IN THIS CHAPTER
This chapter examines password crackers and other programs designed to circumvent password security. Although password cracking is a core skill of most intruders, it is also important for system and network administrators to understand the ins and outs of password security. Comprehending where and why passwords can fail is paramount in maintaining enterprise security; many times, passwords are the first, and unfortunately only, line of defense. This chapter explains how passwords are stored, how they can be stolen, how they are cracked, and what you can do to minimize the risks associated with using passwords.
Passwords and “pass phrases” are used for everything ranging from logging into terminals, checking email accounts, and protecting Excel spreadsheets to securing the encryption keys for PKI-enabled enterprise networks. Their use in enterprise is widespread, to say the least.
Password crackers are programs that aid in the discovery of protected passwords, usually through some method of automated guessing. Although some applications and poorly designed infrastructure equipment will encrypt or encode passwords, most modern day operating systems and devices create a hash of the password instead. I will go into the differences between hashing and encrypting in the next section, but for now simply note that they are two different methods of storing password information.
Although some poor encryption mechanisms can be easily reversed, modern day hashing methods are one-way—that is, they cannot be reversed, and therefore decryption is not an option. Although the use of one-way algorithms can sound like a rock-solid solution, it simply makes the task at hand a little more time-consuming. To circumvent the challenges created by hashing, password crackers simply employ the same algorithm used to encrypt the original password. The tools perform comparative analysis (a process explained later in this chapter), and simply try to match their guesses with the original encrypted phrase or password hash.
Many password crackers are nothing but guessing engines—programs that try word after word, often at high speeds. These programs rely on the theory that eventually you will encounter the right word or phrase. This theory is sound, because humans are lazy creatures. They rarely take the trouble to create strong passwords. However, this shortcoming is not always the user’s fault:
Users are rarely, if ever, educated as to what are wise choices for passwords. If a password is in the dictionary, it is extremely vulnerable to being cracked, and users are simply not coached as to “safe” choices for passwords. Of those users who are so educated, many think that simply because their password is not in | ||
| --A Survey of, and Improvements to, Password Security.Daniel V. Klein, Software Engineering Institute,Carnegie-Mellon University, Pennsylvania.(PostScript creation date reported: February 22, 1991.) | ||
It should be noted, however, that the raw “It’s-not-in-the-dictionary” approach is now somewhat misleading as well. Password-cracking dictionaries now contain hundreds of thousands of popular names, characters, musical bands, slang, expletives, and an assortment of culturally popular terms that might or might not be in a classic dictionary. We’ll explore the depth and versatility of password guessing later on, but the new rule of thumb is to avoid any kind of word all together. For example, “808state” is easily guessed by most password crackers, not only because it’s based on a word (state) and a number (808), but also because it’s the name of a popular band out of Manchester, England. Stronger passwords can be created by using a combination of letters, numbers, and extended characters. Acronyms work wonderfully, for example, “I’m trying to learn information security techniques quickly!” could be translated to “IT2LISTQ!”. This is a MUCH harder password to guess, but is not all that difficult to remember.
The simple password problem is a persistent one, despite the fact that it is easy to provide password-security education. It’s puzzling how such a critical security issue (which can easily be addressed) is often overlooked. The issue goes to the very core of security:
TIP
One additional password pitfall that is frequently overlooked is the password overload scenario. If users have a multitude of passwords to remember, there is a greater chance that they will write them down, use weaker passwords, or introduce an assortment of other insecure password practices into your environment. This is where centralized authentication systems, directory services, and single-sign on solutions can help you. Not only do they reduce operating costs and complexity, they ultimately help you with your overall security posture.
The etymological root of the word cryptography is instructive. The word crypto stems from the Greek word kryptos. Kryptos describes anything that is hidden, obscured, veiled, secret, or mysterious. The word graph is derived from graphia, which means writing. Thus, cryptography is the art of secret writing. Yaman Akdeniz, in his paper Cryptography and Encryption, gives an excellent and concise definition of cryptography:
Cryptography, defined as “the science and study of secret writing,” concerns the ways in which communications and data can be encoded to prevent disclosure of their contents through eavesdropping or message interception, using codes, ciphers, and other methods, so that only certain people can see the real message. | ||
| --“Cryptography and Encryption.”Yaman Akdeniz. Cyber-Rights & Cyber-Liberties (UK), August 1996,at http://www.cyber-rights.org/crypto/cryptog.htm.Criminal Justice Studies of the Law Faculty of University of Leeds. | ||
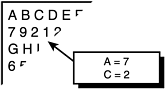
To illustrate the process of cryptography, I’ll reduce it to its most fundamental parts. Imagine that you’ve created your own code, in which each letter of the alphabet corresponds to a number (see Figure 14.1).
Figure 14.1 shows part of a table, or legend. Below each letter is a corresponding number. A = 7, B = 9, and so forth. This is a code of sorts. If you write a message using these rules, only you and the recipient will know what the message really says.
Unfortunately, such a code can be easily broken. For example, if each letter has a fixed numeric counterpart, you will only use 26 different numbers (perhaps 1 through 26, although you could choose arbitrary numbers). Lexical analysis would reveal your code within a few seconds. (Some software programs perform such analysis at high speed, searching for patterns common to your language.)
