Rules for Actions and Constraints
Abstract
Rules provide a form of expression of business requirements abstracted from actual business operations. Rules specify where certain actions or restrictions are required. The chapter begins with discussion of the various forms and applications of rules including rule-based inferencing, regulations, and policies. It concludes with discussion of the administration of the implementation of policies and rules.
Keywords
Business rules; Business constraints; Business policies; Regulations; Rule-based inferencing; Regulation administration; Policy administration
Rules are concise expressions of what must be true or when an action must occur. Rules express business requirements that reflect knowledge of the business and the business environment. Constraints specify what is possible, such as possible entries on a form. Rules with actions can drive business operations such as ordering parts when the inventory is low. Some rules enforce the integrity of business models and data. Some rules represent knowledge for decision-making, analysis, or planning. Some rules are used to express high-level business requirements for competitive advantage, governance, or regulatory compliance.
What makes rules important is that they enable a business person to express a restriction, inference, or circumstances for action but without the need to understand when the rule should be applied nor the technical details required to apply the rule. Essentially rules support a focus on what is required, not how it is to be implemented. If implemented appropriately, rules can also be a mechanism for quickly understanding and implementing business changes—agility. This makes rules a critical aspect for defining requirements for the design of the business and the information systems that support it.
Before computers, all business rules were applied by humans. Today, there are still some business rules that must be applied in human activities, including rules that are informally applied by experts to solve problems or provide advice.
Today, information systems are pervasive, so it is likely that many business rules are, or can be, implemented by information systems. In this book, we are particularly concerned with exploiting information technology for the application of rules because rules in automated systems are more efficient and reliable than those applied manually. Knowledge workers will continue to apply their experience and knowledge that may involve “rules,” but those rules are applied with insights on when and how the rules are relevant to diverse circumstances.
Unfortunately, many business rules are currently embedded in application programs. When there are relevant changes to business operations, programmers must search program code to identify decisions that embody the current business rules. This can be expensive, time consuming, and subject to errors. There are application modernization tools available for mining business rules from legacy applications, but this still requires human analysis to distinguish business rules from less significant program logic. Even when these decisions are implemented in automated business processes, they may be overlooked when a change is required.
It is important for enterprise agility as well as good governance that business rules are implemented explicitly in information systems, so there is visibility and traceability from the business requirement to the realization of that requirement in the operation of the business. Computer-based tools for management of rules will (1) improve reliability of application, (2) improve the ability to change rules, and (3) improve governance—assurance the enterprise is doing the right things and doing them well.
In this chapter, we will first consider an overview of rules technology: the forms in which rules are expressed, rules in knowledge-based systems, and inferred rules in machine learning. We will then examine example business applications. Finally, we will consider how rules can be managed for effective enterprise governance and agility.
Forms of Rules
Rules are logical expressions that may occur in different forms. A rule expression may refer to specific things or their attributes or relationships, or the rule may be expressed with symbolic variables that are assigned specific references when the rule is evaluated. So we could have a logical expression that John is married to Judy, or we could parameterize the expression as ?X is married to ?Y. The latter expression could be applied to an appropriate database to identify all married couples. The following are typical forms of rules.
• Constraint. A constraint expresses a logical relationship that must be true. So a constraint might express that an employee birth date must be in the past, or that a new order cannot be accepted from a customer if the customer's outstanding balance due would exceed the customer's credit limit.
• Logical inference. A logical inference expresses a fact or conclusion that is true if a condition expression is true. So we might express that if a car has a dead battery, or it is out of gasoline, or it is flooded, then it won’t start. We can characterize this form as “then-if.” We might instead express it as “if-then” as a car won’t start if it has a dead battery, or it is out of gasoline, or it is flooded. This form is useful in diagnosis. Of course this example suggests our limited knowledge of reasons a car won’t start. Logical inference rules are used in backward-chaining knowledge-based systems, discussed below.
• Condition-action. A condition-action rule is similar to the then-if logical inference. If the condition is true, then the rule specifies an action that should occur, for example, if car will not start and it is out of gasoline, then put gasoline in it. This rule is likely to be context dependent since you don’t always want to put gasoline in a car that is out of gasoline. Condition-action or “production” rules are applied in forward-chaining knowledge-based systems discussed below.
• Event-condition-action. An event-condition-action (ECA) rule is a refinement of the condition action rule that expresses the context in which the rule is to be evaluated. So the event might be that the car has stalled then the condition is evaluated and the action is performed under appropriate circumstances.
• Pattern recognition. Pattern recognition is the computer application of complex conditions typically developed by machine learning techniques to recognize data patterns of interest. A computer system processes examples of situations that do or don’t represent patterns of interest to develop the pattern recognition capability (effectively the rules). The representations of conditions are generally not meaningful to humans, and it is generally not possible to identify the specific reasons a pattern is recognized or rejected.
Knowledge-Based Systems
Knowledge-based systems provide solutions based on the interactions of multiple rules. The rules represent knowledge learned from experts. Individual rules will be relatively understandable, but technical expertise is required to achieve the necessary structure and relationships of the rules for the knowledge-based system to function properly. While the decisions realized with knowledge-based systems are based on clearly defined rules, the results may not be so obvious.
There are two basic forms of knowledge-based systems; backward chaining, or logic programming systems and forward chaining or production systems. Both forms involve reasoning with rules, but they solve different types of problems and apply rules in quite different ways.
Backward Chaining, Logic Programming Rules
Backward chaining starts with an assertion that is true if an associated condition is true. Prolog is a well-known language for backward chaining or “logic programming.” The condition may be evaluated by evaluating the truth of each element. The truth of each element, in turn, may be based on other conditions. Backward chaining is often used for diagnosis.
We might think of the basic form of a logic programming rule as then-if. For example, the “result” might be, “the car won’t start.” We then look for potential reasons—in other words, things that, if true, would cause the car to not start. So, in a rather informal form, the rules might look something like this:
Car-wont-start(?) <= Battery-dead(?) or Flooded(?) or Out-of-gasoline(?) Battery-dead(?) <= Lights-dont-go-on(?) Flooded(?) <= Smell-gasoline(?) Out-of-gasoline(?) <= Fuel-gauge-shows-empty(?)
Here the question mark (?) represents a reference to the particular vehicle under consideration. More complex rules might reference additional relevant entities or values.
