Chapter 7. Governing the Government
This chapter explores the role of IT governance in support of government infrastructures from the point of view of all three of these categories. Although hundreds of IT efforts are under way to improve governments around the world, we’ll look at the influences of government on business, IT, and citizens from the broader perspectives of the following topics:
• The evolution of e-government
• The U.S. government’s renewed focus on IT
• The government’s role in the future of IT
When most people think about technology and the government, they usually fall into one of three categories—the casual yet savvy observer, the technology expert, or the business professional with a solid working knowledge of IT.
The casual observer sees the end result of technology in government, whether it’s simply accessing forms through a website or engaging in sophisticated social media campaigns that helped elect local politicians, senators, and President Obama. In developing countries, the type of user might benefit from international programs and advances in technology aimed at closing the Digital Divide.
The Digital Divide is a major initiative by governments, businesses, and academic institutions throughout the world to close the gap between those with and those without the ability to acquire skills and gain access to digital information and the Internet through computers and broadband networks.
Regardless of the level of a person’s interactions with government agencies, most casual observers would say that only when a glitch occurs do the complexities of the government infrastructure become apparent.
The second category of IT-in-government watcher is technology experts. They are more focused on the inner workings of IT in the government and making the massive behind-the-scenes complexities less complicated. This audience is more apt to focus on the interconnectedness and standards among agencies from a purely technical point of view.
The third group, business professionals, has a solid grasp of IT and the intricacies of governments and can apply business skills to improve those infrastructures. This type of experience will enable governments to maximize the world’s collective investments in technology to better serve citizens.
The role of IT is slightly different in government because the principles of profit-generating businesses don’t necessarily apply. Although vendors that provide technology products and services to government agencies can realize a profit, the goal of government is to provide effective services and deliver value to the public. Additionally, governments typically are held accountable to more regulations than a business because they deal with far more sensitive data and privacy requirements across various aspects of the populations they serve.
The Evolution of e-Government
In the 1990s, the concept of e-government really began to take hold. Technology and the rapid growth of the Internet fostered more open communication and the exchange of ideas among governments, citizens, and businesses. For developing countries, e-government also represented the promise of improved education and access to better health care and a wealth of services that may not have been accessible in more remote areas.
Since that time, great strides have been made through the use of technology in government in terms of streamlining what were traditionally paper-intensive administrative functions such as applying for licenses, contacting a local representative, or even filing taxes. Yet obstacles still exist to realizing the full benefits of e-government from the perspectives of greater transparency, collaboration, and efficiency. This is primarily due to a plateau in the return on investments and inconsistent approaches to IT architectures.
A Plateau in the Return on Investments
To some degree, an IT budget is relative to the size and scope of the organization it supports. According to Robert Holleyman, president and chief executive officer of the Washington, DC-based Business Software Alliance (BSA), the U.S. government is the world’s single-largest customer of information technology and software.1 Like any organization, the government expects a return on its technology investments in the form of productivity, cost savings, and more effective public offices.
Yet despite significant investments in e-government, the returns are starting to plateau. According to a 2009 report by McKinsey,2 the three biggest obstacles holding back e-government are
• Lack of web-related capabilities
• Reluctance to allow user participation in the creation of applications and content
Although it isn’t in the McKinsey report, I’d cite a fourth obstacle:
• Global stimulus funds and continued investments
Ineffective Governance
Ineffective governance is usually the result of inconsistent approaches to enforcing governance practices, a lack of executive support, and a corporate culture that may undervalue the benefits that can be derived from governance. To reverse the effects of ineffective governance, McKinsey recommends that government agencies adopt a governance model where e-government efforts are owned by line-of-business executives and supported by a dedicated, cross-functional team.
This approach has proven successful in the private sector. Lynn Cox, a program manager at Ford Motor Company with more than 30 years of IT experience, sees it this way: “You have to demand that governance is followed through at an enterprise level where everybody follows the same processes. Otherwise, you won’t have consistency across the board, and it leaves your infrastructure open to vulnerabilities. While you can’t completely close that window, you can make it as narrow as possible through IT governance.”3
Lack of Web-Related Capabilities
Without the ability to foster collaboration among citizens and include Web 2.0 capabilities on government websites, e-government initiatives will deliver diminishing returns. Advances from the private sector have conditioned us to expect higher-end web experiences. Therefore, when this same level of interactivity is unavailable on government sites, citizens will not return. This will add to the complexities that the old-fashioned paper-based methods of working with state, local, and national governments created.