Another slightly more complex method is to make each letter become another letter, based on a standard incremental or decremental operation. One system that works this way is ROT-13 encoding. In ROT-13, a substitute letter is used. Moving 13 letters ahead (see Figure 14.2) in the chosen alphabet derives the substitute letter.
This, too, is an ineffective method of encoding or encrypting a message (although it worked in Roman times for Caesar, who used a shift-by-three formula). Some programs quickly identify this pattern. However, this doesn’t mean that techniques such as ROT-13 are useless. I will illustrate why, and in the process, I can demonstrate the first important point about encryption:
Any form of encryption can be useful, given particular circumstances. These circumstances might depend upon time, the sensitivity of the information, and from whom you want to hide data.
In other words, techniques such as ROT-13 can be quite useful under the right circumstances. Here’s an example: Suppose a cracker wants to post a new cracking technique to Usenet. He’s found a hole and wants to publicize it while it’s still exploitable. To prevent security specialists from discovering that hole as quickly as the crackers, the cracker uses ROT-13 to encode his message.
There are a number of organizations that download Usenet traffic on a wholesale basis. In this way, they gather information about the cracker community. Some organizations even use popular search engines to ferret out cracker techniques. These search engines employ regex (regular expression) searches (that is, they search by word or phrase). For example, the searching party enters a combination of words such as
crackhackvulnerabilityexploit
When this combination of words is entered correctly, a wealth of information emerges. However, if the cracker uses ROT-13, search engines will miss the post. For example, the message
Guvf zrffntr jnf rapbqrq va EBG-13 pbqvat. Obl, qvq vg ybbx fperjl hagvy jr haeniryrq vg!
is beyond the reach of the average search engine. What it really looks like is this:
This message was encoded in ROT-13 coding. Boy, did it look screwy until we unraveled it!
Most modern mail and newsreaders support ROT-13 encoding and decoding (Outlook Express by Microsoft is one; Netscape Communicator’s Mail package is another). Again, this is a rudimentary form of encoding something, but it demonstrates the concept. Now, let’s get a bit more specific.
Today, Internet information servers run many different operating systems. However, for many years, Unix was the only game in town. The greater number of password crackers were designed to crack Unix passwords. Let’s start with Unix, then, and work our way forward.
On most Unix systems, all user login IDs and passwords are centrally stored in either one of two files: the passwd file, usually found in the /etc directory, or a file called shadow, also located in the /etc directory. These files contain various fields. Of those, we are concerned with two: the login ID and the hashed password.
TIP
Using “shadow passwords” is the preferred way of storing password hashes. The /etc/shadow file is only accessible by the root account and system services, as opposed to /etc/passwd, which is readable by everyone. If you have any systems that are still storing password hashes in /etc/passwd, either upgrade them to shadow passwords, or remove them from your environment as soon as possible.
The login ID is stored in plain text, or human-readable English. The password is stored in encrypted form. The encryption process is performed using Crypt(3), a program based on the Data Encryption Standard (DES).
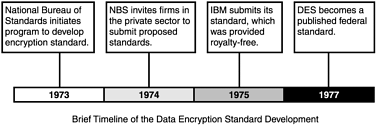
IBM developed the earliest version of DES; today, it is used on all Unix platforms for password encryption. DES is endorsed jointly by the National Bureau of Standards and the National Security Agency. In fact, since 1977, DES has been the generally accepted method for safeguarding sensitive data. Figure 14.3 contains a brief timeline of DES development.
DES was developed to protect certain nonclassified information that might exist in federal offices, as set forth in Federal Information Processing Standards Publication 74, Guidelines for Implementing and Using the NBS Data Encryption Standard:
Because of the unavailability of general cryptographic technology outside the national security arena, and because security provisions, including encryption, were needed in unclassified applications involving Federal Government computer systems, NBS initiated a computer security program in 1973 that included the development of a standard for computer data encryption. Because Federal standards impact on the private sector, NBS solicited the interest and cooperation of industry and user communities in this work.
Information about the original mechanical development of DES is scarce. Reportedly, at the National Security Agency’s request, IBM made certain documents classified. However, the source code for Crypt(3) (the current implementation of DES in Unix) is widely available. This is significant, because in all the years that source has been available for Crypt, no one has yet found a way to easily reverse-encode information encrypted with it.
There are several versions of Crypt, and they work slightly differently. In general, however, the process is as follows:
Your password is taken in plain text (or, in cryptographic jargon, clear text).
Your password is used as a key to encrypt a series of zeros (64 in all). The resulting encoded text is thereafter referred to as cipher text, the unreadable code that results after plain text is encrypted. This cipher text is sometimes referred to as a hash, as well, but the term only loosely fits in this case.
NOTE
One-way hash functions are frequently used as an alternative to actually encrypting passwords. By using hashing algorithms such as MD5 (Message Digest 5) or SHA-1 (Secure Hashing Algorithm 1), a digital footprint can be created of the password that doesn’t contain the actual password itself. This varies from the process of encryption because the output does not contain the original input in any form, and it is therefore impossible to derive the original input from the output. Many modern Unix systems are moving towards the use of MD5, SHA-1, or SSHA (Salted Secure Hashing Algorithm) hashes instead of relying on the crypt/DES process. If you are interested in one-way hashing techniques, or cryptography in general, Bruce Schneier’s Applied Cryptography (John Wiley & Sons, ISBN 0-471-12845-7) is a must-have.