If implemented as Prolog statements, the execution would start with the first rule, where we are interested in finding a potential reason that Car-wont-start could be true. In order for Car-wont-start to be true, one of the subsequent statements must be true, that is, Battery-dead or …If we consider Battery-dead, we see that the next rule evaluates Battery-dead. If Lights-dont-go-on is true, then Battery-dead is true and the cause of Car-wont-start is found. If Lights-dont-go-on is false, then Battery-dead is false and we return to the first rule (we “backtrack”) to examine the next possibility: Flooded. The nesting of rules can be very complex. The ordering and structure of the rules determines the order in which questions are asked. For example, if Lights-dont-go-on is true, we have completed the search and we need not ask about Smell-gasoline or Fuel-gauge-shows-empty.
Note that when one path of the search fails, the search returns up the search tree to explore an alternative path. This is commonly called backtracking and enables the exploration of alternative solutions. Some problems may have multiple possible solutions that can be identified and considered. Such alternatives might have different levels of risk or probabilities of success as in a medical diagnosis and treatment. The risks might be computed from multiple factors involved in a suggested action.
The example is quite trivial; it fails to demonstrate many capabilities of Prolog, it does not cover all possible causes of nonstarting car, and the result is fairly obvious. Much more complex problems can be addressed; among the most sophisticated is mathematical theorem proving.
Logic programming is important for implementing complex searches such as in diagnoses or identification of omissions and inconsistencies in models. The programmer can focus attention on defining the rules and does not need to deal with the mechanics of backward chaining and backtracking. Nevertheless, logic programming does require special skills and attention to the order in which statements are executed.
Forward Chaining, Production Rules
Forward chaining involves an alternative form of reasoning with rules, often called “production rules.” A production rule is triggered when its condition is met in a model of the problem domain—the model is often called the “working storage.” When a rule “fires” its action will update working storage causing other rules to fire. The actions of a sequence of rule executions produces (ie, production of) a working storage that is a solution to the problem.
Production rules are applied by a rules engine, as depicted in Fig. 5.1. A rules engine is a software product that applies rules to a problem. Generally, the rules reside in the runtime environment and, on request, the data representing a problem to be evaluated is loaded into the rules engine working storage. A Rete network (pronounced ree-tee) is created to link the rules to the working storage for efficient processing. The rules engine determines whether any of the rule conditions are met. If the conditions of more than one rule are met, the rules engine has logic to decide which rule to “fire” (ie, execute). When a rule fires, its action is performed. This action likely changes the data in working storage that defines a new, current situation; it may also cause some external effect. When the data change, the conditions of a different subset of the rules may be met, and the rules engine again selects a rule to fire.
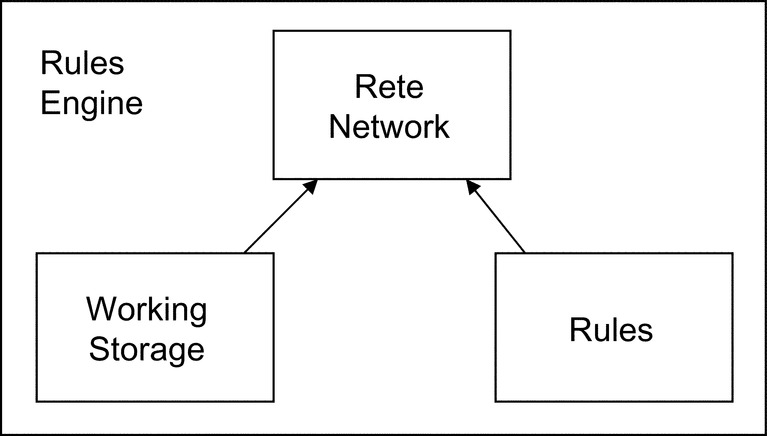
This general class of rules processing is called forward chaining because the action of each fired rule updates the working storage model and affects the selection of the next rule and subsequent chain of actions. The generally accepted mechanism for evaluating, selecting, and firing rules is the Rete algorithm.
Note that rules engines that implement production rules (forward chaining) also usually include backward-chaining capabilities where an evaluation of a condition requires examination of other conditions on which it depends.
The application of production rules does not include backtracking to explore alternative sequences of rule firings. Backtracking would require the engine to determine the point in the search where an alternative rule should be fired and the changes to working storage that would need to be withdrawn to pursue the alternative path. The Rete network links to working storage would further complicate the backtracking.
Production rules are used to produce a complex configuration or a plan such as a process or project or configuration.
Machine Learning
Cognitive computing is a recently popular phase for a collection of techniques for pattern recognition that mimics human cognition and learning. Recent advances emerged from work by IBM to develop a computer system that simulates human brain function. The laboratory implementation demonstrated a new computing paradigm. The vision is for a computer to provide the functionality of an intelligent robot—the ability to hear, see, and learn from receiving data in a variety of forms from multiple sources. Learned patterns and relationships are applied to analyze a new situation, reason about the situation and initiate or recommend appropriate actions. The expectation is to respond to complex, incomplete information, to draw conclusions or make suggestions based on experience—like a human advisor.
The vision is not yet a practical solution to current business problems, but cognitive computing has become a new industry buzzword. There are various definitions and characteristics attributed to cognitive computing. Some are focused on the vision and others are more practical. Here we will focus on systems that combine machine learning and the application of that knowledge. These techniques do not apply rules, per se, but they represent another approach to recognizing important circumstances and inferring results.
Neural networks are an early type of cognitive computing where the computer mimics the responses of neurons to various stimuli. Many examples of relevant circumstances are fed to the neural network, along with an expert's determination of the proper conclusion for each circumstance. The neural network learns to examine a situation and identify the proper conclusion.
Other cognitive computing techniques are being applied in analytic processes for identification of important patterns in natural language documents and “big data” collected from such sources as sensors, surveys, retail customer purchases, and web clicks.
Cognitive computing can provide valuable insights. However, cognitive computing systems must learn from substantial samples that are properly identified and cognitive computing results, generally, cannot be explained. At the same time, pattern recognition can be updated as circumstances change when it would take much longer for humans to define rules—assuming there is sufficient knowledge to identify the patterns of interest.
On the other hand, inferencing with rules may provide solutions for circumstances where there are few if any examples, and conclusions from forward and backward chaining can be explained by examination of the specific combination of rules that derived the result.
Developments in cognitive computing merit continuing attention.
