Chapter 3. Cyber Terrorism and Other Hidden Threats
The subject of cyber terrorism is controversial and fear-inducing—and it’s impossible to overlook in the context of this book’s premise. Based on the research I conducted for this chapter, it’s clear that governments and businesses all over the world have made reducing the threat of cyber terrorism and espionage a high priority.
Countless books, seminars, and conferences cover this topic. There are technology companies and government agencies solely focused on securing our IT infrastructures. Although security is certainly the main priority when it comes to protecting our nations and their citizens, the point of this chapter on cyber attacks, fraud, and overall threats to how we work and live is not to discuss security. Rather, I want to emphasize the importance of a sound infrastructure in supporting the extensive security that is required to keep countries, companies, and people safe.
The Threat Is Real
The experts have yet to agree on a concrete definition of cyber terrorism,1 but suffice it to say that the threat of enemies using technology to cut off our water supplies, power grids, and access to finances is very real.
As quickly as we stockpile technology to fend off cyber attacks, the threat of those attacks becomes stronger. Currently more than 100 foreign intelligence agencies are trying to hack into the 15,000 U.S. government networks that are composed of more than seven million computers.2 And the cost to defend these systems was more than a hundred million dollars during a six-month period in 2008.3
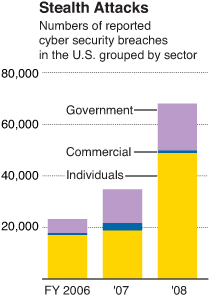
The enemy is no longer limited to being a foreign power. The enemy can be a high school hacker, online crime ring, or internal employee. The damage can be done in seconds but can take years to repair in terms of identifying the source, prosecuting the perpetrator, and reinforcing the compromised network. The issues around cyber defense will only grow in complexity as we continue to introduce more and new technologies into our networks. Figure 3.1 shows the increase in cyber security breaches from 2006 to 2008.4
Figure 3.1 Number of cyber security breaches in the U.S.
Protecting the Power Grid
Imagine what it would be like to spend days without electric power due to a cyber attack. Picture the impact of losing power during an extremely hot or extremely cold day. Imagine the cascading effects of major cities such as New York, Hong Kong, London, Sydney, and Sao Paulo being in complete darkness, without traffic lights, home security, food supplies, and access to money. You may recall the Northeast Blackout of 2003, the largest ever to hit the United States, which left 55 million people throughout the United States and Canada without electricity. While al Qaeda terrorist groups tried to take credit for the blackout, an in-depth probe into the matter found that the blackout could have been prevented through better communication, equipment, and training.5
Regardless, protecting the power grid is top of mind for governments around the world. While not declaring that the U.S. electrical power grid has been attacked, the Department of Homeland Security has stated that the power grid is vulnerable to potentially disabling computer attacks.6 This was in response to reports by the Wall Street Journal that Russian and Chinese cyber spies had made their way into the electrical grid to map the infrastructure and leave behind tools that could destroy parts of the infrastructure in the event of a crisis or a war with the U.S.7
There have also been reports regarding intrusions into the power grid throughout parts of Brazil in 2005, when three cities and tens of thousands of people were left without power. Another, more widespread attack supposedly happened on September 26, 2007 and affected more than three million people in dozens of cities over a two-day period.8 However, the reports of these cyber attacks were largely disputed by the Brazilian government and its energy providers.9
To date, there has not been a full-fledged cyber attack on the U.S. grid, but experts believe it’s just a matter of time. According to director and chief economist Scott Borg of the U.S. Cyber Consequences Unit, the estimated damage from losing power for three months would be $700 billion.10
We need to be careful not to stir up paranoia about the grid’s sustainability, but we must be mindful of the threats that exist. Preventing cyber attacks, or minimizing the effects should an enemy infiltrate a network, requires a deep understanding of the highly complex infrastructures that are currently in place.
