OS X El Capitan forensics
Abstract
Apple’s OS X has a steady growth within the United States. This also means digital forensics laboratories will likely see more OS X products. This chapter looks at Mac OS X 10.11 El Capitan. The chapter begins at the top level or root directory, and it works down the file system. This chapter highlight areas of forensic interest. However, it also takes a basic look at the file system as a whole. This chapter gives the analyst a foundation in OS X. There is also a quick guide at the back of the chapter providing paths to key forensic information.
Keywords
Introduction
Table 7.1
Names of OS X Operating Systems
| OS X Number | Name | Release Date |
| 10.0 | “Cheetah” | March 24, 2001 |
| 10.1 | “Puma” | September 25, 2001 |
| 10.2 | “Jaguar” | August 24, 2002 |
| 10.3 | “Panther” | October 24, 2003 |
| 10.4 | “Tiger” | April 29, 2005 |
| 10.5 | “Leopard” | October 26, 2007 |
| 10.6 | “Snow Leopard” | August 28, 2009 |
| 10.7 | “Lion” | July 20, 2011 |
| 10.8 | “Mountain Lion” | July 25, 2012 |
| 10.9 | “Mavericks” | October 22, 2013 |
| 10.10 | “Yosemite” | October 16, 2014 |
| 10.11 | “El Capitan”* | September 30, 2015 |
Names of Mac OS X Operating Systems and release dates. Mac updates generally have a version number and a name. For example, OS X 10.7 was called Lion. Although OS X can be referenced by either number or name, it is preferred to reference the version number to include minor updates (e.g., OS X 10.7.1).
* Note: All research pertaining to OS X 10.11 in this book was using the developer beta 6. The final version was not released at the writing of this book.

This is an example of the commands listed in Table 7.2. This gives the forensic analyst a sample of command line tools and processes. The commands show how to list all files, change directories, show your current directory, and show running processes.
Default directory structure
Table 7.2
Common Unix Commands
| Hint to Function | Terminal Call | Function |
| Manual | man | Most functions will have a help page dedicated to describing its function. This will list optional calls and define how to call the function. |
| copy | cp | The copy function is the command line version of copy. |
| move | mv | Move a file or directory to another location (think cut and paste). |
| nano | nano | An early predecessor to notepad or Microsoft word |
| vi | vi | An early predecessor to notepad or Microsoft word. A little more complicated to use than nano. |
| list | ls | Lists the files and directories. There are options such as – a that will show hidden files as well. |
| change directory | cd | This command allows a user to change directories. |
| print working directory | pwd | This will show the user where they are in the file structure. |
| process | ps -e | This function will list all processes running on the system. |
These Unix commands can be used on most versions of Linux and OS X. They are basic commands used in the Terminal application.
Root directory
Applications
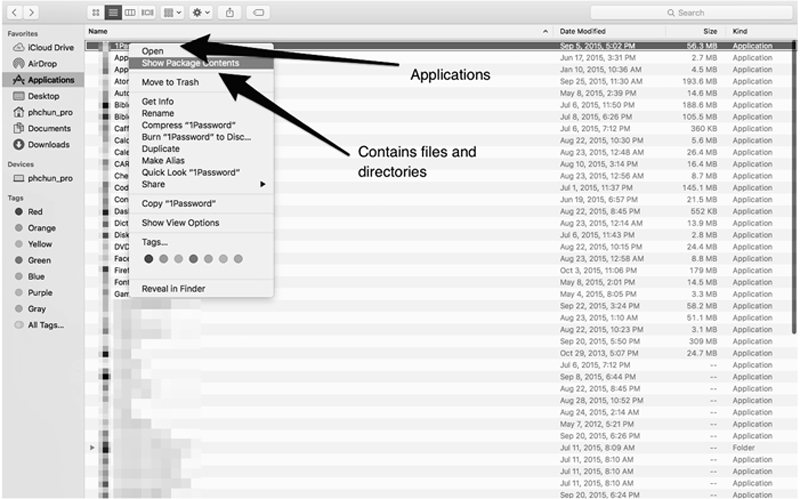
Applications in Mac OS X actually contain files behind the icon. By right clicking and selecting “Show Package Contents,” the investigator can see the files within the application.