Applications of Rules
While the previous section includes some examples of different types of rules, this section focuses on various aspects of business design where rules should be applied. The following sections describe the application of rules under the following topics:
• Event filter
• Process flow control
• Process planning
• Selection
• Product design
• Governance
Data and Model Integrity Rules
Data integrity rules are first incorporated in data models and the design of databases. These rules may also be called business rules by developers of data models and designers of databases. They are constraints that exist in the real world. For example, a person cannot have a birth date in the future, and two people cannot have the same tax ID number. These rules do not change, and violation of these rules would indicate that the integrity of the associated database has been compromised.
Certain constraints are intrinsic to business concepts. For example, an organization unit cannot directly or indirectly report to itself, or a customer order must have at least one order item. These constraints ensure the validity of data when they are applied to data being entered by a person or received from another system.
Integrity rules may be considerably more complex. These rules may be defined in models and implemented in the computer applications. For example,
• In computer-assisted design models, a surface must have closed edges or the model is intrinsically invalid.
• In product specifications, for certain parts, there must not be more than one part number for the same application; for example, the conditions for use of different air conditioning compressors on a vehicle must be mutually exclusive.
• For process design, an iteration must have a termination condition.
• For an organization, a reporting relationship must not be circular.
• For a Value Delivery Modeling Language (VDML) model, the organization unit, management reporting relationships must not be circular (management hierarchy).
These constraints are defined to ensure the integrity of the model and are not dependent on the industry or the particular enterprise.
Some constraints are required to ensure data integrity from a business perspective. For example, a purchase order must be submitted or approved by a person with that level of financial authority. In this case, when a purchase order is entered, the rule will require an authorization that may direct a request, recursively, up the management chain until a person with sufficient authority is reached.
Data constraints are applied in databases to ensure that updates to not violate data integrity. In addition to constraints in databases, rules must be applied as data entry constraints and for validation of data received from other sources. Every field of every record created or received must be validated so that no actions are performed on invalid data. Processing of data should never reach the point where it is rejected in a database update.
This is not usually a concern in conventional systems, but when records are submitted to shared services, there is a greater risk that an invalid request could be submitted. Each service should apply the same rules to data received from other services as it would apply to data entered by a human. A service should be designed to be used in a variety of contexts and cannot assume that all sources are reliable. Similarly, a service may be used by new processes or processes that are independently upgraded or replaced in the future, resulting in potential incompatibility.
Event Rules
Event rules identify events of interest for monitoring or initiation of action. Event processing is discussed in detail in Chapter 8. Rules are important for recognition, filtering, and distribution of events.
External Events
External events may come as messages from other systems or machines, from human inputs and from sensors. Some events are communicated relatively infrequently and are individually evaluated to determine if they are of interest. Other events of interest may be in streams of data from sensors or other systems and may require consideration of inputs from multiple sources for recognition and validation. These inputs are filtered by analytics systems that can derive events from large, multiple streams of data, as the data are being received. Analytics systems are discussed further in Chapter 6.
As external events are received, event rules must be applied to determine the events of interest. In addition, external events, in particular, must be validated to ensure that the enterprise does not react to erroneous or fraudulent events. Validity may be evaluated by correlation of multiple sources, by data integrity rules, and by rules that validate against known, related data.
Database Events
Databases, particularly master-data databases, represent the current state of the business. A database management system can support rules called “triggers” to recognize changes in the state of the business that are of interest.
A trigger “fires” when its condition, referencing database elements, becomes true. Generally, it will not fire again unless its condition becomes false and then becomes true, again. A trigger initiates an action, typically an event notice, which is communicated to an application or process to perform a desired action. The ability to apply triggers is a database system feature.
Notification Broker
A notification broker provides a service of forwarding event notices to subscribers. Subscribers indicate the characteristics of events of interest and express conditions for qualification of individual events with rules. When the event broker receives an event it applies the subscriber rules to determine if and where the notice should be distributed.
Consequently, an event notice may go through several levels of constraints: the determination interest by the source or external event filter, determination of interest to the notification broker, and determination of interest to subscribers. It is likely that the subscriber will apply one or more additional rules to determine appropriate action depending on the purpose of the subscriber.
Process Events
Three types of events can affect a process: events from outside the process, event-condition-action events, and timer events. These events are discussed in the context of BPMN and/or CMMN processes.
Event notices from external sources will typically be received as asynchronous messages from an external source, another internal system, or a notification broker. As noted above, the process may apply rules to further qualify and determine action depending on the process and the context in which it is received. In both BPMN and CMMN, the recognition of these events is represented by a circle—in BPMN it is an event and in CMMN it is an event listener.
CMMN assumes that events from internal activity (case file updates) as well as external sources will be applied to the case file where the effects will cause active event listener rules to fire, thus the case file functions as the clearing house for events to affect the active process. BPMN does not maintain a “case file” representing the current state of the situation, therefore event elements are triggered by the receipt of messages or occurrence of time.
Machine Learning
Large volumes of incoming data may be analyzed to identify patterns of interest representing changes of circumstances in the data sources that may represent market activity, web queries, sales data, various sensors monitoring variables of interest. The occurrence of variances in a pattern can indicate a relevant event and trigger further inquiries and analysis.
“Cognitive computing” techniques are being applied in analytic processes for identification of important patterns in natural language documents and “big data” collected from a variety of sources.
Process Flow Control Rules
Some rules identify risks or expense to be avoided and divert process activity to mitigate or avoid the damage. Other rules recognize policy constraints that, under special circumstances or approvals, may be authorized. For example, all purchases of equipment must go through the purchase order process. However, if equipment is required to resolve a major disruption of operations, an individual can purchase the equipment and submit an expense report with appropriate justification. The constraint is violated, but there is a compensating process required.
Simple Flow Control
In a BPMN process, the simplest form of rule implementation is a gateway branch. The gateway condition is evaluated against one or more variables in the process context to choose between alternative paths. In CMMN, the entry/exit sentry controls what actions are initiated or completed. A CMMN sentry applies an ECA rule to enable the start or end of an activity. An ECA rule is evaluated only when the specified event occurs. The event will usually be an event within the process such as the completion of an activity. The ECA rule enables subsequent activity in the process. For the most part, the gateway and sentry decisions address variations in processing requirements. Alternative paths may be defined for differing circumstances or requirements, for compliance with a policy or regulation, or to direct control to an alternative path to resolve an exception.
