Defining the DMZ Environment
The demilitarized zone (DMZ) is a special network that joins a private corporate network with an untrusted network. That untrusted network might belong to a business partner, a carrier, an Internet service provider (ISP), or other parts of the corporate network. The DMZ supports very specific ingress and egress connectivity between the two networks.
The DMZ contains routers, packet filters, Ethernet switches, DNS servers, web servers, proxy servers, socks servers, and telnet gateways. It’s generally a collection of subnets configured for very specific security-minded functionality. Correct operation of the DMZ is critical and it must be managed proactively.
Ingress into the private network is often restricted to SMTP-based services (e-mail). Egress out of the private network is often restricted to web traffic (HTTP), file transfer get operations (FTP), telnet, and SMTP-based e-mail.
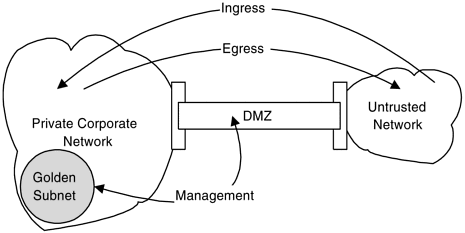
How do you manage the DMZ? Since access to the DMZ is restricted, you could situate an NNM system inside it. How would users gain access to the NNM system? You could require users to access NNM physically from within the DMZ. You could also configure a pinhole through the DMZ firewall to pass X-Windows traffic to a golden subnet located on the private network.
Alternatively, you could situate the NNM system on a golden subnet in the corporate network (see Figure 10-1) and configure pinholes that allow just this system’s network management traffic into the DMZ. Users can access the NNM system from any location since their X-Windows traffic is entirely inside the corporate network.
Figure 10-1. Managing the DMZ.
A golden subnet is a specific subnet from within which a specific NNM system is allowed to access managed devices. The golden subnet is located within the corporate network, and network managers access systems located here to manage the DMZ as well as the rest of the corporate network. Routers are usually configured to accept SNMP requests from either any device on this subnet or just specific devices (usually the NNM systems).