This shows the structure of an application directory. Some applications may store user information or metadata within the application itself.
Bin/sbin
Library/system
Private
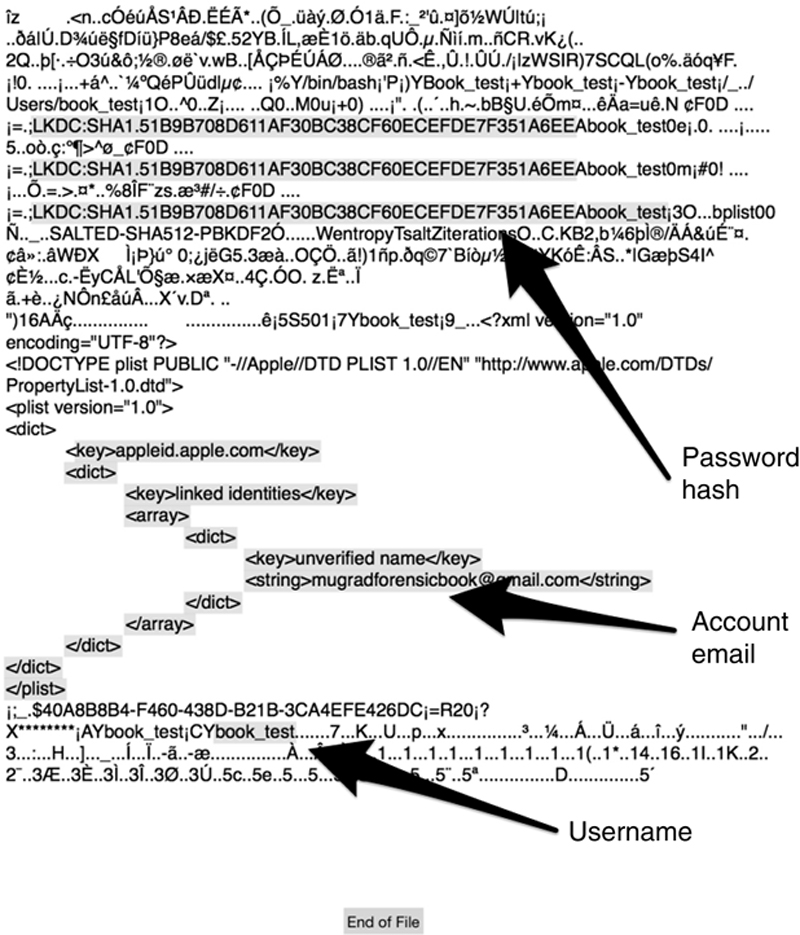
The private directory contains the hash of the user’s password. It will also give the investigator the default email account linked with the user and the user name.

The dhcpclient plist contains the address of the last connected router. It will also contain the date the machine acquired an IP address and the length of the lease. The router hardware address is also given in this file. This could indicate what network the machine assessed.
Usr
Var
User
User’s directory
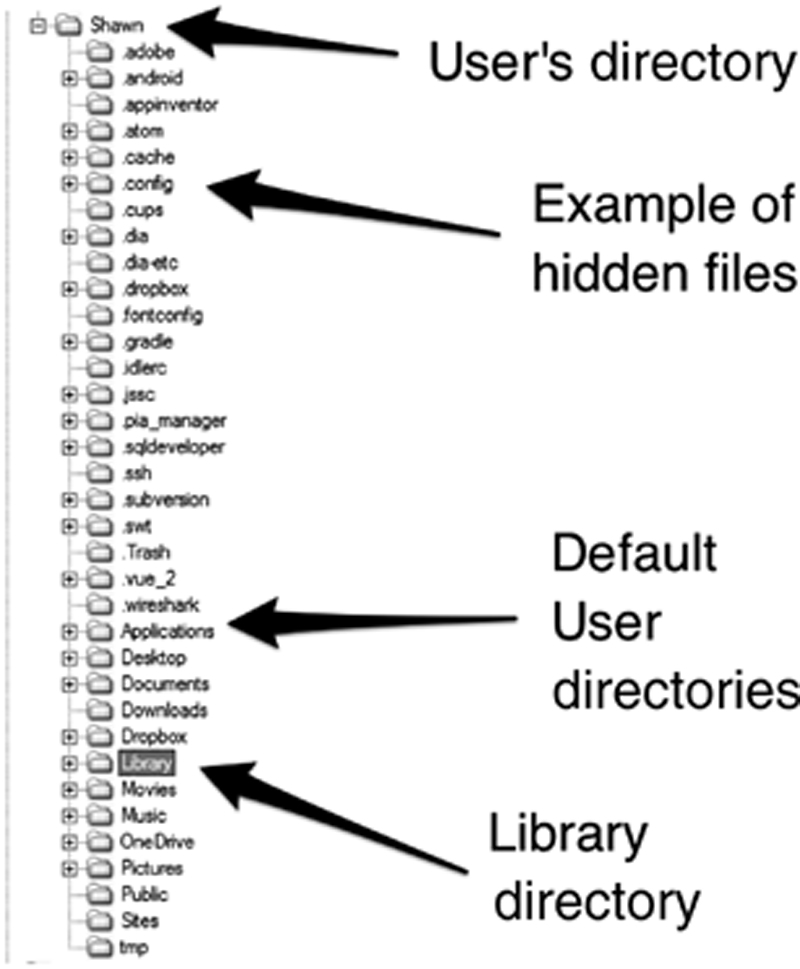
Every user has a directory under their user name. Some examples of hidden directories are shown and will not be shown by default in Finder. The default directories include Applications, Documents, Library, etc. The Library directory contains the user’s preferences, iMessages, email, and more.
.cups
.ssh