For example, a policy rule might be, “if acceptance of an order will cause the customer's credit limit to be exceeded, then the order must be rejected.” Instead of rejecting the order in our example, the rule might be changed to offer the customer an alternative payment option. Sometimes the same rule may be required at multiple points in different business processes. The credit limit rule might be applied in an order-change process as well, and a rule change must be reflected in both processes.
Decision Model and Notation
Sometimes circumstances are not so simple. There may be multiple alternatives described by multiple rules. The decision model and notation (DMN, http://www.omg.org/spec/DMN/) specification of the Object Management Group (OMG) defines a facility for representation of these complex rules in tables.
Fig. 5.2 illustrates the typical structure of a DMN table. The rules are the bottom three rows. There are two input variables and two output variables. The lists of possible values of each input and each output are indicated. The hit indicator, “U”, indicates that each rule is unique (the conditions do not overlap). The completeness indicator, “C”, indicates that there are no gaps between rules, full coverage.
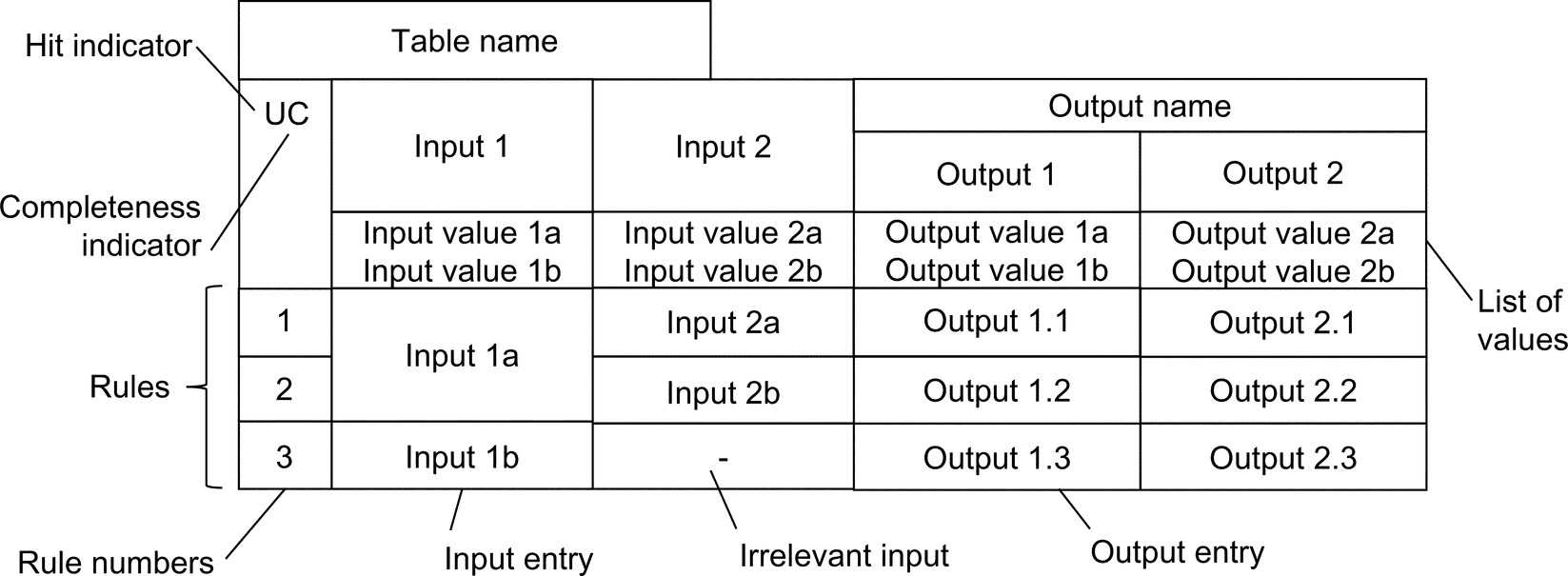
Note that rules 1 and 2 have the same input 1 value, and rule 3 has an input 2 value that is irrelevant—the rule only depends on the input 1 value.
There are various possible hit indicators and completeness indicators that can prescribe the sequence in which rules are evaluated and how overlaps or gaps in rule coverage should be resolved. There is an expression language for specification of the conditions in a form to be interpreted by computer. Each input value or output value may be a computed value dependent on multiple variables. The table can also take various shapes and accommodate different numbers of inputs, outputs and rules. A tool that implements DMN and supports easy configuration of the table graphics and proper syntax of expressions.
It is most useful for business users to express the inputs and outputs as text to be converted to formal expressions by technical people. A table with textual descriptions can be relatively easy to understand and validate unless there are many rules or variables.
The decisions modeled with DMN are explicit and predictable.
Production Rules
In a typical process (such as defined by BPMN or CMMN), a rules engine and an applicable set of rules can be invoked by an activity at a particular point in a business process where there is a need for a complex computation to make a decision. This is typical of claims processing or product configuration. The rules engine is presented with all the relevant data, and the rules are applied. The rules engine returns a result, or it may return a failure to produce a desired result—the claim is invalid, the product cannot be configured, or the solution cannot be reached.
Forward chaining may be used to generate a sequence of activities for a project plan or an adaptive process, coordinating the work of different participants. This is equivalent to planning a trip. You make assumptions about intermediate outcomes, but if an outcome is not as expected, then you replan from that point forward. The end objective remains the same. Each plan identifies the best path to reach the objective from the current point under current circumstances and assumptions.
Alternatively, a process can be dynamically defined as each activity is completed. As an activity is completed or an event is triggered (or in anticipation), production rules can suggest the next activity(s) to be performed or considered for the particular situation based on the state of the process, the work product, and the objective. Rather than allow the rules engine to pick from the rules available to fire, the tentative action of each of the candidate rules could be presented to a knowledge worker. In such a process, there is no obvious, predefined flow, just a set of possible activities, events, and rules. This technique can fit quite well into an implementation of the CMMN specification.
Approval
In either BPMN or CMMN, a rule may call for prior approval for an action. For example, if a customer seeks a refund on a purchase, this may require that refunds greater than a specified amount must be approved by a manager with the appropriate spending authority. This decision may direct the flow of control to an approval service that will locate a person in the management chain with the necessary level of authority. Selection of an appropriate approver may be a backward-chaining rules process.
Complex Computation
A complex decision also may be performed by a rule-based system (forward- or backward-chaining inferencing) that is engaged as a BPMN subprocess or by a CMMN process task. For CMMN, the case file should provide the context information needed to support the inferencing process. In BPMN, the context is not as obvious but must be determined from process context variables associated with the input request record and inputs from the user.