The Million-Dollar-a-Day Upgrade
Although it wasn’t caused by a cyber attack, the technology incident at the Hatch nuclear power plant near Baxley, Georgia is worth addressing. In March 2008, an engineer who was connected to the plant’s network decided to install what he thought was a simple software upgrade on his own computer. Since he was connected to the network, the upgrade inadvertently brought down the entire system for 48 hours in an automatic, unplanned shutdown. Such a shutdown, which was required at Hatch due to federal protocol, forces utilities to purchase power from other parts of the grid—to the tune of $1 million a day.11
The complexities of the infrastructure were unknown to the engineer because of the differing expertise in the organization among IT staff and those responsible for the plant’s industrial control system (ICS). The ICS is the technology brain that enables the delivery of power to customers. It was impossible for the engineer to fully understand how the ICS intersects with the computer network, nor would that knowledge ever be a job requirement. This is an example of where the infrastructure would have benefited from having certain controls and mechanisms in place to prevent the software upgrade. And it underscores the importance of sound IT.
According to Joe Weiss, professional engineer and certified information security manager at Applied Control Systems, a consultancy specializing in optimizing and securing ICS, “The IT staff can cause an outage even while following existing IT policies [because they are] unaware of ICS issues.”12 As the author of Protecting Industrial Control Systems from Electronic Threats,13 Weiss also commented on the threat of terrorists attacking the electric power grid: “The current systems were not designed with awareness of cyber threats, regardless of whether they are deliberate or accidental. Control systems are in the formative stage for cyber security—arguably where IT was ten years ago. It will likely be another five to ten years before we start to design new control systems with security as part of the initial design.”
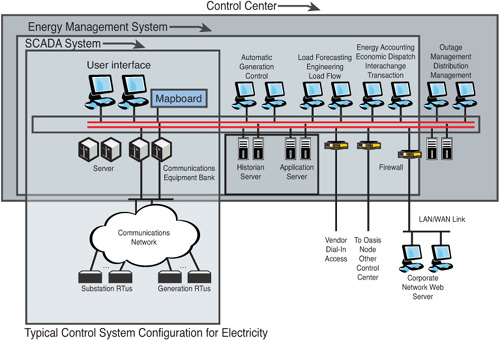
We may fundamentally grasp that our electrical grids, local power suppliers, and government agencies require far more sophisticated technology on the back end, yet the complexities that make those systems run are genius. Figure 3.2 shows the control system at an energy provider and just how complex the infrastructure can be. And this is one of the simplest depictions of it.
Figure 3.2 Control system configuration for electricity14
To be more proactive about the looming threat of porous infrastructures at power plants, Weiss suggests cross-disciplinary training between IT and industrial control systems personnel on equipment and best practices. He also believes that “senior management must provide budget, directive, and get all stakeholders involved in addressing cyber security.”
Building a Sound Employee Infrastructure
Weiss’ recommendations can be applied to nearly every industry and to nearly every facet of the organization. It’s up to the organization to create a culture where security is a priority by making it top of mind for every employee. Along these lines, it would be worth the investment to ensure that each employee has a better understanding of the bigger picture.
We’ve talked about cross-training developers to better manage the COBOL issue, and in our everyday dialog with each other, we stress the importance of managing up. When it comes to IT planning, we’re advised to include line-of-business managers so that each part of the organization is represented. These are great best practices. But I believe we could all benefit from less talking and more action to gain a deeper understanding of each other’s roles across the company in order to build a solid employee infrastructure. Here are some ways to do this:
• Shadowing: Employees can better understand the role of a manager or executive if they spend a day or week attending meetings and learning about the company’s operations. Many companies have such programs in place, but they are often provided for executives-in-training or are too scripted in an effort to shield the employee from confidential information. Confidentiality notwithstanding, the real benefits of a shadow program come when an employee is exposed to real business issues.
• Peer-to-peer job exchange: These can be short- or long-term assignments so that employees gain a better perspective of how a peer in a different part of the company contributes to his or her team and the organization as a whole. Similar programs exist in organizations where employees swap the same role in a different country or state. These exchange programs are valuable, yet a peer-to-peer program across different departments can help create a well-rounded view of the company for the employees.
