The previous chapters revealed the size, use cases, and potential of IoT in various industries, having billions of devices connected. In the discussion of challenges in every chapter, I touched on the provisions of securing the system. This chapter is dedicated to types of risk that can do minor to major damage, agnostic to the type of industry. For an IoT environment, security is an ongoing process in which a proactive attitude and forward-looking actions are nonnegotiable, and there is no true definition of done.
Later in this chapter, we discuss the security provisions in an industrial control system (ICS) at three levels: network and communication, computer systems, and sensors. Architects or managers are responsible for understanding the end-to-end IoT technology stack and securing them from any type of possible exploitation. In an IoT project, security must consider a wider range of issues as compared with traditional IT cybersecurity, because it involves all three of these layers.
IoT technology is no longer in its infancy stage; now that is just an excuse. All of the challenges with this technology are solvable. Here I present how to use the Threat Modeling tool and empower you with all types of STRIDE threats, including step(s) to mitigate them. You can use this tool for any project.
I will finish this chapter and conclude the book with details on the available IoT standards and regulations.
From this book, if there is one key concept to grasp in implementing any IoT project in your organization, it is the importance of security.
This book has attempted to provide practical advice for designing and deploying many types of secured IoT systems.
Risk
When a burglar invading your home, you don’t find who the burglar was; first you find the place he or she entered the house. Similarly, you don’t wait for it to happen; you secure your house to minimize the risk in the first place. This is the same way we need to secure our IT infrastructure in the first place. In this example, the burglar is not the threat; instead, the actions he or she can perform is the threat. In the context of IoT, the threats are that someone can get to the sensors, hold the data hostage, and reduce reliability of service.

Risk flowchart
Accepting the risk sounds bad because you log it and take no action. The transfer method is unacceptable, as you transfer the impact and management of the risk to someone else, and I am not covering any risk that can be exploitable here. This leaves you with only two choices: Avoid risk by changing your plans completely or mitigate risk by limiting the impact of a risk, so that if it does occur, the problem it creates is smaller and easier to fix.
