Threat intelligence, for the importance it plays in cybersecurity operations and in cybersecurity, is complex and difficult to understand. It is also not easy to execute effectively. Effective use of threat intelligence requires an understanding of what intelligence is and is not, defined objectives for its use, a framework to cut through some of the complexity, and a way to gather metrics and assess how the process is implemented.
What Is Intelligence?
Are the malicious domains ones resembling the entity’s domain or domains end users may visit?
Is there traffic involving malicious IPs?
Is the threat intelligence under analysis attributable to adversaries targeting healthcare organizations?
The last bullet point is important. Intelligence must be relevant. It does no good to look for traffic going to and from domains or IPs used by adversaries targeting industrial control systems. Those attackers likely will never target health records.
How Can It Be Useful?
Threat intelligence is used several ways by security operations teams. The first is for threat hunting, which means security operations personnel look at historical logs for “hits” on the intelligence. Whatever the threat indicator, the objective is to see if those indicators are present in historical logs. For operational purposes, threat intelligence is consumed to generate alerts against threat indicators in real time. Or the intelligence is used in conjunction with alerts to enrich the alerting process. Intelligence is also useful during incident response. Indicators gathered during the investigative process pointing to specific types of attack or groups create a roadmap or step-by-step path for the investigation. Splunk’s whitepaper on operationalizing threat intelligence described reviewing previous attacks and analyzing them in terms of how they would play out within entity’s environment.2 This can be done in historical hunting context and with real-time alerts.
Challenges
Challenges and requirements of threat intelligence described by Splunk
Challenge | Requirement | Type of Problem |
|---|---|---|
Maximize coverage | Handle multiple sources | Data management |
Different formats, mechanisms, and tools | Use from central location | Interoperability |
Varying confidence levels | Method to prioritize | Risk modeling |
Difficult to extract value for different tasks | Provide way to enable faster decisions | Flexibility in use |
Multiple responsibilities and levels of knowledge | Deliver threat context into any operational process | Reporting |
The first column lists several types of challenges of creating a quality threat intelligence program. The middle column displays the requirement necessary to address the challenge. The last column identifies a type of problem. The first row describes a challenge of ensuring the threat intelligence covers all threat types and methods for attacking an entity. This requires entities to subscribe to several types of threat feeds. Because of this, the organization must manage all the data multiple threat feeds create.
Steps in the Mandiant/FireEye Attack Lifecycle and the Lockheed Martin Cyber Kill Chain
FireEye Mandiant Attack Lifecycle | Lockheed Martin Cyber Kill Chain |
|---|---|
Initial Compromise | Reconnaissance |
Establish Foothold | Weaponization |
Escalate Privileges | Delivery |
Internal Reconnaissance | Exploitation |
Move Laterally | Installation |
Maintain Persistence | Command and Control |
Complete Mission | Actions or Objectives |
Choosing one framework over another does not change what the SOC team does in terms of how threat intelligence is applied. It just changes the verbiage used or how intelligence is applied.
Just like logs, CTI comes in several formats. A process for normalizing the indicators for use in the environment is needed.
Threat Intelligence Formats
Threat intelligence format and normalization is necessary to use CTI internally and for sharing purposes.
Structured Threat Information eXpression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII) facilitate the packaging and sharing of threat intelligence among entities. STIX 2 is the current version and it facilitates the sharing of indicators between entities, while TAXII is a protocol used to exchange CTI over HTTPS.
Attack Pattern
Campaign
Course of Action
Identity
Indicator
Intrusion Set
Malware
Observed Data
Report
Threat Actor
Tool
Vulnerability
The benefit of using SDOs and JSON is when threat information is passed from one organization to another using STIX, ingesting the CTI is simple because the fields are consistent and the values for each formatted correctly. No additional work is necessary to make the information useful.
Threat Intelligence Strategy and Objectives
Components of security operations and how each enriches other SOC elements
Understanding the tools, tactics, and techniques attackers employ when targeting patient information aids the construction of tactical methods for detecting attacks. At the time of this writing, many attacks suffered by healthcare providers begin with spear phishing and end with ePHI stolen from mail servers. The attackers in these scenarios use spear phishing to gain an initial foothold with the goal of finding a mail server and removing data. In this scenario, the organization first must understand how vulnerable it is to this attack scenario. This is done by confirming if email attachments containing ePHI and are present in the email server. This represents a confirmed vulnerability threats target. Next the organization can review logging and monitoring sources available for the email servers. The goal is monitoring all connections and data exfiltration attempts to that mail server.
When reviewing the definition of strategic threat intelligence in Bob Gourley’s article, “Security Intelligence at the Strategic, Operational and Tactical Level,”4 a threat intelligence strategy must focus on understanding the threat actors carrying out these attacks. Traits such as motivation and capabilities to carry out the attacks are gathered and analyzed so appropriate detective and response capabilities are applied. The objective is to deploy resources in such a manner that security operations make good decisions faster and resources are deployed appropriately to that end. This is done at the strategic level by taking threat intelligence and assessing it based on knowledge of the environment where ePHI is at use, in transit, and at rest.
Recorded Future refers to this process as establishing direction.5 This means identifying and documenting the assets and business processes that are important, understanding the impacts of a compromise, and the need for threat intelligence to help protect those assets accordingly.
Threat Intelligence in Security Operations
Threat feeds, information sharing, and intelligence gathered by entities become part of the day-to-day security operations. Often, these sources are prioritized, which factors in how CTI is consumed and disseminated. Processes for gathering, aggregating, and acting on this information are vital to robust cybersecurity operations. As threat information comes into the environment in the way of indicators, a designee on the team takes the information, analyzes it, and decides on next steps. Some intelligence is consumed tactically in the form of generating alerts. This is as simple as feeding lists of IP addresses and/or domains into a monitoring tool. Intelligence is also used to make key decisions regarding monitoring, vulnerability management, and incident response.