• Executives on the shop floor: When an executive visits a site location, days or even weeks of planning go into the preparation for the internal inspection. I’d argue that a good chunk of that time would be better allocated to making sure the customers are pleased. When executives visit different facilities, there shouldn’t be any fanfare about their arrival, nor should their presence strike fear into employees. Executives would be well served if they spent a few hours or days getting a solid grasp on the organization’s inner workings by parking themselves alongside the employees who are making the products.
Bank Robbers Can Telecommute
Although most of our battles are fought face-to-face, cyber attacks are arguably more alarming, because they subtly steal our identities and slowly drain our pockets. One of the biggest cyber heists to date happened in November 2008. A transnational crime organization withdrew over $9 million in less than 12 hours from 2,100 RBS WorldPay ATMs in 280 cities throughout the U.S., Russia, Ukraine, Estonia, Italy, Japan, and Canada. Along with the money, the hackers also made off with financial data on 1.5 million customers and the social security numbers of 1.1 million customers.15
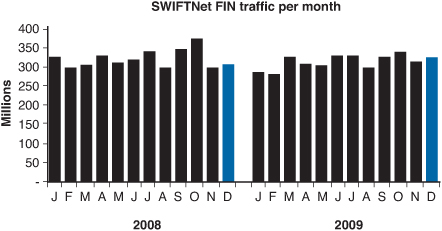
The RBS WorldPay bank robberies were extensive due to the speed of the transactions. These speeds are widely recorded in increments of transactions per minute, per second, and per millisecond. To better understand the speed of transactions in our digital world, more than 3.7 billion standardized financial messages were exchanged in December 2009 alone, according to the Society for Worldwide Interbank Financial Telecommunication (SWIFT). Figure 3.3 shows financial transactions for 2009 according to SWIFT.
Figure 3.3 Record of executed financial transactions according to SWIFT
By the time the RBS WorldPay cyber bank robbers were halted, they had already done a significant amount of damage.16 The victim of a sophisticated hacker ring, RBS WorldPay could just as easily have been another multinational financial organization or perhaps the bank that handles your finances.
It’s All Fun and Games Until...
Moving from a direct hit on a bank to a more subtle form of attack on consumers is very likely in the wildly popular massively multiplayer online game (MMOG) market. Bringing together hundreds of thousands of players simultaneously in an online world escalates the number of transactions in the infrastructure that need to be properly managed. With that many players online at the same time, there is bound to be at least one unscrupulous participant who has more in mind than a harmless round of World of Warcraft. A few minutes in the virtual world could do serious damage to unsuspecting consumers in terms of identity theft and spreading computer viruses to those who are online to simply play a game.
In some instances, the transaction speeds are barely perceptible because they come pretty darn close to breaking the speed of light. Like the RBS WorldPay heist, the perpetrators in MMOG typically aren’t caught until after they’ve done a world of harm.
Going beyond the MMOG example, the rapid pace of technology challenges businesses in nearly every industry to uncover the cause-and-effect relationships among seemingly disparate events or minute market changes that occur in milliseconds yet can have significant business impact.
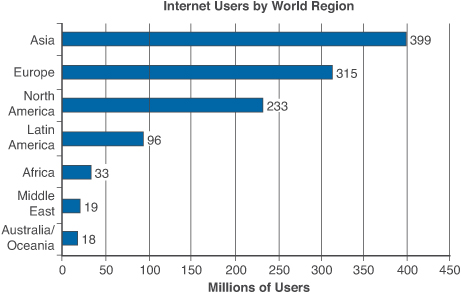
This is especially critical when you consider that approximately 1.8 billion people around the world are connected to the Internet, according to Internet World Stats. Many of them rely on it for personal banking, self-employment, filling prescriptions, and nearly any other transaction that used to be conducted face-to-face. Figure 3.4 shows Internet usage by country.
Figure 3.4 Internet users by world region as of 200917
Spotting trends that represent threats and being able to get ahead of them or stem them as they happen requires a balance between creating a solid IT foundation and reinforcing it through the proper security technologies.