In a typical BPMN or CMMN process, a rules engine and an applicable set of rules can be invoked by an activity at a particular point in a business process where there is a need for a complex computation to make a decision. This is typical of claims processing or product configuration. The rules engine is presented with all the relevant data, and the rules are applied. The rules engine returns a result, or it may return a failure to produce a desired result—the claim is invalid, the product cannot be configured, and the solution cannot be reached.
The complex decision could support a help desk operator with diagnosis of a customer problem or develop a bill of materials for a custom order.
Guidance
Rules may be used to provide guidance in an adaptive process (CMMN). The simplest form of guidance is a planning table where options in the planning table appear based on rules that include planning items based on the role of the participant and the current state of the case file. The choices might be influenced by collaboration with other participants.
However, the decision may require consideration of complex factors some of which the decision-maker might overlook. For example, the course of treatment of a patient with medications may depend on current vital signs, physical symptoms, allergies, other current medications, previous response to potential medications, and a balance of potential outcomes against potential side effects. A backward-chaining rules engine might be used to recommend possible actions or to identify risks of a proposed medication.
Forward-chaining rules might be used to propose a process or next step based on current circumstances in an adaptive process. Continued progress on the plan might depend on achieving expected progress guarded by sentries and event watchers to raise alerts or propose alterative actions.
On the other hand, backward-chaining rules might be used to identify multiple alternatives under the current circumstances and identify risk factors for each alternative. If some of relevant variables are not currently available, a backward-chaining process can be designed to consider options that do not depend on the unavailable variables or allow the participant to provide assumptions.
At the same time, rules can ensure that all relevant factors and possible alternatives are considered and provide measurements to provide guidance to the decision-maker. The rule-based system can also provide explanations of its conclusions and reasons for elimination of some options by consideration of the search paths that lead to each conclusion.
Optimization
Production optimization involves adjusting product mix or workload balancing to minimize cost, maintain quality, and adapt to changes in demand. Sharing of services and resources can improve economies of scale, but of course, sharing makes the problem more complex. The following paragraphs illustrate examples of production optimization problems that might be addressed with knowledge-based systems.
US Federal regulations for vehicle fuel economy require that a vehicle manufacturer not exceed certain average levels of fuel consumption in the vehicles it produces. This means that if the cumulative average is reaching the limit, then the product mix must be adjusted to decrease the production of vehicles with higher rates of fuel consumption. The fuel consumption of each vehicle depends on multiple factors including the weight and streamlining, in addition to the performance of various components. Rules can determine the expected fuel economy of each vehicle based on its features and components. This then provides the basis for computation of the cumulative average.
Average fuel economy is not a rigid limit since, if the limit is exceeded, subsequent production can compensate to bring the cumulative average back in line. This then allows production scheduling to optimize other factors when determining the sequence of vehicles on the production line.
Another form of optimization involves workload balancing. Returning to the vehicle production example, the work content of a vehicle can be determined by rules that consider the assembly operations required at each workstation. The work content will determine the distance a vehicle moves in each station while the work is being done (based on the line production rate). If two or more vehicles with high work content arrive sequentially at a workstation, the operator may end up out of his/her workstation, possibly beyond reach of tools or materials or interfering with the next workstation. The production line-up can be adjusted to space out these high-work-content vehicles.
Workload balancing may also occur with sharing of resources among multiple processes or services. Within a service unit, there may be multiple, different capability methods requiring the participation of people with similar skills. Sharing of services increases economy of scale but also will require more concurrent operations. Some people may have some skills that are more scarce, so bottlenecks can occur if the scarce resources are needed on multiple processes at the same time. Some requests may require more time or expertise than others. This is essentially a configuration problem, but the configuration is continuous as new requests are initiated and different skills are needed as work progresses.
Workload balancing is a common problem where participants can be assigned to a variety of roles in different processes, and the potential savings become greater when consolidation of capabilities provides the opportunity for economies of scale.
Selection
Backward chaining (or logic programming) is important for implementing complex searches. The programmer can focus attention on defining the rules and does not need to deal with the mechanics of backward chaining and backtracking. Nevertheless, logic programming does require special skills and attention to the order in which statements are executed.
For example, backward chaining can determine if the necessary elements to authorize a claim are present and return the allowable fee for the qualifying circumstances. This might include a determination that the claim has already been paid as part of another claim.
Diagnosis is another form of selection. Rules search for a diagnosis that exhibits the observed symptoms of a problem. Diagnosis is frequently a fundamental step in determining corrective action.
Rules provide the basis for selection of a performer to fill a role. Roles in any collaboration should be filled by people or service units that have the necessary skills, relationships, and authority to meet the needs of the collaboration while recognizing workload balancing objectives as discussed above.
Some collaborations are unstructured and require a mix of skills, relationships, and authority. For example, a task force may be assembled to address a particular business problem. The participants must have relevant skills, relationships to organizations that are affected by the problem and potential solution, and authority to gain access to the information needed to analyze and solve the problem. Not every person need have all the relevant skills, and it is likely that no one of them will have all of the organizational relationships or access authorization. Rules can be used to consider candidates for participation in the collaboration that, together, satisfy the requirements.
Different people with the same job classification may each have different, but overlapping skill sets and certifications. Assignments should reflect the level of demand for certain skills so that progress on some undertakings is not delayed because persons with critical skills are assigned to efforts that do not require those critical skills. This is again the workload balance problem discussed above.
A couple other factors may be considered. Even though activities within a collaboration can be done by different performers, assignment of one performer to a series of activities may result in higher productivity, quality, and job satisfaction. This continuity of participant must be curtailed where there is a requirement of separation of responsibility.
Product Design and Configuration Rules
Production rules are used to produce a configuration. Most often they are used for complex system configurations such as configuration of a complex product such as an automobile or a computer. For example, a rule may specify that “if a customer automobile order includes air conditioning, and if the order also includes an optional V-8 engine, then air conditioning compressor 1234 is added to the bill of materials.” Another rule may specify that “if air conditioning compressor 1234 is included, and the order also includes power windows or power door locks, then the alternator must be replaced by a heavy-duty alternator.”
Production rules might also be used for such computations as bill-of-materials generation, project planning, process planning, in-process inventory computation, design of experiments, or forecasting.