Reluctance to Allow User Participation in the Creation of Applications and Content
Even when the government does catch up to the private sector’s advancements in social media and Web 2.0 capabilities, its culture will need to adjust to those changes. This will be a challenge, because the mind-set among many agencies is to control the communications to the public. In the interests of privacy and national security, this is critical. But the ability for citizens to voice themselves through online forums and social media can’t be overlooked.
Part of modernizing the government through technology is to embrace the innovations from the private sector without losing sight of the role that the federal, state, and local agencies play in protecting the public. Striking this balance underscores the importance of IT governance.
What government agencies should be mindful of as they embrace Web 2.0 technologies is the integrity of the applications and services that will be made available on their websites. Mash-ups are one area from the Web 2.0 world that is potentially ripe for glitches.
A mash-up is a combination of tools or data from multiple sources. Mash-ups typically collect data from multiple web pages and bring their information into one simplified web application.4
One example of a government mash-up is from the Bureau of Indian Affairs. This mash-up enables American Indians to complete an online survey about labor statistics within their tribes. This information is included in the Bureau of Labor Statistics (BLS) data and provides all citizens who access the BLS site with the most current information. In 2008, this data was collected by having American Indians fill out forms and fax them back to the BLS.5
Also, it would be impossible to overlook the efforts behind the http://www.data.gov website, which makes the government’s massive sets of data available to the public. One of the primary goals of data.gov is to “expand the creative use of government data beyond the walls of government by encouraging innovative ideas.”6 Some of these mash-ups can range from charting childhood obesity rates by state, crimes by neighborhood, or the environmental health of a specific community.
The ability to quickly create applications that can serve different agencies is a boon to productivity. But without proper policies and best practices in place, those glitches may run rampant through the government. Furthermore, if the government data is used to create a mash-up for the private sector, who is accountable for a glitch? Odds are that the fingers would point back to the government agency, which doesn’t have the infrastructure set up to test and certify third-party applications like the private sector does.
A recent discussion about mash-up capabilities in the private sector further brings this issue to light. Chuck LoCurto is the chief information officer and executive vice president of enterprise applications at Textron Financial, a diversified commercial finance company that is part of Textron Inc.’s $10.5 billion global network of aircraft, defense, industrial, and finance businesses.7
According to LoCurto, “Today, there is less line-by-line software development. By using mash-ups, open source software, and data integration tools, it can be quicker to assemble an application. What happens is that management sees the new application, gets excited about its capabilities, and may not realize that it hasn’t been put through proper IT governance practices to ensure its integrity before it’s released to the company.” To this end, LoCurto believes that “IT governance is simply nonnegotiable.”8
Global Stimulus Funds and Continued Investments
If there’s one lesson we can take away from the financial calamities of 2008, it’s that transparency is a requirement for transacting business in the global economy. Especially when you consider that by October 2009, 50 countries had committed $2.6 trillion to fiscal stimulus and pledged another $18 trillion in public funds to underwrite the financial sector and other industries.9
Before the financial meltdown, many efforts were already under way and investments had been made in fostering stronger e-government infrastructures and improving transparency. Some of these efforts include the International Telecommunication Union’s (ITU) Connect the World by 2015 program. ITU is the leading United Nations agency for information and communication technology (ICT) issues, and Connect the World by 2015 aims to connect the world’s unconnected.10 Also, the United Nations’ World Telecommunication and Information Society Day11 and the Massachusetts Institute of Technology’s IMARA project12 are still actively trying to close the Digital Divide.
Aside from the stimulus package, Congress also allocated $35 million in 2010 to the U.S. Office of Management and Budget (OMB) for the e-Government Fund.13
While these efforts remain strong and are a vital aspect of making e-government successful, progress can sometimes be held back due to geopolitical issues and cultures that may not be as open to uncensored access to the Internet.
Inconsistent Approaches to IT Infrastructures
It’s one thing to call for greater transparency and quite another to make it happen from an IT perspective. When you consider the complexities of a company’s IT infrastructure, you know that hundreds of applications and web services can be strewn throughout the network. And you also know the challenge of trying to mesh two different infrastructures. Now apply that complexity times ten, and you realize how challenging it is to instill transparency across all government offices and agencies.