Does this mean that we should never log on again, or that we should return to the good old days of asking strangers for directions and rushing home to make sure we don’t miss that landline telephone call? Certainly not. After all, we have come too far too fast to disregard the amazing IT industry and profit center that we have collectively created.
When we read about these cyber attacks and inadvertent system failures, we might be tempted to say “Just fix it.” Since the majority of our daily interactions with technology are relatively simple, it’s easy to take the point-and-click experience for granted. It is far more difficult on the part of the engineer, architect, or developer to make the user experience simple. Although turning on a light, powering down a computer, and accessing your 401k online may be simple actions you do on a regular basis, they require thousands if not millions of lines of code behind the scenes to make them happen. From an IT perspective, those activities are important and complex but are not on the same level as the technology that is required to run and protect our governments and global businesses.
The IT Infrastructure as a Strategic Weapon
In this global economy, we have to ask, “If business doesn’t stop at the border, why should our computers?” This can be a matter of national as well as international safety.
In September 2009, police in northwest England stopped Johnny “Mad Dog” Adair on the road because they believed he was a suspicious character, yet they couldn’t recall why his face was familiar. When the Police National Computer didn’t reveal any previous offenses or outstanding warrants, the officers let him go. Still uneasy, the officers followed their gut instinct and decided to conduct a more thorough search on Adair when they returned to the station. The results showed that he was convicted of assaulting his wife in 2005.
If the Police National Computer had been fully integrated with the criminal database in Northern Ireland, the officers would have been alerted to the fact that Adair was also a convicted terrorist and former commander in the terrorist group known as the Ulster Freedom Fighters.
The incompatibilities among the computer systems and an accompanying glitch were making hundreds of convicted terrorists virtually invisible to the British police. These issues were compounded by the fact that many of these terrorists had moved from Northern Ireland to England, Scotland, and Wales.18
The Impact of an Aging Infrastructure
We can well imagine the impact of losing our power supply and can empathize with the frustration of the police in north-west England. Yet fortifying the systems that make it possible to turn on the lights in our homes and keep computers running in the office is not as simple as bolting on additional security mechanisms or simply fusing various sources of information.
The infrastructures that are in place are highly complex, have evolved over decades, and consist of different software applications. Many of those applications are proprietary and have been customized to meet the company’s specific business needs and the customers it supports. These circumstances are not unlike those at many companies across various industries.
To illustrate this point using an analogy, think about the IT infrastructure as the foundation of a house. As you start to build on top of that foundation with beams, floors, plumbing, wiring, and the like, you need to be sure that your architects have designed the right plans and that your builders are following those plans using the right tools. Everybody involved must follow the mandated codes so that you are creating a sound structure that will endure for decades, if not a century and beyond. If any mistakes are made in how the concrete was mixed and poured, or cracks appear over time, the entire structure will eventually break down. When IT architects mapped out infrastructures decades ago, they couldn’t have imagined today’s fully digital and connected world, where an invisible enemy can infiltrate through a computer.
Adding new security tools or complex enterprise software today is like building an addition onto your house. It needs to be carefully included as an extension to the foundation, without disrupting any of the plumbing or wiring. If the technology doesn’t map to the larger architectural strategy, parts of the system can break down, leaving the company more vulnerable to attack.
Introducing New Technologies into Legacy Infrastructures
Taking advantage of newer technologies, including security tools and devices, without compromising the value of the existing infrastructure is a challenge that can deliver significant benefits if approached and executed properly. Here are some recommendations for ensuring a smoother integration with newer technologies:
• Map the infrastructure. Before you add any technology to the infrastructure, be sure you have a comprehensive and current view of the entire architecture, as well as how new technology will impact existing systems. This should include simulations of the domino effect should a new piece of technology be put into the infrastructure.
• Take an incremental approach. Resist the temptation to roll out new technology across the entire organization. First, test it privately among your internal development team, and be sure to test it under the worst possible circumstances. From there, try it with smaller teams in the company. At each stage, make sure you gather feedback, and make adjustments accordingly before the technology advances to the next team. This approach should be a critical part of the planning efforts so that realistic deadlines are set and met.