We need to systematically evaluate the security and potential attacks. As part of the security development life cycle, Microsoft developed a Threat Modeling tool that can be downloaded from https://aka.ms/threatmodelingtool. It allows software architects to identify and mitigate potential security issues early when they are relatively easy and cost-effective to resolve. Threat modeling helps identify the vulnerable entry points in all the assets within a system.
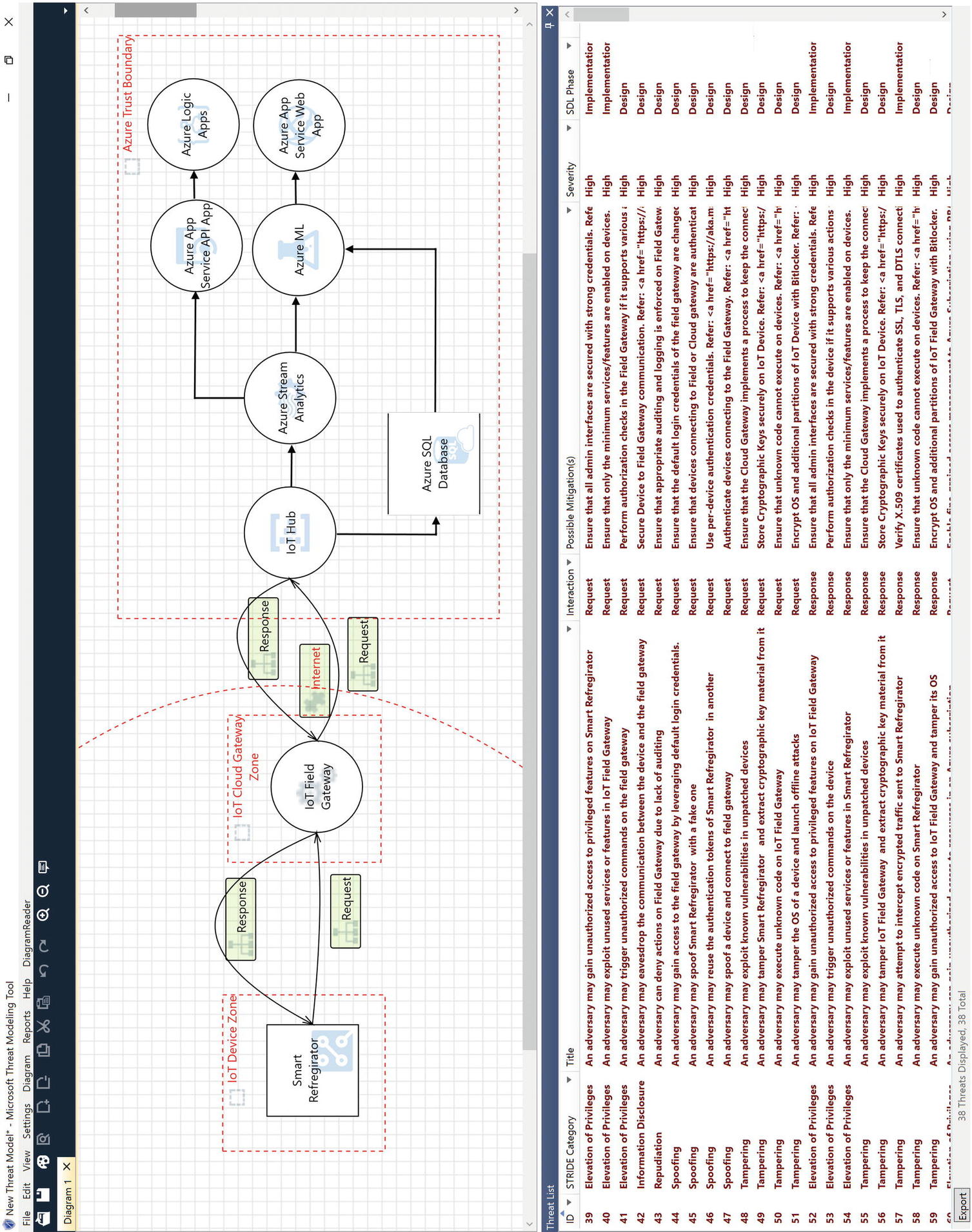
Threat model of Azure IoT architecture
Threat modeling provides us with a methodical approach to performing a security evaluation of a system or system design. To illustrate the threat modeling process, we will evaluate threats to a smart refrigerator, which orders milk from your favorite grocery store based on a real-time analysis of the refrigerator’s contents and your purchasing and consumption history.
Use Case of Smart Refrigerator
Use Case | Placing Order |
|---|---|
Preconditions | Customer has grocery store and payment information registered with refrigerator. |
Action | Smart refrigerator communicates with and collects data from sensors, and places order if low quantity is found. |
Postconditions | Credit card is charged, and order is placed. |
Example of STRIDE Threats
Category | Title | Interaction | Security Development Life Cycle Phase |
|---|---|---|---|
Spoofing | An adversary might spoof the sSmart refrigerator with a fake one. | Request | Design |
Spoofing | An adversary might spoof a device and connect to a field gateway. | Request | Design |
Tampering | An adversary might exploit known vulnerabilities in unpatched devices. | Request | Design |
Repudiation | An adversary can deny actions on the field gateway due to lack of auditing. | Response | Design |
Information disclosure | An adversary might eavesdrop on the communication between the device and the field gateway. | Request | Design |
Elevation of privileges | An adversary might trigger unauthorized commands on the device. | Response | Design |
Elevation of privileges | An adversary might gain unauthorized access to privileged features on the smart refrigerator | Request | Implementation |
To mitigate a spoofing attack, we need ensure that devices connecting to the field or cloud gateway are authenticated and authenticate devices connecting to the field gateway.
To mitigate a tampering attack, ensure that the cloud gateway implements a process to keep the connected devices’ firmware up to date.
To mitigate a repudiation attack, ensure that the appropriate auditing and logging is enforced on the field gateway.
To mitigate information disclosure, an adversary might eavesdrop and interfere with the communication between the device and the field gateway and possibly tamper with the data that are transmitted.
To mitigate an elevation of privileges attack, perform authorization checks on the device if it supports various actions that require different permission levels and ensure that all admin interfaces are secured with strong credentials.