The challenges of creating successful e-government initiatives from an IT perspective are not unlike the challenges facing businesses in today’s global economy. They include the following:
• IT skills issues: Developing countries do not have a stable of skilled IT professionals. Nor do they always have the required education curriculum available to train people how to build sophisticated websites, much less how to manage complex IT infrastructures. Additionally, areas with low literacy rates will be that much further behind in adopting technology.
• Physical infrastructures: In many countries, broadband access is still not at the speed or rate of efficiency that many of us take for granted in Western societies. The ITU reports that only 3.5 percent of the developing world has access to high-speed Internet.14
• Silo approaches: In lieu of being fully connected, governments are forced to build their own infrastructures. The integration efforts required to bring these agencies together will not be insignificant.
Here are some ways to address these issues:
• Establish and enforce the use of best practices and policies so that there is a consistent approach to establishing and maintaining infrastructures, which will save both time and resources.
• Create reusable IT products and services by using standards-based software. Additionally, the creation of templates and reusable web services will help contribute to the arsenal of technology tools and products available without requiring staff to create new applications from scratch.
• Consider additional tax incentives to private industry to reallocate physical assets and employee time to support e-government initiatives.
The U.S. Government’s Renewed Focus on IT
One of the major platforms of the Obama Administration is using technology to create greater transparency across the government. Mandates are in place across nearly every agency to provide more visibility into the inner workings of the federal government.15 One of the first directives put into place was the Open Government Directive. It is based on the principles of transparency, participation, and collaboration.16 Essentially, it holds each federal agency accountable to specific action items to make their activities more visible to the public through the use of technology.
These three pillars of transparency, participation, and collaboration are applied to many IT efforts currently happening across the federal government—most notably, cloud computing. While we’ve addressed cloud computing in a general business and IT context, here we’ll explore it from the perspective of the federal government.
Cloud Computing
On September 15, 2009, Federal CIO Vivek Kundra announced the government’s cloud computing initiative and introduced the http://www.apps.gov website, an “online storefront for federal agencies to quickly browse and purchase cloud-based IT services, for productivity, collaboration, and efficiency.”17 Based on Kundra’s remarks, it was clear that cloud computing would be the path to greater transparency and cost savings for the federal government. This cloud-centric path consists of the following:
• Software as a service makes software applications and web services available through a cloud as opposed to loading the full applications on every desktop or laptop.
• Platform as a service provides the environment to build and run applications, databases, and management systems.
• Infrastructure as a service makes computing resources available as needed to reduce energy consumption and related IT maintenance and management costs.
In terms of budgeting, an estimated $35 million of the Obama Administration’s $79.4 billion IT budget for the year 2011 calls for the adoption of cloud computing.18 The budget will help achieve the objectives set forth in the cloud computing strategy:
• Close the gap in effective technology use between the private and public sectors
• Reduce the number and cost of federal data centers
• Work with agencies to reduce the time and effort required to acquire IT
• Improve the alignment of technology acquisitions with agency needs
• Hold providers of IT goods and services accountable for their performance
• Improve the delivery of IT services
Federal agencies that do not adopt cloud computing will have to explain why. Agencies that fail to comply may risk losing their IT funding.19 The reasoning is easy to understand when you realize that one study estimates that the government could save between 25 and 50 percent of its IT budget by moving to the cloud.20
Those cost savings will not be realized immediately, because the move toward a cloud infrastructure will take time. As Kundra wrote in his post, “We are just beginning this undertaking, and it will take time before we can realize the full potential of cloud computing.”21
Achieving that full potential will require significant efforts across the government from an IT and cultural perspective. This is further evidenced by an April 2010 study conducted by Lockheed Martin. The study found that 70 percent of government technology decision makers in federal, defense/military, and intelligence agencies were most concerned about data security, privacy, and integrity in the cloud.22 Along with those concerns are varying levels of awareness and adoption of cloud computing throughout the government. Figure 7.1 breaks down these various levels.23