• Learn to compromise. Despite aggressive and well-executed efforts, you won’t be able to integrate every piece of your existing technology with the newer offerings. If the architectural strategy is well mapped out in advance of any development or integration work, this will not be a surprise. While you’ll try to migrate as much technology as possible, you should also build in plans from a staffing and budgeting perspective to rewrite the code in the newer environment.
• Know when to leave well enough alone. Given fluctuations in staffing and long-term investments in technology, the reality is that you simply won’t fully understand certain applications. You will know what they do and how they work to help the business, but you will not always know exactly what makes them tick from a software code perspective. If it’s a business-critical application, such as one that makes sure the electricity goes from the power supplier to the home, you may not need to know every line of code if the application is running properly. In this instance, the risk of compromising the infrastructure by opening the application far outweighs the need to sate curiosity.
Preventing a Digital Pearl Harbor
Dr. Jim Lewis is the director of the Center for Strategic and International Studies (CSIS) and one of the world’s most respected experts on cyber terrorism. One of Lewis’ more recent reports on the subject was the “Report of the CSIS Commission on Cybersecurity for the 44th Presidency.”19 This report is a comprehensive review of the current state of cyber terrorism that was prepared in December 2008 for then-President-elect Barack Obama.
In February 2010, Dr. Lewis testified before the Senate Commerce Committee and brought to light the impact of cyber crime on a day-to-day basis. In his testimony, Lewis said, “We talk about cyber attack and cyber war when we really should be saying cyber espionage and cyber crime. Espionage and crime are not acts of war. They are, however, daily occurrences on the Internet, with the U.S. being the chief victim, and they have become a major source of harm to national security. The greatest damage to the U.S. comes from espionage, including economic espionage. We have lost more as a nation to espionage than at any time since the 1940s. The damage is usually not visible, but, of course, the whole purpose of espionage is not to be detected.”20
While reading some of Lewis’ research in preparation for the interview with him,21 I was reminded of the discussions from the 1990s about the threat of a digital Pearl Harbor and how relevant that catchphrase still is today.
Lewis shared as much as he could about the state of our national security infrastructure without compromising the safety of our country. What follows is an excerpted Q&A from my interview with Lewis:
Q. What can we do better to reduce the threat of cyber terrorism?
A. We need to get more people and more companies to adopt the better technologies that will make us more secure. To do this, we need to better define the incentives that will advance the adoption of better technology. We also need to work with other governments so that we are all in agreement with the rules of the road when it comes to cyberspace.
It used to be that the U.S. was by far the dominant force in technology, and while it is still the leader, other countries have come to the forefront, and we are taking advantage of those technologies as well. We learned to work with other countries in that regard. Now we need to learn to work with other governments so that we are all in agreement on how we can better respond to threats in cyberspace.
Q. We’ve come so far in technology over the past few decades, so what is it about the threat of cyber attacks that makes conquering them so elusive?
A. While we have come very far in all areas of technology, including our defense against cyber attacks, we’re not quite there yet. It’s a maturity issue. You have to remember that while we just formally celebrated the 40th anniversary of the Internet, the commercial Internet that the majority of us know and use is only about 15 years old.
Just like we saw with the first airplanes and automobiles, we had to be working with them for a longer period of time to advance them and eliminate their issues as each new model is developed. The same can be said for new technologies and applications. We will see better versions of applications down the road, but it’s an iterative process. We continue to improve it, and we’re certainly getting closer to our goals.
Q. What can we do as citizens to help curb the threat of cyber terrorism?
A. A lot of it comes down to education and awareness. Education is definitely one way of making people more aware. For example, I gave a talk a few years back, and I asked the audience how many of them had been to the Beijing Olympics, and a good amount of people raised their hands. The next question I asked was how many of them brought their BlackBerrys with them when they were at the Olympics, and a fair amount of hands went up. Then I asked how many were aware that the Chinese government was monitoring their BlackBerry while they were in the country. The surprised look on their faces pretty much gave me my answer about the level of awareness of how the Internet works in countries outside the U.S.
