Code signing is a technique for signing executable programs with digital signatures. Code signing is designed to improve the reliability of software distributed over the Internet by making it possible to detect very minor alterations to programs. Code signing is also designed to combat the problem of malicious programs, including computer viruses and Trojan horses.
This chapter describes the mechanics of code signing. For a discussion of why code signing might not provide the degree of safety its backers hope for, see Chapter 12.
Walk into a computer store and buy a copy of Microsoft Windows, and you can be pretty sure the box contains a genuine CD-ROM with a computer operating system written by the Redmond software giant. The program, after all, comes shrinkwrapped in a box, with a difficult-to-forge security hologram seal. Inside the box is a CD-ROM that may include its own hologram. You have great confidence that your CD-ROM or floppy disks have the same program as every other CD-ROM or floppy disk sold in every other Windows box. Presumably, the software was checked at the factory, so you have every reason to believe that you’ve got a legitimate and unaltered copy.
The same can’t be said for software downloaded over the Internet. When Microsoft released its 1,264,640-byte Service Pack 1 for Windows 95, the only way to be sure that you had a legitimate and unaltered copy was to download it directly from Microsoft’s web site—and then hope the file wasn’t accidentally or intentionally corrupted either on Microsoft’s site or while it was being downloaded.
What’s worse, if you wanted to save yourself some time by copying Service Pack 1 from a friend, there was no way that you could inspect the file and know whether it was good or not: your friend’s copy might have been corrupted on his hard disk, or it might have been infected with a virus, or it might not even be the right program. How do you know if it is a true copy, other than trusting your friend at his word?
With Microsoft Windows 95 Service Pack 1, there was no way to electronically certify the contents of code downloaded over the Internet. But starting with Internet Explorer 3.0, Windows users were given a powerful system for trusting the authenticity of their software: digital signatures for executable programs. Called Authenticode , the Microsoft digital signature system is specifically designed to allow users to verify that downloaded programs are authentic and unmodified.
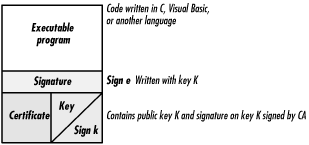
Code signing was supposed to bring the assurance of shrink-wrapped software to the world of software that’s distributed electronically. It does this by adding two things to an executable:
A digital signature that signs the executable with a secret key.
A digital certificate that contains the corresponding public key, the name of the person or organization to whom that key belongs, and a digital signature signed by a recognized certification authority.
These are shown in Figure 22-1.
Figure 22-1. A piece of signed code, showing the code’s digital signature and the corresponding digital certificate.
To work, code signing presupposes the existence of a working public key infrastructure. Otherwise, there is no way to tell whose signature is on a piece of signed code. Code signing also requires that those individuals and organizations that hold secret keys protect them properly. Otherwise, there is no way to know if a signature was written by an authorized individual or by a malicious attacker who obtained a copy of another’s secret key.[190]
Microsoft’s Authenticode system is used most often with VeriSign’s public key infrastructure, although any certification authority key that is approved for code signing and that is in the Internet Explorer key store can be used for verifying Authenticode signatures.
To be useful, the signatures must be verified. Internet Explorer will analyze code after it is downloaded to determine if a signature is or is not present. Later versions of Windows, including Windows 2000, ME, and XP take Authenticode one step further and use it for signing critical parts of the Windows operating system. These signatures are verified every time the Windows operating system starts up. In this way, code signing can detect malicious attempts to modify code, accidental modifications that might result from operating system errors or hardware failure, and unauthorized modification attempts by the user. Thus, code signing can dramatically boost the reliability of today’s computer systems by allowing us to detect modifications in programs before those programs are run.
Code signing has also been proposed as a way of creating accountability for people who write programs and distribute them on the Internet. The idea is that Internet users should be taught not to run programs that are unsigned.[191] Then, if a malicious program is distributed on the Internet, it will be a simple matter to find out who distributed the program and punish them. By establishing significant penalties for people who distribute malicious programs, as well as a reliable technique for tracking those authors, it is thought that the incidence of such programs will be greatly diminished.
There are several code signing systems in use today:
Authenticode, which is Microsoft’s system for signing CAB, CAT, CTL, DLL, EXE, and OCX files
Microsoft Office 2000 and VBA Signing, which allows software publishers to digitally sign Microsoft Office Macros and Visual Basic for Applications objects
Netscape Object Signing, which can be used to digitally sign Java Archive ( JAR) files, Netscape plug-ins, Java programs, and JavaScript programs
Macromedia Shockwave digital signatures (requires Director 8 Shockwave Studio or Macromedia Flash)
Marimba Castanet, which supports code signing for certification information distributed over a Castanet Channel
In contrast to other encryption technologies, there are no significant legal restrictions on code signing technology. This is because signing does not embed secret messages in the signed documents and because the patents that once covered public key cryptography have now expired.
[190] We’ll also assume that the algorithms used are strong, that the key is big enough and sufficiently random, and the overall software infrastructure was coded and protected properly. There are many more assumptions, but these should illustrate the point—at some level, you need to trust a lot of things that can go wrong. The reputation and competence of the parties involved help you gain confidence in the structure, or contribute to a lack of confidence.
[191] If public education fails, system software can always be modified so that unsigned programs cannot run.