You now have the choice to avoid risk by changing your plans or mitigate risk as recommended by the Threat Modeling tool.
Privacy
The confidentiality of data has always been and remains a primary concern. For any organization, small or large, there are legal, regulatory, and commercial obligations to protect intellectual property and customer data, especially intellectual property, financial, and health care data. This emphasis is applicable to data collected manually or by IT systems. Among all the issues, intellectual property confidentiality and human privacy are critical.
Privacy is the most important subject we discuss today. Organizations are even more responsible to protect the privacy of users. Unfortunately, the definition of privacy is vague, changes from person to person, and has different ranking levels. is the definition is so vague that something we share on social media, we assume cannot be shared by an organization. In fact, many countries have privacy legislation, and therefore it is a fundamental human right. I am not debating the true definition of privacy here, but would like to mention the GDPR legislation passed in 2016.
Individual certification as a Certified Information Privacy Professional (CIPP) from the International Association of Privacy Professionals (IAPP) focuses on data privacy.
Safety
Safety and security are closely related linguistically, so here I use them interchangeably. The safety focus is frequently driven by the security impacts that an organization has historically experienced, known as reactive actions. Most of the time, managers understand security only after critical data are exposed to the public, corrupted, or deleted. At that point they start making security a priority and start approving budgets for security-related projects. By that time, though, damage has already been done.
Networks, computer systems, and sensors are typical IoT or industrial system assets, and security begins with these assets. In most cases there exists a tight coupling between network design and operational processes; therefore, to avoid any business process impacts, securing the network and all communication channels is even more important.
Securing a network sounds simple when talking about a small, confined environment like a few buildings situated within a known boundary (e.g., a manufacturing unit). Disconnecting an internal network from a public network is as simple as said it seems. In geographically distributed environments, it is not possible to disconnect from the public network entirely. For those networks, we need sophisticated network devices and explicit partnering with Internet service providers. Modern networking equipment offers a rich set of access control and secured communications capabilities.
Botnets: Talking about Botnets brings Mirai to mind. It continues to be a problem today with millions of IoT devices affected. Mirai has the capability to use smart, connected devices to transfer private and sensitive data, which could be sold on the dark web, or to disable a device. Botnets are networks of systems, such as those used for denial-of-service (DoS) attacks explained later in this list.
Man-in-the-middle: Man-in-the-middle attacks are the most common in IoT systems. In this type of attack, a hacker breaches communication between a sensor and a system and tricks the recipient into thinking they are receiving a legitimate message. An example might be sending the wrong D2S message to IoT Hub about a critical physical condition like heat or vibration, or sending the wrong S2D message to a sensor to switch off. These can be dangerous attacks because a hacker can trick the recipient into thinking they are still getting a legitimate message. As in the previous example, these attacks can be extremely dangerous in the IoT, affecting things like garage door openers and industrial machinery.
Firmware hijacking : Firmware is the piece of code that runs on startup and later subverts the operating system. BIOS is not the only firmware in our system; it is the very core of every hardware device. For example, your noise-canceling headphones, printer, and security camera all have their own firmware. Therefore, firmware is the most vulnerable attach point to access your system before it has even booted up. Once in, a hacker could change the firmware for good, target sections of the OS, or stop antimalware software to execute and steal CPU processing power (e.g., cryptomining). Because firmware is installed on a special chip attached to the system on a chip (SOC), replacing a hard drive or reinstalling the OS won't help. Many manufacturers release updates regularly based on newly discovered vulnerabilities, but in some cases if a company goes out of business or discontinues supporting a product, you are widely exposed. With proper IT processes in place to look for updates and update your firmware to the latest versions quickly and often, you can close off lax security avenues and keep the system running smoothly.
Ransomware: Ransomware is a type of malicious software that cybercriminals use to block users from accessing their own files, usually by encrypting them with a key. Then they share instructions with the user on how to pay a ransom to get the decryption key. This type of attack is a hostage-like situation and comes with a price, depending on how badly the user needs those files back. For example, hackers might be able to access a power grid and blackmail the utility company by causing a complete blackout if they refuse to pay the ransom using cryptocurrency.