Since rules can be used to identify the parts required for a product configuration(s) this may be used to generate a bill of materials. An extension of the mechanism is to compute the addition of parts to correspond to a production-line sequence to determine assembled parts to determine inventory without emptying the production line.
Forward chaining may be used to generate a sequence of activities for a project plan or an adaptive process, coordinating the work of different participants. This is equivalent to planning a trip. You make assumptions about intermediate outcomes, but if an outcome is not as expected, then you replan from that point forward. The end objective remains the same. Each plan identifies the best path to reach the objective from the current point under current circumstances and assumptions.
Alternatively, a process can be dynamically defined as each activity is completed. As an activity is completed or an event is triggered (or in anticipation), production rules can determine the next activity(s) to be performed or considered for the particular situation based on the state of the process, the work product, and the objective. Rather than allow the rules engine to pick from the rules available to fire, the tentative action of each of the candidate rules could be presented to a knowledge worker. In such a process, there is no obvious, predefined flow, just a set of possible activities, events, and rules. This technique can fit quite well into an implementation of the CMMN specification.
A number of important features of a product can be computed (or estimated) using rules based on the configuration of the particular product (eg, car or truck).
• Weight can be computed as the sum of the components in the particular vehicle configuration.
• Cost of parts can be computed based on the particular configuration, but it is often more important to determine the cost based on product options (eg, air conditioning, power seats, sound system) which may involve different components for different vehicle configurations. Labor costs can also be computed based on product configuration. This can determine the cost of each unit, although idle operator time may be difficult to allocate. Overall production costs will be a function of the product mix.
• Fuel economy of an individual vehicle can be evaluated based on the components that affect fuel economy along with the impact of weight and aerodynamic characteristics of the vehicle model.
• Load capacity can be computed based on the suspension components and vehicle weight with some constraints based on the particular vehicle model.
• Failure mode analysis involves modeling components for analysis of potential failures and the consequences. This might be applied to the fuel system, the brake system, the drive train, and so on.
Design for Production
Rules can be used to apply design constraints for certain types of components and production operations, for example,
• Molded parts may require rounded edges and minimum thickness of sections.
• Stampings may limit minimum radii on creases and maximum draw on concave surfaces.
• Some parts may require minimum section thickness for heat transfer or strength.
Governance
Governance is the responsibility of the board of directors or other governing body to ensure that the enterprise is “doing the right thing and doing it well.” Governance must be supported by the management of the enterprise, and governance will be a basis for evaluation of manager performance. Consequently, managers will also be concerned that organizations within their area of responsibility are doing the right thing and doing it well on a basis similar to the criteria of the governing body.
Governance involves (1) setting policies based on regulations, business objectives, good business practices, and monitoring compliance, (2) setting objectives, and monitoring performance, (3) ensuring accountability, and monitoring compliance with appropriate standards of conduct, and (4) identification of risks and assessment of risk mitigation or avoidance.
In this chapter, we are concerned with support of governance with rules applied in information systems. We will examine the mechanisms of governance in greater detail in Chapter 11. Much of governance involves the application of rules and measurement of compliance. This must be supported by a facility for management of the rules and traceability to their implementation as well as traceability from the effect of a rule back to the record of intent. Rules management is addressed later in this chapter.
Here we will consider the application of rules under the following topics:
• Policies
• Objectives
• Approval levels
• Monitoring
Regulations
Regulations are most often expressed in natural language text although there is interest in expressing them more precisely to remove ambiguity and support automated analysis for impact and compliance.
Regulations should not be applied directly to the enterprise but should be translated into policies appropriate to the particular enterprise. There should, nevertheless, be clear traceability between the regulations and the policies and rules that enforce them.
Most regulations are not published in a form that could be used directly by automated systems. There must be some transformation by humans to codify the required intent and identify where, if possible, the controls can be implemented in business processes or computations.
Some regulations are quite abstract, expressing an objective rather than a clear restriction on operations. The Sarbanes-Oxley Act (http://www.soxlaw.com/introduction.htm), for example, requires accountability and control. Executives must ensure accurate corporate reporting. This requires controls such as separation of duties, disclosure of conflicts of interest, restrictions on spending authority, and independent review of actions. In addition, there must be strict record-keeping for accountability. These measures are pervasive and must be addressed in the design of enterprise processes. Essentially, these are requirements for good governance.
Regulations must be interpreted in the context of a particular enterprise and in the context in which they will be applied. Furthermore, the approach to application of the regulation may reflect consideration of risks of violation such as the likelihood of accidents, oversights, or mistakes, as well as the potential consequences to the enterprise and individual employees.
For example, restrictions on shipment and storage of hazardous materials can be enforced by rules applied to shipping and receiving orders. Material control records should indicate which items are or contain hazardous materials. Hazardous shipments and material handling processes can include special handling based on the hazardous material identifier.
Some regulations can be very specific. Tariffs, for example, define the rates to be charged for specific types of service. Tax regulations are usually very specific as well. Similarly, hazardous materials regulations can be very specific about precautions and prohibitions regarding use, storage, and transportation. It may be relatively straightforward to implement such regulations.
In the future, regulations may be codified so that they can be interpreted and analyzed by computers. The semantics of business vocabulary and rules specification (SBVR, http://www.omg.org/technology/documents/br_pm_spec_catalog.htm#sbvr) from the OMG provides a formal way to capture and express rules in a natural language-like form. In fact this facility supports the specification of multiple vocabularies, so rules could be expressed in terms from different natural languages. The rules are represented in a computer model that can be used to analyze the rules for inconsistencies. The formal structure of the rules helps remove ambiguities. However, regulations will still require interpretation and development of controls based on the specific enterprise and the risks of violations.
Policies
A policy is a declarative expression of intent independent of specific business operations. For example, a policy might express that “any purchase of a personal computer or laptop computer must conform to an approved hardware and software configuration.” The policy does not define an action to be taken nor who must take an action, but rather it defines a constraint on business operations.
A policy may require multiple rules with different points of application. At the same time, there may be degrees of enforcement or a level of discretion, where deviation might be authorized under special circumstances, as opposed to a level of absolute compliance with regulations where there could be civil or criminal liability. This computer purchase rule might have a level of enforcement which allows exceptions with prior approval—perhaps approval by the manager of the personal computer support activity.
Rules that express policies are a mechanism for governing the enterprise. Other management directives such as strategic initiatives, high-level business collaborations, organization structure, and allocation of resources are important aspects of enterprise management, but they have only indirect effect on how the enterprise actually operates. Policy rules define management controls that can have direct effect on daily operations as well as longer-term results.