Figure 7.1 Government state of cloud engagement
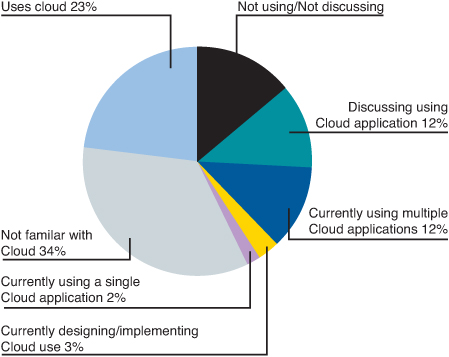
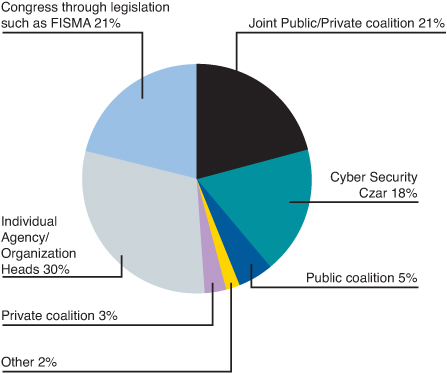
More important in the context of outlining the hidden impact of faulty software, the role of governance has yet to be determined with regard to federal cloud computing adoption. Figure 7.2 shows the differing views among government IT and business professionals in response to the question “Who should govern cloud computing?”24
Figure 7.2 Survey feedback to “Who should govern cloud computing?”
To address some of these widespread concerns, the federal government’s Interagency Cloud Computing Advisory Council created a joint authorization board that helps vet agency-wide cloud-based applications so that they can be more easily adopted by other agencies.25
By offering a form of governance through this overseeing board, federal agencies can accelerate their cloud computing efforts while reducing the risk of potentially creating and sharing faulty or unauthorized applications and services.
While the goals set forth by the cloud computing initiative may at first appear to be a daunting task, we likely won’t see the entire federal government move to a cloud as a matter of privacy and security.
Kevin McDonald,26 senior cyber security analyst for ICF International, Inc., a consultancy based in Washington, DC, explained that the cloud mandate means federal agencies will need to articulate how they’ll approach cloud computing as opposed to putting every aspect of their infrastructure in a cloud. As the author of Above the Clouds: Managing Risk in the World of Cloud Computing27 and as a member of the Tech America Cloud Computing Committee and the IAC-ACT Cloud Computing in Government committee, McDonald is entrenched in the government’s cloud computing efforts. With regard to cloud adoption, McDonald believes that “it will be a while before it happens. And even then, you have to apply it where it makes sense.”
Continued Open Source Momentum
It would be impossible to overlook the role of open source in government computing initiatives. Advances in open source have resulted in dedicated communities that foster the continued evolution of open source standards and protocols. For the government, this means greater access to technology at reduced cost without vendor lock-in.
Historically, the government has been a bit reluctant to embrace open source technologies due to the perceived fears of security breaches. But this mind-set is changing as the open source community continues to prove its value on an enterprise level.
Arguably, the nature of open source speaks to the Open Government Directive and reinforces the principles of transparency, participation, and collaboration. Yet fostering those principles and effectively applying open source technology to federal initiatives requires a level of IT governance throughout the entire infrastructure to ensure the quality of the code and its alignment with the agency’s larger goals of serving the public.
The Government’s Role in the Future of IT
The role of government in business is not exactly a new wrinkle. From the Roman Empire to the swashbuckling pirates threatening free trade on the high seas, history has countless examples of the government’s stepping in to mediate and mitigate the potential risks to its country’s economic stability. Today these issues are becoming more complicated when it comes to understanding the evolution of technology and its far-reaching implications for the future of society and business.
Three of the more complex issues are
• The IT infrastructure as the path to the future
Overseeing the Internet
Here’s a question that’s guaranteed to start a debate: How much should the government be involved when it comes to the Internet as a vehicle of commerce? Although you likely formulated your opinion on that topic years ago, it’s still very much a heated discussion both inside and outside the United States.
You may recall the Senate Commerce, Science and Transportation Committee working on the Cybersecurity Act of 2009. This bill essentially would have given the president the authority to shut down compromised federal or critical networks in the event of an emergency.28 Although this hasn’t come to pass, you can imagine the polarizing effects of the idea. As of June 2010, this issue was again raised as the “Protecting Cyberspace as a National Asset Act of 2010.”29
Privacy advocates who closely monitored both sides of the issue raised the point that the government has not yet proven that it can do a better job than the private sector at securing networks. The obvious fine line is drawn when you think about government’s role in public safety. I suspect we haven’t seen the end of this bill, especially when you consider that attacks on a country are no longer limited to physical combat; more and more of them are occurring in cyberspace.