Log data
Metadata
Feeds
Firsthand intelligence
Sources and types of intelligence should vary with an eye on “limiting how much time the team spends collecting data” so more time is spent conducting analysis.6
Threat Intelligence Sources
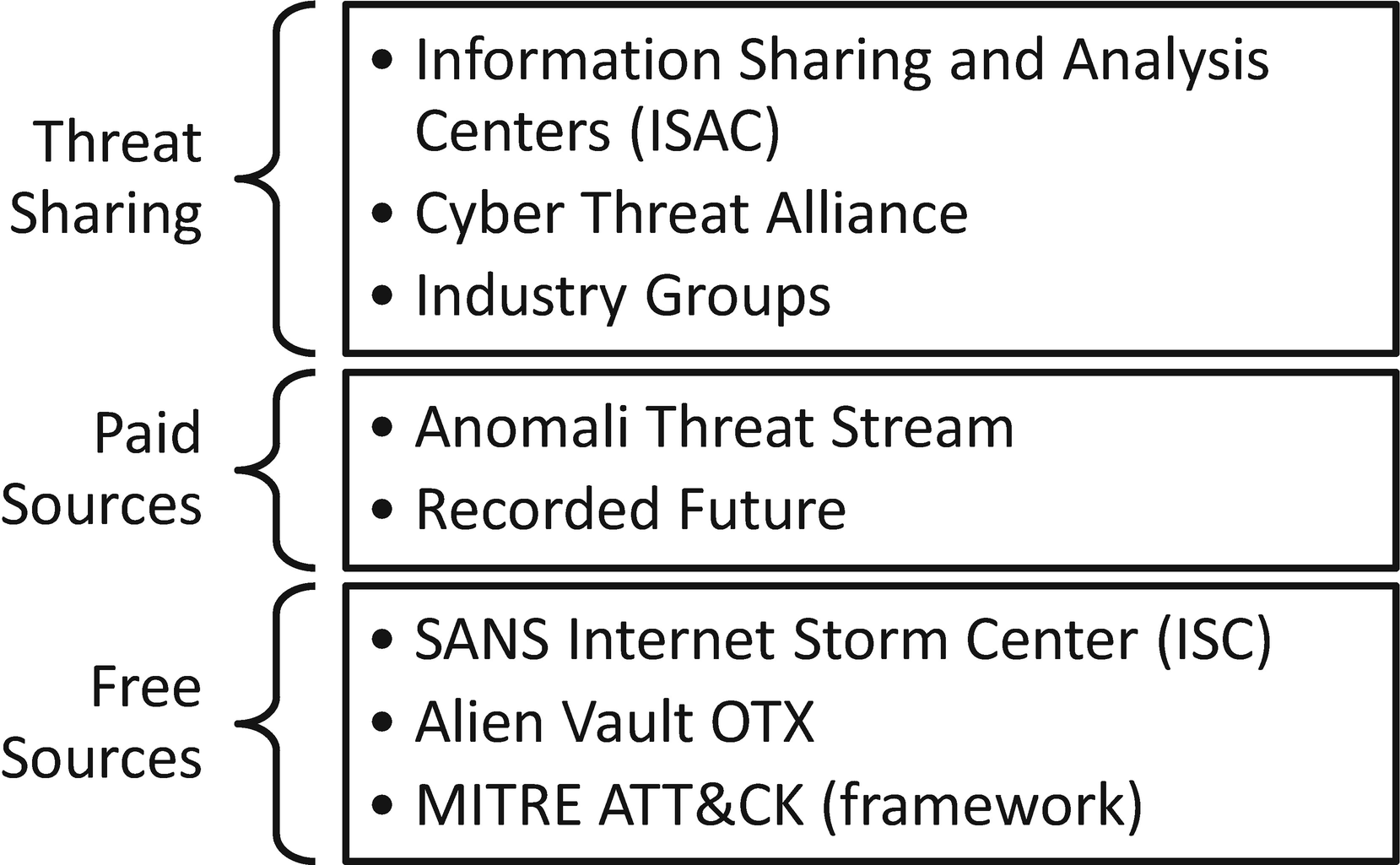
Examples of different types of threat feeds and sources
The threat sharing communities often require membership and have rules about distribution of the CTI provided. The ISAC groups denote this based on the color assigned to the alert. This is not an exhaustive list by any means but examples of each. Some offer free services and paid with additional features. These are examples.
Threat Intelligence Tactics
What logs/monitoring sources can the intelligence enrich?
What level of quality does the intelligence possess?
Threat intelligence must enrich logs and alerts generated in the environment. For instance, if an alert is generated for an outbound connection to a malicious domain, that is blacklisted. If the alert comes with additional context noting the malicious domain is active and used by an adversary targeting healthcare, the alert means much more. Any additional data informing the SOC team of contextual examples of how the indicators are used in current attacks indicates the level of quality for the intelligence and alerting.