The known_host file contains all the SSH connections for the user. This will include domains or IP addresses of connections. The file contains the method of key encryption, as well as the private key for this machine.
.Trash

The .DS_Store file is similar to the $I and $R files in Windows. It maintains the name of the deleted item. It also stores the path of the deleted item in the event the user decides to restore the item.
Desktop/documents/.DS_Store
Pictures

Users can pick faces out of their photographs in the Photos application. Photos will scan other photographs for that face, and it will link the name with a contact if available.

The Faces feature keeps randomly named file on every identified face. The name can be located in the random string file, and it can also contain an email address for the identified face. An investigator would use this to build connections.
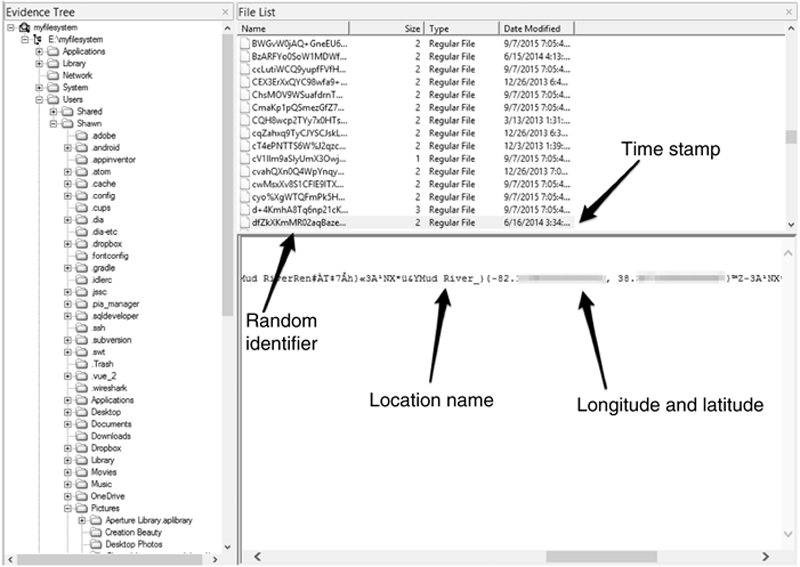
Places uses the EXIF data out of the photographs in Photos. It records the information in a cryptic file name. The modified dates can help the investigator to link the actual photograph to Places and Faces files. Also, Places attempts to pull a location name using the coordinates.
iMovie
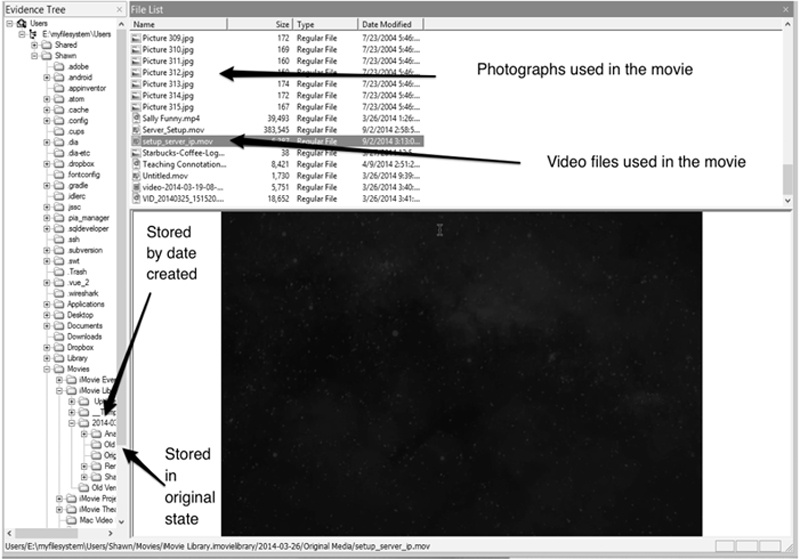
iMovie stores information in a similar fashion to most of Apple’s applications. The project file actually contains a directory of files and subdirectories. Also, every image and video used in a movie project is stored inside the project directory.
{User name}/library
Accounts