My intention is not to invoke riots by bringing up the topic of Internet regulation and the role of government in business. I raise the subject because on many levels we are affected by the government’s role in technology. This includes a citizen’s interactions with state and federal government agencies, large corporations that must adhere to government regulations set by the countries where they conduct business, and companies that directly provide products and services to the government.
Google Sets the Stage for Future Legislation
The significant role that government has played in business has become increasingly important since the Internet ushered in new economic models by helping level the playing field across the globe. Along with those models came unprecedented challenges and opportunities regarding overseas commerce. Still uncharted territory in many ways after all these years, we are likely to see the incidents of today evolve into major legislation in the near future as companies become more selective about how, when, and where they conduct business. Google is a good example.
In January 2010, Google found itself entangled in a very public issue regarding its operations in China. The previous December, hackers from China are believed to have broken into the Google corporate infrastructure with the primary goal of accessing the Gmail accounts of human rights activists, among others.30
The U.S. government got involved, and Secretary of State Hilary Clinton asked for a thorough investigation into the matter,31 while the Chinese government denied its involvement in the attacks.32 Exacerbating the situation was Google’s public statement that it believed as many as 33 other major technology companies had also been hacked by the Chinese government.33
As the Google China story continued to make headlines, the search engine giant stopped censoring some search results, which was a stipulation set in place by the Chinese government in 2005.34 This mutual violation of trust in agreed-upon business policies eventually led to Google’s formal exit from mainland China in the spring of 2010. By July 2010, Google was back in China at least through 2011 according to the agreed-upon terms.
When we think of glitches, it’s easy to draw a direct line between error and impact. However, the Google situation in China speaks to the need for greater visibility into the infrastructure to protect it from hackers and provide a sound platform for conducting business.
There are many different ways to view this situation from the perspectives of free trade, unrestricted Internet access, privacy, human rights, international treaties, and so on. On a global stage, this is the type of incident that can force new legislation regarding overseas technology ventures. While we don’t want to create new laws as a knee-jerk reaction to negative experiences with overseas partners, we also want to protect ourselves as we continue to rely on a global infrastructure to sustain our businesses.
Public Safety
There is a real safety factor to be considered in the context of the intersection of technology in business and government. Aside from the proposed Cybersecurity Act of 2009, there are networks and infrastructures that demand IT governance to protect and serve the public in the event of an emergency.
More specifically, emergency response technology is differentiated by its ability to bypass the existing network infrastructure when power lines and/or systems are down, thereby making sure the proper help is immediately available for citizens. In the event of an emergency, a sophisticated and glitch-free infrastructure enables local municipalities to dispatch emergency crews, alert hospitals, and bring in backup help if necessary. Yet this level of sophistication is not as widespread as one would hope. Despite the advances in technology, it is still very much a long-term goal for the majority of cities and towns throughout the world.
To make this vision a reality, local municipalities need to work with federal agencies. The good news is that a lot of work is already under way. According to Sue Levine, project manager of Regional Interoperable Communications at San Diego County Emergency Services, “I think the coordinated efforts are something that any region in any area can work on, but it really centers around governance and agency cooperation across many levels of government.”35
As Levine pointed out, the Department of Homeland Security (DHS) has focused on working with state and local municipalities to ensure that people are working together toward a common goal. This common goal, from an IT perspective, requires a common platform. In fact, the 2010 guidance for the Urban Area Security Initiative (UASI) grants from the DHS requires adherence to the APCO Project 25 standard for public safety digital radio. The APCO Project 25 standard is aimed at standardizing communications among federal, state, city, and county agencies and vendors for public safety digital radio.
Additionally, public safety agencies have rallied around the long-term evolution (LTE) standard that we addressed in Chapter 6. To recap, this highly anticipated platform for mobile voice offers global roaming capabilities across different operators so that the network doesn’t keep a message from reaching its destination due to incompatibilities in the infrastructure. LTE will be critical in the creation of a nationwide, interoperable broadband network.
