Key concepts in this chapter are:
Using hash digests for storing and verifying passwords
Using private key encryption
Writing a public key encryption routine
Modifying a database to store passwords and bank account numbers in encrypted format
Protecting password fields on forms
Knowing where to use encryption in your own applications
If you read the Introduction, you’ll recall that this book is for Visual Basic .NET programmers new to security, not security experts new to Visual Basic .NET. This book unashamedly simplifies concepts and leaves out unnecessary techno-babble with the goal of making security easier to understand and implement—without sacrificing accuracy. For many programmers, this simplified look at security is all they will ever need, whereas others, after given a taste of security, will want to know more. In a nutshell, this book is not the last word in security; instead, it is the first book you should read on the subject.
What is encryption? Before discussing how to implement encryption with Visual Basic .NET, you need to have an understanding of encryption in general. Encryption is about keeping secrets safe by scrambling messages to make them illegible. In encryption terms, the original message is known as plain text, the scrambled message is called cipher text, the process of turning plain text into cipher text is called encryption, and the process of turning cipher text back into plain text is called decryption.
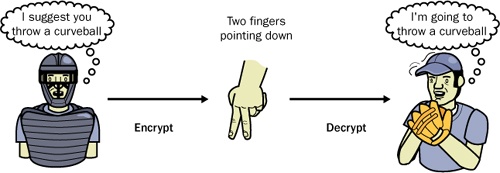
Encryption isn’t just used in cyberspace or in mysterious government work either. You can find examples of it in everyday activities such as baseball. For example, in the game of baseball, the catcher commonly uses hand signals to suggest to the pitcher the type of ball the pitcher should throw next. Curveballs, sinkers, sliders, and fastballs all have a different hand signal. As long as the batter and others on the opposing team don’t understand the catcher’s hand signals, their secret is safe. Figure 1-1 shows the process of encryption as it applies to baseball.
Computers allow us to encrypt rich messages in real time, but the underlying principle is the same as in the simple baseball example. For encryption to be effective, the sender and the recipient must be the only parties who know how to encrypt and decrypt the messages. Microsoft Windows and the .NET Framework provide robust algorithms for doing encryption, and we’ll use these routines in this chapter. Unless you’re an encryption expert, you shouldn’t try to write your own encryption algorithm, for exactly the same reason that only aviation engineers should build their own airplanes.
It’s a common misconception that encryption algorithms and hash functions must be secret to be secure. The encryption algorithms and hash functions used in this book are commonly understood, and the associated source code is distributed freely on the Internet. They are, however, still secure because they are designed to be irreversible (in the case of hash functions) or they require the user to supply a secret key (in the case of encryption algorithms). As long as only the authorized parties know the secret key, the encrypted message is safe from intruders. Encryption helps to ensure three things:
Some cryptography mechanisms are one way; that is, they produce cipher text that can’t be decrypted. A good example of a one-way cryptography is a hash. A hash is a very large number (the hashes in this chapter are 160 bits in size) mathematically generated from a plain-text message. Because the hash contains no information about the original message, the original message can’t be derived from the hash. "What use is cipher text that can’t be decrypted?" you might ask. As you’ll see soon, a hash is useful for verifying that someone knows a secret without actually storing the secret.
In the examples in this chapter, you’ll learn how to create and use a hash for verifying passwords. You’ll also learn how to use private key encryption for storing and retrieving information in a database. We’ll also begin building a library of easy-to-use encryption functions that you can reuse in your Visual Basic programs.
If you haven’t already installed the practice files, which you can download from the book’s Web site at http://www.microsoft.com/mspress/books/6432.asp, now would be a good time to do so. If you accept the default installation location, the samples will be installed to the folder C:Microsoft PressVBNETSec, although you’ll be given an opportunity to change the destination folder during the installation process. The practice files are organized by version of Microsoft Visual Basic, chapter, and exercise. The practice files for each chapter give a starting point for the exercises in that chapter. Many chapters also have a finished version of the practice files so that you can see the results of the exercise without actually performing the steps. To locate the practice file for a particular exercise, look for the name of the exercise within the chapter folder. For example, the Visual Basic .NET 2003 versions of the practice files for the following section on using hash digests for encrypting database fields will be in the folder
C:Microsoft PressVBNETSECVB.NET 2003CH01_Encryption EncryptDatabaseFieldStart
In many of the exercises in this book, you’ll modify an employee management system, adding security features to make the program more secure. The employee management system is a sample program that adds, edits, and removes employees for a fictional company. For background on the employee management system, see Appendix A. The system uses a Microsoft Access database named EmployeeDatabase.mdb. The techniques you learn are equally relevant to Microsoft SQL Server, Oracle, DB2, and other databases. You don’t need Microsoft Access to use the practice files because the database drivers are installed with Microsoft Visual Studio .NET. In some exercises, we modify the database structure. These exercises are optional. If you don’t have Microsoft Access installed, don’t worry: the practice files have been designed to work with the database whether or not you make the changes to the database structure.