 27001 implementations I’ve performed for smaller organizations (with maybe a few thousand users). Larger organizations need more policy-related paperwork, although it typically did not exceed 60 pages.
The third form of documentation is the documentation/records generated as a consequence of running the controls/procedures, such as visitor records, change control records, and penetration test reports, where the type of documentation generated is highly reliant on what is implemented.
If you have more than this, you may have made things more complicated than necessary. Or maybe you do need it all to effectively handle information security concerns. But I doubt it.
So, once everything is in place (policies, controls, procedures, and so on), you can have your audit and, if it’s successful, you can obtain your ISO 27001 certification. But can you later lose it?
Yes. Auditors will periodically return on-site (or remotely) and request evidence that you are continuing to comply with all regulations. If you cannot provide evidence that you are, they will revoke your ISO 27001 certification. So, we must ensure that we continue to comply with all ISO 27001 requirements.
- Be familiar with the primary tenets of your information security policy.
- Be familiar with the primary concepts of the content of the intranet’s primary information security pages and complete the yearly training on information security.
- Know where to locate the organization’s rules and procedures, especially those that pertain to information security and apply to you.
- You are not required to grasp every detail, but you should understand the fundamentals.
- Read, understand, and agree to the terms of the acceptable use policy annually.
- Understand your role in helping to secure the organization’s information and the significance of that information. For instance, avoid revealing your password and handle sensitive information with extreme caution.
Be aware that if the organization has a policy or procedure that specifies how things should be done, it is crucial that the policy or process is accurate. For instance, if a policy or procedure states All visitors must be accompanied by a relevant member of staff, it is imperative that all visitors without exception. If a policy or procedure is not consistently adhered to in practice, either the policy or procedure must be revised, or individuals must ensure that they adhere to it.
It is vital to record instances of disparity between an organization’s policies/processes and what is really in place in order to determine whether the policy/process should be amended. Remember that a policy or practice does not need to be recorded in order to be legitimate and adhered to.
Be cautious when adopting improvements, shortcuts, or changes that do not align with the organization’s rules or processes. You should get formal approval for this action and, if required, modify the policies/processes properly.
You should also report anything that seems to have the potential to expose sensitive information to unauthorized parties, for instance, if you notice that a door lock is broken or that critical papers have been left on a desk overnight.
Remember the fundamentals of security , such as the following:
- Use extreme caution when links from people external to your organization emails
- Clear your desk papers with confidential information while you are not present
- Lock your workstation’s display before leaving your desk
- Deposit all rubbish containing confidential information in the designated containers
In previous paragraphs, I translated the main requirements of Clause 7 to demonstrate how to use them more easily. Of course, as we have said many times, ISO 27001 is continuously evolving and improving. You can improve on the basic requirements proposed within the clause. For instance, you can require internal training every 3 months for all your employees and install document shredding machines to destroy documents. It’s entirely up to you; there is always room for improvement. Just remember: don’t excessively implement bureaucratic or unsustainable procedures; they can be a waste of time for your employees and your company.
Summary
Well, that’s another chapter filled with a lot of information that we’ve completed. You’ve learned what the requirements, steps, and documentation to provide to fulfill ISO 27001 accomplishment are. At the same time, you should be aware that you can lose the status of ISO 27001 certified company just by non-completing the relevant information.
In the next chapter, we’ll deep dive into risk management, policies, and controls.