In the United States, we have free access to any information on the Internet, so we just assume this is the way it is overseas. And China is not the only country that monitors its citizens on the Internet. So there’s still a lot of work to be done to figure out the rules of the road with cyber usage in different countries as it relates to preventing cyber attacks.
Q. Where does IT governance fit into the picture with regard to protecting us against cyber attacks?
A. IT governance is critical to protecting us against cyber attacks. You have to think about IT governance like wearing a seatbelt every time you get behind the wheel. In order for the seat belt to be effective, you have to not only wear it, it also has to be enforced by the law. It’s the IT governance process that will create better and more secure environments. There will also be things that technology can’t do, and that is why we need to work more closely with governments to address all of the security issues.
Lewis is a realist when it comes to advising about cyber attacks. As he so accurately pointed out, although we can’t solve every issue through technology, IT governance certainly plays a critical role. Lewis is not the only industry luminary to use the seat belt analogy, as you’ll see in a future chapter. I’ve included it twice in the book because it’s a direct quote from two industry experts that helps illustrate the relevance and role of IT governance to a broader audience. In addition, I believe this analogy eloquently raises the issue that perhaps IT governance should be mandated by law in certain high-risk, high-visibility situations.
Great Strides, Yet Miles to Go
On November 17, 2009, Steven R. Chabinsky, deputy assistant director of the Cyber Division of the United States Federal Bureau of Investigation (FBI), testified at a Congressional hearing. Chabinsky provided an overview of how the FBI’s anti-cyber crime task force works, along with its latest accomplishments.
In a transcript from the session, Chabinsky shared many positive milestones of the agency’s work. Within the context of the update, Chabinsky was quoted as saying, “...a compelling act of terror in cyberspace could take advantage of a limited window of opportunity to access and then destroy portions of our networked infrastructure.” He went on to say, “...we, as a nation, continue to deploy new technologies without having in place sufficient hardware or software assurance schemes or sufficient security processes that extend through the entire life cycle of our networks.”22
Earlier that year, similar warnings and recommendations were shared at the Conference on International Police Cooperation Against Cyber Crime held in New Delhi. During the conference, Senior Cabinet Secretary K. M. Chandrasekhar warned, “There could be attacks on critical infrastructure such as telecommunications, power distribution, transportation, financial services, essential public utility services, and others.”23 Certainly, government leaders throughout the world echo these sentiments.
A Global IT Governance Council
It’s clear that none of us is 100 percent safe from a cyber attack or cyber crime, regardless of how sophisticated and encrypted our systems are. However, we can get much closer to that 100 percent range than we currently are.
The U.S. government is hard at work addressing these issues and assembling forces across its various agencies and the private sector to use technology to thwart attacks. Augmenting these efforts could be the Global IT Governance Council, which would work in concert with businesses, government agencies, and existing security councils to establish more concrete guidelines and policies to protect the infrastructure. More specifically, the council would have the following goals:
• Work with government leaders throughout the world to establish criteria for creating more solid IT infrastructures through governance to protect countries from cyber attacks, cyber crime, and espionage.
• Establish and enforce consistent penalties and fines across the globe against the perpetrators of cyber crimes and cyber attacks.
• Create a warning system to alert the online community when they are about to enter a website that doesn’t meet minimum security requirements as determined by the Global IT Governance Council.
• Provide more education for citizens on how to better protect against cyber crime. This would include working with state and local governments to offer free workshops for adults, as well as coordinating with educators to include courses on preventing cyber attacks as part of the high school curriculum.
• Serve as an expert resource that organizations could freely consult for unbiased third-party advice and best practices related to protecting the infrastructure.
Endnotes
1. Harvard Law Record. “What is cyberterrorism? Even experts can’t agree.” Victoria Baranetsky. November 5, 2009. http://www.hlrecord.org/news/what-is-cyberterrorism-even-experts-can-t-agree-1.861186.