Denial of service : A DoS attack happens when a service becomes unavailable, usually due to capacity overload . A large number of requests are made to a service (target) at the same time. In comparison to other hacking attacks like phishing or brute-force attacks, DoS is not interested in stealing any information; it just tries to bring a system down, causing damage to a company’s reputation and seriously affecting the business.
Whether you’re just getting started with an IoT project or you’ve already implemented it, it’s important to regularly perform a cybersecurity audit to determine whether you need to take additional steps to protect your devices.
IoT Standards and Regulations
The National Institute of Standards and Technology (NIST) defines national standards on security, encryption, and networking. The organization also provides guides for the security of connected devices. They also maintain national and internationally recognized standards regarding security. Supporting materials can be found at http://csrc.nist.gov.
The U.S. Department of Homeland Security mandates guidance for Congress, other agencies, and the private sector regarding cybersecurity standards under the National Security Telecommunications Advisory Committee. Supporting materials can be found at https://www.dhs.gov/topic/cybersecurity.
A part of the U.S. Department of Commerce called the National Telecommunications and Information Administration controls U.S. radio spectrum allocation, domain naming, and security. More information can be found at https://www.ntia.doc.gov.
In Europe, the European Union Agency for Cybersecurity issues standards and publications on various information security practices. In Australia, the IoT Alliance Australia maintains a set of guidelines and practices.
IEEE IoT is a multidisciplinary organization comprised of academic institutions, government bodies, and industry and engineering professionals to drive IoT development. More information is available at iot.ieee.org.
The Computer Emergency Response Team identifies and responds to national high-impact computer security emergencies (https://www.us-cert.gov/ncas/current-activity).
The Children’s Online Privacy Protection Act (COPPA) requires that operators provide notice to parents and obtain verifiable parental consent prior to collecting, using, or disclosing personal information from children under 13 years of age.
HIPAA covers regulations and guidance on anything related to health care. It is applicable to wearables to. The HIPAA Security Rule identifies 18 criteria that define Protected Health Information (PHI).
GDPR, mentioned earlier, outlines a set of data subject rights. These include breach notifications, right to access, right to be forgotten, data portability, and privacy by design.
Bonus Read: Azure Sphere
I know you need help protecting your data, privacy, physical safety, and infrastructure, and you are looking for an end-to-end solution. Azure IoT Edge allows you to offload most of the cloud processing near the device. Therefore, we need even more security on an Edge device and Azure Sphere aims to provide security solutions for such IoT devices. This bonus read is about Azure Sphere, a comprehensive IoT security solution including hardware, OS, and cloud components developed by Microsoft.
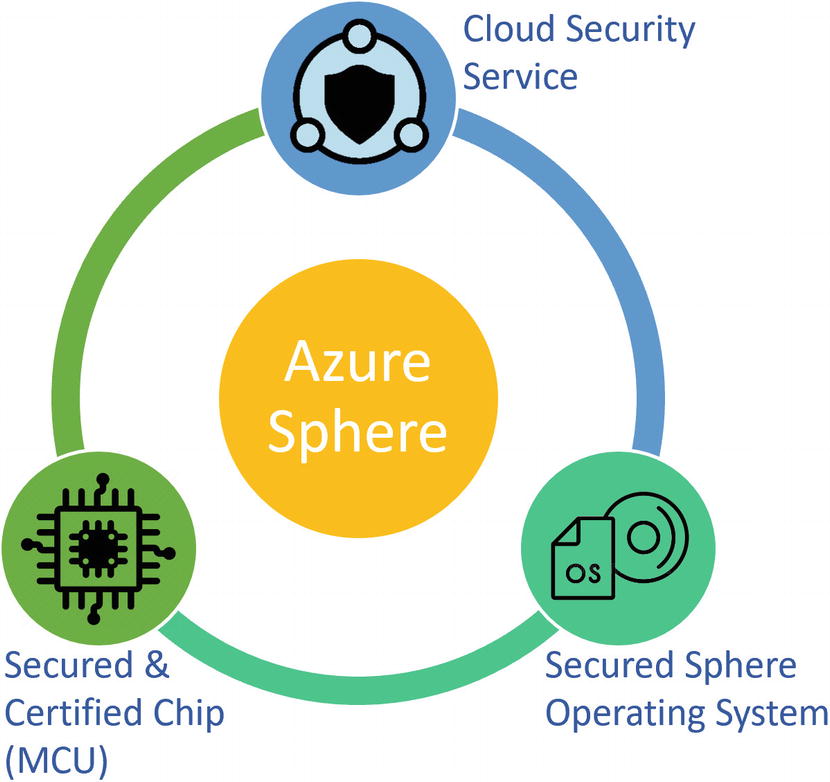
Azure Sphere
The Azure Secured Sphere OS is based on Microsoft’s custom Linux-based microcontroller OS that is built for security and agility to create a trustworthy platform for new IoT experiences. It runs a custom Linux kernel developed by Microsoft fit in just 4 MB of RAM and based on mainline Linux 4.9. Every device has a certificate on it and is known by Microsoft before that Azure Sphere is sold. Therefore, Microsoft maintains the OS and updates it using over-the-air (OTA) updates. It connects to the other components and the Azure Sphere Security Service (AS3).