Certain versions of Crypt, notably Crypt(3), take additional steps. For example, after going through this process, the encrypted text is again encrypted, numerous times, using the password as a key. This is a fairly strong method of encryption; it is extremely difficult to break. It is estimated, for example, that the same password can be encoded in 4,096 different ways. The average user, without any knowledge of the system, could probably spend her entire life trying to crack DES and never be successful. To get that in proper perspective, here’s an estimate from the National Institute of Standards and Technology:
The cryptographic algorithm [DES] transforms a 64-bit binary value into a unique 64-bit binary value based on a 56-bit variable. If the complete 64-bit input is used (i.e., none of the input bits should be predetermined from block to block) and if the 56-bit variable is randomly chosen, no technique other than trying all possible keys using known input and output for the DES will guarantee finding the chosen key. As there are more than 70,000,000,000,000,000 (seventy quadrillion) possible keys of 56 bits, the feasibility of deriving a particular key in this way is extremely unlikely in typical threat environments. | ||
| --“Data Encryption Standard (DES),”Federal Information Processing Standards Publication 46-2,NIST, December 30, 1993.http://csrc.nist.gov/fips/fips46-2.txt. | ||
One might think that DES is entirely infallible. It isn’t. Although the information cannot be reverse-encoded, passwords encrypted via DES can be revealed through a comparative process. The process works as follows:
You obtain a dictionary file, which is really no more than a flat file (plain text) list of words (commonly referred to as wordlists).
These words are encrypted using DES.
Each encrypted word is compared to the target password. If a match occurs, there is a 98% chance that the password was cracked.
The process itself is both simple and brainless, yet quite effective. However, password-cracking programs made for this purpose are often times a little more clever. For example, such cracking programs often subject each word to a list of rules.
NOTE
Because DES is a rather old algorithm and is limited by its 56-bit key, most people are of the opinion that is it at the end of its useful life. The first improvement to DES was Triple DES (3DES), which is three DES operations with three 56-bit keys. This leads to an effective key size of 168 bits.
3DES is partially just a stopgap, but is going to remain a government approved standard for a while. The U.S. government went through a selection process for their replacement for DES, which they are calling Advanced Encryption Standard (AES). The algorithm selected was originally called Rijndael. Provided no unexpected holes are found, Rijndael is trillions of times stronger than DES.
A rule could be anything, any manner in which a word might appear. Typical rules might include the following:
Alternate uppercase and lowercase lettering.
Spell the word forward and then backward and then fuse the two results (for example,
canbecomescannac).Add the number 1 to the beginning or end of each word.
Naturally, the more rules you apply, the longer the cracking process takes. However, more rules also guarantee a higher likelihood of success for a number of reasons:
The Unix file system is case sensitive (
WORKSTATIONis interpreted differently thanWorkstationorworkstationis).Alternating letters and numbers in passwords is a common practice.
Password crackers have had a tremendous impact on Internet security, chiefly because they are so effective:
Crypt uses the resistance of DES to known plain text attack and make [sic] it computationally unfeasible to determine the original password that produced a given encrypted password by exhaustive search. The only publicly known technique that can reveal certain passwords is password guessing: passing large wordlists through the crypt function to see whether any match the encrypted password entries in an /etc/passwd file. Our experience is that this type of attack is successful unless explicit steps are taken to thwart it. Generally we find 30 percent of the passwords on previously unsecured systems. | ||
| --UNIX Password Security—Ten Years Later.David Feldmeier and Philip R. Karn. (Bellcore) | ||
Password-cracking programs are improving in their effectiveness, too. The newer programs incorporate more extensive rules and diverse wordlists. Most wordlists are plain text files with one word per line. These files range in size from 1MB to more than 20MB. Many wordlists are available on the Internet; they come in a wide variety of languages (so an English-speaking American cracker can crack an Italian machine, and vice versa). In fact, the new password-cracking programs are so effective that one site with 5,000 users ran the L0phtcrack cracking program and had broken 90% of the users’ passwords within two hours.
TIP
There are several popular wordlist collections. Some are simply dictionaries, and others contain hyphenated words, uppercase and lowercase, and so on. One of the best sites for wordlists is http://www.cotse.com/tools/wordlists2.htm.
If you’re new to system administration, you’re probably wondering how you can benefit from password crackers. Password crackers can help you identify weak passwords on your network.
Ideally, you should run a password cracker once a month. If your network supports several platforms, you might need a wide range of password-cracking utilities. Although password crackers such as John the Ripper can crack both Windows NT-based password files and Unix-based ones, most password crackers are designed to crack only a single type of password.
To crack passwords, you need the following elements:
Sufficient hardware (a Pentium III-based machine will do nicely)
A password cracker (such as John the Ripper, Crack, L0phtCrack, and so on)
A password file (
/etc/shadow, the NT SAM file, and so on)
I discuss methods of grabbing password files (like the Unix shadow file, or the Windows NT SAM file) throughout this book, and we will examine the password-cracking programs themselves in the next section. On the hardware front, however, you need only really know one thing: More is better.