Pyramid of Pain
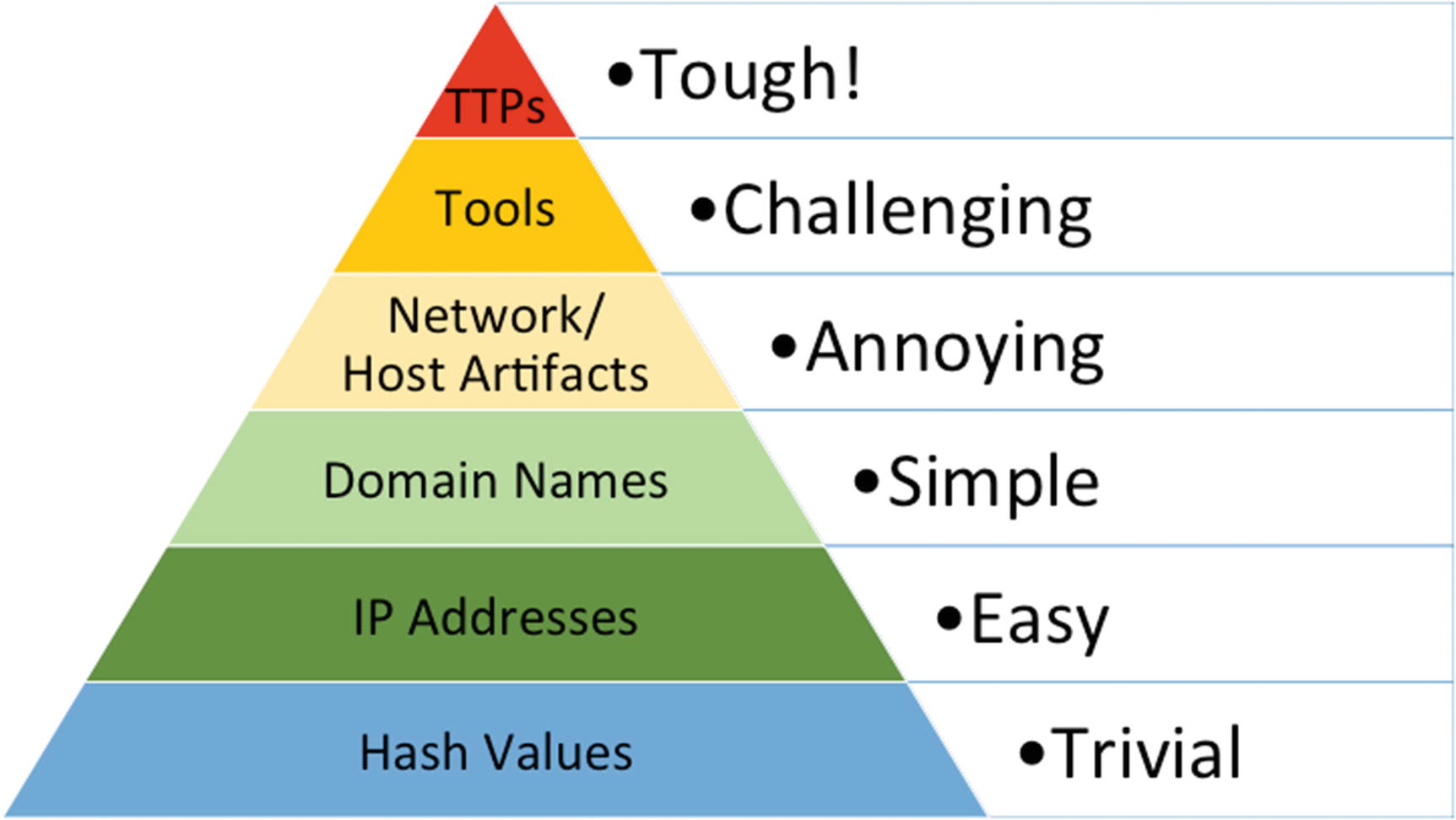
The Pyramid of Pain described by David J. Bianco8
As you can see, hashes provide some value but are so trivial to change, detecting on them is not going to generate meaningful alerts. Often, by the time a list of known hashes is available, adversaries make the necessary changes to avoid detection. Getting a hash value to change is as trivial as adding a period to a string of characters.
IP addresses and domains are not much better. Most malicious domains used in phishing campaigns and for C2 communications are only a few months old. Changing these indicators takes little additional effort compared to changing file hashes.
Bianco recommends focusing the upper layers of the pyramid. Network artifacts are things like user agent strings, uri patterns, and SMTP values used during C2 communications.
Host-based artifacts include directories created, registry changes, and new services started. The blog post rates Network and Host Artifacts as “annoying” for attackers to change. Odds are detecting these events are more valuable than the items at the bottom of the pyramid.
Tools include commands entered and software/malware used by attackers. To make changes here forces attackers to go back to the drawing board, compiling and rendering new software.
Tactics are methods such as command-line use during the execution phase of an attack. Techniques are specific actions described such as downloading tools to the victim machine via the command line. Procedures are the methods attackers go through during an attack. When dissecting Deep Panda, procedures are compromising an endpoint, downloading tools via the command line, then scanning the network for other hosts available.
Feedback
The primary use of the intelligence
Collecting the right intelligence
If the data needs further enrichment
If the intelligence is actionable
The feedback process tells the team if the threat intelligence makes a difference for the security operations team. First, identifying the use of the intelligence is important and will be based on available resources. In most instances, intelligence is used for monitoring and detection, or for threat hunting. The primary objective should be to enhance detection so that if anything significant occurs, it is detected as quickly as possible. If the time and people are available, intelligence can be used to review historical logs and data to find out if the indicators existed in the environment previously. It is a historical analysis of the environment based on new information. Teams may not always have the resources available to conduct these operations, and defining the expected use up front removes the possibility of working outside the defined objectives. Entities must understand what the right intelligence is for them and how to get it. A generic feed is not going to derive much value for security operations. Once the intelligence needs are understood, it is important for the organization to make the CTI actionable, and if it is not actionable, determine if enrichment will make it actionable.