AS3, the Cloud Security service layer on Azure Sphere communication between Azure and the device, uses HTTPS and the same trusted certificates for authentication. It is integrated with Azure IoT Hub for device provisioning and machine-to-machine (M2M) communication. Although Azure is the preferred cloud for Sphere, it can be connected to any cloud-based device management layer.
Secured and Certified Azure Sphere’s chip (MCU) is built by Microsoft’s silicon partners, so they possess the hardware root of trust needed. Currently the certified chip is MT3620AN, where Microsoft will support OS and security service updates through July 2031. The custom Linux-based OS mentioned earlier runs on this certified chip.
I believe security should start with hardware and extends to your solution end to end to deliver a holistic, secure system that protects you from almost all threats. Most of the time we put effort into building a perfect architecture and developing a solution, but we ignore the hardware piece. With many IoT devices suffering from security vulnerabilities and trojans, this MCU is a solution. These three components create and provide a complete, secure software environment for IoT application development.
So far in this book we have used Raspberry Pi. Is Raspberry Pi different from Azure Sphere? Yes, these are two different platforms. However, they both offer a few similar features for building IoT solutions. For example, they both have processing units, RAM, connectivity like Wi-Fi, GPIO ports to extend the capability, and so on. The biggest difference is the security features of the Azure Sphere platform that do not exist for Raspberry Pi. There are many cases where either a Raspberry Pi or Azure Sphere device could be used to build an IoT solution. If security is important to your IoT project, however, Azure Sphere might be the best platform.
Even if the price is your primary decision factor, Azure Sphere is not too costly. At the time of writing, there were two approved Azure Sphere development kits recommended by Microsoft (see https://azure.microsoft.com/en-us/services/azure-sphere/get-started/) and available for less than $100, and a mini board is available for less than $35, which is sufficient for any regular project. There are no ongoing subscription fees or consumption fees associated with your Azure Sphere purchase or the Azure Sphere Security Service from Microsoft. Pricing and support for Azure Sphere certified MCU MT3620AN is less than $8.65. This is already included in the purchase price of the development kit.
Getting Your Device Ready
Avnet Azure Sphere starter kit
You can use Visual Studio or the Visual Studio Core CLI command to develop Sphere security-enabled applications on a certified board. Developing solutions for Azure Sphere requires Visual Studio Enterprise, Professional, or Community 2019 version 16.4 or higher.
Download the Azure Sphere SDK from https://aka.ms/AzureSphereSDKDownload. You will see the Azure Sphere Developer command prompt shortcut on your Start menu.
Download the Azure Sphere SDK extension for Visual Studio from https://marketplace.visualstudio.com/items?itemName=AzureSphereTeam.AzureSphereSDKforVisualStudio2019.
Claiming a Device
An Azure Sphere can be claimed only once; that is, once activated, the device cannot be sold or transferred to another person or organization. If you are purchasing a preowned device, make sure it is not yet claimed. The process of claiming is not straightforward and not well documented online.
- 1.
Search for and select Azure Active Directory.
- 2.
In the left pane, under Manage, select Users.