The IT Infrastructure as the Path to the Future
Technology, in its purest form, will continue to connect people around the globe through computers and networks. As we’ve seen and will continue to see, technology is vital to supporting efforts around e-government, closing the Digital Divide, and protecting citizens.
From a much broader perspective, the IT infrastructure will also play a critical role in the economic development of nations. Here are some of these efforts that are supported by the government:
• Agriculture: Using technology to connect rural farmers so that they can share best practices with regard to climate, human environments, and day-to-day farming operations is critical to the sustainability of our food supply.
• Water: This involves enabling research to support purification processes and strengthen the infrastructures that literally make water available through a pipe. Today, dirty water kills more people than wars or other violence. Up to 60 percent of potable water is lost due to leaky pipes and poorly maintained sewage networks.36 Much as we discussed in the section on providing better support for our energy supplies, technology can also play a role in fortifying and designing the infrastructures for the world’s water supply.
• Health care: Providing technology resources to developing nations won’t have a direct effect on curing diseases. However, making technology resources available so that health care workers around the world can communicate with and further educate each other is well worth the investment. For example, the Health InterNetwork (HINARI), led by the World Health Organization, gives public health workers, researchers, and policy makers access to the most current medical information from more than 6,000 journals and medical textbooks. A consortium consisting of representatives from businesses, academia, and government provides the information. Some of these members include the world’s leading biomedical publishers, Microsoft, Yale University Library, and the U.S. National Library of Medicine.37
In these few examples, you can see how important it is to build a sound IT infrastructure to sustain and advance economic development throughout the world.
Next Steps
The strength of the federal government’s infrastructure affects all of us in our business and personal lives. Although we need to protect intellectual property and data for security purposes, we also need to enable other countries to use technology to thrive. This might sound like a contradiction in terms, but it really isn’t. True competitive advantage is not about tripping up the smaller players through faulty technology. Competitive advantage is about opening the channels of opportunity to businesses and countries that otherwise might not be able to compete.
From the view of the IT infrastructure, the following are recommendations to further complement the many efforts that are currently under way to support governments and citizens around the world:
• Create a global IT repository. This repository of software tools, frameworks, and web services would be made available for free to developing countries so that infrastructures could be created more easily and quickly. The Global Governance IT Council that was suggested in Chapter 3 would oversee the repository. Their role would be to review, test, and certify the technology before it was made available in the repository so that users would be assured of its validity and quality.
• Appoint IT governance leads at government agencies. This senior-level position would oversee the IT governance efforts across an agency and would be responsible for assembling a cross-agency team to help ensure the creation and enforcement of policies and best practices.
• Establish a global emergency network. This is certainly an enormous undertaking. However, the concept of being able to more effectively connect different nations through a specialized network in the event of catastrophe is worth considering. There are, of course, many obstacles to making this a reality because of IT resources, capital, broadband availability, different flavors of mobile platforms, and so on. However, as each country looks at enhancing connectivity through standards such as LTE, it’s not inconceivable to imagine a future with a separate global emergency network.
As we close this chapter on governing the government, I recall a conversation I had with Robert Holleyman from the BSA38 about how we can all improve government infrastructures. He shared a terrific analogy regarding the institution of IT governance as part of the software development process.
Holleyman believes IT governance is very similar to how we learned to use the seat belts in our automobiles. As you may recall, this reflects the same thoughts shared by cyber security expert Dr. Jim Lewis. Both of these industry experts pointed out that before seat belts were mandatory, they weren’t as widely used. As soon as the law required the use of seat belts, we had to remember to buckle up when we got in the car. Now the “click it or ticket” American catchphrase is stuck in our heads, and buckling up has become a reflex. Following the seat belt analogy further, we all realize that seat belts won’t eliminate injuries, but they can certainly reduce the number and severity of injuries.
We should take the same approach to IT governance for the government in terms of building in security, policies, and best practices. The end result will be the most efficient, bulletproof software products possible that will better protect and serve citizens.
Endnotes
1. Interview with Robert Holleyman by Jeff Papows. December 2009.
2. McKinsey Quarterly. “e-Government 2.0.” July 2009.
3. Interview with Lynn Cox by Kathleen Keating. February 2010.
4. WiseGeek. “What Is a Mash-Up?” http://www.wisegeek.com/what-is-a-mash-up.htm.
5. Washington Technology. “Mashups go mainstream as agencies mix data with social media.” Rutrell Yasin. January 28, 2010.