Some policy rules may be incorporated in automated business processes or computer applications, and some rules must be applied to the behavior of humans. Where possible we should look for ways to manage and implement rules in automated processes and applications to ensure objective and consistent application and ensure agility in the ability to adapt policies to new circumstances.
Rules for implementation of policies, including those that reflect regulations, may affect many aspects of enterprise operations. Rules may be applied in business processes to enforce constraints defined by policies. Many forms are discussed under other topics in this section. Additional rules may be used to detect when policies are violated. These are discussed under “monitoring” below.
Objectives
Objectives are defined by management, in particular not only in strategic planning but also in response to concerns by the governing body. Objectives are to be measurable and time limited. This can be expressed as rules that determine if the enterprise has failed to meet an objective, and additional rules might raise attention to objectives where appropriate progress is not being achieved. Current measurements should be accessible from normal operating data. Rules can be evaluated at appropriate times and report if progress is not satisfactory or if the objective has been achieved or failed.
Approval Levels
For some persons, an action may not be authorized without approval by another person. There is typically one of several reasons for approval: (1) exception to a policy; (2) restriction of level of financial authority; (3) restricted access authorization; (4) requirement for separation of responsibility; (5) approval of a deliverable, particularly a project plan, acquisition, design or product; and (6) application of special expertise or responsibility.
Each of these requirements for approval can be expressed as rules to be inserted in business processes where authorization is required. A request for authorization may need to be escalated to reach a manager with appropriate authorization.
Security Authorization
A complementary authorization service is required for access control. A service should determine that requests are properly authorized which may include not only actions by requestors but also, when necessary, independent approval of a request. This requires a different process for application of authorization policies. Authorization is discussed in detail in Chapter 7.
Monitoring
Determination if an enterprise is “doing the right thing and doing it well” requires that the governing body monitor the actions, effects, and circumstances of the enterprise. Some of this is accomplished by reviewing financial reports, reports of exceptions as noted above, and other management reports. However, other mechanisms are needed to raise attention to other exceptions and external developments that indicate a need for special consideration. Here we consider the use of rules for monitoring under five topics: performance, level of service, threat recognition, time exceptions, and alerts.
Performance
Certain operational performance measures should be reported for normal business management. Reductions of customer satisfaction and profit will always be a concern. Significant variance in performance measurements, such as cost and defects, will be of concern. Triggers can evaluate measurements against acceptable levels of variance for all operations to report a need for attention. These detailed variances will be addressed by the responsible managers. Governance monitoring may focus on significant variance in end product value measurements as cause for attention. As necessary, with a value stream model (such as with VDML), these can be traced back to the responsible activities.
Level of Service Agreements
The agile enterprise will share capabilities as services. These may be outsourced as well as internal services. All services must have level of service agreements so that the consumers of those services have a clear understanding of what they can expect and how it will affect their areas of responsibility.
Furthermore, actual performance of services should be tracked and reported for management oversight. Rules can be added to these reporting facilities or as triggers on an associated database to provide governance reporting of variances from the level of service agreements. In the alternative, periodic governance reports should highlight service level exceptions.
Time Exceptions
Time exceptions are situations when something is expected to happen and it is late or does not occur. Some time exceptions can be identified from records of activities and can be reported periodically or identified by database triggers. On the other hand, time events in BPMN or timer event listeners (CMMN) can be set to act when an expected action is over-due.
Time exceptions can be important for monitoring performance from a number of perspectives. For example, a time event could be set to report when delivery time for a product or service exceeds an acceptable duration. A time event can report when an objective is not achieved on time. A time event can report when supplier shipments are late. Some such delays may always be important, while others will be of interest when there is a particular area of concern to be monitored. Particularly serious delays should result in alerts that get immediate attention of top management with follow-up reporting to the governing body.
Ecosystem Alerts
Many factors of concern to the governing body are a result of changes in the enterprise ecosystem, such as economic factors, market demand, commodity and critical resource prices, international conflicts, disruptions in the power grid or Internet, and competitor announcements of pricing changes or new products.
Some of these factors, such as stock market indexes, can be monitored by reporting from specialized services that can provide regular updates. Rules or neural networks can be applied to identify significant trends and exceptions.
Other factors may require monitoring volumes of data such as publications, sales data or web clicks to discover announcements, trends, and world events that may affect challenges and opportunities for the enterprise. Recent advances in distributed computing, now called analytics, have made it possible to analyze large volumes of data in a short time. More recent advances have made it possible to analyze continuous streams of data from multiple sources. These data may be in different formats including unstructured data and images.
Many threats can only be recognized by human awareness of events in the world around us. However, rules can help recognize some forms of threat.
Market activity can be monitored from sales and other internet sources. Rules can be used to recognize significant changes in prices or demand. Analytics can be used to monitor trends from sales data for trends in market demand. Commodity prices can also be tracked to detect significant shifts, particularly commodities that have a direct impact on production of the enterprise.
Analytics techniques can be used to scan industry publications for research advances and competitor product announcements. Analytics is discussed further in Chapter 6.
Administration of Business Policies and Rules
Effective specification and management of business rules can ensure consistency in operating practices and compliance with policies, governance, and regulatory requirements. The ability to change and quickly deploy or modify business rules can have a significant impact on enterprise agility as well as the cost of implementation of changing regulations from political entities around the world.
We have talked about the many ways rules can be used to express decisions and constraints. Here we are concerned with rules that express business regulations or policies—business rules as opposed to operational rules that define operating efficiencies or practices and determine how a capability is applied. A control or decision that rises to an enterprise level of concern will be considered a business objective or policy.
A business objective of interest can be reported as achieved by a rule implemented as a database trigger for notification when a variable has reached a critical level. An objective may also be of concern when there is a failure to maintain a desired level or to achieve a desired result by a target date. It is appropriate that these objectives be observed in the dashboard of the concerned business leader(s). In general, such objectives are of temporary interest to particular stakeholders and, as opposed to policies, objectives do not, per se, control business operations.
Regulations come from outside the enterprise and policies come from top management and/or the governing board. Regulations must be interpreted as policies that are specific to the particular enterprise. To the extent their implementation may be automated, these should be expressed as computer-readable business rules that express the automated decision criteria. The regulations, policies, and rules should be centrally managed to ensure consistency and timeliness of rule implementation or change. Business rules will frequently affect different parts of the organization, possibly in different ways. Whenever a policy is changed, it is necessary to identify and adapt all the relevant rules.