MITRE ATT&CK Framework
The ATT&CK framework10 is a knowledge base of tactics and techniques used by attackers. Several dozen attack groups are highlighted, and dynamically created dashboards are utilized for planning detection capabilities based on adversaries that organizations anticipate attacks from. The framework consists of 11 tactics and 217 techniques. The tactics include
Initial Access
Execution
Persistence
Privileged Escalation
Defensive Evasion
Credential Access
Discovery
Lateral Movement
Collection
Exfiltration
Command and Control
Each tactic contains a list of techniques used to achieve attacker objectives.
Katie Nickels wrote several blogs outlining steps for getting started with ATT&CK. The first states the benefits of using such a framework vs. traditional approaches to CTI. The second focuses on specific questions to consider when designing an ATT&CK plan.
Nickels states the goal of ATT&CK is to improve how cyber threat intelligence is performed so that it is useful to entities.11 ATT&CK defines CTI as the application of information about adversaries in such a way that it provides value to defenders through analysis. Nickels says having analysts read reports by vendors and collecting data points from disparate sources to develop written summaries for his or her audience is outdated and unproductive. ATT&CK does not focus on indicators of compromise like IP addresses, domains, and hashes. Like the Pyramid of Pain, the focus is on the top of the pyramid, specifically, the tip where TTPs lie.
Ingesting TTPs
Focusing on detecting behaviors
Assessing and viewing TTPs of multiple adversaries and tools at the same time

A partial visual comparison of APT 3 and APT 29 using the ATT&CK Navigator tool
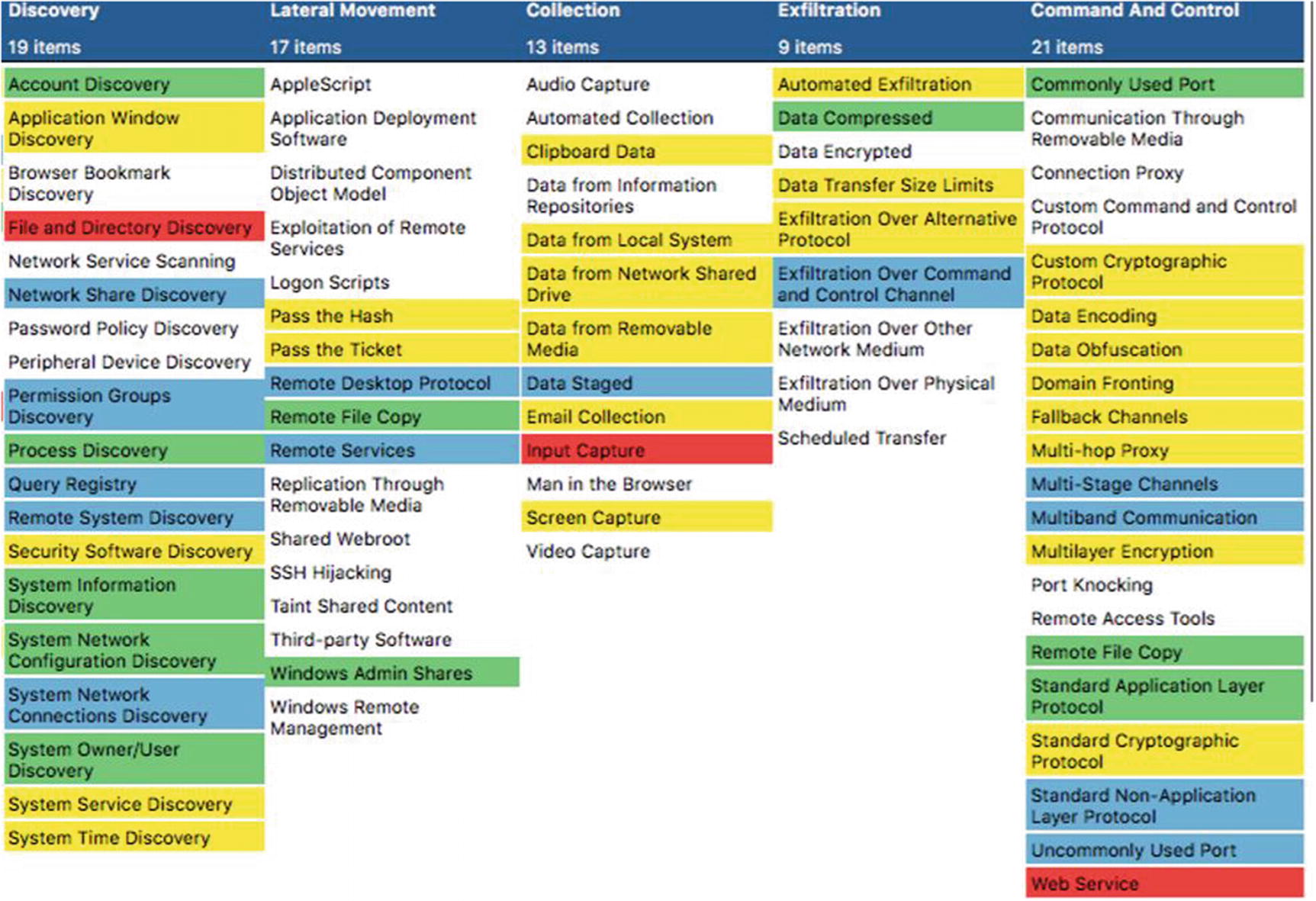
A visual comparison of APT 3 and APT 29 using the ATT&CK Navigator tool with entities’ capabilities input
ATT&CK is flexible. While Katie Nickels provides an easy-to-use method for getting started, it by no means is the only way to use ATT&CK. The visual representation makes ATT&CK easy to view and understand. The team can color-code the techniques of concern, using colors to indicate level of concern. The level of concern usually depends on the existence of capabilities to defend against those techniques. As Nickels put in her blog, the ones in red did not have defenses available.