- 3.
Click +New User
- 4.
Select the Create User option. Notice in Figure 14-5 that the domain is already present with the name <your account>hotmail.onmicrosoft.com.
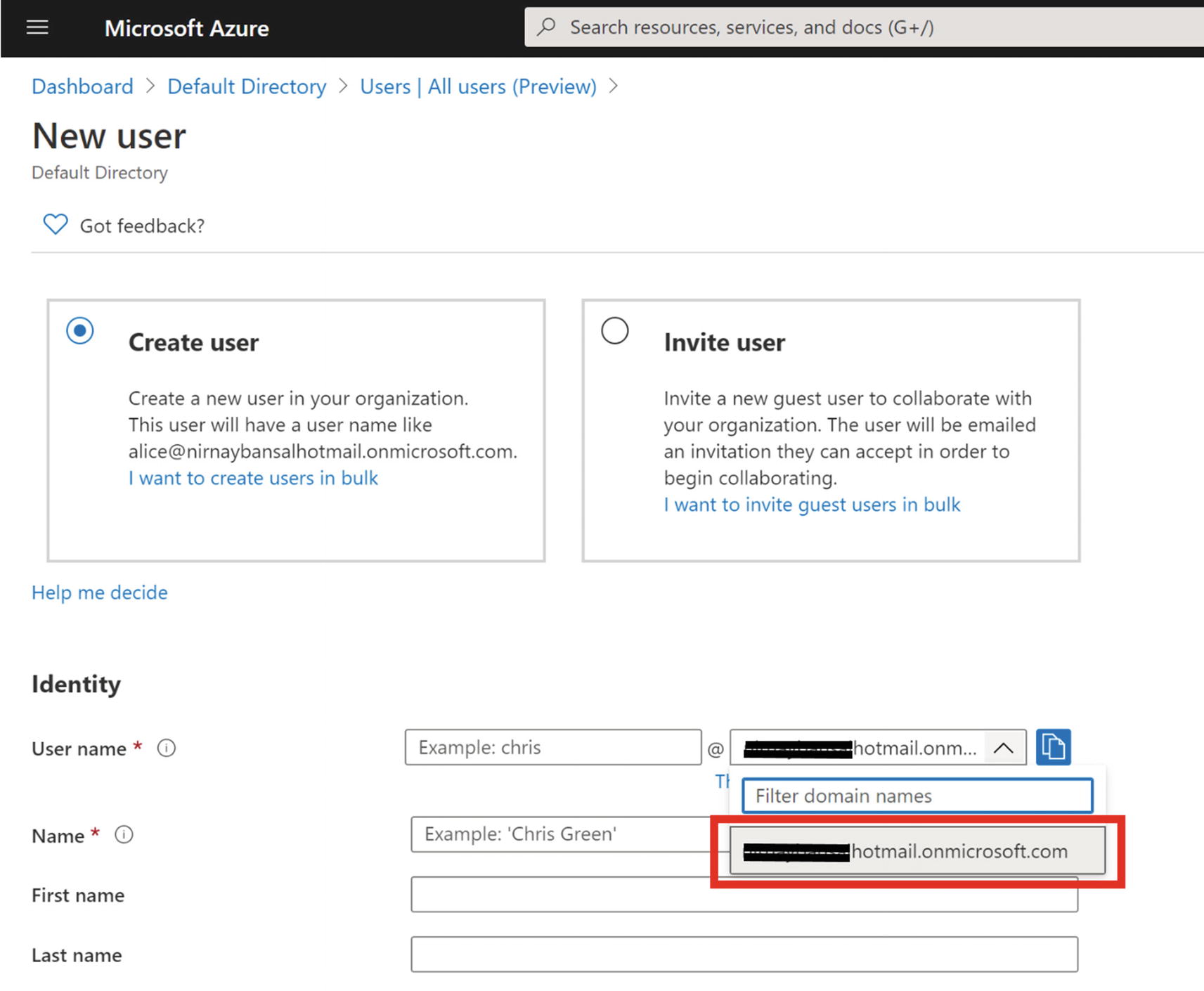
Creating a new user in Azure Active Directory
- 5.