Cracking passwords is a CPU- and memory-intensive task. It can take seconds, minutes, days, weeks, months, or even years depending on the strength of the password and the algorithms used. To crack passwords effectively, you need suitable hardware. The more powerful the hardware, the faster you will be able to crack even relatively strong passwords.
For cracking common password files, like those found on Unix and Windows NT systems, I have found that to comfortably handle large password files, you should have the following resources:
A 400MHz Pentium II or better
64MB of RAM or better
A single-processor Pentium II-based system dedicated to password cracking can chew through most NT SAM (password) files in under 48 hours. Dual-processor, Pentium III-based systems will work even faster.
There are techniques, however, for overcoming hardware restrictions. One is the parlor trick of distributed cracking. In distributed cracking, you run the cracking program simultaneously on separate processors. There are a few ways to do this. One is to break the password file into pieces and crack those pieces on separate machines. In this way, the job is distributed among a series of workstations, thus cutting resource drain and the time it takes to crack the entire file.
The problem with distributed cracking is that it makes a lot of noise. Remember the Randal Schwartz case? Mr. Schwartz probably would never have been discovered if he were not distributing the CPU load. Another system administrator noticed the heavy processor power being eaten. (He also noted that one process had been running for more than a day.) Distributed cracking really isn’t viable for a cracker unless he is the administrator of a site or he has a network at home (which is not so unusual these days; I have a network at home that consists of Windows 95, Windows NT, Linux, Sun, and Novell boxes).
Most of the remainder of this chapter is devoted to individual password crackers. Some tools are made for cracking Unix passwd and shadow files, some are for cracking NT SAM files, and some work across applications and services you might not have even heard of. Some of the tools here are not even password crackers; instead, they are auxiliary utilities that can be used in conjunction with existing password-related tools.
Windows NT keeps password hashes in a protected portion of the Registry called the SAM. However, there are a number of ways to get these hashes. The easiest method is to use the rdisk command to create a backup of the SAM, and then copy that file to a password-cracking machine. rdisk /s- will create a compressed SAM image in the repair directory of the %systemroot% (usually c:winnt
epair).
Another trick is to sniff the password hashes off of the wire. L0phtCrack, for example, has this feature built in. Regardless of how you get the NT password hashes themselves, the following utilities can be used to aid your Windows NT-based cracking efforts.
L0phtCrack is the most celebrated NT password-cracking tool to date, primarily because it uses a two-prong approach, as explained by its authors:
Passwords are computed using 2 different methods. The first, a dictionary lookup, called dictionary-cracking, uses a user supplied dictionary file. The password hashes for all the words in the dictionary file are computed and compared against all the password hashes for the users. When there is a match the password is known. This method is extremely fast. Thousands of users can be checked with a 100,000-word dictionary file in just a few minutes on a PPro 200. The drawback to this method is that it only finds very simple passwords…. The second method is the brute-force computation. This method uses a particular character set such as A–Z or A–Z plus 0–9 and computes the hash for every possible password made up of those characters.
When L0phtCrack was released, it caused considerable debate, especially because the program’s authors pointed out that Microsoft’s password algorithm was “intrinsically flawed.” Microsoft officials hotly disputed that claim, but their efforts were for naught. L0phtCrack works very well, and it is now an accepted fact that Windows NT’s password-hashing techniques are flawed from a security standpoint.
To effectively use L0phtCrack, you need the password hashes.
LC4, the most recent version of L0phtCrack, is located at http://www.atstake.com/research/lc/.
John the Ripper is one of the most diverse password crackers in circulation today. John runs on both DOS and Windows platforms, as well as on most flavors of Unix. The binary distribution was released in December 1996, and the package has continued to be updated ever since.
John’s real strength lies in its diversity. John can crack Unix files natively and Windows NT SAM files with the use of Pwdump. Modules have been created to attack other platforms, such as LDAP and Kerberos as well. John can also perform true brute-forcing of password files—that is, password cracking going beyond basic dictionary-based guessing. It is extremely resource intensive, and has only become practical in recent years by the rapid advances in processing power.
Penetration testers and crackers alike love John because they can perform cross-platform password cracking on a single, centralized machine. John is maintained by Solar Designer, and its home page is http://www.openwall.com/john/.
If you are cracking SHA-based passwords on an LDAP server, a patch is available to make John the Ripper work with that as well. It is available at http://www.bastard.net/~dos/john-sha.
NTCrack is a curious utility. As its authors explain, it isn’t really intended for cracking passwords in a practical sense. However, it does demonstrate that a brute-force cracker can work against Windows NT. The program’s purpose is to perform high-speed, brute-force attacks against an NT box. As reported by the folks at Somarsoft, the original maintainers of the program:
The program below [NTCrack] does about 1000 logins per minute, when run on a client 486DX-33 with 16MB of RAM, a server 486DX2-66 with 32MB of RAM, and a 10 MBps Ethernet. This is equivalent to testing 1,152,000 passwords per day. By comparison, there are perhaps 100,000 common words in the English language.