In her second blog introducing ATT&CK, Nickels mentions the need to have a database where indicators are stored. If one already exists, then it can be used by the entity. If one does not, then the MISP platform can be used.12 MISP is Malware Information Sharing Platform supported by the Open Standards for Threat Information Sharing (OSINT). MISP is a platform for sharing, storing, and correlating threat intelligence indicators. These indicators include information about malware, incidents, and attackers both technical and non-technical.
Again, this platform, like ATT&CK, brings value and maturity to security operations. Automatic correlation, finding relationships between attributes and indicators from malware, and attack campaigns are example use cases. The correlation engine is capable of advanced correlations like Fuzzy hashing. This technique looks for domains that are close to yours referenced in network traffic. Often, attackers will use domains close in name to fool end users and avoid detection. Entities using MISP can choose to enable and disable attributes based on need. Data from the platform can be fed into tools like intrusion detections systems (IDS). Data exports in CSV, XML, or JSON make it possible to parse the data with relatively little effort. This also allows for bulk, batch, or ad hoc imports of indicators to monitoring tools.13
Walkthrough Using ATT&CK
One adversary known for targeting healthcare entities are Deep Panda (a.k.a. Black Vine) a group Symantec credited with the 2015 breaches of Anthem and Premera Blue Cross.14 A discussion of these groups and how ATT&CK can be used to prepare defenses follows.
Deep Panda/Black Vine
Shell Crew
WebMasters
KungFu Kittens
Pink Panther
Black Vine
For our purposes here, the objective is identifying defenses against these attack groups. Earlier we discussed the Pyramid of Pain15 by David J. Bianco. Using the pyramid focuses security operations on ways to detect the presence of these groups. ATT&CK describes indicators located at the top of the pyramid. Much of the data describes the tools/software used and TTPs. For example, software tools used by attackers are where entities should focus detection capabilities. Detecting an attacker’s presence based on specific actions of software/tools used forces the group to find or develop new tools. This is not a trivial task, so attackers do not make changes like this very often.
Derusbi: This software/malware tool is used across many of the tactics: execution, privilege escalation, evasion, credential access, discovery, and collection. That is six of the ten tactics ATT&CK tracks. Derusbi also communicates via command and control.
Mivast: This is a software/malware tool that creates a backdoor assisting attackers in persistence, privilege escalation, and lateral movement.
Sakula: This is a Remote Administration Trojan used in execution, privilege escalation, and defense evasion. Sakula also communicates via command and control.
Black Vine ATT&CK Matrix

Deep Panda techniques used during execution
Execution is the first phase in the attack chain developed by MITRE. A lot of activity occurs at the command line. Running commands vs. executing programs in files avoids detecting by scanning tools. Each software tool documented by ATT&CK uses the command line at some point. PowerShell is used by Deep Panda. Programs are downloaded and executed using this tool to avoid detection by file analysis tools.
There are ways to log commands executed at the command line. The ability to log commands executed is valuable when investigating endpoints of interest. Long commands and commands not normally executed by end users on an endpoint are signs of trouble. Looking for the use of Invoke-Expression, its alias iex and Net.WebClient the command line are potential indicators of nefarious behavior.

Examples of tactics used by Deep Panda during the persistence phase
Deep Panda uses sticky keys to bypass login screens where Windows Remote Desktop is enabled. RSA reported in its Emerging Threat Profile of Shell_Crew in January 2014 that this is achieved in one of two ways: either via replacing the sethc.exe file or by making registry modifications. Once either of these techniques is implemented, the attacker only needed to hit the Shift key five times to bypass the login screen and get a shell prompt.17
Symantec’s report on the use of Mivast malware highlights changes made in the registry, specifically, HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunMicromedia.18
Web shells report19 describes the use of web shells and Deep Panda’s use during attacks. These shells are commonly used as backdoors and leverage scripting languages. Examples include ASP, ASPX, PHP, and JSP. Commonly, this is used for attackers to remotely access systems to perform malicious actions. Attackers often use these shells as the foothold into organizations during initial phases of attack. CrowdStrike found that Deep Panda used these shells as a form of persistence. Deep Panda uses Internet Control Message Protocol (ICMP) Echo Request (a.k.a. ping) for remote system discovery. Spotting ping sweeps from web servers might indicate a compromise and enumeration of the environment underway.

Techniques used by Deep Panda to escalate privileges
The privilege escalation techniques titled Accessibility Techniques, used by Deep Panda in Windows environments, is C:WindowsSystem32sethc.exe. attributed to Shell Crew in RSA’s Emerging Threat Profile.20 Known as the sticky key backdoor, it is used against systems using Microsoft Remote Desktop Protocol (RDP). The threat profile documented by RSA describes two methods used to make this technique successful. One involves replacing the sethc.exe file and the other making modification to the registry. Security operations objectives should include evaluating capabilities that may detect registry changes like those described in RSA’s documentation.
By injecting itself into a Secure Shell (SSH) process, Derusbi can elevate privileges. SSH is used to create secure connections between servers. Administrators use this protocol often when remotely accessing servers on the network. Process injection is described in detail during the defense evasion section, but here, Derusbi injects code into memory where the SSH process instructions are located. This can allow Derusbi to capture the credentials used for that process, thus elevating privileges.
Deep Panda uses web shells for a few reasons. Web shells are key in some initial compromises, used as a persistence mechanism and a method to escalate privileges. The shell may have elevated privileges when gained, or it can be a pivot to other opportunities for privilege escalation.