2. Center for Strategic and International Studies. Speech on Cyber Security at the Center for Strategic and International Studies. Delivered by Deputy Secretary of Defense William J. Lynn. June 15, 2009. http://www.defense.gov/speeches/speech.aspx?speechid=1365.
3. Ibid.
4. United States Department of Homeland Security.
5. Report to the U.S.-Canada Power System Outage Task Force. “The August 14, 2003 Blackout One Year Later: Actions Taken in the United States and Canada to Reduce Blackout Risk.” Natural Resources Canada, The United States Department of Energy. August 13, 2004.
6. Reuters. “Has Power Grid Been Hacked? U.S. Won’t Say.” Steve Holland and Randall Mikkelsen. April 8, 2009.
7. Wall Street Journal. “Electricity Grid in U.S. Penetrated by Spies.” Siobhan Gorman. April 8, 2009.
8. 60 Minutes. CBS Television. “Cyberwar: Sabotaging the System.” November 8, 2009.
9. Wired. “Brazilian Blackout Traced to Sooty Insulators, Not Hackers.” Marcelo Soares. November 9, 2009.
10. CNN.com. “Staged cyber attack reveals vulnerability in power grid.” http://edition.cnn.com/2007/US/09/26/power.at.risk/index.html.
11. Washington Post. “Cyber Incident Blamed for Nuclear Power Plant Shutdown.” Brian Krebs. June 5, 2008. http://waterfallsecurity.com/wp-content/uploads/2009/11/CyberIncidentBlamedForNuclearPowerPlantShutdownJune08.pdf.
12. Interview with Joe Weiss by Barbara McGovern. February 2010.
13. Protecting Industrial Control Systems from Electronic Threats. Joseph Weiss. Momentum Press, 2010. ISBN: 978-1-60650-197-9.
14. Control System Configuration for Electricity. “Roadmap to Secure Control Systems in the Energy Sector.” Sponsored by the United States Department of Energy and the United States Department of Homeland Security. Prepared by Energetics Incorporated.
15. Washington Post. “Eight Indicted in $9M RBS WorldPay Heist.” Brian Krebs. November 10, 2009. http://voices.washingtonpost.com/securityfix/2009/11/eight_indicted_in_9m_rbs_world.html.
16. RBS WorldBank: United States of America Versus Viktok Pleschuk, Sergei Tsurikov, Hacker 3, Oleg Covelin, Igor Grudijev, Ronald Tsoi, Evelin Tsoi, and Mihhail Jevgenov. United States District Court for the Northern District of Georgia, Atlanta Division. November 10, 2009. http://voices.washingtonpost.com/securityfix/RBSIndictment.pdf.
17. Internet World Stats. http://www.internetworldstats.com/stats.htm.
18. Times Online. “Computer Glitch Leaves Ulster Terrorists Invisible.” Sean O’Neill. September 14, 2009. http://www.timesonline.co.uk/tol/news/uk/crime/article6832946.ece.
19. “Securing Cyberspace for the 44th Presidency.” A report of the CSIS Commission. December 2008. Center for Strategic and International Studies. http://csis.org/files/media/csis/pubs/081208_securingcyberspace_44.pdf.
20. U.S. Senate Committee on Commerce, Science, and Transportation Hearings. “Cybersecurity: Next Steps to Protect Our Critical Infrastructure.” Dr. James Lewis. February 23, 2010.
21. Interview with Dr. Jim Lewis by Jeff Papows. February 2010.
22. U.S. Senate Judiciary Committee Subcommittee on Terrorism and Homeland Security at a hearing titled “Cybersecurity: Preventing Terrorist Attacks and Protecting Privacy Rights in Cyberspace.” Steven R. Chabinsky. November 17, 2009. http://judiciary.senate.gov/pdf/11-17-09%20New%20Chabinsky%20Testimony.pdf.
23. Conference on International Police Cooperation Against Cyber Crime, held in New Delhi. March 26, 2009. Central Bureau of Investigation. http://cbi.nic.in/speech/dcbi_cybercrime_20090326.php.