To prevent such attacks, it is suggested that you enable account lockout, rename the Administrator account, disable network logins for Administrator, and disable SMB over TCP/IP (if appropriate). You can read more about passfilt and securing Windows NT servers in Chapter 20, “Microsoft.”
You can find NTCrack at http://www.wiretrip.net/na/NTCrack.zip.
The NT accessories listed in Table 14.1 are indispensable.
Table 14.1. Accessories for Use in Cracking NT Passwords
Application | Description and Location |
|---|---|
Samdump | Samdump is a utility that automates the process of dumping NT password hashes. It dumps these values from the SAM file located either in the Registry on an emergency repair disk or off the hard disk drive. Samdump is available at http://www.multimania.com/toopert/samdump.zip. |
Pwdump2 | Pwdump2 is similar to Samdump. It dumps NT usernames and passwords, and it can dump Active Directory as well. (Fortunately, Pwdump2 requires Administrator privileges.) Pwdump2 is available at http://razor.bindview.com/tools/desc/pwdump2_readme.html. |
NTFSDOS (Pro) | NTFSDOS and NTFSDOS Pro are tools that enable you to mount NTFS volumes and view them as though they were FAT32. You can use these tools to extract SAM password information from a NTFS drive. The older, free NTFSDOS is available at http://www.sysinternals.com/ntw2k/freeware/NTFSDOS.shtml. There is also a more advanced Professional version available at http://www.winternals.com/products/repairandrecovery/ntfsdospro.asp. |
Rather than simply use the utilities described here, you might want to investigate exactly what factors led to such poor password security in NT in the first place. The following documents are excellent resources:
A L0phtCrack Technical Rant. A detailed analysis (really, the gory details) of NT password weaknesses. Authored by [email protected]. http://packetstormsecurity.nl/Crackers/NT/l0phtcrack/l0phtcrack.rant.nt.passwd.txt
“On NT Password Security.” Jos Visser. An excellent paper that discusses both the mechanical and theoretical problems with the NT password scheme. The author also discusses how to perform an attack against Windows NT password dumps. http://ihide.virtualave.net/archive/pwsec.html
NT Cryptographic Password Attacks and Defences FAQ. Alan Ramsbottom. This document provides information on why certain Microsoft fixes didn’t work, as well as perspective on the weakness in Microsoft’s implementation of DES. http://www.ntbugtraq.com/default.asp?sid=1&pid=47&aid=17
This next section discusses the issues surrounding Unix password cracking. Most of these programs were designed for Unix as the hosting platform, but some of them will run on other platforms such as DOS and Windows 95. All of them are, however, designed to crack Unix passwords.
Unix password security, when implemented correctly, is fairly reliable. The main problem is that people continue to pick weak passwords. Unfortunately, because Unix is a multiuser system, every user with a weak password represents a risk to the remaining users. This is a problem that must be addressed:
It is of utmost importance that all users on a system choose a password that is not easy to guess. The security of each individual user is important to the security of the whole system. Users often have no idea how a multiuser system works and don’t realize that they, by choosing an easy-to-remember password, indirectly make it possible for an outsider to manipulate the entire system. | ||
| --“UNIX Password Security.” Walter Belgers. December 6, 1993. | ||
TIP
The paper “UNIX Password Security” gives an excellent overview of exactly how DES works into the Unix password scheme. It includes a schematic that shows the actual process of encryption using DES. For users new to security, this paper is an excellent starting point. You can find “UNIX Password Security” at http://www.het.brown.edu/guide/UNIX-password-security.txt.
What are weak passwords? Characteristically, they are anything that might occur in a dictionary. Moreover, proper names are poor choices for passwords. However, there is no need to theorize on what passwords are easily cracked. It’s safe to say that if the password appears in a password-cracking wordlist available on the Internet, the password is no good.
TIP
Start your search for wordlists at http://www.cotse.com/tools/wordlists2.htm.
By regularly checking the strength of the passwords on your network, you can ensure that crackers cannot penetrate it (at least not through exploiting bad password choices). Such a regimen can greatly improve your system security. In fact, many ISPs and other sites now employ tools that check a user’s password when it is first created. This basically implements the philosophy that
…the best solution to the problem of having easily guessed passwords on a system is to prevent them from getting on the system in the first place. If a program such as a password cracker reacts by guessing detectable passwords already in place, then although the security hole is found, the hole existed for as long as the program took to detect it…. If however, the program that changes users’ passwords…checks for the safety and guessability before that password is associated with the user’s account, then the security hole is never put in place. | ||
| --“Improving System Security Via Proactive Password Checking.”Matthew Bishop, UC Davis, California, and Daniel Klein, LoneWolf Systems Inc.Computers and Security [14, pp. 233–249], 1995. | ||
TIP
The paper “Improving System Security Via Proactive Password Checking” is probably one of the best case studies and treatments of easily guessable passwords. It treats the subject in depth, illustrating real-life examples of various passwords that you might think are secure but actually are not. You can find “Improving System Security Via Proactive Password Checking” at http://seclab.cs.ucdavis.edu/papers/bk95.ps.