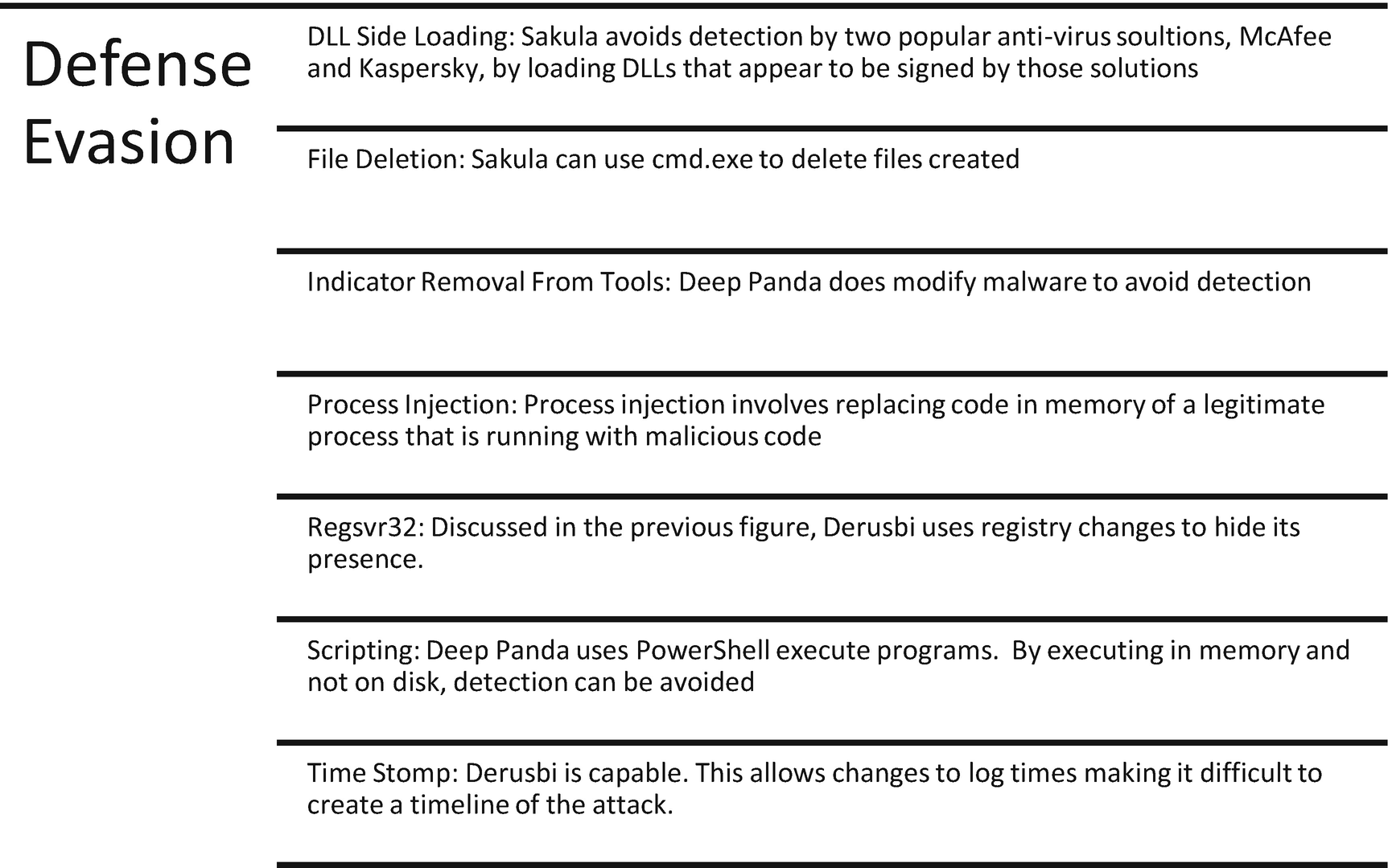
Defense evasion techniques used by Deep Panda
Deep Panda and its software use several techniques to avoid detection. Dynamic Link Libraries (DLLs) are code libraries for use in Windows programs. DLL imports are common in malware, and here Sakula uses DLLs signed by Kaspersky and McAfee to avoid detection by these solutions.
Process injection involves injecting malicious code into memory address spaces used by legitimate processes. This allows the malicious code to use the resources meant for the use by the legitimate process making it difficult to detect the malicious process because it appears the legitimate process is running normally.
The use of PowerShell scripting and executing programs in memory, keeping scripts out of files and disk space, avoids detection. This means detection capabilities must detect the use of PowerShell. Enabling module or script block logging of PowerShell use and/or deploying Sysmon detects the use of malicious PowerShell activity.
Removing evidence by deleting files and changing timestamps in logs make the SOC’s job harder. These actions make it difficult for analysts and investigators to put together a complete picture of an attack sequence.

Credential access techniques used by Deep Panda
New Technology LAN Manager is a security protocol designed by Microsoft. In Microsoft lingo, NT stands for New Technologies. NTLM v2 is the current version. This protocol uses a 128-bit MD4 hash to store password values on a server, usually a domain controller (DC). If the attacker obtains these hashes, they can be used to authenticate to systems through attack techniques known as pass the hash. To learn more, most pen testing books and articles contain detailed walkthroughs of these techniques. Deep Panda also used software tools to capture keystrokes. If successful, a log containing usernames and passwords can be gathered.