A capability map, a taxonomy of capabilities (the capability library in VDML), provides a framework for identification of capabilities relevant to a policy. If there are many relevant capabilities, it may be appropriate to consider creation of a shared capability to implement the policy and engage that capability from the many affected capabilities. This is particularly true if implementation of the policy is complex, such as the implementation of rule-based reasoning.
Policies in VDML
To the extent a policy affects collaborations, activities, and deliverable flows, VDML can provide a context for the implementation of policies. Generally, such a policy will affect the flow of deliverables—a policy decision will produce an alternative flow. VDML can express the policy condition and define an alternative deliverable flow to resolve the policy violation or constraint.
However, additional deliverable flows may be avoided as too much detail in a VDML model where a policy violation flow should never occur, but the relevance of a policy can be included as an annotation on the affected activity. In addition, a policy may be characterized as a practice and can be represented in the VDML Practice Library for cross-referencing.
In general, a VDML model will assist in the identification of relevant value stream(s) and capability(s) that may be affected by a policy. Resources or deliverables that are referenced in the rules will also suggest relevant capabilities and activities (those that consume or deliver). This includes value streams in product development where product design and production engineering decisions may affect regulatory compliance, as well as value streams of support services such as purchasing, receipt and storage of materials, maintenance of equipment, and so on. Each relevant value stream should be examined to find the earliest point where a rule should be applied to avoid rework or the consequences of noncompliance. The value stream also supports consideration of the impact of the policy on customer values. The customer value impact may be a basis for reconsideration of the policy, reconsideration of the way the policy is translated to rules, or consideration of changes to the structure of the value stream or the product.
In addition, where the consequences of violation may be more severe, it would be appropriate to apply rules prior to potential occurrence of the undesirable consequence. For example, if there are regulations that apply to a product, it may be appropriate to inspect finished products for compliance prior to shipment. This may reveal a circumstance where an early stage restriction was overlooked. This is a particular concern where there has been a significant product or business change.
There may be multiple capability methods for implementation of a policy. For example, an employee termination policy should require termination of any authority for access to information or participation in operations. Similarly, a new assignment should result in reconsideration of existing authorizations. These controls may require not only a rule, but the initiation of a process to effect the required changes to role and authorization records. This requirement could be driven by a trigger on the employment record. While this might be considered a data integrity issue, the scope of effect is broad, and there may be some discretion required regarding the propagation of changes and the timing of their effect.
Mapping business policies and rules to capability methods and business processes will also provide the opportunity to recognize where policies may overlap or conflict. Note that not all policies will be implemented with rules. Some policies will affect the way processes are structured, the way activities are performed, or the way resources are allocated, including people, machines, and materials.
Ecosystem Conditions
A policy may require attention to certain market events or trends. The criteria for identification of changes of interest may be expressed as policies or rules. The translation of these requirements for analysis will be in internal responsibility of the analytics or enterprise intelligence service unit. These should be addressed by the Sense and Respond Directory discussed in Chapter 9. If a relevant new or revised law or regulation is under consideration or has been adopted, this will be a situation to be reported in the Sense and Respond Directory. Such changes may affect not only activities and decisions but may require specific actions to achieve compliance of existing facilities, products, contracts, records, or other business items.
Consolidation of Control
It is desirable that implementation of policies and rules should have rapid effect. For example, consider an enterprise policy that “returns must be in original packaging, accompanied by the original receipt and received within 30 days of the sale.” Suppose that a competitor starts a holiday season campaign drawing attention to their policy that “returns must be in original packaging suitable for resale, goods must be current stock items, and refunds without receipts are in the form of a gift card.” It may be important to quickly implement a more accommodating policy to avoid potential lost business, particularly during the holiday season. This could take days if not weeks if there are different retail systems for different lines of business.
Consolidation of business control functions can provide a greater opportunity for rapid deployment of rules or codification of complex decisions. For example, computation of billing for specialized services might be a time-consuming manual process performed by individual, field service units, whereas consolidation of the billing function as a shared service might justify the development of a consolidated billing unit or an expert system solution. This is similar to the use of purchasing, accounting, and personnel services to control vendor selection, ensure control of financial records, and achieve consistency in personnel administration throughout the enterprise.
Regulations and Policies Directory
A Regulations and Policies Directory is needed to support an enterprise unit for administration of regulations and policies. Regulations must be interpreted to determine policies that are relevant to the particular enterprise, and policies must be expressed as rules that are precise expressions of intent and that can define relevant circumstances and be analyzed for overlaps and gaps. A policy may require multiple rules applicable in different contexts. The resulting rules must be deployed wherever they are appropriate, throughout the enterprise.
The Regulations and Policies unit must consider requirements for compliance with regulations and identify the appropriate organizations and processes where associated rules apply. From an enterprise perspective rules should be associated with capability offers. Capability offers identify not only the capability but the organization unit responsible for the capability and thus the organization unit responsible for application of the rule.
Relevant capabilities may be identified by analysis of value streams as discussed above, or by identification of other factors such as resources or deliverables affected by a policy. These are associated with capabilities where the policies may be applicable.
The directory must provide the linkage between regulations, policies, and rules. In the context of a VDM model, the implementation of policies and rules can be traced to capability offers and activities of capability methods, if appropriate. The VDM capability offers, methods, and activities are expected to align to operational models of service units, processes, and activities. Consequently, regulations can be traced to deployment in processes and activities, and the rules that implement policies (and regulations where applicable) can be linked back to the policy or rule that is the basis of the rule.
The Regulations and Policies Directory might also be the basis for analysis of the relationships between regulations and policies to consider overlaps, conflicts, and gaps. Rules reference business entities, attributes, and relationships in the rule condition expressions. The rule conditional expressions should reference these business entities, attributes, and relationships consistent with the enterprise logical data model as discussed in Chapter 6. Rules that reference the same business entities are related, so similar rules may be found by examining rules that reference some or all of the same business entities, and rule relationships can be further refined by identifying the references to attributes and relationships. There are various techniques for analysis of the relationships between conditional expressions (eg, using Venn diagrams).
Moving Forward
Rules have a significant impact in chapters that follow. They define data integrity constraints, database triggers for events, and criteria for analytics in Chapter 6. They are fundamental to specification of access control in Chapter 7. They define events of interest and event notice routing in Chapter 8.