On the User page, enter the user information as shown in Figure 14-6.
Adding user information
- 6.
Click Create to add the new user to your Azure Active Directory organization, as shown in Figure 14-7.

Azure Active Directory users list
- 7.
Open the Azure Sphere Developer command prompt.
- 8.Execute the following command to log in to Azure Sphere using a new user account.D:>azsphere login --newuser sphere@<your account>hotmail.onmicrosoft.comRegistration successful. Press any key to log in with your new account.>Login successful as 'sphere@<your account>hotmail.onmicrosoft.com'.warn: You don't have access to any Azure Sphere tenants.warn: Type 'azsphere tenant create --name <name>' or, if you have used Azure Sphere before, type 'azsphere tenant migrate'.
- 9.
Use your browser to complete the sign-in process and change the user password when prompted, as shown in Figure 14-8.
Azure Sphere login prompt and first-time password change screen
- 10.Next, create a new tenant:D:>azsphere tenant create --name iotazurespheretenantwarn: You have logged in with the following account:warn: [email protected] (21b1xxxx-xxxx-xxxx-xxxx-5225xxxx4c1e)warn: Do you want to use this account to create a new Azure Sphere tenant using the attached device?warn: You cannot change the tenant name 'iotazurespheretenant' once it has been created.Enter 'yes' to continue. Enter anything else to exit.> yesCreated a new Azure Sphere tenant:--> Tenant Name: iotazurespheretenant--> Tenant ID: '65axxxxx-xxxx-xxxx-xxxx-f49xxxxfb851Selected Azure Sphere tenant 'iotazurespheretenant' as the default.You may now wish to claim the attached device into this tenant using 'azsphere device claim'.When you create a new tenant, your user identity is automatically made an administrator of the tenant. Make sure your tenant is created.D:>azsphere tenant listID Name Roles-- ---- -----'65axxxxx-xxxx-xxxx-xxxx-f49xxxxfb851 iotazurespheretenant Administrator
- 11.Claim your deviceD:>azsphere device claimClaiming device.Successfully claimed device ID '5E1Exxxxxxxxxxxxxxxxx8B' into tenant 'iotazurespheretenant' with ID '65axxxxx-xxxx-xxxx-xxxx-f49xxxxfb851'.
Add network succeeded: | |
SSID | <yourSSID> |
Configuration state | enabled |
Connection state | unknown |
Security state | psk |
Targeted scan | False |
SSID | <yourSSID> |
Configuration state | enabled |
Connection state | connected |
Security state | psk |
Frequency | 5765 |
Mode | Station |
Key management | WPA2-PSK |
WPA State | COMPLETED |
IP Address | 192.168.0.31 |
MAC Address | xx:xx:xx:xx:xx:xx |
- 1.
Each time the device boots.
- 2.
When it connects to the Internet for the first time.
- 3.
Once every 24-hour interval thereafter.
If you see any error in executing this command, that means the OS is still updating and requires a manual reset.
Congratulations! Your Azure Sphere device is now enabled and ready for debugging and closed to cloud application updates until you explicitly change that setting using the azsphere device enable-cloud-test command.
Azure Sphere MT3620 Blank solution
C-based solutions are usually lengthy and require significant knowledge of the language. Building applications using C is outside the scope of this book. There are quite a few samples provided by Avnet (https://github.com/Avnet) and third-party developers to clone, and they can be executed on your device as is.
Summary
This chapter detailed the risks of IoT security. IoT projects are more vulnerable because of their surface area, from hardware to software and everything in between. Therefore, an architect must be cognizant of security at each level.
Protecting privacy is challenging for the IoT, and you need to budget time and money for this important task. In this chapter, we’ve covered identifying risk, threats, and how to mitigate them. You can use the Threat Modeling tool to flag all the threats and learn how to mitigate them. I provided a list of government and private organizations that provide standardization and technical roadmaps of this technology.
As a bonus, I added a brief introduction to Azure Sphere, the security offering from Microsoft.
This book has attempted to provide practical advice for designing and deploying many types of complex IoT systems. I have thoroughly enjoyed presenting unique use cases and solving them practically with different technology in each chapter. I hope you enjoyed learning them, too.