The accounts database contains all the usernames of accounts accessed by the user. This can include Facebook, Twitter, email service providers, and some messaging services. Since most usernames are emails, this will also give the investigator an idea of what email addresses belong to the user.
Application support/call history
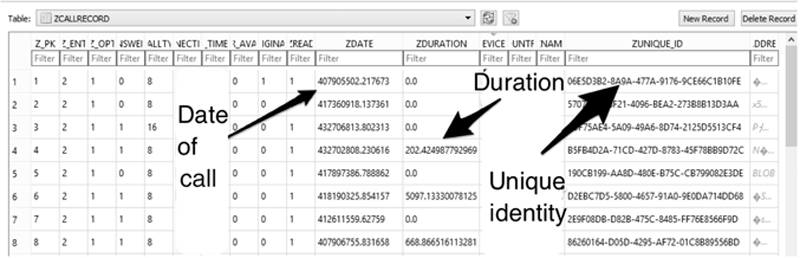
This database contains the unique identifier, call date and time, duration, and more. This database does not contain the phone number used, but the unique identity can be linked with the CallHistoryTransaction database.
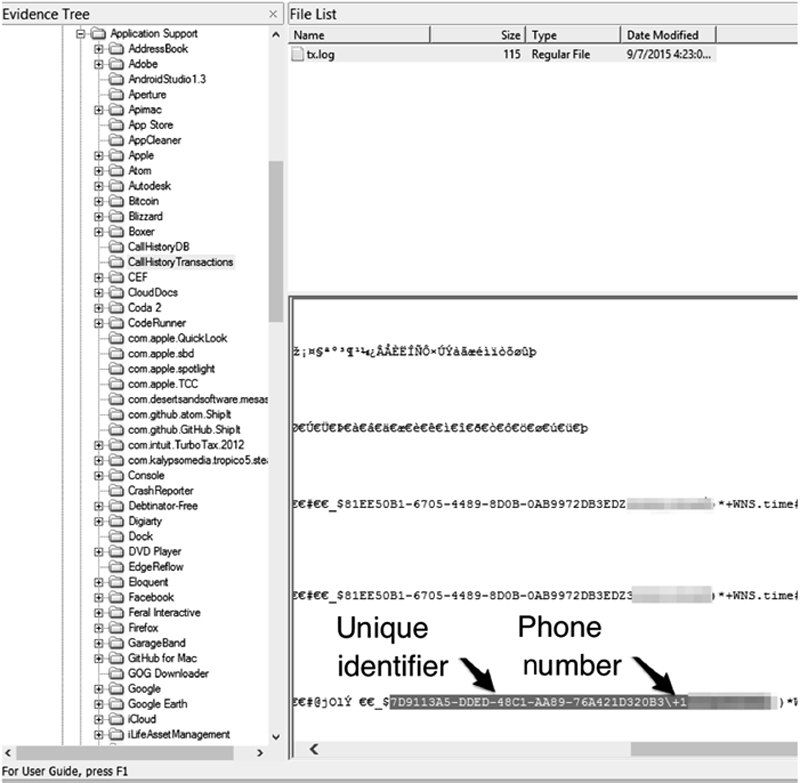
This database is needed with the CallHistoryDB database. This contains the numbers called or received, as well as the numbers unique identification used in CallHistoryDB.
Caches
Calendar