Crack is the de facto standard for Unix password cracking. It was written by Alec D. E. Muffett, a Unix software engineer in Wales. In the documentation, Muffett concisely articulated the program’s purpose:
Crack is a freely available program designed to find standard Unix eight-character DES encrypted passwords by standard guessing techniques…. It is written to be flexible, configurable and fast, and to be able to make use of several networked hosts via the Berkeley rsh program (or similar), where possible.
Crack runs on Unix only. It comes as a tarred, gzipped file, and is available at http://www.users.dircon.co.uk/~crypto/.
To get Crack up and running, set the root directory. You assign this variable (Crack_Home) in the configuration files. The Crack_Home variable tells the Crack program where Crack’s resources reside. To set this variable, edit the shell script Crack. After you do that, you can begin.
NOTE
Most distributions of Crack are accompanied by a sample wordlist. However, that wordlist is limited. If you anticipate cracking large password files (or files in other languages), you will probably need additional dictionary files.
You begin your Crack session by starting the program and providing the name of the file to crack (as well as any command-line arguments, including specifications for using multiple workstations). A bare command line looks like this:
Crack my_password_file
What follows is difficult to describe, so I ran a sample Crack session. Crack started the process and wrote the progress of the operation to files with an out prefix. In this case, the file was called outSamsHack300. The following is an excerpt from that file:
1: pwc: Jan 30 19:26:49 Crack v4.1f: The Password Cracker, (c) Alec D.E. Muffett, 1992 2: pwc: Jan 30 19:26:49 Loading Data, host=SamsHack pid=300 3: pwc: Jan 30 19:26:49 Loaded 2 password entries with 2 different (salts: 100% 4: pwc: Jan 30 19:26:49 Loaded 240 rules from 'Scripts/dicts.rules'. 5: pwc: Jan 30 19:26:49 Loaded 74 rules from 'Scripts/gecos.rules'. 6: pwc: Jan 30 19:26:49 Starting pass 1 - password information 7: pwc: Jan 30 19:26:49 FeedBack: 0 users done, 2 users left to crack. 8: pwc: Jan 30 19:26:49 Starting pass 2 - dictionary words 9: pwc: Jan 30 19:26:49 Applying rule '!?Al' to file 'Dicts/bigdict' 10: pwc: Jan 30 19:26:50 Rejected 12492 words on loading, 89160 words (left to sort 11: pwc: Jan 30 19:26:51 Sort discarded 947 words; FINAL DICTIONARY .(SIZE: 88213 12: pwc: Jan 30 19:27:41 Guessed ROOT PASSWORD root (/bin/bash (in my_password_file) [laura] EYFu7c842Bcus 13: pwc: Jan 30 19:27:41 Closing feedback file.
Crack guessed the correct password for root in just under a minute. Line 1 reveals the time at which the process was initiated (Jan 30 19:26:49); line 12 reveals that the password—Laura—was cracked at 19:27:41. This session occurred on a 133MHz processor with 32MB of RAM.
Because the password file I used was small, neither time nor resources were an issue. In practice, however, if you crack a file with hundreds of entries, Crack will eat resources voraciously. This hunger is especially evident if you use multiple wordlists that are in compressed form. (Crack automatically identifies them as compressed files and decompresses them.)
As mentioned earlier, you can get around this resource drain. Crack can distribute the work to different workstations of different architectures. You can use Crack on an IBM compatible running Linux, a RS/6000 running AIX, and a Macintosh running A/UX.
Crack is extremely lightweight and one of the best password crackers available.
TIP
To perform a networked cracking session, you must build a network.conf file. This file identifies which hosts to include, their architecture, and several other key variables. You can also specify what command-line options are invoked as Crack is unleashed on each machine. In other words, each member machine can run Crack with different command-line options.
John was discussed in the NT section, so I will only briefly touch on it here. Although John can crack both NT- and Unix-based passwords, the one thing that is unique about John on the Unix side of the fence is its capability to do raw brute-forcing. Performing a raw brute-force attack (trying every possible combination of characters) was impractical on hardware of a few years ago, but is a reality today. If you want to get medieval on a Unix password file, John is the tool for you.
PaceCrack95 ([email protected])
PaceCrack95 runs on Windows 95 in console mode or in a shell window. Its author reports that the development of PaceCrack95 was prompted by deficiencies in other DOS-based crackers. He writes
Well you might be wondering why I have written a program like this when there already is[sic] many out there that do the same thing. There are many reasons, I wanted to challenge myself and this was a useful way to do it. Also there was this guy (Borris) that kept bugging me to make this for him because Cracker Jack (By Jackal) doesn’t run in Win95/NT because of the weird way it uses the memory. What was needed was a program that runs in Win95 and the speed of the cracking was up there with Cracker Jack.
To the author’s credit, he created a program that does just that. It is fast, compact, and efficient.
You can find PaceCrack95 at http://www.securityadvise.de/deny/files/BruteForce/pacecrack.zip.
Star Cracker, which was designed to work under the DOS4GW environment, is a complete password-cracking suite. Some of its more interesting advantages are
A fail-safe power outage provision—. If a blackout in your city shuts down your computer, your work is not lost. Upon reboot, Star Cracker recovers all work previously done (up until the point of the power outage) and keeps right on going.
Time-release operation—. You can establish time windows when the program does its work. That means you could specify, “Crack this file for 11 hours. When the 11 hours are up, wait 3 hours more. After the 3 hours, start again.”