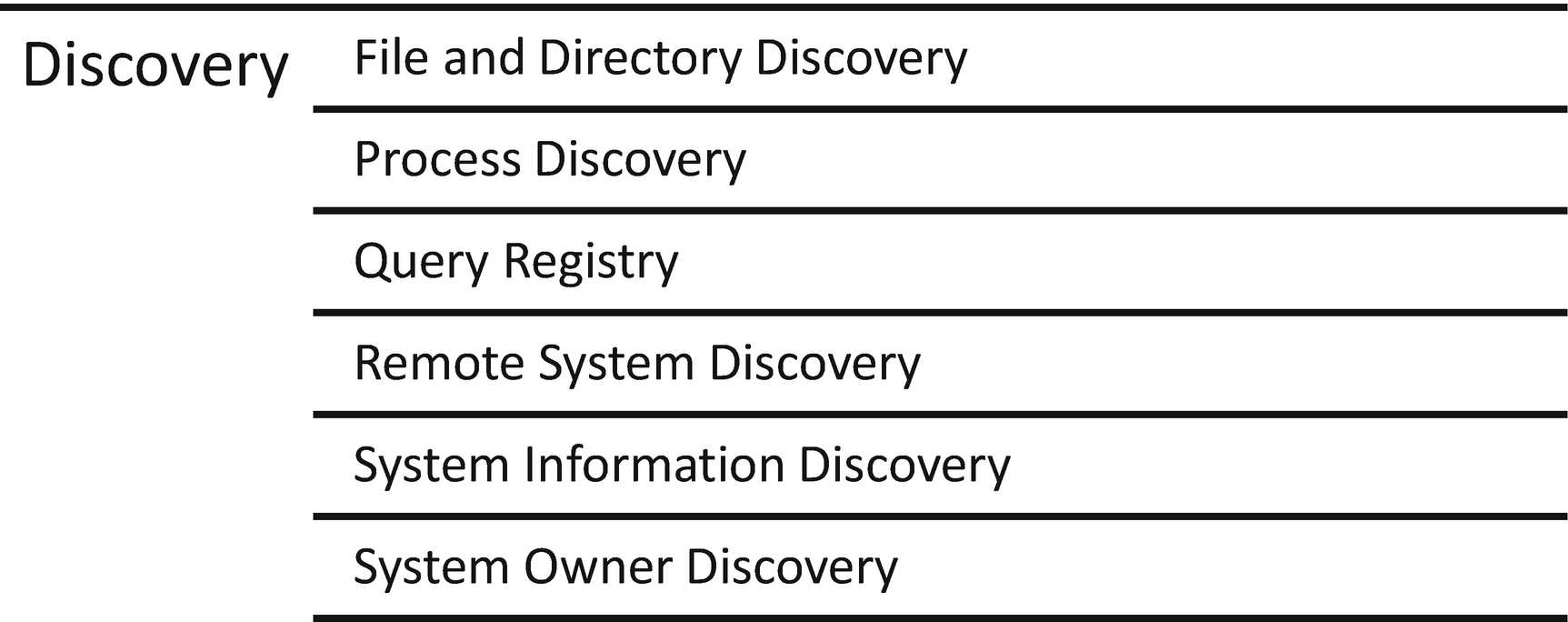
Discovery tactics used by Deep Panda
Just like any other attack group, Deep Panda uses resources available in the network to achieve its objectives. Either manually or using software tools, Deep Panda enumerates file systems, identifies processes running on endpoints, and uses them to its advantage. Blending in with expected processes makes it difficult to identify malicious use. Derusbi will query the registry to gather keys and values.21 This way, settings can be changed to aid in maintaining persistence. Other techniques include understanding if remote systems are in play – like using Windows Remote Desktop Services (RDS) or Virtual Private Networks (VPNs). Gathering information on system owners, naming conventions for endpoints, and service account usage give Deep Panda insight into understanding what administrative credentials are useful.

Collection tactics used by Deep Panda
Deep Panda uses several techniques to collect data based on the objectives of the attack. These techniques are executed by Derusbi, which FireEye also calls PHOTO in its threat research blog.22 Derusbi captures data on screens, user input, video, and audio files.