This shows the Holiday calendar in the Calendar application. Each account is given a randomly named identity. All events are stored in a subdirectory called Events. Every event will have its own file.
Mail downloads
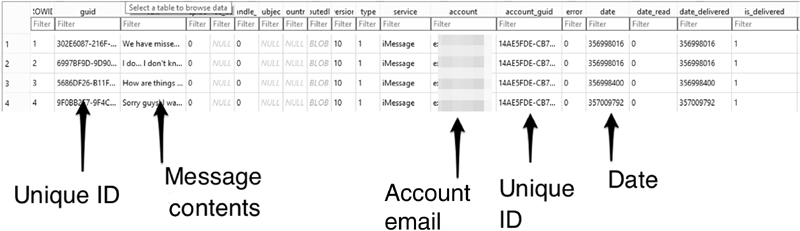
Messages

Notes
New features in OS X 10.11 El Capitan
Conclusion
Quick reference table
Table 7.3
Table of Key Default Locations
| Category | Item | Path | Description |
| Root | Root directory | / | The top of the file hierarchy |
| Application | /Application | The applications available to all users. | |
| Binaries | /bin | Binaries for command line tools | |
| Library | /library | Universal configurations for users and applications. | |
| Private | /private | Contains sensitive information usually restricted to users (such as hashes) | |
| System binaries | /sbin | Binaries used by the operating system | |
| System | /system | Contains a Library directory for system configurations | |
| Users | /User | Contains the user’s content and configurations. Each user should have a subdirectory here. | |
| Password | User passwords | /private/var/db/dslocal/nodes/Default/users/{user’s name}.plist | This contains a plist with the user’s password hash in SHA1. |
| Exterior Interactions | .ssh | /User/{un}/.ssh/ | Contains SSH private keys and IP addresses of sessions |
| .cups | /User/{un}/.cups/ | Contains the printers used | |
| Trash | System trash | /.Trashes | Contains system’s deleted items |
| User trash | /User/{un}/.Trash | Contains files and directories deleted by user | |
| Trash data | /User/{un}/.Trash/.DS_Store | This contains the last location of items in the .Trash directory | |
| Accounts | User accounts | /User/{un}/Library/Accounts | Contains an SQLite database of accounts |
| Calendar | /User/{un}/Library/Calendars/{Random string} | Contains info.plist of accounts with calendar capabilities | |
| Mail accounts | /User/{un}/Library/Mail/V{Some number}/ | Contains a subdirectory for each account with email address | |
| Safari | Cache | /User/{un}/Library/Caches/com.apple.Safari/WebKitCache/ | This contains a cache of images from Safari |
| History | /User/{un}/Library/Safary/history.db | This is an SQLite database of the user’s history | |
| Bookmarks | /User/{un}/Library/Safari/Bookmarks.plist | Contains the user’s bookmarks | |
| Messages | Message database | /User/{un}/Library/Messages/chat.db | Contains the user’s iMessages and SMS if enabled |
| Mail messages | /User/{un}/Library/Mail/V{Some number}/{Account}/{Inbox name}/{Random string}/Data/Messages | Leads to email messages stored on the system. Emails are stored in an .emxl format. | |
| Photos | Photo library | /User/{un}/Photos/Photos Library.photoslibrary/Masters | This contains the unedited photos in the Photo application. |
| Photo faces | {un}/Pictures/Photos Library.photoslibrary/Database/Faces/Facenames | This contains the information for faces identified in the Photo’s app | |
| Movies | Movie location | /User/{un}/Movies | |
| Calendars | Calendar location | /User/{un}/Library/Calendars/{Random string} | Calendars separate accounts with subdirectories with random strings. The info.plist will give you an idea of what the account is used. |
| iCloud | Synced iCloud data | /User/{un}/Library/Mobile Documents | Contains synced iCloud data |
| Documents | Documents | /User/{un}/Documents | Local document default storage path |
| iCloud documents | /User/{un}/Library/MobileDocuments/com∼apple∼CloudDocs | Synced iCloud Documents | |
| Calls | Facetime metadata | /User/{un}/Library/ApplicationSupport/CallHistoryDB/Callhistory.storedata | This contains metadata of Facetime and phone calls including duration, date, and type (Facetime, etc.). The phone numbers are not included, but the unique ID can be matched to the tx.log file (see below). |
Facetime Phone numbers |
/User/{un}/Library/ApplicationSupport/CallHistoryTransactions/tx.log | Log file that contains the phone numbers with the unique ID used in the CallHistory.storedata file. |


Quick Reference Chart: {un} indicated the user’s name.