Star Cracker really makes the password-cracking process painless.
You can find Star Cracker at http://www.kontek.net/pi/pass_crack/sc10b1.zip.
Although you can certainly use password crackers for devious activities, there are plenty of legitimate reasons for needing to access data that might be password protected. For example, if an employee forgets the password to a protected-access database, or if someone leaves the company without passing on the pass phrase for a zip file, an organization might have legitimate needs to get at that data.
The following section goes over some of the password crackers for less common (not OS-related) applications. I encourage the reader to note the diverse assortment of password crackers listed. Hopefully this list will help dispel the myth that application-level passwords are inherently secure. The truth of the matter is that rarely do application vendors create secure password-protection mechanisms—most are easily broken.
Cisco stores encrypted login, username, and “enable” passwords in standard IOS configuration files. If these configuration files are not protected, they can be run through decryption scripts that will reveal the passwords in clear text. We will talk more about securing Cisco equipment in Chapter 23, “Routers, Switches and Hubs,” but, for now, know that protecting your configuration files is extremely important.
Many scripts exist for decrypting standard Cisco passwords. One such script can be found at http://www.alcrypto.co.uk/cisco/perl/ios7decrypt.pl. GetPass is a Windows-based program that does the same thing, and it can be found at http://www.boson.com/promo/utilities/getpass/getpass_utility.htm.
TIP
A neat tool for auditing Cisco router configuration files can be found at http://packetstormsecurity.nl/cisco/CiscoAuditingTool-v1.tar.gz. Cisco administrators would be wise to check this one out.
There are a number of companies that provide commercial password-cracking services and tools. A couple of the fairly well-known ones are
PWD Service, Inc. http://www.pwdservice.com
Password Crackers, Inc. http://www.pwcrack.com
Here is just a sample list of some of the applications these organizations offer password-cracking software for:
Microsoft Word
Microsoft Excel
Microsoft Access
Microsoft Outlook
Microsoft Project
Microsoft Backup
Microsoft Money
Lotus 1-2-3
Lotus Word Pro
Quickbooks
ACT
Paradox
M.Y.O.B
Quicken
Peachtree Accounting
PKZIP
WordPerfect
It’s important to note that many of these password crackers do their cracking in less than a few seconds. Although I am not a password or cryptography expert, I think it’s safe to draw the conclusion that most application-based password protection schemes are little more than an annoyance for intruders. If you can crack them with a $30 piece of software in a few seconds, realize that anyone else can, too.
ZipCrack does just what you think it would: It is designed to brute-force crack passwords that have been applied to files with a *.zip extension. (In other words, it cracks the password on files generated with PKZIP.)
No documentation is included in the distribution (at least, not the few files that I have examined), but I am not sure there is any need for documentation. The program is straightforward. You simply provide the target file, and the program does the rest.
The program was written in Turbo Pascal, and the source code is included with the distribution. ZipCrack works on any IBM compatible that is a 286 or higher. The file description reports that ZipCrack cracks all the passwords generated by PKZIP 2.0. The author also warns that, although you can crack short passwords within a reasonable length of time, long passwords can take “centuries.” Nevertheless, I sincerely doubt that many individuals provide passwords longer than five characters. ZipCrack is a useful utility for the average toolbox. It’s one of those utilities you think you will never need, and later, at 3:00 in the morning, you swear bitterly because you don’t have it.
ZipCrack can be found at http://packetstormsecurity.org/crypt/msdos/ZIPCRACK.ZIP.
AMI Decode is designed expressly to grab the CMOS password from any machine using an American Megatrends BIOS. Before you search for this utility, however, you might use the factory default CMOS password. It is, oddly enough, AMI. In any event, the program works, and that is what counts.
AMI Decode can be found at http://packetstormsecurity.org/Crackers/bios/amidecod.zip.
NOTE
Many BIOS chips have backdoor passwords built into them. One list of these passwords can be found at http://www.freelabs.com/~whitis/security/backdoor.html.
Before readers who use PGP get all worked up about PGPCrack, a bit of background information is in order. Pretty Good Privacy (PGP) is one of the strongest and most reliable encryption utility available to the public sector. Its author, Phil Zimmermann, summed it up as follows:
PGP uses public-key encryption to protect email and data files. Communicate securely with people you’ve never met, with no secure channels needed for prior exchange of keys. PGP is well featured and fast, with sophisticated key management, digital signatures, data compression, and good ergonomic design.
PGP can apply a series of encryption techniques. One of these, which is discussed in Chapter 15, “Sniffers,” is IDEA. To hint about how difficult IDEA is to crack, here is an excerpt from the PGP Attack FAQ, authored by Route (an authority on encryption and the editor of Phrack magazine):
If you had 1,000,000,000 machines that could try 1,000,000,000 keys/sec, it would still take all these machines longer than the universe as we know it has existed and then some, to find the key. IDEA, as far as present technology is concerned, is not vulnerable to brute-force attack, pure and simple.