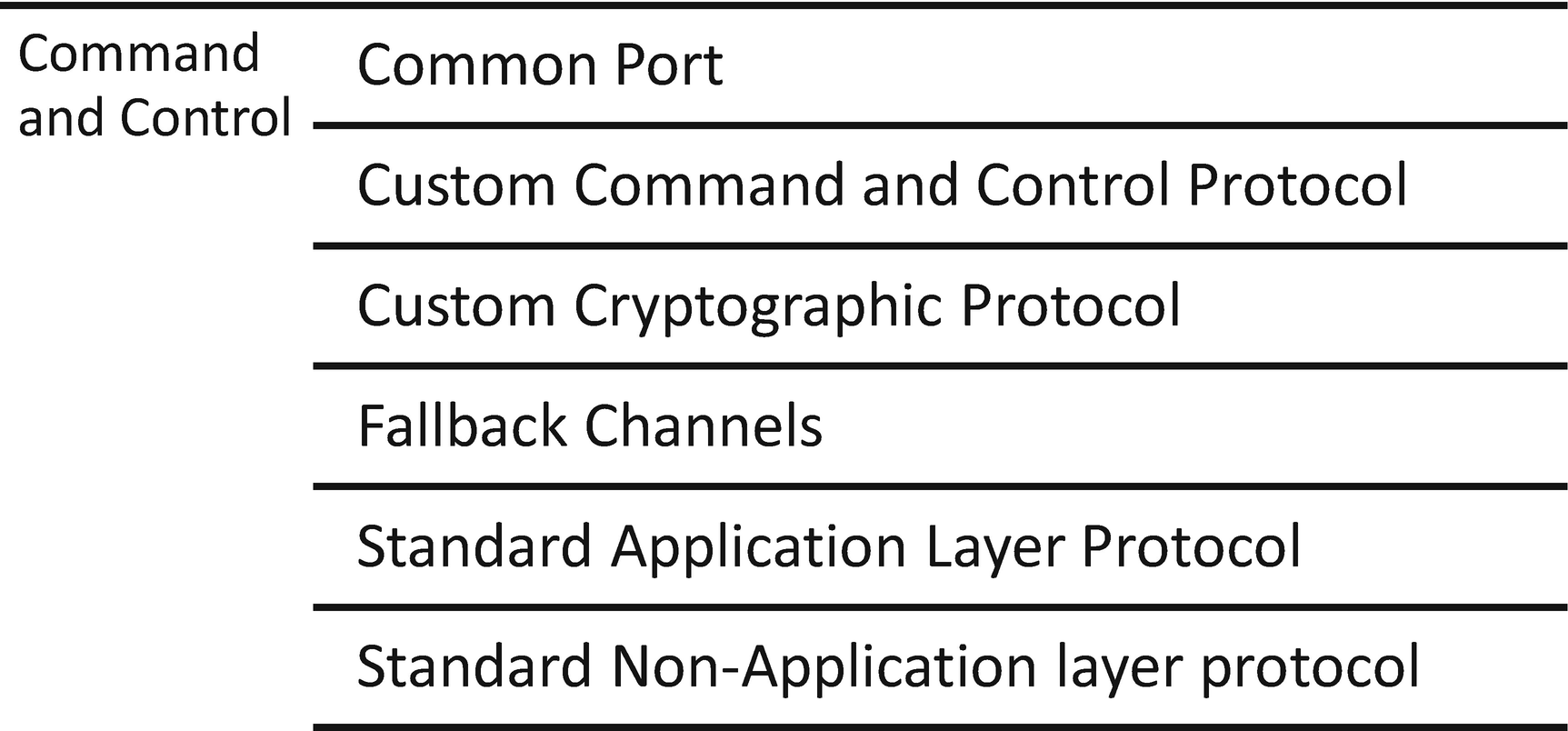
Command and control tactics used by Deep Panda
Malware like the ones attributed to Black Vine need to communicate with the group’s command and control servers. This is done via application layer protocols like DNS, SMTP, HTTP, or HTTPS. Others may be used, but these techniques are most common. Common ports are sometimes used with the protocols and sometimes non-standard ports are used. Some tools associate protocols with common ports, so any traffic on port 80 is considered HTTP by the monitoring tool. Deep Panda also uses custom ports. Derusbi, ATT&CK states, does use ports 31,800 to 31,900 during command and control communication. These are raw socket connections operating as a customized protocol. A tool like Zeek would catch this technique because it looks for specific attributes in the traffic. GET and POST requests on any port will identify as HTTP and be logged by Zeek as such. Finally, Black Vine’s tactics will disguise communications using encryption.23 Alerting on the ports used and the standard and non-standard protocols can detect the use of these techniques. Derusbi also uses custom cryptographic protocols for command and control. Deep Panda XORs the communications with a 4-byte key. There is really no way to see this artifact in any traffic analysis tools. To detect C2 communications by Deep Panda, flow data showing connections to known/current IPs and domains in use by Deep Panda is the key to detection. Finally, the fallback channels noted describe Deep Panda’s plan B move to common protocols and applications when the custom options do not work.
Other Threat Intelligence Frameworks
Other threat intelligence frameworks besides ATT&CK exist. These alternatives are used as stand-alone implementations or as complements to each other. The two detailed here are the Malware Information Sharing Platform (MISP) with integration to the ATT&CK framework and Palo Alto’s Unit 42.
Malware Information Sharing Platform (MISP)
Ability to correlate and link indicators
Sharing functionality
Graphical interface
Importing, exporting, and storing data
Integration with other threat feeds
API used to integrate with internal systems
Adjustable taxonomy for tagging and classifying intelligence
MISP comes with default built-in threat feeds that users can choose to incorporate. When configuring the initial installation, feeds desired are enabled. MISP also provides a matrix showing the overlap between each feed to limit duplication within the platform.24 The other feature is the ability to use nomenclature from ATT&CK in MISP.
Unit 42
OilRig
Sofacy
PickAxe
PatchWork
DarkHydrus
Reaper
Rancor
Tick
DragonOK
menuPass
Conclusion
Cyber threat intelligence (CTI) is a value-add component of security operations. The benefits derived occur if the right people and processes exist. Subscribing to a threat feed, integrating it with monitoring devices and/or a Security Incident and Event Management (SIEM) solutions, and waiting for matches to occur is a process that does not work. The Pyramid of Pain illustrates this. IP addresses, domain names, and file hashes that make up the bulk of some feeds do not trigger substantive alerts. Instead false positives abound. An IP address considered malicious six months ago may not be when seen in the network. Analysts take time investigating these false alerts taking time away from more value-added activities. Using CTI and indicators at the top of the pyramid helps enrich alerts and direct the security team toward meaningful alerts.
To get started using threat intelligence, organizations must first ensure the fundamental security processes are in place. Control frameworks such as the NIST Cybersecurity Framework and Center for Internet Security (CIS) list of 20 controls signify fundamental processes needed. Once complete, CTI adds enrichment to logging and alerting. Stakeholders must convey threat intelligence needs. Large organizations with separate duties between information security and SOC analyst teams require those operating the SOC to collect and disseminate intelligence useful to members of the security team. In small and medium organizations like most healthcare providers and business associates where individuals wear both types of hats, the intelligence gathered should augment logs and alerts.