6. http://www.data.gov. An official website of the United States Government.
7. Textron website. http://www.textron.com/about/company/index.jsp.
8. Interview with Chuck LoCurto by Kathleen Keating. May 2010.
9. United Nations E-Government Survey 2010. “Leveraging E-Government at a Time of Financial and Economic Crisis.”
10. International Telecommunication Union. “Connect the World by 2015.”
11. International Telecommunication Union. World Telecommunication and Information Society Day. http://www.itu.int/wtisd/.
12. Massachusetts Institute of Technology. IMARA Project. http://imara.csail.mit.edu/?q=about.
13. Office of Management and Budget. Office of E-Government and Information Technology. http://www.whitehouse.gov/omb/e-gov/.
14. International Telecommunication Union. “Measuring the Information Society 2010.” February 2010.
15. The White House. Open Government Flagship Initiatives. http://www.whitehouse.gov/open/documents/flagship-initiatives.
16. Executive Office of the President. Office of Management and Budget. Memorandum for the Heads of Executive Departments and Agencies. December 2009.
17. Office of Social Innovation and Civic Participation. “Streaming at 1:00: In the Cloud.” Posted by Vivek Kundra. September 15, 2009. http://www.whitehouse.gov/blog/Streaming-at-100-In-the-Cloud.
18. Budget of the U.S. Government, Fiscal Year 2011. http://www.whitehouse.gov/omb/budget/fy2011/assets/budget.pdf.
19. Channel Insider. “Feds Now Need to Explain Lack of Cloud Plans.” http://blogs.channelinsider.com/cloud_computing/content/government/feds_now_need_to_explain_lack_of_cloud_plans.html.
20. Brookings Institution. “Saving Money Through Cloud Computing.” Darrell M. West. April 7, 2010.
21. Office of Social Innovation and Civic Participation. “Streaming at 1:00: In the Cloud.” Posted by Vivek Kundra. September 15, 2009. http://www.whitehouse.gov/blog/Streaming-at-100-In-the-Cloud.
22. “Awareness, Trust and Security to Shape Government Cloud Adoption.” A white paper by Lockheed Martin, LM Cyber Security Alliance, Market Connections, Inc. April 2010.
23. Ibid.
24. Ibid.
25. Brookings Institution. “The Economic Gains of Cloud Computing.” An Address by Federal Chief Information Officer Vivek Kundra. Washington, DC. April 7, 2010. http://www.brookings.edu/~/media/Files/events/2010/0407_cloud_computing/20100407_cloud_computing.pdf.
26. Interview with Kevin McDonald by Kathleen Keating. February 2010.
27. Above the Clouds: Managing Risk in the World of Cloud Computing. Kevin T. McDonald. IT Governance Publishing, 2010.
28. The Library of Congress. Cybersecurity Act of 2009. http://thomas.loc.gov/cgi-bin/bdquery/z?d111:s.00773:.
29. The Protecting Cyberspace as a National Asset Act of 2010. United States Homeland Security and Governmental Affairs Committee.
30. The Official Google blog. “A new approach to China.” http://googleblog.blogspot.com/2010/01/new-approach-to-china.html.
31. Remarks on Internet Freedom. Hilary Rodham Clinton. January 21, 2010.
32. CNN. “China’s Government Denies Involvement in Alleged Cyber Attacks.” January 24, 2010.
33. The Official Google blog. “A new approach to China.” http://googleblog.blogspot.com/2010/01/new-approach-to-china.html.
34. “Google May Quit China After Activist Attacks.” Glenn Chapman (AFP). January 12, 2010. http://www.google.com/hostednews/afp/article/ALeqM5iNi073Lf9J3llWZbddlt8FUsyX2g.
35. Interview with Sue Levine by Barbara McGovern. January 2010.
36. United Nations World Water Day, 2010.
37. World Health Organization. HINARI Access to Research Initiative. http://www.who.int/hinari/HINARI_INFOSHEET_ENGLISH_2009.pdf.
38. Interview with Robert Holleyman by Jeff Papows. December 2009.