In essence, a message encrypted using a 1,024-bit key generated with a healthy and long pass phrase is, for all purposes, unbreakable. Why did Mr. Miller author this interesting tool? Pass phrases can be poorly chosen, and if you are going to crack a PGP-encrypted message, the pass phrase is a good place to start. Miller reports
On a 486/66DX, I found that it takes about seven seconds to read in a 1.2 megabyte passphrase file and try to decrypt the file using every passphrase. Considering the fact that the NSA, other government agencies, and large corporations have an incredible amount of computing power, the benefit of using a large, random passphrase is quite obvious.
Is this utility of any use? It is quite promising. Miller includes the source with the distribution as well as a file of possible pass phrases. (I have found that at least one of those pass phrases is one I have used.) The program is written in C and runs in DOS, Unix, and OS/2 environments.
You can find PGPCrack at http://packetstormsecurity.org/crypt/pgp/pgpcrack99.tgz.
All is not hopeless in the fight against crackers breaking your passwords. First, you should develop a strong password policy. This is discussed in Chapter 25, “Policies, Procedures, and Enforcement.” This should give your users some guidance in picking a good password.
As was mentioned earlier, you can run these password cracker programs periodically against your site. However, this is quite a bit of work and requires you to block accounts when the passwords are cracked. A class of products now exist that automatically enforce your password policy by not allowing users to enter bad passwords to begin with.
The way these programs work is by screening the user’s password when she tries to change it. The program has a set of rules that the password must match. If the password does not match these guidelines, the password change request fails, and the user is told why.
Windows NT has a DLL called passfilt.dll from Microsoft that can be installed. The rules it enforces are very minimal. They stipulate that the password must be at least six characters in length, a mix of different types of characters must be used, and passwords can’t match part of your username or full name. More information can be found at http://support.microsoft.com/default.aspx?scid=KB;EN-US;Q161990&.
In Windows 2000, passfilt.dll is built in. To enable it, you have to run the appropriate management tools, such as Local Security Policy, Domain Security Policy, or Domain Controller Security Policy. Within these programs, you will find the available settings in Security Settings, Account Policies, Password Policy.
If you are a programmer, it’s possible to write your own version of passfilt.dll and install it on the system. However, care should be taken when doing so.
passfilt.dll is pretty weak, so it is not surprising to find companies out there offering improved replacements. Passfilt Pro is a commercial upgraded version of passfilt.dll. Passfilt Pro adds about a dozen more rules, and a check against a dictionary as well. More information is available at http://www.altusnet.com/passfilt/overview.htm.
Remember the administrator we discussed earlier that could break 90% of his users’ passwords in two hours? He installed the Password Bouncer product from Avatier. After installing it with a minimal product configuration and making his users change their password, he ran l0phtCrack again. This time it took three days to crack 12% of his passwords. With even more configuration, it might be possible to improve those numbers.
Password Bouncer is similar to Passfilt Pro, except that it has even more features and rules that can be set within the product, allowing the user even more control over the password policy. Finally, Password Bouncer can be integrated into Avatier’s other management products, Trusted Enterprise Manager and PasswordStation.Net. Password Bouncer can be found at http://www.passwordbouncer.com.
Each of the major Unix versions has some type of password policy system built into them. HP-UX, Linux, and Solaris are all very similar. They each have a couple of configuration files that control the password policy rules. For example, on Solaris, these are /etc/shadow and /etc/default/passwd. They all use PAM (Pluggable Authentication Modules), which provide hooks for administrators and programmers into the password system so they can greatly customize password policy.
AIX has a very advanced password policy system, but does not use PAM. It has the most rules of any OS system, and it also has a documented API for programming additional rules.
This section contains a list of sources for further education. Some of these documents are not available on the Internet. However, you can obtain some articles through various online services (perhaps Uncover), or at your local library through interlibrary loan or microfiche. You might have to search more aggressively for some of these papers, perhaps using the Library of Congress (http://www.loc.gov), or perhaps an even more effective tool such as WorldCat (http://www.oclc.org).
NOTE
Many of the files for papers have .ps extensions. This signifies a PostScript file. PostScript is a language and method of preparing documents. It was created by Adobe, the makers of Acrobat and Photoshop.
To read a PostScript file, you need a viewer. One good viewer is Ghostscript, which is shareware available at http://www.cs.wisc.edu/~ghost/.
Another good package (and a little more lightweight) is a utility called Rops. Rops is available for Windows, and is located at http://www.rops.org/.
TIP
You can find the Department of Defense Password Management Guideline at http://www.alw.nih.gov/Security/FIRST/papers/password/dodpwman.txt.
Password crackers provide a valuable service to system administrators by alerting them of weak passwords on the network. The problem is not that password crackers exist; the problem is that they aren’t used frequently enough by the good guys. Administrators should take the time to build password cracking into their monthly routines. By doing so, they can proactively pursue any weaknesses in their enterprise that result from weak passwords. However, administrators should also take care to ensure that both the raw password files and the results of their cracking efforts be deleted after their cracking sessions. Leftover password files can create issues that are worse than bad passwords themselves.
Finally, although the days of passwords serving as a primary means of authentication might be numbered, their overall use is not. Pass phrases will be used for some time to come for protecting keys, certificates, and a varying assortment of protected data. The technology might become more complex, but the solution to the surrounding problems will not. Education is key—use it.